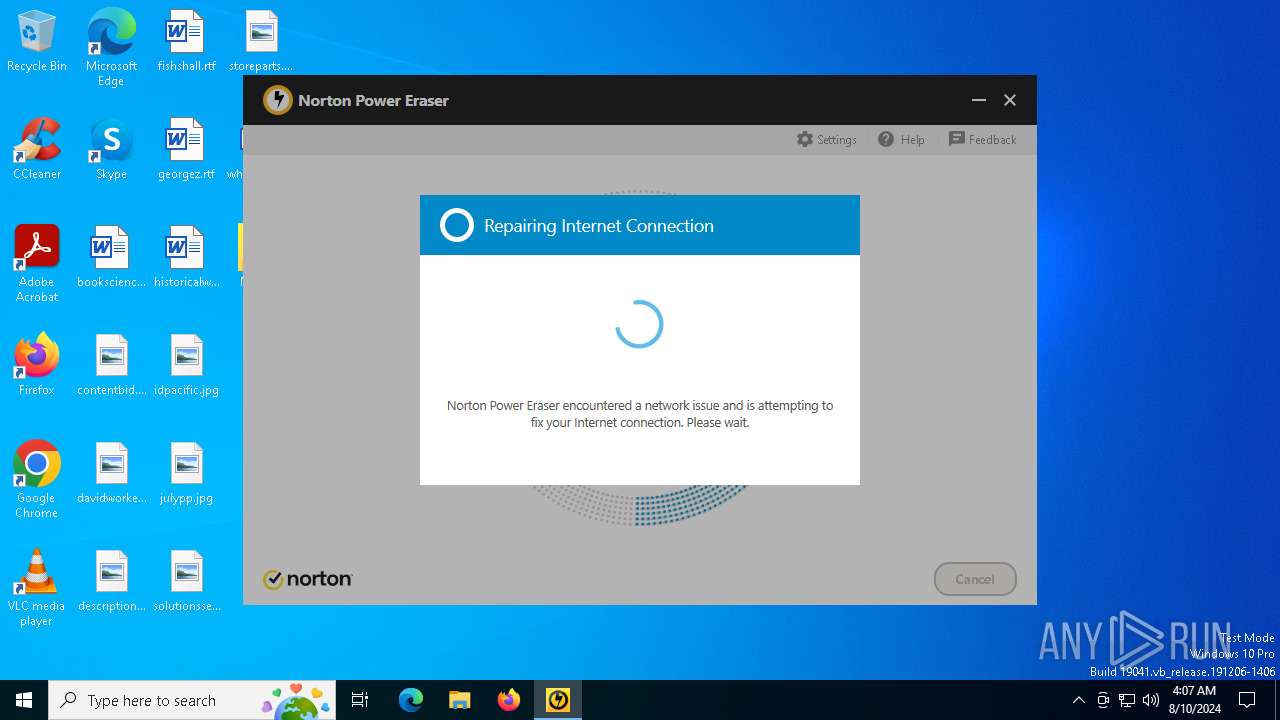
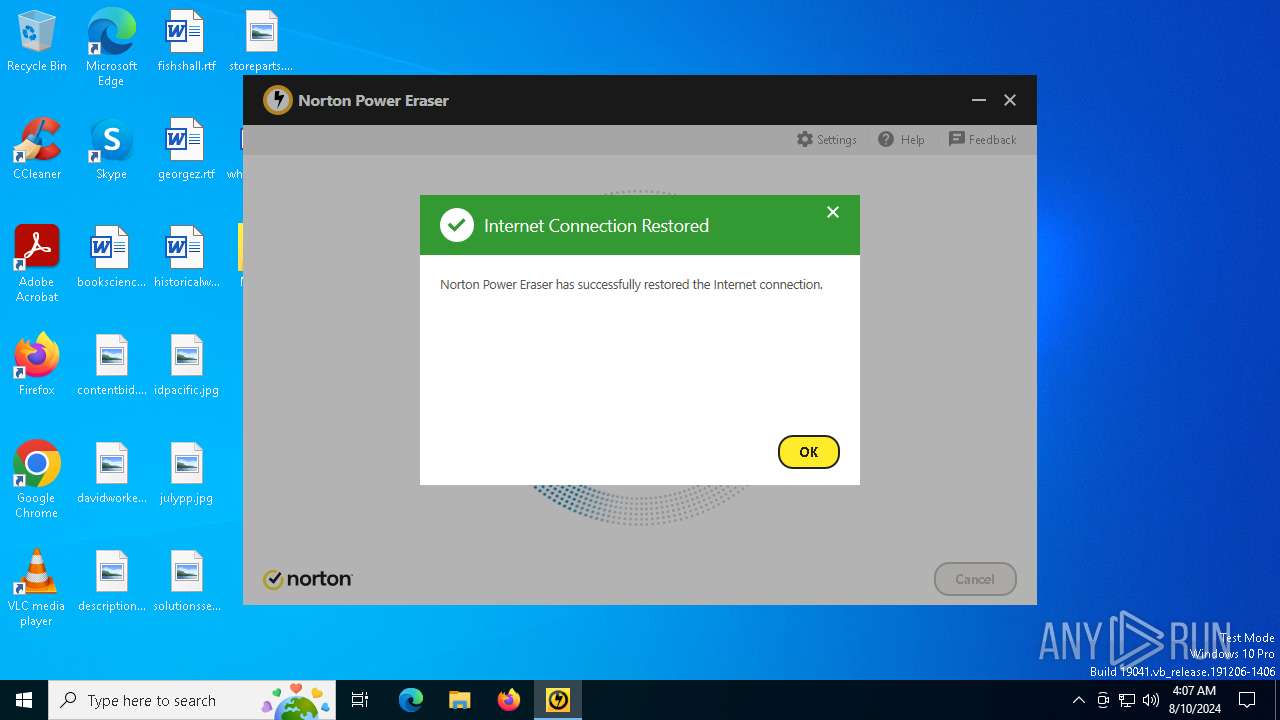
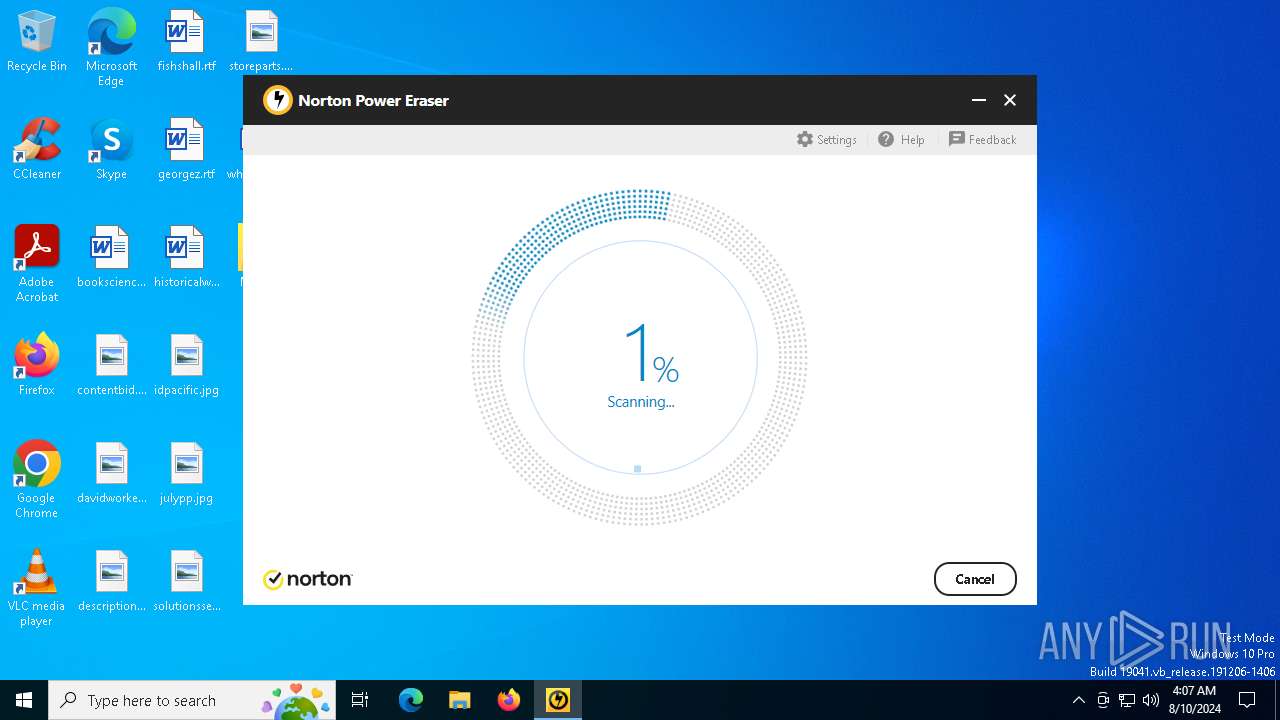
| File name: | NPE.exe |
| Full analysis: | https://app.any.run/tasks/40bcd41b-27dd-4090-9f3b-5eb52bf3c778 |
| Verdict: | Malicious activity |
| Analysis date: | August 10, 2024, 04:05:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | DDFC82CF4EAB81965E3EC8CA8915B00A |
| SHA1: | 1E5B94BE6922E6198AFE39A7FC695DB291BFFCF6 |
| SHA256: | 4819D87FE9D0D0485FE85A3843A3E3ECD61EBE50A115DAD01EC10275272BE82A |
| SSDEEP: | 98304:1gofEjfq3qcr6qburyFWcjIoiUS7PxMwBN+dwiRLcfNKxRLYZRMlfx9RWaAznMAn:Ghu7QdNyJCTwJWFEG |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops the executable file immediately after the start
- NPE.exe (PID: 7024)
Creates files in the driver directory
- NPE.exe (PID: 7024)
Drops a system driver (possible attempt to evade defenses)
- NPE.exe (PID: 7024)
Executable content was dropped or overwritten
- NPE.exe (PID: 7024)
Reads security settings of Internet Explorer
- NPE.exe (PID: 7024)
Checks Windows Trust Settings
- NPE.exe (PID: 7024)
INFO
Checks supported languages
- NPE.exe (PID: 7024)
Creates files in the program directory
- NPE.exe (PID: 7024)
Creates files or folders in the user directory
- NPE.exe (PID: 7024)
Reads the computer name
- NPE.exe (PID: 7024)
Reads the machine GUID from the registry
- NPE.exe (PID: 7024)
Reads the software policy settings
- NPE.exe (PID: 7024)
Reads Environment values
- NPE.exe (PID: 7024)
Reads product name
- NPE.exe (PID: 7024)
Checks proxy server information
- NPE.exe (PID: 7024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2022:07:07 19:40:02+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.14 |
| CodeSize: | 8996352 |
| InitializedDataSize: | 7988736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x64f1c4 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.6.0.2153 |
| ProductVersionNumber: | 6.6.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | NortonLifeLock Inc. |
| FileDescription: | Norton Power Eraser |
| FileVersion: | 6.6.0.2153 |
| InternalName: | NPE |
| LegalCopyright: | Copyright (c) 2022 NortonLifeLock Inc. All rights reserved. |
| OriginalFileName: | NPE.exe |
| ProductName: | Norton Power Eraser |
| ProductVersion: | 6.6 |
Total processes
115
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6868 | "C:\Users\admin\Desktop\NPE.exe" | C:\Users\admin\Desktop\NPE.exe | — | explorer.exe | |||||||||||
User: admin Company: NortonLifeLock Inc. Integrity Level: MEDIUM Description: Norton Power Eraser Exit code: 3221226540 Version: 6.6.0.2153 Modules
| |||||||||||||||
| 7024 | "C:\Users\admin\Desktop\NPE.exe" | C:\Users\admin\Desktop\NPE.exe | explorer.exe | ||||||||||||
User: admin Company: NortonLifeLock Inc. Integrity Level: HIGH Description: Norton Power Eraser Version: 6.6.0.2153 Modules
| |||||||||||||||
Total events
4 640
Read events
4 635
Write events
4
Delete events
1
Modification events
| (PID) Process: | (7024) NPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\LocalDumps\NPE.exe |
| Operation: | write | Name: | DumpType |
Value: 0 | |||
| (PID) Process: | (7024) NPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\LocalDumps\NPE.exe |
| Operation: | write | Name: | DumpCount |
Value: 4 | |||
| (PID) Process: | (7024) NPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\LocalDumps\NPE.exe |
| Operation: | write | Name: | DumpFlags |
Value: 0 | |||
| (PID) Process: | (7024) NPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\LocalDumps\NPE.exe |
| Operation: | write | Name: | DumpFolder |
Value: C:\Users\admin\AppData\Local\NPE\LocalDumps | |||
| (PID) Process: | (7024) NPE.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\WMI\Autologger\NPETraceSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
1
Suspicious files
9
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7024 | NPE.exe | C:\ProgramData\Norton\NPE\NPEsettings.dat.log | abr | |
MD5:84932679368B3216119FF54406E82EB3 | SHA256:E93EE39BBAFD75DEF229AEAD6C05E2658958E4D600D816681189576C27ECB520 | |||
| 7024 | NPE.exe | C:\ProgramData\Norton\NPE\NPEsettings.dat | binary | |
MD5:8DF30707ADE007F7D5F6819CEE62CC4A | SHA256:E2CCE357FD88FBACE4A41CA8D6A78D2871927FAD96016BD3EF6B7ACC1808801E | |||
| 7024 | NPE.exe | C:\Windows\Temp\BC7EF976.tmp | binary | |
MD5:DC4EE428EB6DC11F0955C66E92F85779 | SHA256:7BBF1547FA62E5B93F0F0F1F172FBC1BC2804EAAC81E2F486FDCF2F22B2E1B70 | |||
| 7024 | NPE.exe | C:\Users\admin\AppData\Local\NPE\ErrMgmt\SQCLIENT.dat.log | binary | |
MD5:683C1D60FAB1590F48F49168A1560FFC | SHA256:7F976066406C32D2A643C2091085AA518BEDC2FC0B11225B9F1AE7E981771A69 | |||
| 7024 | NPE.exe | C:\Windows\Temp\6E789724.tmp | binary | |
MD5:DC4EE428EB6DC11F0955C66E92F85779 | SHA256:7BBF1547FA62E5B93F0F0F1F172FBC1BC2804EAAC81E2F486FDCF2F22B2E1B70 | |||
| 7024 | NPE.exe | C:\Windows\System32\drivers\SMR540.SYS | executable | |
MD5:836BF59E8E3F6BBA0BD958B63FC3A6A2 | SHA256:48C18955D0BB46AAF2F95B31CD5F34478DB9E3A25B7600BC3F1DDC43241C0A5E | |||
| 7024 | NPE.exe | C:\Users\admin\AppData\Local\NPE\ErrMgmt\SQCLIENT.dat | binary | |
MD5:62D3B68970109DED90C10FD398497FE5 | SHA256:4424674553EBB44D2B06C5B9767697AE5BF3256B1A07098E07D5786A60441D5F | |||
| 7024 | NPE.exe | C:\ProgramData\Norton\{086A63F0-6B13-4F29-9695-134E7A01E963}\LC.INI | text | |
MD5:98D3204BACC3C60C9F8AE8230849A074 | SHA256:B658B0BA42208761A3C304CDFA25B30BDDE82680550D196731CC14DC3D23CA85 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
24
DNS requests
64
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 40.78.85.248:443 | https://vss.norton.com/npe/availability | unknown | text | 10 b | unknown |
— | — | POST | 200 | 52.188.144.172:443 | https://stats.norton.com/n/p?module=9801&product=NPE&version=6.6.0.2153&language=EN&mid=B4228EFB-3970-4753-B0AF-80510E824C15&platform=windows&os=Microsoft%20Windows%2010%20Professional%2010.00.19045%20(64-bit)&a=2037 | unknown | text | 13 b | unknown |
— | — | GET | 200 | 40.78.85.248:443 | https://vss.norton.com/npe/availability | unknown | text | 10 b | unknown |
— | — | POST | 200 | 13.64.142.149:443 | https://stats.norton.com/n/p?module=9801&product=NPE&version=6.6.0.2153&language=EN&mid=B4228EFB-3970-4753-B0AF-80510E824C15&platform=windows&os=Microsoft%20Windows%2010%20Professional%2010.00.19045%20(64-bit)&a=2010&b=System | unknown | text | 13 b | unknown |
— | — | GET | 200 | 52.239.174.100:443 | https://mue2supportsmrdefprodsa.blob.core.windows.net/smrdefinitions/smrscd.7z | unknown | compressed | 6.27 Kb | unknown |
— | — | GET | 200 | 52.239.174.68:443 | https://mue2supportsmrdefprodsa.blob.core.windows.net/smrdefinitions/smrdat.7z | unknown | compressed | 282 Kb | unknown |
— | — | POST | 200 | 52.188.144.172:443 | https://stats.norton.com/n/p?module=9801&product=NPE&version=6.6.0.2153&language=EN&mid=B4228EFB-3970-4753-B0AF-80510E824C15&platform=windows&os=Microsoft%20Windows%2010%20Professional%2010.00.19045%20(64-bit)&a=2041 | unknown | text | 13 b | unknown |
— | — | GET | 200 | 52.239.174.68:443 | https://mue2supportsmrdefprodsa.blob.core.windows.net/smrdefinitions/smrdat.7z | unknown | compressed | 282 Kb | unknown |
— | — | GET | 200 | 52.239.174.68:443 | https://mue2supportsmrdefprodsa.blob.core.windows.net/smrdefinitions/smrscd.7z | unknown | compressed | 6.27 Kb | unknown |
— | — | POST | 200 | 52.188.144.172:443 | https://stats.norton.com/n/p?module=9801&product=NPE&version=6.6.0.2153&language=EN&mid=B4228EFB-3970-4753-B0AF-80510E824C15&platform=windows&os=Microsoft%20Windows%2010%20Professional%2010.00.19045%20(64-bit)&a=6503&b=SMRInit | unknown | text | 13 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5060 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7024 | NPE.exe | 40.78.85.248:443 | vss.norton.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
7024 | NPE.exe | 13.64.142.149:443 | stats.norton.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
7024 | NPE.exe | 52.239.174.100:443 | mue2supportsmrdefprodsa.blob.core.windows.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
7024 | NPE.exe | 52.188.144.172:443 | stats.norton.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
vss.norton.com |
| whitelisted |
stats.norton.com |
| whitelisted |
mue2supportsmrdefprodsa.blob.core.windows.net |
| whitelisted |
Threats
Process | Message |
|---|---|
NPE.exe | Information at self.ready (res:main_frame.tis(13))
'main_frame.tis' loaded
|
NPE.exe | Information at showEulaPage (res:main_frame.tis(146))
'showEulaPage()' called
|
NPE.exe | Information at loadFrameContent (res:main_frame.tis(33))
'loadFrameContent(eula)' called
|
NPE.exe | Information at updateCurrentLangCode (res:main_frame.tis(714))
main_frame.tis : 'updateCurrentLangCode' called
|
NPE.exe | Information at updatePageDirection (res:main_frame.tis(753))
main_frame.tis : 'updatePageDirection' called
|
NPE.exe | Information at updateProductName (res:main_frame.tis(761))
main_frame.tis : 'updateProductName' called
|
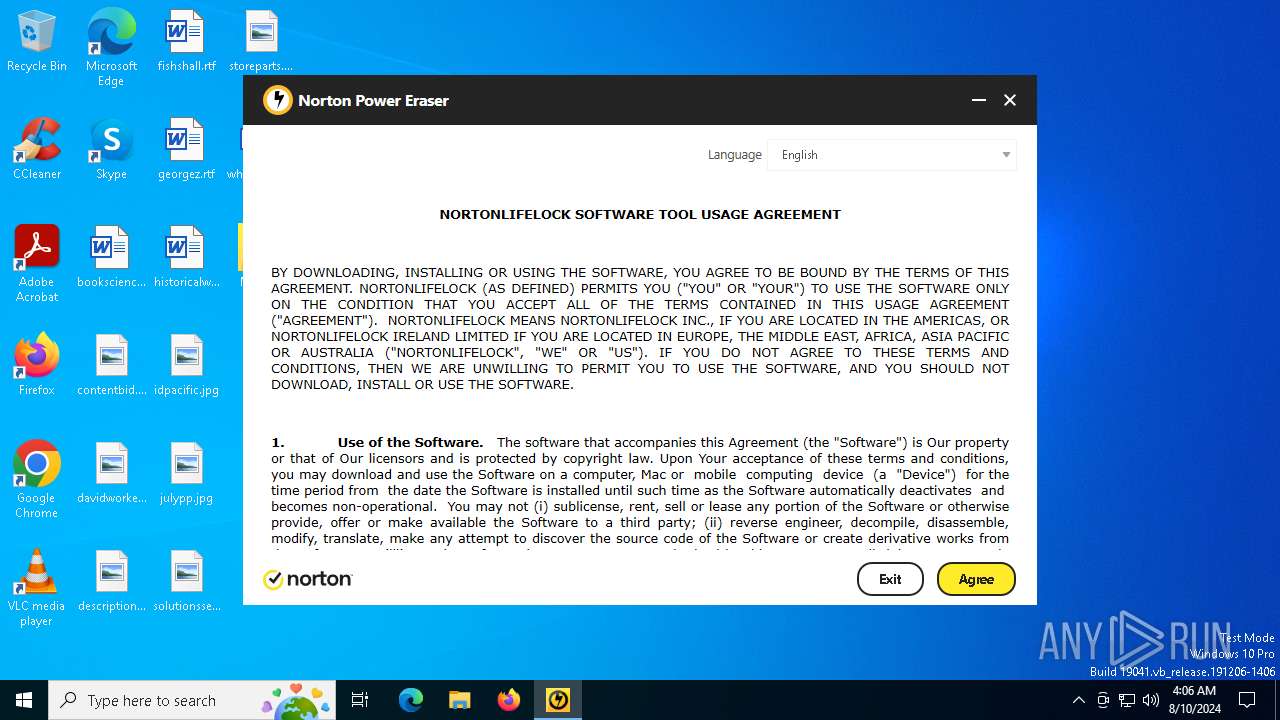
NPE.exe | Information at self.ready (res:eula.tis(8))
'eula.tis' loaded
|
NPE.exe | Information at setup (res:eula.tis(16))
'eula.tis: setup()' called
|
NPE.exe | Information at setup (res:eula.tis(22))
Initial Language ID: 1033
|
NPE.exe | Information at assignEULA (res:eula.tis(79))
Assigning Language ID: 1033
|