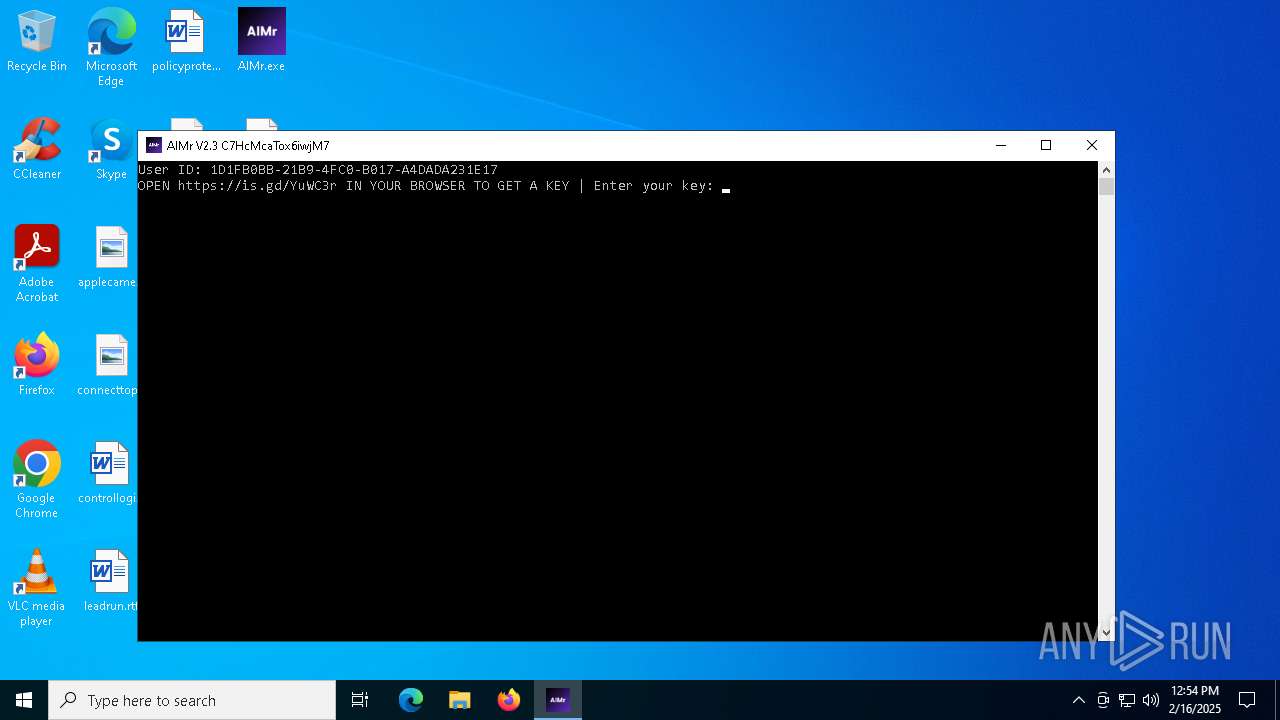
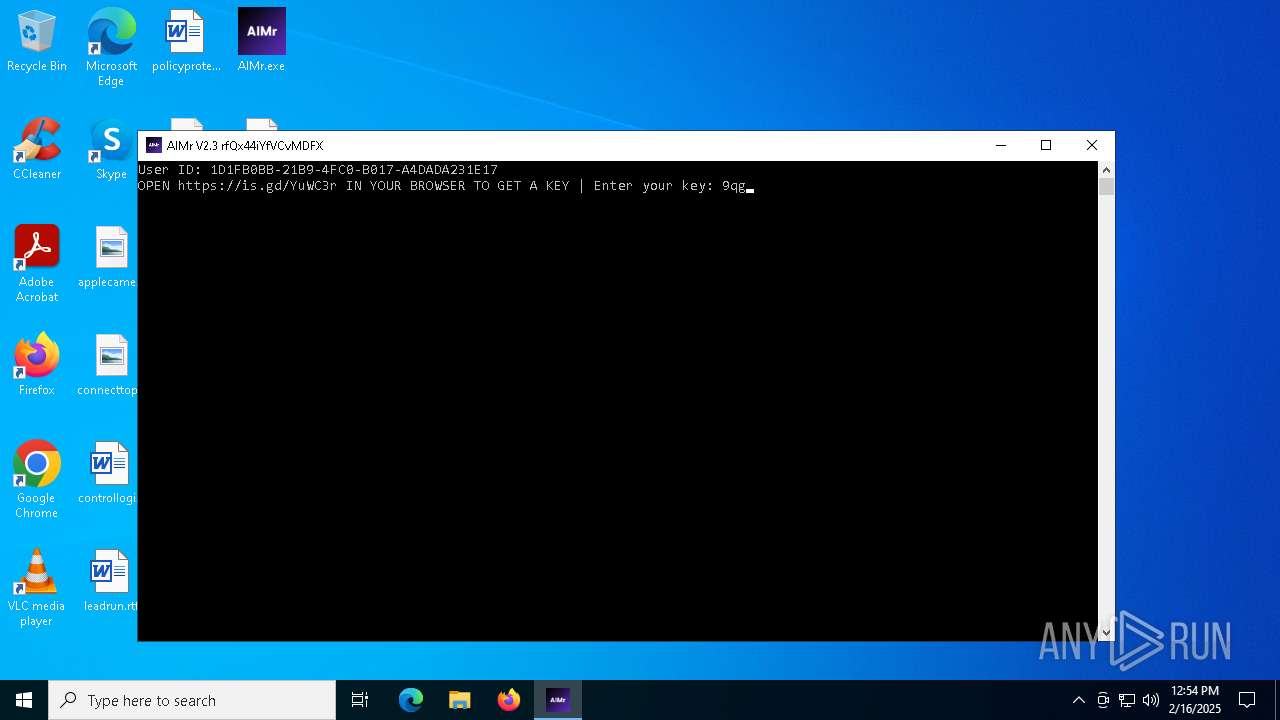
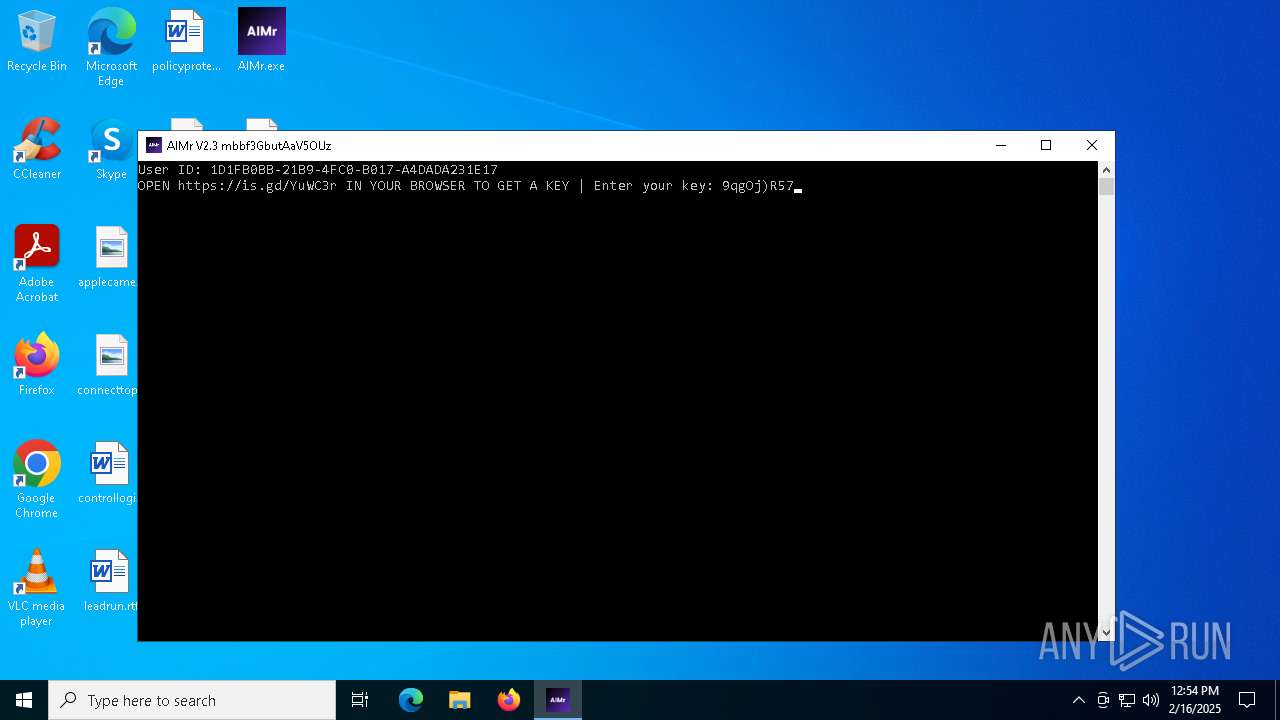
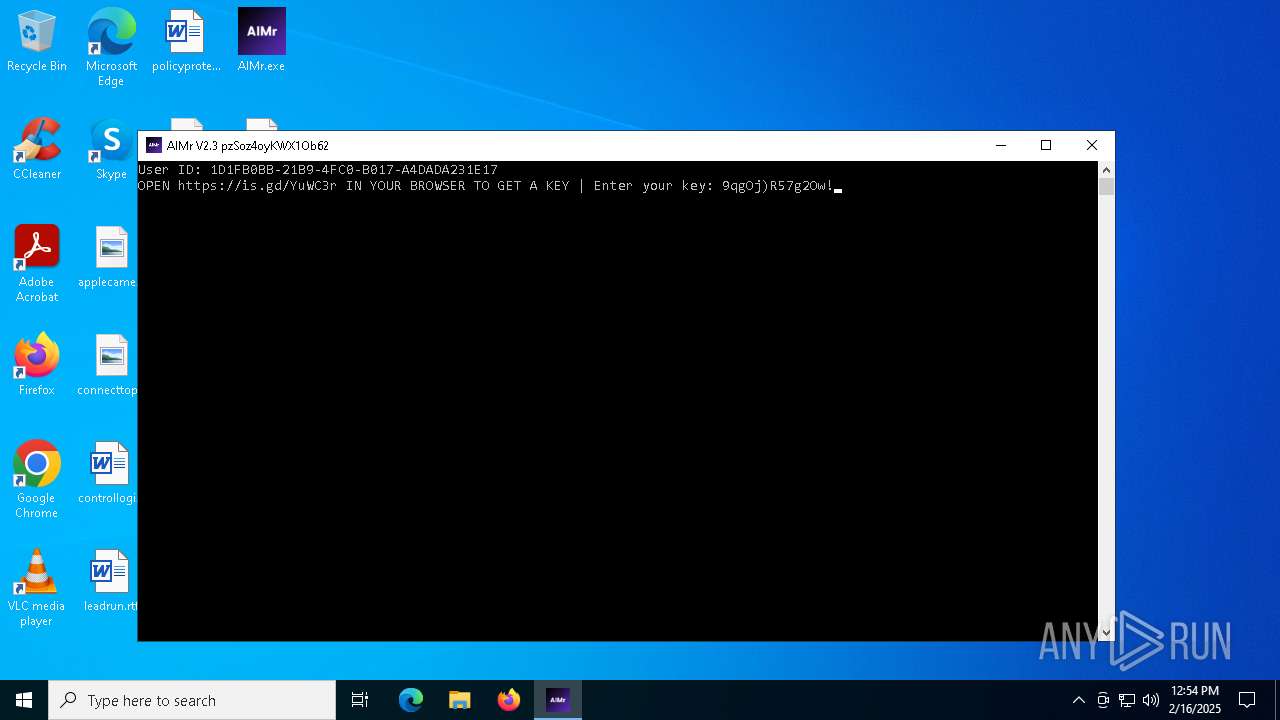
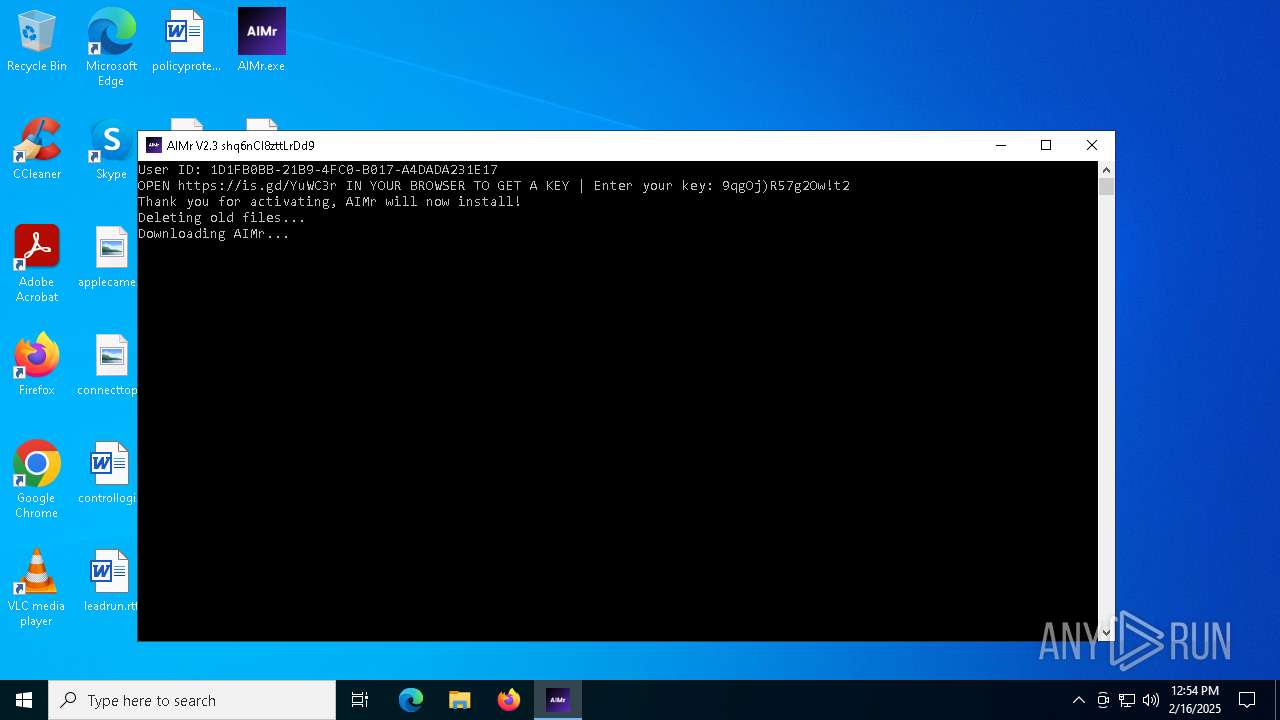
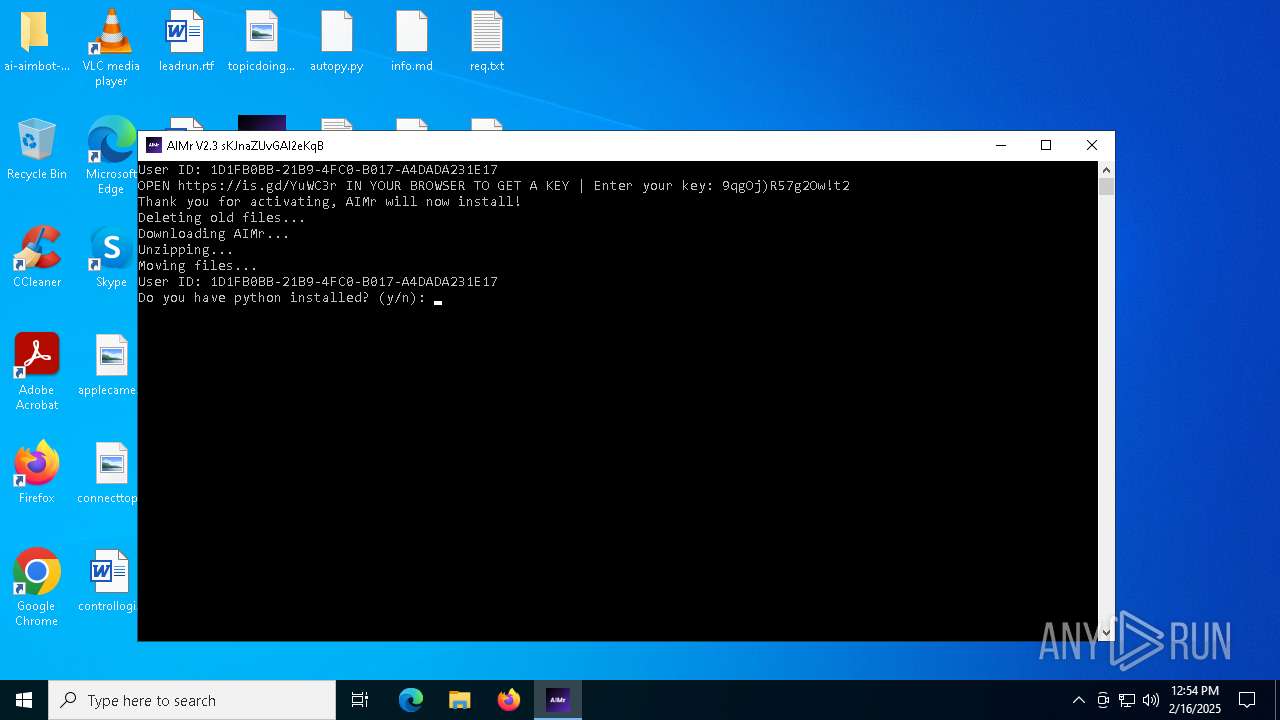
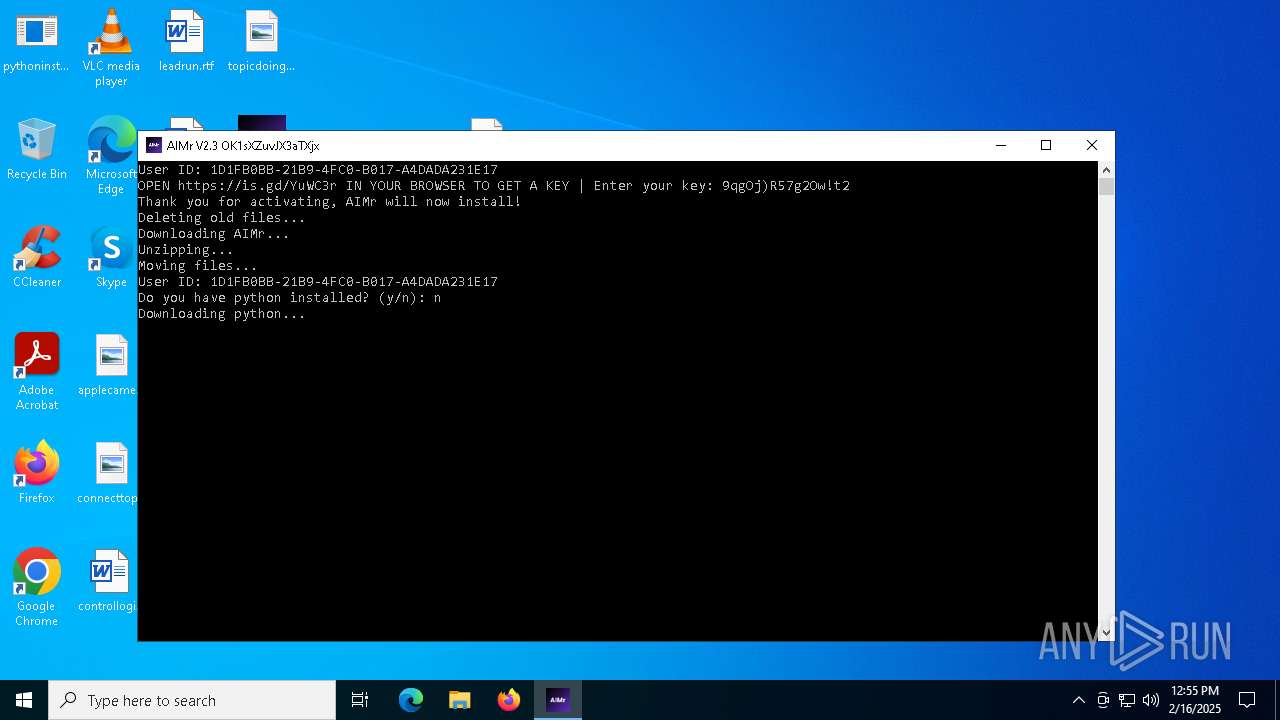
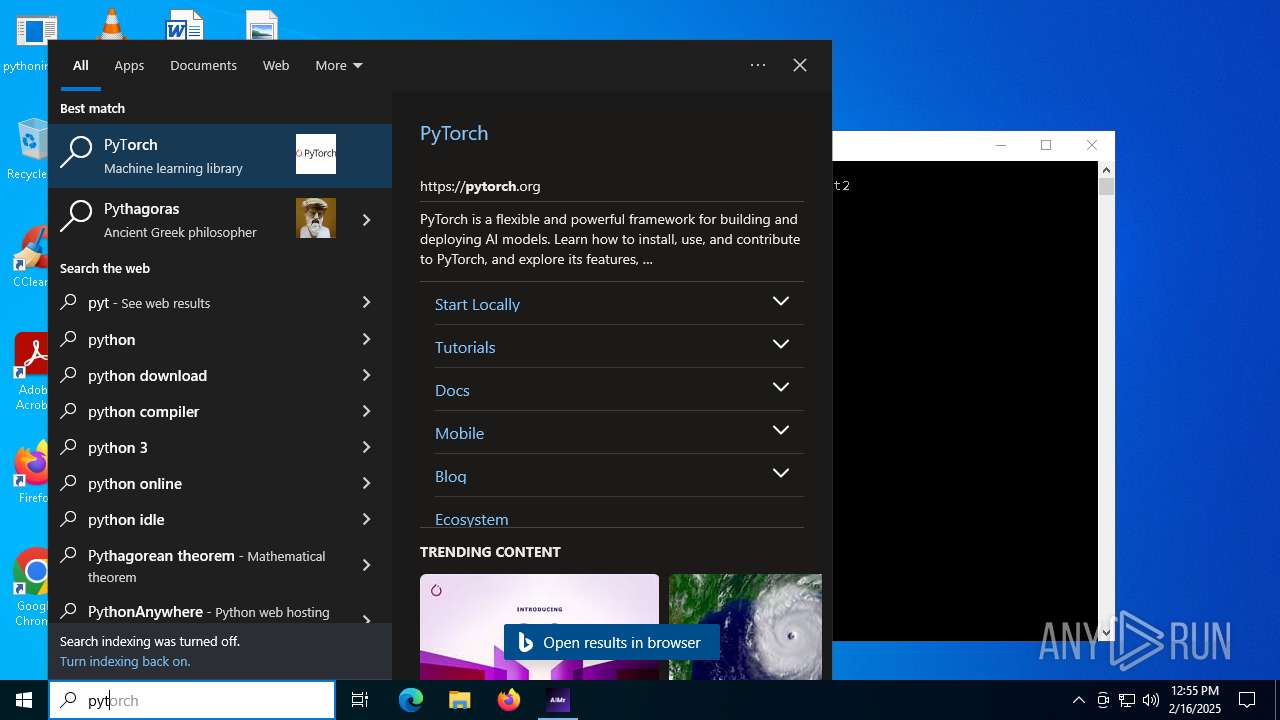
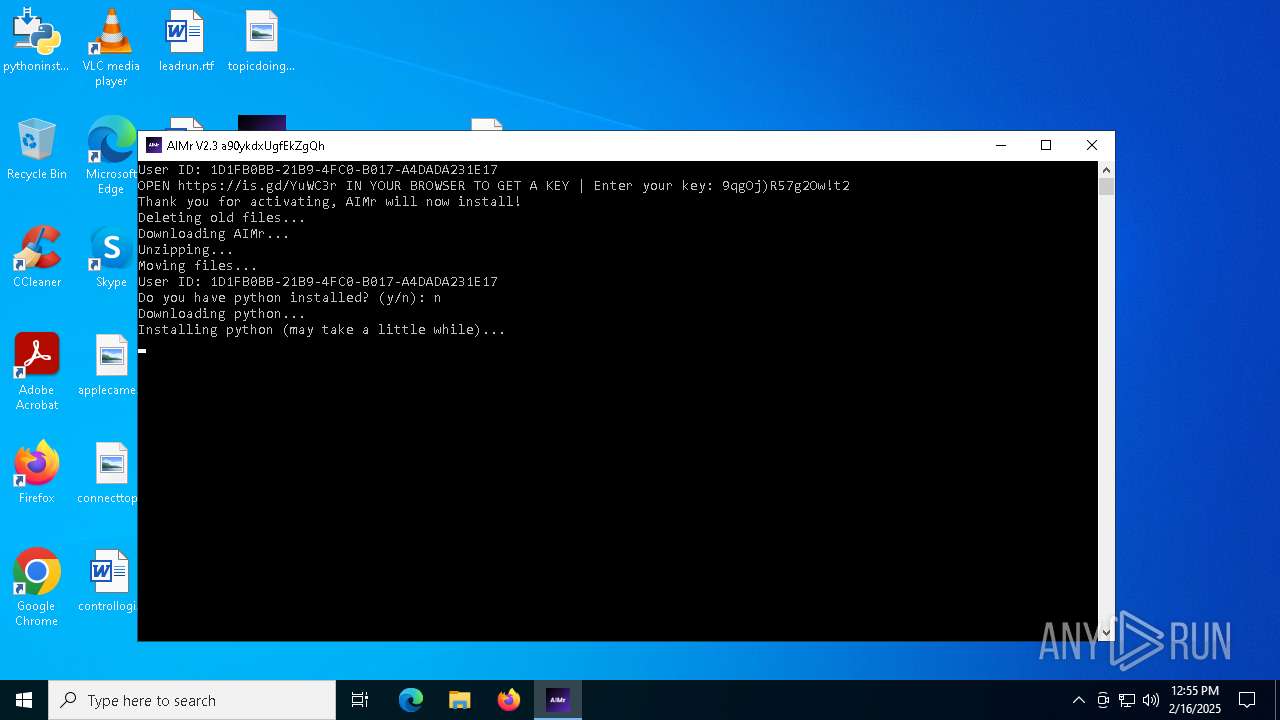
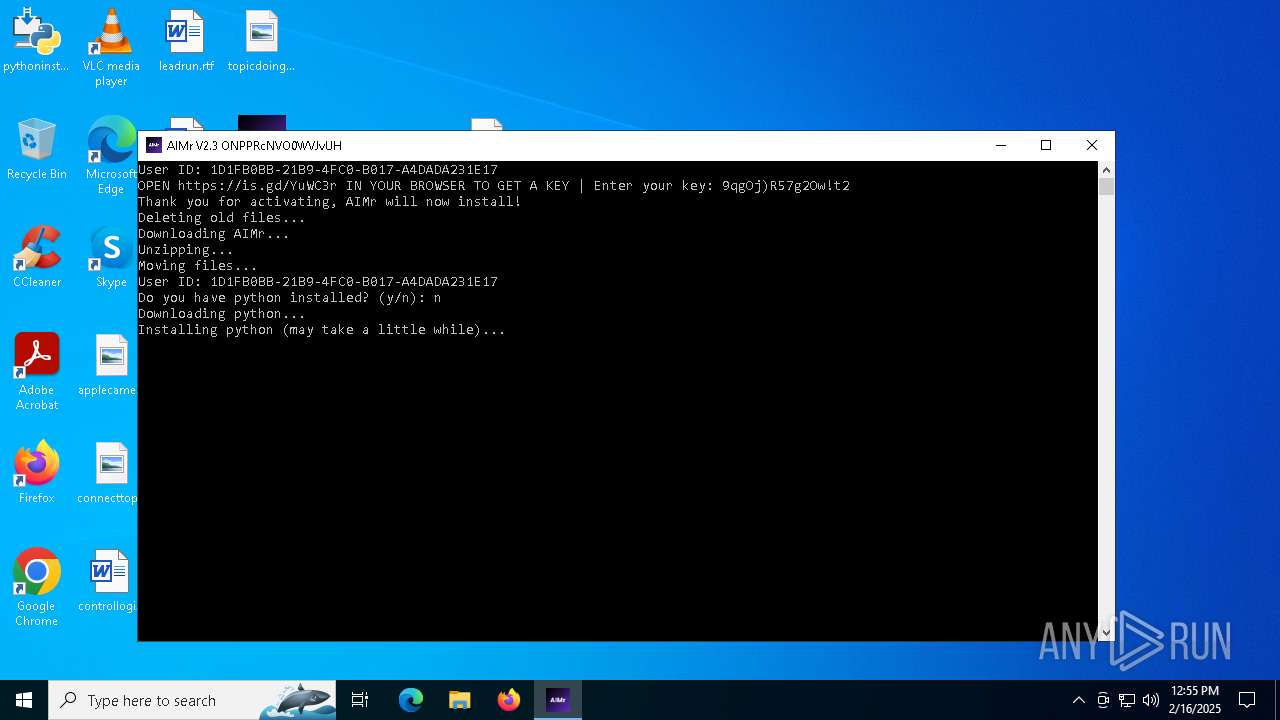
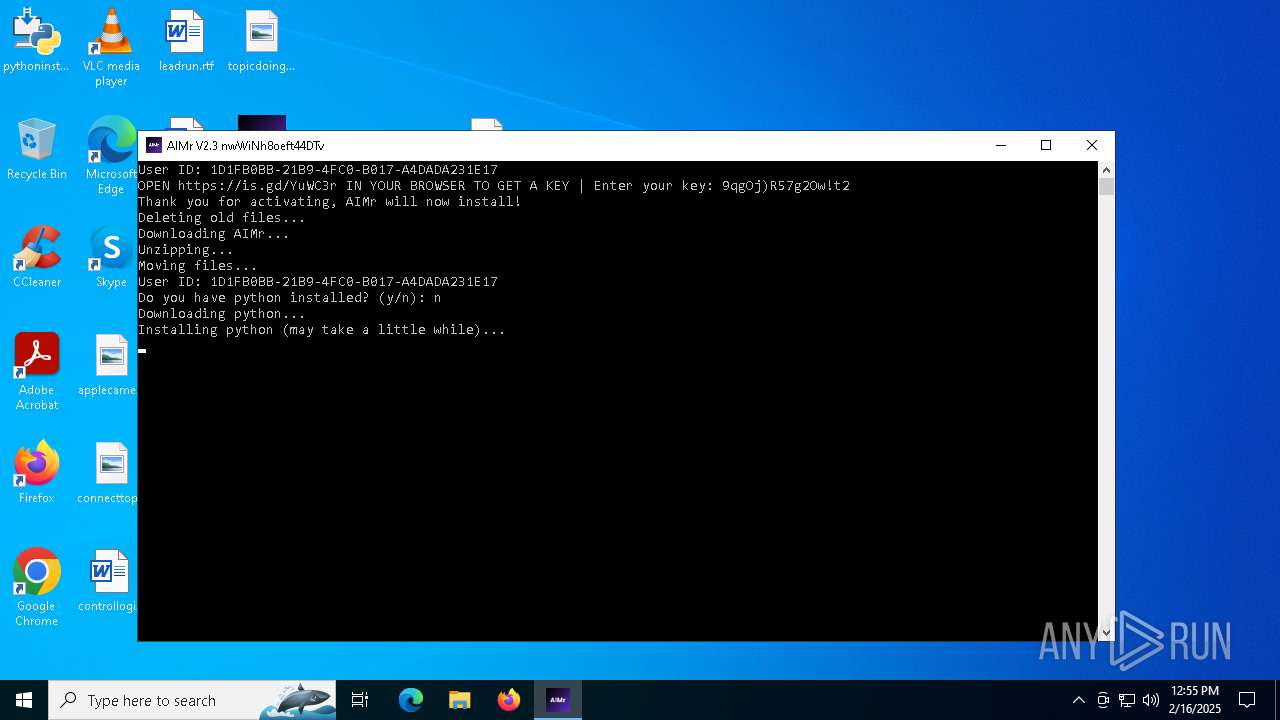
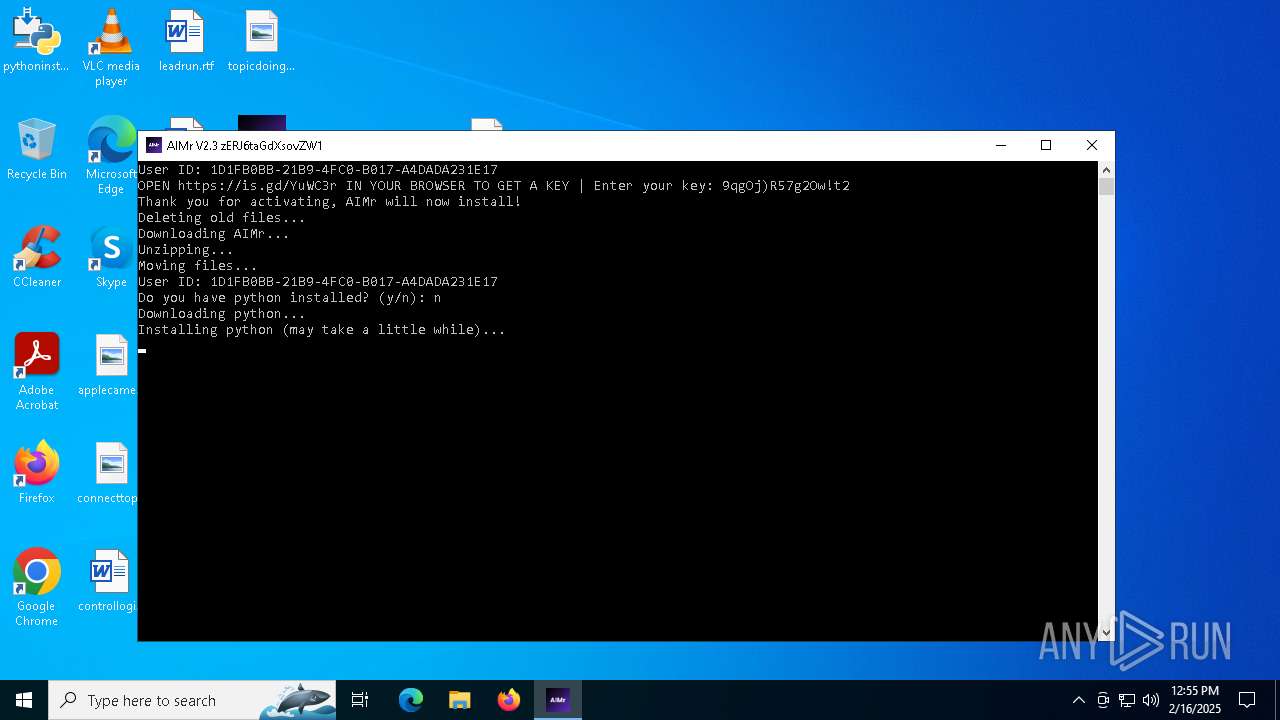
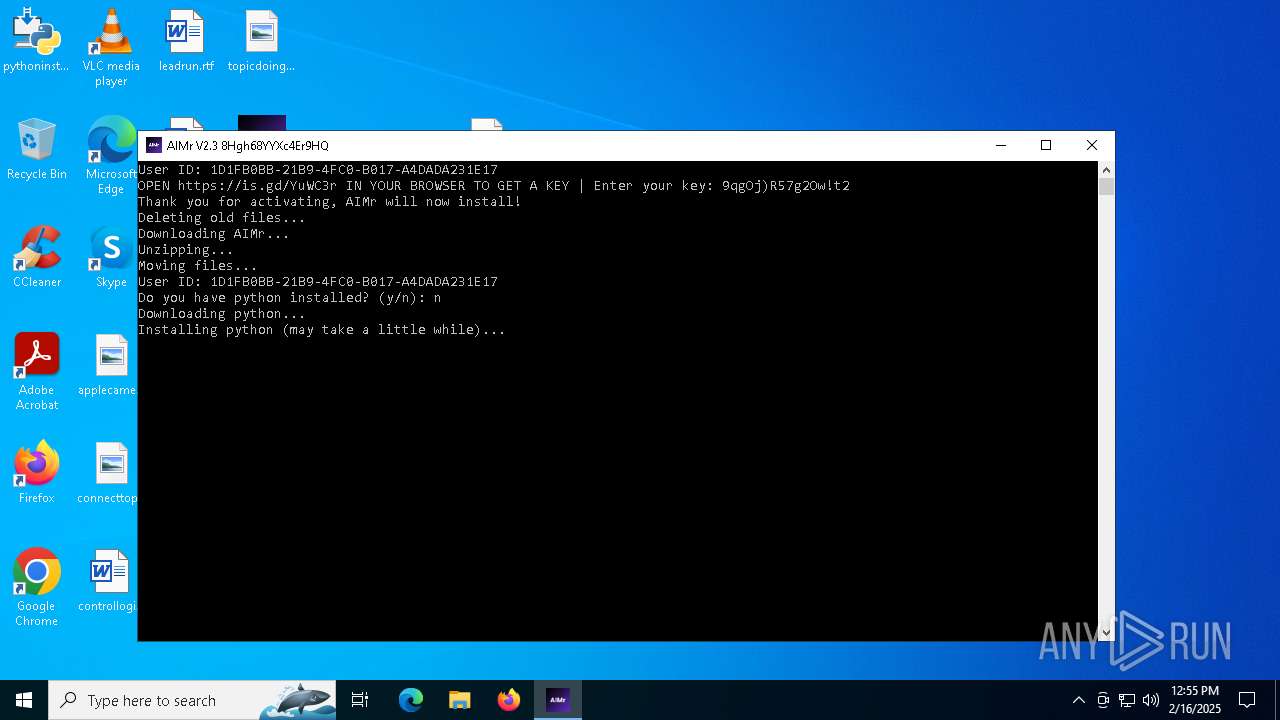
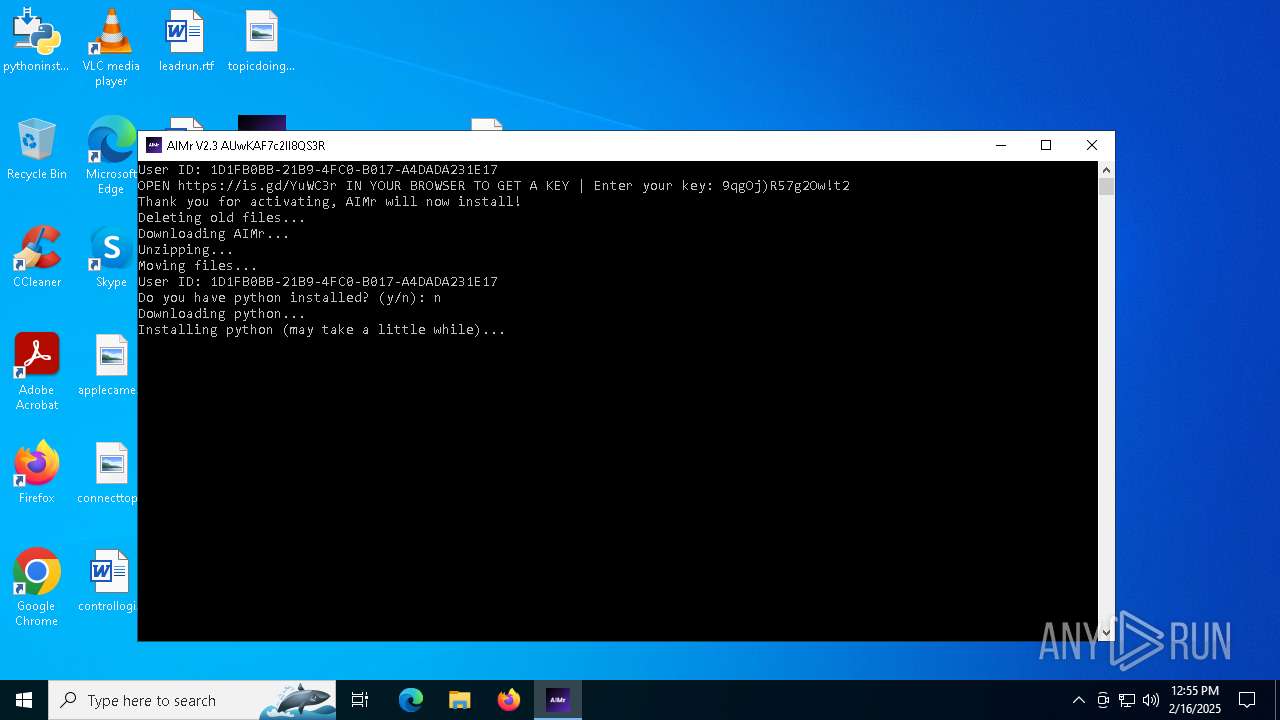
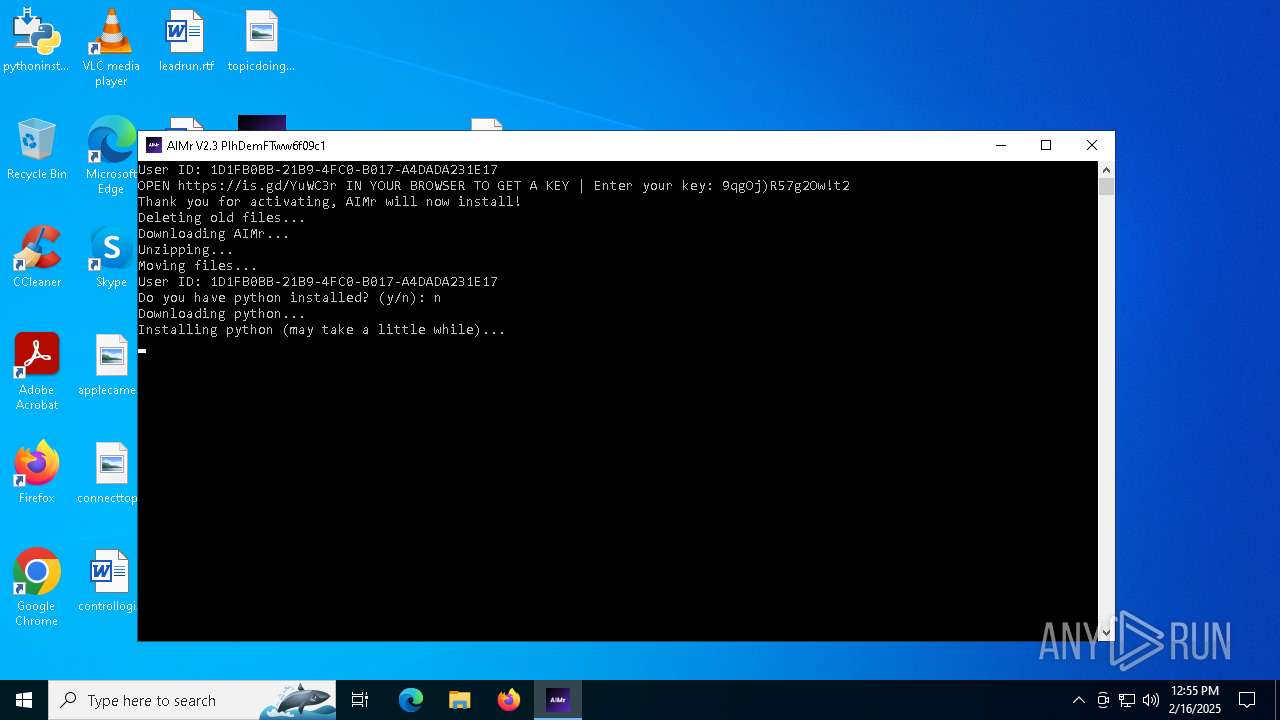
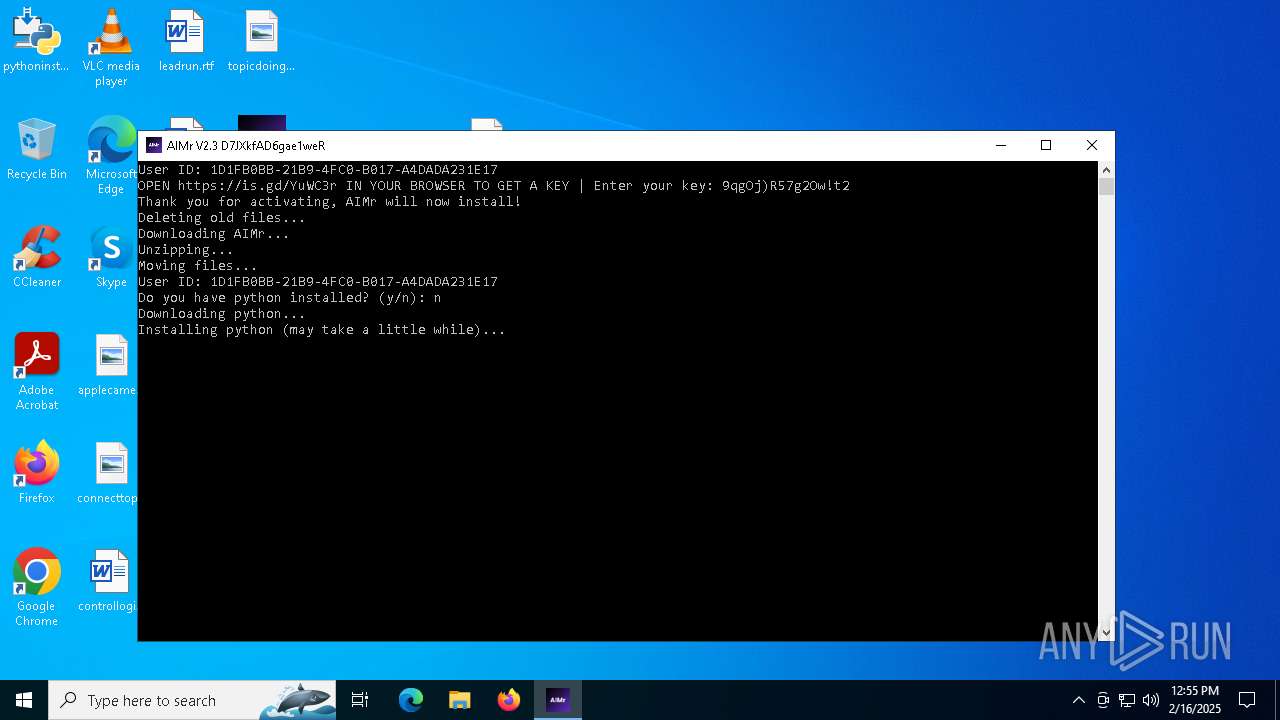
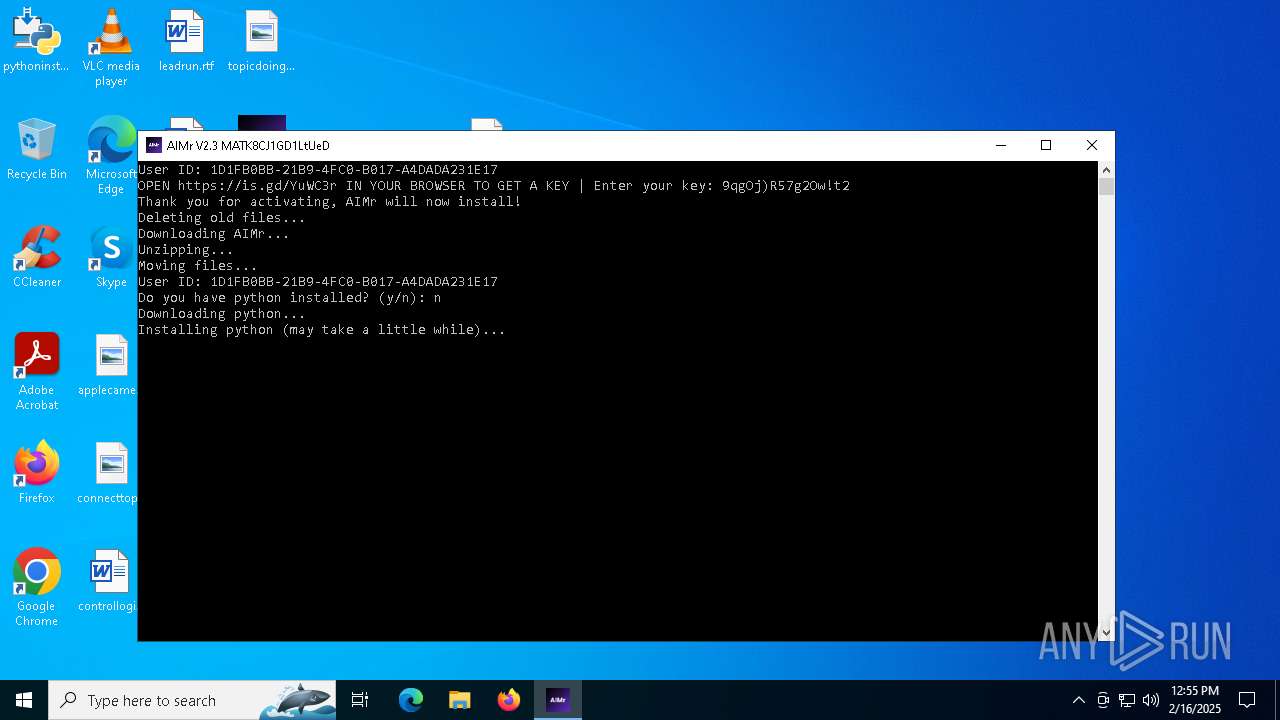
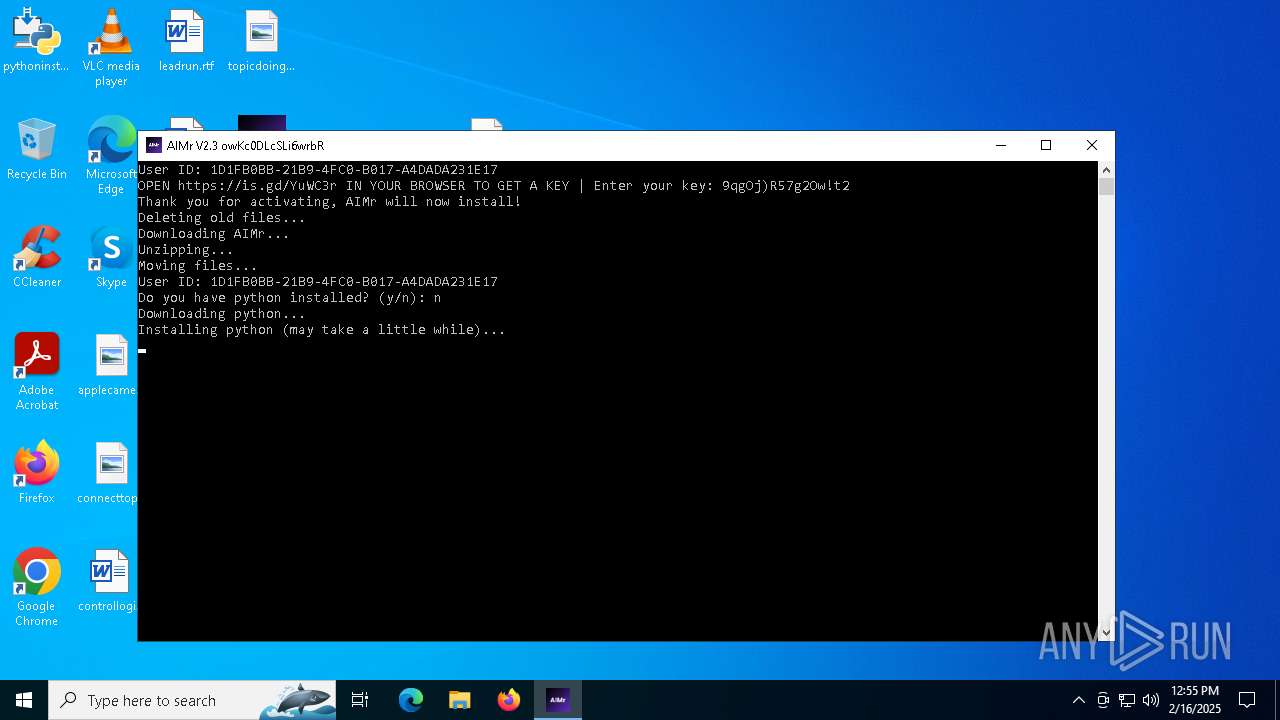
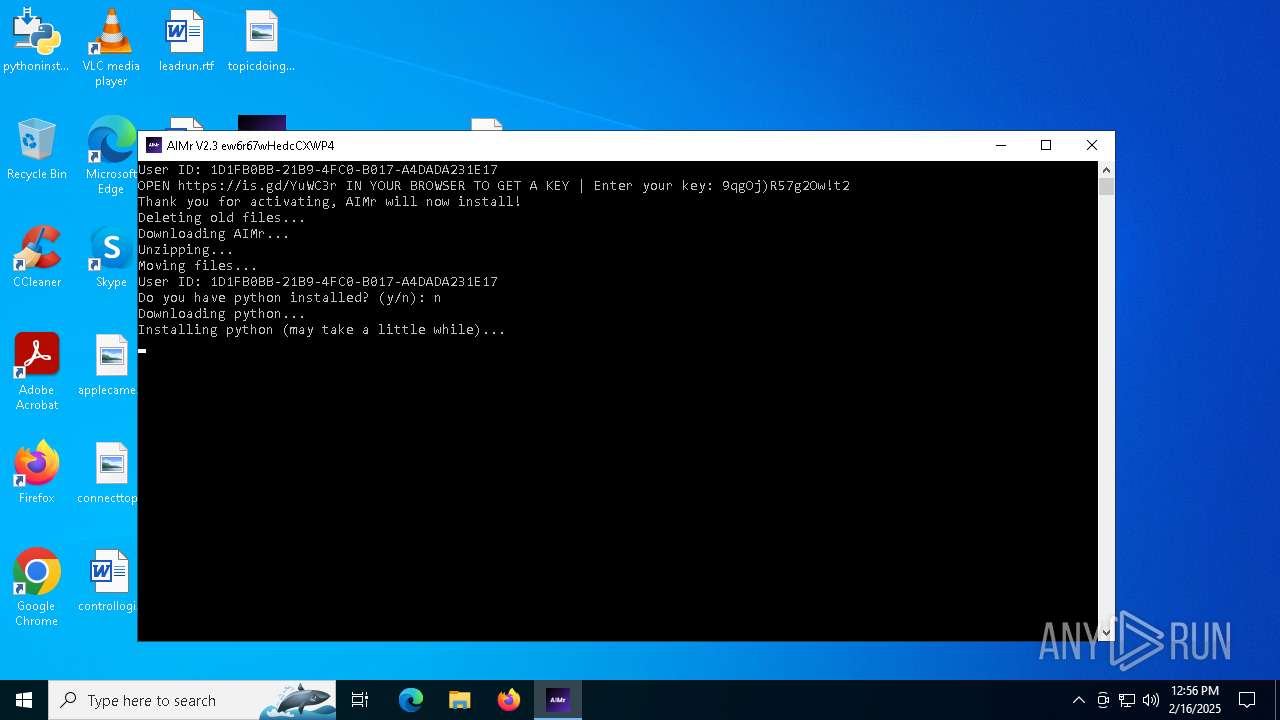
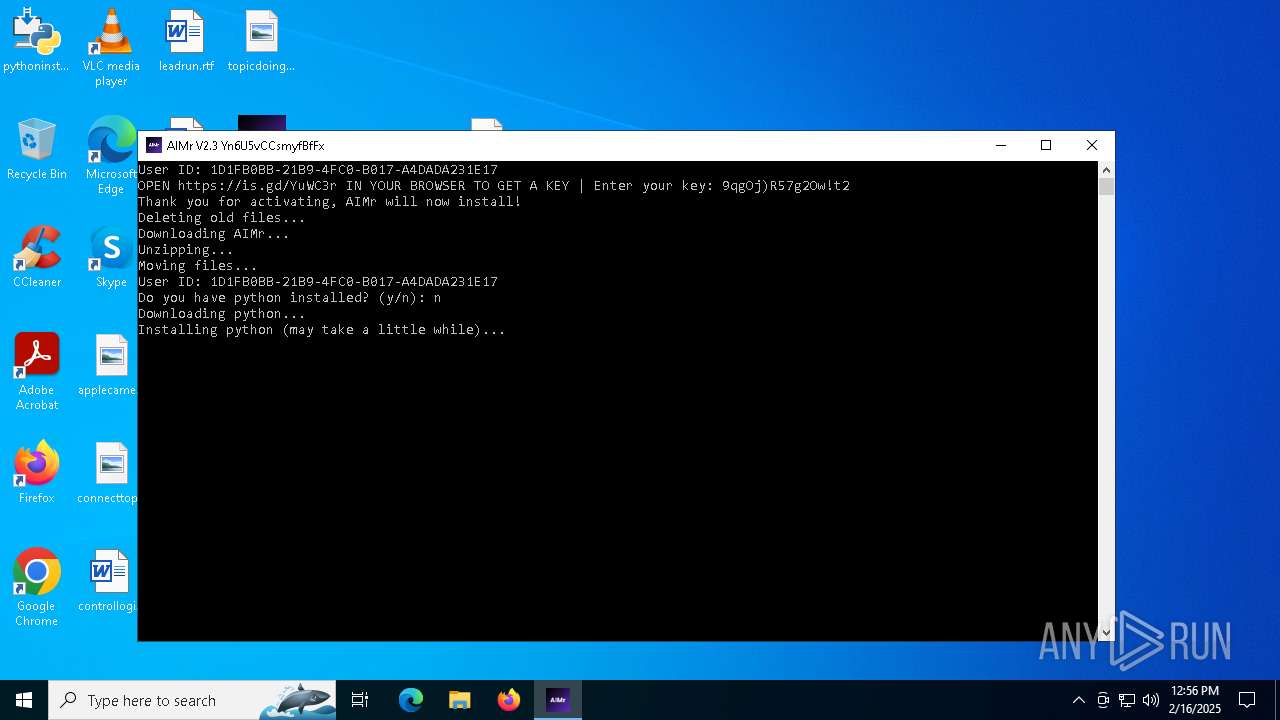
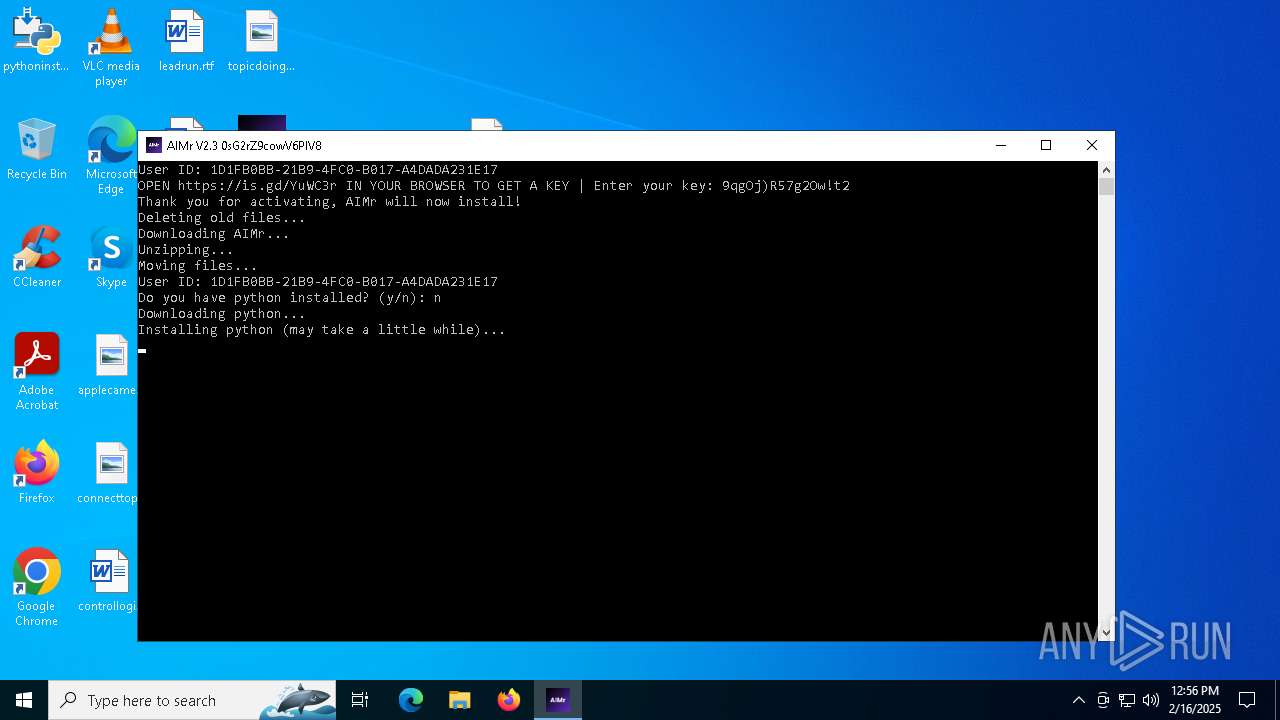
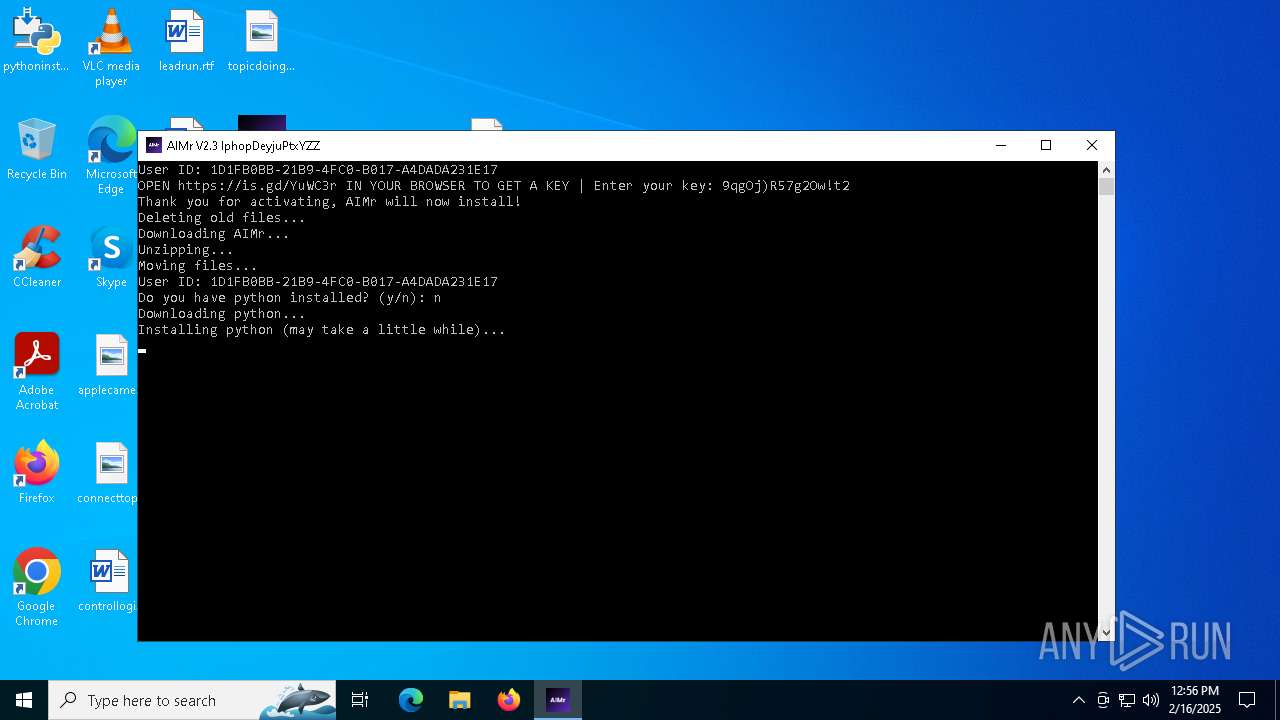
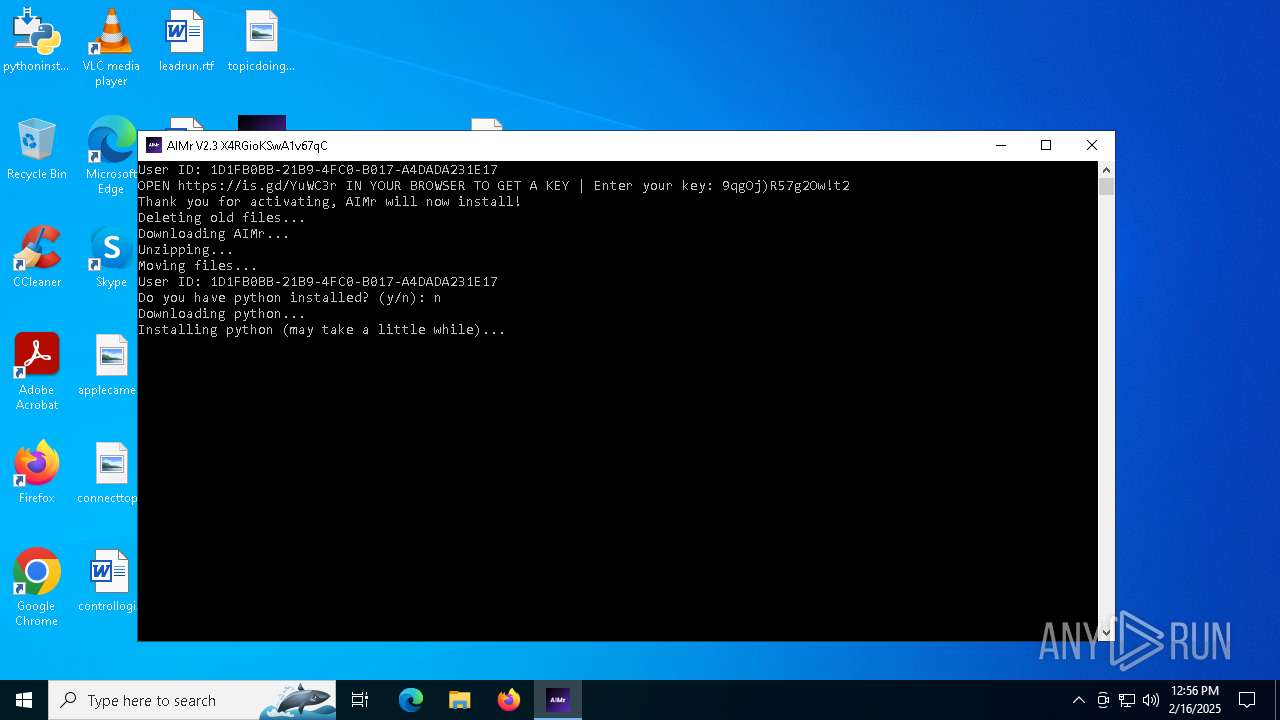
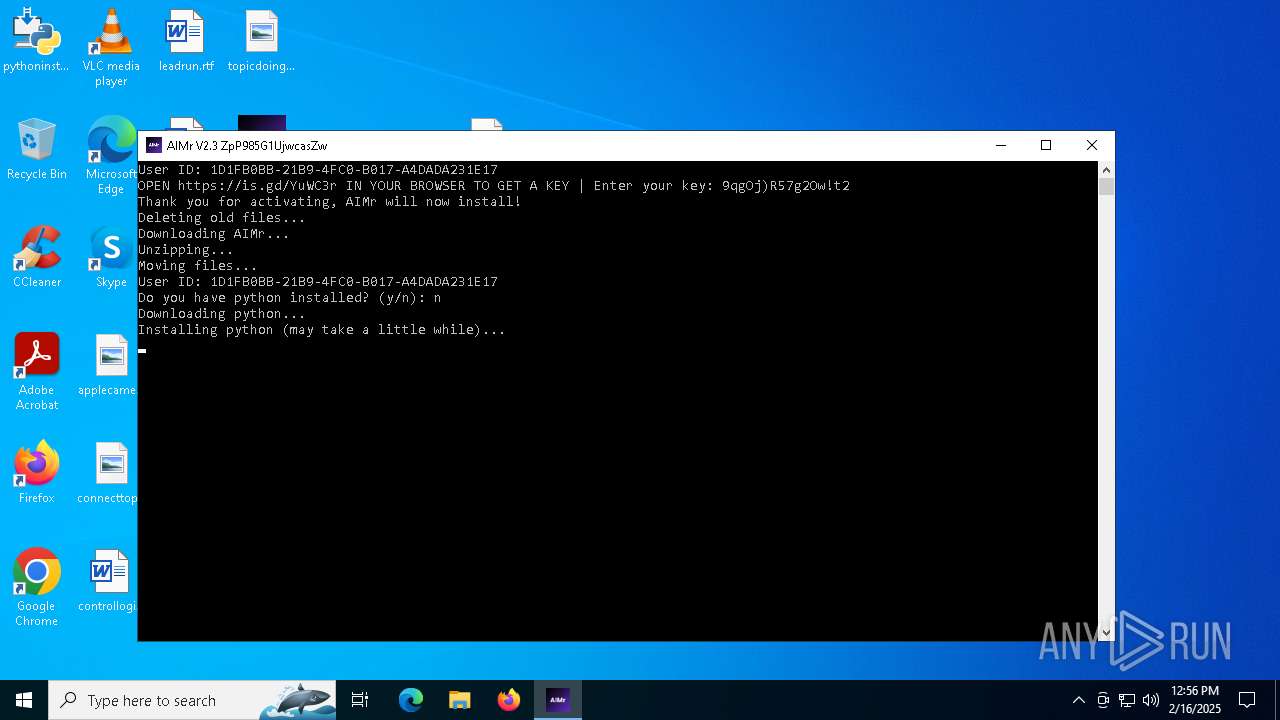
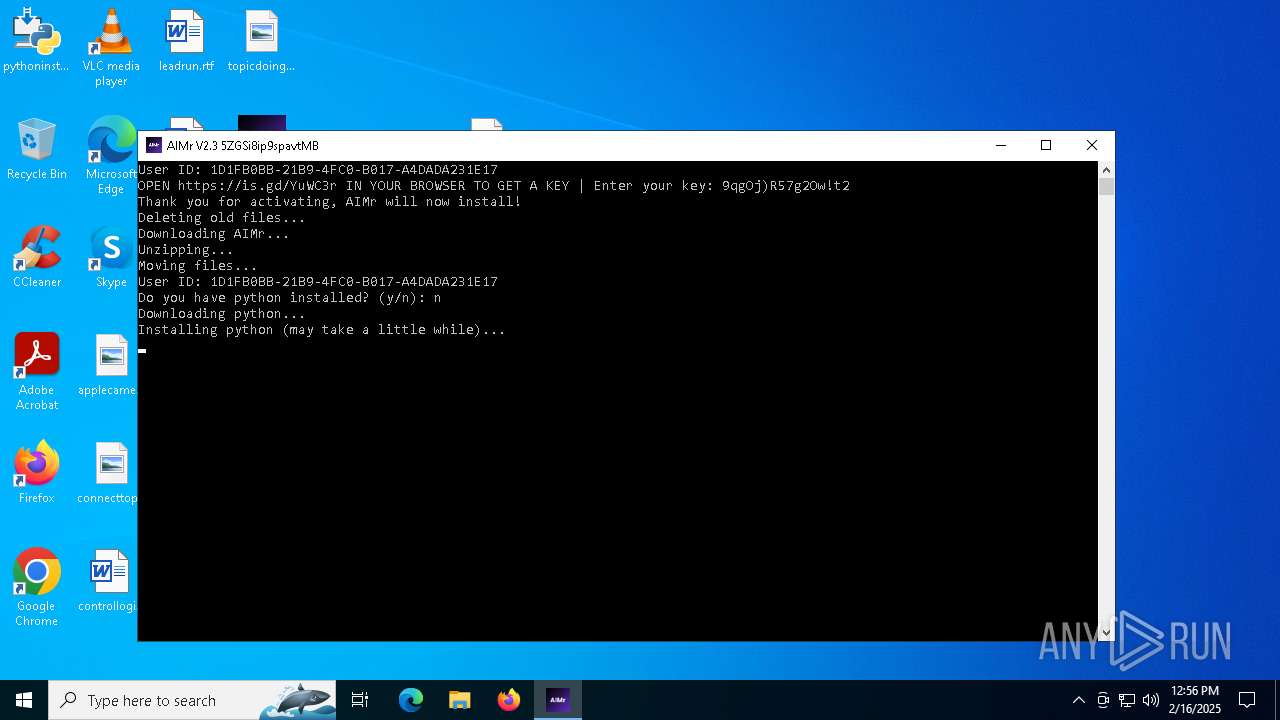
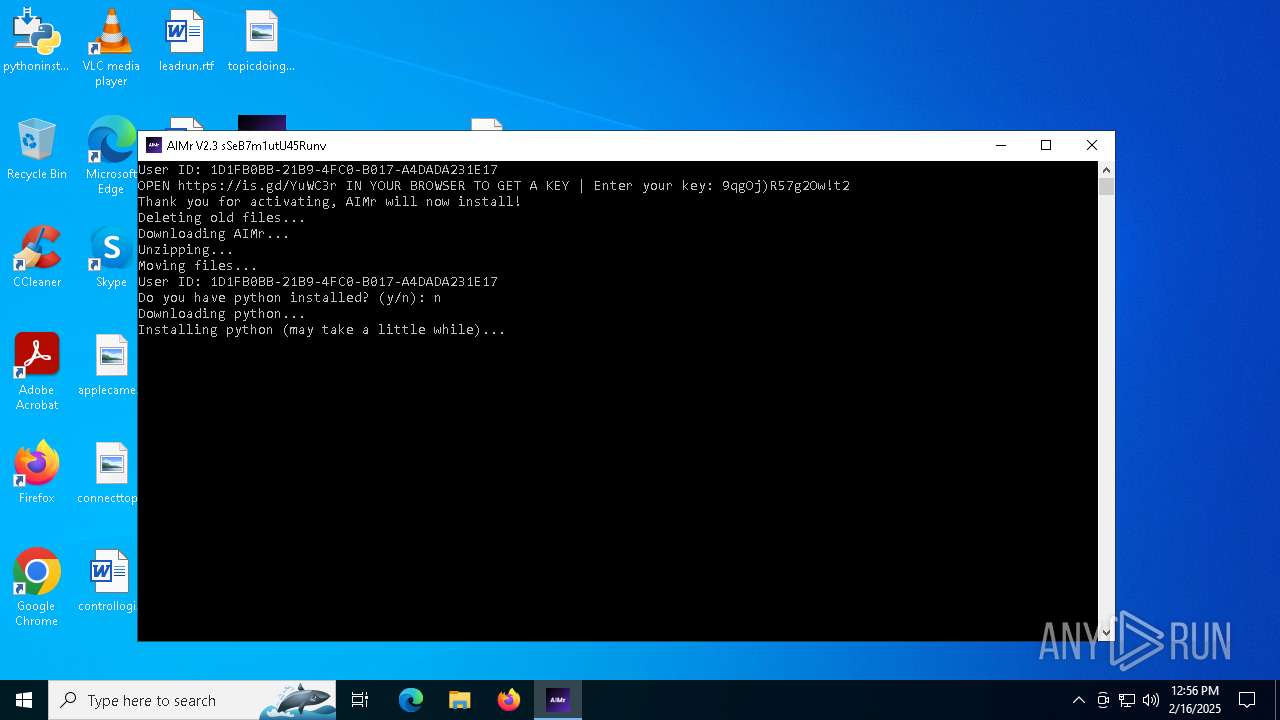
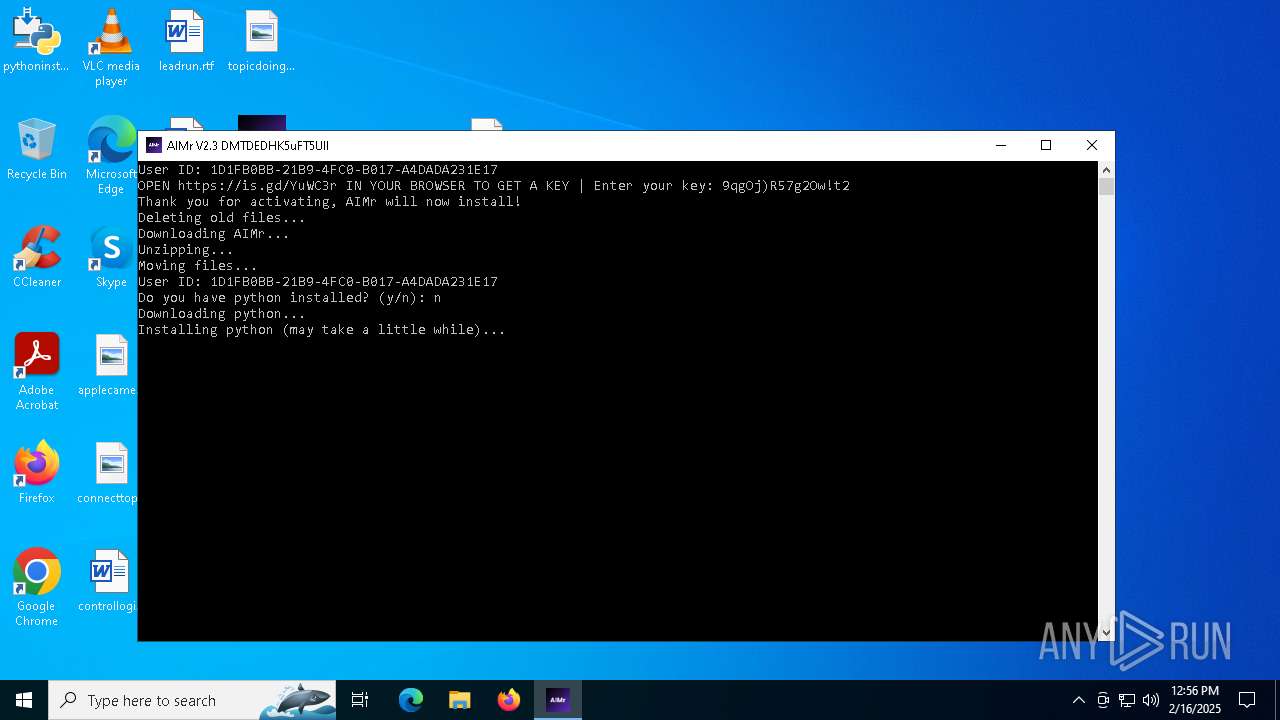
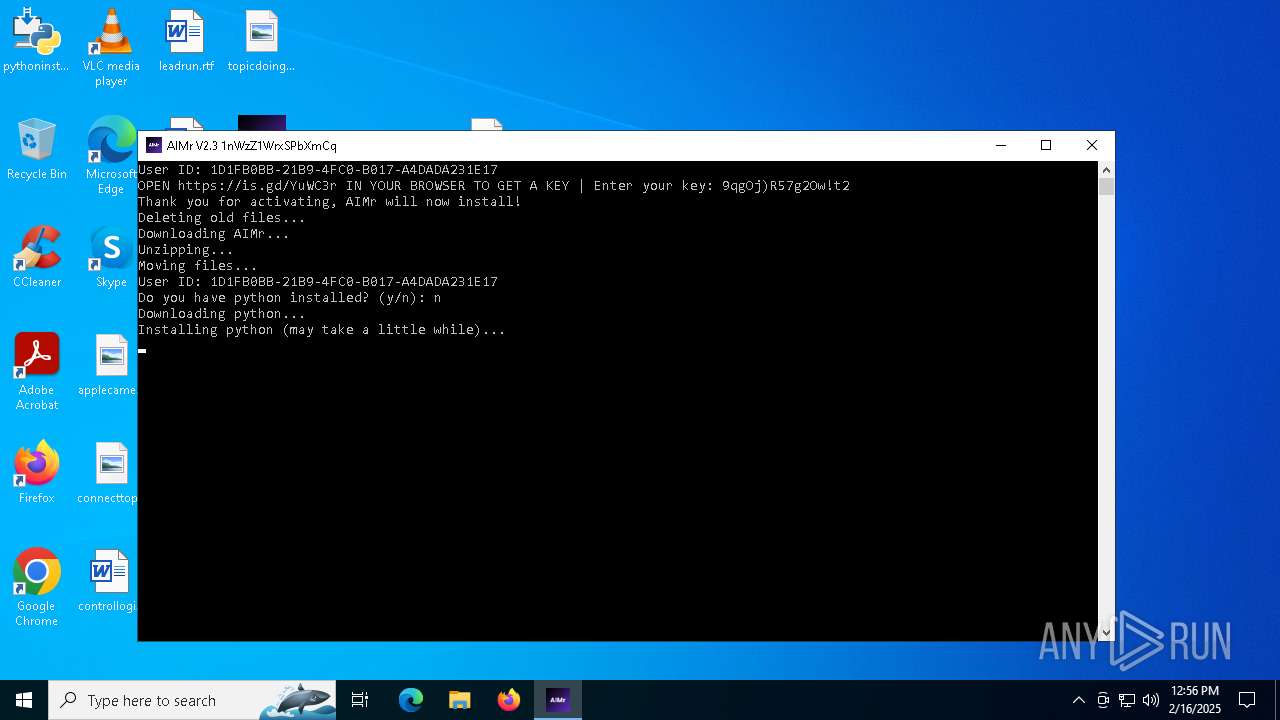
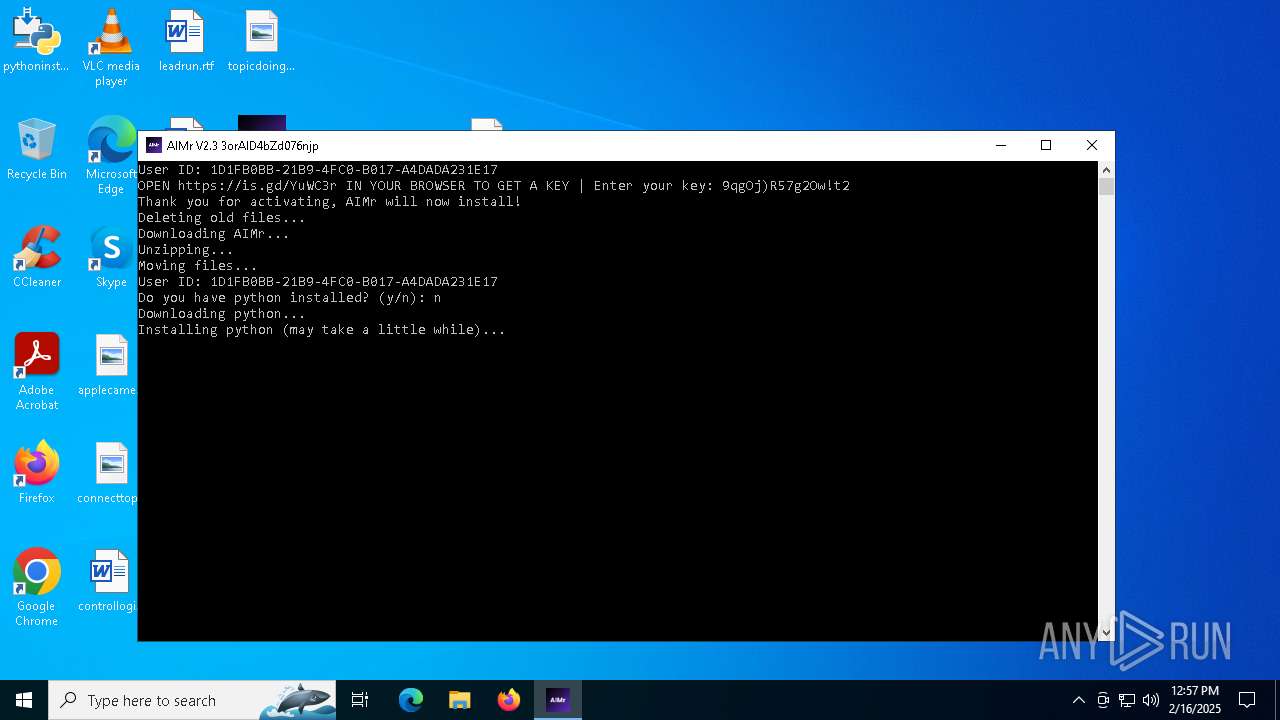
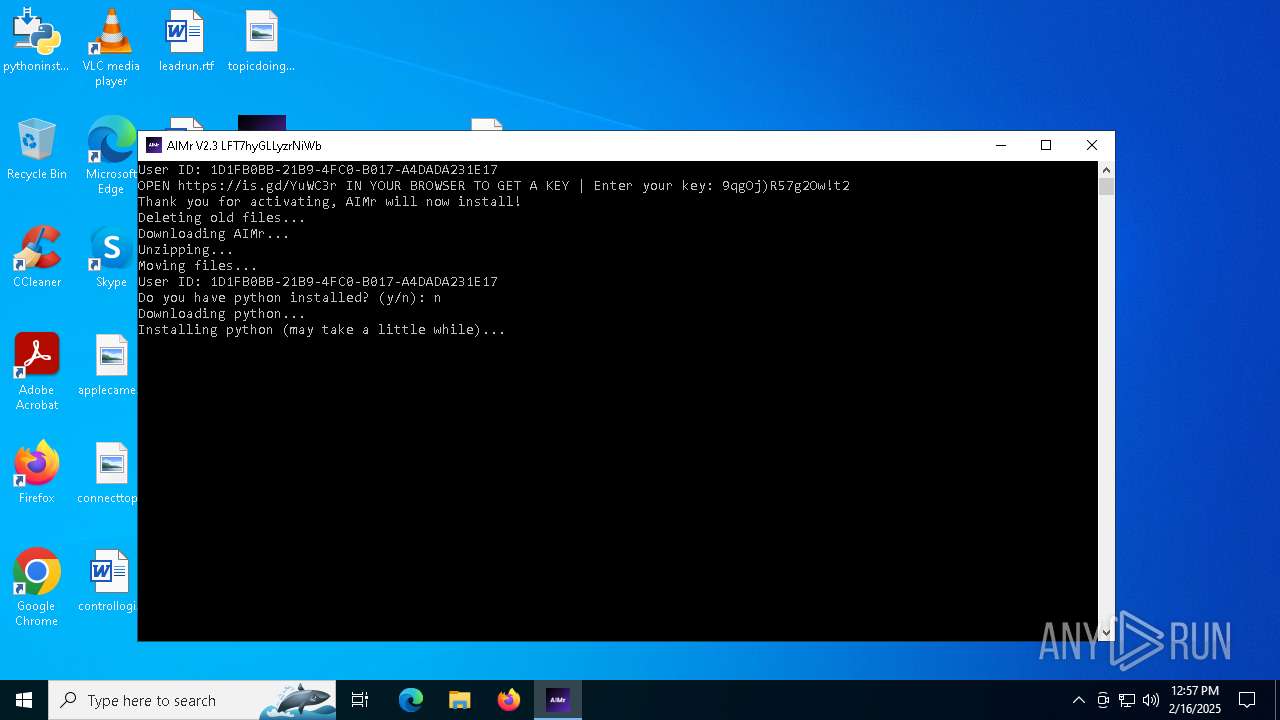
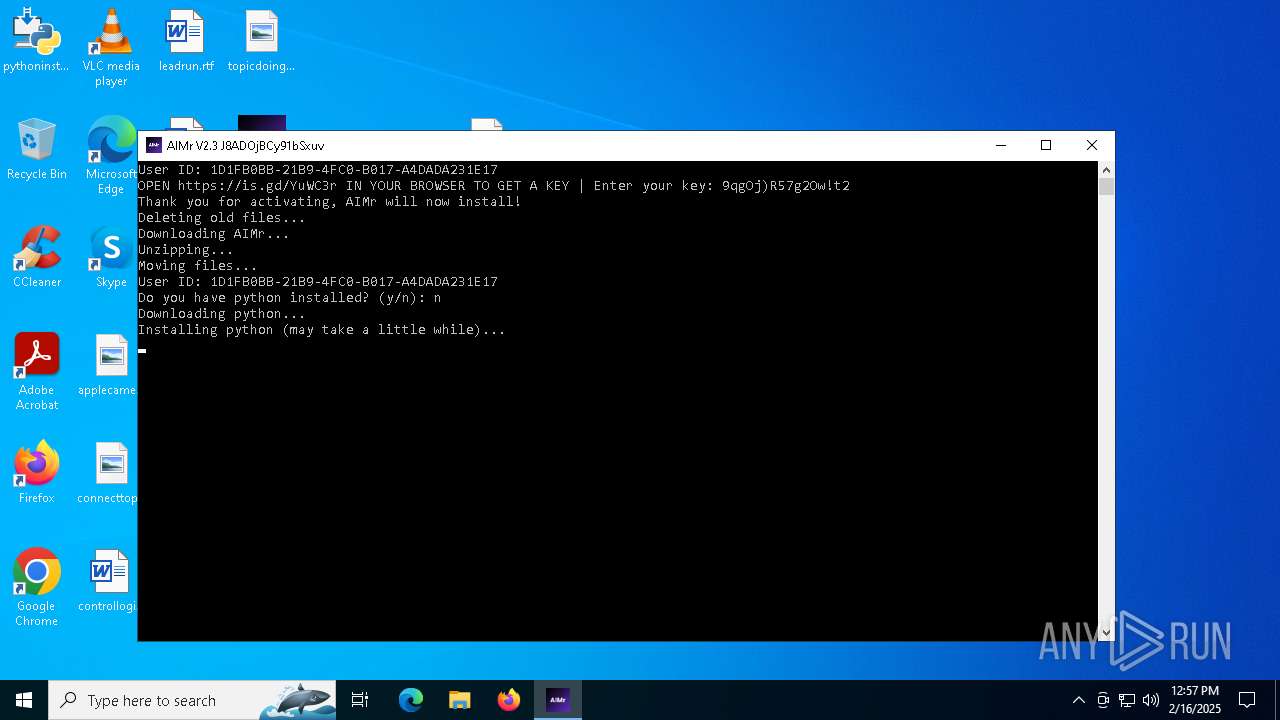
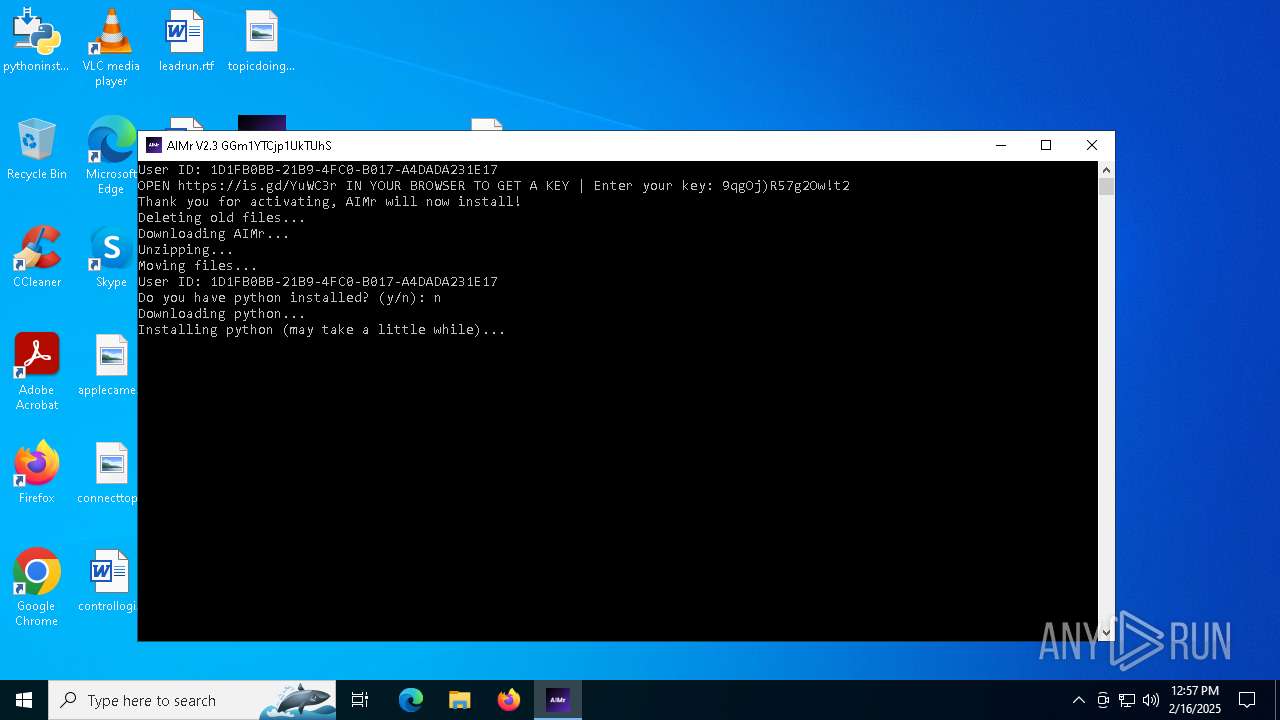
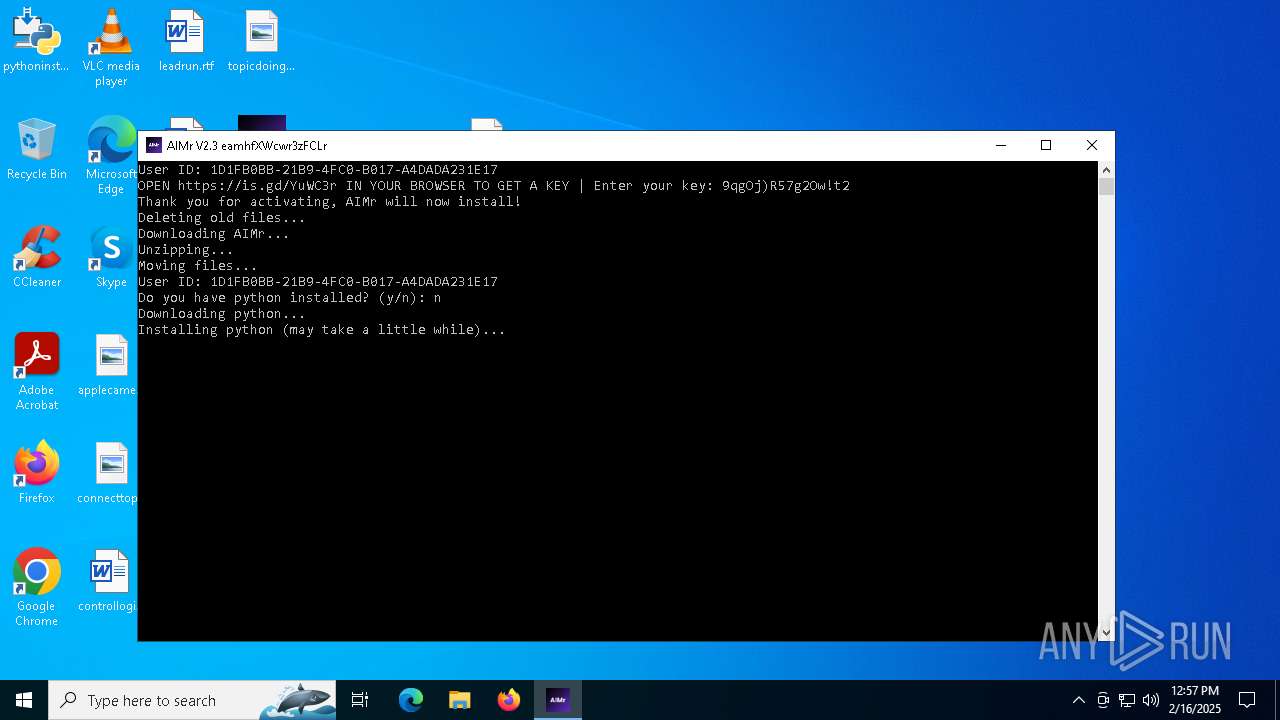
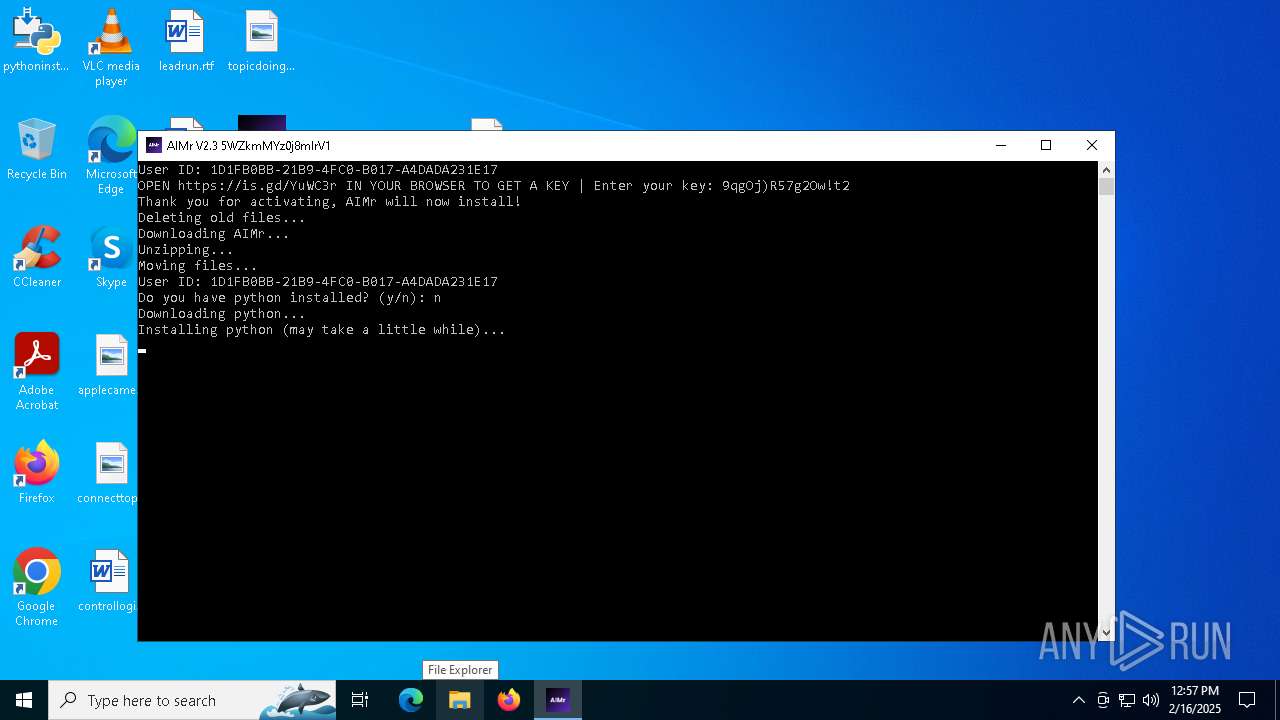
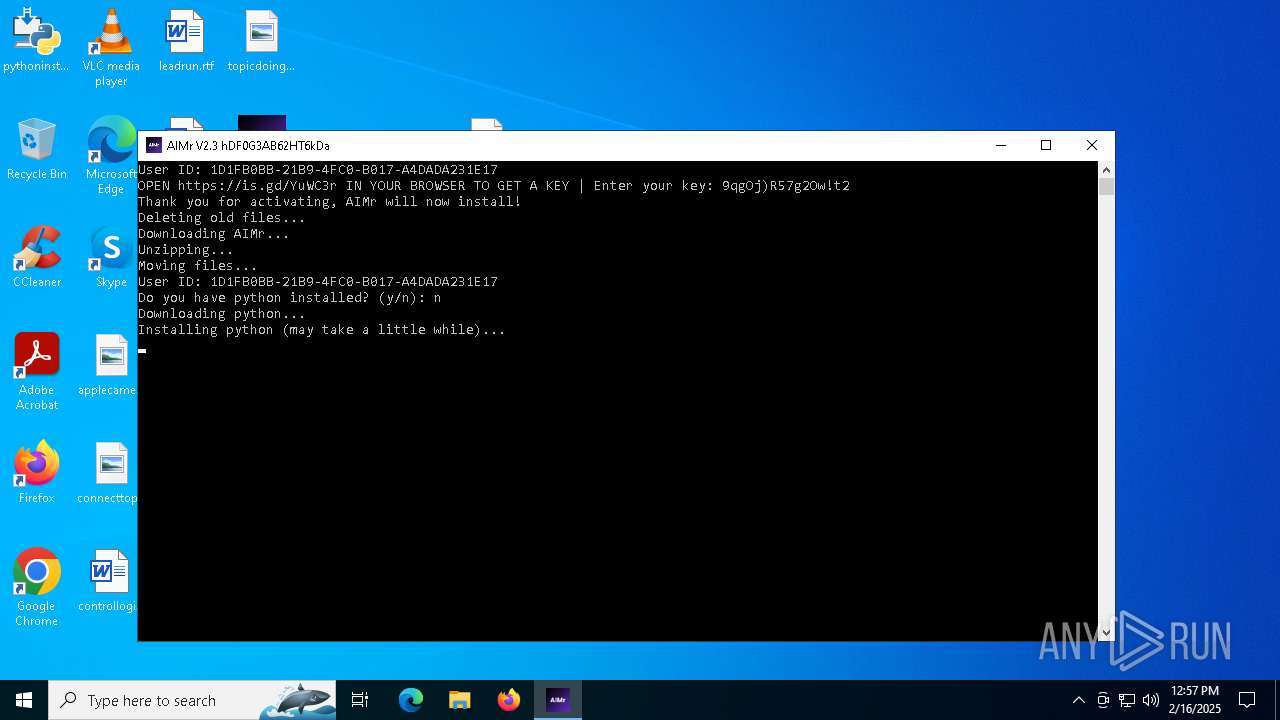
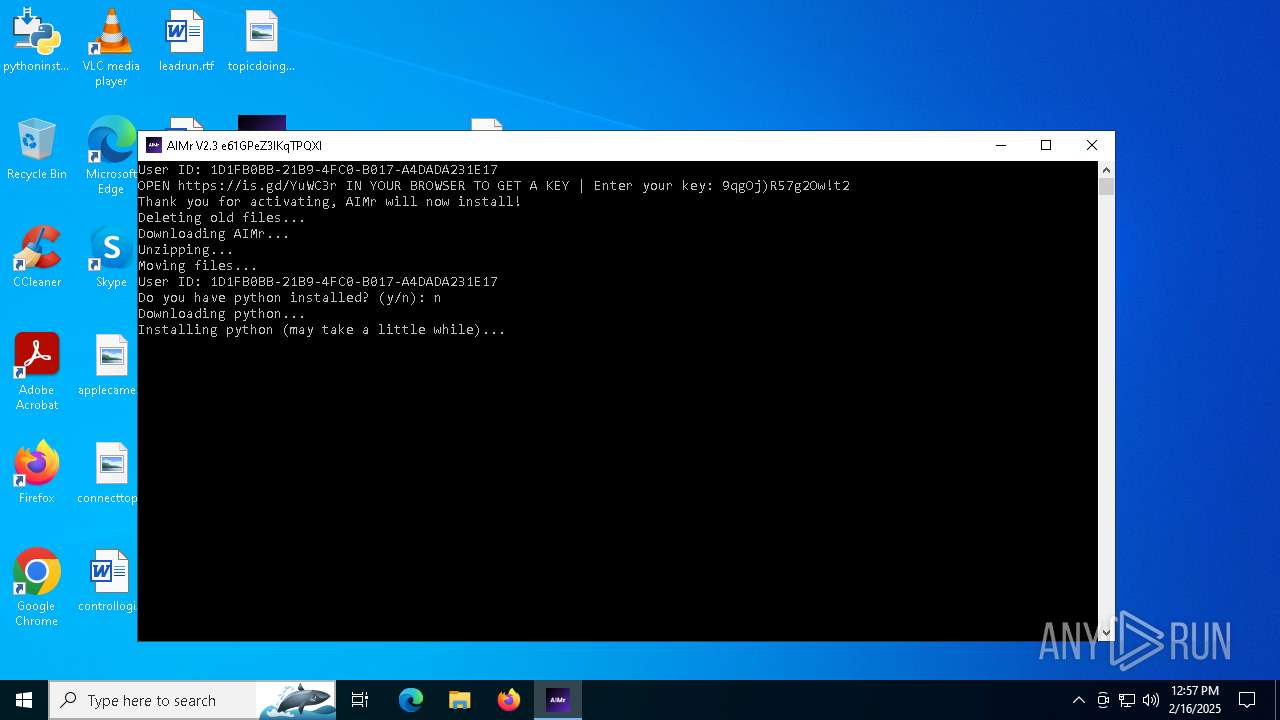
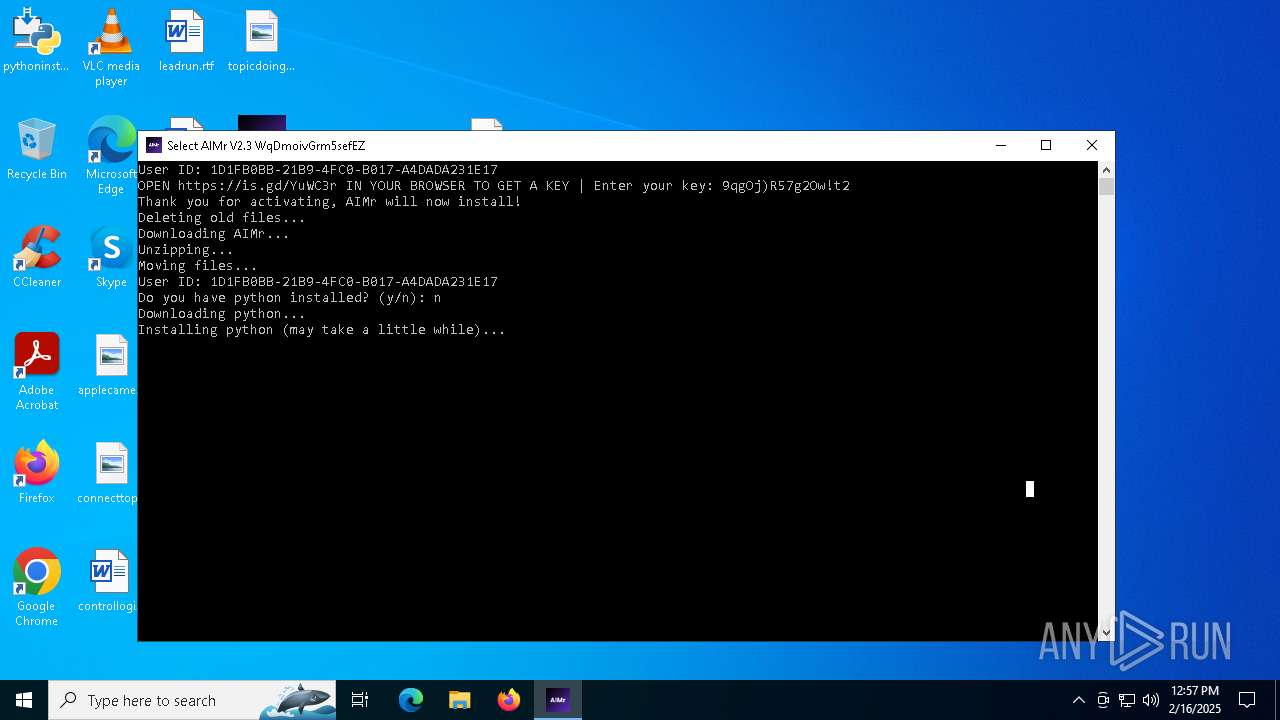
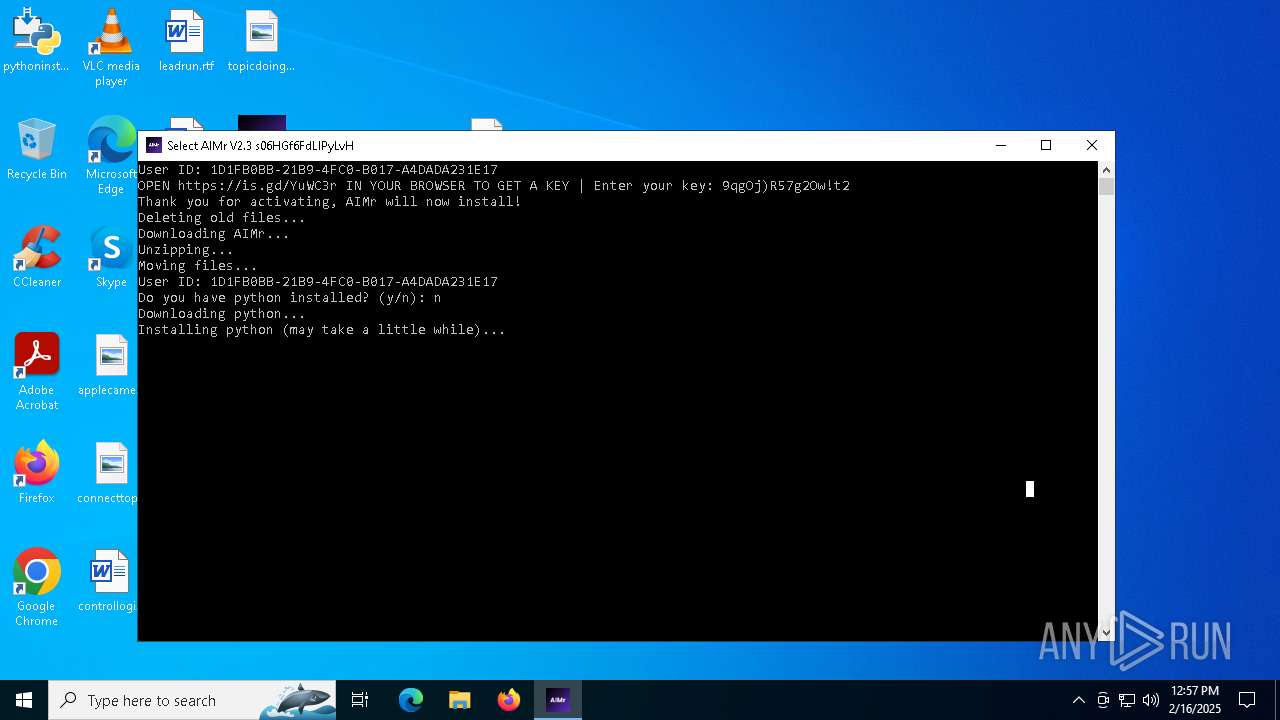
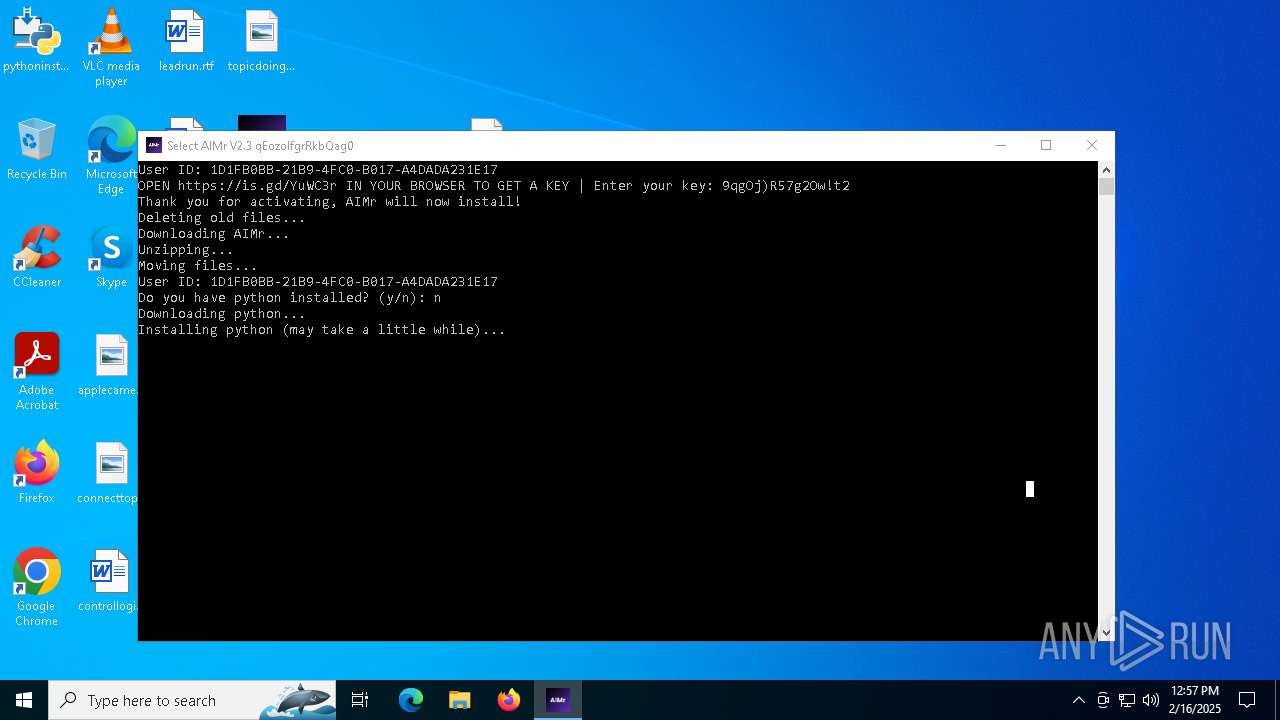
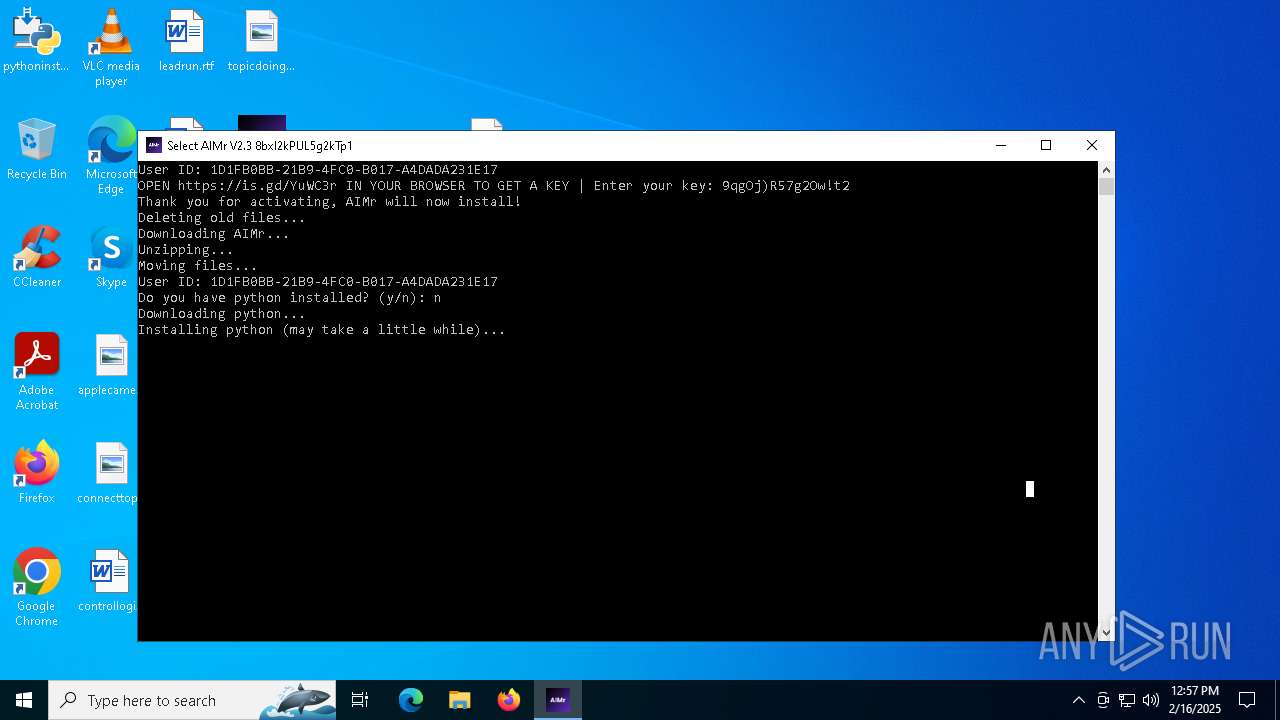
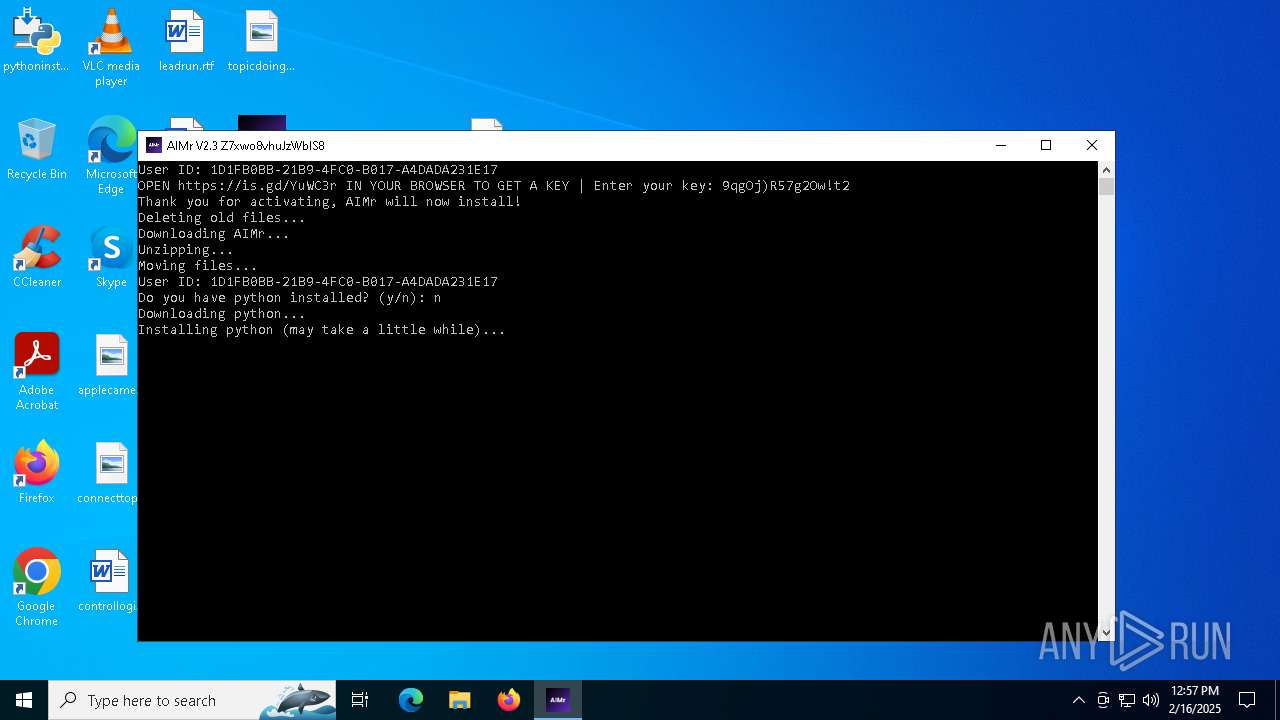
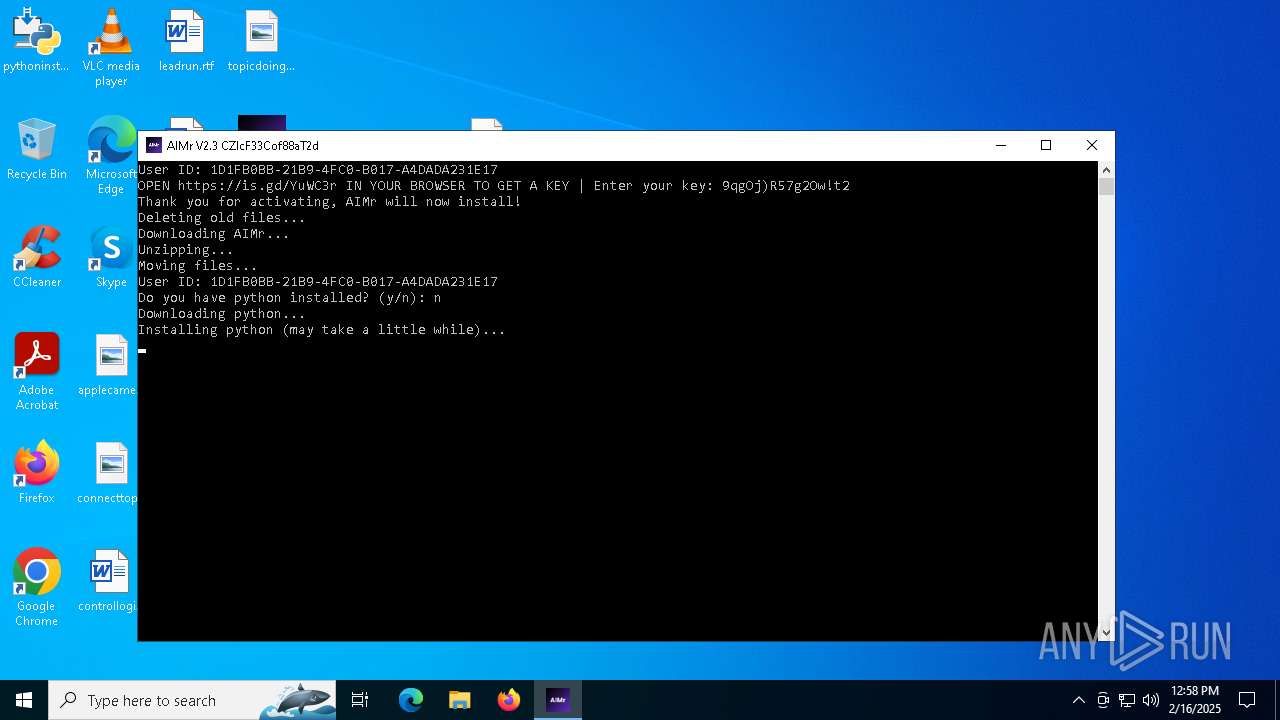
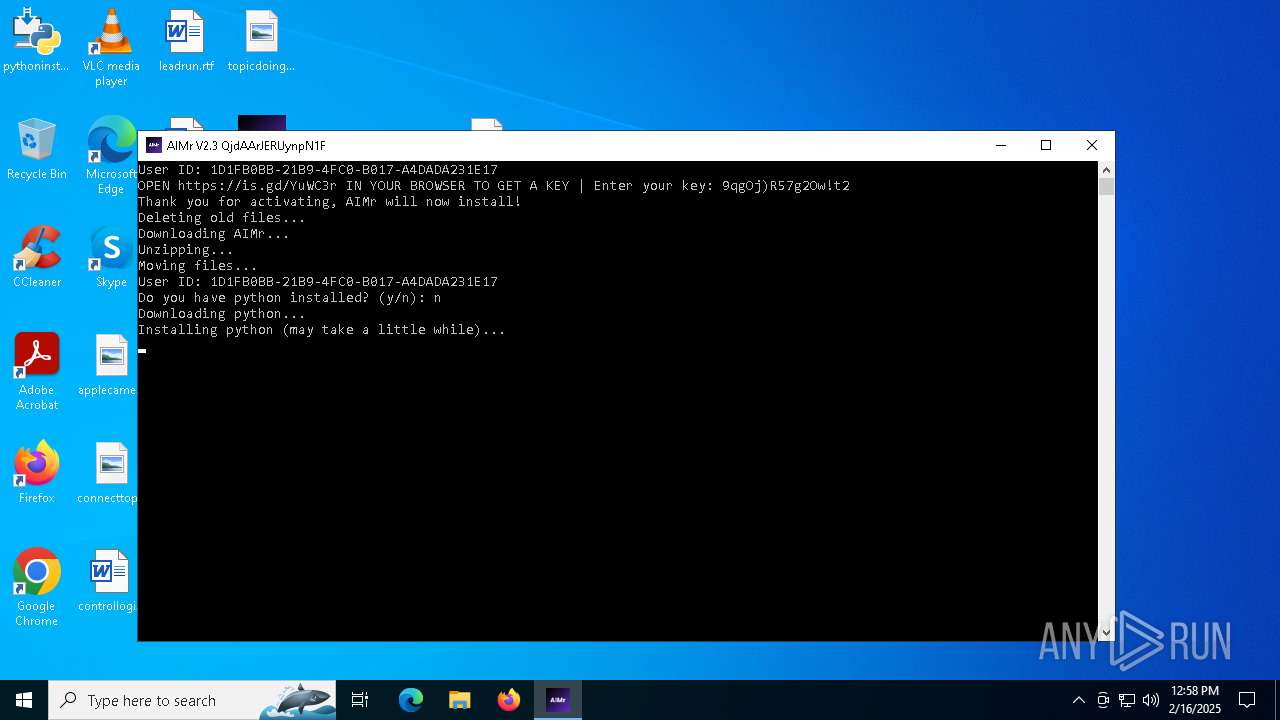
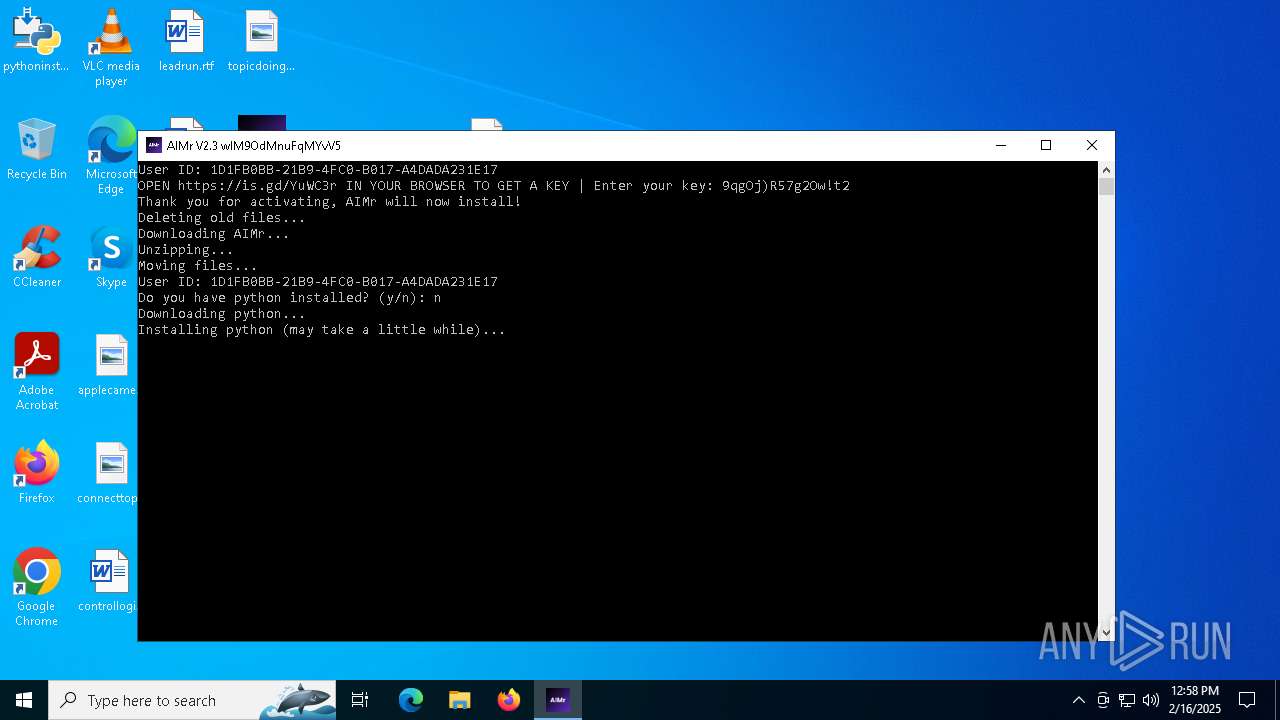
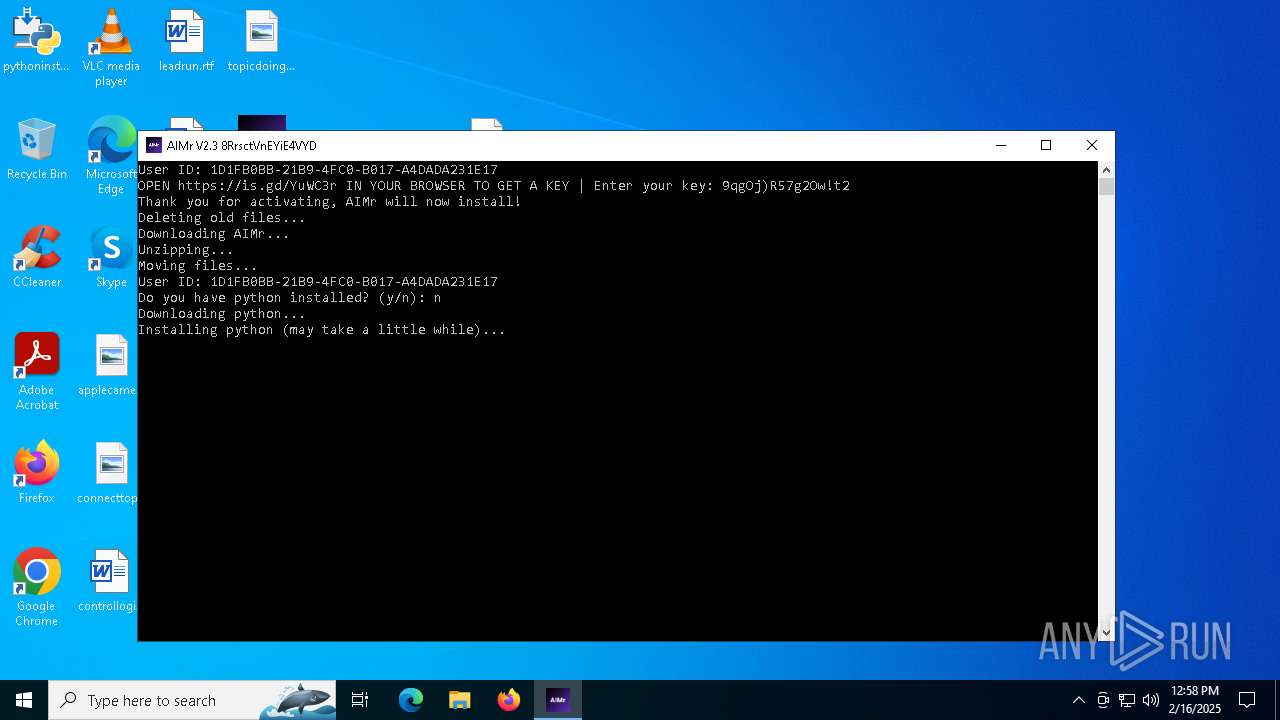
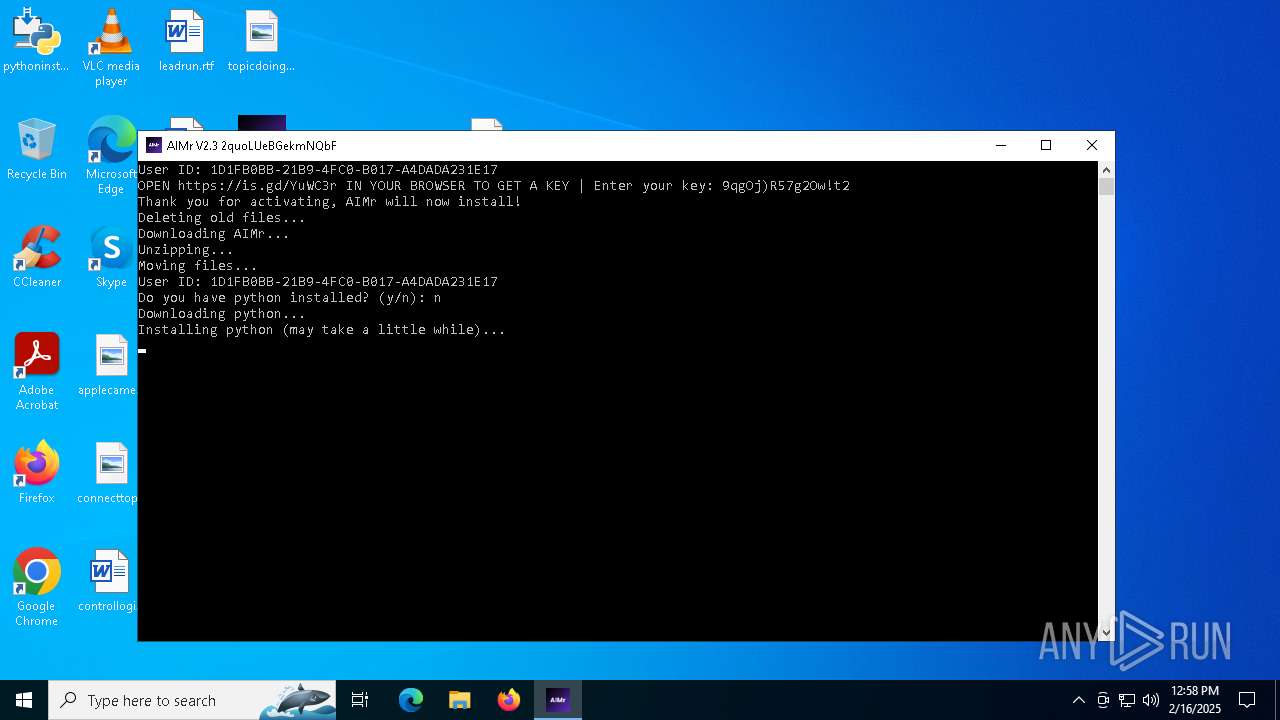
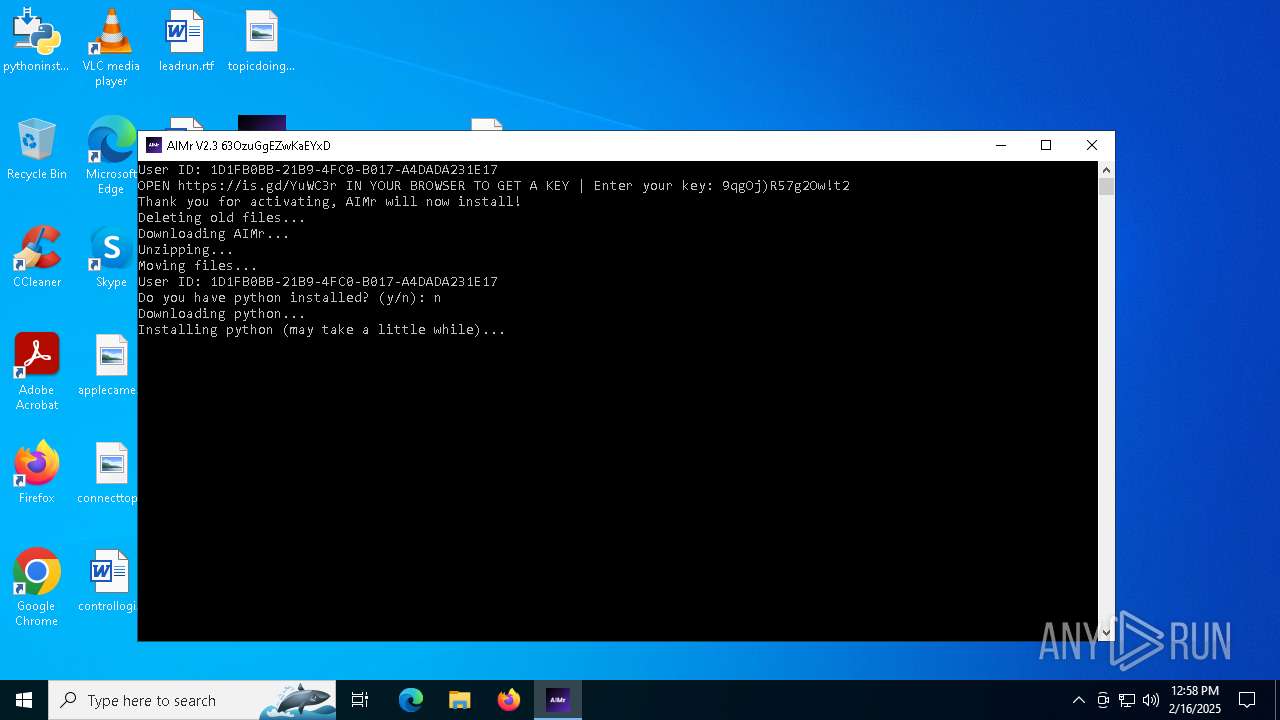
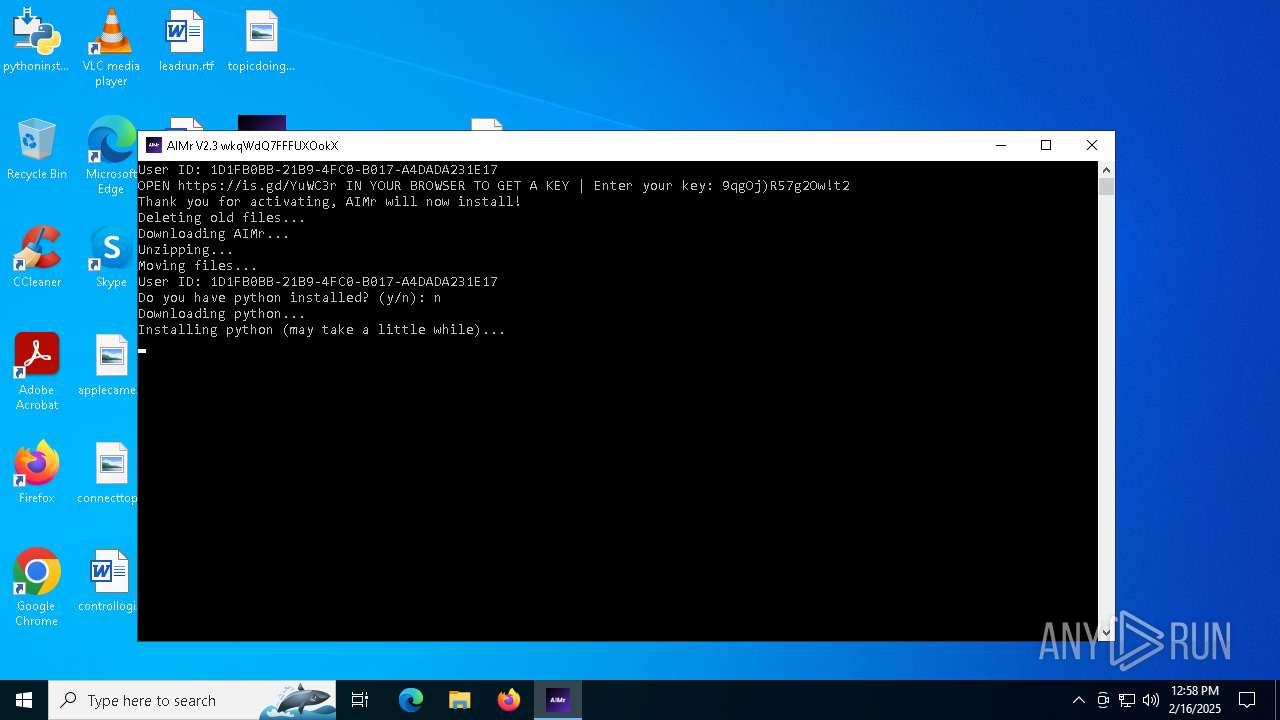
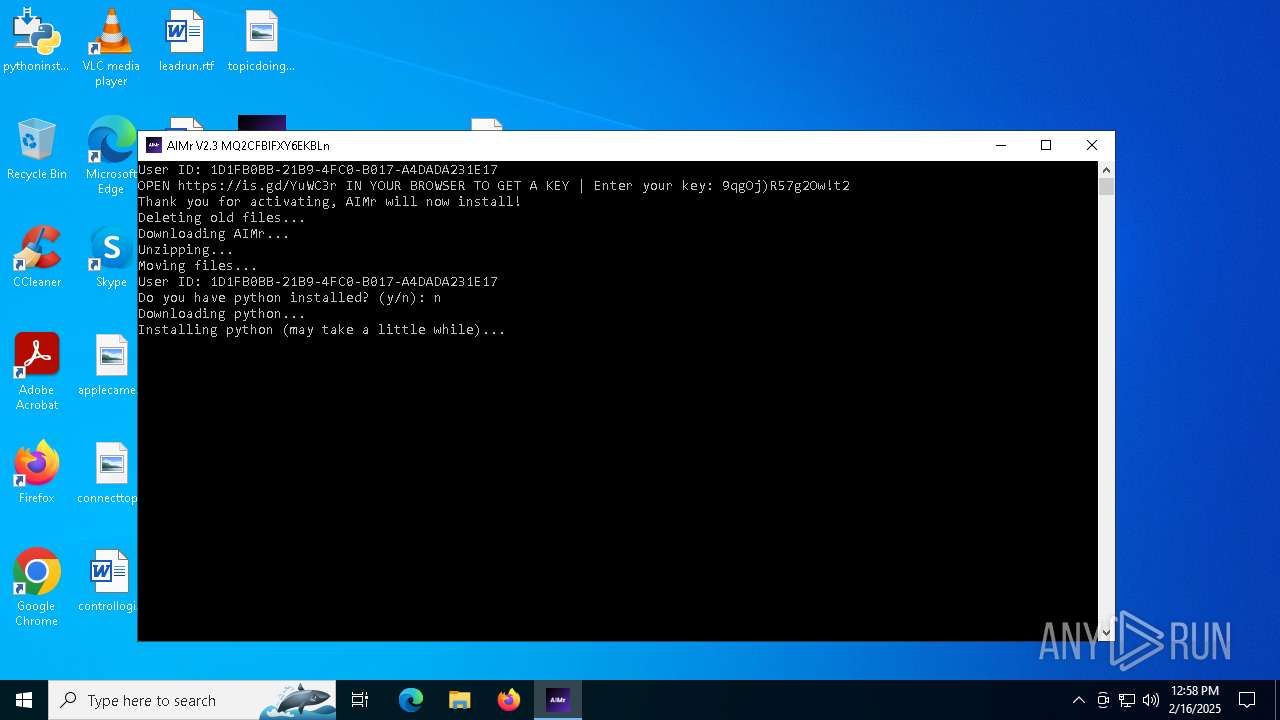
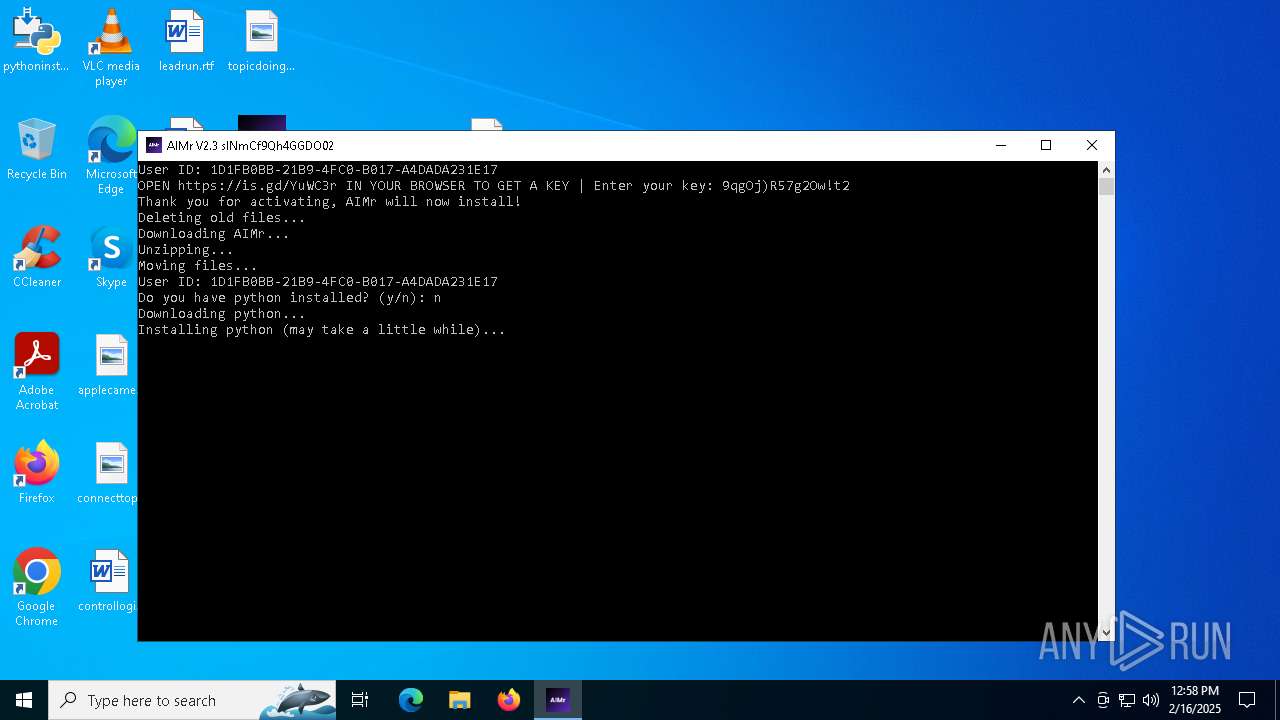
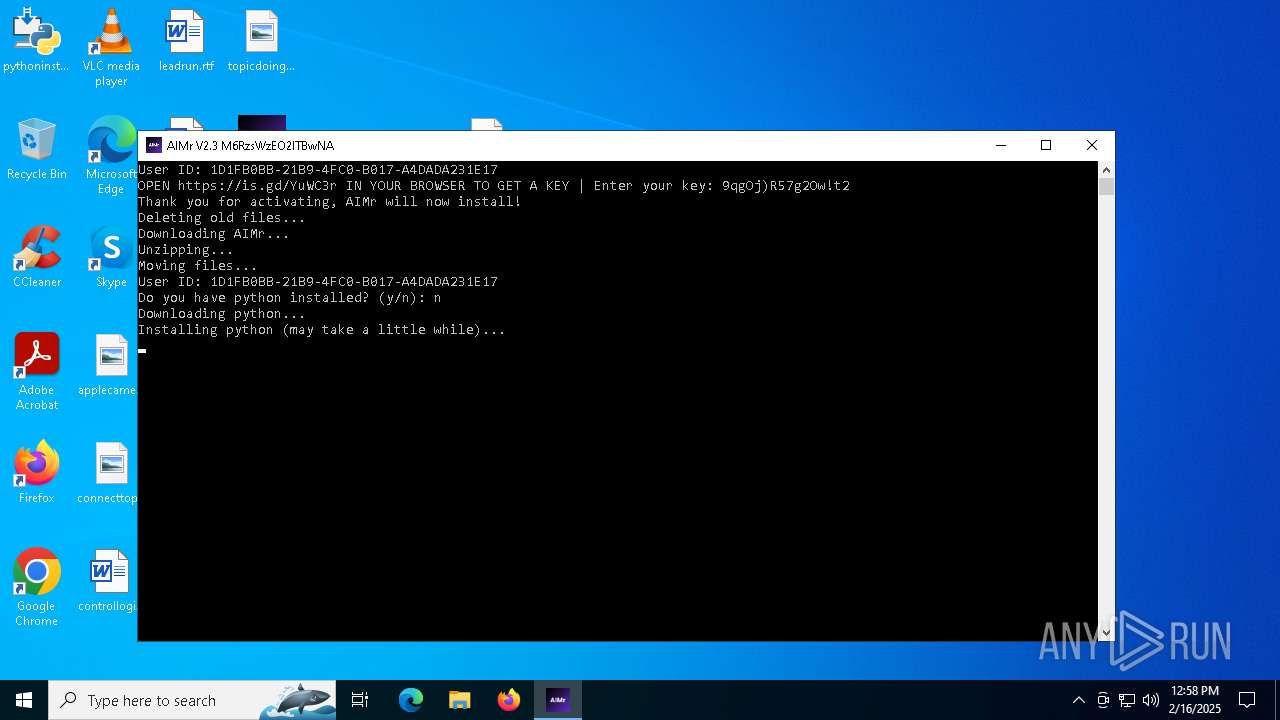
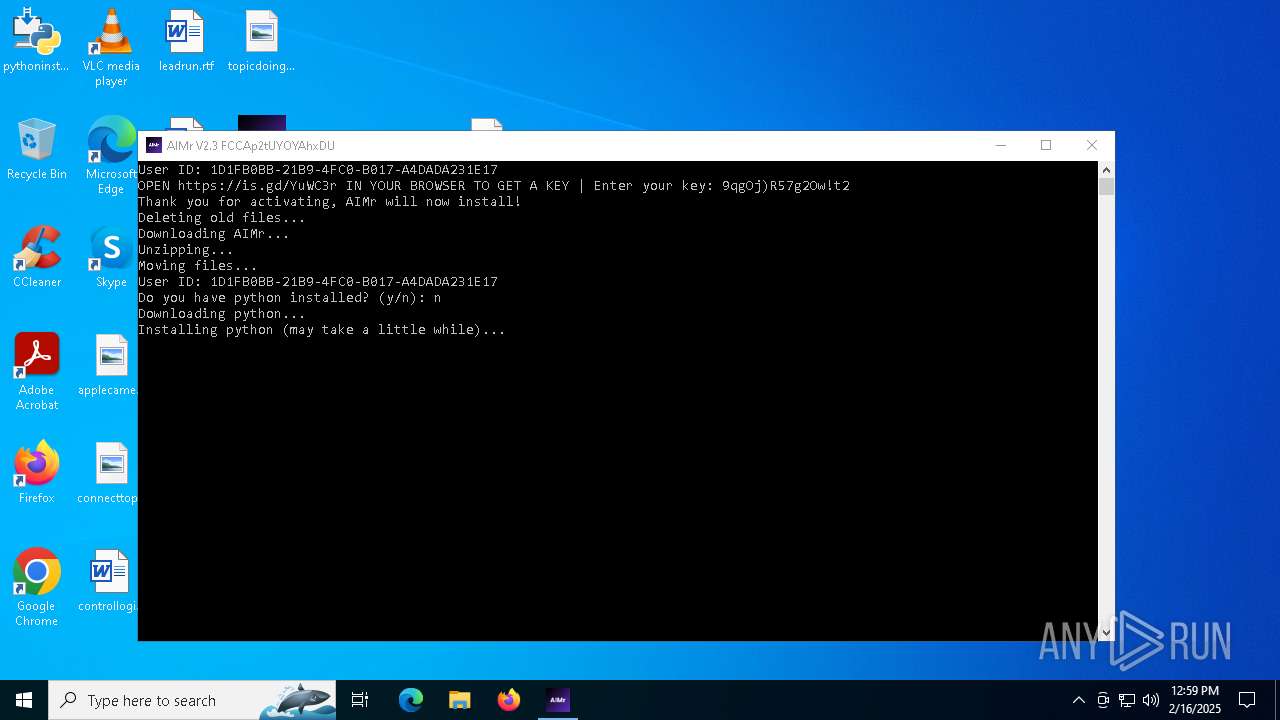
| File name: | AIMr.exe |
| Full analysis: | https://app.any.run/tasks/69f8bd7b-d2a2-41bd-a78c-30ecd40293a4 |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2025, 12:54:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | ADCD61646DD9EE3238279FF36DC0E88E |
| SHA1: | 8C679E249394AF001E72225DD866A9F6C0AB3BDA |
| SHA256: | 481865D699E7B4DC3C160E33181F4D2A82067D2D03DD661E0C8FBE047E9F283C |
| SSDEEP: | 98304:rUkBOrFRDIAGzlFOu19sjjn0BjmWxYeAM1EIfspEW1EEE/j1VD+21FNsdYE5JpDD:FPxqkRjuZfdXRWKAXeJ |
MALICIOUS
Changes the autorun value in the registry
- pythoninstaller.exe (PID: 7164)
SUSPICIOUS
Process drops legitimate windows executable
- AIMr.exe (PID: 3696)
- python-3.12.1-amd64.exe (PID: 5540)
- pythoninstaller.exe (PID: 7164)
- msiexec.exe (PID: 2792)
Executable content was dropped or overwritten
- AIMr.exe (PID: 3696)
- pythoninstaller.exe (PID: 7140)
- pythoninstaller.exe (PID: 7164)
- python-3.12.1-amd64.exe (PID: 5540)
- python.exe (PID: 1876)
The process drops C-runtime libraries
- AIMr.exe (PID: 3696)
- python-3.12.1-amd64.exe (PID: 5540)
- pythoninstaller.exe (PID: 7164)
- msiexec.exe (PID: 2792)
Process drops python dynamic module
- AIMr.exe (PID: 3696)
- msiexec.exe (PID: 2792)
Application launched itself
- AIMr.exe (PID: 3696)
- python.exe (PID: 1544)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 6196)
Loads Python modules
- pythoninstaller.exe (PID: 7164)
- python.exe (PID: 1544)
- AIMr.exe (PID: 3688)
- python.exe (PID: 1876)
Reads security settings of Internet Explorer
- pythoninstaller.exe (PID: 7164)
Starts itself from another location
- pythoninstaller.exe (PID: 7164)
Searches for installed software
- pythoninstaller.exe (PID: 7164)
- dllhost.exe (PID: 2336)
Creates a software uninstall entry
- pythoninstaller.exe (PID: 7164)
Executes as Windows Service
- VSSVC.exe (PID: 5256)
Checks Windows Trust Settings
- msiexec.exe (PID: 2792)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2792)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 2792)
There is functionality for taking screenshot (YARA)
- pythoninstaller.exe (PID: 7164)
Uses WMIC.EXE to obtain Windows Installer data
- AIMr.exe (PID: 3688)
INFO
Checks supported languages
- AIMr.exe (PID: 3696)
- SearchApp.exe (PID: 5064)
- pythoninstaller.exe (PID: 7140)
- pythoninstaller.exe (PID: 7164)
- python-3.12.1-amd64.exe (PID: 5540)
- msiexec.exe (PID: 2792)
- msiexec.exe (PID: 5992)
- python.exe (PID: 1544)
- python.exe (PID: 1876)
- AIMr.exe (PID: 3688)
The sample compiled with english language support
- AIMr.exe (PID: 3696)
- pythoninstaller.exe (PID: 7140)
- pythoninstaller.exe (PID: 7164)
- python-3.12.1-amd64.exe (PID: 5540)
- msiexec.exe (PID: 2792)
- python.exe (PID: 1876)
Reads the computer name
- AIMr.exe (PID: 3696)
- AIMr.exe (PID: 3688)
- python-3.12.1-amd64.exe (PID: 5540)
- pythoninstaller.exe (PID: 7164)
- msiexec.exe (PID: 2792)
- msiexec.exe (PID: 5992)
- python.exe (PID: 1876)
Reads the machine GUID from the registry
- AIMr.exe (PID: 3688)
- SearchApp.exe (PID: 5064)
- msiexec.exe (PID: 2792)
- python-3.12.1-amd64.exe (PID: 5540)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6196)
PyInstaller has been detected (YARA)
- AIMr.exe (PID: 3688)
- AIMr.exe (PID: 3696)
Process checks computer location settings
- SearchApp.exe (PID: 5064)
- pythoninstaller.exe (PID: 7164)
Reads the software policy settings
- SearchApp.exe (PID: 5064)
- msiexec.exe (PID: 2792)
Create files in a temporary directory
- pythoninstaller.exe (PID: 7140)
- pythoninstaller.exe (PID: 7164)
- python-3.12.1-amd64.exe (PID: 5540)
- python.exe (PID: 1544)
- python.exe (PID: 1876)
- AIMr.exe (PID: 3696)
Manages system restore points
- SrTasks.exe (PID: 4864)
Creates files or folders in the user directory
- pythoninstaller.exe (PID: 7164)
- msiexec.exe (PID: 2792)
Creates files in the program directory
- python-3.12.1-amd64.exe (PID: 5540)
- python.exe (PID: 1544)
- python.exe (PID: 1876)
Mutex for Python MSI log
- msiexec.exe (PID: 2792)
- python-3.12.1-amd64.exe (PID: 5540)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2792)
Python executable
- python.exe (PID: 1544)
- python.exe (PID: 1876)
Creates a software uninstall entry
- msiexec.exe (PID: 2792)
Drops encrypted JS script (Microsoft Script Encoder)
- python.exe (PID: 1876)
Checks proxy server information
- AIMr.exe (PID: 3688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:04:03 02:18:31+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.38 |
| CodeSize: | 176128 |
| InitializedDataSize: | 111104 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb820 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
163
Monitored processes
18
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AIMr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1544 | "C:\Program Files\Python312\python.exe" -E -s -m ensurepip -U --default-pip | C:\Program Files\Python312\python.exe | — | msiexec.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python Version: 3.12.1 Modules
| |||||||||||||||
| 1876 | "C:\Program Files\Python312\python.exe" -W ignore::DeprecationWarning -c " import runpy import sys sys.path = ['C:\\Users\\admin\\AppData\\Local\\Temp\\tmpl4r6fh3t\\pip-23.2.1-py3-none-any.whl'] + sys.path sys.argv[1:] = ['install', '--no-cache-dir', '--no-index', '--find-links', 'C:\\Users\\admin\\AppData\\Local\\Temp\\tmpl4r6fh3t', '--upgrade', 'pip'] runpy.run_module(\"pip\", run_name=\"__main__\", alter_sys=True) " | C:\Program Files\Python312\python.exe | python.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python Version: 3.12.1 Modules
| |||||||||||||||
| 2336 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2792 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3688 | "C:\Users\admin\Desktop\AIMr.exe" | C:\Users\admin\Desktop\AIMr.exe | AIMr.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3696 | "C:\Users\admin\Desktop\AIMr.exe" | C:\Users\admin\Desktop\AIMr.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4804 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4864 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
47 382
Read events
43 172
Write events
4 126
Delete events
84
Modification events
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 929 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\ConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0049006E007000750074005F007B00380033003200620036003800640032002D0037006600650032002D0034006500370031002D0061003300610064002D003200360031003600360062003600350036006500630036007D000000C3E48BE47180DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LatestConstraintIndexFolder |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0041007000700073005F007B00660038006300350032003800640030002D0032003600620030002D0034003500300035002D0061003100340066002D003500390065003000640032006400310061003400310032007D000000C3E48BE47180DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LastConstraintIndexBuildCompleted |
Value: 60EE8CE47180DB01C3E48BE47180DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Input_{832b68d2-7fe2-4e71-a3ad-26166b656ec6} | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | LatestConstraintIndexFolder |
Value: C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{f8c528d0-26b0-4505-a14f-59e0d2d1a412} | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicText |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicTextTruncated |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | IndexedLanguage |
Value: en-US | |||
Executable files
148
Suspicious files
1 335
Text files
3 630
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3696 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI36962\VCRUNTIME140.dll | executable | |
MD5:8697C106593E93C11ADC34FAA483C4A0 | SHA256:FF43E813785EE948A937B642B03050BB4B1C6A5E23049646B891A66F65D4C833 | |||
| 3696 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI36962\_hashlib.pyd | executable | |
MD5:917CD9D31245F587CB36E92650B05952 | SHA256:68B478F11FE94F4C325B0239DC3F2BBB4B81ED1A7D40F0109A98990351D89967 | |||
| 3696 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI36962\_socket.pyd | executable | |
MD5:6DF98284426330435E5AA6B8434CF461 | SHA256:153F1D66C0FD99A6FBC77496F8A91591D8850A122CC57B99A2AF95FA58951401 | |||
| 3696 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI36962\_bz2.pyd | executable | |
MD5:054708E16D5775C58669CB2AA4E2CE88 | SHA256:FD08E5A2AA5D4E5C413C87A2193044B568E2A2C01AE0EBFEBDE56C42BB7A80B9 | |||
| 3696 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI36962\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:49C3FFD47257DBCB67A6BE9EE112BA7F | SHA256:322D963D2A2AEFD784E99697C59D494853D69BED8EFD4B445F59292930A6B165 | |||
| 3696 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI36962\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:BFFFA7117FD9B1622C66D949BAC3F1D7 | SHA256:1EA267A2E6284F17DD548C6F2285E19F7EDB15D6E737A55391140CE5CB95225E | |||
| 3696 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI36962\api-ms-win-core-handle-l1-1-0.dll | executable | |
MD5:CCE27FF9B1E78B61955682788452F785 | SHA256:8EE2DE377A045C52BBB05087AE3C2F95576EDFB0C2767F40B13454F2D9F779DE | |||
| 3696 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI36962\_lzma.pyd | executable | |
MD5:012D4FF37E52E0D258BDBBE4C17FC012 | SHA256:D6297ABB919F3F69E94C035FCA327E56841E5ABEBBFF29FF95FE0A68BE46432D | |||
| 3696 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI36962\_ctypes.pyd | executable | |
MD5:11399D7C6D62ED339ADA949DCF41F127 | SHA256:AF49DBAB240639E26C6186122B1E660FC33B15105D67C2523A162BEE0F75A46B | |||
| 3696 | AIMr.exe | C:\Users\admin\AppData\Local\Temp\_MEI36962\_ssl.pyd | executable | |
MD5:B2EC752BF3928BF6C8A8F1EE36CA5607 | SHA256:E65568773DB94E6F2DD33B5973DEEAD718ADC8BC47E99ABDF314C7629C359E5B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
79
DNS requests
43
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2548 | svchost.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2548 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6660 | SIHClient.exe | GET | 200 | 72.246.169.155:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4204 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6660 | SIHClient.exe | GET | 200 | 72.246.169.155:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2548 | svchost.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
2548 | svchost.exe | 23.209.214.100:80 | www.microsoft.com | PT. Telekomunikasi Selular | ID | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.209.214.100:80 | www.microsoft.com | PT. Telekomunikasi Selular | ID | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.19.122.39:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2624 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2548 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
5064 | SearchApp.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |