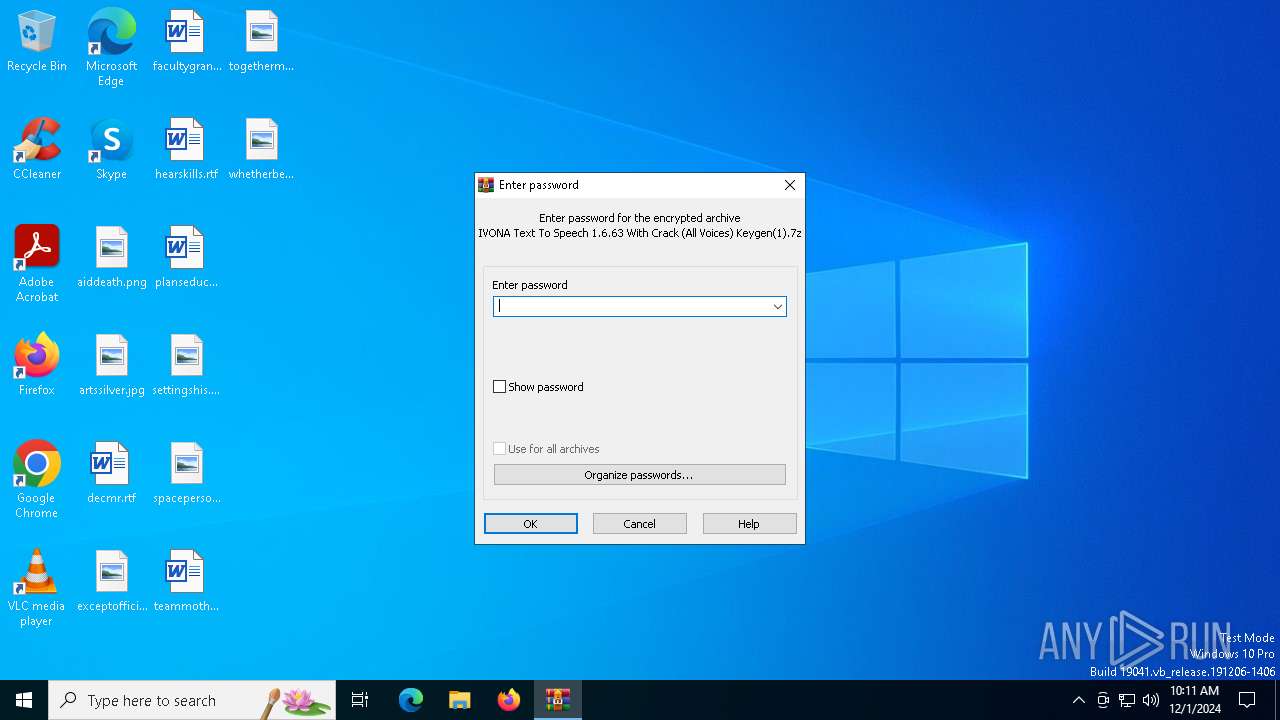
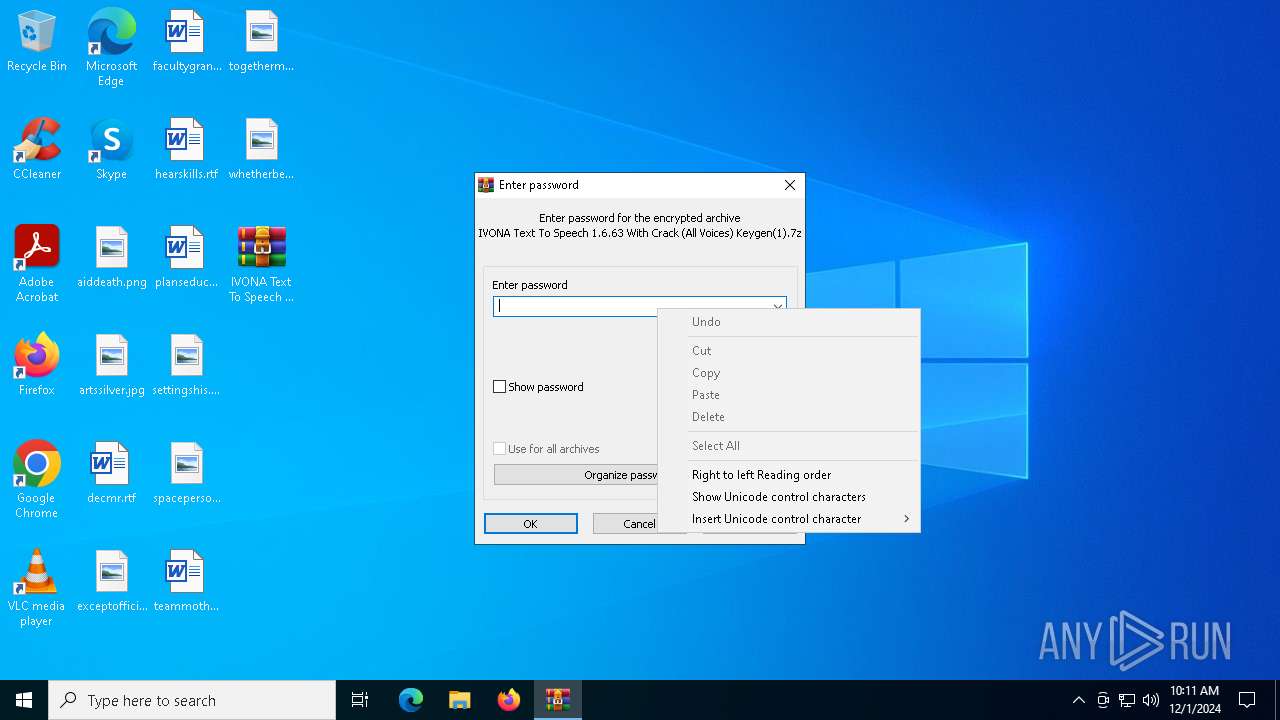
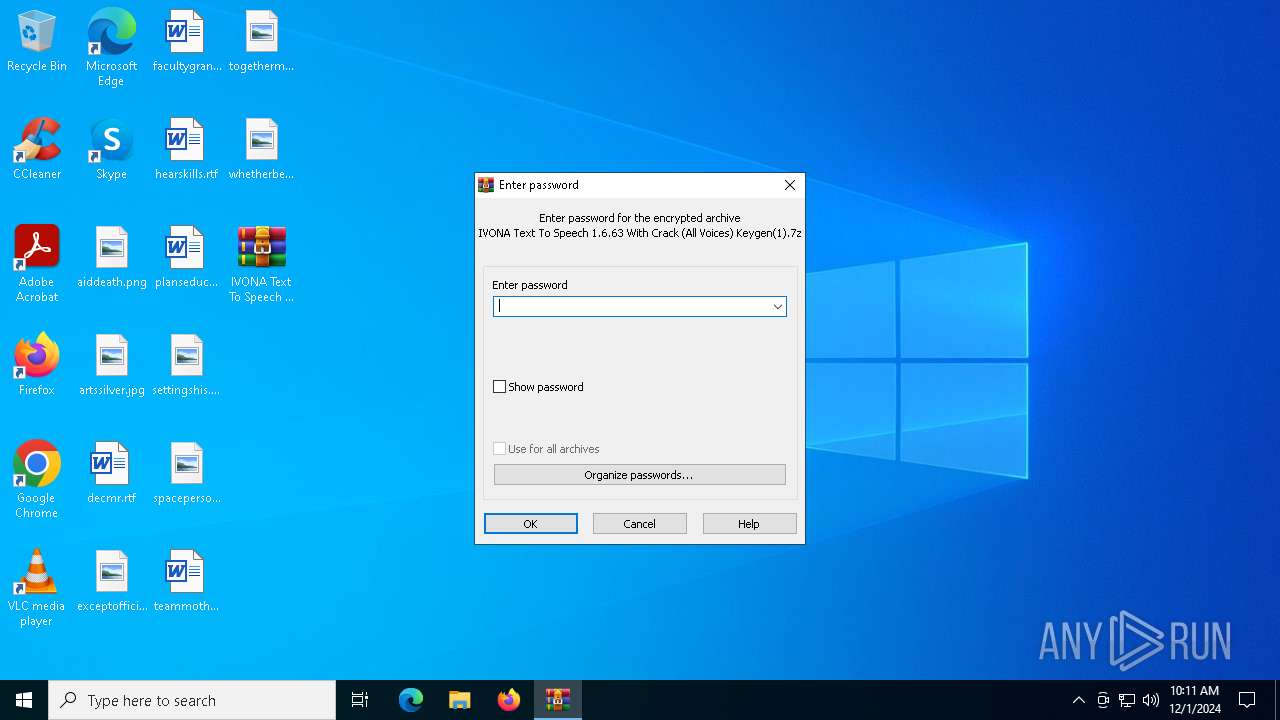
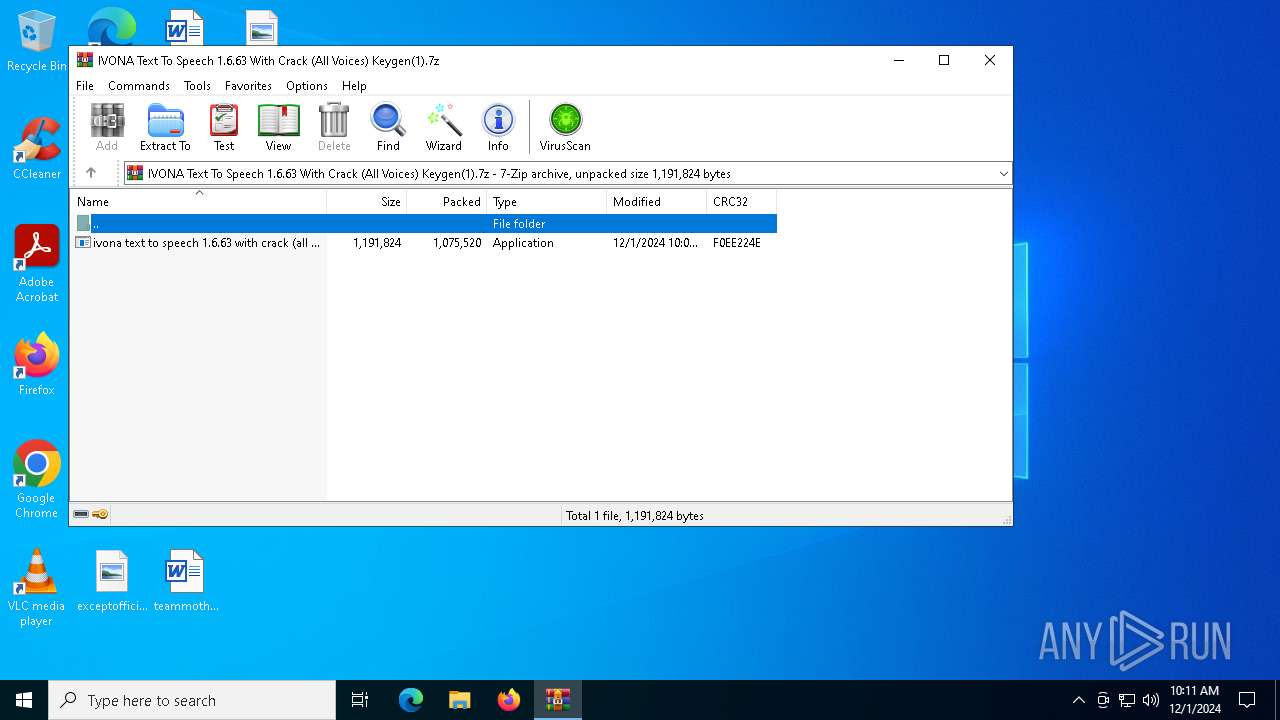
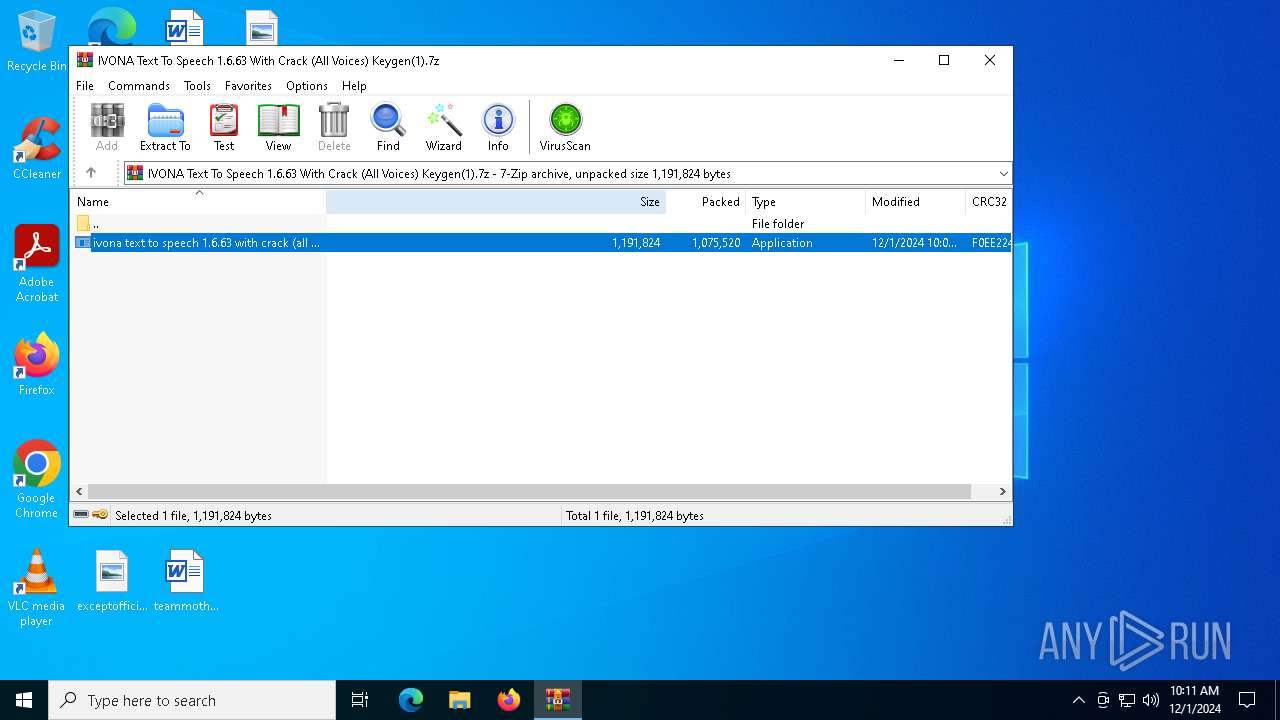
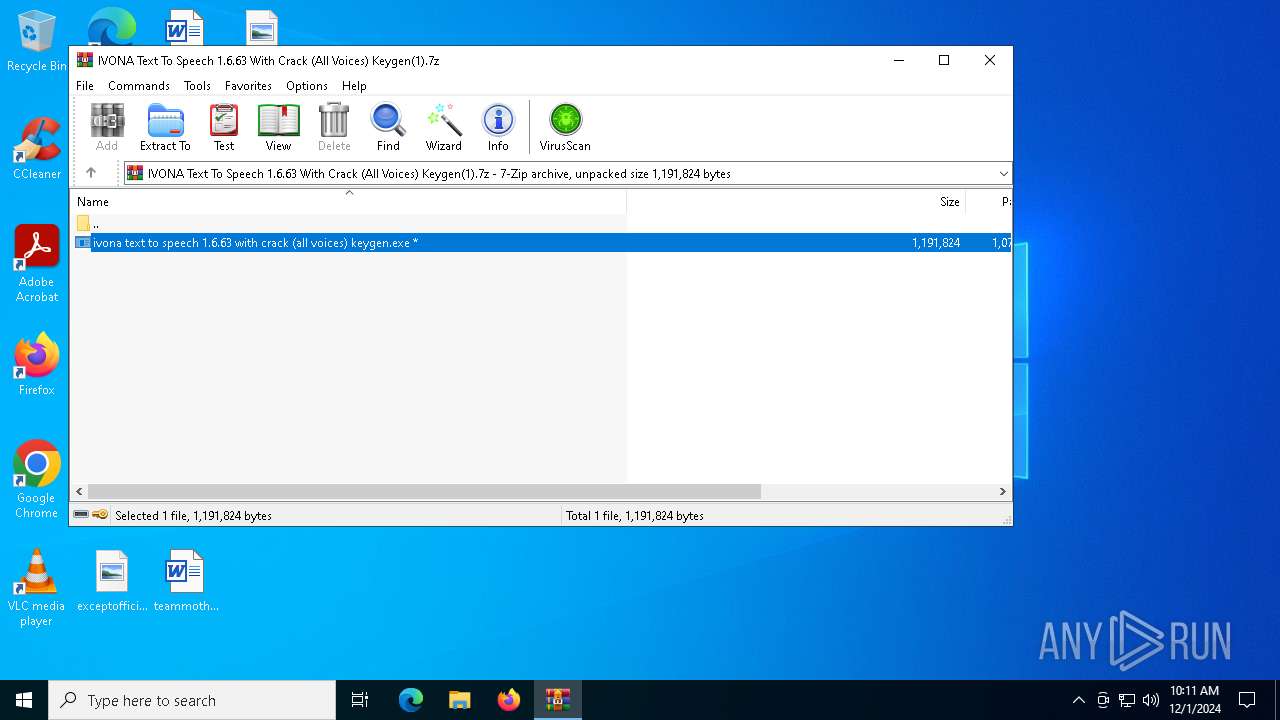
| File name: | IVONA Text To Speech 1.6.63 With Crack (All Voices) Keygen(1).7z |
| Full analysis: | https://app.any.run/tasks/693b2d07-ec68-4305-81c6-339c88e72aca |
| Verdict: | Malicious activity |
| Analysis date: | December 01, 2024, 10:10:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 4B05ED940DB80C1610BA8DB2304E4A6D |
| SHA1: | 9E38E0D4D947A6A40A0446E5F7E7A854F97A5984 |
| SHA256: | 4810B879EBC844D2F0974DD9865D8CAF4F00554AE2EFBA83FAF0E2F4D936493A |
| SSDEEP: | 49152:kD8U6tf+PxukjxrZR4OprTKaTkkGVMWnkn12xjTynOs5UHKYoPk+hoDFYLwC6c7k:0P6d+PxpRHBlTk3VMWnw2xjqxUHKJLwN |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- ivona text to speech 1.6.63 with crack (all voices) keygen.exe (PID: 4628)
- cmd.exe (PID: 4764)
Get information on the list of running processes
- cmd.exe (PID: 4764)
Executing commands from ".cmd" file
- ivona text to speech 1.6.63 with crack (all voices) keygen.exe (PID: 4628)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4764)
Starts the AutoIt3 executable file
- cmd.exe (PID: 4764)
Starts application with an unusual extension
- cmd.exe (PID: 4764)
Executable content was dropped or overwritten
- cmd.exe (PID: 4764)
Application launched itself
- cmd.exe (PID: 4764)
The executable file from the user directory is run by the CMD process
- Arrangements.com (PID: 6528)
INFO
Manual execution by a user
- ivona text to speech 1.6.63 with crack (all voices) keygen.exe (PID: 4628)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6240)
Creates a new folder
- cmd.exe (PID: 4164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
142
Monitored processes
13
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3876 | findstr "AvastUI AVGUI bdservicehost nsWscSvc ekrn SophosHealth" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | cmd /c md 247269 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | "C:\Users\admin\Desktop\ivona text to speech 1.6.63 with crack (all voices) keygen.exe" | C:\Users\admin\Desktop\ivona text to speech 1.6.63 with crack (all voices) keygen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4764 | "C:\Windows\System32\cmd.exe" /c copy Jokes Jokes.cmd && Jokes.cmd | C:\Windows\SysWOW64\cmd.exe | ivona text to speech 1.6.63 with crack (all voices) keygen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4816 | findstr /I "wrsa opssvc" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4876 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5032 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5036 | findstr /V "displayedstartkaraokeequivalent" Titten | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5592 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6240 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\IVONA Text To Speech 1.6.63 With Crack (All Voices) Keygen(1).7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
2 184
Read events
2 175
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\IVONA Text To Speech 1.6.63 With Crack (All Voices) Keygen(1).7z | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
8
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4628 | ivona text to speech 1.6.63 with crack (all voices) keygen.exe | C:\Users\admin\AppData\Local\Temp\Adaptive | binary | |
MD5:BA1264B8A6F38342F8611A4447CA4C11 | SHA256:FD0AA19B15DF7FDB4FB86BB7B09E785C7D9B3B87BDC1069E64753FB437452EA5 | |||
| 4628 | ivona text to speech 1.6.63 with crack (all voices) keygen.exe | C:\Users\admin\AppData\Local\Temp\Seems | binary | |
MD5:5A8351E7575B8AE43083EB4F5614259B | SHA256:C6EA97F6A9D7AAE0235EC5617ABD10CE1A65F6EE9C89022648DFEA366B4DF16F | |||
| 4628 | ivona text to speech 1.6.63 with crack (all voices) keygen.exe | C:\Users\admin\AppData\Local\Temp\Jokes | text | |
MD5:977321FAC0DB15C755D7B88BDC018967 | SHA256:56C4483C5CD720F4FB34A45A0F10E707BC41C94187F3C595E7E4015A5BB9CF0C | |||
| 4628 | ivona text to speech 1.6.63 with crack (all voices) keygen.exe | C:\Users\admin\AppData\Local\Temp\Named | binary | |
MD5:8818AC4338EDA73576023030C9091F3C | SHA256:09F45844F1906F0FAF28F3BD1FED12AF4889FA1C0C0257DECB9F55D7A1EACE7D | |||
| 4628 | ivona text to speech 1.6.63 with crack (all voices) keygen.exe | C:\Users\admin\AppData\Local\Temp\Bufing | binary | |
MD5:B66AE963702D9DFF703C5BBE19941F67 | SHA256:F14C5664EC7C07B87176753612A57B919F8FC43450CEC0D33337563F5D19CCAC | |||
| 4628 | ivona text to speech 1.6.63 with crack (all voices) keygen.exe | C:\Users\admin\AppData\Local\Temp\Titten | binary | |
MD5:339695CC66C72D4435BDF023C010DBF9 | SHA256:B33A84A36B25D9148FB3A86E94187BDE13A8384204B9AB8344B1C1EFD4676458 | |||
| 4764 | cmd.exe | C:\Users\admin\AppData\Local\Temp\247269\Arrangements.com | executable | |
MD5:6EE7DDEBFF0A2B78C7AC30F6E00D1D11 | SHA256:865347471135BB5459AD0E647E75A14AD91424B6F13A5C05D9ECD9183A8A1CF4 | |||
| 4628 | ivona text to speech 1.6.63 with crack (all voices) keygen.exe | C:\Users\admin\AppData\Local\Temp\Smell | binary | |
MD5:2116597C6F944641CAEFF8572D8FE202 | SHA256:EF72BF0B2EFCCF0E1508EBB152E486628594693E94D314D1EAF573A27826695E | |||
| 4764 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Jokes.cmd | text | |
MD5:977321FAC0DB15C755D7B88BDC018967 | SHA256:56C4483C5CD720F4FB34A45A0F10E707BC41C94187F3C595E7E4015A5BB9CF0C | |||
| 6516 | cmd.exe | C:\Users\admin\AppData\Local\Temp\247269\r | binary | |
MD5:F4E7DE91405F602ED6575804D896F4E8 | SHA256:119901EA0BE881E4900AA79532F87BCD87183CB59FC5E3E8E1702080E05287BA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
440 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5432 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
440 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5432 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6756 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
440 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3296 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 104.126.37.160:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
440 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
440 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |