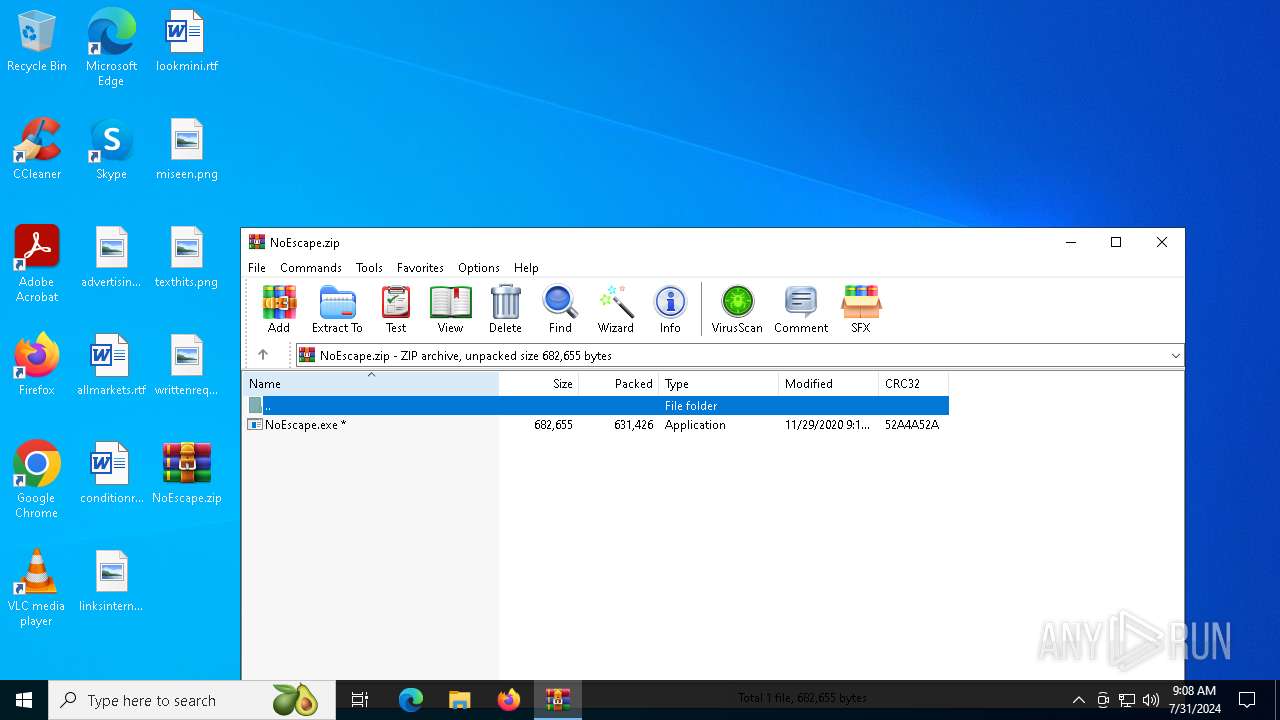
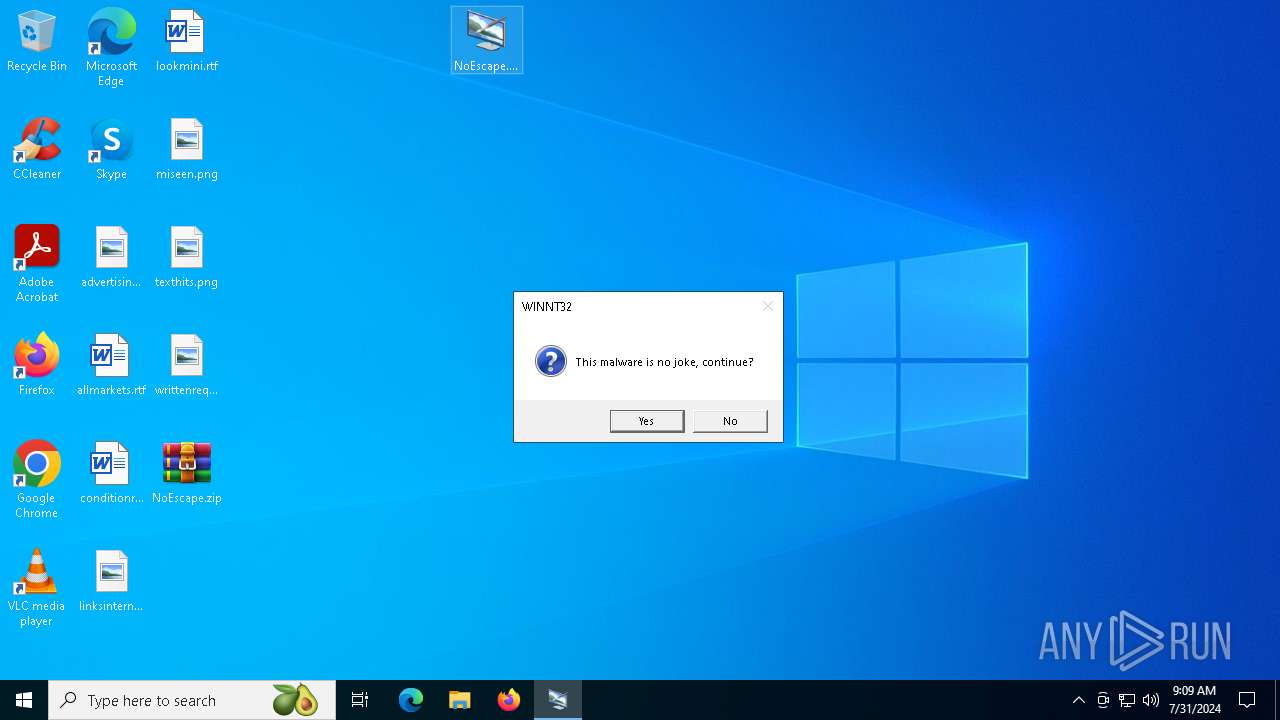
| File name: | NoEscape.zip |
| Full analysis: | https://app.any.run/tasks/ab96b906-d645-4f2a-989c-d4ff6366a14f |
| Verdict: | Malicious activity |
| Analysis date: | July 31, 2024, 09:08:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | EF4FDF65FC90BFDA8D1D2AE6D20AFF60 |
| SHA1: | 9431227836440C78F12BFB2CB3247D59F4D4640B |
| SHA256: | 47F6D3A11FFD015413FFB96432EC1F980FBA5DD084990DD61A00342C5F6DA7F8 |
| SSDEEP: | 12288:1PQuO1JLx2auoA82iqOxdOc7XPkmpOw6mqc5m937hnTMktj1H:1PVqJx2auYqw7dOw6mql3nNBd |
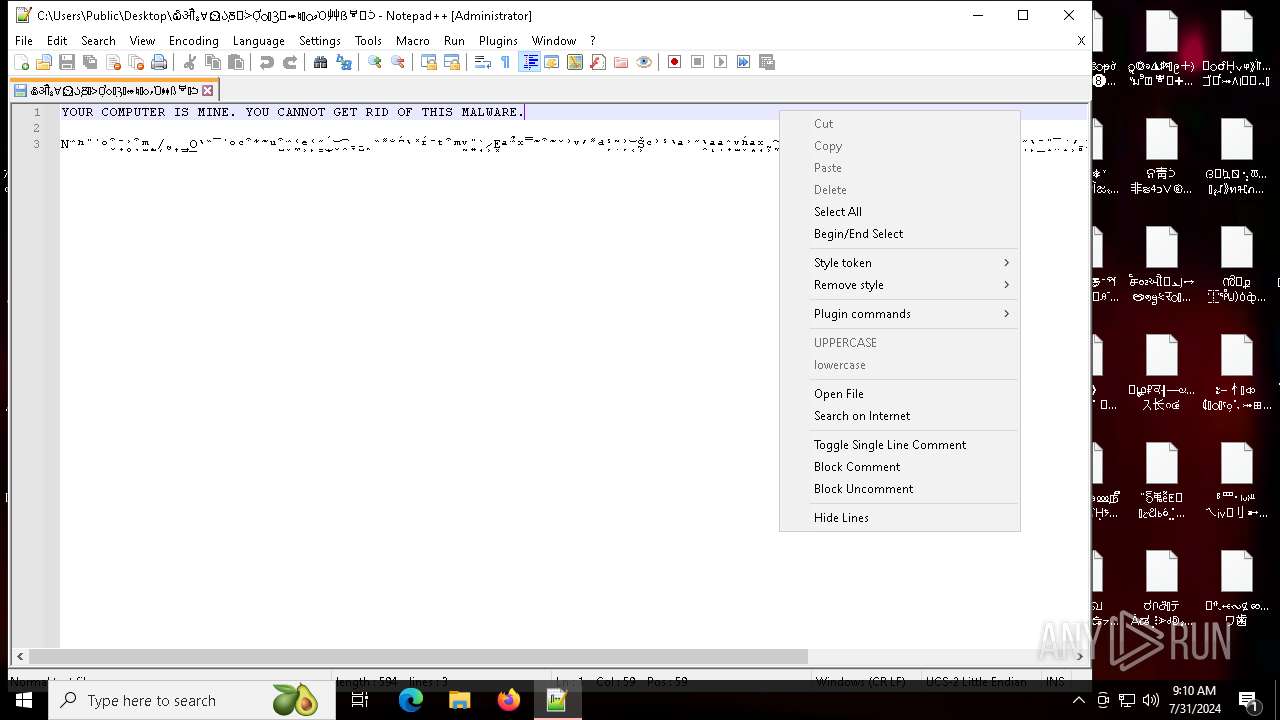
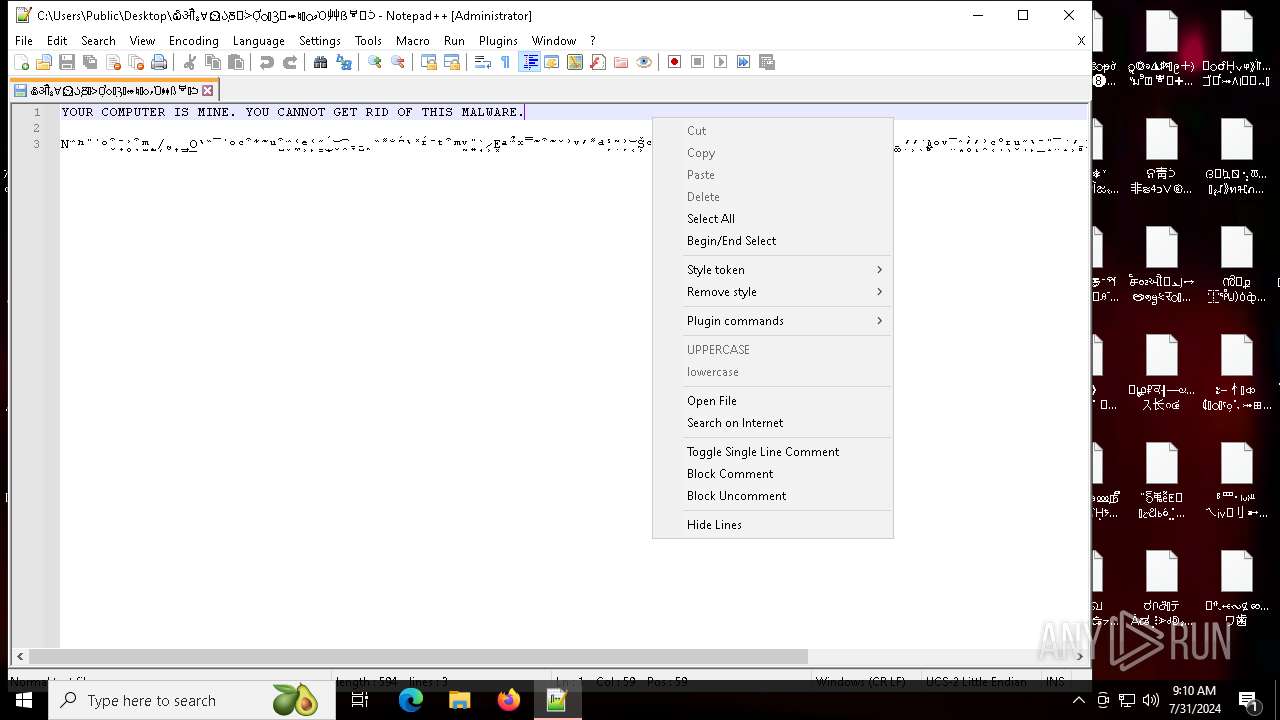
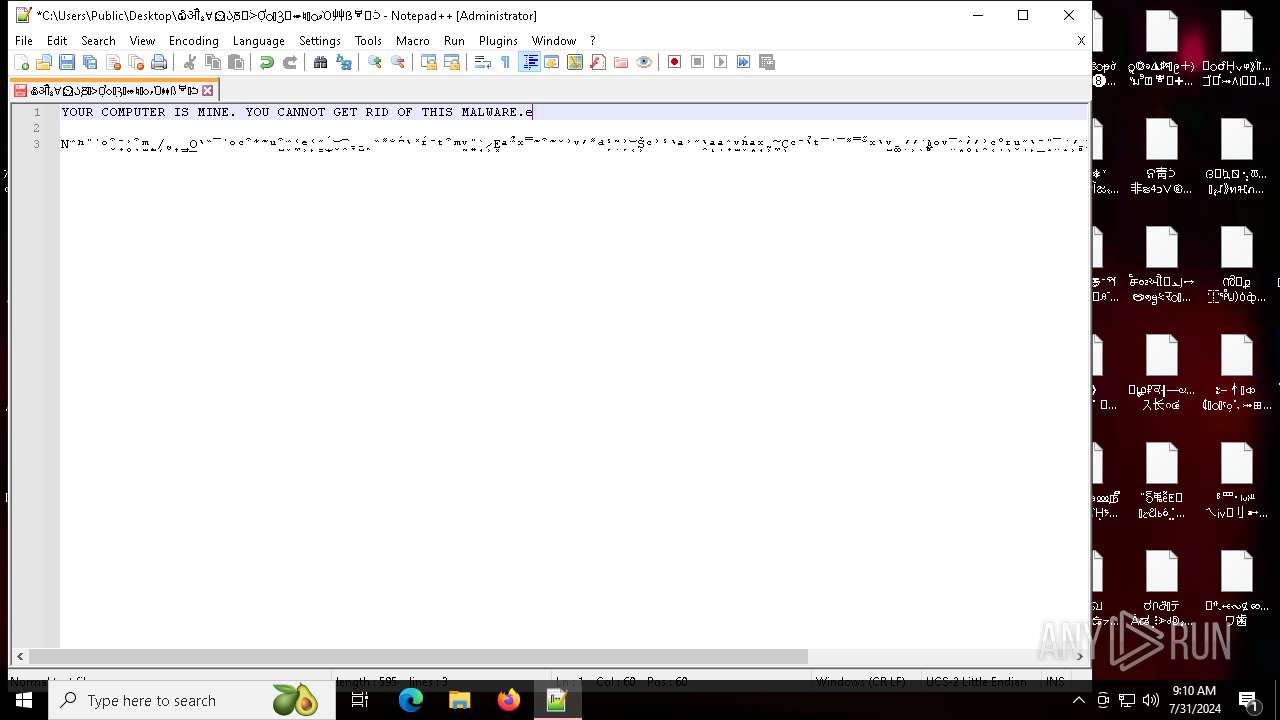
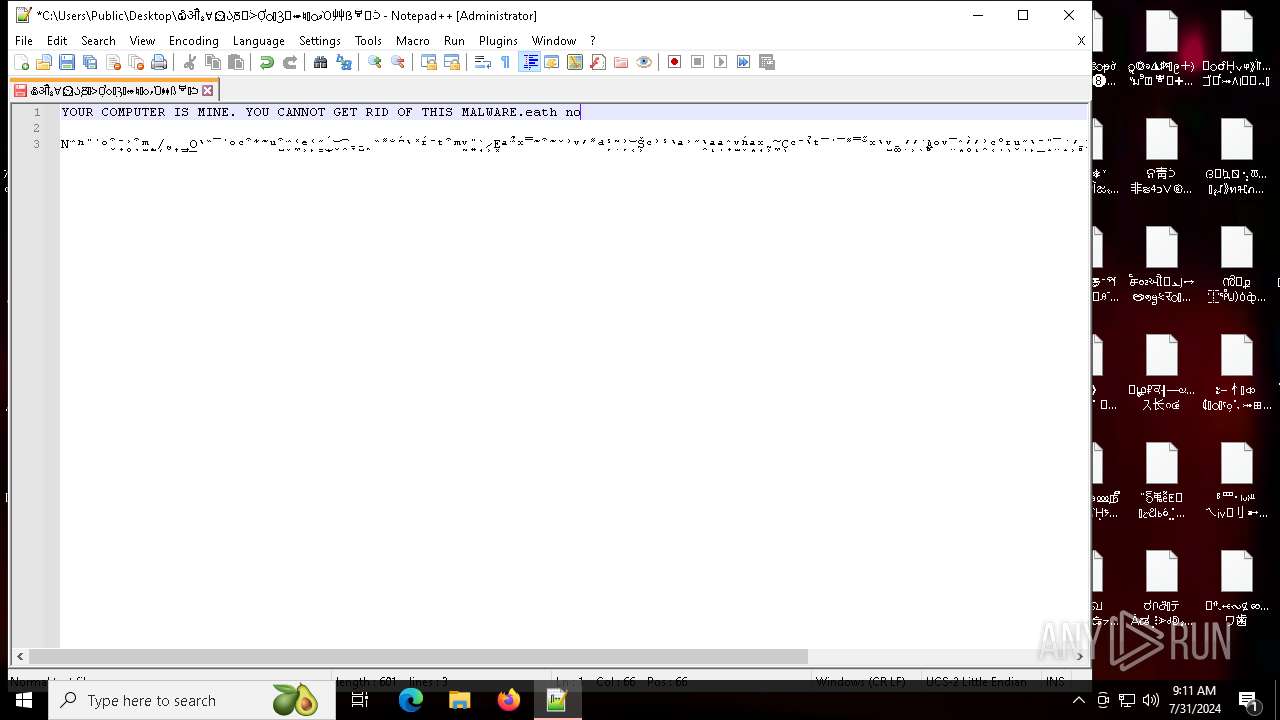
MALICIOUS
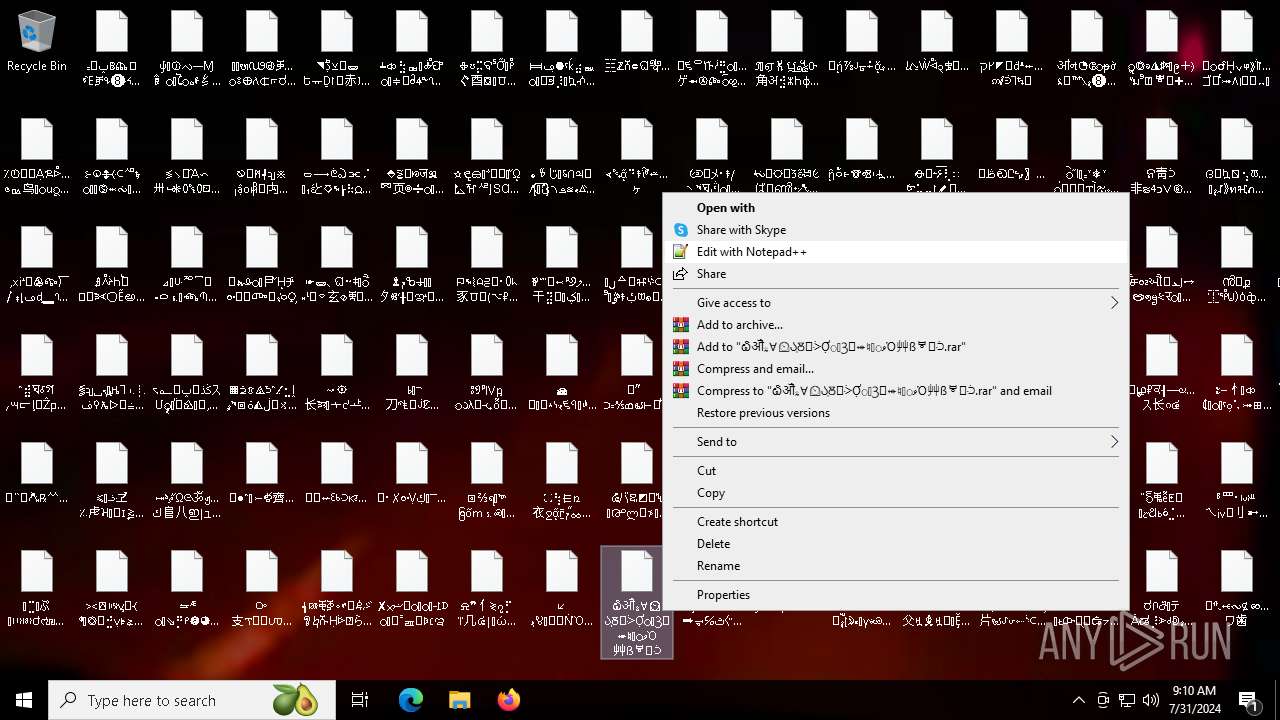
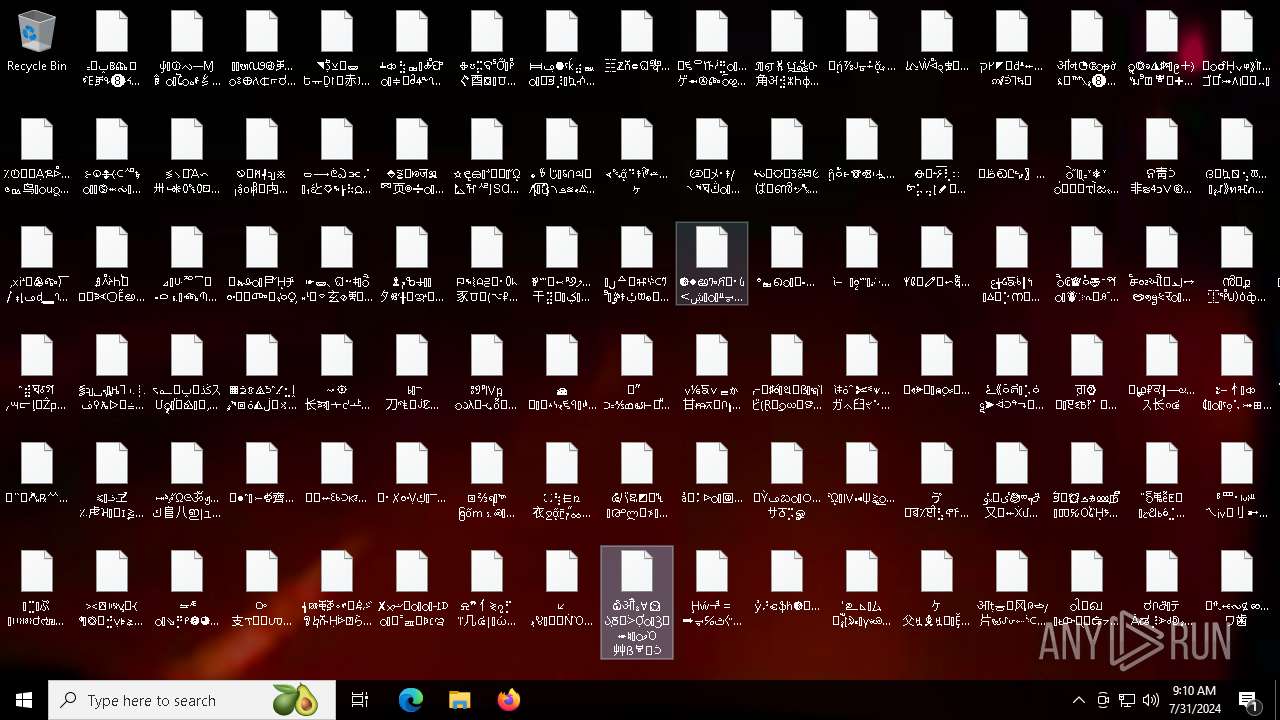
Drops the executable file immediately after the start
- NoEscape.exe (PID: 6960)
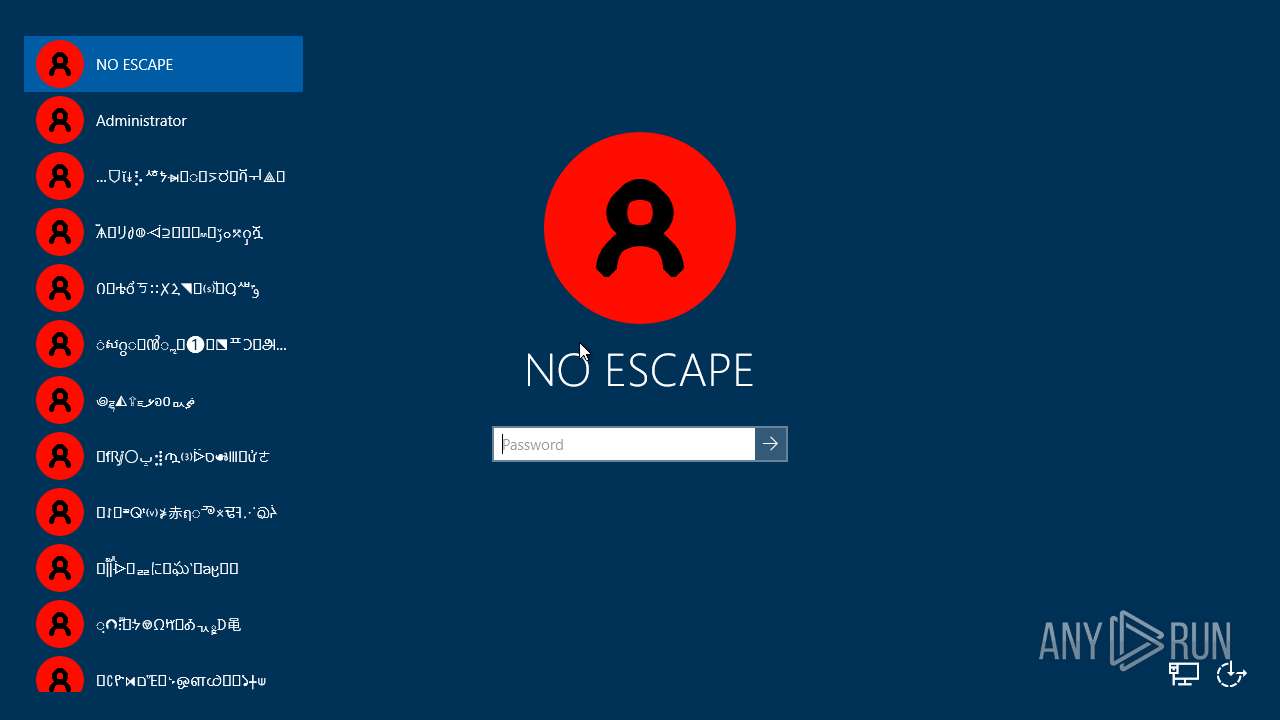
Changes the login/logoff helper path in the registry
- NoEscape.exe (PID: 6960)
Disables the Shutdown in the Start menu
- NoEscape.exe (PID: 6960)
UAC/LUA settings modification
- NoEscape.exe (PID: 6960)
SUSPICIOUS
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 2464)
- NoEscape.exe (PID: 2960)
Reads the date of Windows installation
- NoEscape.exe (PID: 2960)
Application launched itself
- NoEscape.exe (PID: 2960)
Executable content was dropped or overwritten
- NoEscape.exe (PID: 6960)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4204)
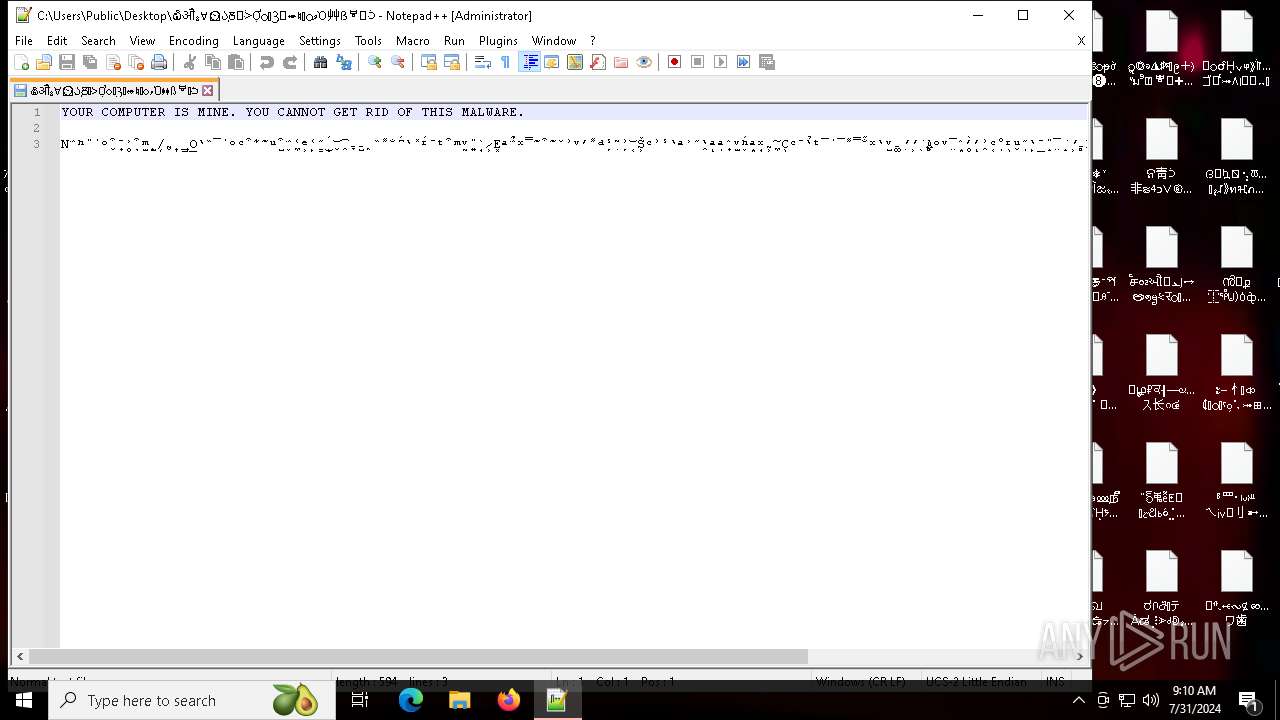
Likely accesses (executes) a file from the Public directory
- notepad++.exe (PID: 6704)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6688)
Checks supported languages
- ShellExperienceHost.exe (PID: 2464)
- NoEscape.exe (PID: 2960)
- NoEscape.exe (PID: 6960)
- PLUGScheduler.exe (PID: 4204)
Creates files or folders in the user directory
- NoEscape.exe (PID: 6960)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6688)
Manual execution by a user
- NoEscape.exe (PID: 2960)
- notepad++.exe (PID: 6704)
Reads the computer name
- NoEscape.exe (PID: 2960)
- PLUGScheduler.exe (PID: 4204)
- NoEscape.exe (PID: 6960)
- ShellExperienceHost.exe (PID: 2464)
Process checks computer location settings
- NoEscape.exe (PID: 2960)
Creates files in the program directory
- PLUGScheduler.exe (PID: 4204)
- NoEscape.exe (PID: 6960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:11:29 12:11:58 |
| ZipCRC: | 0x52a4a52a |
| ZipCompressedSize: | 631426 |
| ZipUncompressedSize: | 682655 |
| ZipFileName: | NoEscape.exe |
Total processes
246
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2464 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2960 | "C:\Users\admin\Desktop\NoEscape.exe" | C:\Users\admin\Desktop\NoEscape.exe | — | explorer.exe | |||||||||||
User: admin Company: Endermanch Integrity Level: MEDIUM Description: Windows Customization Tool Exit code: 0 Version: 6.6.6.6 Modules
| |||||||||||||||
| 4204 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6688 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\NoEscape.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
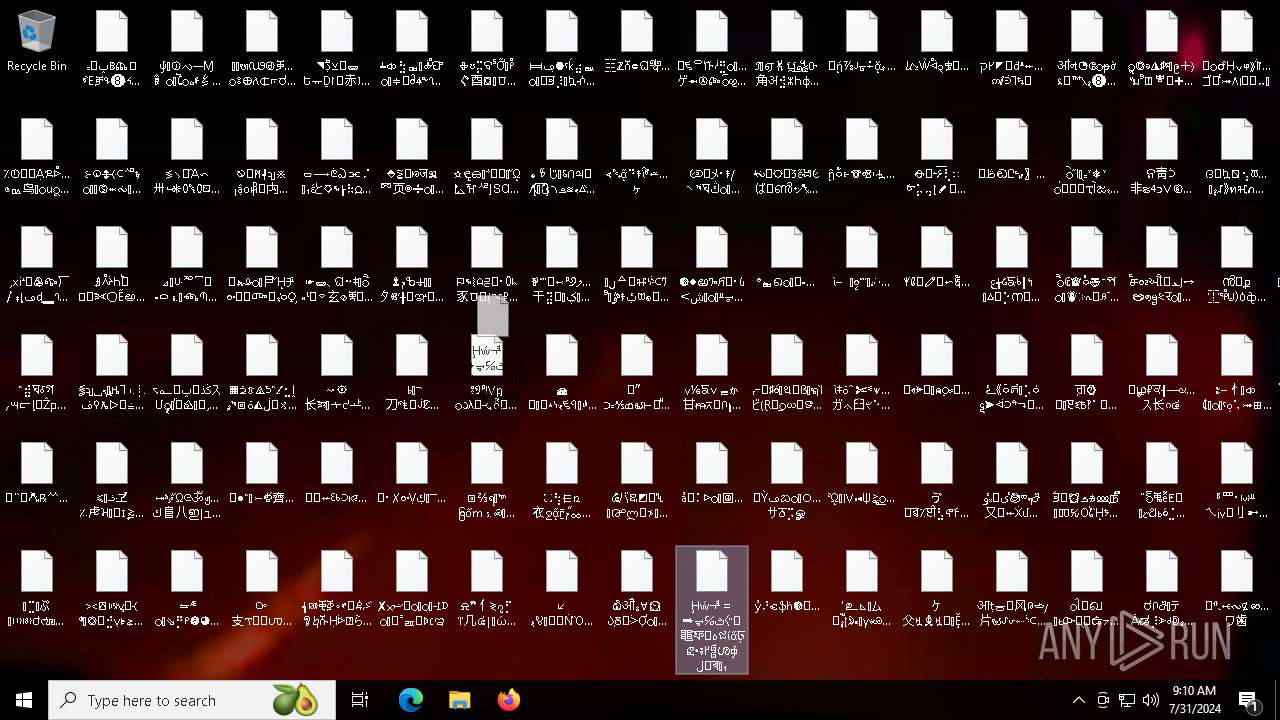
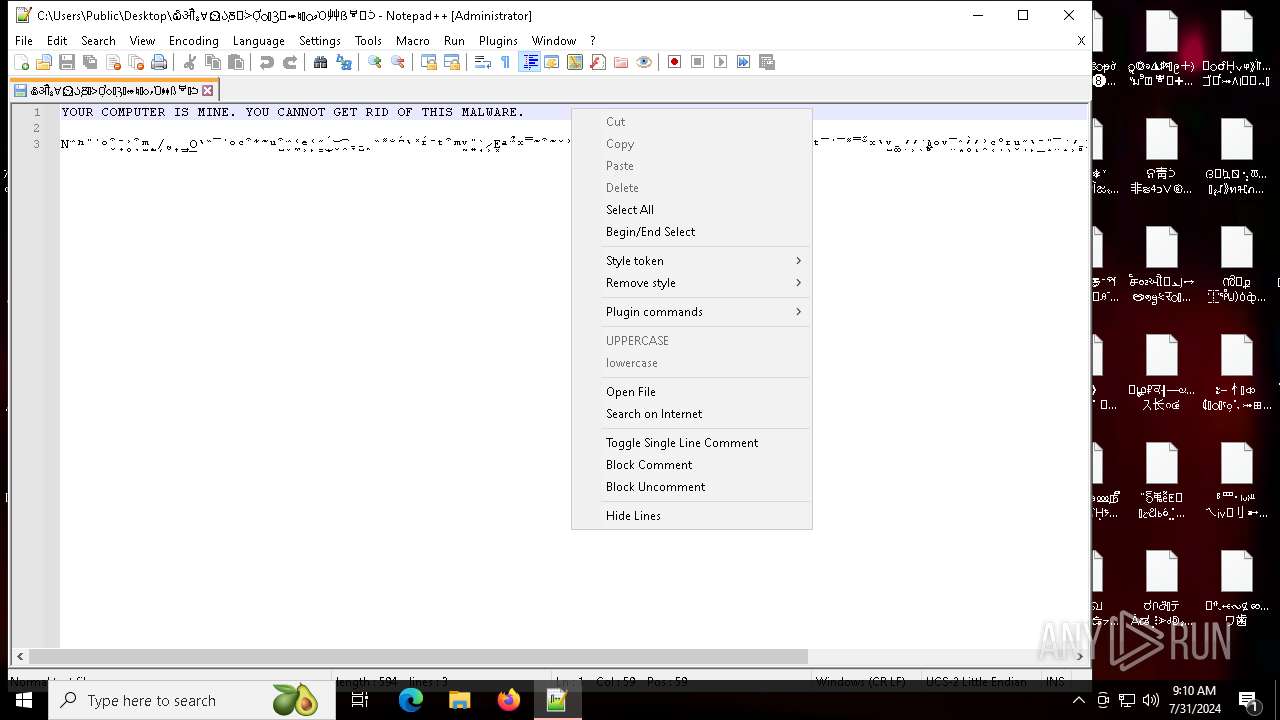
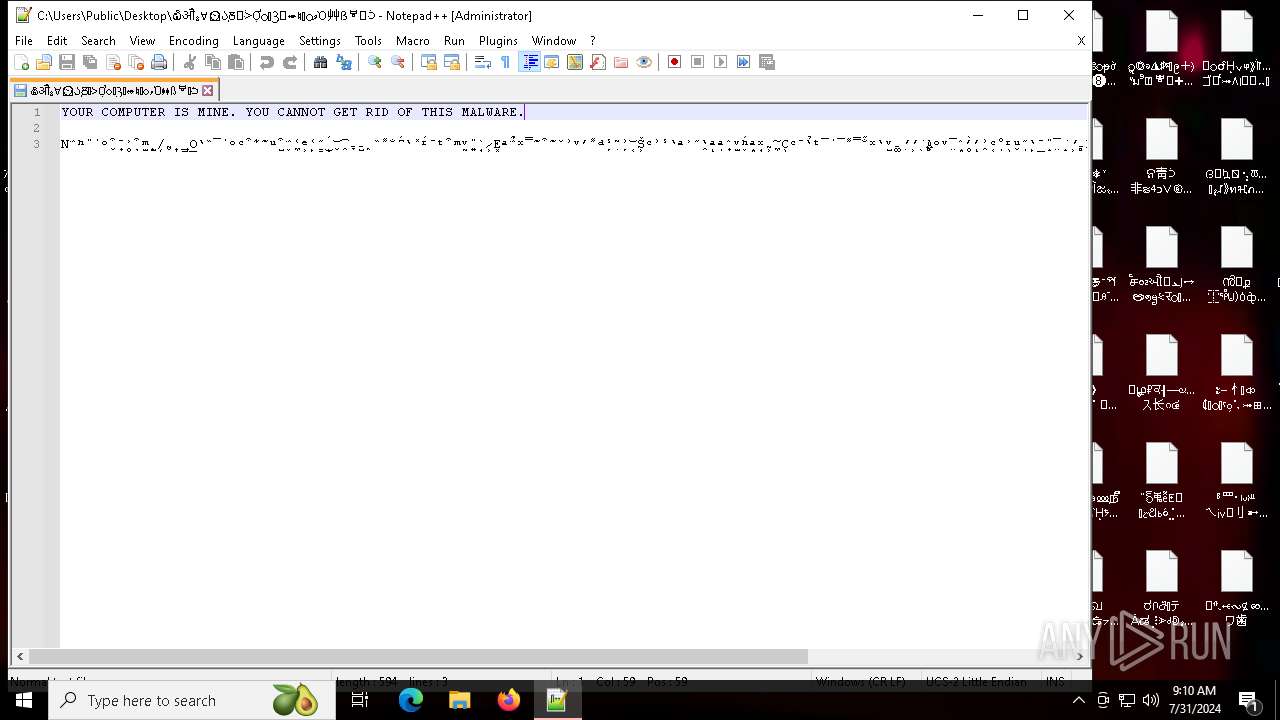
| 6704 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\Public\Desktop\໖ॵྎ∀⏲ᲐֽⰋᑂỢᬁⳌ⬰♮ᮦވὉ⾋ẞᄫᑟ" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: HIGH Description: Notepad++ : a free (GNU) source code editor Version: 7.91 Modules
| |||||||||||||||
| 6960 | "C:\Users\admin\Desktop\NoEscape.exe" | C:\Users\admin\Desktop\NoEscape.exe | NoEscape.exe | ||||||||||||
User: admin Company: Endermanch Integrity Level: HIGH Description: Windows Customization Tool Exit code: 0 Version: 6.6.6.6 Modules
| |||||||||||||||
Total events
6 296
Read events
6 254
Write events
42
Delete events
0
Modification events
| (PID) Process: | (6688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\NoEscape.zip | |||
| (PID) Process: | (6688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFE9000000E3000000A9040000CC020000 | |||
Executable files
2
Suspicious files
191
Text files
12
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6960 | NoEscape.exe | C:\ProgramData\Microsoft\User Account Pictures\user-40.png | image | |
MD5:D8E22EF10BD7AB65F56220D2845D6A94 | SHA256:B115A4548AD8E9C7CADB707A0FF79FCD55D9D900EEFA7A922CA50C85C4D3CA1D | |||
| 6688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6688.24265\NoEscape.exe | executable | |
MD5:989AE3D195203B323AA2B3ADF04E9833 | SHA256:D30D7676A3B4C91B77D403F81748EBF6B8824749DB5F860E114A8A204BCA5B8F | |||
| 6960 | NoEscape.exe | C:\ProgramData\Microsoft\User Account Pictures\user.bmp | image | |
MD5:2AB3698B005B421349512142ED6B965E | SHA256:150E95DA6C1E09511241130DA0E376878F5E24E21C2A9DFE7FBCC1022660E29F | |||
| 6960 | NoEscape.exe | C:\ProgramData\Microsoft\User Account Pictures\user-192.png | image | |
MD5:6BF949C62C5E9D07593BA5B604E36773 | SHA256:E54EA8405024F1FA72E470417059BDD186B0A3836F7D5E1C2C95C6003383912F | |||
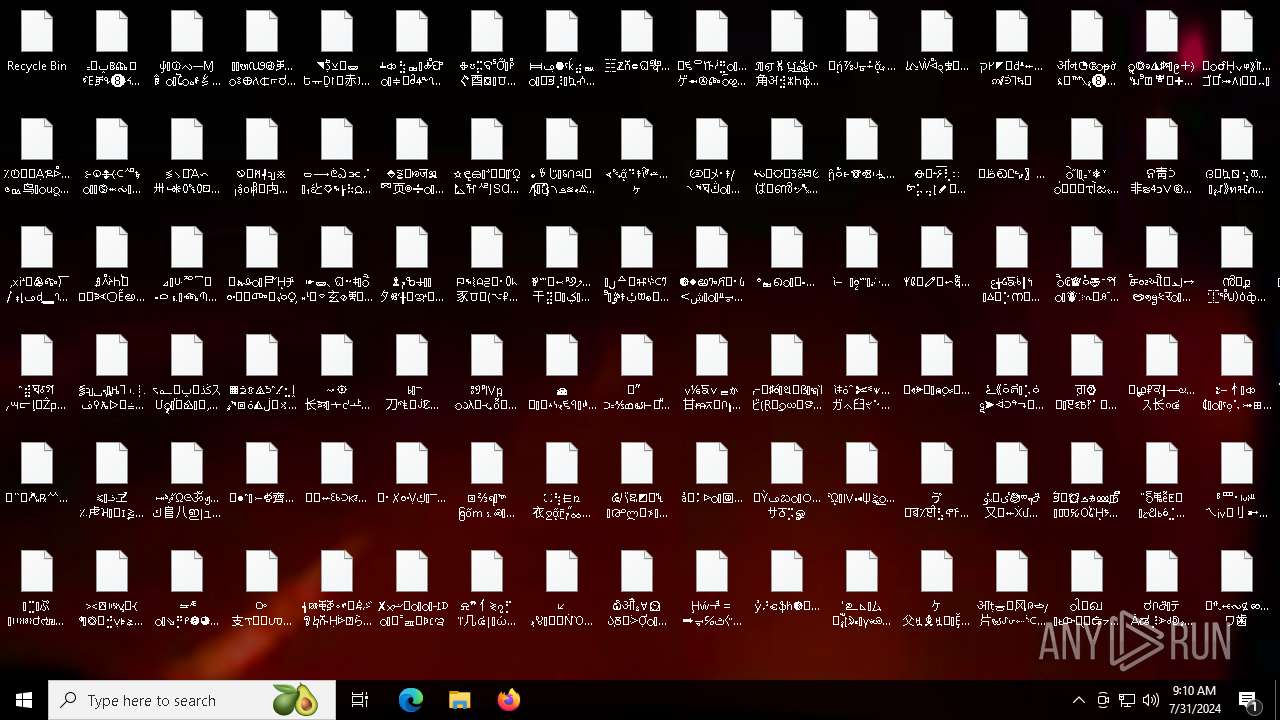
| 6960 | NoEscape.exe | C:\Users\admin\AppData\Local\noescape.png | image | |
MD5:9E655CFD3D501F1ED01D6A2E0DB0E744 | SHA256:CF7B5334E06A13501821834CD1AEDB7C3306A543F7D8EC03D1F20BFAF9BED613 | |||
| 6960 | NoEscape.exe | C:\Users\Public\Desktop\ع╆Ᏽਙᒀ┃↰ᤓᐏ⡑ന⪁᭖⇖ᴪⰋⓏرせ | binary | |
MD5:E49F0A8EFFA6380B4518A8064F6D240B | SHA256:8DBD06E9585C5A16181256C9951DBC65621DF66CEB22C8E3D2304477178BEE13 | |||
| 6960 | NoEscape.exe | C:\Users\Public\Desktop\קᚴ◤ḋᵜ⇷፯ẖ⊥ဢⅈᣦႨᛪ | binary | |
MD5:E49F0A8EFFA6380B4518A8064F6D240B | SHA256:8DBD06E9585C5A16181256C9951DBC65621DF66CEB22C8E3D2304477178BEE13 | |||
| 6960 | NoEscape.exe | C:\ProgramData\Microsoft\User Account Pictures\user.png | image | |
MD5:96F17C361A25164E71716D5BB56CB3D8 | SHA256:1025314EF977B5D07041B8B73E4ADBEA779E5E06096C3C66BD1F06FBBBA7FD1C | |||
| 6960 | NoEscape.exe | C:\ProgramData\Microsoft\User Account Pictures\user-32.png | image | |
MD5:5D572D54E293ACD90D5B8AD6036333DA | SHA256:4810DC6C101937DDE12D4581DE81E608EA144761D1307779DC6A256872330EDE | |||
| 6960 | NoEscape.exe | C:\Users\Public\Desktop\ᱢᇁᵼ⮄⠜≆ሒ۩ඳ⠽ᷙ⩧Ᾰ⤯⣋ۓ⨬⎬ᰙ╘ቍᆪݱ܆ት | binary | |
MD5:E49F0A8EFFA6380B4518A8064F6D240B | SHA256:8DBD06E9585C5A16181256C9951DBC65621DF66CEB22C8E3D2304477178BEE13 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
58
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4364 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6552 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6600 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3000 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2536 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4484 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5336 | SearchApp.exe | 92.123.104.40:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4364 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |