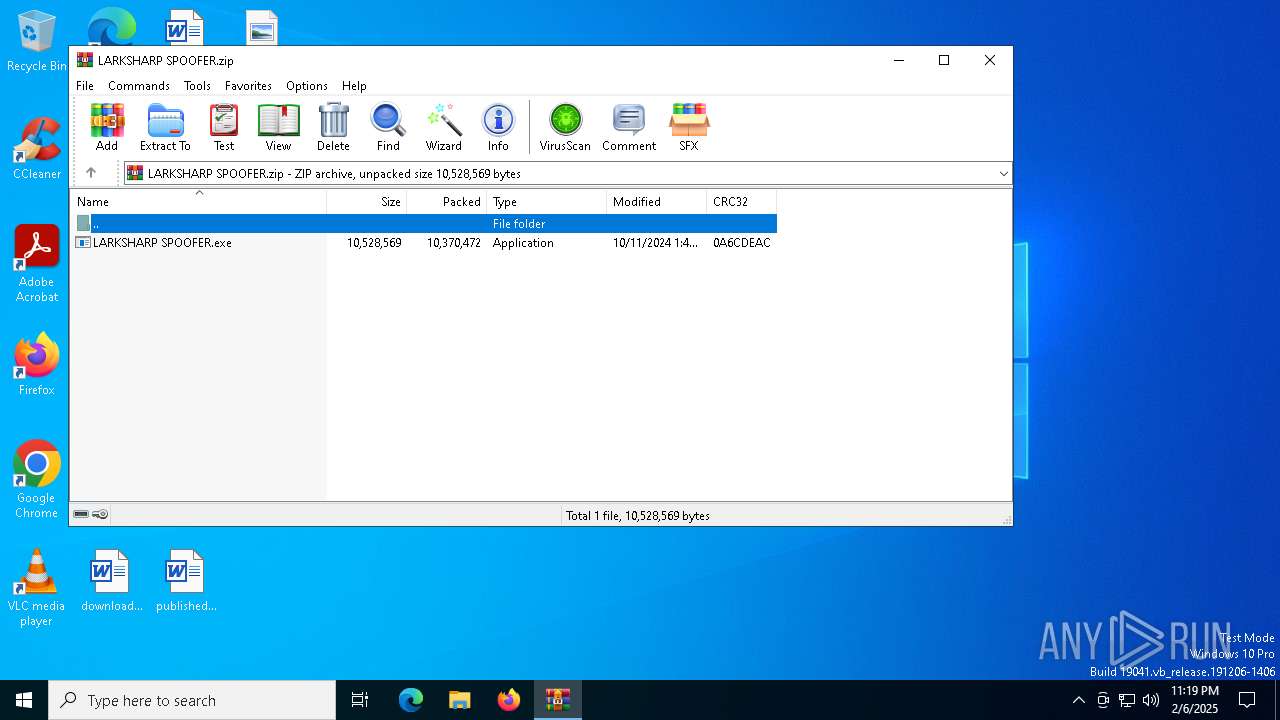
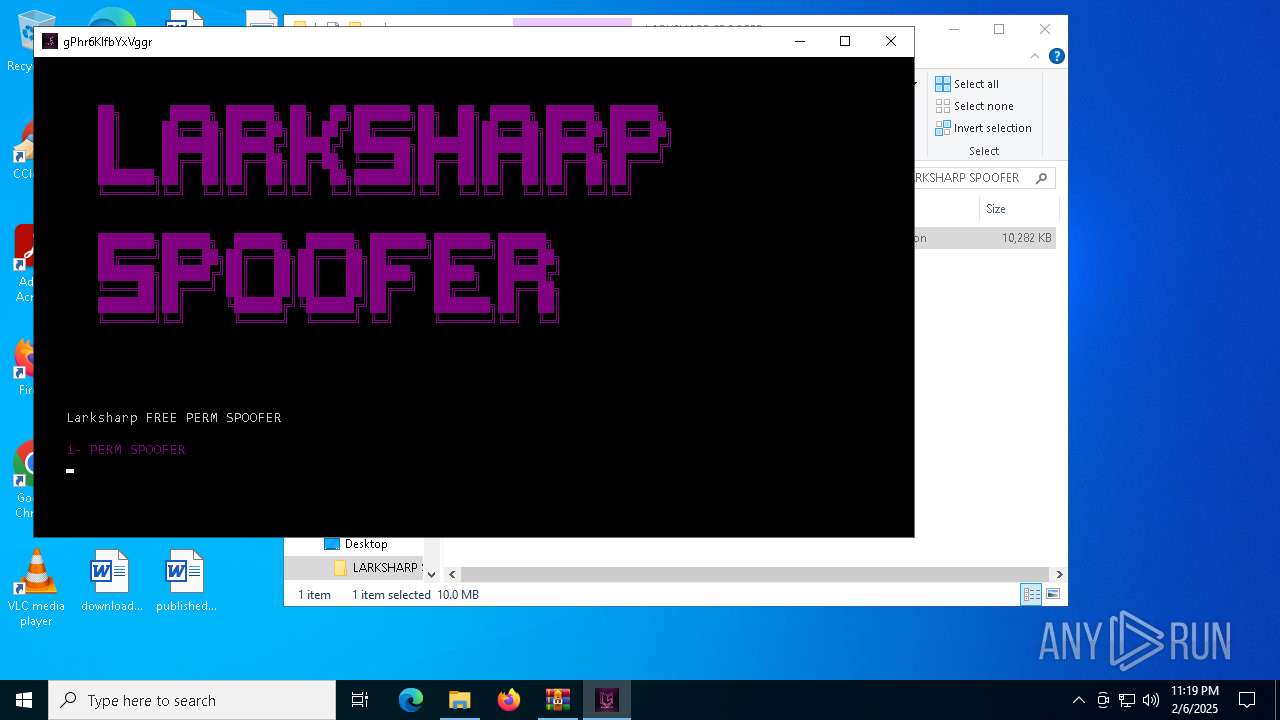
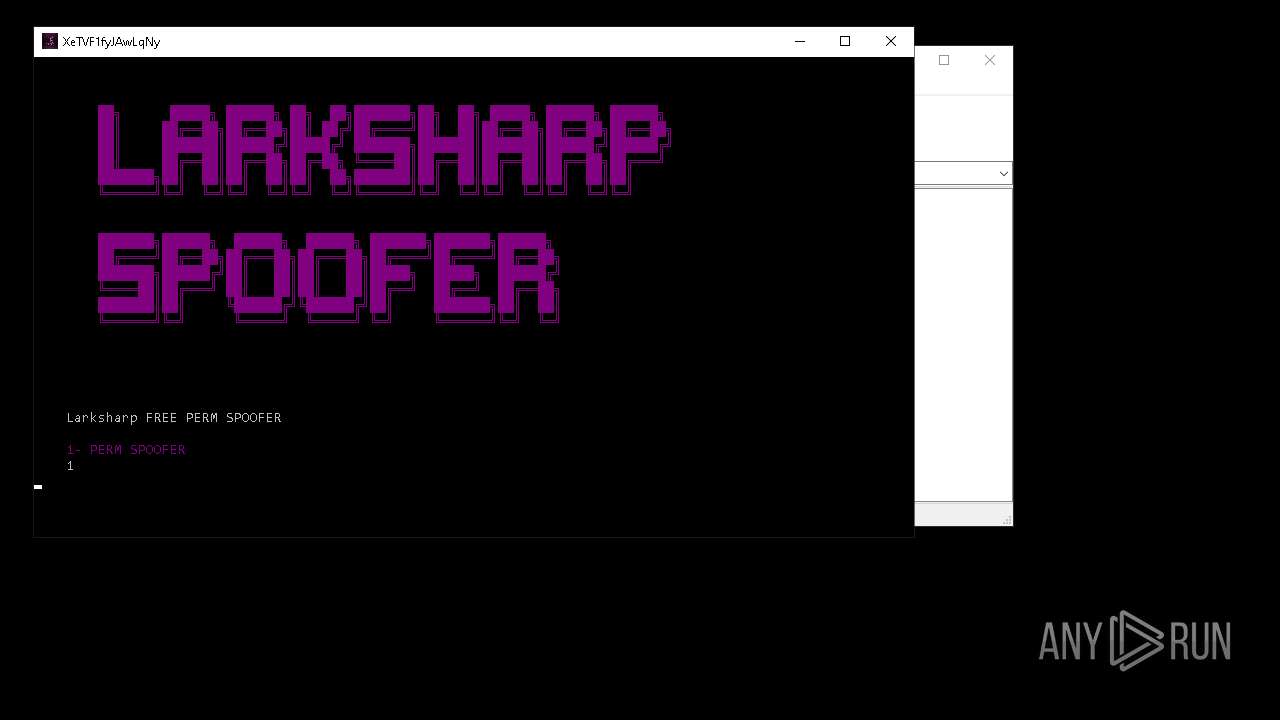
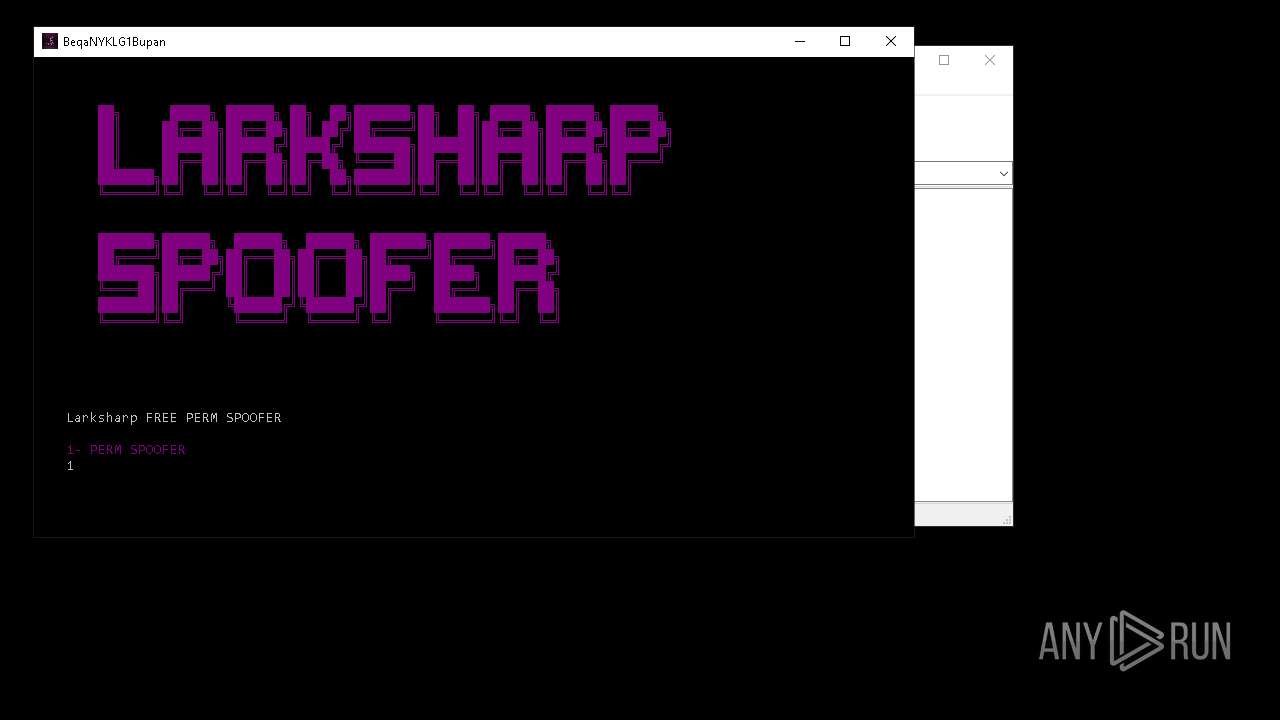
| File name: | LARKSHARP SPOOFER.zip |
| Full analysis: | https://app.any.run/tasks/f43da023-4806-417a-ba0c-6a5a2a5b24b7 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | February 06, 2025, 23:19:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 5E5A8A54FC1283A440CE9D35DF48551D |
| SHA1: | 2EBCE3A9C9F3A514F7F35E180400E7AB4DC12EDC |
| SHA256: | 47F42570C1328798A903A976412A5D004FA38CA514F7262CD2FD3F80F55D02DA |
| SSDEEP: | 98304:oxZ5IVvggs2lCJL3KK6NC6/lmNVD0Z9Nu6HYWFV5kAwtL7ex00CQVXe5plC964U5:EbZIDf89VLE4iF85yfepv |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6732)
Starts CertUtil for downloading files
- wscript.exe (PID: 4204)
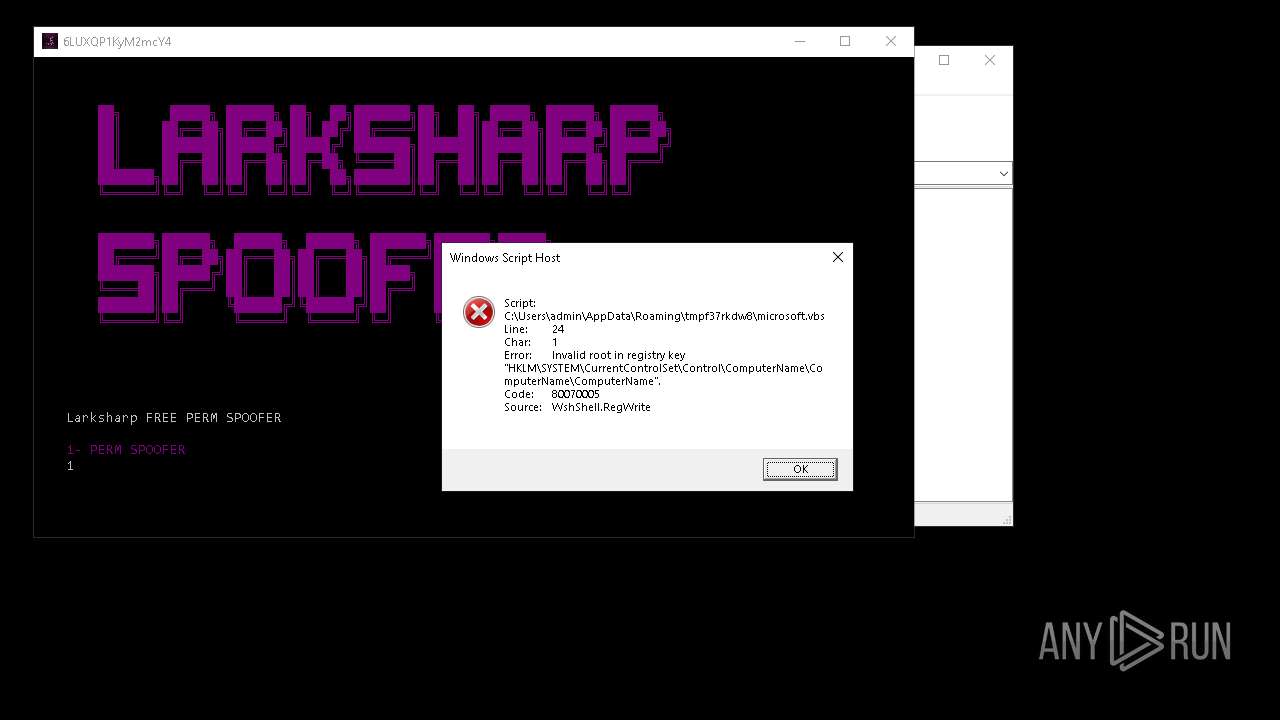
Creates a new registry key or changes the value of an existing one (SCRIPT)
- wscript.exe (PID: 6668)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6732)
Process drops legitimate windows executable
- LARKSHARP SPOOFER.exe (PID: 1864)
- randomizer.exe (PID: 5872)
Drops a system driver (possible attempt to evade defenses)
- LARKSHARP SPOOFER.exe (PID: 1864)
- LARKSHARP SPOOFER.exe (PID: 2800)
Process drops python dynamic module
- LARKSHARP SPOOFER.exe (PID: 1864)
- randomizer.exe (PID: 5872)
Application launched itself
- LARKSHARP SPOOFER.exe (PID: 1864)
- randomizer.exe (PID: 5872)
- cmd.exe (PID: 4244)
- cmd.exe (PID: 6208)
The process drops C-runtime libraries
- LARKSHARP SPOOFER.exe (PID: 1864)
- randomizer.exe (PID: 5872)
Executable content was dropped or overwritten
- LARKSHARP SPOOFER.exe (PID: 1864)
- LARKSHARP SPOOFER.exe (PID: 2800)
- randomizer.exe (PID: 5872)
Starts CMD.EXE for commands execution
- LARKSHARP SPOOFER.exe (PID: 2800)
- cmd.exe (PID: 4244)
- mac.exe (PID: 5328)
- mac.exe (PID: 4400)
- mac.exe (PID: 4300)
- mac.exe (PID: 6032)
- cmd.exe (PID: 6208)
- mac.exe (PID: 3288)
Loads Python modules
- LARKSHARP SPOOFER.exe (PID: 2800)
- randomizer.exe (PID: 5028)
Uses TASKKILL.EXE to kill process
- LARKSHARP SPOOFER.exe (PID: 2800)
Hides command output
- cmd.exe (PID: 4244)
- cmd.exe (PID: 520)
- cmd.exe (PID: 6340)
- cmd.exe (PID: 4116)
- cmd.exe (PID: 4840)
- cmd.exe (PID: 3508)
- cmd.exe (PID: 5732)
- cmd.exe (PID: 5472)
- cmd.exe (PID: 7076)
- cmd.exe (PID: 68)
- cmd.exe (PID: 7116)
- reg.exe (PID: 6076)
- reg.exe (PID: 6428)
- reg.exe (PID: 4792)
- cmd.exe (PID: 6208)
- cmd.exe (PID: 5792)
- reg.exe (PID: 1228)
- ipconfig.exe (PID: 6240)
- ipconfig.exe (PID: 5080)
- ipconfig.exe (PID: 4320)
- ipconfig.exe (PID: 4624)
- reg.exe (PID: 5284)
- reg.exe (PID: 2144)
The executable file from the user directory is run by the CMD process
- AMIDEWINx64.EXE (PID: 2672)
- AMIDEWINx64.EXE (PID: 5244)
- AMIDEWINx64.EXE (PID: 5712)
- AMIDEWINx64.EXE (PID: 6148)
- AMIDEWINx64.EXE (PID: 4320)
- AMIDEWINx64.EXE (PID: 3560)
- AMIDEWINx64.EXE (PID: 6448)
- AMIDEWINx64.EXE (PID: 1740)
- AMIDEWINx64.EXE (PID: 6176)
- AMIDEWINx64.EXE (PID: 6892)
- AMIDEWINx64.EXE (PID: 6916)
- AMIDEWINx64.EXE (PID: 6676)
- AMIDEWINx64.EXE (PID: 7144)
- AMIDEWINx64.EXE (PID: 7068)
- AMIDEWINx64.EXE (PID: 7152)
- AMIDEWINx64.EXE (PID: 7164)
- AMIDEWINx64.EXE (PID: 7084)
- AMIDEWINx64.EXE (PID: 4864)
- AMIDEWINx64.EXE (PID: 4328)
- AMIDEWINx64.EXE (PID: 4516)
- AMIDEWINx64.EXE (PID: 3640)
- AMIDEWINx64.EXE (PID: 628)
- AMIDEWINx64.EXE (PID: 2132)
- AMIDEWINx64.EXE (PID: 6296)
- AMIDEWINx64.EXE (PID: 5432)
- AMIDEWINx64.EXE (PID: 968)
- AMIDEWINx64.EXE (PID: 6264)
- AMIDEWINx64.EXE (PID: 1620)
- AMIDEWINx64.EXE (PID: 6220)
- AMIDEWINx64.EXE (PID: 6424)
- AMIDEWINx64.EXE (PID: 2828)
- AMIDEWINx64.EXE (PID: 5000)
- AMIDEWINx64.EXE (PID: 6384)
- AMIDEWINx64.EXE (PID: 6380)
- AMIDEWINx64.EXE (PID: 4968)
- AMIDEWINx64.EXE (PID: 4932)
- AMIDEWINx64.EXE (PID: 4632)
- AMIDEWINx64.EXE (PID: 4832)
- AMIDEWINx64.EXE (PID: 4856)
- AMIDEWINx64.EXE (PID: 4636)
- AMIDEWINx64.EXE (PID: 5912)
- volumeid.exe (PID: 1328)
Executing commands from a ".bat" file
- cmd.exe (PID: 4244)
- LARKSHARP SPOOFER.exe (PID: 2800)
Uses WMIC.EXE
- cmd.exe (PID: 4116)
- cmd.exe (PID: 3508)
- cmd.exe (PID: 4840)
- cmd.exe (PID: 5732)
- cmd.exe (PID: 6340)
- cmd.exe (PID: 7076)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 5472)
- cmd.exe (PID: 5792)
- cmd.exe (PID: 68)
The process executes VB scripts
- cmd.exe (PID: 3364)
- cmd.exe (PID: 776)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 4204)
Uses REG/REGEDIT.EXE to modify registry
- wscript.exe (PID: 4204)
Suspicious use of NETSH.EXE
- wscript.exe (PID: 4204)
Process uses IPCONFIG to renew DHCP configuration
- wscript.exe (PID: 4204)
Process uses IPCONFIG to get network configuration information
- wscript.exe (PID: 4204)
Process uses IPCONFIG to discard the IP address configuration
- wscript.exe (PID: 4204)
Process uses IPCONFIG to clear DNS cache
- wscript.exe (PID: 4204)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4204)
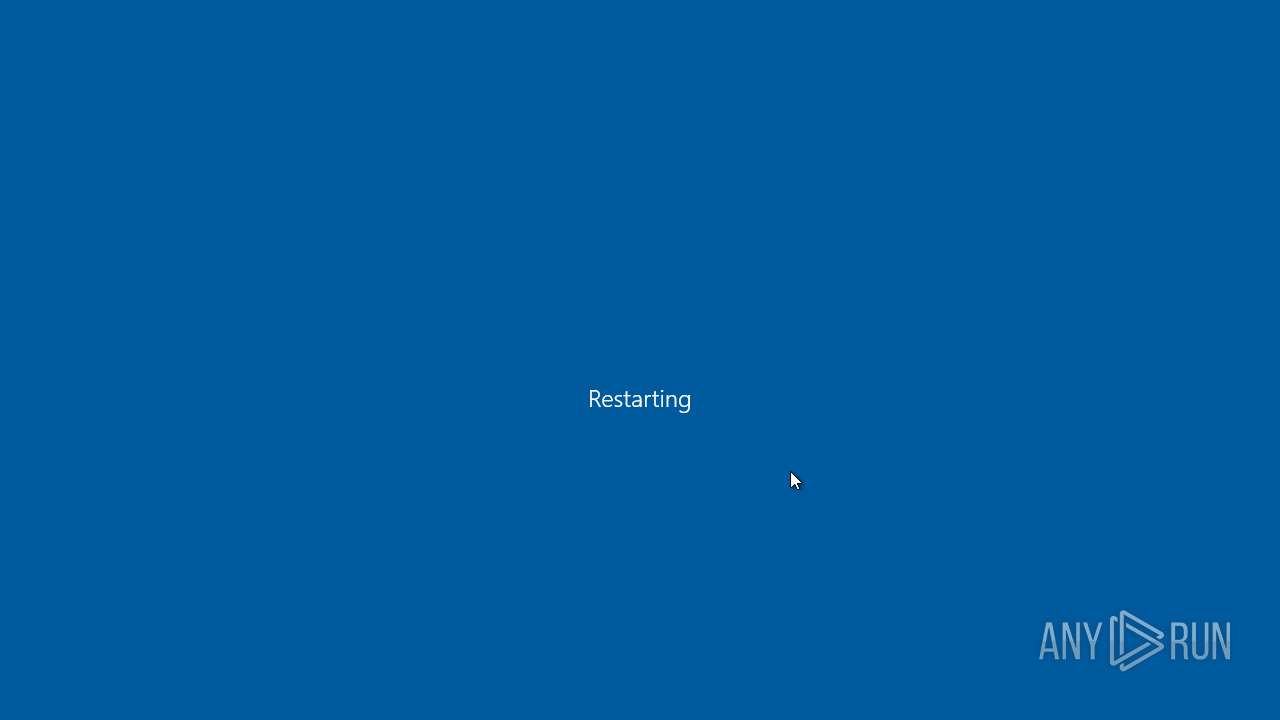
The system shut down or reboot
- LARKSHARP SPOOFER.exe (PID: 2800)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6732)
The sample compiled with english language support
- LARKSHARP SPOOFER.exe (PID: 1864)
- randomizer.exe (PID: 5872)
- LARKSHARP SPOOFER.exe (PID: 2800)
Checks supported languages
- LARKSHARP SPOOFER.exe (PID: 2800)
- LARKSHARP SPOOFER.exe (PID: 1864)
- mode.com (PID: 5728)
- randomizer.exe (PID: 5872)
- randomizer.exe (PID: 5028)
- AMIDEWINx64.EXE (PID: 2672)
- AMIDEWINx64.EXE (PID: 5244)
- AMIDEWINx64.EXE (PID: 5712)
- AMIDEWINx64.EXE (PID: 4320)
- AMIDEWINx64.EXE (PID: 6148)
- AMIDEWINx64.EXE (PID: 3560)
- AMIDEWINx64.EXE (PID: 1740)
- AMIDEWINx64.EXE (PID: 6892)
- AMIDEWINx64.EXE (PID: 6176)
- AMIDEWINx64.EXE (PID: 6916)
- AMIDEWINx64.EXE (PID: 6676)
- AMIDEWINx64.EXE (PID: 6448)
- AMIDEWINx64.EXE (PID: 7084)
- AMIDEWINx64.EXE (PID: 7152)
- AMIDEWINx64.EXE (PID: 7144)
- AMIDEWINx64.EXE (PID: 7068)
- AMIDEWINx64.EXE (PID: 7164)
- AMIDEWINx64.EXE (PID: 4864)
- AMIDEWINx64.EXE (PID: 628)
- AMIDEWINx64.EXE (PID: 4328)
- AMIDEWINx64.EXE (PID: 4516)
- AMIDEWINx64.EXE (PID: 2132)
- AMIDEWINx64.EXE (PID: 3640)
- AMIDEWINx64.EXE (PID: 6296)
- AMIDEWINx64.EXE (PID: 4932)
- AMIDEWINx64.EXE (PID: 5432)
- AMIDEWINx64.EXE (PID: 968)
- AMIDEWINx64.EXE (PID: 6264)
- AMIDEWINx64.EXE (PID: 1620)
- AMIDEWINx64.EXE (PID: 6220)
- AMIDEWINx64.EXE (PID: 6424)
- AMIDEWINx64.EXE (PID: 2828)
- AMIDEWINx64.EXE (PID: 5000)
- AMIDEWINx64.EXE (PID: 6384)
- AMIDEWINx64.EXE (PID: 6380)
- AMIDEWINx64.EXE (PID: 4968)
- AMIDEWINx64.EXE (PID: 5912)
- AMIDEWINx64.EXE (PID: 4632)
- AMIDEWINx64.EXE (PID: 4832)
- AMIDEWINx64.EXE (PID: 4856)
- AMIDEWINx64.EXE (PID: 4636)
- mac.exe (PID: 5328)
- mac.exe (PID: 4400)
- mac.exe (PID: 4300)
- mac.exe (PID: 6032)
- mac.exe (PID: 3288)
- volumeid.exe (PID: 1328)
Manual execution by a user
- LARKSHARP SPOOFER.exe (PID: 1864)
Reads the computer name
- LARKSHARP SPOOFER.exe (PID: 1864)
- randomizer.exe (PID: 5872)
- AMIDEWINx64.EXE (PID: 5712)
- AMIDEWINx64.EXE (PID: 4320)
- AMIDEWINx64.EXE (PID: 2672)
- AMIDEWINx64.EXE (PID: 5244)
- AMIDEWINx64.EXE (PID: 6148)
- AMIDEWINx64.EXE (PID: 3560)
- AMIDEWINx64.EXE (PID: 1740)
- AMIDEWINx64.EXE (PID: 6448)
- AMIDEWINx64.EXE (PID: 6176)
- AMIDEWINx64.EXE (PID: 6892)
- AMIDEWINx64.EXE (PID: 6916)
- AMIDEWINx64.EXE (PID: 6676)
- AMIDEWINx64.EXE (PID: 7144)
- AMIDEWINx64.EXE (PID: 7068)
- AMIDEWINx64.EXE (PID: 7152)
- AMIDEWINx64.EXE (PID: 7164)
- AMIDEWINx64.EXE (PID: 7084)
- AMIDEWINx64.EXE (PID: 4864)
- AMIDEWINx64.EXE (PID: 4328)
- AMIDEWINx64.EXE (PID: 2132)
- AMIDEWINx64.EXE (PID: 4516)
- AMIDEWINx64.EXE (PID: 3640)
- AMIDEWINx64.EXE (PID: 628)
- AMIDEWINx64.EXE (PID: 6296)
- AMIDEWINx64.EXE (PID: 5432)
- AMIDEWINx64.EXE (PID: 968)
- AMIDEWINx64.EXE (PID: 6264)
- AMIDEWINx64.EXE (PID: 1620)
- AMIDEWINx64.EXE (PID: 6220)
- AMIDEWINx64.EXE (PID: 6424)
- AMIDEWINx64.EXE (PID: 2828)
- AMIDEWINx64.EXE (PID: 6384)
- AMIDEWINx64.EXE (PID: 5000)
- AMIDEWINx64.EXE (PID: 6380)
- AMIDEWINx64.EXE (PID: 4932)
- AMIDEWINx64.EXE (PID: 4968)
- AMIDEWINx64.EXE (PID: 5912)
- AMIDEWINx64.EXE (PID: 4832)
- AMIDEWINx64.EXE (PID: 4632)
- AMIDEWINx64.EXE (PID: 4636)
- AMIDEWINx64.EXE (PID: 4856)
Create files in a temporary directory
- LARKSHARP SPOOFER.exe (PID: 1864)
- randomizer.exe (PID: 5872)
- LARKSHARP SPOOFER.exe (PID: 2800)
Reads the machine GUID from the registry
- LARKSHARP SPOOFER.exe (PID: 2800)
- randomizer.exe (PID: 5028)
Starts MODE.COM to configure console settings
- mode.com (PID: 5728)
Creates files or folders in the user directory
- LARKSHARP SPOOFER.exe (PID: 2800)
PyInstaller has been detected (YARA)
- LARKSHARP SPOOFER.exe (PID: 1864)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 716)
- WMIC.exe (PID: 4896)
- WMIC.exe (PID: 3744)
- WMIC.exe (PID: 6608)
- WMIC.exe (PID: 5712)
- WMIC.exe (PID: 644)
- WMIC.exe (PID: 6944)
- WMIC.exe (PID: 6688)
- WMIC.exe (PID: 3884)
- WMIC.exe (PID: 4500)
- certutil.exe (PID: 5044)
Disables trace logs
- netsh.exe (PID: 4144)
- netsh.exe (PID: 716)
- netsh.exe (PID: 3632)
- netsh.exe (PID: 4592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:10:11 09:49:10 |
| ZipCRC: | 0x0a6cdeac |
| ZipCompressedSize: | 10370472 |
| ZipUncompressedSize: | 10528569 |
| ZipFileName: | LARKSHARP SPOOFER.exe |
Total processes
292
Monitored processes
172
Malicious processes
7
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | C:\WINDOWS\system32\cmd.exe /c WMIC PATH WIN32_NETWORKADAPTER WHERE PHYSICALADAPTER=TRUE CALL DISABLE >nul 2>&1 | C:\Windows\System32\cmd.exe | — | mac.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | "C:\Windows\System32\reg.exe" ADD HKLM\System\CurrentControlSet\Control\SystemInformation /v ComputerHardwareId /t REG_SZ /d 42178 /f | C:\Windows\System32\reg.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 520 | cmd.exe /c "C:\Users\admin\AppData\Roaming\tmpf37rkdw8\spoof.bat >nul 2>&1" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 16 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | AMIDEWINx64.EXE /BSH 3 WfPdcwlkyHBoGqW | C:\Users\admin\AppData\Roaming\tmpf37rkdw8\AMIDEWINx64.EXE | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 16 Modules
| |||||||||||||||
| 644 | WMIC PATH WIN32_NETWORKADAPTER WHERE PHYSICALADAPTER=TRUE CALL ENABLE | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 716 | WMIC PATH WIN32_NETWORKADAPTER WHERE PHYSICALADAPTER=TRUE CALL DISABLE | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 631
Read events
9 587
Write events
26
Delete events
18
Modification events
| (PID) Process: | (6732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\LARKSHARP SPOOFER.zip | |||
| (PID) Process: | (6732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
36
Suspicious files
2
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1864 | LARKSHARP SPOOFER.exe | C:\Users\admin\AppData\Local\Temp\_MEI18642\VCRUNTIME140_1.dll | executable | |
MD5:9CFF894542DC399E0A46DEE017331EDF | SHA256:B1D3B6B3CDEB5B7B8187767CD86100B76233E7BBB9ACF56C64F8288F34B269CA | |||
| 1864 | LARKSHARP SPOOFER.exe | C:\Users\admin\AppData\Local\Temp\_MEI18642\_bz2.pyd | executable | |
MD5:A49C5F406456B79254EB65D015B81088 | SHA256:CE4EF8ED1E72C1D3A6082D500A17A009EB6E8ED15022BF3B68A22291858FECED | |||
| 1864 | LARKSHARP SPOOFER.exe | C:\Users\admin\AppData\Local\Temp\_MEI18642\libcrypto-1_1.dll | executable | |
MD5:89511DF61678BEFA2F62F5025C8C8448 | SHA256:296426E7CE11BC3D1CFA9F2AEB42F60C974DA4AF3B3EFBEB0BA40E92E5299FDF | |||
| 1864 | LARKSHARP SPOOFER.exe | C:\Users\admin\AppData\Local\Temp\_MEI18642\MSVCP140.dll | executable | |
MD5:72F3D84384E888BF0D38852EB863026B | SHA256:A4C2229BDC2A2A630ACDC095B4D86008E5C3E3BC7773174354F3DA4F5BEB9CDE | |||
| 1864 | LARKSHARP SPOOFER.exe | C:\Users\admin\AppData\Local\Temp\_MEI18642\_socket.pyd | executable | |
MD5:4827652DE133C83FA1CAE839B361856C | SHA256:87832A3B89E2ADA8F704A8F066013660D591D9CE01CE901CC57A3B973F0858BA | |||
| 1864 | LARKSHARP SPOOFER.exe | C:\Users\admin\AppData\Local\Temp\_MEI18642\amifldrv64.sys | executable | |
MD5:785045F8B25CD2E937DDC6B09DEBE01A | SHA256:37073E42FFA0322500F90CD7E3C8D02C4CDD695D31C77E81560ABEC20BFB68BA | |||
| 1864 | LARKSHARP SPOOFER.exe | C:\Users\admin\AppData\Local\Temp\_MEI18642\_ctypes.pyd | executable | |
MD5:291A0A9B63BAE00A4222A6DF71A22023 | SHA256:820E840759EED12E19F3C485FD819B065B49D9DC704AE3599A63077416D63324 | |||
| 1864 | LARKSHARP SPOOFER.exe | C:\Users\admin\AppData\Local\Temp\_MEI18642\_hashlib.pyd | executable | |
MD5:5E5AF52F42EAF007E3AC73FD2211F048 | SHA256:A30CF1A40E0B09610E34BE187F1396AC5A44DCFB27BC7FF9B450D1318B694C1B | |||
| 1864 | LARKSHARP SPOOFER.exe | C:\Users\admin\AppData\Local\Temp\_MEI18642\libffi-7.dll | executable | |
MD5:EEF7981412BE8EA459064D3090F4B3AA | SHA256:F60DD9F2FCBD495674DFC1555EFFB710EB081FC7D4CAE5FA58C438AB50405081 | |||
| 1864 | LARKSHARP SPOOFER.exe | C:\Users\admin\AppData\Local\Temp\_MEI18642\microsoft.vbs | text | |
MD5:AF1905DC8BD39D2D407F12FB08272BEB | SHA256:BB113A896A43CB1B03A8B57A85E8D46FAF39FE4AE4AF97581B264415EF32BD3B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
24
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6504 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6268 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6268 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
448 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6504 | backgroundTaskHost.exe | 20.223.36.55:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6504 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6268 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |