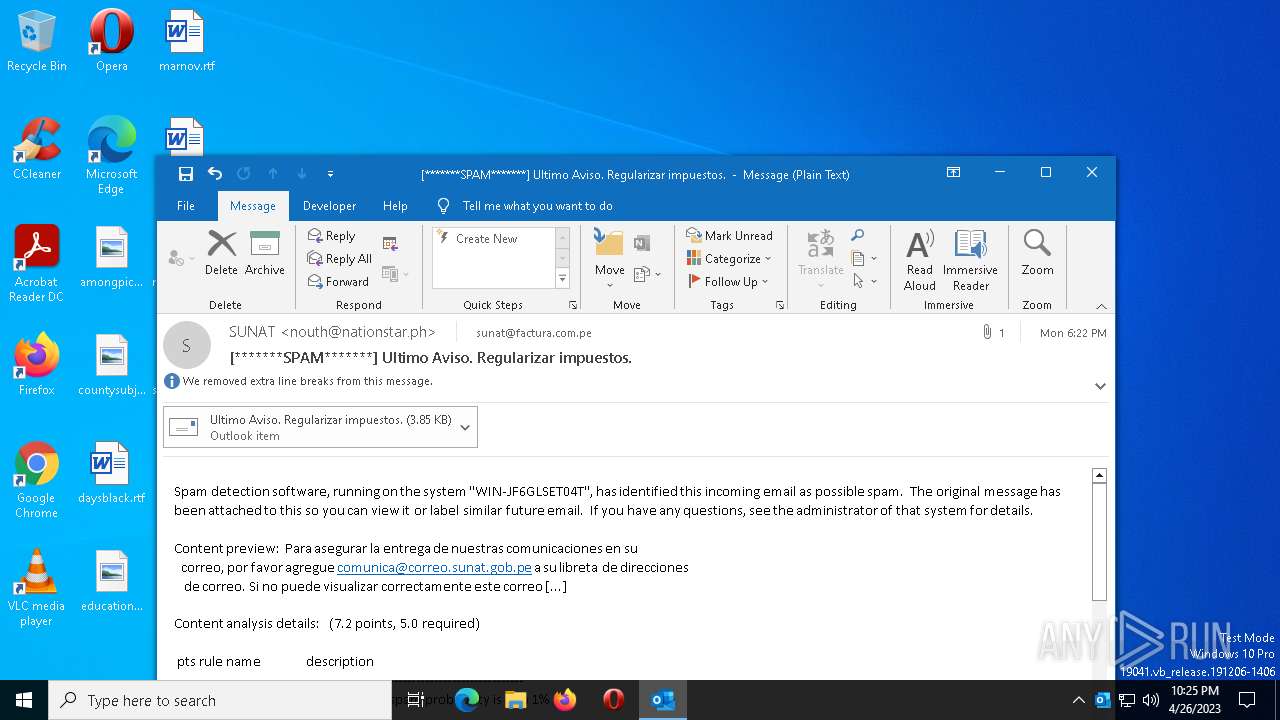
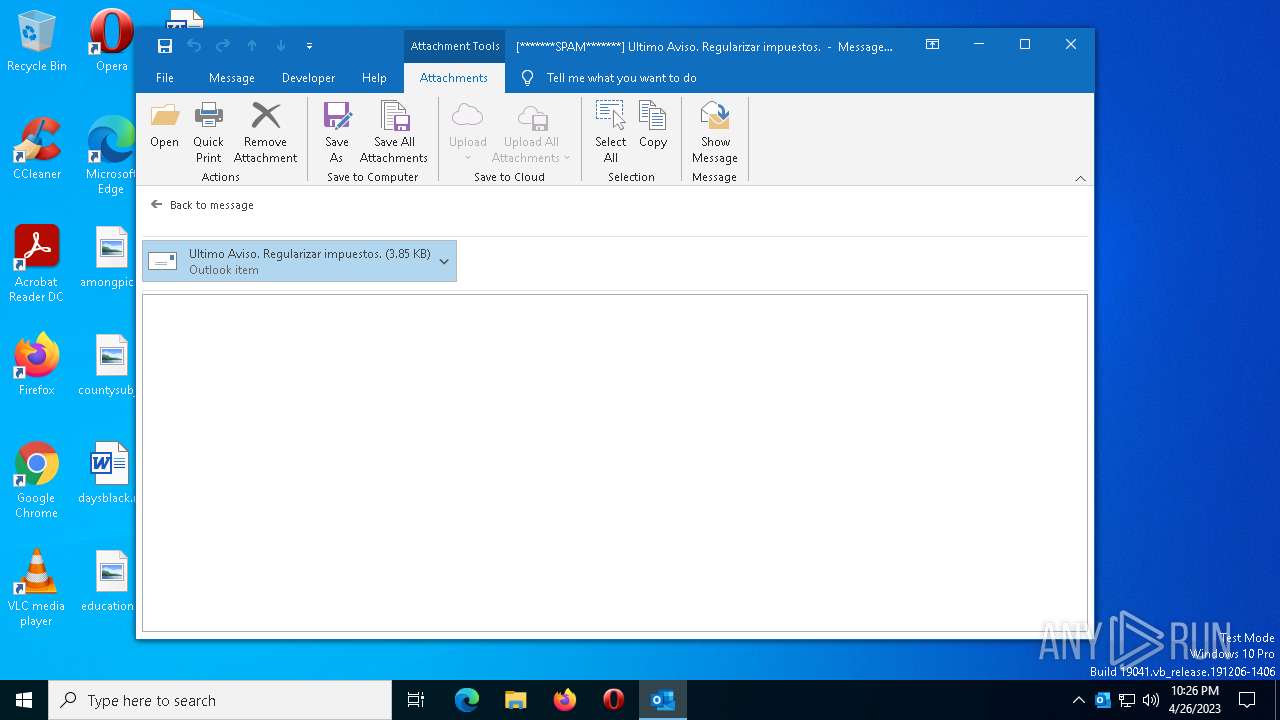
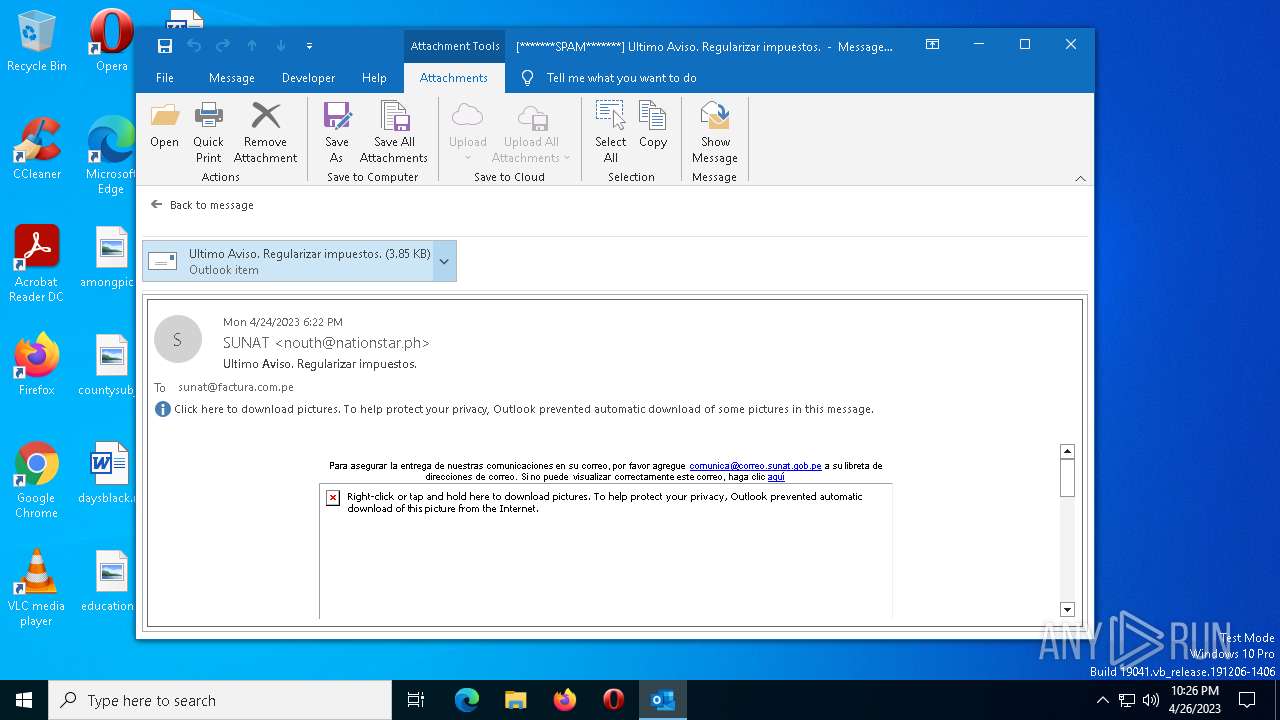
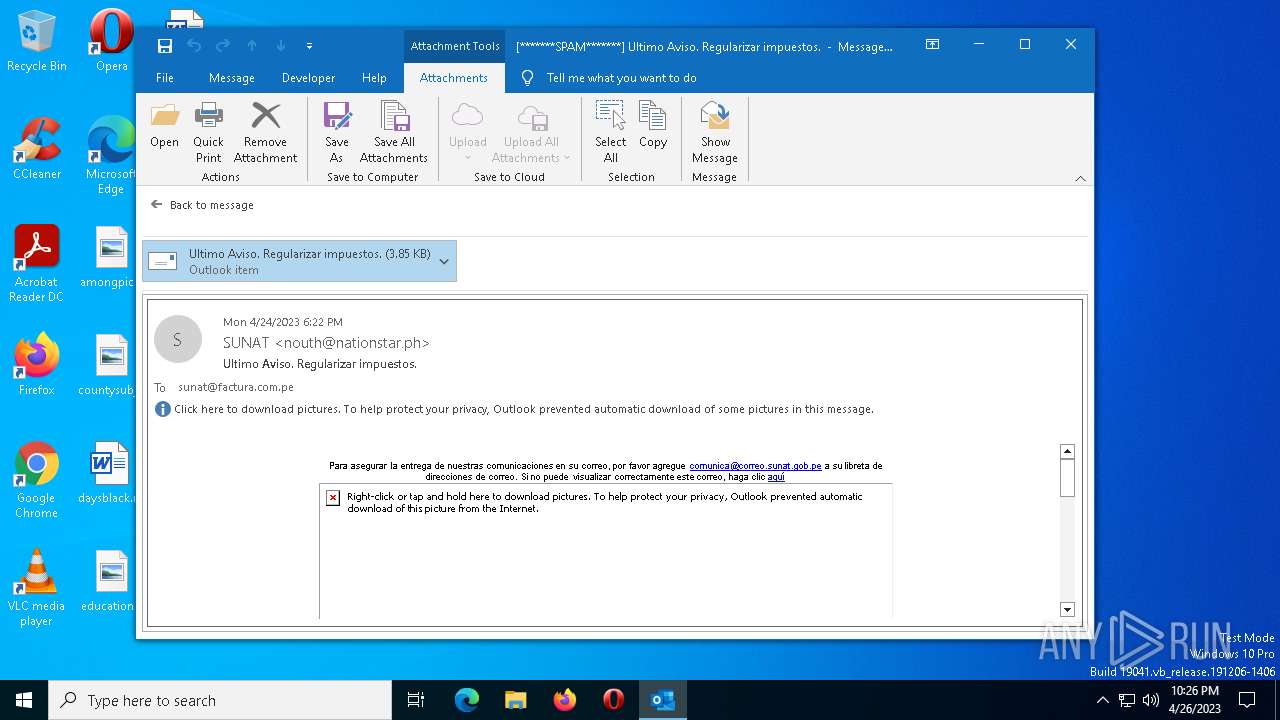
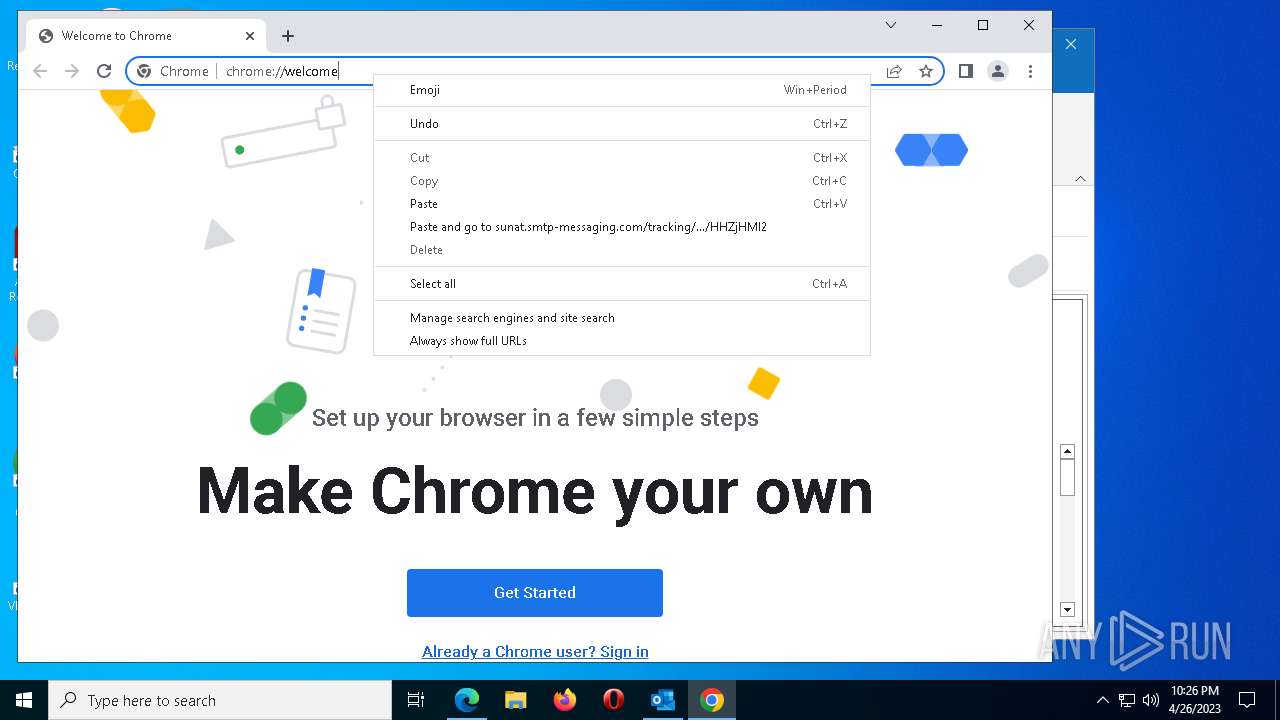
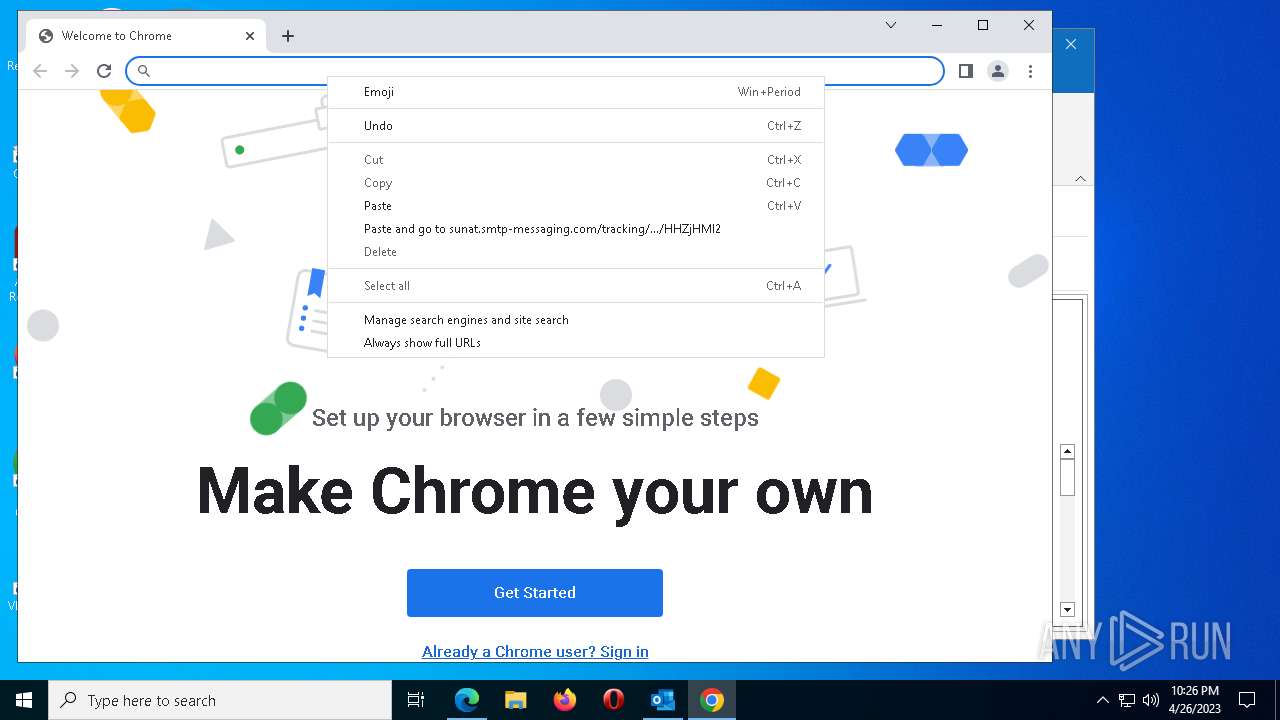
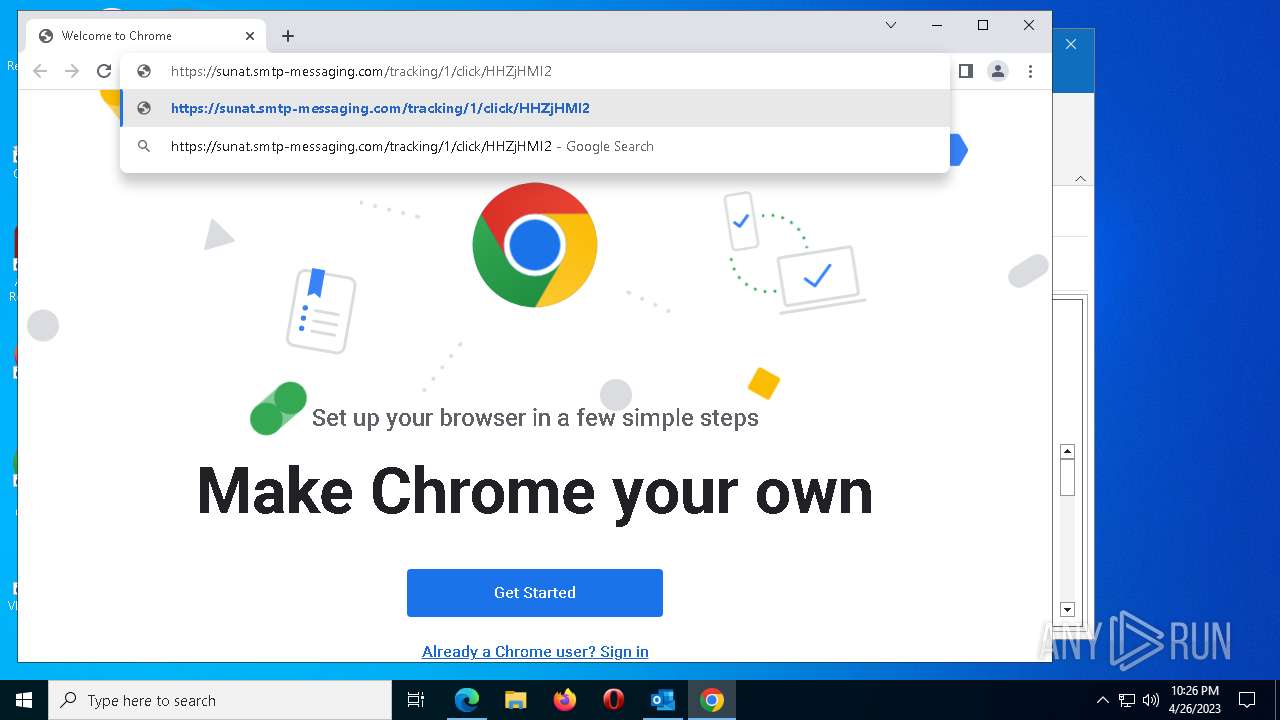
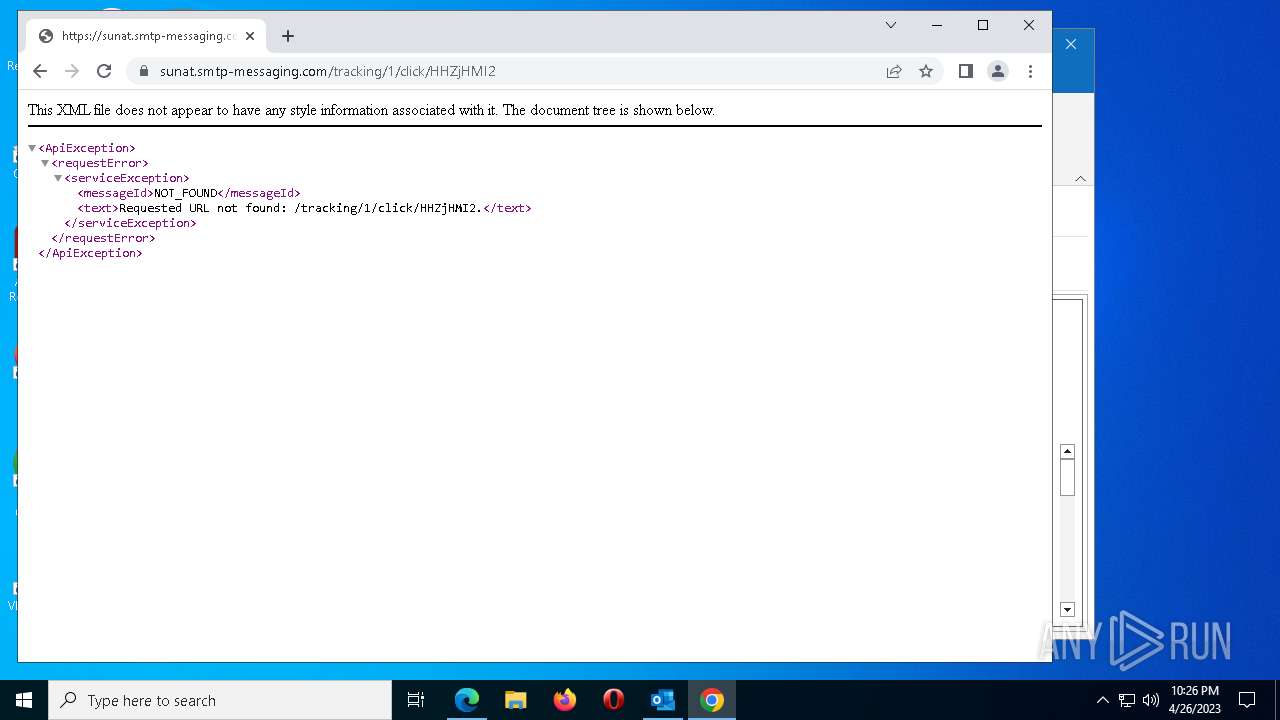
| File name: | 1682360557-1625ab24bf0cc40001-yr3sSN.eml |
| Full analysis: | https://app.any.run/tasks/5e4bce09-d140-4e45-944b-0b4947d2f355 |
| Verdict: | Malicious activity |
| Analysis date: | April 26, 2023, 22:25:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
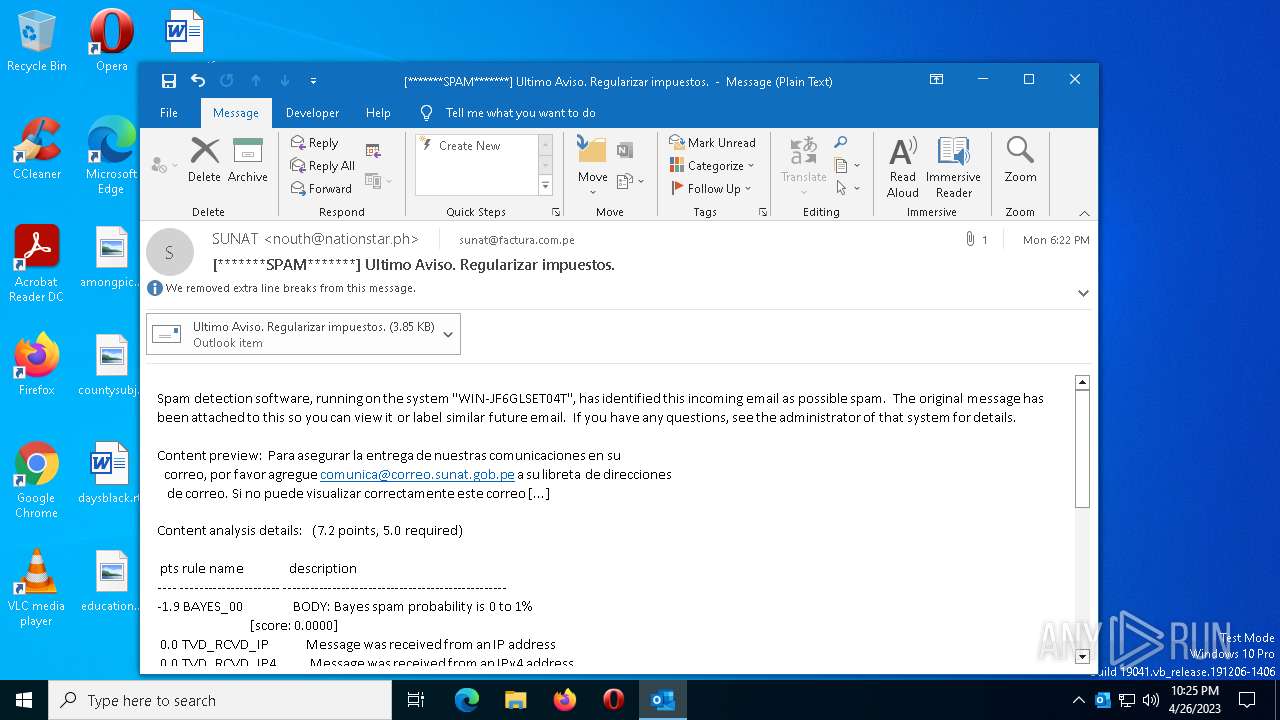
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 12CB08F3A2E2C6D8CA13CAD44878CFDB |
| SHA1: | D1BCA1A16561D01D4D0DCBE5ED79907D42C08D6A |
| SHA256: | 47F2A9AEAD275E205B0A713DB95939F6AF0CC7D68F4D1650CCFCD078C168CC07 |
| SSDEEP: | 192:VhBz4n67uwBtSCIQVihWPBFosf4yLiq7ofKiPTPQ4Ky8ADpIQSw6Q2Z:b5HuwBt3oWZZfbeuofKidIv |
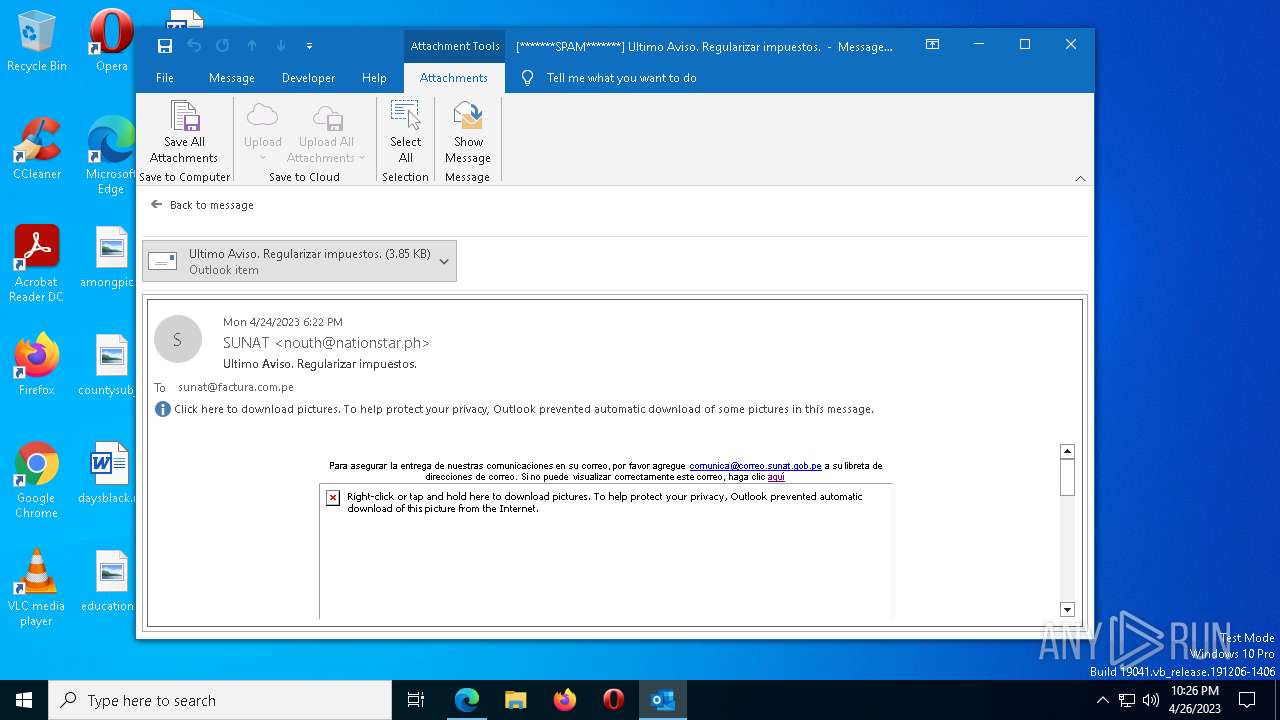
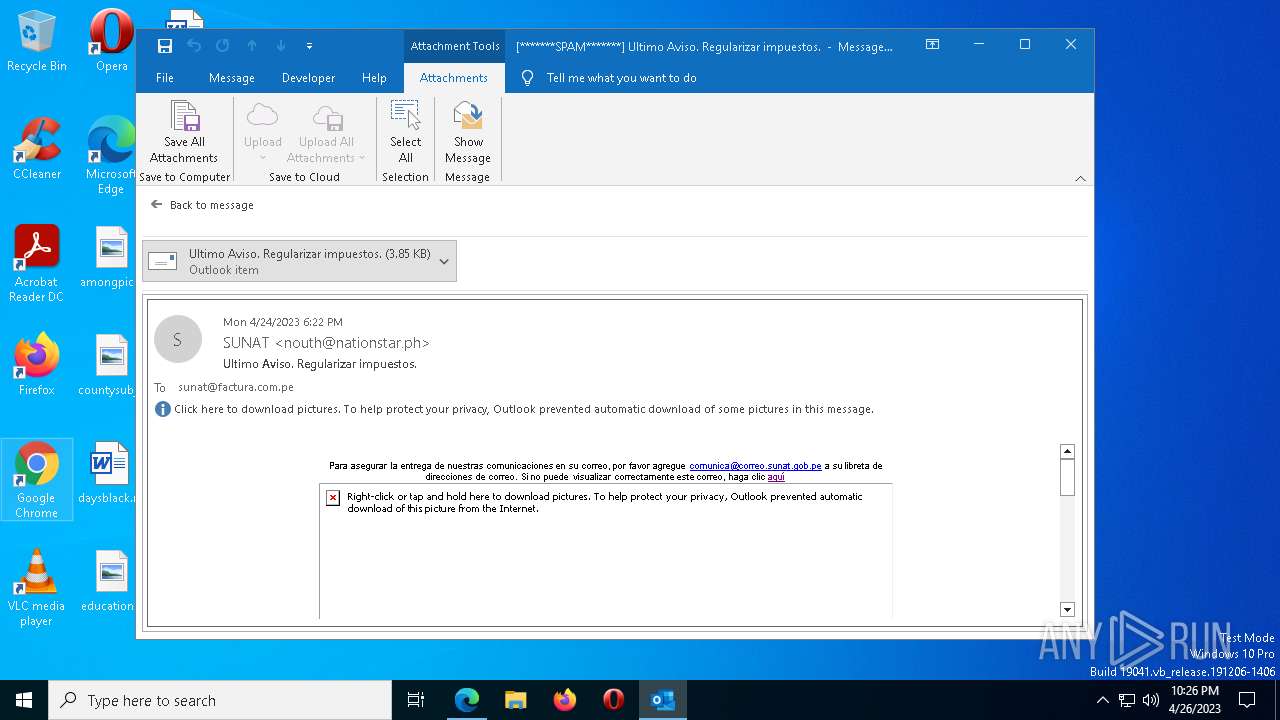
MALICIOUS
Unusual execution from MS Office
- OUTLOOK.EXE (PID: 6324)
Application was injected by another process
- msedge.exe (PID: 7988)
Runs injected code in another process
- SystemSettings.exe (PID: 6100)
SUSPICIOUS
Executes as Windows Service
- elevation_service.exe (PID: 7460)
- elevation_service.exe (PID: 3748)
Executable content was dropped or overwritten
- elevation_service.exe (PID: 3748)
Reads settings of System Certificates
- ChromeRecovery.exe (PID: 7836)
- SystemSettings.exe (PID: 6100)
INFO
Reads product name
- OUTLOOK.EXE (PID: 6324)
Reads the computer name
- ai.exe (PID: 6228)
- identity_helper.exe (PID: 1260)
- elevation_service.exe (PID: 7460)
- elevation_service.exe (PID: 3748)
- ChromeRecovery.exe (PID: 7836)
- SystemSettings.exe (PID: 6100)
Manual execution by a user
- chrome.exe (PID: 6392)
Application launched itself
- chrome.exe (PID: 6392)
- msedge.exe (PID: 6432)
- chrmstp.exe (PID: 7880)
- chrmstp.exe (PID: 7604)
Checks supported languages
- ai.exe (PID: 6228)
- identity_helper.exe (PID: 1260)
- elevation_service.exe (PID: 7460)
- elevation_service.exe (PID: 3748)
- ChromeRecovery.exe (PID: 7836)
- SystemSettings.exe (PID: 6100)
Reads Microsoft Office registry keys
- ai.exe (PID: 6228)
The process checks LSA protection
- ai.exe (PID: 6228)
- slui.exe (PID: 3980)
- identity_helper.exe (PID: 1260)
- elevation_service.exe (PID: 7460)
- elevation_service.exe (PID: 3748)
- ChromeRecovery.exe (PID: 7836)
- SystemSettings.exe (PID: 6100)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 6324)
- chrome.exe (PID: 3380)
- chrome.exe (PID: 1728)
- chrome.exe (PID: 7288)
- chrome.exe (PID: 1444)
- chrome.exe (PID: 7500)
Checks proxy server information
- slui.exe (PID: 3980)
Creates files in the program directory
- elevation_service.exe (PID: 3748)
Reads the software policy settings
- slui.exe (PID: 3980)
Create files in a temporary directory
- msedge.exe (PID: 6432)
- chrome.exe (PID: 6392)
Process checks computer location settings
- SystemSettings.exe (PID: 6100)
Executable content was dropped or overwritten
- chrome.exe (PID: 6824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 3) (100) |
|---|
Total processes
247
Monitored processes
95
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3512 --field-trial-handle=1872,i,13730186961534441280,12143492753837809134,131072 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 540 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4580 --field-trial-handle=1872,i,13730186961534441280,12143492753837809134,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 716 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=46 --mojo-platform-channel-handle=5988 --field-trial-handle=1932,i,11199055603070791984,1691863515237707043,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1260 | "C:\Program Files (x86)\Microsoft\Edge\Application\111.0.1661.62\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=5916 --field-trial-handle=1872,i,13730186961534441280,12143492753837809134,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\111.0.1661.62\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 1444 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1720 --field-trial-handle=1932,i,11199055603070791984,1691863515237707043,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1504 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=6204 --field-trial-handle=1872,i,13730186961534441280,12143492753837809134,131072 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 1728 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3220 --field-trial-handle=1932,i,11199055603070791984,1691863515237707043,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=5108 --field-trial-handle=1932,i,11199055603070791984,1691863515237707043,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3436 --field-trial-handle=1932,i,11199055603070791984,1691863515237707043,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 2364 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=5200 --field-trial-handle=1932,i,11199055603070791984,1691863515237707043,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
Total events
68 758
Read events
67 890
Write events
524
Delete events
344
Modification events
| (PID) Process: | (6324) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 1 | |||
| (PID) Process: | (6324) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 1 | |||
| (PID) Process: | (6324) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 1 | |||
| (PID) Process: | (6324) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 1 | |||
| (PID) Process: | (6324) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 1 | |||
| (PID) Process: | (6324) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 1 | |||
| (PID) Process: | (6324) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 1 | |||
| (PID) Process: | (6324) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 1 | |||
| (PID) Process: | (6324) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ru-ru |
Value: 1 | |||
| (PID) Process: | (6324) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | tr-tr |
Value: 1 | |||
Executable files
21
Suspicious files
1 235
Text files
631
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6324 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6324 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:12459A1B71B0134A19DD20AD2B338CD5 | SHA256:6B81C285049869DD1E01A9D040F55FB15F3399B1677C4245C5181861132A8014 | |||
| 6324 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6324 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | binary | |
MD5:5BBFBC12F26E8535B02536724D44595E | SHA256:F18AB7EDBBE0E1905DD6FE3BD5C962940EFD93F24EA85859FBFBBE4709671CC6 | |||
| 6324 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | abr | |
MD5:53F81109FF6D257DA1285434BA7C8F1D | SHA256:B007134C69872DA6828BD3178F0C9641308323B9DE1F884622A409C1A135BD67 | |||
| 6324 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FORMS\FRMDATA64.DAT | binary | |
MD5:6D4DE3C5917BAA7B9B0C272974B2FD4E | SHA256:EA295E017CCCD7A740EE9B7BFED3CC7C0FBBE82C991C26C051F8B3F549AB2F14 | |||
| 6324 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_E503B048B745DFA14B81FCFC68D6DECE | binary | |
MD5:641AEF7631A316C9131F3C2AE2E9C580 | SHA256:4639FEEAAE49AD1E6DBC3A6E6DBE6458532DE2B2792A9EBCA4EF2A6F9F979B00 | |||
| 6432 | msedge.exe | C:\USERS\ADMIN\APPDATA\LOCAL\MICROSOFT\EDGE\USER DATA\CRASHPAD\SETTINGS.DAT | binary | |
MD5:712BA76045CAB7030E763B2928AC4396 | SHA256:B3738796F96BF942AA684BAFB516CAAAAE25203695B9013725A70197D973AA59 | |||
| 6324 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\OTele\outlook.exe.db-journal | binary | |
MD5:83BCB5DB9011D6AE06C13B457CE716E9 | SHA256:87DDB9DDDCC473717E76B2FE72FB9099742F7BFB5AAF3D63C1B870F3FEE33F41 | |||
| 6324 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\OTele\outlook.exe.db-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
83
TCP/UDP connections
148
DNS requests
148
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7768 | svchost.exe | HEAD | 200 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d6dac2cd-b55a-4a7d-aeb4-1cff97bb9dd4?P1=1683102445&P2=404&P3=2&P4=CTofZo4eGLaJSvKcRPlvVoA9QQABvfkDePZn0LkSm3tanzqhxHj%2fG6tCc%2fHOz9teQVtWpIJZ%2fz%2bYW9S6xWVhzw%3d%3d | US | — | — | whitelisted |
7768 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
1872 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | der | 418 b | whitelisted |
7768 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d6dac2cd-b55a-4a7d-aeb4-1cff97bb9dd4?P1=1683102445&P2=404&P3=2&P4=CTofZo4eGLaJSvKcRPlvVoA9QQABvfkDePZn0LkSm3tanzqhxHj%2fG6tCc%2fHOz9teQVtWpIJZ%2fz%2bYW9S6xWVhzw%3d%3d | US | binary | 40.5 Kb | whitelisted |
7768 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d6dac2cd-b55a-4a7d-aeb4-1cff97bb9dd4?P1=1683102445&P2=404&P3=2&P4=CTofZo4eGLaJSvKcRPlvVoA9QQABvfkDePZn0LkSm3tanzqhxHj%2fG6tCc%2fHOz9teQVtWpIJZ%2fz%2bYW9S6xWVhzw%3d%3d | US | binary | 1.68 Kb | whitelisted |
6324 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | US | der | 471 b | whitelisted |
6324 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
7768 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 1.30 Kb | whitelisted |
7768 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d6dac2cd-b55a-4a7d-aeb4-1cff97bb9dd4?P1=1683102445&P2=404&P3=2&P4=CTofZo4eGLaJSvKcRPlvVoA9QQABvfkDePZn0LkSm3tanzqhxHj%2fG6tCc%2fHOz9teQVtWpIJZ%2fz%2bYW9S6xWVhzw%3d%3d | US | binary | 784 Kb | whitelisted |
5780 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | crx | 242 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6324 | OUTLOOK.EXE | 51.105.71.136:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | suspicious |
5756 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6324 | OUTLOOK.EXE | 52.109.124.153:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | suspicious |
7004 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6324 | OUTLOOK.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
6324 | OUTLOOK.EXE | 52.109.76.225:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | suspicious |
6324 | OUTLOOK.EXE | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
5952 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1872 | SIHClient.exe | 20.3.187.198:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1872 | SIHClient.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
nleditor.osi.office.net |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |