| File name: | CSM_V2.0.0.2.exe |
| Full analysis: | https://app.any.run/tasks/86c31457-d137-4eb5-b359-7a3c21064443 |
| Verdict: | Malicious activity |
| Analysis date: | October 24, 2024, 14:16:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | 843F117B09AA29652143CEBE6E9A2926 |
| SHA1: | 2800F479A77C473C64672BBAFF14F82FDDC37EB0 |
| SHA256: | 47EB8F2611ABD35E0ECA6E76CAA2E5A1B359E64FE61A4894C4594B3DA36808C3 |
| SSDEEP: | 98304:I+QQmF4YZKSnzCL2kz+n8Z6rkDtuqqj2Dz5XclQ3MUiANMoK+hFQrzwpTEQSV6dg:9cSEFsVifVi6qW9bowT+f9YR |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- CSM_V2.0.0.2.exe (PID: 4072)
- CSM_V2.0.0.2.exe (PID: 6604)
- CSM_V2.0.0.2.exe (PID: 7396)
- CSM.exe (PID: 8112)
- CSM_V2.0.0.2.exe (PID: 7508)
- CSM_V2.0.0.2.tmp (PID: 7532)
- CSM.exe (PID: 7736)
- CSM_V2.0.0.2.tmp (PID: 5624)
Reads security settings of Internet Explorer
- CSM_V2.0.0.2.tmp (PID: 5832)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7568)
- cmd.exe (PID: 2708)
Starts CMD.EXE for commands execution
- CSM_V2.0.0.2.tmp (PID: 7532)
- CSM_V2.0.0.2.tmp (PID: 5624)
Drops a system driver (possible attempt to evade defenses)
- CSM.exe (PID: 8112)
- CSM.exe (PID: 7736)
Executes as Windows Service
- WmiApSrv.exe (PID: 1952)
- WmiApSrv.exe (PID: 3156)
- WmiApSrv.exe (PID: 7524)
- WmiApSrv.exe (PID: 7408)
INFO
Reads the computer name
- CSM_V2.0.0.2.tmp (PID: 5832)
Checks supported languages
- CSM_V2.0.0.2.tmp (PID: 5832)
- CSM_V2.0.0.2.exe (PID: 4072)
Create files in a temporary directory
- CSM_V2.0.0.2.exe (PID: 4072)
Process checks computer location settings
- CSM_V2.0.0.2.tmp (PID: 5832)
Manual execution by a user
- CSM.exe (PID: 5828)
- CSM.exe (PID: 5284)
- CSM.exe (PID: 6240)
- mspaint.exe (PID: 2364)
- CSM.exe (PID: 7944)
- CSM.exe (PID: 8032)
- CSM.exe (PID: 7736)
- CSM.exe (PID: 8000)
- CSM.exe (PID: 8112)
- CSM_V2.0.0.2.exe (PID: 7396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:03:14 17:59:41+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 100864 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
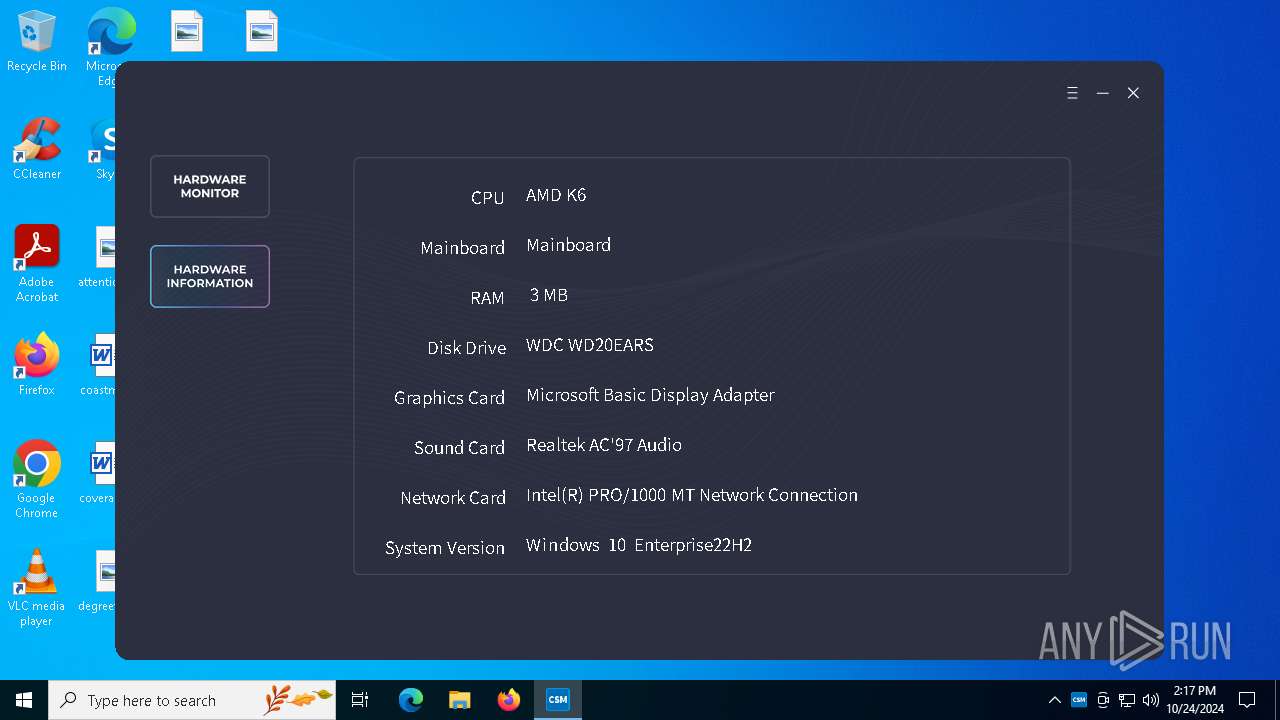
| FileVersionNumber: | 2.0.0.2 |
| ProductVersionNumber: | 2.0.0.2 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | CSM Setup |
| FileVersion: | 2.0.0.2 |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | CSM |
| ProductVersion: | 2.0.0.2 |
Total processes
169
Monitored processes
31
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1112 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1952 | C:\WINDOWS\system32\wbem\WmiApSrv.exe | C:\Windows\System32\wbem\WmiApSrv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Performance Reverse Adapter Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
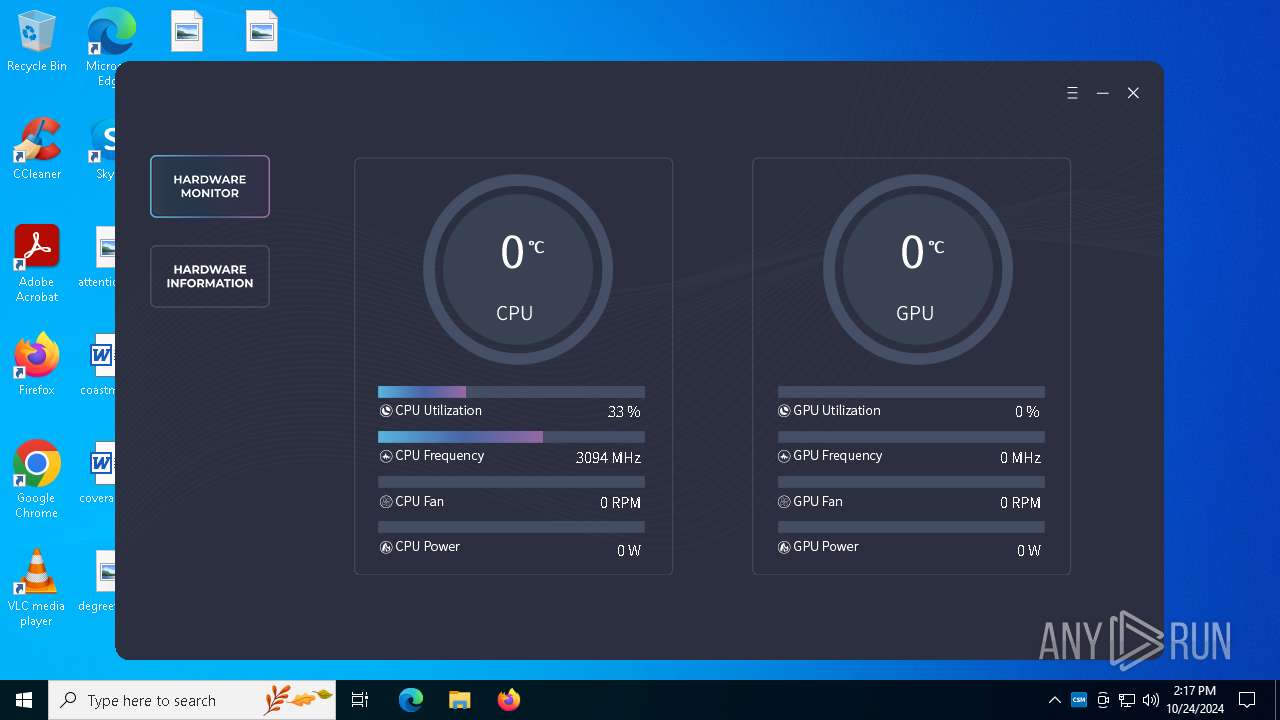
| 2364 | "C:\WINDOWS\system32\mspaint.exe" "C:\Program Files (x86)\CSM\Resources\Animation_P.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) | |||||||||||||||
| 2708 | "C:\WINDOWS\system32\cmd.exe" /c taskkill /f /t /im "CSM.exe" | C:\Windows\SysWOW64\cmd.exe | — | CSM_V2.0.0.2.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3156 | C:\WINDOWS\system32\wbem\WmiApSrv.exe | C:\Windows\System32\wbem\WmiApSrv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Performance Reverse Adapter Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4072 | "C:\Users\admin\Desktop\CSM_V2.0.0.2.exe" | C:\Users\admin\Desktop\CSM_V2.0.0.2.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: CSM Setup Exit code: 2 Version: 2.0.0.2 Modules
| |||||||||||||||
| 5284 | "C:\Program Files (x86)\CSM\CSM.exe" | C:\Program Files (x86)\CSM\CSM.exe | — | explorer.exe | |||||||||||
User: admin Company: Computer system monitoring Integrity Level: MEDIUM Description: CSM Exit code: 3221226540 Version: 2.0.0.2 Modules
| |||||||||||||||
| 5624 | "C:\Users\admin\AppData\Local\Temp\is-RH097.tmp\CSM_V2.0.0.2.tmp" /SL5="$60270,8965982,843264,C:\Users\admin\Desktop\CSM_V2.0.0.2.exe" /SPAWNWND=$7020C /NOTIFYWND=$5029C | C:\Users\admin\AppData\Local\Temp\is-RH097.tmp\CSM_V2.0.0.2.tmp | CSM_V2.0.0.2.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 2 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 5828 | "C:\Program Files (x86)\CSM\CSM.exe" | C:\Program Files (x86)\CSM\CSM.exe | explorer.exe | ||||||||||||
User: admin Company: Computer system monitoring Integrity Level: HIGH Description: CSM Exit code: 0 Version: 2.0.0.2 Modules
| |||||||||||||||
| 5832 | "C:\Users\admin\AppData\Local\Temp\is-LBJI3.tmp\CSM_V2.0.0.2.tmp" /SL5="$5029C,8965982,843264,C:\Users\admin\Desktop\CSM_V2.0.0.2.exe" | C:\Users\admin\AppData\Local\Temp\is-LBJI3.tmp\CSM_V2.0.0.2.tmp | — | CSM_V2.0.0.2.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 2 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
5 881
Read events
5 845
Write events
36
Delete events
0
Modification events
| (PID) Process: | (7532) CSM_V2.0.0.2.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Montserrat (TrueType) |
Value: Montserrat.otf | |||
| (PID) Process: | (7532) CSM_V2.0.0.2.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | 思源黑体 (TrueType) |
Value: SourceHanSansCN.ttf | |||
| (PID) Process: | (7532) CSM_V2.0.0.2.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\CSM_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.0.4 (u) | |||
| (PID) Process: | (7532) CSM_V2.0.0.2.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\CSM_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files (x86)\CSM | |||
| (PID) Process: | (7532) CSM_V2.0.0.2.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\CSM_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\CSM\ | |||
| (PID) Process: | (7532) CSM_V2.0.0.2.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\CSM_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: CSM | |||
| (PID) Process: | (7532) CSM_V2.0.0.2.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\CSM_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (7532) CSM_V2.0.0.2.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\CSM_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: en | |||
| (PID) Process: | (7532) CSM_V2.0.0.2.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\CSM_is1 |
| Operation: | write | Name: | DisplayName |
Value: CSM version 2.0.0.2 | |||
| (PID) Process: | (7532) CSM_V2.0.0.2.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\CSM_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\CSM\CSM.exe | |||
Executable files
20
Suspicious files
8
Text files
81
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7532 | CSM_V2.0.0.2.tmp | C:\Program Files (x86)\CSM\unins000.exe | executable | |
MD5:F26AA1BF2F4BD940B38CDE5800CA6756 | SHA256:FBB436B8812F4D8F508A24BEBB491980B66E7ACB664BAD5169BEBAC123378603 | |||
| 6604 | CSM_V2.0.0.2.exe | C:\Users\admin\AppData\Local\Temp\is-RH097.tmp\CSM_V2.0.0.2.tmp | executable | |
MD5:7326D07214018EE6D99538397A0FD09B | SHA256:40A71BA14F1E5115024766FDA2199B24536EFEB453A8E8714C588932D1A346A1 | |||
| 7532 | CSM_V2.0.0.2.tmp | C:\Users\admin\AppData\Local\Temp\is-8991V.tmp\_isetup\_isdecmp.dll | executable | |
MD5:77D6D961F71A8C558513BED6FD0AD6F1 | SHA256:5DA7C8D33D3B7DB46277012D92875C0B850C8ABF1EB3C8C9C5B9532089A0BCF0 | |||
| 5624 | CSM_V2.0.0.2.tmp | C:\Users\admin\AppData\Local\Temp\is-46PD7.tmp\_isetup\_isdecmp.dll | executable | |
MD5:77D6D961F71A8C558513BED6FD0AD6F1 | SHA256:5DA7C8D33D3B7DB46277012D92875C0B850C8ABF1EB3C8C9C5B9532089A0BCF0 | |||
| 7396 | CSM_V2.0.0.2.exe | C:\Users\admin\AppData\Local\Temp\is-NDK8I.tmp\CSM_V2.0.0.2.tmp | executable | |
MD5:7326D07214018EE6D99538397A0FD09B | SHA256:40A71BA14F1E5115024766FDA2199B24536EFEB453A8E8714C588932D1A346A1 | |||
| 5624 | CSM_V2.0.0.2.tmp | C:\Users\admin\AppData\Local\Temp\is-46PD7.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 7532 | CSM_V2.0.0.2.tmp | C:\Program Files (x86)\CSM\is-4KRU0.tmp | executable | |
MD5:F26AA1BF2F4BD940B38CDE5800CA6756 | SHA256:FBB436B8812F4D8F508A24BEBB491980B66E7ACB664BAD5169BEBAC123378603 | |||
| 7532 | CSM_V2.0.0.2.tmp | C:\Program Files (x86)\CSM\Resources\is-F64T7.tmp | image | |
MD5:6F3216F434EAC7AE1F575D60DFBDC6C7 | SHA256:6A96CB6443AF8AFB06CD56E0712C99A59408681C136A8429072AE93E47729E46 | |||
| 7508 | CSM_V2.0.0.2.exe | C:\Users\admin\AppData\Local\Temp\is-FQ8OI.tmp\CSM_V2.0.0.2.tmp | executable | |
MD5:7326D07214018EE6D99538397A0FD09B | SHA256:40A71BA14F1E5115024766FDA2199B24536EFEB453A8E8714C588932D1A346A1 | |||
| 7532 | CSM_V2.0.0.2.tmp | C:\Program Files (x86)\CSM\Resources\is-D3HKV.tmp | image | |
MD5:79AB7EFD99C924EE973F6939D2EFF8D9 | SHA256:CC3FD7F40BFE5869323CFE9953FF782B70EA51DEA7209C91E264B3EC9F182D11 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
55
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6708 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6024 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6708 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7028 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1764 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4360 | SearchApp.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6944 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6944 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
Process | Message |
|---|---|
CSM.exe | c5 01 00 00 00 00 00 00 00 02 00 00 00 00 00 00 01 c9
|