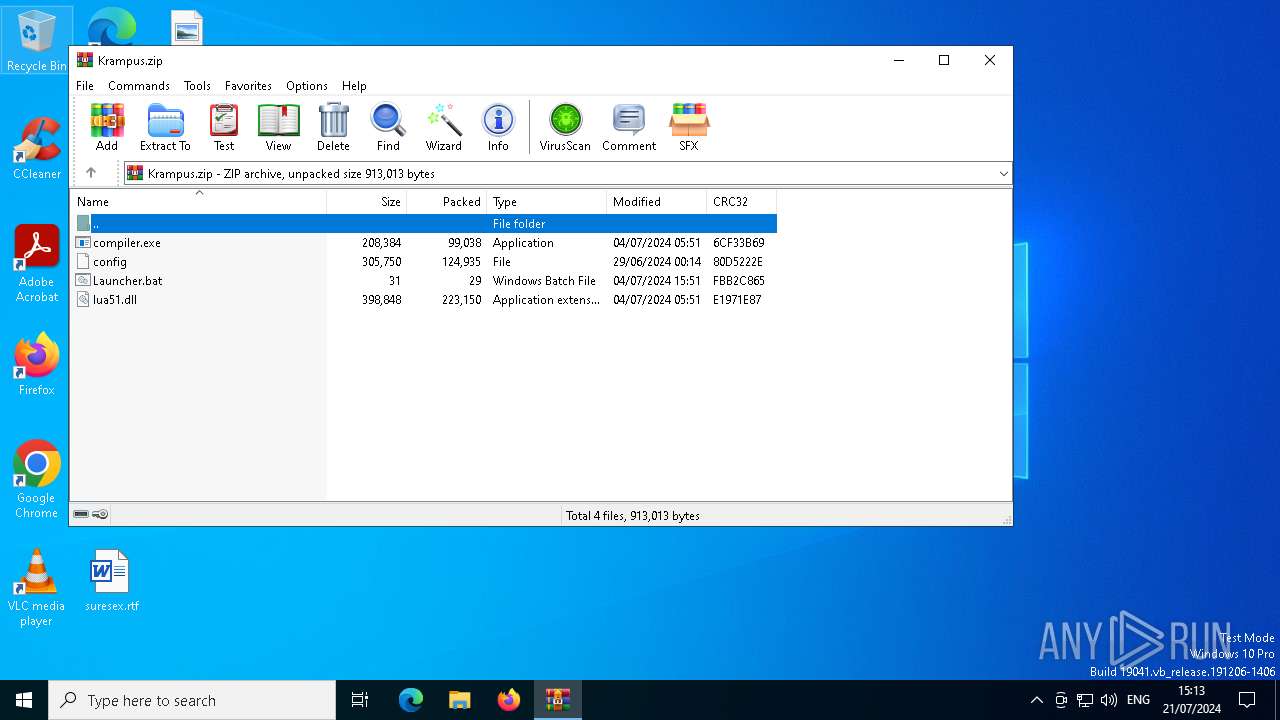
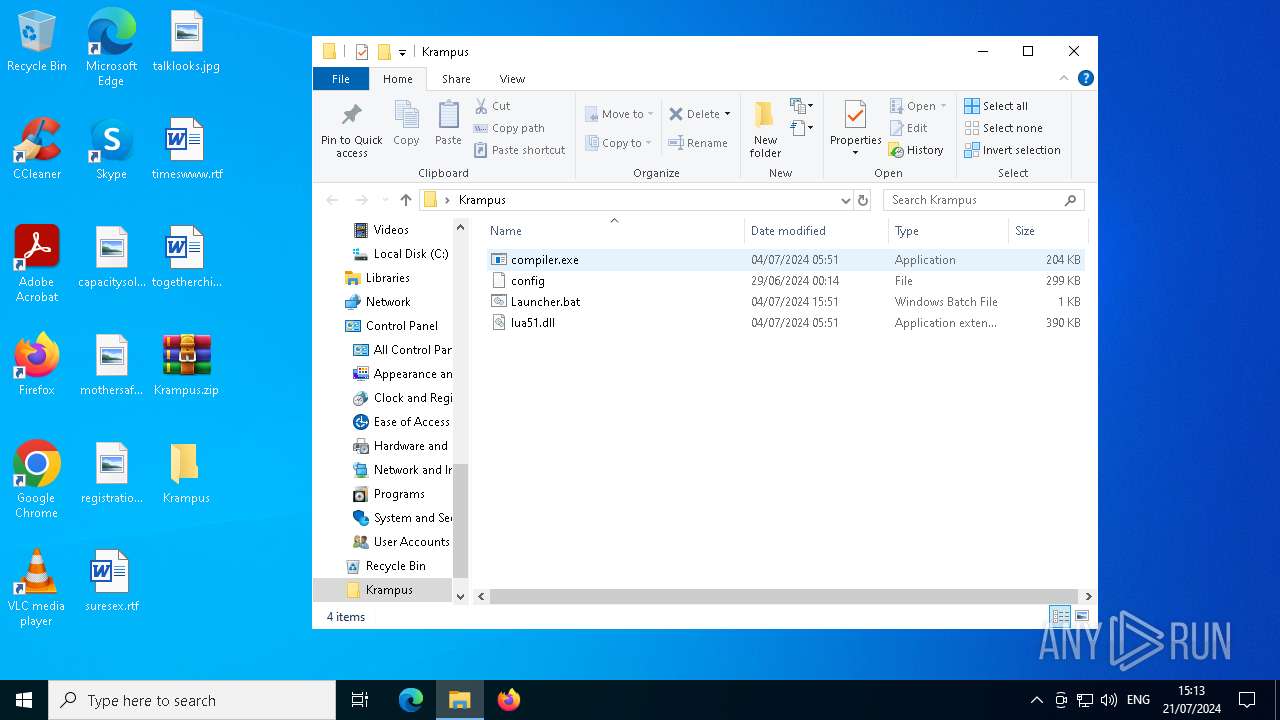
| File name: | Krampus.zip |
| Full analysis: | https://app.any.run/tasks/9709115e-9256-4d85-bbe3-5f5ff94f1051 |
| Verdict: | Malicious activity |
| Analysis date: | July 21, 2024, 14:13:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 772066657856854D0A971DD2BB712EF8 |
| SHA1: | 06AEE58AE65189ACC923CB75324F9A1A6D970E4F |
| SHA256: | 47E9B7E8DAE0E4BAEC0AAB32A3DBF59972BC3DD4549BD38CD951F49EDF7C9302 |
| SSDEEP: | 24576:5pHAFQ9J8PpCYFMiM577Dbof12BvI4JKf6n6xKBvOde4ys:5pHAFEJQCYFMiM5vDbof12BvI4JKfo61 |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6424)
SUSPICIOUS
Reads security settings of Internet Explorer
- compiler.exe (PID: 2252)
Checks for external IP
- compiler.exe (PID: 2252)
Checks Windows Trust Settings
- compiler.exe (PID: 2252)
INFO
Checks proxy server information
- slui.exe (PID: 4368)
- compiler.exe (PID: 2252)
Reads the software policy settings
- slui.exe (PID: 4368)
- compiler.exe (PID: 2252)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 8132)
Manual execution by a user
- WinRAR.exe (PID: 8132)
- compiler.exe (PID: 6292)
- cmd.exe (PID: 6440)
- cmd.exe (PID: 6908)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8132)
Checks supported languages
- compiler.exe (PID: 6292)
- compiler.exe (PID: 2252)
Reads the computer name
- compiler.exe (PID: 2252)
Creates files or folders in the user directory
- compiler.exe (PID: 2252)
Reads the machine GUID from the registry
- compiler.exe (PID: 2252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:07:04 07:51:46 |
| ZipCRC: | 0x6cf33b69 |
| ZipCompressedSize: | 99038 |
| ZipUncompressedSize: | 208384 |
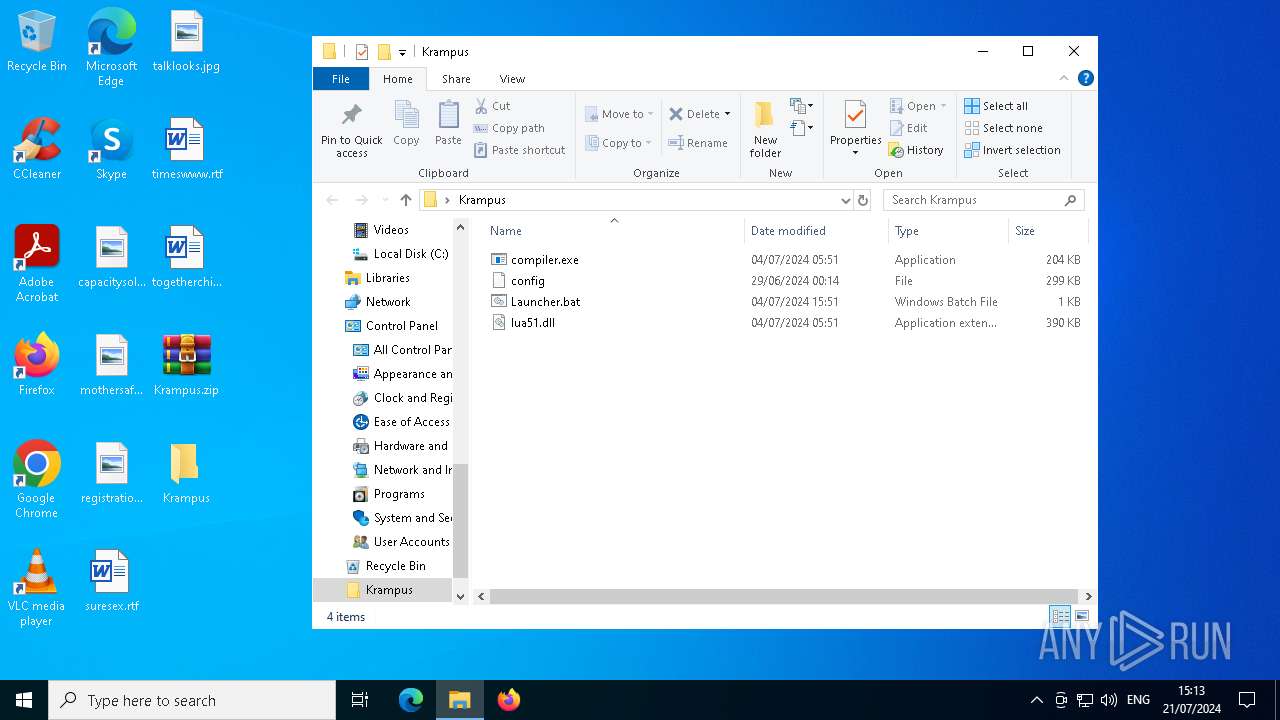
| ZipFileName: | compiler.exe |
Total processes
162
Monitored processes
12
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
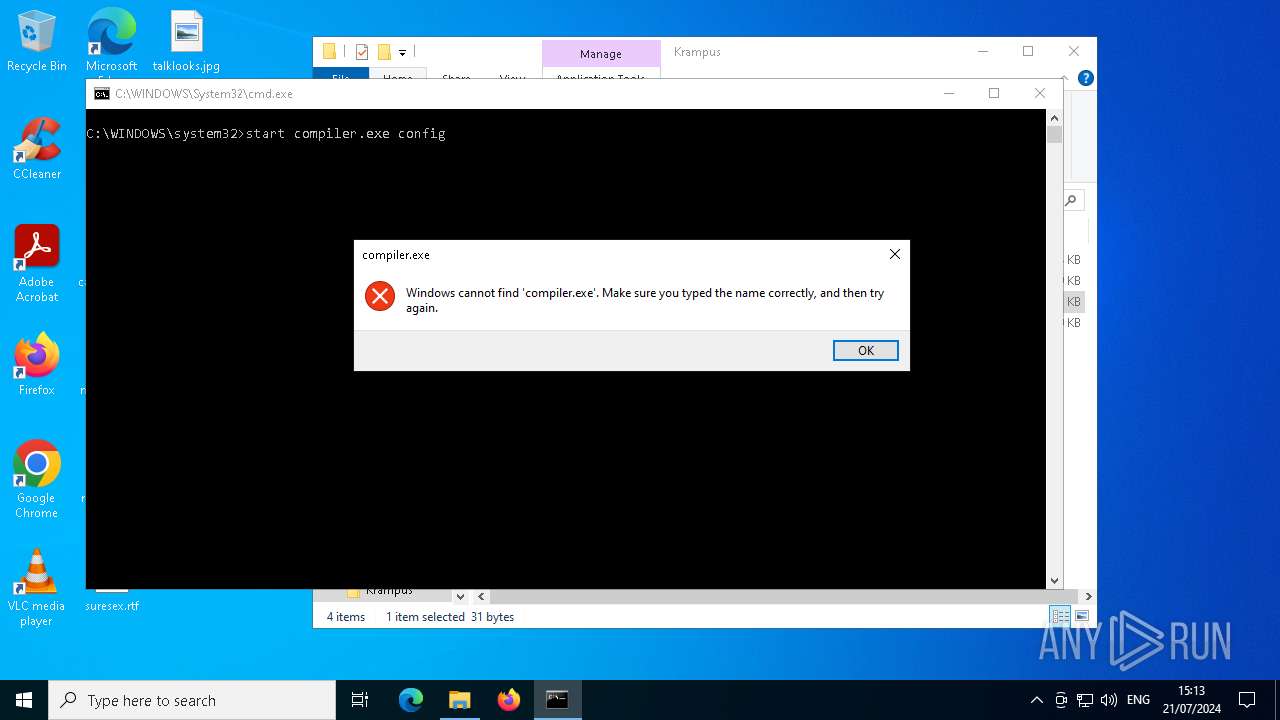
| 2252 | compiler.exe config | C:\Users\admin\Desktop\Krampus\compiler.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2276 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4368 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5112 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6292 | "C:\Users\admin\Desktop\Krampus\compiler.exe" | C:\Users\admin\Desktop\Krampus\compiler.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6424 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Krampus.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6440 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\Krampus\Launcher.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6908 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Krampus\Launcher.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7208 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 142
Read events
12 104
Write events
38
Delete events
0
Modification events
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Krampus.zip | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (6424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
3
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2252 | compiler.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\json[1].json | binary | |
MD5:81F6C4E098F67FCF7C5F4AFCCABC6F32 | SHA256:44856DE77317A3D6CA2BB19BB31D75CFD196E4B0E6AC823A092690E75F0C3C44 | |||
| 8132 | WinRAR.exe | C:\Users\admin\Desktop\Krampus\config | text | |
MD5:4AD602C68EB3AA4C84C73834E653605F | SHA256:AA2AC19E959BECA447E34DA002CC63149C208D8427BB8631344EA069F4BBCCBA | |||
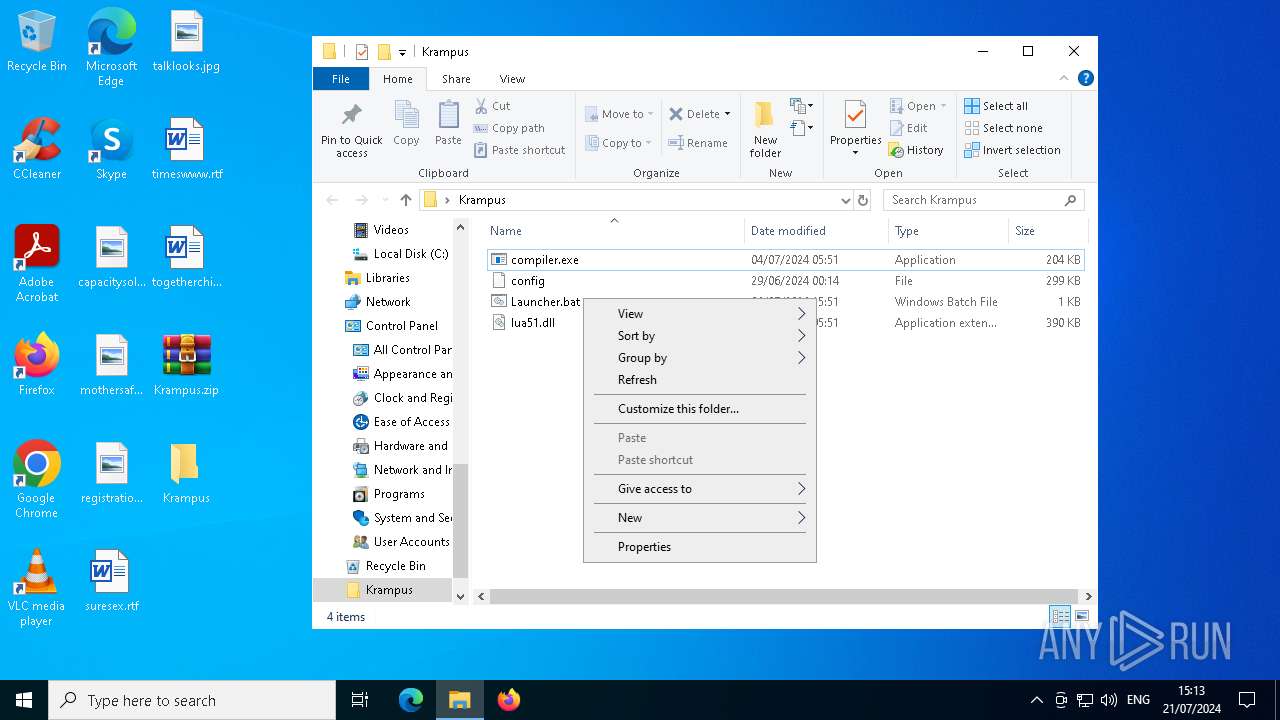
| 8132 | WinRAR.exe | C:\Users\admin\Desktop\Krampus\compiler.exe | executable | |
MD5:43BACCE037526B58BC2E9BD1F6F7AA0D | SHA256:AAD44EEDB5B0ED756C2212D8C88B0C882271CA4D6C4B41600EFC2B7A6DE7A5E9 | |||
| 8132 | WinRAR.exe | C:\Users\admin\Desktop\Krampus\lua51.dll | executable | |
MD5:5B7166EEFFB7C256CDAE8DD6140F0900 | SHA256:89A7DC0754C79F8A5E457DDDD4AEC0C3DA605CB6E3775206FE706482300D420B | |||
| 2252 | compiler.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\DMJhfVFs[1].txt | text | |
MD5:2B3A42FA6FEE8806273AD428E0BD30BC | SHA256:B3DA4828D40D9308AC5B5303F1577C9A8D475565F6B863F1EBA04AA31D85783A | |||
| 8132 | WinRAR.exe | C:\Users\admin\Desktop\Krampus\Launcher.bat | text | |
MD5:41132BF2FE575A1B1E4C1504AFE5324A | SHA256:A6A10D3AD76F6AC73DDB8026CEA7024523B67210CAD1FF64E0DEEA00BBF54DF5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
81
DNS requests
33
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 40.68.123.157:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 13.85.23.206:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
— | — | GET | 200 | 40.68.123.157:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
— | — | GET | 302 | 23.35.229.160:443 | https://www.microsoft.com/ | unknown | — | — | unknown |
2252 | compiler.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | shared |
— | — | GET | 302 | 23.35.229.160:443 | https://www.microsoft.com/ | unknown | — | — | unknown |
— | — | GET | 304 | 40.68.123.157:443 | https://slscr.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 200 | 20.103.156.88:443 | https://arc.msn.com/v4/api/register?asid=B6492EBE33414ABB8B8215F0FFE8C5CE&placement=cdmdevreg&country=GB&locale=en-GB&poptin=0&fmt=json&arch=AMD64&chassis=1&concp=0&d3dfl=D3D_FEATURE_LEVEL_12_1&devfam=Windows.Desktop&devosver=10.0.19045.4046&dinst=1661339444&dmret=0&flightbranch=&flightring=Retail&icluc=0&localid=w%3AAC7699B0-48EA-FD22-C8DC-06A02098A0F0&oem=DELL&osbranch=vb_release&oslocale=en-US&osret=1&ossku=Professional&osskuid=48&prccn=4&prccs=3094&prcmf=AuthenticAMD&procm=Intel%28R%29%20Core%28TM%29%20i5-6400%20CPU%20%40%202.70GHz&ram=4096&tinst=Client&tl=1&pat=0&smc=0&sac=0&disphorzres=1280&dispsize=15.3&dispvertres=720&ldisphorzres=1280&ldispvertres=720&moncnt=1&cpdsk=260281&frdsk=218542&lo=3613332&tsu=1003862 | unknown | — | — | unknown |
— | — | POST | — | 20.190.159.71:443 | https://login.live.com/RST2.srf | unknown | — | — | unknown |
— | — | POST | — | 40.126.31.69:443 | https://login.live.com/RST2.srf | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5620 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4716 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.209.33.156:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6308 | backgroundTaskHost.exe | 20.103.156.88:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
arc.msn.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
ip-api.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
2168 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2168 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2252 | compiler.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |