| download: | /HackerSinhos/You-Are-An-Idiot/releases/download/1.0.1/You-are-an-idiot.zip |
| Full analysis: | https://app.any.run/tasks/e3066482-6154-4bb6-84a0-a06eebc029d6 |
| Verdict: | Malicious activity |
| Analysis date: | February 15, 2024, 22:48:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
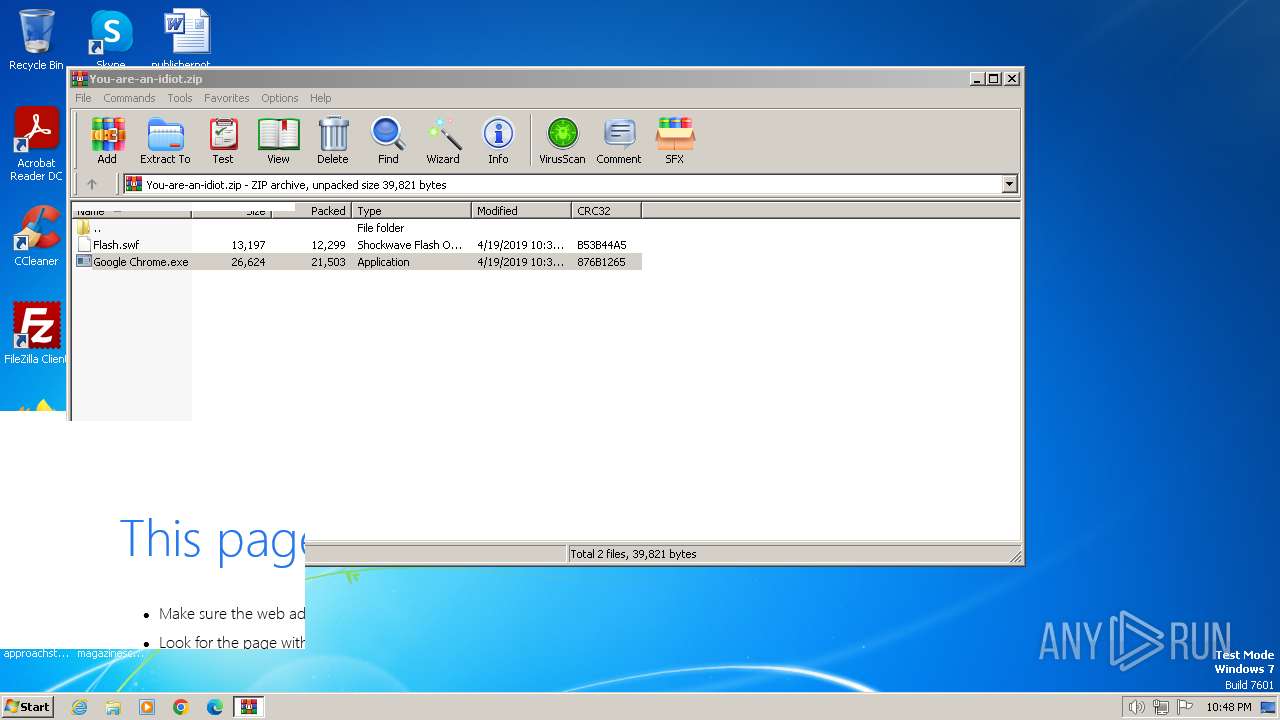
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4ACD75F2BFEB99226A8C9CC721284208 |
| SHA1: | 4C5FC527D8825952A6F45D4FCBAB3BDB074E9713 |
| SHA256: | 47DCA4E070081DF4B70053C858A851DBD720845D4AC579EB5E7334A44FFA16C7 |
| SSDEEP: | 768:XSAiCxuDCOUT3qQG7VepMaNNo3Bn9JtmqU731RY4EF:CAi5OnTDG7kPNu9zeLEF |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3864)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3864)
- Google Chrome.exe (PID: 3692)
- Google Chrome.exe (PID: 3464)
- Google Chrome.exe (PID: 1696)
Reads Microsoft Outlook installation path
- Google Chrome.exe (PID: 3692)
- Google Chrome.exe (PID: 3464)
- Google Chrome.exe (PID: 1696)
Reads the Internet Settings
- Google Chrome.exe (PID: 3692)
- Google Chrome.exe (PID: 3464)
- Google Chrome.exe (PID: 1696)
Reads the date of Windows installation
- pwsh.exe (PID: 2792)
Reads Internet Explorer settings
- Google Chrome.exe (PID: 1696)
- Google Chrome.exe (PID: 3464)
- Google Chrome.exe (PID: 3692)
INFO
Checks supported languages
- Google Chrome.exe (PID: 3692)
- Google Chrome.exe (PID: 3464)
- pwsh.exe (PID: 2792)
- Google Chrome.exe (PID: 1696)
Reads the computer name
- Google Chrome.exe (PID: 3692)
- Google Chrome.exe (PID: 3464)
- Google Chrome.exe (PID: 1696)
- pwsh.exe (PID: 2792)
Reads the machine GUID from the registry
- Google Chrome.exe (PID: 3692)
- Google Chrome.exe (PID: 3464)
- Google Chrome.exe (PID: 1696)
Creates files or folders in the user directory
- Google Chrome.exe (PID: 3692)
- Google Chrome.exe (PID: 3464)
- Google Chrome.exe (PID: 1696)
Checks proxy server information
- Google Chrome.exe (PID: 3692)
- Google Chrome.exe (PID: 3464)
- Google Chrome.exe (PID: 1696)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3864)
Manual execution by a user
- pwsh.exe (PID: 2792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:04:19 10:31:24 |
| ZipCRC: | 0xb53b44a5 |
| ZipCompressedSize: | 12299 |
| ZipUncompressedSize: | 13197 |
| ZipFileName: | Flash.swf |
Total processes
45
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1696 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3864.29165\Google Chrome.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3864.29165\Google Chrome.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: YouAreAnIdiot Exit code: 1073807364 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2792 | "C:\Program Files\PowerShell\7\pwsh.exe" -WorkingDirectory ~ | C:\Program Files\PowerShell\7\pwsh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: pwsh Exit code: 1073807364 Version: 7.2.11.500 Modules
| |||||||||||||||
| 3464 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3864.29104\Google Chrome.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3864.29104\Google Chrome.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: YouAreAnIdiot Exit code: 1073807364 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3692 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3864.28182\Google Chrome.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3864.28182\Google Chrome.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: YouAreAnIdiot Exit code: 1073807364 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3864 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\You-are-an-idiot.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1073807364 Version: 5.91.0 Modules
| |||||||||||||||
Total events
90 705
Read events
90 587
Write events
118
Delete events
0
Modification events
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\You-are-an-idiot.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
4
Text files
2
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2792 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\7.2.11\update1_v7.4.1_2024-01-11 | — | |
MD5:— | SHA256:— | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3864.28182\Flash.swf | swf | |
MD5:EA1D5719A0D457B49B5D5BE974E79E33 | SHA256:CD62F379B66B3AB3A877E2A11AF49D0200037802C350972301C1842EE41B7B20 | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3864.29165\Flash.swf | swf | |
MD5:EA1D5719A0D457B49B5D5BE974E79E33 | SHA256:CD62F379B66B3AB3A877E2A11AF49D0200037802C350972301C1842EE41B7B20 | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3864.29104\Google Chrome.exe | executable | |
MD5:403939B2425A7DF005F44BEFEA8DEF6F | SHA256:A59D6DF0AE2C12F5D0249C1F7F8B66DB170252DE8406124BEA2311802D6A27A0 | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3864.29165\Google Chrome.exe | executable | |
MD5:403939B2425A7DF005F44BEFEA8DEF6F | SHA256:A59D6DF0AE2C12F5D0249C1F7F8B66DB170252DE8406124BEA2311802D6A27A0 | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3864.28182\Google Chrome.exe | executable | |
MD5:403939B2425A7DF005F44BEFEA8DEF6F | SHA256:A59D6DF0AE2C12F5D0249C1F7F8B66DB170252DE8406124BEA2311802D6A27A0 | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3864.29104\Flash.swf | binary | |
MD5:EA1D5719A0D457B49B5D5BE974E79E33 | SHA256:CD62F379B66B3AB3A877E2A11AF49D0200037802C350972301C1842EE41B7B20 | |||
| 2792 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\StartupProfileData-Interactive | binary | |
MD5:ECADBE591A402A0A7226461F589F270B | SHA256:2D54E281A7854D7E108F3FC4FBC89A75751697A2DCEF68C7064212C11D02FCD2 | |||
| 2792 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\e1a648060a327b80.customDestinations-ms~RF18e4dd.TMP | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3864.29349\Flash.swf | swf | |
MD5:EA1D5719A0D457B49B5D5BE974E79E33 | SHA256:CD62F379B66B3AB3A877E2A11AF49D0200037802C350972301C1842EE41B7B20 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2792 | pwsh.exe | 184.30.22.2:443 | aka.ms | AKAMAI-AS | DE | unknown |
2792 | pwsh.exe | 52.239.160.36:443 | pscoretestdata.blob.core.windows.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
aka.ms |
| whitelisted |
pscoretestdata.blob.core.windows.net |
| unknown |
Threats
Process | Message |
|---|---|
pwsh.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 2792. Message ID: [0x2509].
|