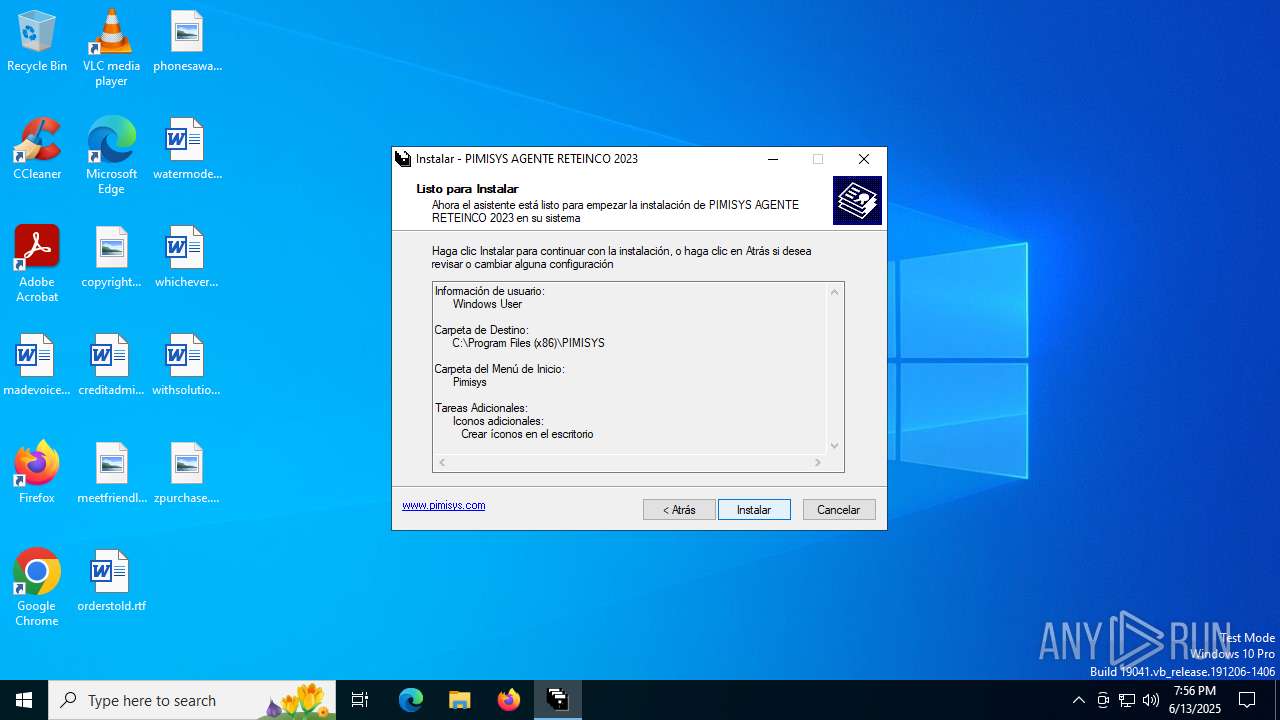
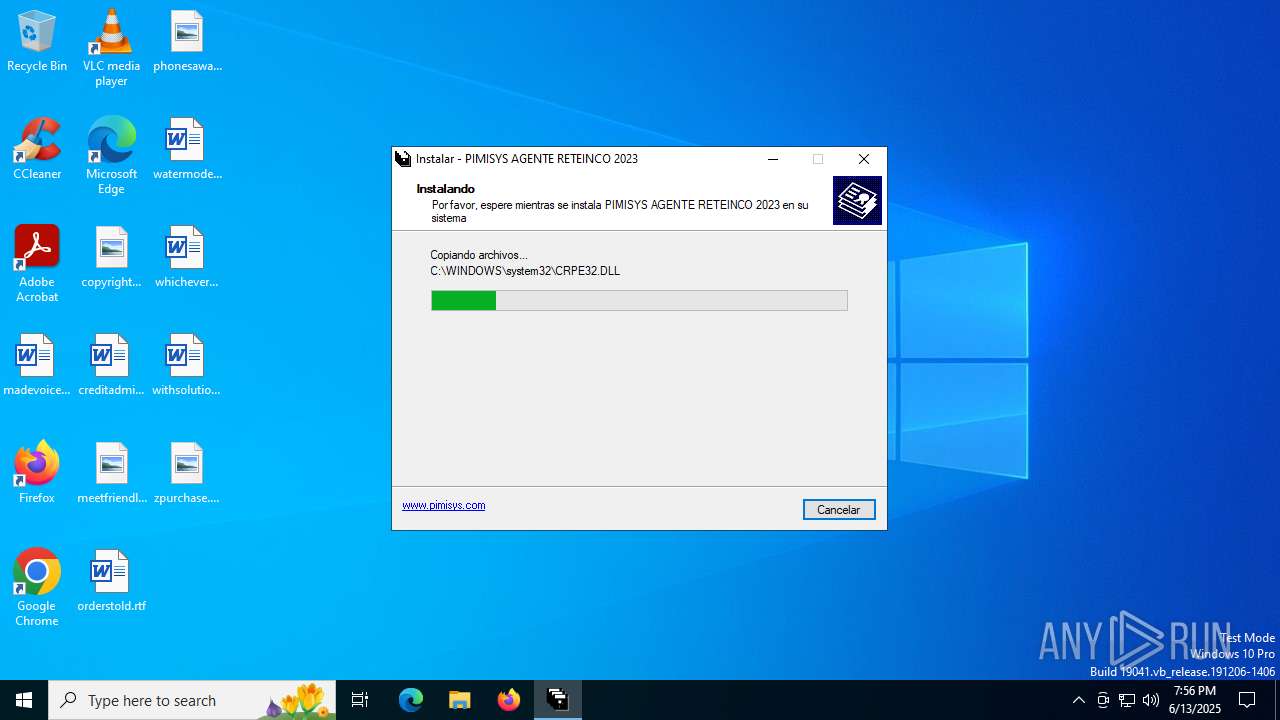
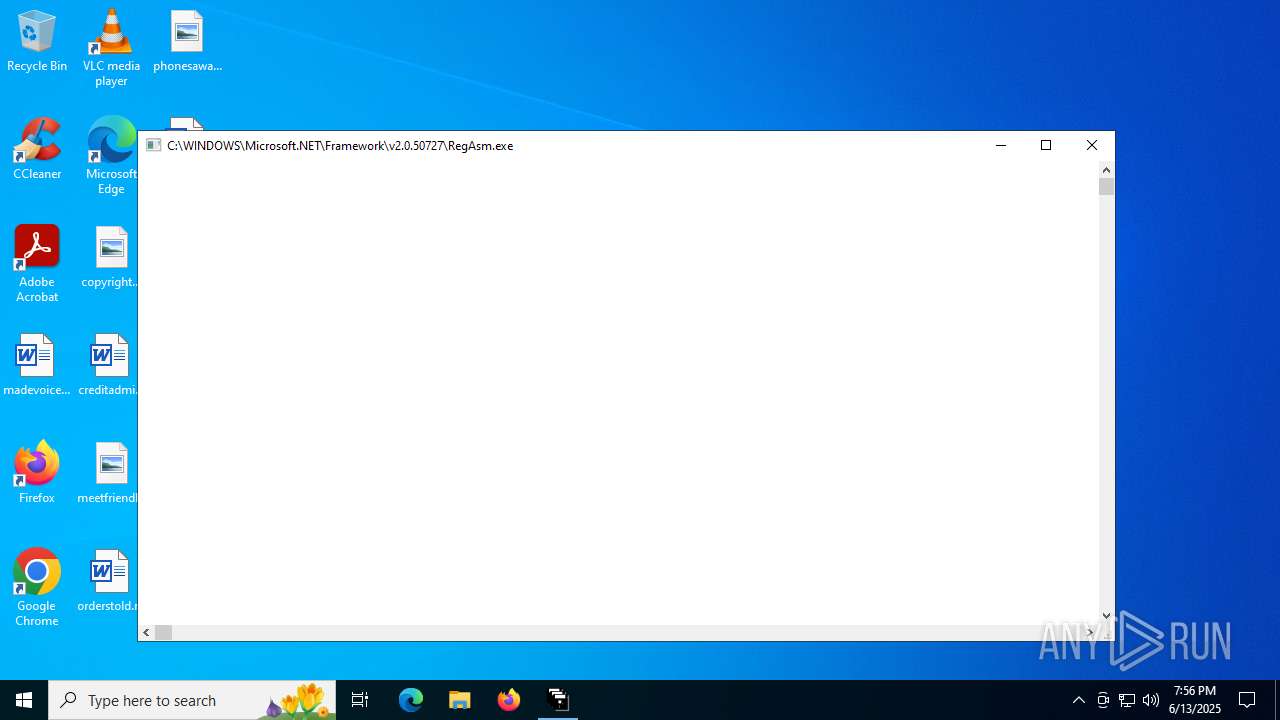
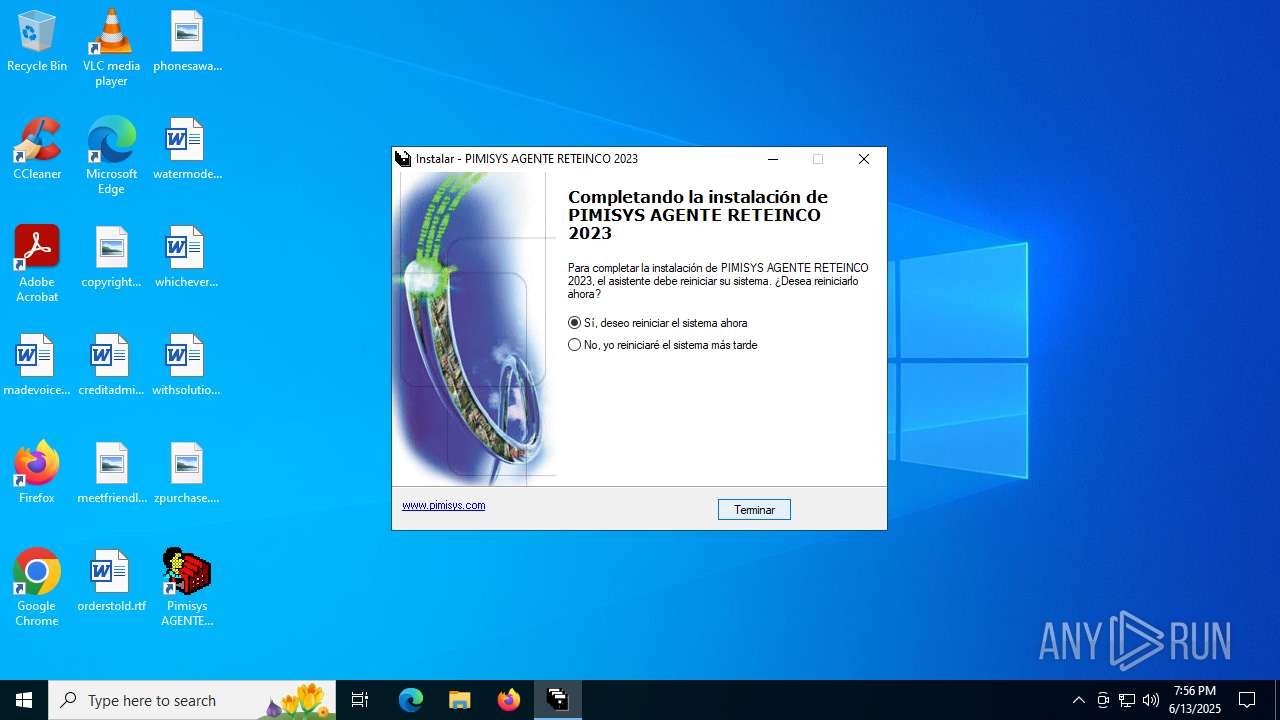
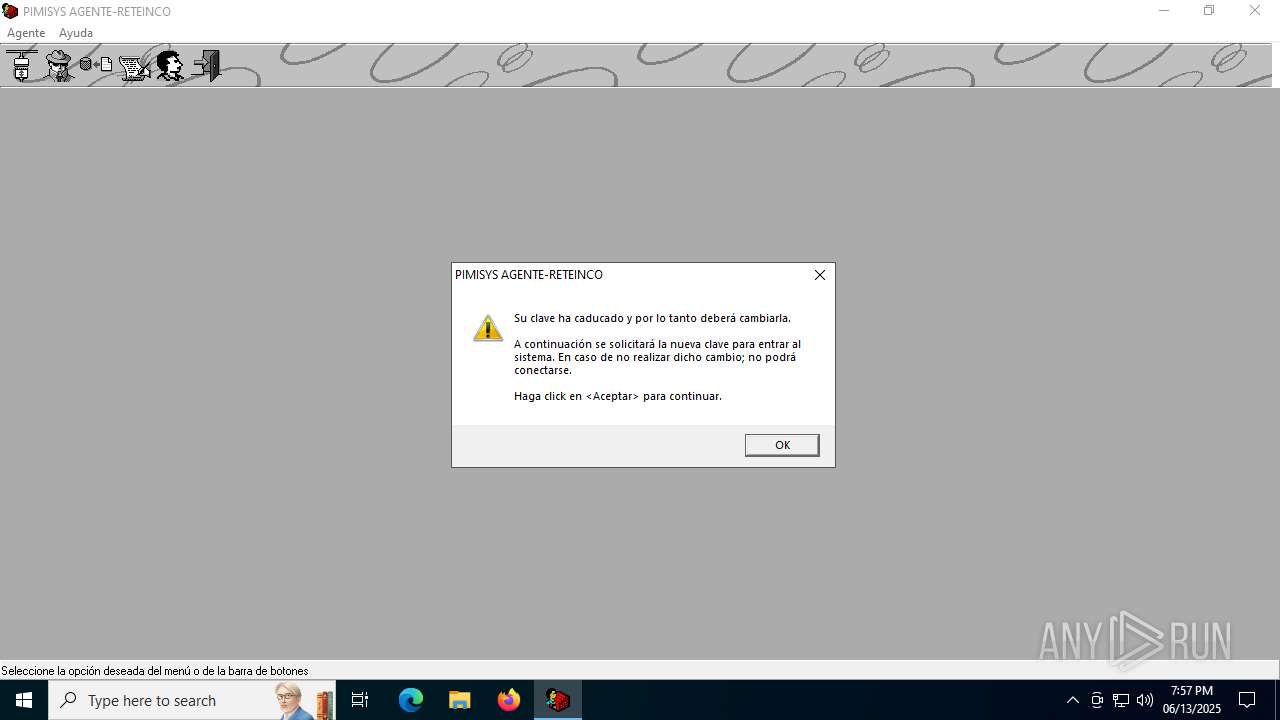
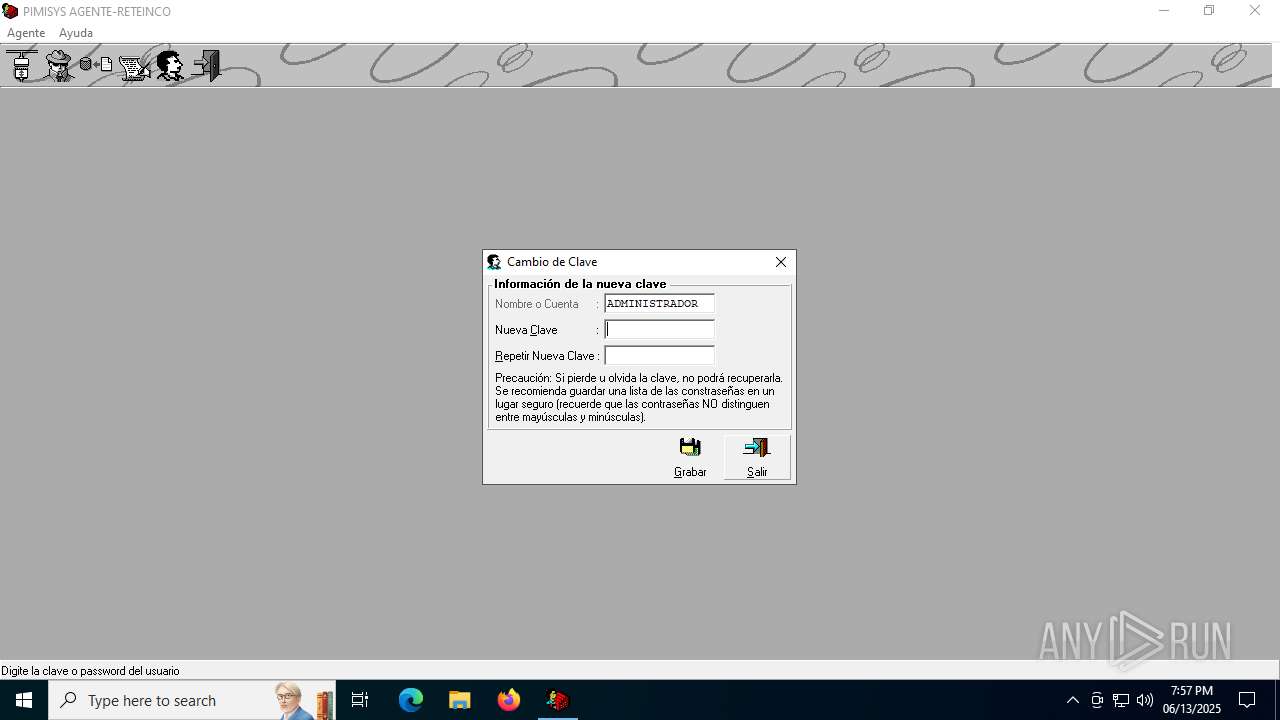
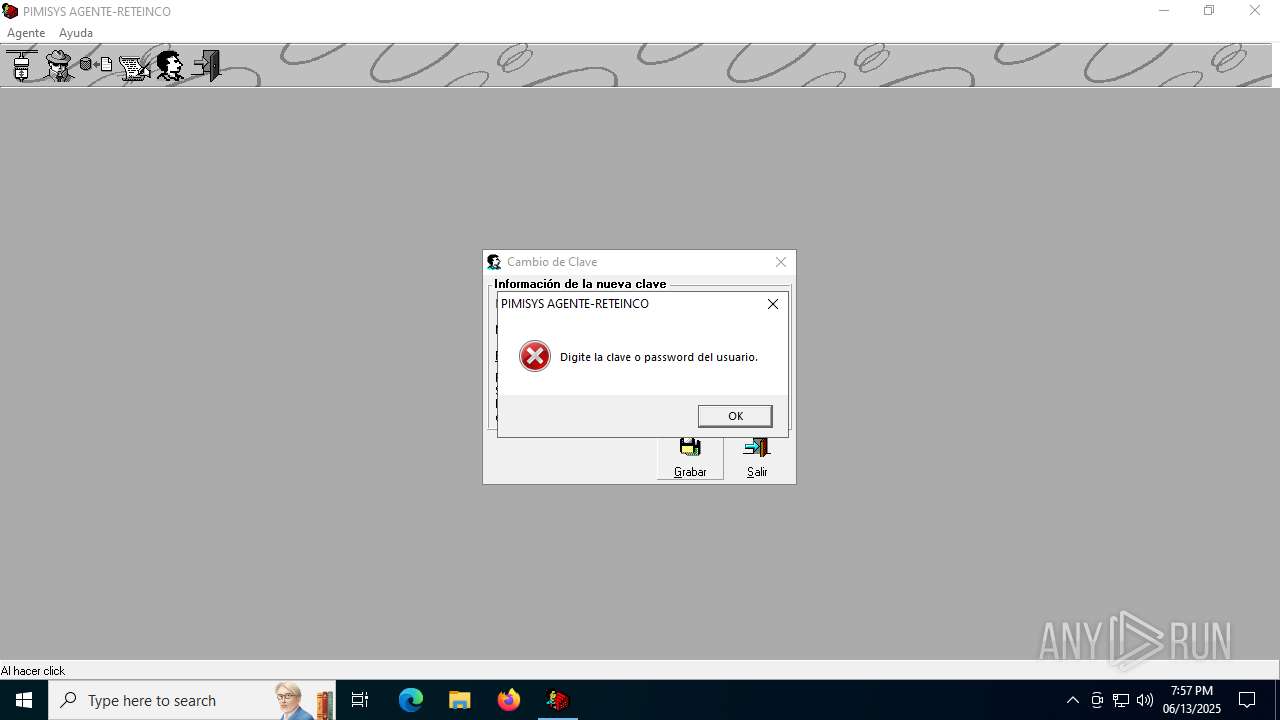
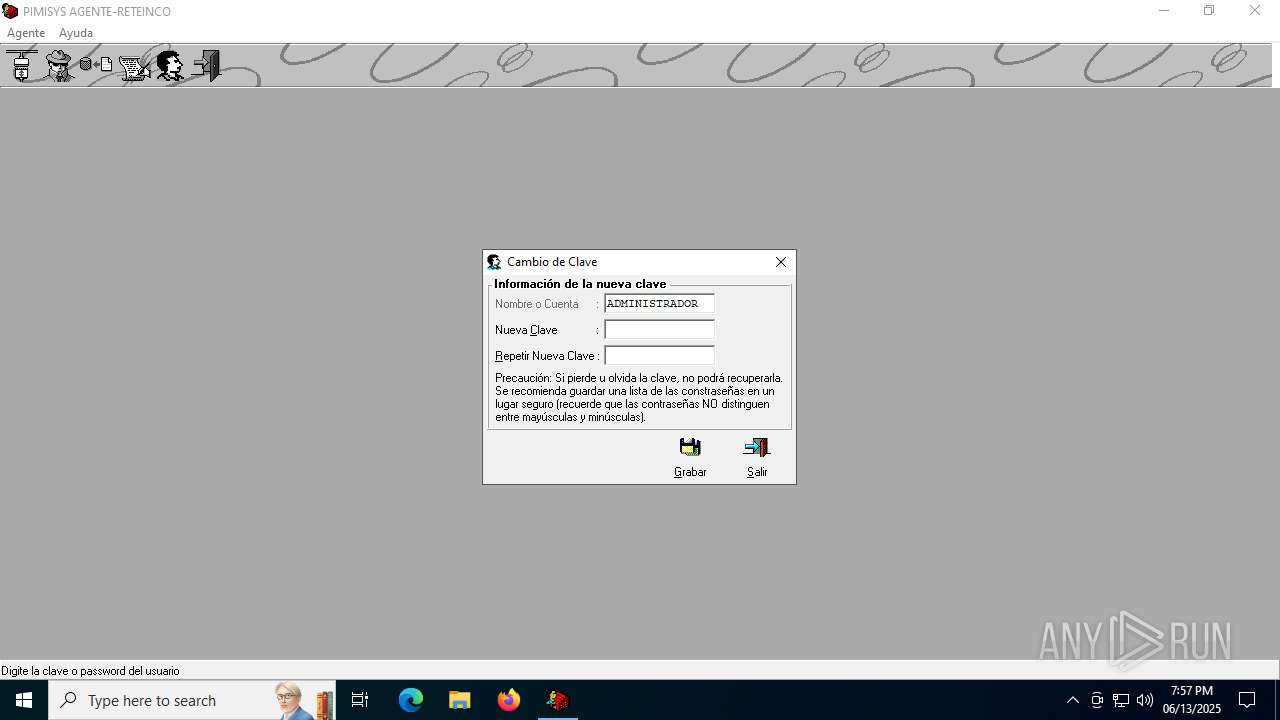
| File name: | INSTALAR.EXE |
| Full analysis: | https://app.any.run/tasks/133ae6d3-ab31-4b13-8a39-dcd4a2e8d735 |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2025, 19:55:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InnoSetup self-extracting archive, 8 sections |
| MD5: | 9E2974536D3EFB98F26047BE19B9383A |
| SHA1: | 6605F5FAB7C1EC202B14157340C943A37CB78AFF |
| SHA256: | 47A2B5C77922B840B27F7FDB8F17AA43C1F459E59568C5C4917B8757CC72AD65 |
| SSDEEP: | 98304:xqTzwhWT88MyP9WQ3mvkbP7mzGPqmDqsSOrZ853YTx3IeuDJXxgjBvIIKC6YQS5S:ob47+mofa8zNv+A8 |
MALICIOUS
Changes the autorun value in the registry
- is-BEL3B.tmp (PID: 1488)
Starts Visual C# compiler
- RICOAGNT.EXE (PID: 6200)
SUSPICIOUS
Executable content was dropped or overwritten
- INSTALAR.EXE.exe (PID: 5764)
- is-BEL3B.tmp (PID: 1488)
- csc.exe (PID: 6296)
Process drops legitimate windows executable
- is-BEL3B.tmp (PID: 1488)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 3976)
- updater.exe (PID: 3680)
Application launched itself
- updater.exe (PID: 3680)
Uses .NET C# to load dll
- RICOAGNT.EXE (PID: 6200)
Creates/Modifies COM task schedule object
- RegAsm.exe (PID: 3608)
INFO
Reads the computer name
- is-BEL3B.tmp (PID: 1488)
- RegAsm.exe (PID: 4084)
- RegAsm.exe (PID: 3608)
- INSTALAR.EXE.exe (PID: 5764)
Create files in a temporary directory
- INSTALAR.EXE.exe (PID: 5764)
- is-BEL3B.tmp (PID: 1488)
The sample compiled with english language support
- INSTALAR.EXE.exe (PID: 5764)
- is-BEL3B.tmp (PID: 1488)
Checks supported languages
- INSTALAR.EXE.exe (PID: 5764)
- is-BEL3B.tmp (PID: 1488)
- RegAsm.exe (PID: 4084)
- RegAsm.exe (PID: 3608)
Detects InnoSetup installer (YARA)
- INSTALAR.EXE.exe (PID: 5764)
- is-BEL3B.tmp (PID: 1488)
Compiled with Borland Delphi (YARA)
- is-BEL3B.tmp (PID: 1488)
Creates files in the program directory
- is-BEL3B.tmp (PID: 1488)
- RegAsm.exe (PID: 3608)
Creates files or folders in the user directory
- is-BEL3B.tmp (PID: 1488)
Creates a software uninstall entry
- is-BEL3B.tmp (PID: 1488)
The sample compiled with spanish language support
- is-BEL3B.tmp (PID: 1488)
Launching a file from a Registry key
- is-BEL3B.tmp (PID: 1488)
Manual execution by a user
- runonce.exe (PID: 4784)
- RICOAGNT.EXE (PID: 6200)
Reads the machine GUID from the registry
- RegAsm.exe (PID: 3608)
- RegAsm.exe (PID: 4084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (82.8) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10.7) |
| .exe | | | Win32 Executable (generic) (3.4) |
| .exe | | | Generic Win/DOS Executable (1.5) |
| .exe | | | DOS Executable Generic (1.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 35328 |
| InitializedDataSize: | 10240 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9264 |
| OSVersion: | 1 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2023.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | This installation was built with Inno Setup: http://www.innosetup.com |
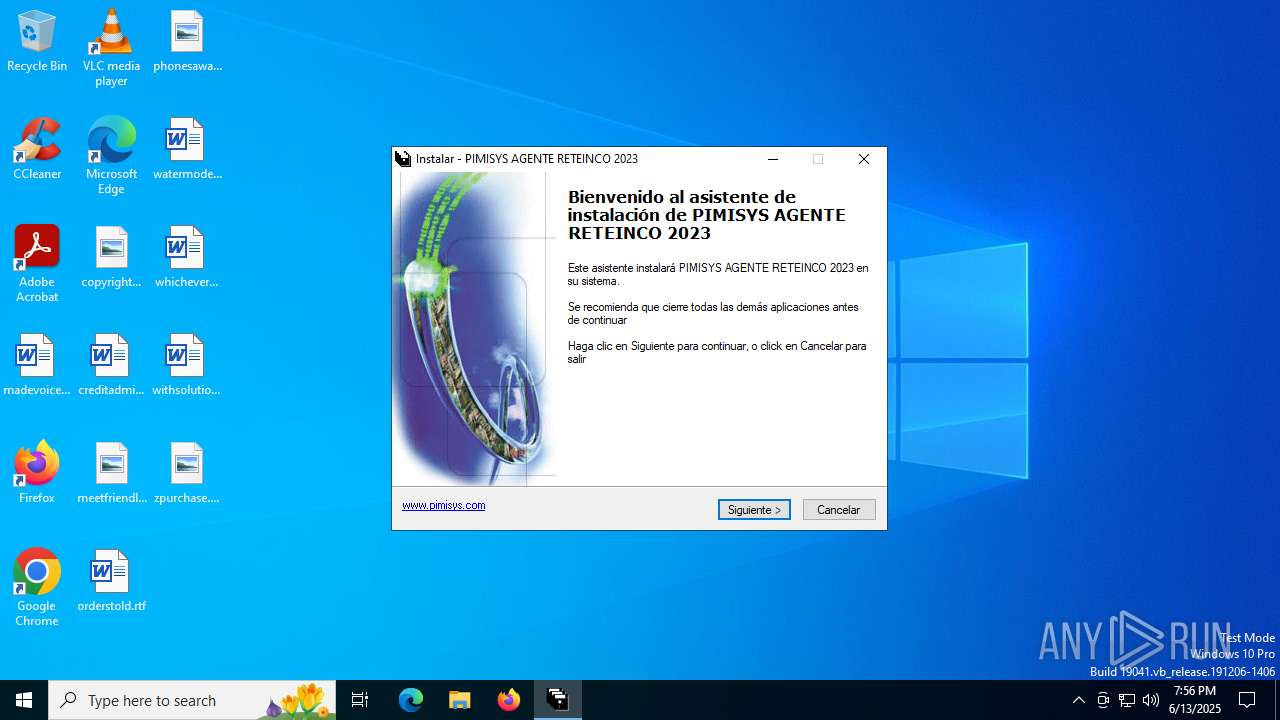
| CompanyName: | PIMISYS S.A.S. |
| FileDescription: | PIMISYS AGENTE RETEINCO 2023 |
| FileVersion: | PIMISYS AGENTE RETEI |
| InternalName: | - |
| OriginalFileName: | - |
| ProductName: | - |
| ProductVersion: | - |
Total processes
297
Monitored processes
17
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1488 | "C:\Users\admin\AppData\Local\Temp\is-5ETJK.tmp\is-BEL3B.tmp" /SL4 $70374 C:\Users\admin\AppData\Local\Temp\INSTALAR.EXE.exe 9646648 46592 | C:\Users\admin\AppData\Local\Temp\is-5ETJK.tmp\is-BEL3B.tmp | INSTALAR.EXE.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2120 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RegAsm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3608 | "C:\WINDOWS\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" "C:\Program Files (x86)\PIMISYS\RICOAGNT\netPIMIRETEAGENTECli.DLL" /silent /nologo /codebase /tlb | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | — | is-BEL3B.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 3680 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --wake --system | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 3908 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RegAsm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3976 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4084 | "C:\WINDOWS\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" "C:\Program Files (x86)\PIMISYS\RICOAGNT\uninst\PIMIRETEAGENTECli.DLL" /silent /nologo /tlb /unregister | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | — | is-BEL3B.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 4784 | runonce.exe /Explorer | C:\Windows\System32\runonce.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4824 | C:\WINDOWS\SysWOW64\runonce.exe /RunOnce6432 | C:\Windows\SysWOW64\runonce.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5060 | "C:\Windows\is-KG7EB.exe" /REG | C:\Windows\is-KG7EB.exe | — | runonce.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
3 500
Read events
2 465
Write events
893
Delete events
142
Modification events
| (PID) Process: | (1488) is-BEL3B.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\CRXF_PDF.DLL |
Value: 1 | |||
| (PID) Process: | (1488) is-BEL3B.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\CRXLAT32.DLL |
Value: 1 | |||
| (PID) Process: | (1488) is-BEL3B.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\CRYSTL32.OCX |
Value: 1 | |||
| (PID) Process: | (1488) is-BEL3B.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\EXLATE32.DLL |
Value: 1 | |||
| (PID) Process: | (1488) is-BEL3B.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\P2CTDAO.DLL |
Value: 1 | |||
| (PID) Process: | (1488) is-BEL3B.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\P2LIFMX.DLL |
Value: 1 | |||
| (PID) Process: | (1488) is-BEL3B.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\P2LSQL.DLL |
Value: 1 | |||
| (PID) Process: | (1488) is-BEL3B.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\P2SMAPI.DLL |
Value: 1 | |||
| (PID) Process: | (1488) is-BEL3B.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\P2SOLEDB.DLL |
Value: 1 | |||
| (PID) Process: | (1488) is-BEL3B.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\CRPE32.DEP |
Value: 1 | |||
Executable files
184
Suspicious files
62
Text files
10
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1488 | is-BEL3B.tmp | C:\Windows\SysWOW64\is-66LF9.tmp | binary | |
MD5:BF6525E88423C0E912D96120E5D56637 | SHA256:CF508F2176A551C130F4381B354C47A23E5881D09DF803D7BAA2C3BBD3AB0FB7 | |||
| 1488 | is-BEL3B.tmp | C:\Users\admin\AppData\Local\Temp\is-J1LV2.tmp\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 5764 | INSTALAR.EXE.exe | C:\Users\admin\AppData\Local\Temp\is-5ETJK.tmp\is-BEL3B.tmp | executable | |
MD5:5D121A8B3124CA576F707B1195D1FD7F | SHA256:B6B9B3C14C7A2EC0834A90FF416F0254FE6D7722EBCBF13F95587E2801ED5520 | |||
| 1488 | is-BEL3B.tmp | C:\Users\admin\AppData\Local\Temp\is-J1LV2.tmp\isxdl.dll | executable | |
MD5:997A36E9E1DBBF7E280B52B4603327B3 | SHA256:80724CCCC8487F37E76FF3D970A898E628FCAB4C707BA6BFEF7F332FBC9553BB | |||
| 1488 | is-BEL3B.tmp | C:\Program Files (x86)\PIMISYS\uninst\unins000.exe | executable | |
MD5:FF47828B25EBF1F884C58A2A74BD9B90 | SHA256:6BA62AF4C825DB157B0D0EC11A3D0EC9352714FA17EFD223AC90B00F93B6AE2B | |||
| 1488 | is-BEL3B.tmp | C:\Windows\SysWOW64\CRXLAT32.DLL | executable | |
MD5:7D33AE1FC01E63DEE1A452A1DDFDFC95 | SHA256:1028432A6C023BEED6073CD496ACADF8AF795A925EEBD89FF61DD5B7EBDECDE9 | |||
| 1488 | is-BEL3B.tmp | C:\Program Files (x86)\PIMISYS\uninst\is-ATGKN.tmp | executable | |
MD5:FF47828B25EBF1F884C58A2A74BD9B90 | SHA256:6BA62AF4C825DB157B0D0EC11A3D0EC9352714FA17EFD223AC90B00F93B6AE2B | |||
| 1488 | is-BEL3B.tmp | C:\Windows\SysWOW64\is-KE7RS.tmp | executable | |
MD5:1015DA7E35A2B86165D653838D380811 | SHA256:804D3EDC1DCDDFDEC90FA40A659DB0C05F8935B980ADAAEF63ED696D62AEADA3 | |||
| 1488 | is-BEL3B.tmp | C:\Windows\SysWOW64\CRPE32.DEP | binary | |
MD5:BF6525E88423C0E912D96120E5D56637 | SHA256:CF508F2176A551C130F4381B354C47A23E5881D09DF803D7BAA2C3BBD3AB0FB7 | |||
| 1488 | is-BEL3B.tmp | C:\Windows\SysWOW64\CRPE32.DLL | executable | |
MD5:E907B99A242FAC081452BCF7F7E33549 | SHA256:EF509C948C3048825BC1B9EDAB1BFE5E9910E3A85FDB04A0ED1643791A942DAC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
69
DNS requests
36
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5532 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5684 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5556 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:gTfZzvnp-7mGwsoSC6S5gWvKqCYiDDt6mQXaseQ3csk&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6632 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
4672 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5116 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5252 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
56.163.245.4.in-addr.arpa |
| unknown |