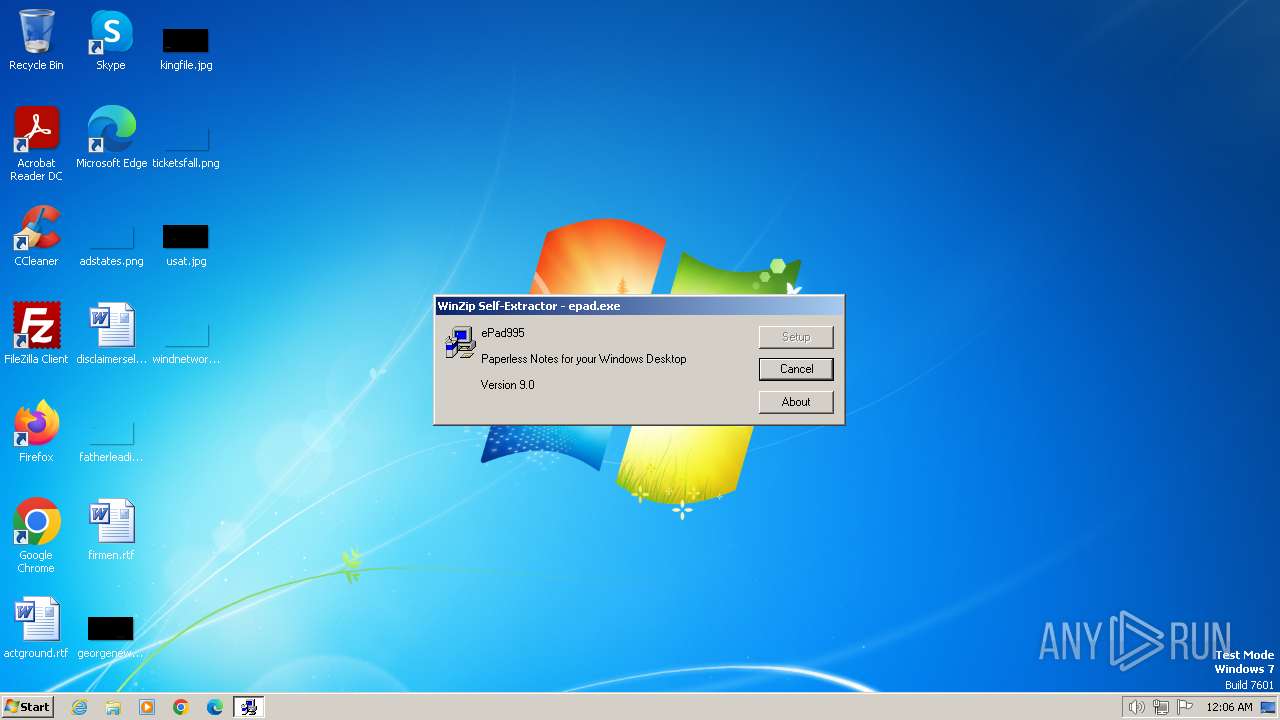
| File name: | epad.exe |
| Full analysis: | https://app.any.run/tasks/03c527c8-e2d1-4588-835b-7c8bd65e4af1 |
| Verdict: | Malicious activity |
| Analysis date: | March 20, 2024, 00:05:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 381E2EA63A1AEF1D644DCC7C4E380416 |
| SHA1: | 91DD7E40EE4F31E2DFA59AF6446EA7DEBF90F6C9 |
| SHA256: | 479AFADC9DA70051B93C6992B90F4D5C3DBE9D7CB63B8FAC945F196D3A366AC1 |
| SSDEEP: | 98304:dUI5tQA9WAEddugmOguU0K9oF6MvIeYcJ9LXAg4N38HZBArxyeALAICNTA7AdUws:cx+c4g |
MALICIOUS
Drops the executable file immediately after the start
- epad.exe (PID: 2908)
- thinsetup.exe (PID: 2672)
Create files in the Startup directory
- thinsetup.exe (PID: 2672)
SUSPICIOUS
Process drops legitimate windows executable
- epad.exe (PID: 2908)
- thinsetup.exe (PID: 2672)
The process drops C-runtime libraries
- thinsetup.exe (PID: 2672)
- epad.exe (PID: 2908)
Executable content was dropped or overwritten
- epad.exe (PID: 2908)
- thinsetup.exe (PID: 2672)
Creates a software uninstall entry
- thinsetup.exe (PID: 2672)
Reads the Internet Settings
- thinsetup.exe (PID: 2672)
INFO
Checks supported languages
- epad.exe (PID: 2908)
- thinsetup.exe (PID: 2672)
- splash.exe (PID: 956)
Reads the computer name
- thinsetup.exe (PID: 2672)
Creates files in the program directory
- thinsetup.exe (PID: 2672)
Create files in a temporary directory
- epad.exe (PID: 2908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (30.7) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (22.2) |
| .exe | | | Win64 Executable (generic) (19.7) |
| .exe | | | Winzip Win32 self-extracting archive (generic) (16.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:11:02 20:24:15+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 77824 |
| InitializedDataSize: | 40960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaf1e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
43
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP//splash.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\splash.exe | — | thinsetup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2672 | .\thinsetup.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\thinsetup.exe | epad.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: thinsetup MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2908 | "C:\Users\admin\AppData\Local\Temp\epad.exe" | C:\Users\admin\AppData\Local\Temp\epad.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3936 | "C:\Users\admin\AppData\Local\Temp\epad.exe" | C:\Users\admin\AppData\Local\Temp\epad.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
1 064
Read events
1 061
Write events
3
Delete events
0
Modification events
| (PID) Process: | (2672) thinsetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ePad995 |
| Operation: | write | Name: | DisplayName |
Value: ePad995 | |||
| (PID) Process: | (2672) thinsetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ePad995 |
| Operation: | write | Name: | UninstallString |
Value: c:\ePad995\thinsetup.exe - uninstall | |||
| (PID) Process: | (2672) thinsetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 116 | |||
Executable files
12
Suspicious files
3
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2908 | epad.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\about.gif | image | |
MD5:5CD121C985D948F04181ACC818071E54 | SHA256:2A4D8DF8FAB0F5F745DE75DCC61114C0B866FE4D95CEFEE4402FC6302EBB9955 | |||
| 2908 | epad.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\masthead.gif | image | |
MD5:7DE69AFFECAE191D181078E7E479CC97 | SHA256:4E8AC025806AC6E1567139C52312B859A69ABAEDEEA508E2C93161980555DDE1 | |||
| 2908 | epad.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\ePad995.exe | executable | |
MD5:FCC1478C35C4D9018E7999159227A19F | SHA256:E698E5A5B30C42BCAA339C19D0D424908402671ED750BBBA41C389F2C5FC9676 | |||
| 2908 | epad.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\ep995.css | text | |
MD5:6CEFAFFF6FA9C049C9FC0BCE24AD2897 | SHA256:8F9A0FB91CB5FC4B3D9670F3AE04BD4777FA3D5C67D17C52E712C1AAFB508827 | |||
| 2908 | epad.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\download.gif | image | |
MD5:1EB89A7198D939F556608EC67D440D1D | SHA256:145F0BE40825840067A2DEE2ACCA62AD817DA513FC4E9475050F81102D43E6DB | |||
| 2908 | epad.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\masthead_rule.gif | image | |
MD5:DB5753F14C154D21E4BE7EF52F33DE35 | SHA256:25187209929AA03B058708DC762EA52E700B59255E564BA8E685D744350FAFF9 | |||
| 2908 | epad.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\ePad995.jpg | image | |
MD5:BC41323E06DD6392F9762564623BB1CB | SHA256:F949839F4729A0AA42A358A4ACDE76DA031AFA37383FE5E48C929B1FF7BAD33B | |||
| 2908 | epad.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\thinsetup.exe | executable | |
MD5:A014D31121CDC090F79C966092FA8129 | SHA256:F0AC645D6166FE962264C704BCCFE7947394B27DA4EBDD0089931731A5BD3ADC | |||
| 2672 | thinsetup.exe | C:\ePad995\download.gif | image | |
MD5:1EB89A7198D939F556608EC67D440D1D | SHA256:145F0BE40825840067A2DEE2ACCA62AD817DA513FC4E9475050F81102D43E6DB | |||
| 2908 | epad.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\mfc100.dll | executable | |
MD5:07BCCDCC337D393D7DB0B2F8FE200B3F | SHA256:BF38DDA13B938B49A4DF72B6477342373EE6E151BE12C25CB0C17662FCB4BCD4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |