| File name: | ymsgres.exe |
| Full analysis: | https://app.any.run/tasks/01e7c6c3-f140-4b46-a356-cfd3031b016e |
| Verdict: | Malicious activity |
| Analysis date: | January 16, 2024, 18:45:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C93DC3397F828D0080466250B3BC69CE |
| SHA1: | 61814880C79DAADDFC87FBEB501EF9F87AE7D055 |
| SHA256: | 47992A3EFBA1DB0A465322C5D227E2E48E6BF3E65D21FA201DF82860F147EC7D |
| SSDEEP: | 98304:03/jJcWr3O87TR8jdED3yXj4nxVJHwVFXFxgcQnEy5WaEu6Svu52D+eB6QpvvWWU:Uy+U |
MALICIOUS
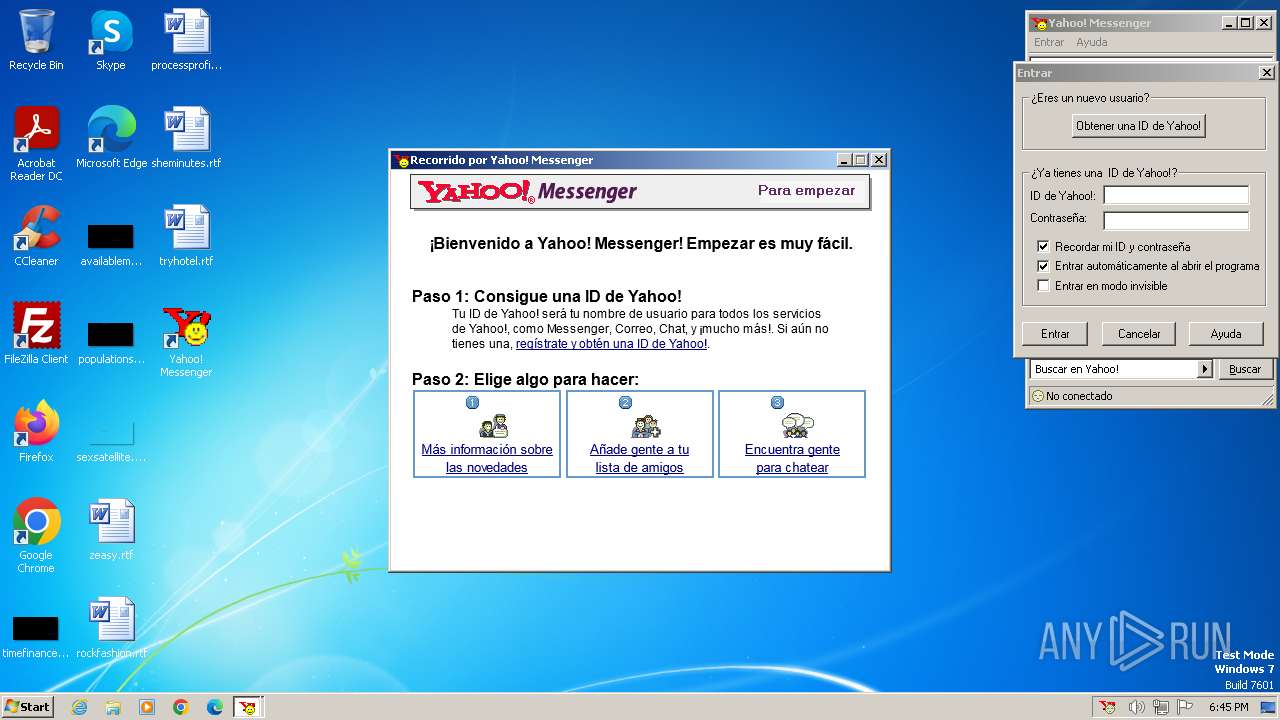
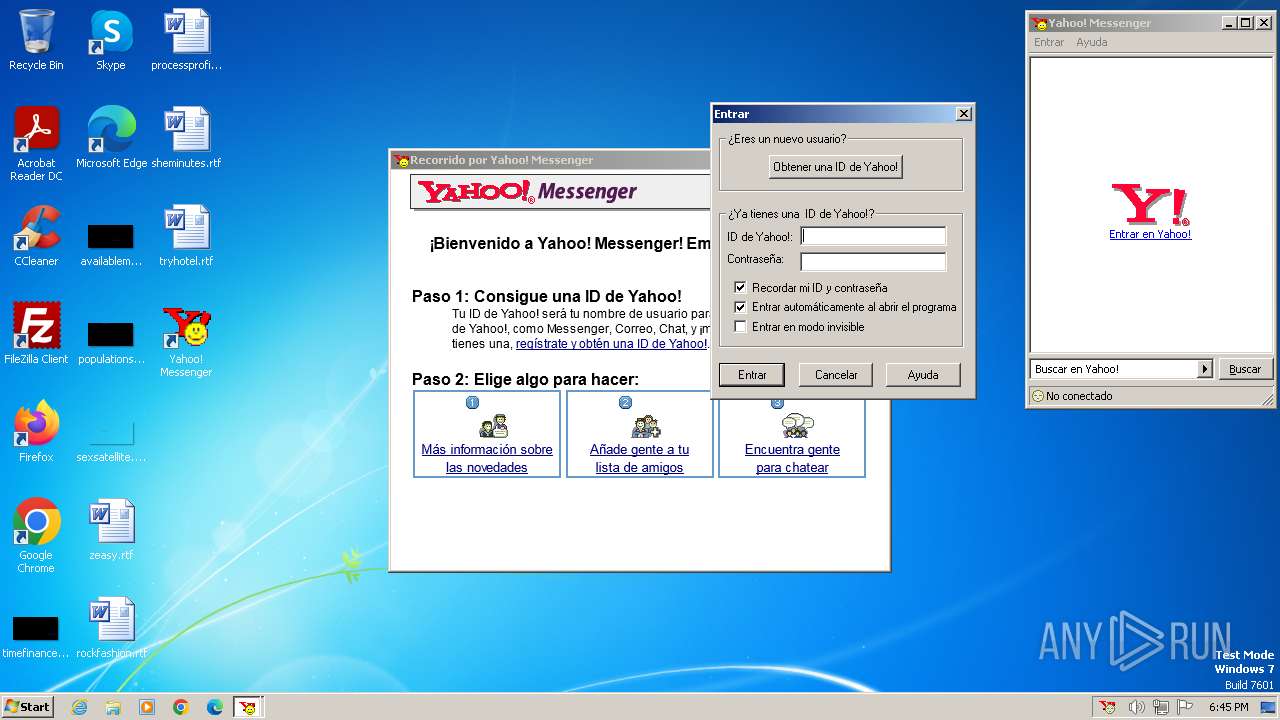
Drops the executable file immediately after the start
- ymsgres.exe (PID: 2208)
Scans artifacts that could help determine the target
- YPager.exe (PID: 1816)
- YPager.exe (PID: 1900)
SUSPICIOUS
Executable content was dropped or overwritten
- ymsgres.exe (PID: 2208)
- ntvdm.exe (PID: 2420)
Reads the Internet Settings
- ntvdm.exe (PID: 2420)
- YPager.exe (PID: 1900)
Uses REG/REGEDIT.EXE to modify registry
- ntvdm.exe (PID: 2420)
- YPager.exe (PID: 1900)
Starts application with an unusual extension
- ntvdm.exe (PID: 2420)
Reads Microsoft Outlook installation path
- YPager.exe (PID: 1900)
Reads Internet Explorer settings
- YPager.exe (PID: 1900)
Creates/Modifies COM task schedule object
- ~GLJ3069.TMP (PID: 1264)
- ~GLJ3069.TMP (PID: 1576)
INFO
Checks supported languages
- ymsgres.exe (PID: 2208)
- ~GLJ3069.TMP (PID: 1772)
- ~GLJ3069.TMP (PID: 1588)
- ~GLJ3069.TMP (PID: 1780)
- ~GLJ3069.TMP (PID: 1840)
- ~GLJ3069.TMP (PID: 1264)
- ~GLJ3069.TMP (PID: 1112)
- ~GLJ3069.TMP (PID: 1972)
- ~GLJ3069.TMP (PID: 1576)
- YServer.exe (PID: 1592)
- ~GLJ3069.TMP (PID: 1804)
- YPager.exe (PID: 1900)
- YPager.exe (PID: 1816)
- Ymsgr_tray.exe (PID: 1732)
- ~GLJ3069.TMP (PID: 1928)
- ~GLJ3069.TMP (PID: 2168)
- ~GLJ3069.TMP (PID: 712)
- Ymsgr_tray.exe (PID: 1852)
Create files in a temporary directory
- ymsgres.exe (PID: 2208)
- ntvdm.exe (PID: 2420)
Creates files in the program directory
- ntvdm.exe (PID: 2420)
Drops the executable file immediately after the start
- ntvdm.exe (PID: 2420)
Reads the computer name
- ~GLJ3069.TMP (PID: 1264)
- ~GLJ3069.TMP (PID: 1804)
- YPager.exe (PID: 1816)
- YPager.exe (PID: 1900)
- ~GLJ3069.TMP (PID: 1576)
Creates files or folders in the user directory
- ntvdm.exe (PID: 2420)
Reads the machine GUID from the registry
- YPager.exe (PID: 1900)
Checks proxy server information
- YPager.exe (PID: 1900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ 4.x (88.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (4.3) |
| .exe | | | Win32 Executable (generic) (2.9) |
| .exe | | | Win16/32 Executable Delphi generic (1.3) |
| .exe | | | Generic Win/DOS Executable (1.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1997:06:16 23:32:11+02:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 4.2 |
| CodeSize: | 512 |
| InitializedDataSize: | 2491392 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
65
Monitored processes
28
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Users\admin\AppData\Local\Temp\ymsgres.exe" | C:\Users\admin\AppData\Local\Temp\ymsgres.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 188 | C:\Windows\regedit.exe /s "C:\PROGRA~1\Yahoo!\MESSEN~1\Default.reg" | C:\Windows\regedit.exe | — | YPager.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 712 | "C:\Users\admin\AppData\Local\Temp\~GLJ3069.TMP" C:\PROGRA~1\Yahoo!\MESSEN~1\ft.dll | C:\Users\admin\AppData\Local\Temp\~GLJ3069.TMP | — | ntvdm.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1112 | "C:\Users\admin\AppData\Local\Temp\~GLJ3069.TMP" C:\PROGRA~1\Yahoo!\MESSEN~1\MyYahoo.dll | C:\Users\admin\AppData\Local\Temp\~GLJ3069.TMP | — | ntvdm.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1264 | "C:\Users\admin\AppData\Local\Temp\~GLJ3069.TMP" C:\PROGRA~1\Yahoo!\MESSEN~1\ypagerps.dll | C:\Users\admin\AppData\Local\Temp\~GLJ3069.TMP | — | ntvdm.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1344 | C:\Windows\regedit.exe /s "C:\Program Files\Yahoo!\Messenger\intl.reg" | C:\Windows\regedit.exe | — | ntvdm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1544 | C:\Windows\regedit.exe /s "C:\PROGRA~1\Yahoo!\MESSEN~1\default.reg" | C:\Windows\regedit.exe | — | ntvdm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1576 | "C:\Users\admin\AppData\Local\Temp\~GLJ3069.TMP" C:\PROGRA~1\Yahoo!\MESSEN~1\proxy.dll | C:\Users\admin\AppData\Local\Temp\~GLJ3069.TMP | — | ntvdm.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1588 | "C:\Users\admin\AppData\Local\Temp\~GLJ3069.TMP" C:\PROGRA~1\Yahoo!\MESSEN~1\yacscom.dll | C:\Users\admin\AppData\Local\Temp\~GLJ3069.TMP | — | ntvdm.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1592 | C:\PROGRA~1\Yahoo!\MESSEN~1\YServer.exe /REGSERVER | C:\Program Files\Yahoo!\Messenger\YServer.exe | — | ntvdm.exe | |||||||||||
User: admin Company: Yahoo! Inc. Integrity Level: HIGH Description: YServer Module Exit code: 0 Version: 2, 0, 0, 6 Modules
| |||||||||||||||
Total events
5 257
Read events
4 541
Write events
711
Delete events
5
Modification events
| (PID) Process: | (2420) ntvdm.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2420) ntvdm.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2420) ntvdm.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2420) ntvdm.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1344) regedit.exe | Key: | HKEY_CURRENT_USER\Software\Yahoo\Pager |
| Operation: | write | Name: | PreLogin |
Value: http://msg.edit.yahoo.com/config/ | |||
| (PID) Process: | (1344) regedit.exe | Key: | HKEY_CURRENT_USER\Software\Yahoo\Pager\IMUnified |
| Operation: | write | Name: | Disable Imip |
Value: 1 | |||
| (PID) Process: | (1344) regedit.exe | Key: | HKEY_CURRENT_USER\Software\Yahoo\Pager\yurl |
| Operation: | write | Name: | Finance Disclaimer |
Value: http://msg.edit.yahoo.com/config/jlb | |||
| (PID) Process: | (1576) ~GLJ3069.TMP | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-500_CLASSES\CLSID\{CAFEEFAC-0017-0000-0129-ABCDEFFEDCBC}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (1576) ~GLJ3069.TMP | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-500_CLASSES\CLSID\{CAFEEFAC-0017-0000-0130-ABCDEFFEDCBB}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (1576) ~GLJ3069.TMP | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-500_CLASSES\CLSID\{CAFEEFAC-0017-0000-0131-ABCDEFFEDCBB}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
Executable files
71
Suspicious files
96
Text files
264
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2420 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs1307.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 2420 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs1308.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2420 | ntvdm.exe | C:\USERS\ADMIN\APPDATA\LOCAL\TEMP\~GLJ3069.TMP | executable | |
MD5:6F608D264503796BEBD7CD66B687BE92 | SHA256:49833D2820AFB1D7409DFBD916480F2CDF5787D2E2D94166725BEB9064922D5D | |||
| 2208 | ymsgres.exe | C:\Users\admin\AppData\Local\Temp\GLB12B8.tmp | executable | |
MD5:2E95CF9158819AB5528CB6EFADADFB2E | SHA256:1808F34FC73295E66506D0E97DB0DF936A822855421D7CC57A5DD117F5037F50 | |||
| 2420 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\~GL_316E.EXE | executable | |
MD5:815372073DA85B2098A37DED84083C8A | SHA256:166E8FE44186F356E162CEAC313100D0992B70D3A6A029906C2242AFC8691C85 | |||
| 2420 | ntvdm.exe | C:\Windows\~GLH0000.TMP | executable | |
MD5:3880BDC203719F808345CCFDF9A74066 | SHA256:79A6D0024D14A70D7F739AB98B87670D0415A5EEEDA772DEC9F15EFE3572A427 | |||
| 2420 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\~GLF3706.TMP | executable | |
MD5:EE137AA648F5A30F5522A48C176BF13C | SHA256:3E0C4E282A232B65F22911A4AB25C7B8F84660DC52A2A2BC4F1A90892AD02472 | |||
| 2420 | ntvdm.exe | C:\Program Files\Yahoo!\Messenger\~GLH0005.TMP | executable | |
MD5:0938040C3F7EA59B340CBA84BBF1D875 | SHA256:EB89C26F108B4806920A5089C472C7F89C616D56AAE8D6F95594ABA55AF45C8C | |||
| 2420 | ntvdm.exe | C:\Program Files\Yahoo!\Messenger\UNWISE.INI | text | |
MD5:F75488B1D6EDF55BE39557E20D915715 | SHA256:B04933660A1D01503D0C6AD2E578EC47F0BD1C618CE4689813B121CC568D817F | |||
| 2420 | ntvdm.exe | C:\Program Files\Yahoo!\Messenger\UNWISE.EXE | executable | |
MD5:0938040C3F7EA59B340CBA84BBF1D875 | SHA256:EB89C26F108B4806920A5089C472C7F89C616D56AAE8D6F95594ABA55AF45C8C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |