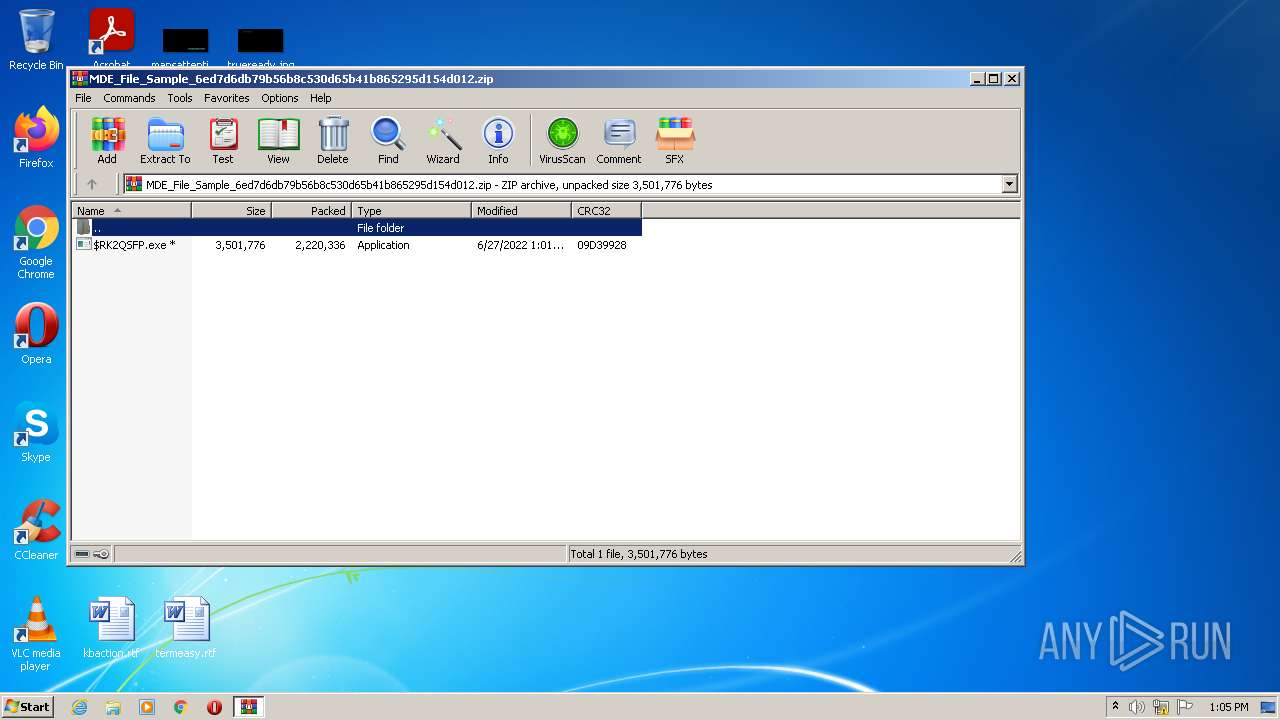
| File name: | MDE_File_Sample_6ed7d6db79b56b8c530d65b41b865295d154d012.zip |
| Full analysis: | https://app.any.run/tasks/b29c9491-d3ee-44ef-89b1-9378b1e158e8 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 12:05:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | DC8AEE97E40F5D67ADFFFB1B07B831B8 |
| SHA1: | 3075E7DBEF57DD2921F4254B941B0CCDBC8D8D79 |
| SHA256: | 476463C2D6D316216FBBBB15B650482F877031E03288DDC2178DB1C5C6221843 |
| SSDEEP: | 49152:EHJ8QfKcBOwZn/huw93vfBzw5badsxEjsQWDvMsYemi5xG2mYkd:EDkwZn4w93BzwbadzQZDksDNG3d |
MALICIOUS
Application was dropped or rewritten from another process
- $RK2QSFP.exe (PID: 1840)
- $RK2QSFP.exe (PID: 1268)
Drops executable file immediately after starts
- WinRAR.exe (PID: 2624)
Actions looks like stealing of personal data
- $RK2QSFP.exe (PID: 1268)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2624)
- $RK2QSFP.exe (PID: 1268)
Checks supported languages
- WinRAR.exe (PID: 2624)
- $RK2QSFP.exe (PID: 1268)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2624)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2624)
Reads Microsoft Outlook installation path
- $RK2QSFP.exe (PID: 1268)
Reads internet explorer settings
- $RK2QSFP.exe (PID: 1268)
INFO
Dropped object may contain Bitcoin addresses
- $RK2QSFP.exe (PID: 1268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | $RK2QSFP.exe |
|---|---|
| ZipUncompressedSize: | 3501776 |
| ZipCompressedSize: | 2220336 |
| ZipCRC: | 0x09d39928 |
| ZipModifyDate: | 2022:06:27 12:01:03 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 20 |
Total processes
38
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1268 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2624.18064\$RK2QSFP.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2624.18064\$RK2QSFP.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0 Modules
| |||||||||||||||
| 1840 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2624.18064\$RK2QSFP.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2624.18064\$RK2QSFP.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.0 Modules
| |||||||||||||||
| 2624 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\MDE_File_Sample_6ed7d6db79b56b8c530d65b41b865295d154d012.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 480
Read events
1 449
Write events
31
Delete events
0
Modification events
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MDE_File_Sample_6ed7d6db79b56b8c530d65b41b865295d154d012.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
0
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2624.18064\$RK2QSFP.exe | executable | |
MD5:3632F27604F5A82CF73B9ADE710A1656 | SHA256:4B34E3637FA7AF93AB628AE5ADAD2C7F3464053316963297844324A4F649A206 | |||
| 1268 | $RK2QSFP.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\curl-ca-bundle.crt | text | |
MD5:BE2B0736EA029FFF398559FA7DF4E646 | SHA256:C05A79296D61E3B2A2EBAF5AF476839B976D69A5ACB6F581A667E60E681049A2 | |||
| 1268 | $RK2QSFP.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\Montserrat-Regular.eot | eot | |
MD5:2DD0A1DE870AF34D48D43B7CAD82B8D9 | SHA256:057BC6C47C47AACCDF31ADC48A6B401F6090A02C28E354099EFF80907DC2AF32 | |||
| 1268 | $RK2QSFP.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\VerdanaPro-Regular.eot | eot | |
MD5:8CED6BD6A0A63B27EE3B18E0B679F8AC | SHA256:A59FFC5ABE4274FC224C8EDCB5877C94AF974C949FD391B056265F470E08CDF9 | |||
| 1268 | $RK2QSFP.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\page-wait.png | image | |
MD5:A8210694C45753A7A027296EF745E316 | SHA256:14DE6662062ADC45202E2021AA4D60E98637DC892A22ACB2C7CC16DA3344C14D | |||
| 1268 | $RK2QSFP.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\preloader.html | html | |
MD5:2E27CD9ADDC9B7EEF2CE2E0520BF75C5 | SHA256:EBE5989FC69C4CF0508F190EED7D787A98063F768BC2B41A6B095AC8A8AB5C6C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | $RK2QSFP.exe | 51.158.184.220:443 | mediaget.com | — | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mediaget.com |
| suspicious |