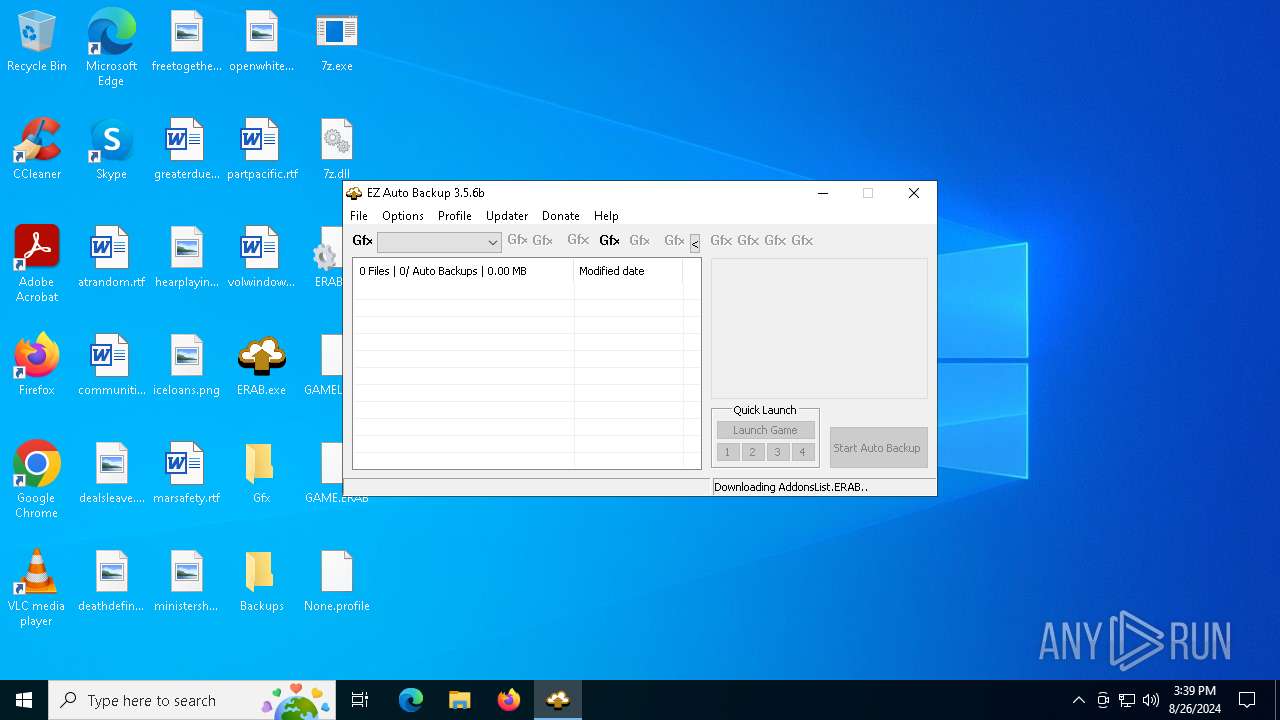
| File name: | ERAB.exe |
| Full analysis: | https://app.any.run/tasks/017b9e58-87f9-4ce3-b0c7-0df02e72c38d |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2024, 15:39:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | DFA3BC45245A6F8F6C7085E625AFBB99 |
| SHA1: | 6681658325E03CAE168AA15455E9380F9DBFB8A6 |
| SHA256: | 475525D4CBAB512F143238013112EFA360DE9FA46DBBA201A7219D50C69E0697 |
| SSDEEP: | 98304:VCysPt+uc4c69aOSdyzjZpm7hj52H+dwfcJdZrtq+gYV7CXxV:ir |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops the executable file immediately after the start
- ERAB.exe (PID: 3304)
- ERAB.exe (PID: 6420)
Reads security settings of Internet Explorer
- ERAB.exe (PID: 3304)
- ERAB.exe (PID: 6420)
Reads the date of Windows installation
- ERAB.exe (PID: 3304)
Drops 7-zip archiver for unpacking
- ERAB.exe (PID: 6420)
Executable content was dropped or overwritten
- ERAB.exe (PID: 6420)
Application launched itself
- ERAB.exe (PID: 3304)
There is functionality for taking screenshot (YARA)
- ERAB.exe (PID: 6420)
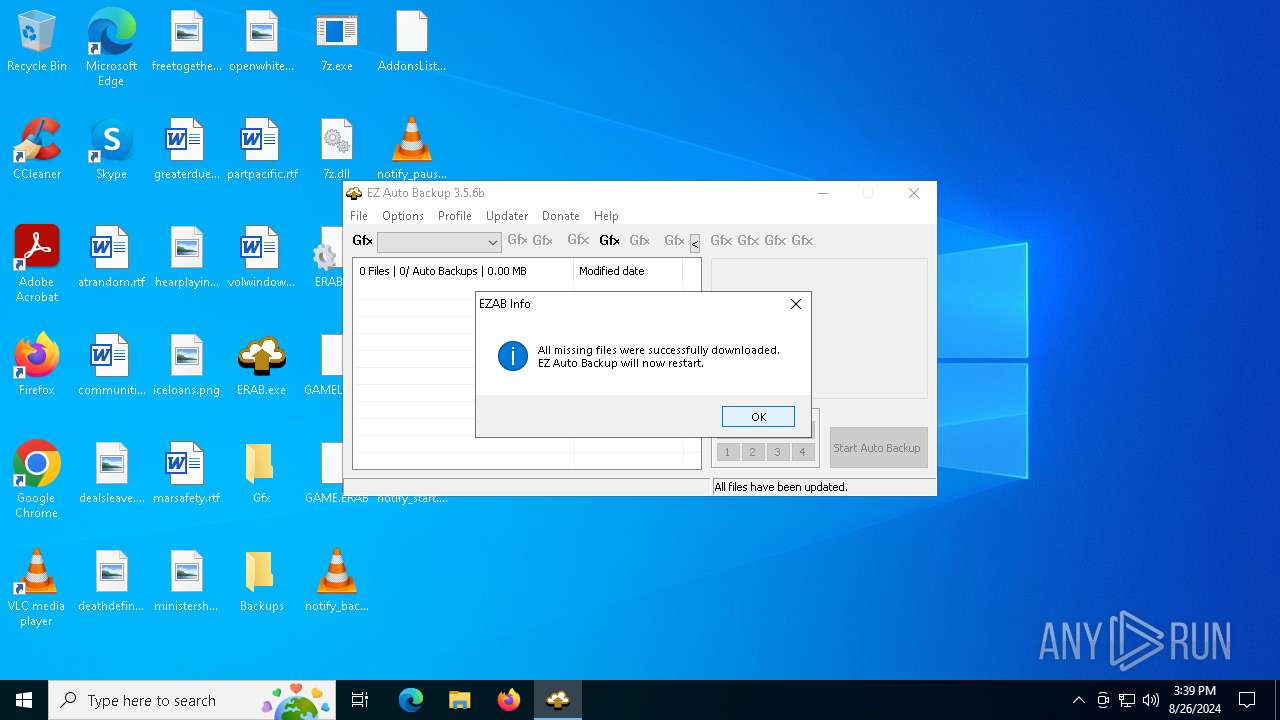
Process requests binary or script from the Internet
- ERAB.exe (PID: 6420)
The process creates files with name similar to system file names
- ERAB.exe (PID: 6420)
INFO
Reads the computer name
- ERAB.exe (PID: 3304)
- ERAB.exe (PID: 6420)
Process checks computer location settings
- ERAB.exe (PID: 3304)
Checks supported languages
- ERAB.exe (PID: 6420)
- ERAB.exe (PID: 3304)
Checks proxy server information
- ERAB.exe (PID: 6420)
Reads the machine GUID from the registry
- ERAB.exe (PID: 6420)
Reads the software policy settings
- ERAB.exe (PID: 6420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (35.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (31.7) |
| .scr | | | Windows screen saver (15) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.5) |
| .exe | | | Win32 Executable (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:08 05:25:57+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 657408 |
| InitializedDataSize: | 2307584 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x93a73 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.37.1 |
| ProductVersionNumber: | 1.1.37.1 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | - |
| FileVersion: | 1.1.37.01 |
| InternalName: | - |
| LegalCopyright: | - |
| CompanyName: | - |
| OriginalFileName: | - |
| ProductName: | - |
| ProductVersion: | 1.1.37.01 |
Total processes
121
Monitored processes
2
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3304 | "C:\Users\admin\Desktop\ERAB.exe" | C:\Users\admin\Desktop\ERAB.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.1.37.01 Modules
| |||||||||||||||
| 6420 | "C:\Users\admin\Desktop\ERAB.exe" | C:\Users\admin\Desktop\ERAB.exe | ERAB.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.1.37.01 Modules
| |||||||||||||||
Total events
4 319
Read events
4 303
Write events
16
Delete events
0
Modification events
| (PID) Process: | (3304) ERAB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3304) ERAB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3304) ERAB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3304) ERAB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6420) ERAB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6420) ERAB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6420) ERAB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6420) ERAB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
2
Suspicious files
5
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6420 | ERAB.exe | C:\Users\admin\Desktop\Gfx\CoOp.ico | image | |
MD5:CB204FE297DD57FA8ED62B4B159D1DDD | SHA256:75AFF0DF5C3BA1E686B3018A84B60A1059B13C698C6F973B28667CB0FEDA1F67 | |||
| 6420 | ERAB.exe | C:\Users\admin\Desktop\7z.exe | executable | |
MD5:62D2156E3CA8387964F7AA13DD1CCD5B | SHA256:59CBFBA941D3AC0238219DAA11C93969489B40F1E8B38FABDB5805AC3DD72BFA | |||
| 6420 | ERAB.exe | C:\Users\admin\Desktop\None.profile | text | |
MD5:F1E50EB9EEC1A481A95309F30541601B | SHA256:626BD47A8EBA0901D4768ACB33D5802814BE2FEB0D5BF35A4D0FC0A282D7B04D | |||
| 6420 | ERAB.exe | C:\Users\admin\Desktop\Gfx\backup.png | image | |
MD5:774F4B2B1CD5F5A0093BFA42FB89E32A | SHA256:127BDA1FF96EEFC75A31D01F134AC3F6C41D21FD750104613612F9DD700B567F | |||
| 6420 | ERAB.exe | C:\Users\admin\Desktop\AddonsList.ERAB | text | |
MD5:4C6A9F86B4BDF33F36B6647CC39D0E19 | SHA256:CC8881DF2E1055E0D254C894F4A39B0E606112E58FF45DD897A4E3585C84F384 | |||
| 6420 | ERAB.exe | C:\Users\admin\Desktop\Gfx\autobackup.png | image | |
MD5:B07B7FD6ED04DBFE890EAE4FE0ABD664 | SHA256:4B20021E559DBDDC38E08CE2FC842ED9C9998B7BD339DE630B29F1A0659DD60C | |||
| 6420 | ERAB.exe | C:\Users\admin\Desktop\Gfx\default2.png | image | |
MD5:7DD045A8DC0E884B0A49F53ABF22D2D0 | SHA256:77096EEE1CE7B12EB8FE029DDE44705A8E19F7D449EB25910D717F645F1CAFB1 | |||
| 6420 | ERAB.exe | C:\Users\admin\Desktop\Gfx\autobackup1.png | image | |
MD5:010D10BFF06DAE3F17380EC3698B8089 | SHA256:8CAD0434E4B8D292C9BFD324B7EBE33AAAD8D77A06075065498DF51C2AF70944 | |||
| 6420 | ERAB.exe | C:\Users\admin\Desktop\Gfx\backup2.png | image | |
MD5:622AA8BC93B64C20A659461C75BC6930 | SHA256:D0279D24CB078D8BFCDEA63ADA6A5FF4A59A903060E0B528FC85D23F435FD4E4 | |||
| 6420 | ERAB.exe | C:\Users\admin\Desktop\Gfx\default1.png | image | |
MD5:B9F200F5750A5BB6CC59E95C7E0EE7CE | SHA256:A7B527FAFBCC7BD33439ECF05CB453DDC667141BC11FE79040771776284B198F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
17
DNS requests
4
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6420 | ERAB.exe | GET | 200 | 146.247.97.33:80 | http://asurastrike.de/ERAB/version2.txt | unknown | — | — | malicious |
6420 | ERAB.exe | GET | 200 | 146.247.97.33:80 | http://asurastrike.de/ERAB/files.txt | unknown | — | — | malicious |
6420 | ERAB.exe | GET | 200 | 146.247.97.33:80 | http://asurastrike.de/ERAB/autobackup.png | unknown | — | — | malicious |
6420 | ERAB.exe | GET | 200 | 146.247.97.33:80 | http://asurastrike.de/ERAB/autobackup1.png | unknown | — | — | malicious |
6420 | ERAB.exe | GET | 200 | 146.247.97.33:80 | http://asurastrike.de/ERAB/backup.png | unknown | — | — | malicious |
6420 | ERAB.exe | GET | 200 | 146.247.97.33:80 | http://asurastrike.de/ERAB/backup1.png | unknown | — | — | malicious |
6420 | ERAB.exe | GET | 200 | 146.247.97.33:80 | http://asurastrike.de/ERAB/GAMELIST.ERAB | unknown | — | — | malicious |
6420 | ERAB.exe | GET | 200 | 146.247.97.33:80 | http://asurastrike.de/ERAB/bugs.png | unknown | — | — | malicious |
6420 | ERAB.exe | GET | 200 | 146.247.97.33:80 | http://asurastrike.de/ERAB/backup2.png | unknown | — | — | malicious |
6420 | ERAB.exe | GET | 200 | 146.247.97.33:80 | http://asurastrike.de/ERAB/CoOp.ico | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6420 | ERAB.exe | 146.247.97.33:80 | asurastrike.de | MKQ Internetservice | DE | unknown |
4324 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6192 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6420 | ERAB.exe | 217.160.0.130:443 | reshade.me | IONOS SE | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
asurastrike.de |
| unknown |
reshade.me |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6420 | ERAB.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (AutoHotkey) |
6420 | ERAB.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (AutoHotkey) |