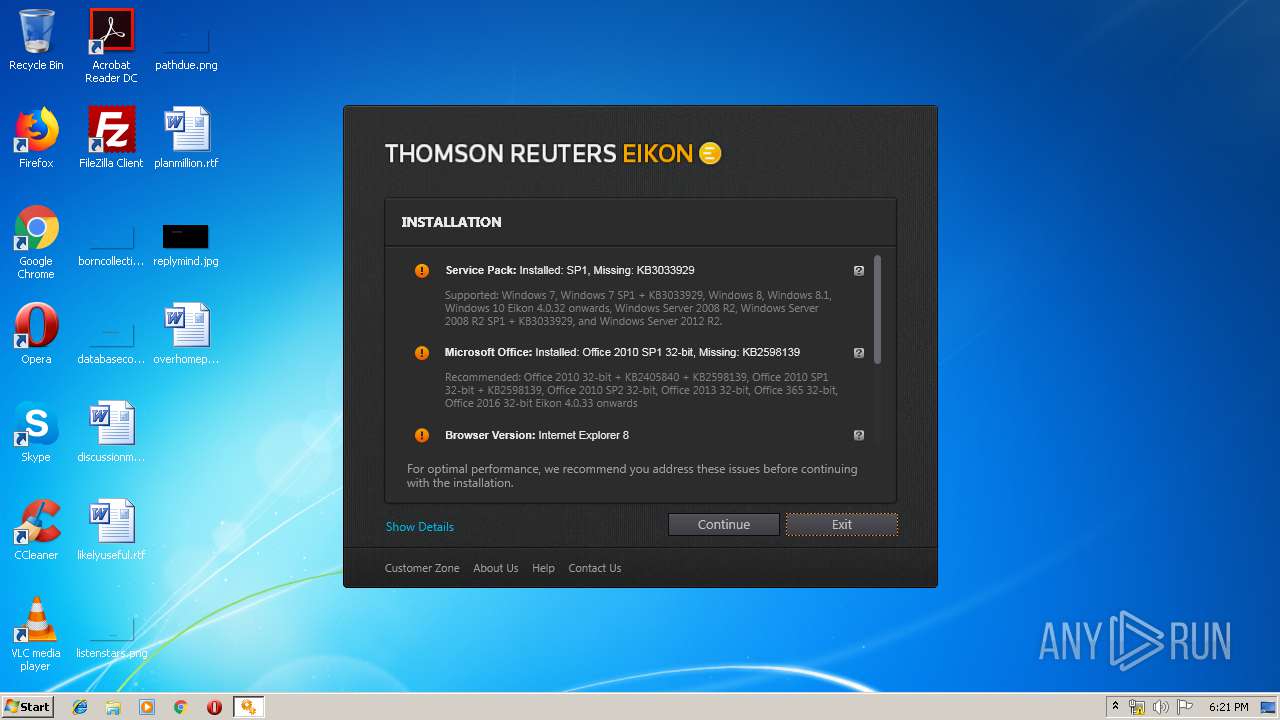
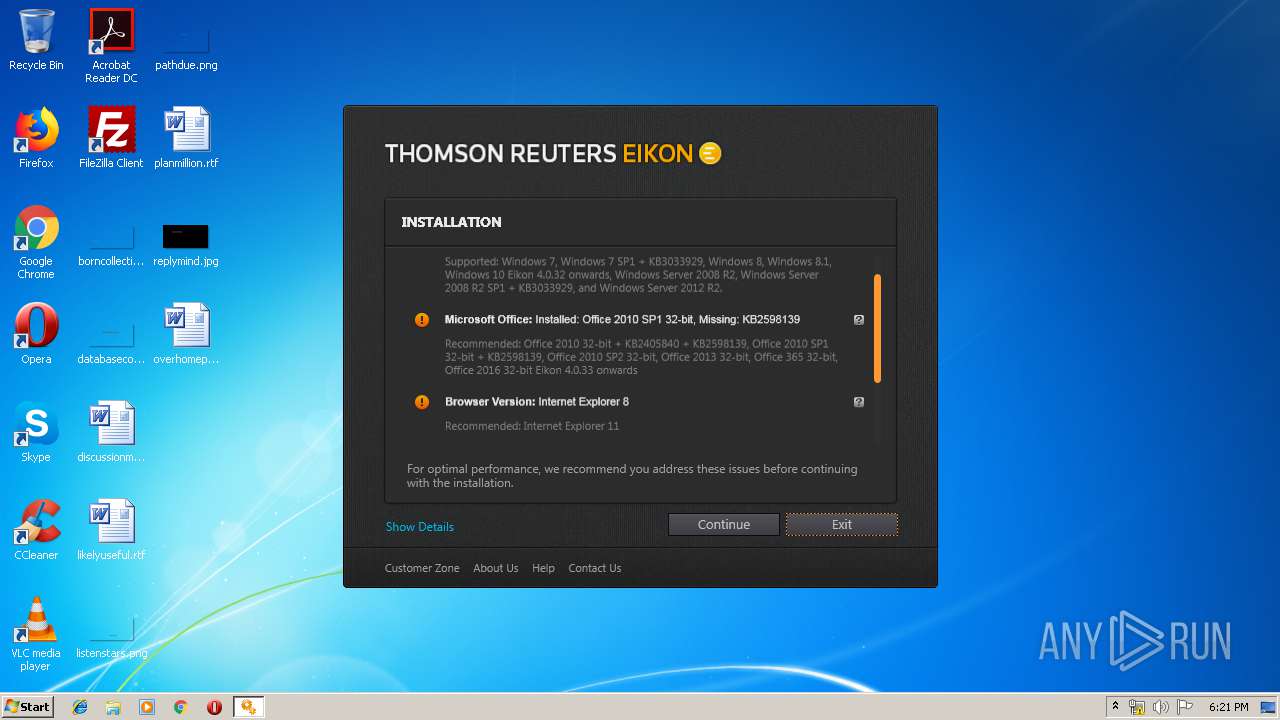
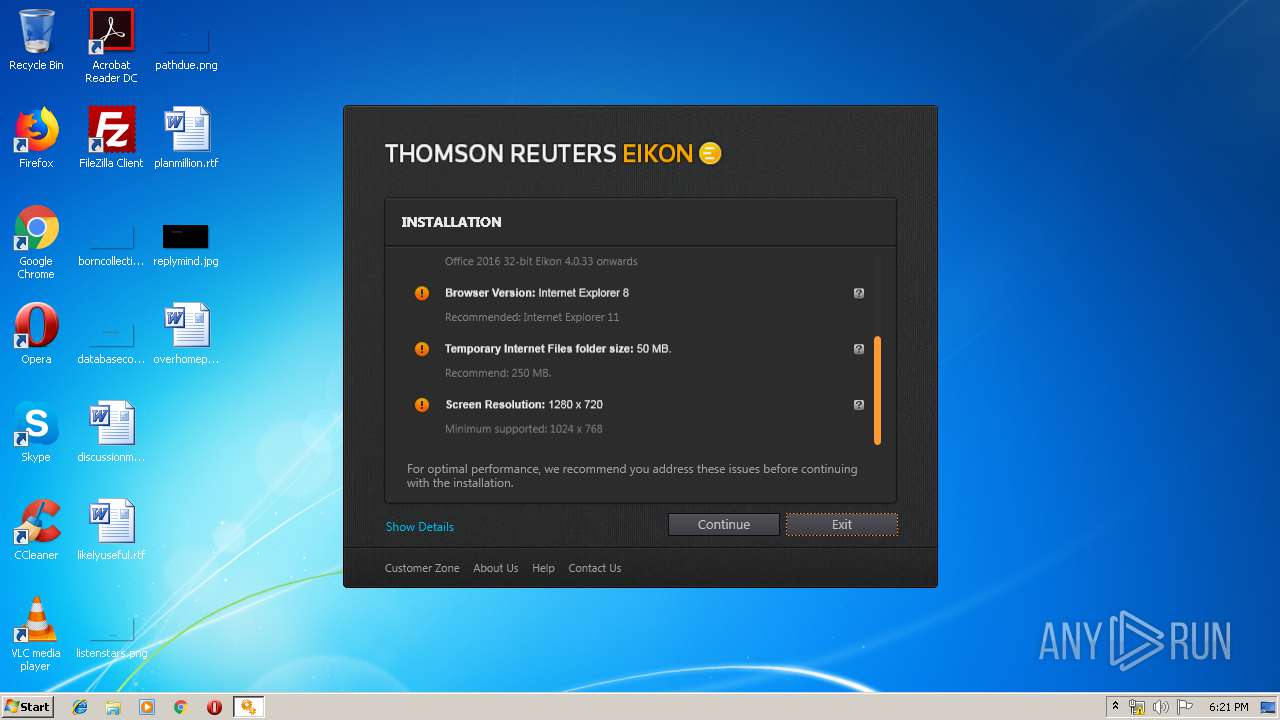
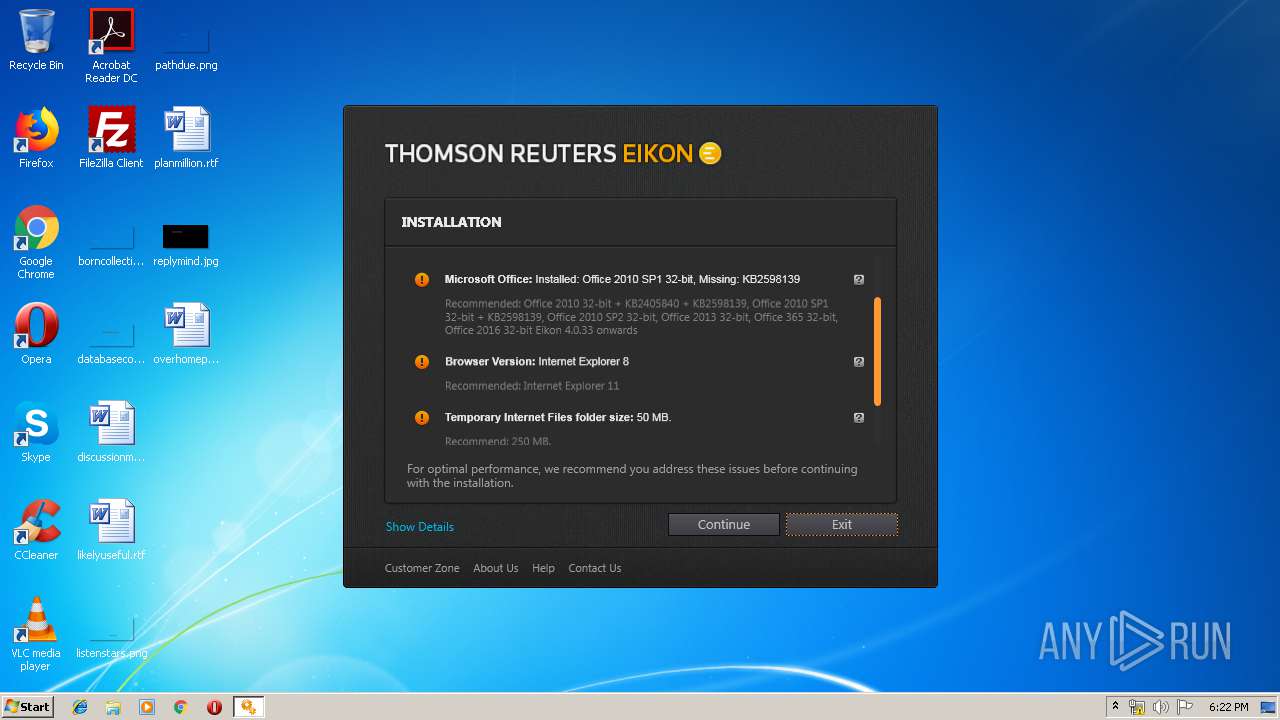
| File name: | EikonInstaller.exe |
| Full analysis: | https://app.any.run/tasks/730ebbb1-5f19-4289-a007-954f7bebd1e3 |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2019, 17:21:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 9F2E020724ED8709FB335E44CFDE7A54 |
| SHA1: | 3C10F8F722A07BE2C23826294BB4B35913DEF466 |
| SHA256: | 474B970CE066B2B75EDBFB5117A424612E1EAB33151172C134ED74B3995B35B4 |
| SSDEEP: | 49152:e4WU6Po4bpolUjicWBXhWCeIhFsw0Pelu8G5Uos6X+:eLbpsLlpePeoVOoh+ |
MALICIOUS
Application was dropped or rewritten from another process
- EikonInstaller.exe (PID: 1824)
- EikonDM.exe (PID: 1480)
- EikonDM.exe (PID: 2112)
- EikonDM.exe (PID: 4008)
- EikonDM.exe (PID: 2148)
- Eikon.exe (PID: 2172)
- Eikon.exe (PID: 3316)
- EikonBoxNet.exe (PID: 3360)
- ConnectionManagement.exe (PID: 1704)
Loads dropped or rewritten executable
- EikonInstaller.exe (PID: 3616)
- EikonInstaller.exe (PID: 1824)
- EikonDM.exe (PID: 1480)
- EikonDM.exe (PID: 2112)
- EikonDM.exe (PID: 2148)
- EikonDM.exe (PID: 4008)
- Eikon.exe (PID: 2172)
- ConnectionManagement.exe (PID: 1704)
- EikonBoxNet.exe (PID: 3360)
- Eikon.exe (PID: 3316)
Changes settings of System certificates
- EikonDM.exe (PID: 2112)
Changes the autorun value in the registry
- EikonDM.exe (PID: 4008)
SUSPICIOUS
Executable content was dropped or overwritten
- EikonInstaller.exe (PID: 3616)
- EikonInstaller.exe (PID: 1824)
- EikonDM.exe (PID: 2112)
- EikonDM.exe (PID: 2148)
- EikonDM.exe (PID: 4008)
Reads Environment values
- EikonDM.exe (PID: 1480)
- EikonInstaller.exe (PID: 1824)
- EikonDM.exe (PID: 2112)
- EikonDM.exe (PID: 4008)
- EikonBoxNet.exe (PID: 3360)
Application launched itself
- EikonDM.exe (PID: 1480)
Creates files in the program directory
- EikonDM.exe (PID: 2112)
- EikonDM.exe (PID: 2148)
- Eikon.exe (PID: 3316)
- EikonBoxNet.exe (PID: 3360)
- EikonDM.exe (PID: 4008)
Adds / modifies Windows certificates
- EikonDM.exe (PID: 2112)
Reads CPU info
- EikonDM.exe (PID: 2112)
Creates a software uninstall entry
- EikonDM.exe (PID: 4008)
Reads internet explorer settings
- Eikon.exe (PID: 3316)
Creates COM task schedule object
- EikonDM.exe (PID: 4008)
Modifies the open verb of a shell class
- EikonDM.exe (PID: 4008)
INFO
Reads settings of System Certificates
- EikonInstaller.exe (PID: 1824)
- EikonDM.exe (PID: 2112)
Reads Microsoft Office registry keys
- EikonDM.exe (PID: 2112)
Dropped object may contain Bitcoin addresses
- EikonDM.exe (PID: 4008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:01:30 04:57:45+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25600 |
| InitializedDataSize: | 162816 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x320c |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.0.46118.1 |
| ProductVersionNumber: | 4.0.46118.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | Thomson Reuters Eikon Installer |
| CompanyName: | Thomson Reuters |
| FileDescription: | Thomson Reuters Eikon Installer |
| FileVersion: | 4.0.46118.1 |
| LegalCopyright: | Copyright 2015 Thomson Reuters |
| LegalTrademarks: | Thomson Reuters |
| ProductName: | Thomson Reuters Eikon |
| ProductVersion: | 4.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 30-Jan-2018 03:57:45 |
| Detected languages: |
|
| Comments: | Thomson Reuters Eikon Installer |
| CompanyName: | Thomson Reuters |
| FileDescription: | Thomson Reuters Eikon Installer |
| FileVersion: | 4.0.46118.1 |
| LegalCopyright: | Copyright 2015 Thomson Reuters |
| LegalTrademarks: | Thomson Reuters |
| ProductName: | Thomson Reuters Eikon |
| ProductVersion: | 4.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 30-Jan-2018 03:57:45 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000628F | 0x00006400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.4422 |
.rdata | 0x00008000 | 0x00001354 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.23627 |
.data | 0x0000A000 | 0x00025518 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.04938 |
.ndata | 0x00030000 | 0x0000C000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0003C000 | 0x0000D990 | 0x0000DA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.18102 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.2992 | 830 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.47322 | 9640 | UNKNOWN | English - United States | RT_ICON |
3 | 4.97492 | 4264 | UNKNOWN | English - United States | RT_ICON |
4 | 5.11626 | 2440 | UNKNOWN | English - United States | RT_ICON |
5 | 5.21367 | 1128 | UNKNOWN | English - United States | RT_ICON |
103 | 2.64638 | 76 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.66174 | 256 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.88094 | 284 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.48825 | 96 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
50
Monitored processes
12
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | "C:\Windows\explorer.exe" C:\Program Files\Thomson Reuters\Eikon\Eikon.exe | C:\Windows\explorer.exe | — | EikonDM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1480 | "C:\Users\admin\AppData\Local\Temp\EikonDM_4mj3vcqo.kqc\EikonDM.exe" _webStartPath="C:\Users\admin\AppData\Local\Temp" _execute=INSTALL _platformConfig=PROD _region=AMERS2 _calledByInstaller=1 | C:\Users\admin\AppData\Local\Temp\EikonDM_4mj3vcqo.kqc\EikonDM.exe | — | EikonInstaller.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Thomson Reuters Eikon Deployment Manager Exit code: 4294967295 Version: 9.45.0.005 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Thomson Reuters\Eikon\X\Bin\ConnectionManagement.exe" "getcookie" "https://login.cp.thomsonreuters.net" "iPlanetDirectoryPro" "C:\Users\admin\AppData\LocalLow\Temp\TRS5E88.tmp" | C:\Program Files\Thomson Reuters\Eikon\X\Bin\ConnectionManagement.exe | — | Eikon.exe | |||||||||||
User: admin Company: Thomson Reuters Integrity Level: LOW Description: Thomson Reuters Eikon 4.0, Connection Management Exit code: 0 Version: 9.47.0.108 Modules
| |||||||||||||||
| 1824 | "C:\Users\admin\AppData\Local\Temp\EikonInstaller_9723\EikonInstaller.exe" _webStartPath="C:\Users\admin\AppData\Local\Temp" | C:\Users\admin\AppData\Local\Temp\EikonInstaller_9723\EikonInstaller.exe | EikonInstaller.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Thomson Reuters Eikon Installer Exit code: 4294967295 Version: 4.0.3.0 Modules
| |||||||||||||||
| 2112 | "C:\Users\admin\AppData\Local\Temp\EikonDM_4mj3vcqo.kqc\EikonDM.exe" _webStartPath="C:\Users\admin\AppData\Local\Temp" _execute=INSTALL _platformConfig=PROD _region=AMERS2 _calledByInstaller=1 _rerun=1 _killRDMC=0 _sameLog=0 _waitPid=1480 _sso=1 _envVarFilePath="EikonDM\ExportEnvironmentVariables.xml" | C:\Users\admin\AppData\Local\Temp\EikonDM_4mj3vcqo.kqc\EikonDM.exe | EikonDM.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Thomson Reuters Eikon Deployment Manager Exit code: 4294967295 Version: 9.45.0.005 Modules
| |||||||||||||||
| 2148 | "C:\Program Files\Thomson Reuters\Eikon\EikonSetup\0xqjs0ip.xvp\Setup\EikonDM.exe" | C:\Program Files\Thomson Reuters\Eikon\EikonSetup\0xqjs0ip.xvp\Setup\EikonDM.exe | EikonDM.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: EikonUpgradeTools Exit code: 4294967294 Version: 1.0.2.0624 Modules
| |||||||||||||||
| 2172 | "C:\Program Files\Thomson Reuters\Eikon\Eikon.exe" | C:\Program Files\Thomson Reuters\Eikon\Eikon.exe | — | explorer.exe | |||||||||||
User: admin Company: Thomson Reuters Integrity Level: MEDIUM Description: Thomson Reuters Eikon 4.0, Eikon Desktop Exit code: 0 Version: 9.47.0.108 Modules
| |||||||||||||||
| 3316 | "C:\Program Files\Thomson Reuters\Eikon\X\Bin\Eikon.exe" | C:\Program Files\Thomson Reuters\Eikon\X\Bin\Eikon.exe | Eikon.exe | ||||||||||||
User: admin Company: Thomson Reuters Integrity Level: MEDIUM Description: Thomson Reuters Eikon 4.0, Eikon Desktop Exit code: 0 Version: 9.47.0.108 Modules
| |||||||||||||||
| 3360 | "C:\Program Files\Thomson Reuters\Eikon\X\Bin\EikonBoxNet.exe" -b -a -EikonPipe true -EikonPipeId 3316 -EikonProcessId 3316 -HwndComInterop 0x1 -AffinityName singleInstance[THOMSONREUTERS.EIKON.STARTERNET]_031D9D90 -Context "C:\Program Files\Thomson Reuters\Eikon\X\Bin\Apps\THOMSONREUTERS.EIKON.STARTERNET\0.0.0.0" -DelayInitKobraProvider true /prefetch:4 | C:\Program Files\Thomson Reuters\Eikon\X\Bin\EikonBoxNet.exe | Eikon.exe | ||||||||||||
User: admin Company: Thomson Reuters Integrity Level: MEDIUM Description: Thomson Reuters EikonBoxNet Exit code: 0 Version: 9.47.0.108 Modules
| |||||||||||||||
| 3616 | "C:\Users\admin\AppData\Local\Temp\EikonInstaller.exe" | C:\Users\admin\AppData\Local\Temp\EikonInstaller.exe | explorer.exe | ||||||||||||
User: admin Company: Thomson Reuters Integrity Level: MEDIUM Description: Thomson Reuters Eikon Installer Exit code: 4294967295 Version: 4.0.46118.1 Modules
| |||||||||||||||
Total events
2 001
Read events
1 468
Write events
532
Delete events
1
Modification events
| (PID) Process: | (1824) EikonInstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: EikonInstaller.exe | |||
| (PID) Process: | (1824) EikonInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EikonInstaller_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1824) EikonInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EikonInstaller_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1824) EikonInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EikonInstaller_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (1824) EikonInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EikonInstaller_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (1824) EikonInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EikonInstaller_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1824) EikonInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EikonInstaller_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1824) EikonInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EikonInstaller_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1824) EikonInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EikonInstaller_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1824) EikonInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EikonInstaller_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
Executable files
2 146
Suspicious files
104
Text files
1 838
Unknown types
87
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1824 | EikonInstaller.exe | C:\Users\admin\AppData\Local\Temp\EikonDM_4_0_47109.eik.EikonUpdater | — | |
MD5:— | SHA256:— | |||
| 1824 | EikonInstaller.exe | C:\Users\admin\AppData\Local\Temp\EikonDM_4_0_47109.eik | compressed | |
MD5:— | SHA256:— | |||
| 3616 | EikonInstaller.exe | C:\Users\admin\AppData\Local\Temp\EikonInstaller_9723\ThomsonReuters.Core.dll | executable | |
MD5:— | SHA256:— | |||
| 3616 | EikonInstaller.exe | C:\Users\admin\AppData\Local\Temp\EikonInstaller_9723\KobraZLib.dll | executable | |
MD5:— | SHA256:— | |||
| 3616 | EikonInstaller.exe | C:\Users\admin\AppData\Local\Temp\EikonInstaller_9723\EikonUpdater.dll | executable | |
MD5:— | SHA256:— | |||
| 3616 | EikonInstaller.exe | C:\Users\admin\AppData\Local\Temp\EikonInstaller_9723\EikonInstaller.exe | executable | |
MD5:— | SHA256:— | |||
| 3616 | EikonInstaller.exe | C:\Users\admin\AppData\Local\Temp\EikonInstaller_9723\KobraTrace.dll | executable | |
MD5:— | SHA256:— | |||
| 3616 | EikonInstaller.exe | C:\Users\admin\AppData\Local\Temp\EikonInstaller_9723\ThomsonReuters.Desktop.SDK.UI.dll | executable | |
MD5:AA4822A6CAD45330E2F3D5AD1AEF6E01 | SHA256:79FDA63E6370D572D83137287BDF55C4DCBFFB9FE929C186E261ECC2F2E5BE24 | |||
| 3616 | EikonInstaller.exe | C:\Users\admin\AppData\Local\Temp\nsy5D11.tmp\System.dll | executable | |
MD5:B0C77267F13B2F87C084FD86EF51CCFC | SHA256:A0CAC4CF4852895619BC7743EBEB89F9E4927CCDB9E66B1BCD92A4136D0F9C77 | |||
| 1824 | EikonInstaller.exe | C:\Users\admin\AppData\Local\Temp\EikonDM_4mj3vcqo.kqc\EikonDM.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
16
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3316 | Eikon.exe | GET | 200 | 159.220.1.73:80 | http://emea1.heartbeat.cp.thomsonreuters.net/network.xml | US | xml | 215 b | unknown |
2112 | EikonDM.exe | GET | 404 | 2.16.186.99:80 | http://eikontest.thomsonreuters.com/Eikon/EIKONTEST.TXT | unknown | text | 16 b | whitelisted |
2112 | EikonDM.exe | POST | 200 | 159.220.16.71:80 | http://heartbeat.cp.thomsonreuters.net/network.xml | US | xml | 215 b | suspicious |
2112 | EikonDM.exe | GET | 404 | 2.16.186.99:80 | http://eikontest.thomsonreuters.com/Eikon/EIKONTEST.TXT | unknown | text | 16 b | whitelisted |
2112 | EikonDM.exe | GET | 200 | 143.204.208.230:80 | http://amers2.download.cp.thomsonreuters.net/Packages/EikonCore/Eikon/Eikon_Core_4_0_47109.eik | US | compressed | 141 Mb | whitelisted |
1824 | EikonInstaller.exe | POST | 200 | 159.220.16.71:80 | http://heartbeat.cp.thomsonreuters.net/network.xml | US | xml | 215 b | suspicious |
1824 | EikonInstaller.exe | GET | 200 | 143.204.208.230:80 | http://amers2.download.cp.thomsonreuters.net/Packages/EikonDM/EikonDM_4_0_47109.eik | US | compressed | 3.03 Mb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1824 | EikonInstaller.exe | 159.220.16.71:80 | heartbeat.cp.thomsonreuters.net | 18 Science Park Drive | US | unknown |
1824 | EikonInstaller.exe | 192.165.219.184:443 | amers2.views.cp.thomsonreuters.com | Thomson Reuters U.S. LLC | SE | unknown |
1824 | EikonInstaller.exe | 143.204.208.230:80 | amers2.download.cp.thomsonreuters.net | — | US | suspicious |
2112 | EikonDM.exe | 2.16.186.99:80 | eikontest.thomsonreuters.com | Akamai International B.V. | — | whitelisted |
2112 | EikonDM.exe | 159.220.16.71:443 | heartbeat.cp.thomsonreuters.net | 18 Science Park Drive | US | unknown |
2112 | EikonDM.exe | 159.220.16.65:443 | apac1.login.cp.thomsonreuters.net | 18 Science Park Drive | US | unknown |
2112 | EikonDM.exe | 159.220.16.71:80 | heartbeat.cp.thomsonreuters.net | 18 Science Park Drive | US | unknown |
3316 | Eikon.exe | 159.220.1.64:443 | emea1.login.cp.thomsonreuters.net | Thomson Reuters Ireland Limited | US | unknown |
2112 | EikonDM.exe | 192.165.219.184:443 | amers2.views.cp.thomsonreuters.com | Thomson Reuters U.S. LLC | SE | unknown |
3316 | Eikon.exe | 159.220.1.73:80 | emea1.heartbeat.cp.thomsonreuters.net | Thomson Reuters Ireland Limited | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
heartbeat.cp.thomsonreuters.net |
| suspicious |
amers2.views.cp.thomsonreuters.com |
| unknown |
amers2.download.cp.thomsonreuters.net |
| whitelisted |
eikontest.thomsonreuters.com |
| whitelisted |
apac1.login.cp.thomsonreuters.net |
| unknown |
dns.msftncsi.com |
| shared |
emea1.heartbeat.cp.thomsonreuters.net |
| unknown |
emea1.login.cp.thomsonreuters.net |
| unknown |
Threats
Process | Message |
|---|---|
Eikon.exe | SD_BOOTSTRAP: Configuring traces from resource IDR_XML_TRACE_SOURCES |
Eikon.exe | Log config warning: TraceSource 'MAIN' already exists and will be reconfigured |
Eikon.exe | Log config warning: TraceSource 'RDMC_SCHED' already exists and will be reconfigured |
Eikon.exe | Log config warning: TraceSource 'SD_BOOTSTRAP' already exists and will be reconfigured |
Eikon.exe | Log config warning: TraceSource 'BOOT_SCHED' already exists and will be reconfigured |
Eikon.exe | Log config warning: TraceSource 'SD_FDM_MISC' already exists and will be reconfigured |
Eikon.exe | Log config warning: TraceSource 'SD_FDM_ASYNCDF' already exists and will be reconfigured |
Eikon.exe | Log config warning: TraceSource 'SD_FDM_WKTH' already exists and will be reconfigured |
Eikon.exe | Log config warning: TraceSource 'SD_KPROMGR' already exists and will be reconfigured |
Eikon.exe | Log config warning: TraceSource 'SD_RPHAPI' already exists and will be reconfigured |