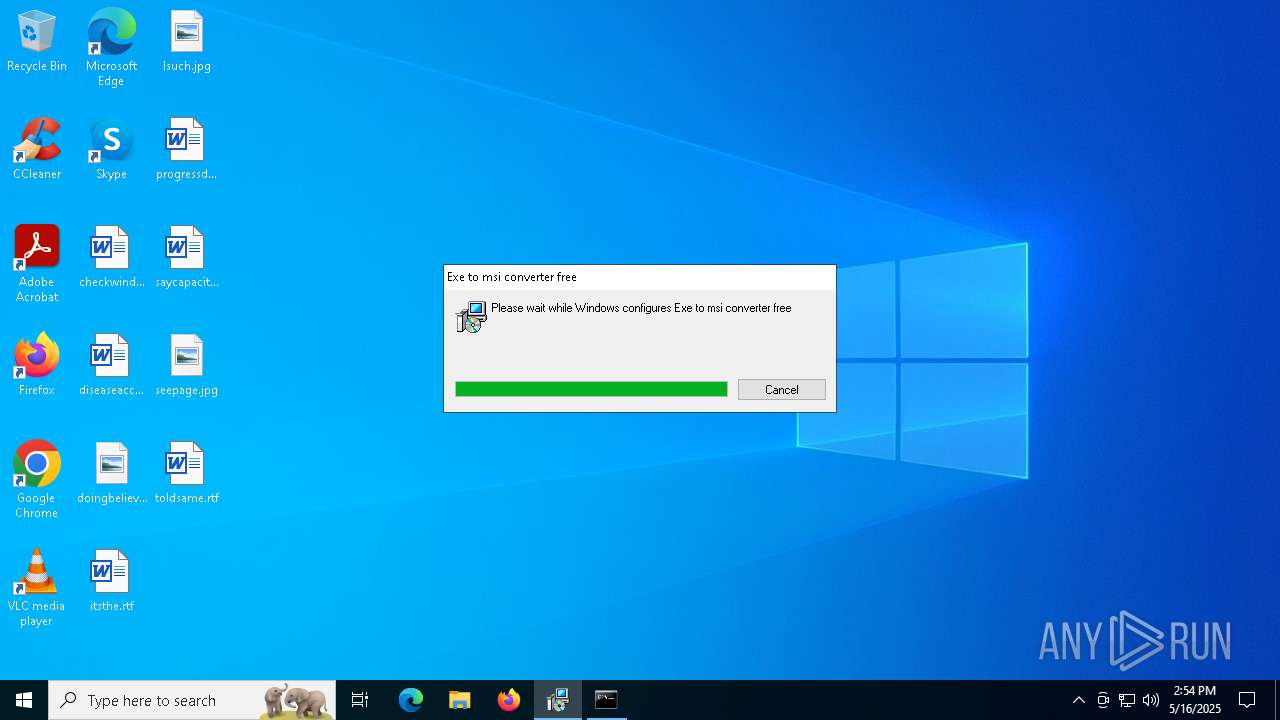
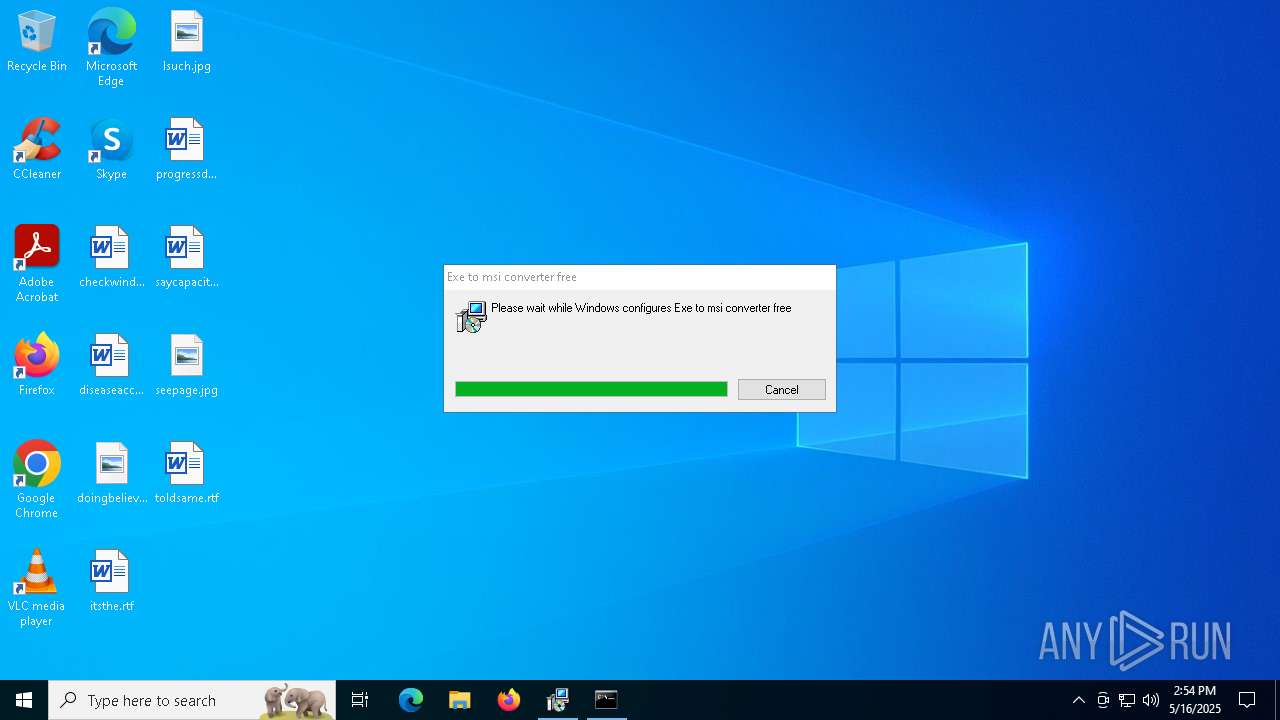
| File name: | Server_Certificate.msi |
| Full analysis: | https://app.any.run/tasks/bf43219c-b03b-4d54-8ea0-018c1bcbd3fc |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 14:53:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
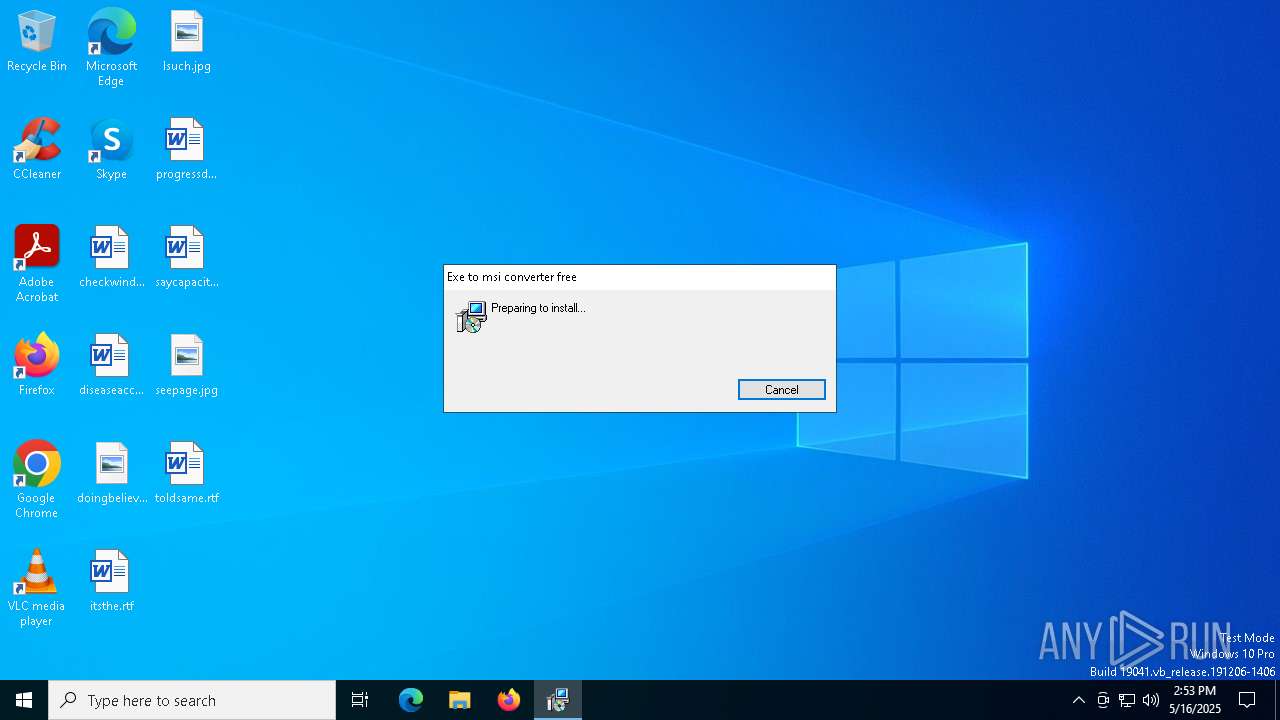
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Code page: 1252, Last Printed: Fri Sep 21 09:56:09 2012, Create Time/Date: Fri Sep 21 09:56:09 2012, Name of Creating Application: Windows Installer, Title: Exe to msi converter free, Author: www.exetomsi.com, Template: ;0, Last Saved By: devuser, Revision Number: {C35CF0AA-9B3F-4903-9F05-EBF606D58D3E}, Last Saved Time/Date: Tue May 21 11:56:44 2013, Number of Pages: 100, Number of Words: 0, Security: 0 |
| MD5: | C58D16762A12320418757EAF3C58789E |
| SHA1: | 7720B07CD08C9556A466A6A076C89E85C98F3F3D |
| SHA256: | 472E1E73419968BB61C8123E2CACE1F767942809F807AAF6D62B535399122606 |
| SSDEEP: | 98304:Re0dKWU8pMOri6pi2i2ZzXRdGeP6ywAh66PO7COgzlz3HeqjI8Lj605w/y6lZ6Ai:FrkMrt73 |
MALICIOUS
No malicious indicators.SUSPICIOUS
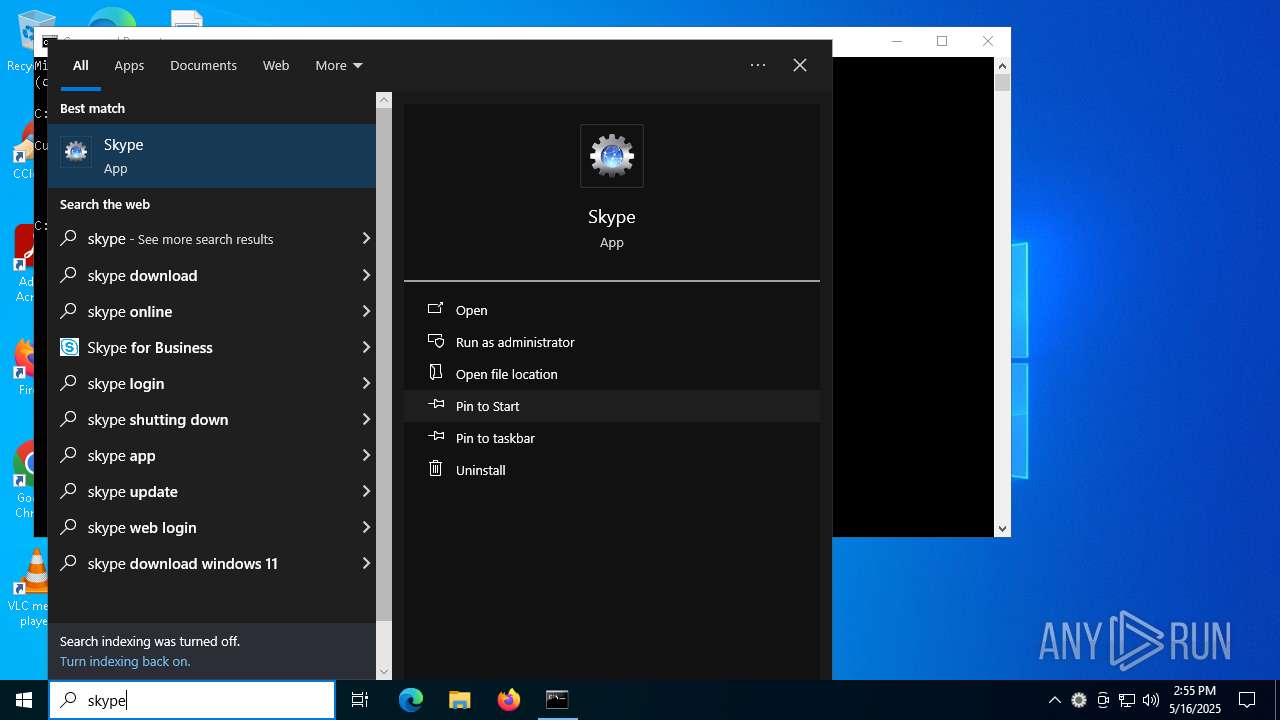
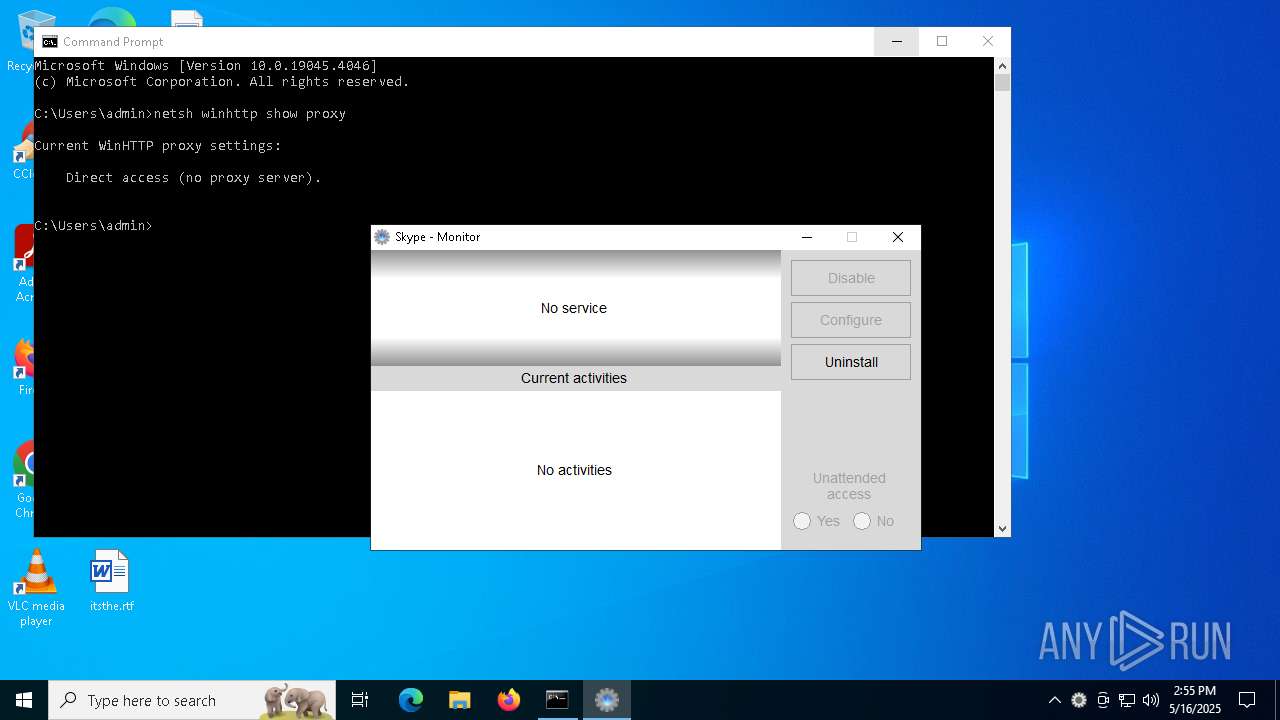
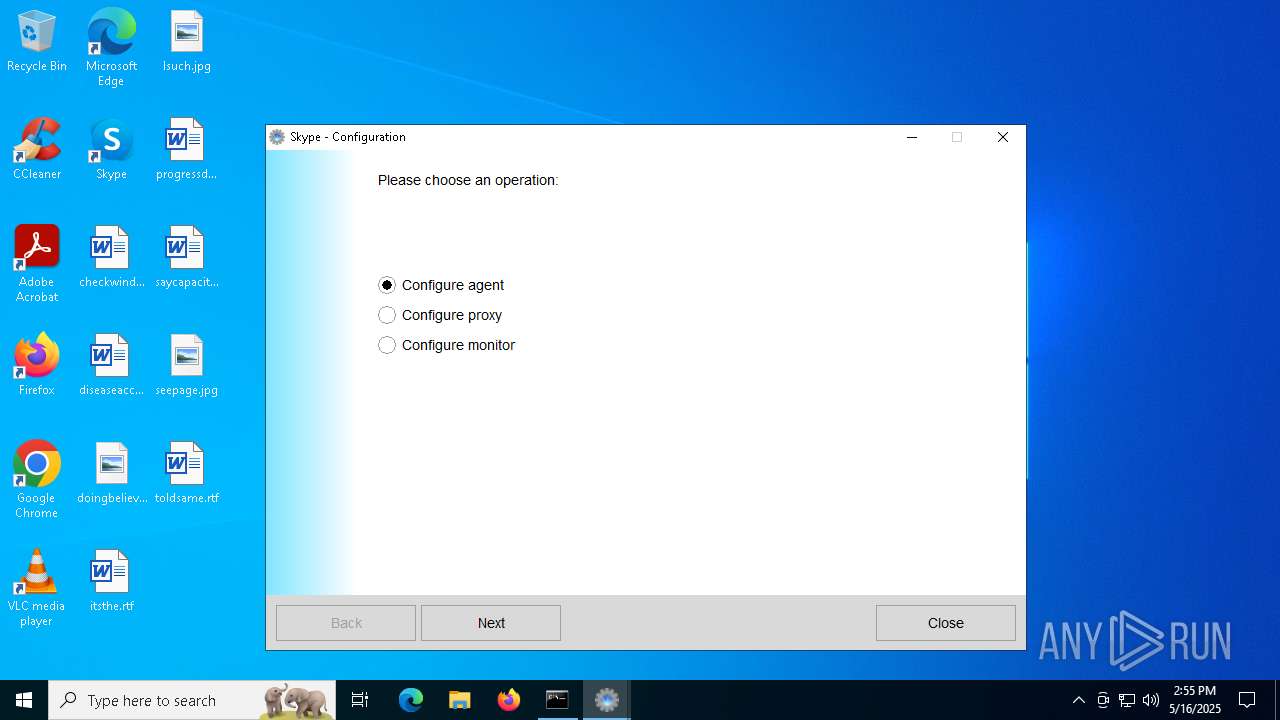
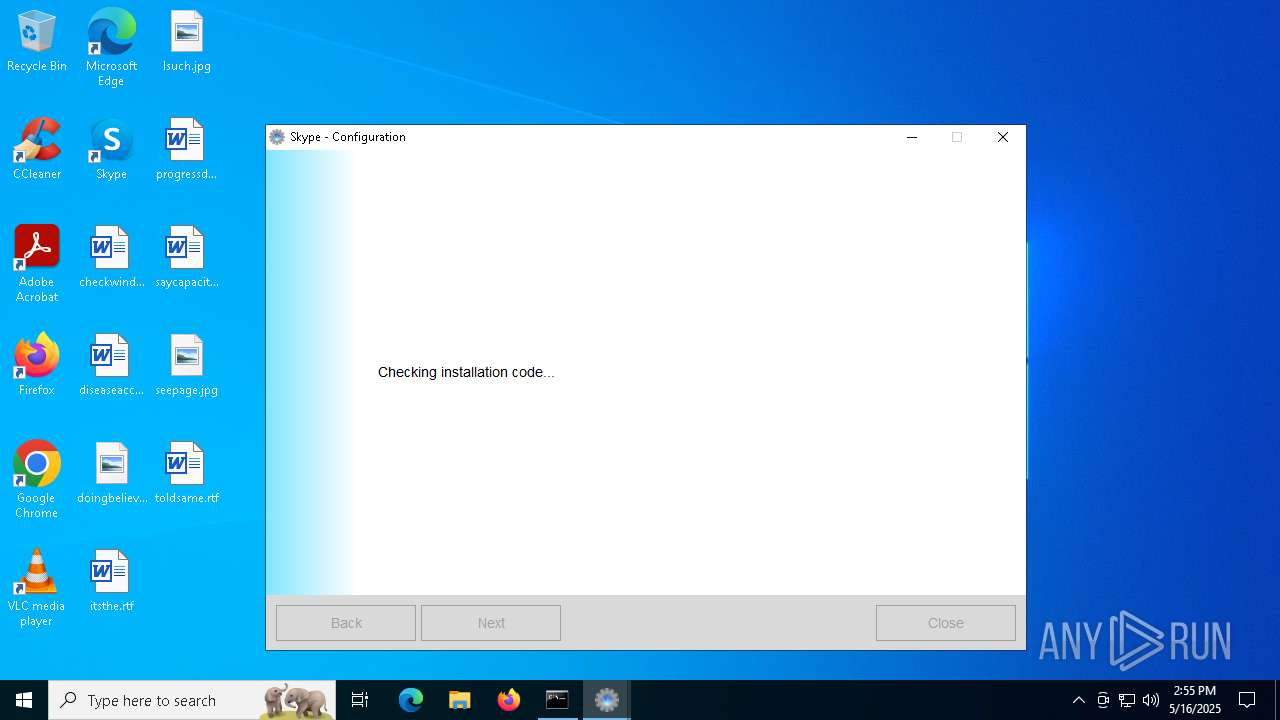
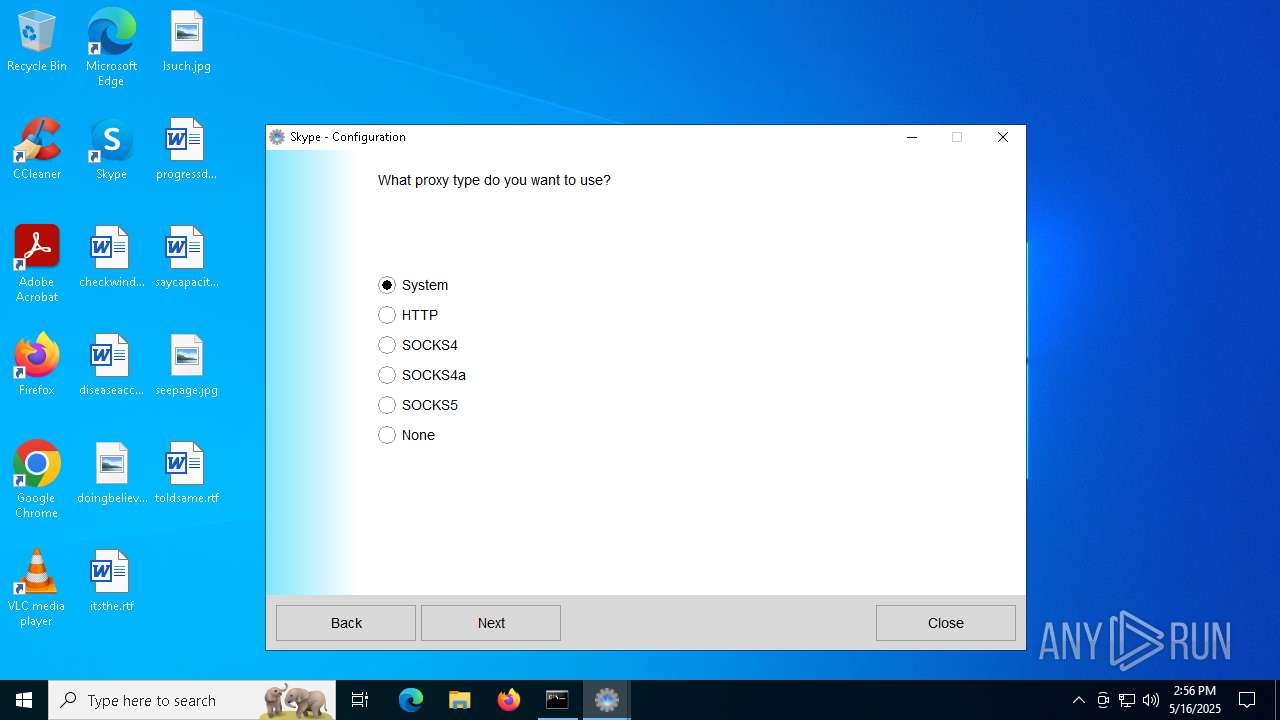
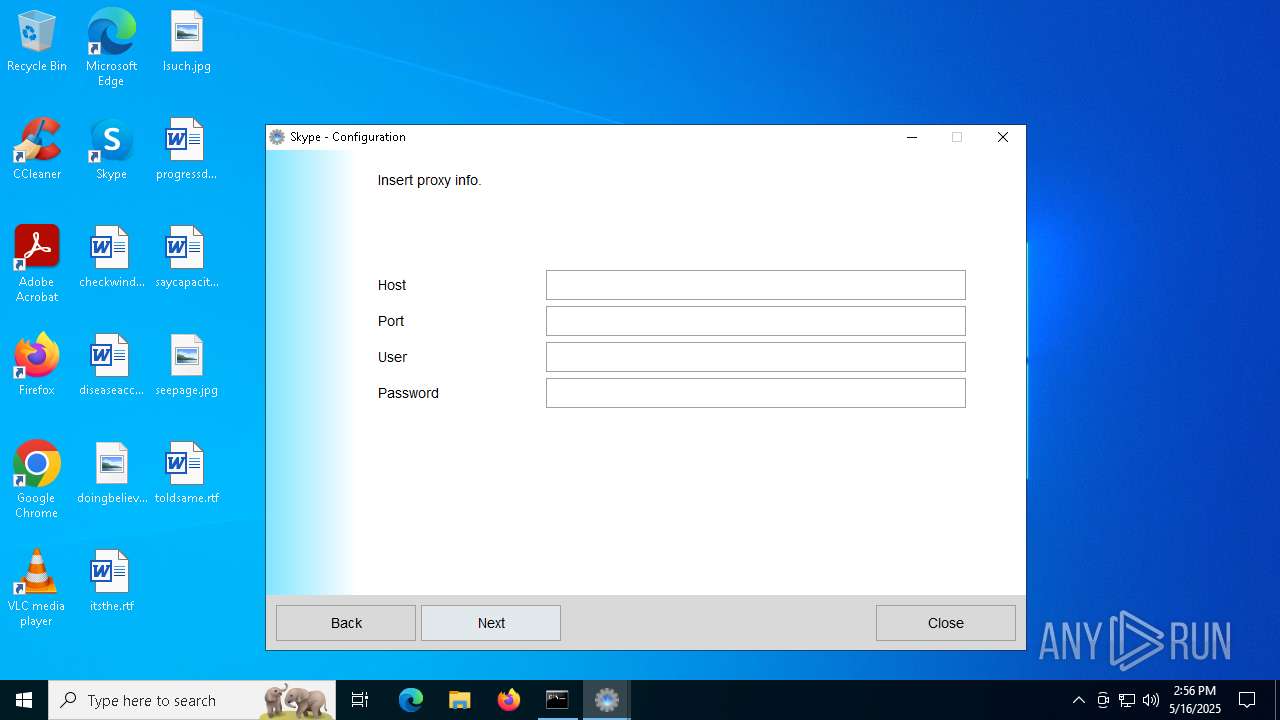
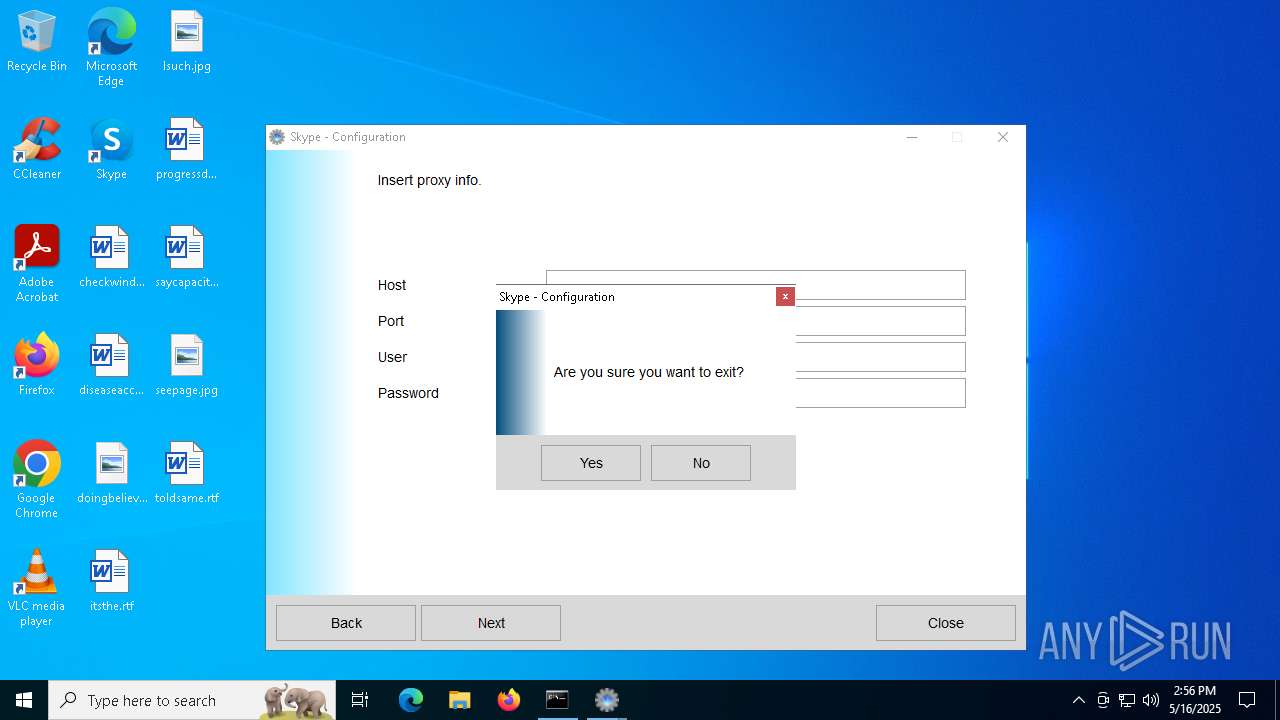
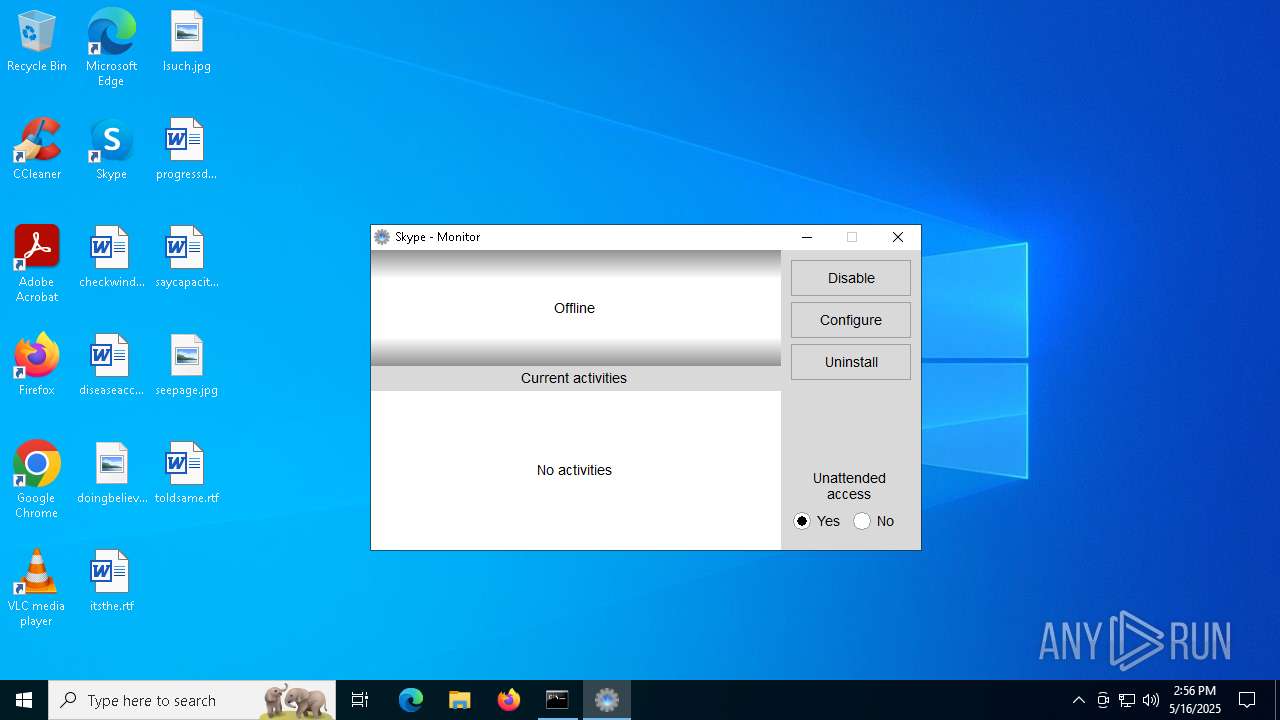
Drops the ExeToMSI Application
- msiexec.exe (PID: 1280)
Executes as Windows Service
- VSSVC.exe (PID: 7012)
- dwagsvc.exe (PID: 5008)
Process drops python dynamic module
- MSI1163.tmp (PID: 5244)
- skype.exe (PID: 6436)
Executable content was dropped or overwritten
- MSI1163.tmp (PID: 5244)
- skype.exe (PID: 6436)
The process drops C-runtime libraries
- MSI1163.tmp (PID: 5244)
- skype.exe (PID: 6436)
Process drops legitimate windows executable
- MSI1163.tmp (PID: 5244)
- skype.exe (PID: 6436)
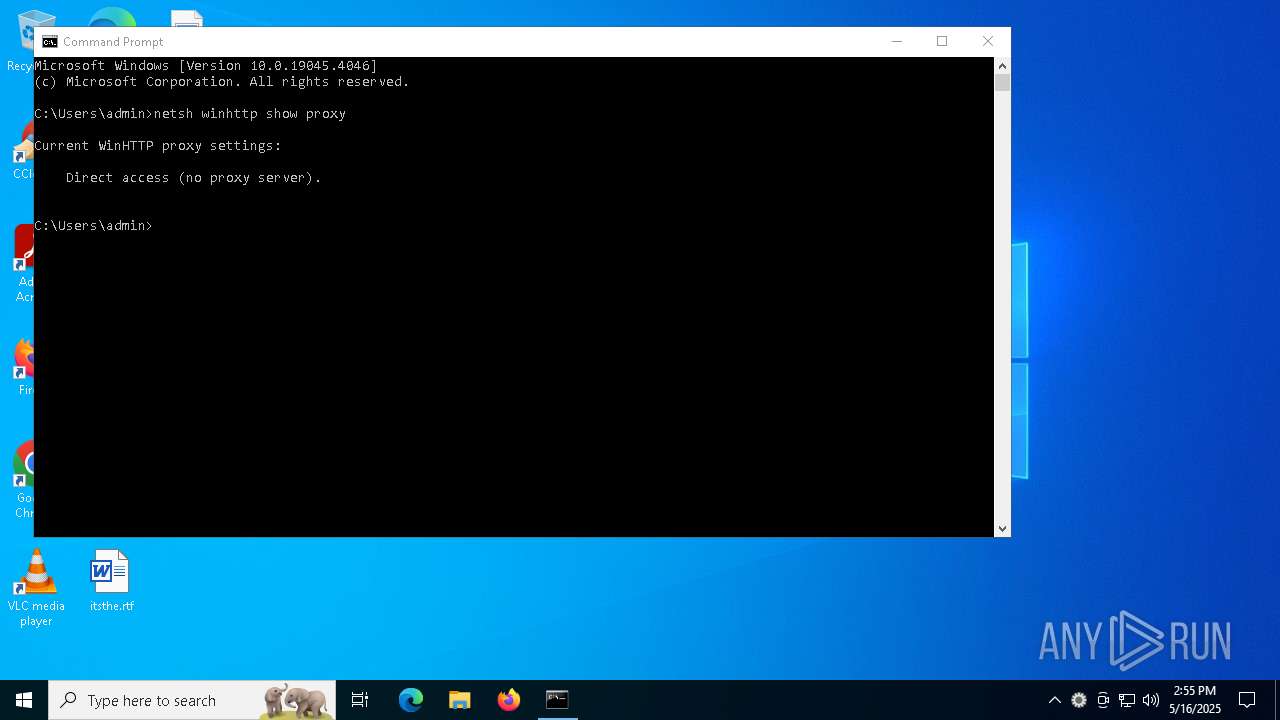
Starts CMD.EXE for commands execution
- skype.exe (PID: 6436)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 6592)
INFO
Checks supported languages
- msiexec.exe (PID: 4164)
Reads the computer name
- msiexec.exe (PID: 4164)
Manages system restore points
- SrTasks.exe (PID: 4408)
Starts application with an unusual extension
- msiexec.exe (PID: 4164)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4164)
The sample compiled with english language support
- MSI1163.tmp (PID: 5244)
- skype.exe (PID: 6436)
Manual execution by a user
- cmd.exe (PID: 6592)
- dwaglnc.exe (PID: 736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| LastPrinted: | 2012:09:21 09:56:09 |
| CreateDate: | 2012:09:21 09:56:09 |
| Software: | Windows Installer |
| Title: | Exe to msi converter free |
| Subject: | - |
| Author: | www.exetomsi.com |
| Keywords: | - |
| Comments: | - |
| Template: | ;0 |
| LastModifiedBy: | devuser |
| RevisionNumber: | {C35CF0AA-9B3F-4903-9F05-EBF606D58D3E} |
| ModifyDate: | 2013:05:21 11:56:44 |
| Pages: | 100 |
| Words: | - |
| Security: | None |
Total processes
184
Monitored processes
47
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\Skype\native\dwagsvc.exe" deleteService" | C:\Windows\System32\cmd.exe | — | skype.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\Program Files\Skype\native\dwaglnc.exe" monitor | C:\Program Files\Skype\native\dwaglnc.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 924 | "C:\Program Files\Skype\runtime\skype.exe" -S -m agent -filelog | C:\Program Files\Skype\runtime\skype.exe | dwagsvc.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Modules
| |||||||||||||||
| 976 | "C:\Program Files\Skype\native\dwagsvc.exe" startService | C:\Program Files\Skype\native\dwagsvc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\Skype\native\dwaglnc.exe" systray" | C:\Windows\System32\cmd.exe | — | skype.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\Skype\native\dwagsvc.exe" removeShortcuts" | C:\Windows\System32\cmd.exe | — | skype.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\Server_Certificate.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 739
Read events
6 541
Write events
180
Delete events
18
Modification events
| (PID) Process: | (7012) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000B362895772C6DB01641B0000AC190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7012) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000B362895772C6DB01641B000058190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7012) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000B362895772C6DB01641B000004140000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7012) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000B362895772C6DB01641B0000300F0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7012) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000378E905772C6DB01641B0000AC190000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7012) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7012) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000378E905772C6DB01641B000058190000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7012) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (7012) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7012) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
Executable files
70
Suspicious files
1 093
Text files
96
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4164 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4164 | msiexec.exe | C:\Windows\Installer\110c70.msi | — | |
MD5:— | SHA256:— | |||
| 4164 | msiexec.exe | C:\Windows\Installer\MSI10D5.tmp | — | |
MD5:— | SHA256:— | |||
| 5244 | MSI1163.tmp | C:\Users\admin\AppData\Local\Temp\MSI116320250516145414\win.7z | — | |
MD5:— | SHA256:— | |||
| 4164 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{6ecd9e19-a522-4712-a20a-39e6d9bd9d63}_OnDiskSnapshotProp | binary | |
MD5:C774A75D95610A8E4D35FD127A53DABF | SHA256:8DE8713AB0B820FBC132933DAD6D3BC53FA399954955ACE35D7F715302986CAF | |||
| 4164 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:C774A75D95610A8E4D35FD127A53DABF | SHA256:8DE8713AB0B820FBC132933DAD6D3BC53FA399954955ACE35D7F715302986CAF | |||
| 4164 | msiexec.exe | C:\Windows\Installer\MSI1163.tmp | executable | |
MD5:09004AC513357369911E34CC02E55EEE | SHA256:8F56E45C011453A9116461728A3627FC780ABCDCE4A05FD35C66490D8EE1FD49 | |||
| 4164 | msiexec.exe | C:\Windows\Temp\~DFD28B3696DF6758AF.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 4164 | msiexec.exe | C:\Windows\Temp\~DF6D562102E7411AD6.TMP | binary | |
MD5:2FFFC5C8E00E8AA8BD6A97BB9036525A | SHA256:D5F9ABB062EAD537B5003279E614E5634616D95DD791C539C72A22F143B80481 | |||
| 5244 | MSI1163.tmp | C:\Users\admin\AppData\Local\Temp\MSI116320250516145414\runtime\bit64\DLLs\pyexpat.pyd | executable | |
MD5:2A69DAB6A61D6837F3F597EA44E5415B | SHA256:24B321A24C67B6AFB095F9BDC38FF1ECF74E95B59928FA36E6011C2FC37E4B96 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
57
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.15:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1116 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1116 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.15:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |