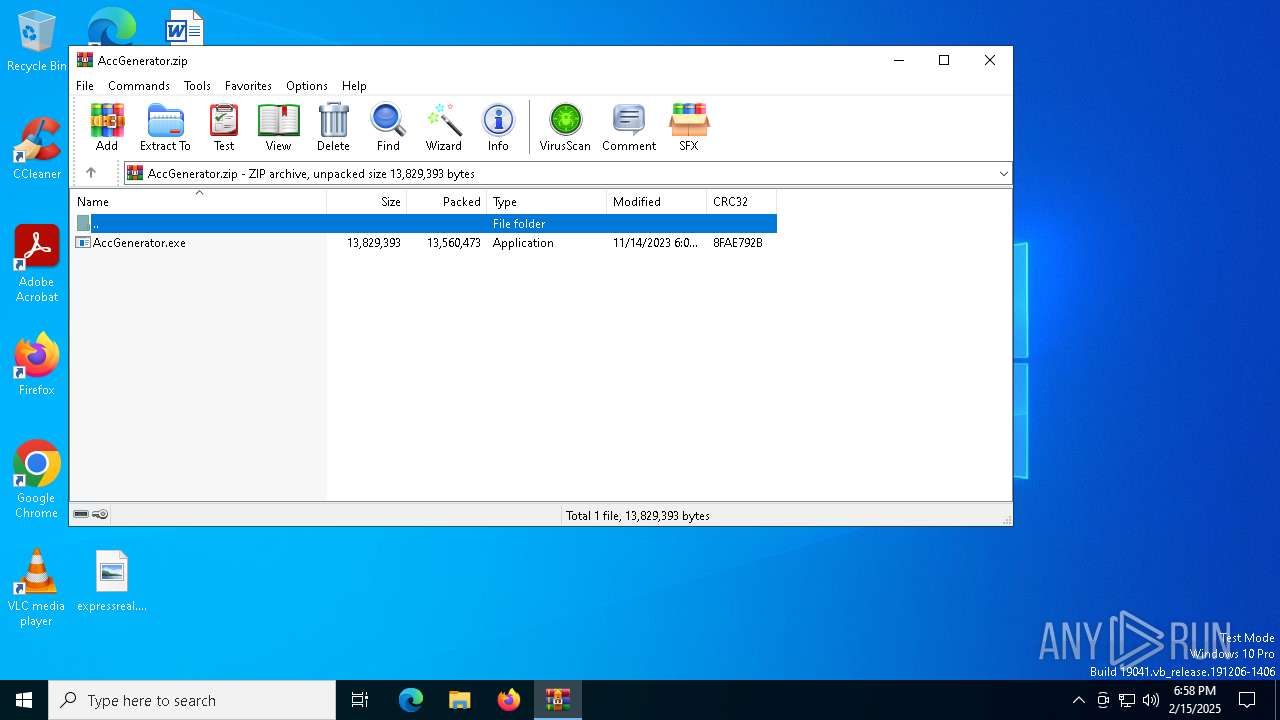
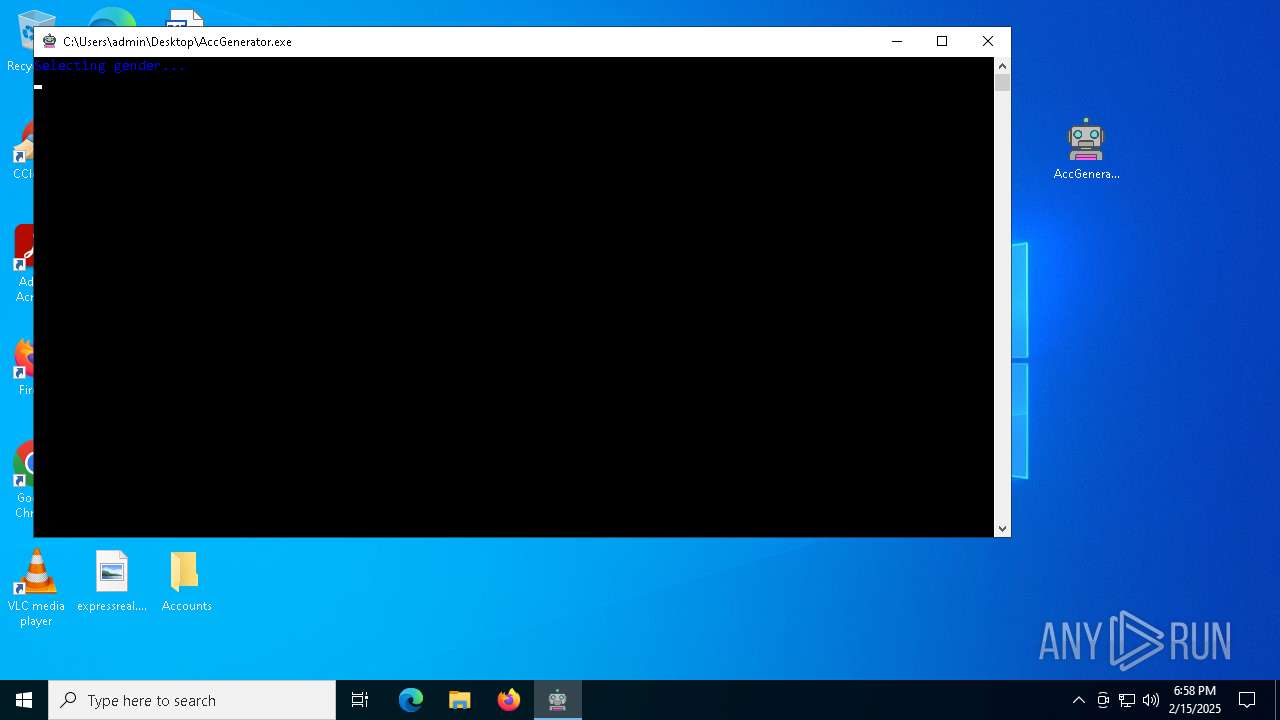
| File name: | AccGenerator.zip |
| Full analysis: | https://app.any.run/tasks/d34666df-1812-4e9b-9db3-90e9eede43df |
| Verdict: | Malicious activity |
| Analysis date: | February 15, 2025, 18:57:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | CE094A9EF628CD7BA0616D58AEC42512 |
| SHA1: | BCD7075F77CBD97A6196008F73F1768142C4DC39 |
| SHA256: | 470D90EC620DA317D6365412EC34A411D4ED0B12B90CC02399C5A57CA209A78E |
| SSDEEP: | 98304:RLAa4VEcXufZIHJlixL2rqqzjELMYvjQLQTnplr91Mulot99/boTS0mhrQlronlX:ua2AbZZ1OrQegZrSk0d1zN |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6364)
SUSPICIOUS
The process drops C-runtime libraries
- AccGenerator.exe (PID: 6812)
Process drops legitimate windows executable
- AccGenerator.exe (PID: 6812)
- selenium-manager.exe (PID: 7104)
Executable content was dropped or overwritten
- AccGenerator.exe (PID: 6812)
- selenium-manager.exe (PID: 7104)
Process drops python dynamic module
- AccGenerator.exe (PID: 6812)
Application launched itself
- AccGenerator.exe (PID: 6812)
Loads Python modules
- AccGenerator.exe (PID: 6884)
Starts CMD.EXE for commands execution
- AccGenerator.exe (PID: 6884)
- selenium-manager.exe (PID: 7104)
- selenium-manager.exe (PID: 6656)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7132)
- cmd.exe (PID: 5892)
Uses WMIC.EXE
- cmd.exe (PID: 904)
- cmd.exe (PID: 3552)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6364)
Checks supported languages
- AccGenerator.exe (PID: 6812)
- AccGenerator.exe (PID: 6884)
- selenium-manager.exe (PID: 7104)
- msedgedriver.exe (PID: 2076)
- msedgedriver.exe (PID: 7024)
- selenium-manager.exe (PID: 6656)
Reads the computer name
- AccGenerator.exe (PID: 6812)
- AccGenerator.exe (PID: 6884)
- selenium-manager.exe (PID: 7104)
- msedgedriver.exe (PID: 2076)
- msedgedriver.exe (PID: 7024)
Manual execution by a user
- AccGenerator.exe (PID: 6812)
The sample compiled with english language support
- AccGenerator.exe (PID: 6812)
- selenium-manager.exe (PID: 7104)
Create files in a temporary directory
- AccGenerator.exe (PID: 6812)
- selenium-manager.exe (PID: 7104)
- msedgedriver.exe (PID: 2076)
- msedgedriver.exe (PID: 7024)
Checks proxy server information
- AccGenerator.exe (PID: 6884)
- selenium-manager.exe (PID: 7104)
- selenium-manager.exe (PID: 6656)
Drops encrypted JS script (Microsoft Script Encoder)
- AccGenerator.exe (PID: 6884)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7148)
- WMIC.exe (PID: 5028)
- WMIC.exe (PID: 6512)
- WMIC.exe (PID: 6500)
Checks operating system version
- AccGenerator.exe (PID: 6884)
Reads Environment values
- msedgedriver.exe (PID: 2076)
- msedgedriver.exe (PID: 7024)
Application launched itself
- msedge.exe (PID: 6720)
- msedge.exe (PID: 6936)
PyInstaller has been detected (YARA)
- AccGenerator.exe (PID: 6812)
Reads the machine GUID from the registry
- msedgedriver.exe (PID: 2076)
- msedgedriver.exe (PID: 7024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:11:14 18:00:08 |
| ZipCRC: | 0x8fae792b |
| ZipCompressedSize: | 13560473 |
| ZipUncompressedSize: | 13829393 |
| ZipFileName: | AccGenerator.exe |
Total processes
224
Monitored processes
91
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 640 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Local\Temp\scoped_dir7024_1788179866" --no-appcompat-clear --enable-automation --enable-logging --log-level=0 --remote-debugging-port=0 --test-type=webdriver --allow-pre-commit-input --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=4512 --field-trial-handle=2312,i,4332145636189932282,9270041941028546741,262144 --enable-features=msMetricsLogFastStartup,msSendMetricsLogOnClose --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --enable-logging --log-level=0 --onnx-enabled-for-ee --user-data-dir="C:\Users\admin\AppData\Local\Temp\scoped_dir7024_1788179866" --no-appcompat-clear --enable-logging --log-level=0 --mojo-platform-channel-handle=3564 --field-trial-handle=2312,i,4332145636189932282,9270041941028546741,262144 --enable-features=msMetricsLogFastStartup,msSendMetricsLogOnClose --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 904 | "cmd" /v/c "set PFILES=%PROGRAMFILES(X86)%&& wmic datafile where name='!PFILES:\=\\!\\Microsoft\\Edge\\Application\\msedge.exe' get Version /value" | C:\Windows\SysWOW64\cmd.exe | — | selenium-manager.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --enable-logging --log-level=0 --user-data-dir="C:\Users\admin\AppData\Local\Temp\scoped_dir2076_789356361" --no-appcompat-clear --enable-logging --log-level=0 --mojo-platform-channel-handle=3828 --field-trial-handle=2272,i,16339092535393957953,13128668726113382074,262144 --enable-features=msMetricsLogFastStartup,msSendMetricsLogOnClose --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1020 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --enable-logging --log-level=0 --user-data-dir="C:\Users\admin\AppData\Local\Temp\scoped_dir2076_789356361" --no-appcompat-clear --enable-logging --log-level=0 --mojo-platform-channel-handle=3452 --field-trial-handle=2272,i,16339092535393957953,13128668726113382074,262144 --enable-features=msMetricsLogFastStartup,msSendMetricsLogOnClose --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1580 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --enable-logging --log-level=0 --user-data-dir="C:\Users\admin\AppData\Local\Temp\scoped_dir7024_1788179866" --no-appcompat-clear --enable-logging --log-level=0 --mojo-platform-channel-handle=2440 --field-trial-handle=2312,i,4332145636189932282,9270041941028546741,262144 --enable-features=msMetricsLogFastStartup,msSendMetricsLogOnClose --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2076 | C:\Users\admin\.cache\selenium\msedgedriver\win64\122.0.2365.120\msedgedriver.exe --port=49696 | C:\Users\admin\.cache\selenium\msedgedriver\win64\122.0.2365.120\msedgedriver.exe | AccGenerator.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge WebDriver Exit code: 0 Version: 122.0.2365.120 Modules
| |||||||||||||||
| 2380 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --enable-logging --log-level=0 --user-data-dir="C:\Users\admin\AppData\Local\Temp\scoped_dir2076_789356361" --no-appcompat-clear --enable-logging --log-level=0 --mojo-platform-channel-handle=5136 --field-trial-handle=2272,i,16339092535393957953,13128668726113382074,262144 --enable-features=msMetricsLogFastStartup,msSendMetricsLogOnClose --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2632 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | AccGenerator.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3040 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | AccGenerator.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 157
Read events
11 071
Write events
50
Delete events
36
Modification events
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AccGenerator.zip | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
30
Suspicious files
515
Text files
96
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6812 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI68122\_hashlib.pyd | executable | |
MD5:787B82D4466F393366657B8F1BC5F1A9 | SHA256:241322647BA9F94BDC3AE387413FFB57AE14C8CF88BD564A31FE193C6CA43E37 | |||
| 6812 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI68122\selenium\webdriver\common\linux\selenium-manager | — | |
MD5:— | SHA256:— | |||
| 6812 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI68122\_decimal.pyd | executable | |
MD5:692C751A1782CC4B54C203546F238B73 | SHA256:C70F05F6BC564FE400527B30C29461E9642FB973F66EEC719D282D3D0B402F93 | |||
| 6812 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI68122\_bz2.pyd | executable | |
MD5:A62207FC33140DE460444E191AE19B74 | SHA256:EBCAC51449F323AE3AE961A33843029C34B6A82138CCD9214CF99F98DD2148C2 | |||
| 6812 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI68122\libcrypto-1_1.dll | executable | |
MD5:9D7A0C99256C50AFD5B0560BA2548930 | SHA256:9B7B4A0AD212095A8C2E35C71694D8A1764CD72A829E8E17C8AFE3A55F147939 | |||
| 6812 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI68122\charset_normalizer\md__mypyc.cp311-win_amd64.pyd | executable | |
MD5:2D1F2FFD0FECF96A053043DAAD99A5DF | SHA256:207BBAE9DDF8BDD64E65A8D600FE1DD0465F2AFCD6DC6E28D4D55887CD6CBD13 | |||
| 6812 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI68122\_lzma.pyd | executable | |
MD5:0C7EA68CA88C07AE6B0A725497067891 | SHA256:F74AAF0AA08CF90EB1EB23A474CCB7CB706B1EDE7F911DAF7AE68480765BDF11 | |||
| 6812 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI68122\_queue.pyd | executable | |
MD5:06248702A6CD9D2DD20C0B1C6B02174D | SHA256:AC177CD84C12E03E3A68BCA30290BC0B8F173EEE518EF1FA6A9DCE3A3E755A93 | |||
| 6812 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI68122\libssl-1_1.dll | executable | |
MD5:BEC0F86F9DA765E2A02C9237259A7898 | SHA256:D74CE01319AE6F54483A19375524AA39D9F5FD91F06CF7DF238CA25E043130FD | |||
| 6812 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI68122\_uuid.pyd | executable | |
MD5:AEA6A82BFA35B61D86E8B6A5806F31D6 | SHA256:27B9545F5A510E71195951485D3C6A8B112917546FE5E8E46579B8FF6CE2ACB0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
129
DNS requests
123
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5320 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3560 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3560 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5356 | svchost.exe | GET | 200 | 23.48.23.189:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5356 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
— | — | 2.19.96.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 92.123.18.10:443 | go.microsoft.com | AKAMAI-AS | AT | whitelisted |
1076 | svchost.exe | 92.123.18.10:443 | go.microsoft.com | AKAMAI-AS | AT | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
msedgedriver.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
Process | Message |
|---|---|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir2076_789356361 directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir7024_1788179866 directory exists )
|