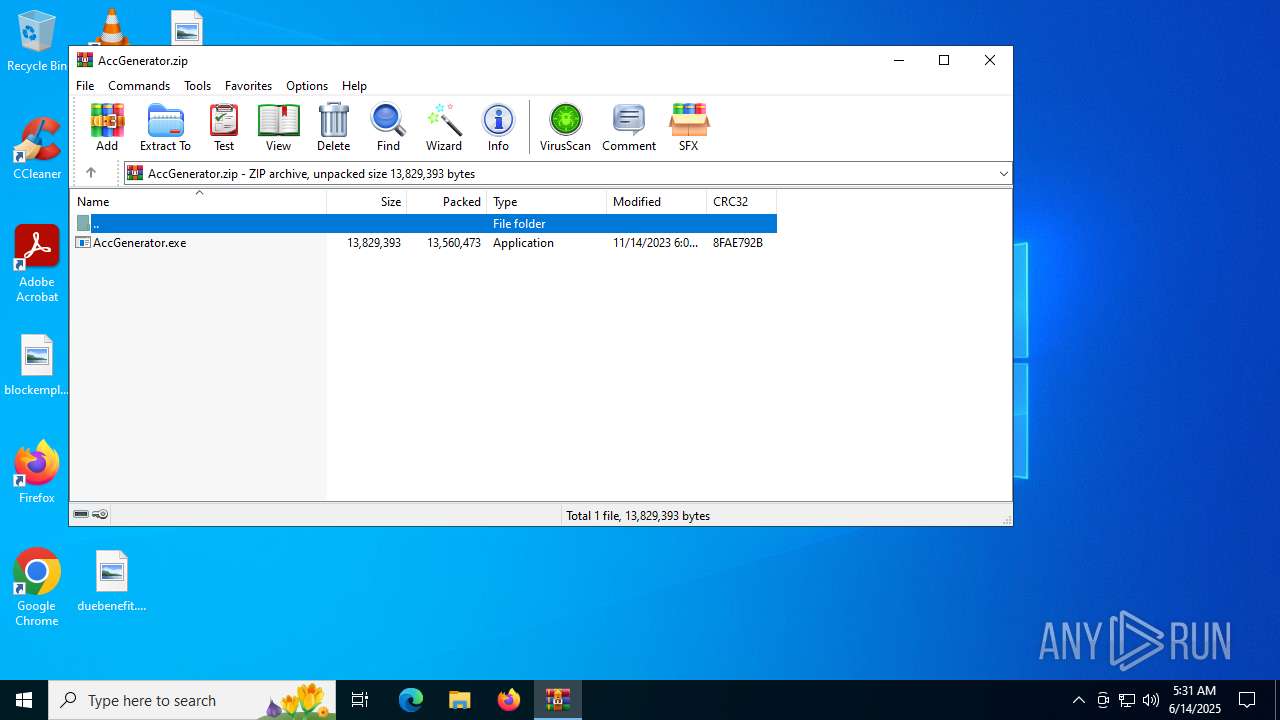
| File name: | AccGenerator.zip |
| Full analysis: | https://app.any.run/tasks/4c4c4e37-35dd-4fd1-a1c9-1323e4ec2e93 |
| Verdict: | Malicious activity |
| Analysis date: | June 14, 2025, 05:31:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | CE094A9EF628CD7BA0616D58AEC42512 |
| SHA1: | BCD7075F77CBD97A6196008F73F1768142C4DC39 |
| SHA256: | 470D90EC620DA317D6365412EC34A411D4ED0B12B90CC02399C5A57CA209A78E |
| SSDEEP: | 98304:RLAa4VEcXufZIHJlixL2rqqzjELMYvjQLQTnplr91Mulot99/boTS0mhrQlronlX:ua2AbZZ1OrQegZrSk0d1zN |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1560)
SUSPICIOUS
Process drops legitimate windows executable
- AccGenerator.exe (PID: 2864)
Executable content was dropped or overwritten
- AccGenerator.exe (PID: 2864)
The process drops C-runtime libraries
- AccGenerator.exe (PID: 2864)
Process drops python dynamic module
- AccGenerator.exe (PID: 2864)
Application launched itself
- AccGenerator.exe (PID: 2864)
Loads Python modules
- AccGenerator.exe (PID: 5504)
Starts CMD.EXE for commands execution
- AccGenerator.exe (PID: 5504)
INFO
Manual execution by a user
- AccGenerator.exe (PID: 2864)
Checks supported languages
- AccGenerator.exe (PID: 2864)
- AccGenerator.exe (PID: 5504)
Reads the computer name
- AccGenerator.exe (PID: 2864)
- AccGenerator.exe (PID: 5504)
The sample compiled with english language support
- AccGenerator.exe (PID: 2864)
Create files in a temporary directory
- AccGenerator.exe (PID: 2864)
Checks proxy server information
- AccGenerator.exe (PID: 5504)
- slui.exe (PID: 3624)
Reads the software policy settings
- slui.exe (PID: 3624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:11:14 18:00:08 |
| ZipCRC: | 0x8fae792b |
| ZipCompressedSize: | 13560473 |
| ZipUncompressedSize: | 13829393 |
| ZipFileName: | AccGenerator.exe |
Total processes
139
Monitored processes
6
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1560 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\AccGenerator.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2864 | "C:\Users\admin\Desktop\AccGenerator.exe" | C:\Users\admin\Desktop\AccGenerator.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 3624 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5504 | "C:\Users\admin\Desktop\AccGenerator.exe" | C:\Users\admin\Desktop\AccGenerator.exe | AccGenerator.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 5952 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AccGenerator.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7132 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | AccGenerator.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 300
Read events
5 285
Write events
15
Delete events
0
Modification events
| (PID) Process: | (1560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\AccGenerator.zip | |||
| (PID) Process: | (1560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (1560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
18
Suspicious files
7
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2864 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI28642\selenium\webdriver\common\linux\selenium-manager | — | |
MD5:— | SHA256:— | |||
| 2864 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI28642\charset_normalizer\md.cp311-win_amd64.pyd | executable | |
MD5:FA50D9F8BCE6BD13652F5090E7B82C4D | SHA256:FFF69928DEA1432E0C7CB1225AB96F94FD38D5D852DE9A6BB8BF30B7D2BEDCEB | |||
| 2864 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI28642\_decimal.pyd | executable | |
MD5:692C751A1782CC4B54C203546F238B73 | SHA256:C70F05F6BC564FE400527B30C29461E9642FB973F66EEC719D282D3D0B402F93 | |||
| 2864 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI28642\_hashlib.pyd | executable | |
MD5:787B82D4466F393366657B8F1BC5F1A9 | SHA256:241322647BA9F94BDC3AE387413FFB57AE14C8CF88BD564A31FE193C6CA43E37 | |||
| 2864 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI28642\libcrypto-1_1.dll | executable | |
MD5:9D7A0C99256C50AFD5B0560BA2548930 | SHA256:9B7B4A0AD212095A8C2E35C71694D8A1764CD72A829E8E17C8AFE3A55F147939 | |||
| 2864 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI28642\_lzma.pyd | executable | |
MD5:0C7EA68CA88C07AE6B0A725497067891 | SHA256:F74AAF0AA08CF90EB1EB23A474CCB7CB706B1EDE7F911DAF7AE68480765BDF11 | |||
| 2864 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI28642\_queue.pyd | executable | |
MD5:06248702A6CD9D2DD20C0B1C6B02174D | SHA256:AC177CD84C12E03E3A68BCA30290BC0B8F173EEE518EF1FA6A9DCE3A3E755A93 | |||
| 2864 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI28642\_ssl.pyd | executable | |
MD5:AB0E4FBFFB6977D0196C7D50BC76CF2D | SHA256:680AD2DE8A6CFF927822C1D7DD22112A3E8A824E82A7958EE409A7B9CE45EC70 | |||
| 2864 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI28642\_uuid.pyd | executable | |
MD5:AEA6A82BFA35B61D86E8B6A5806F31D6 | SHA256:27B9545F5A510E71195951485D3C6A8B112917546FE5E8E46579B8FF6CE2ACB0 | |||
| 2864 | AccGenerator.exe | C:\Users\admin\AppData\Local\Temp\_MEI28642\VCRUNTIME140.dll | executable | |
MD5:4585A96CC4EEF6AAFD5E27EA09147DC6 | SHA256:A8F950B4357EC12CFCCDDC9094CCA56A3D5244B95E09EA6E9A746489F2D58736 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
41
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6172 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6172 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.75:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.129:443 | https://login.live.com/RST2.srf | unknown | xml | 11.0 Kb | whitelisted |
— | — | GET | 304 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1352 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6172 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6172 | RUXIMICS.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |