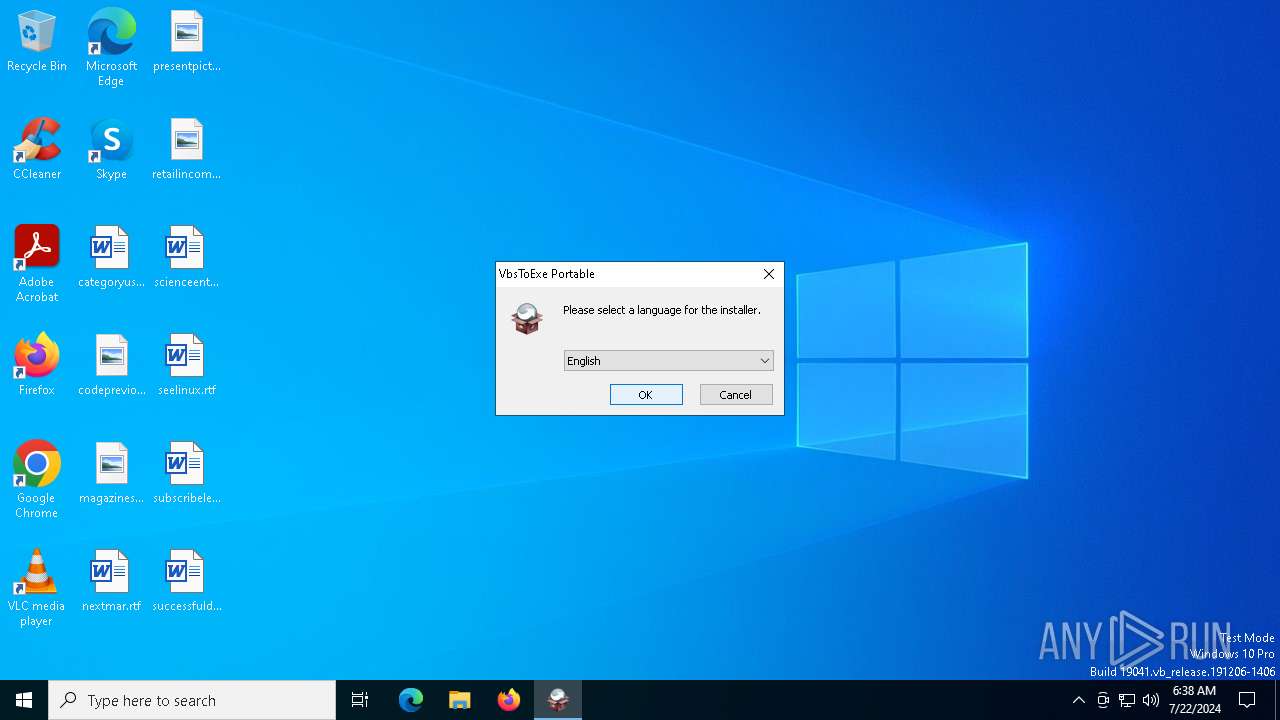
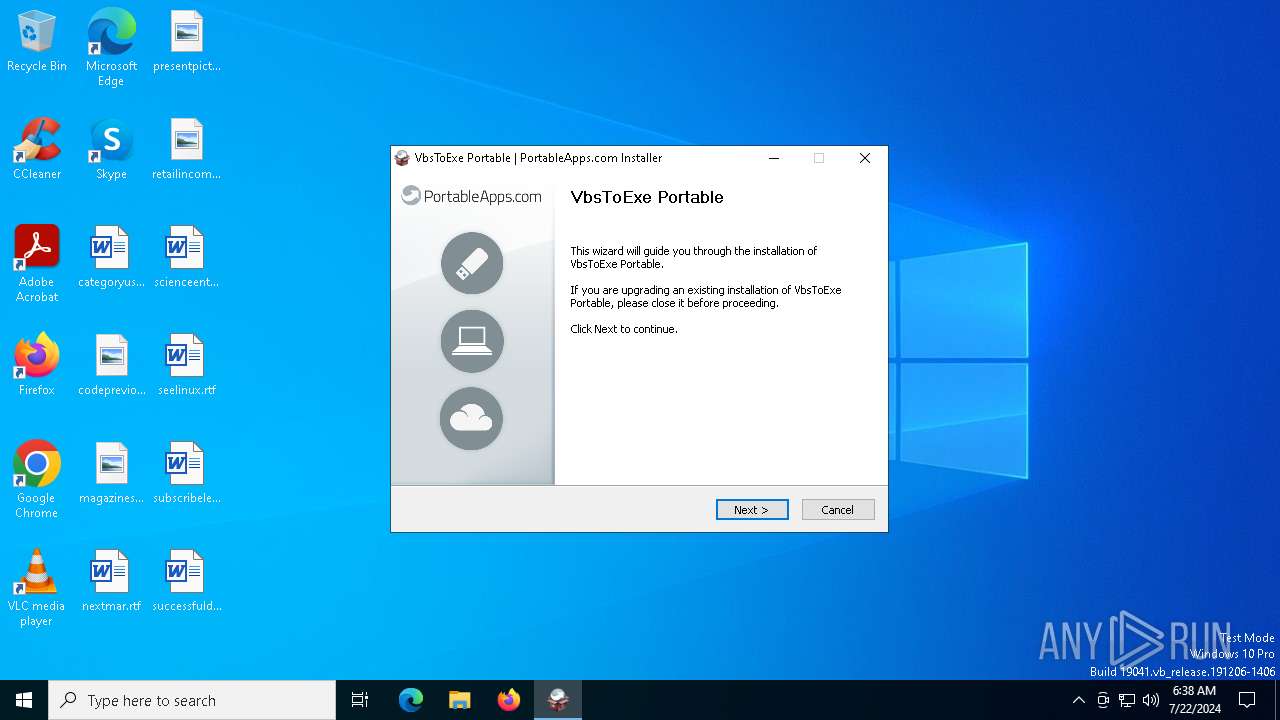
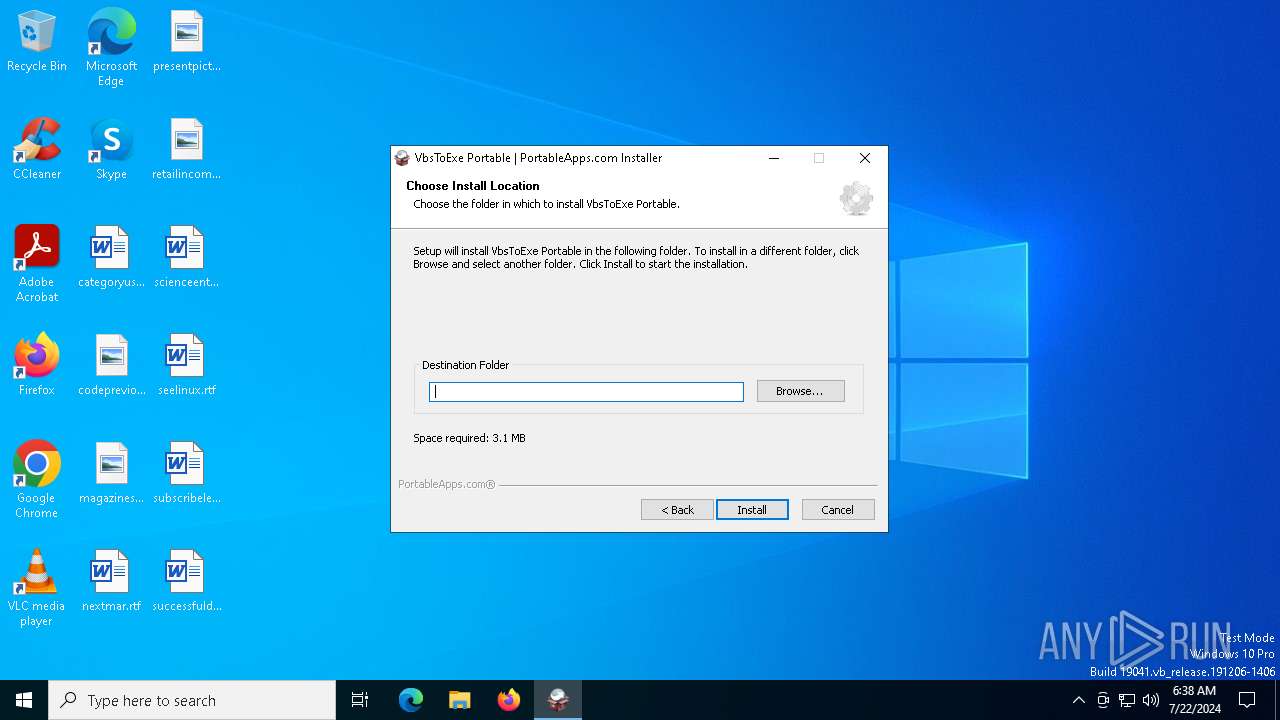
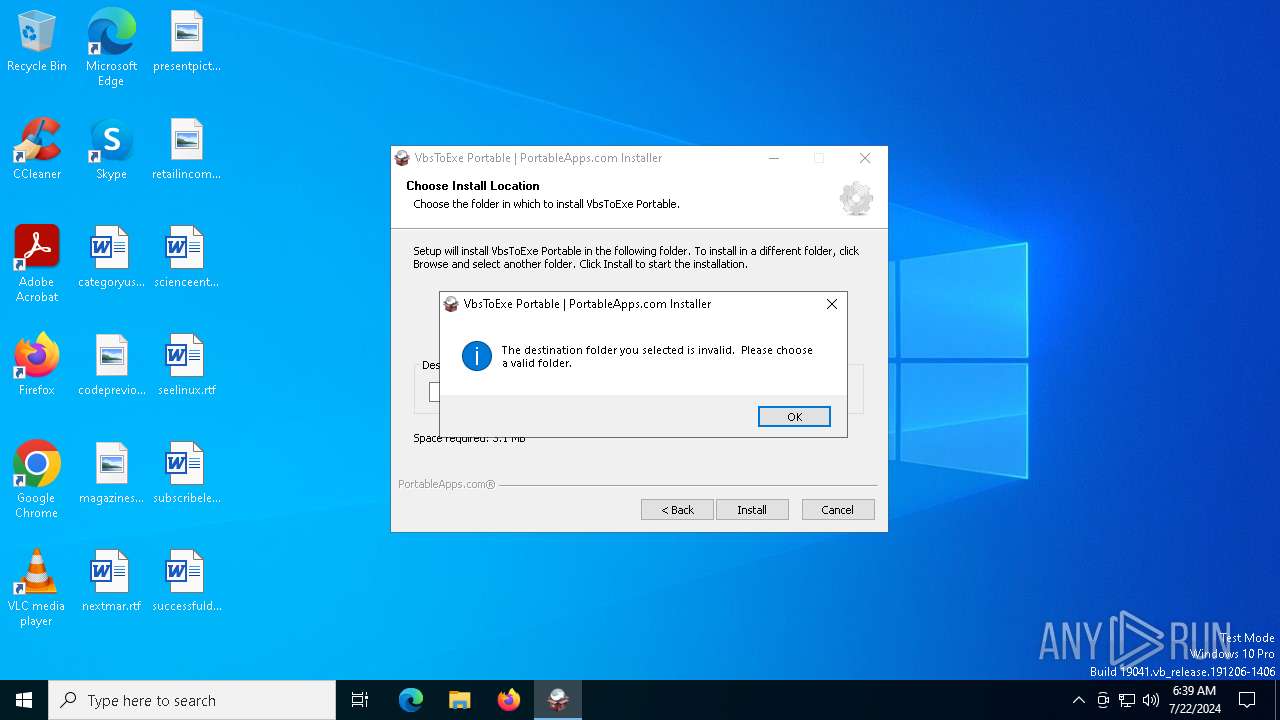
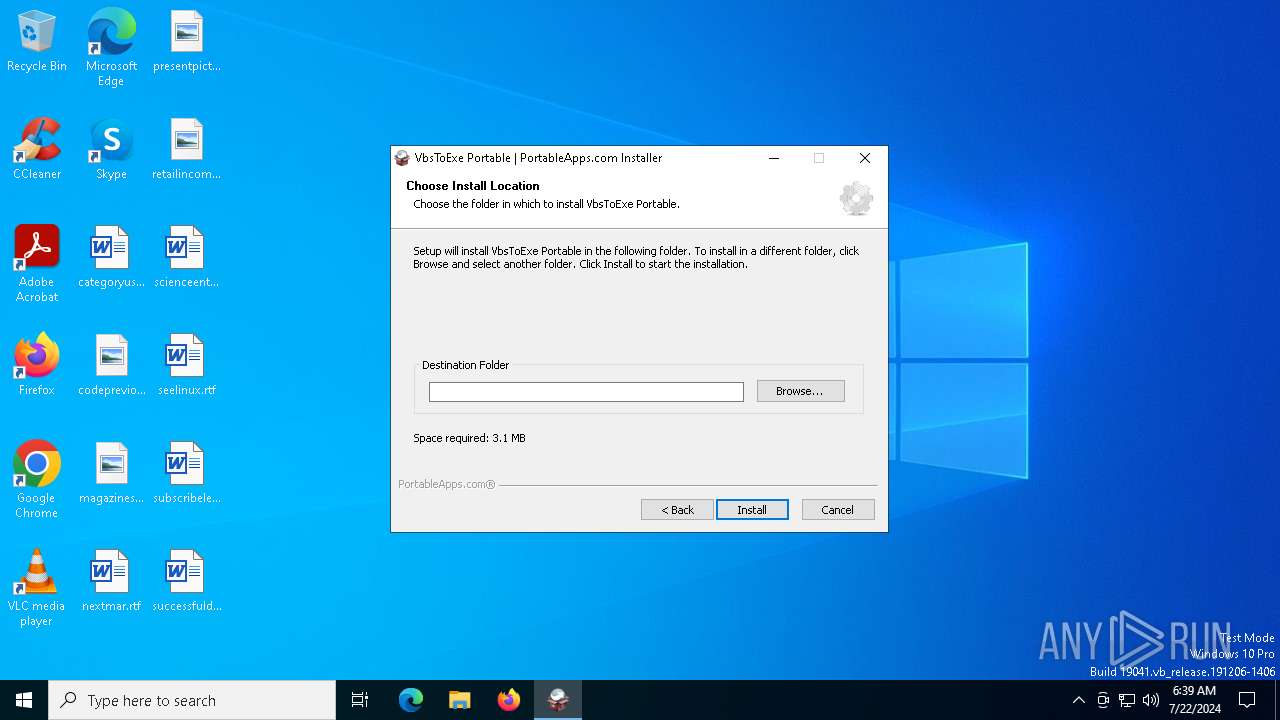
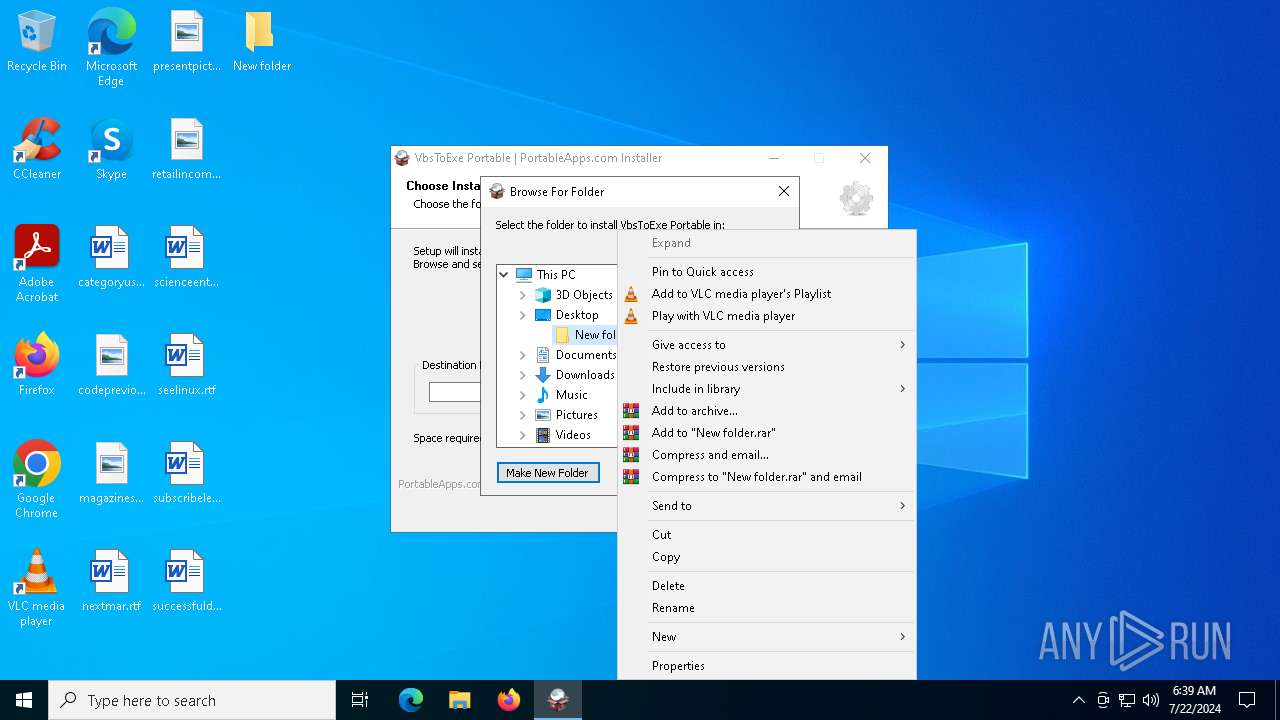
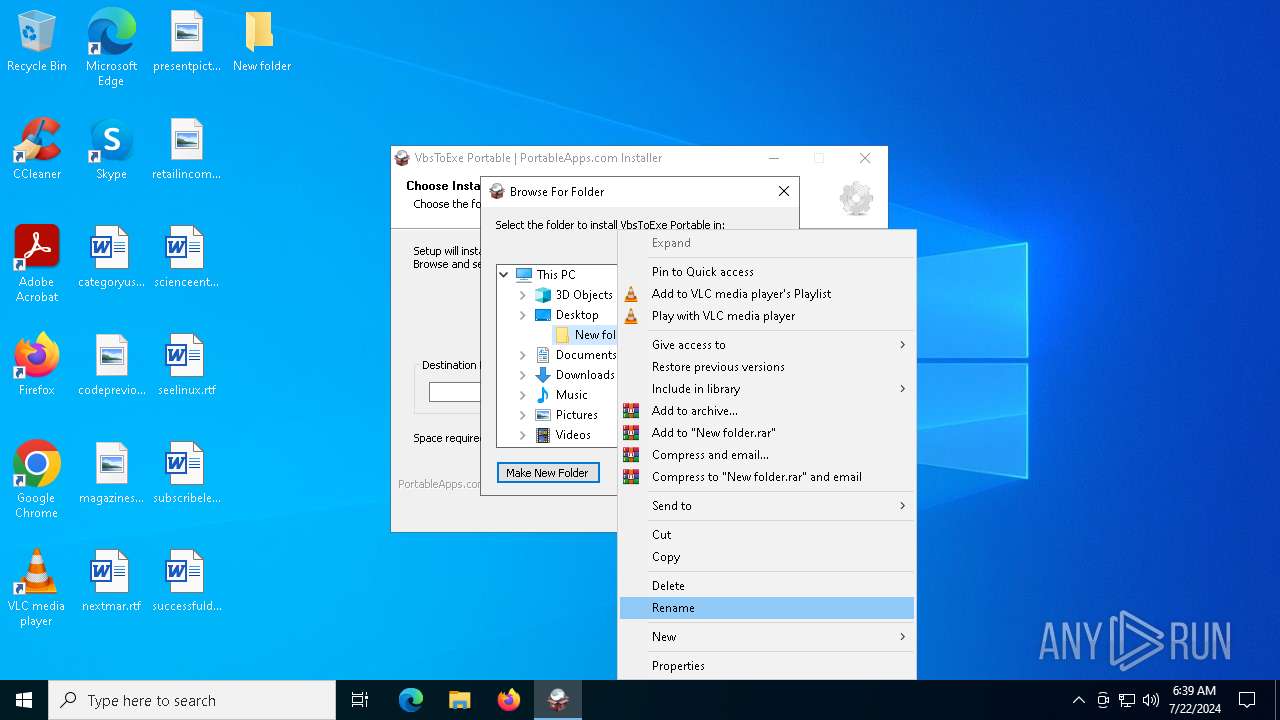
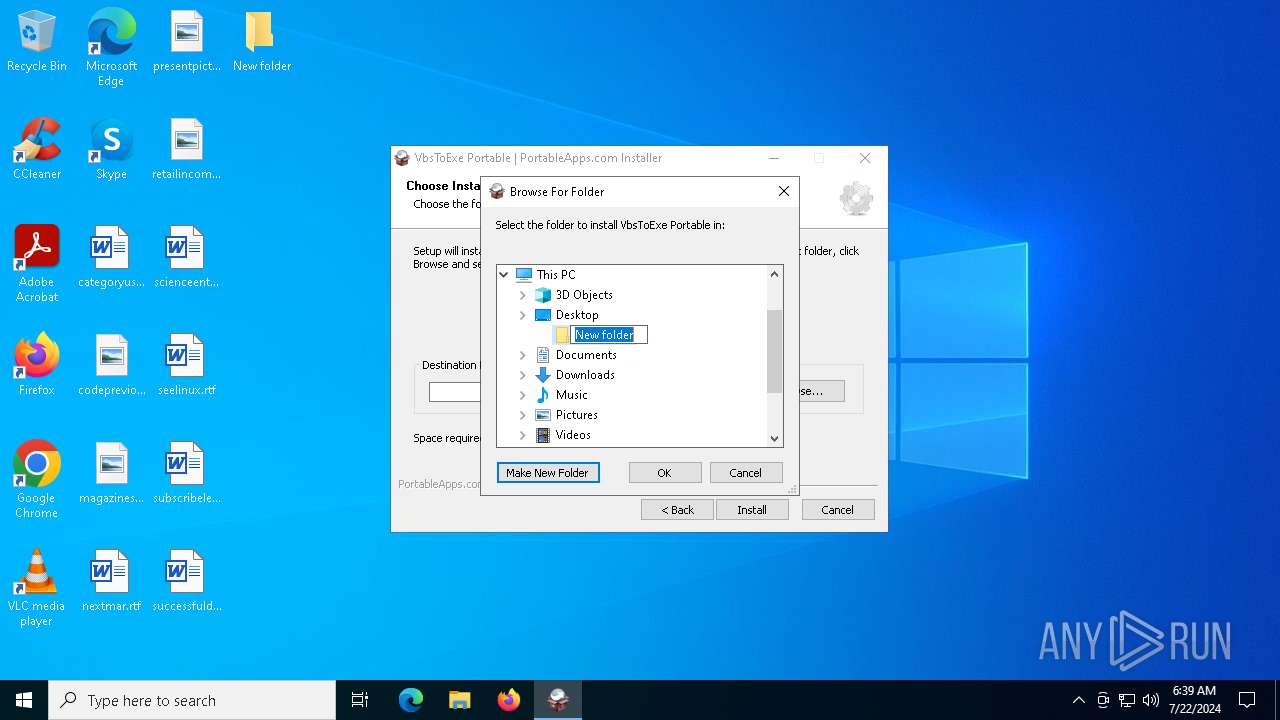
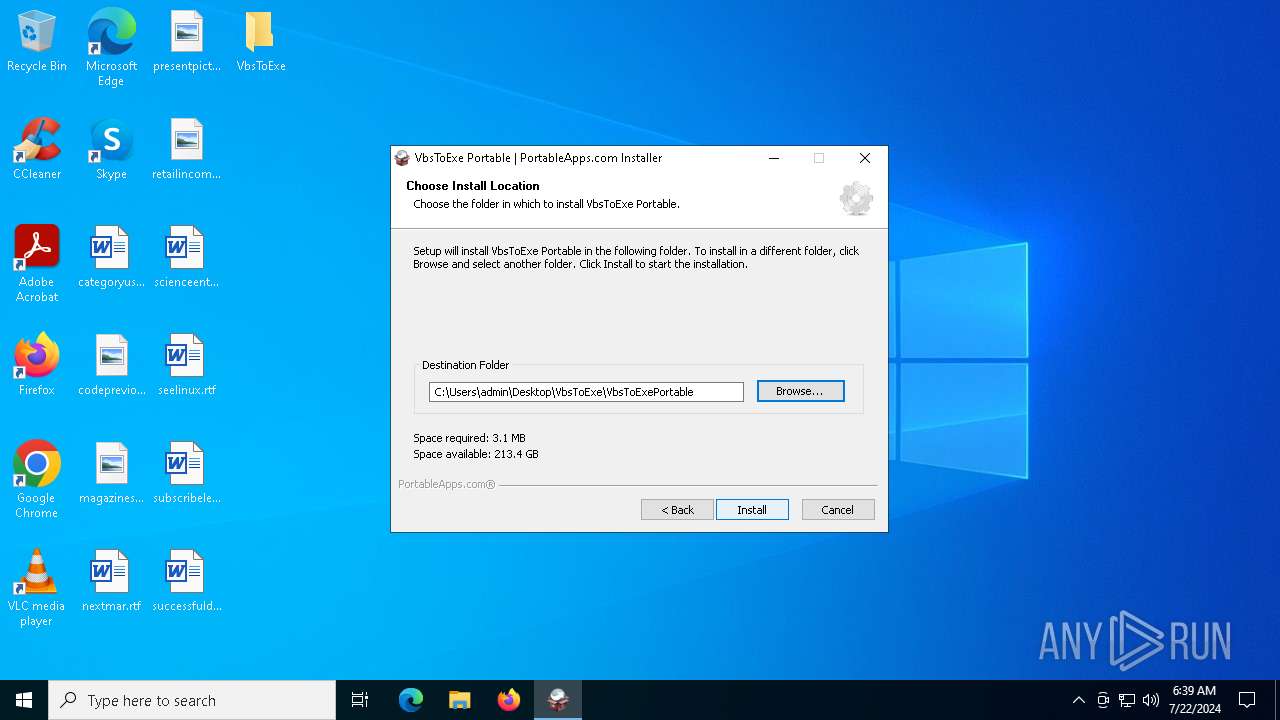
| File name: | VbsToExePortable_3.2_Dev_Test_1.paf.exe |
| Full analysis: | https://app.any.run/tasks/0d6f9cc4-2858-40fc-836a-b9c4269b20b0 |
| Verdict: | Malicious activity |
| Analysis date: | July 22, 2024, 06:38:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | ED9776CDE2D5CBEFE7A9694FB6764CDD |
| SHA1: | D0D06013E017291F5EA2DBBA652DD133B2CA55F5 |
| SHA256: | 470887F40264DCECD818DED225970338D2C84CBC3B7D0A3169BDA7582D83633B |
| SSDEEP: | 98304:1aXNOJY5KMlZA0Tkffj8kmI3OB3l6hOlWApuOlEuXve4OM9kIOhIxOsshp1nqgML:vIo4FsLLMUY |
MALICIOUS
Drops the executable file immediately after the start
- VbsToExePortable_3.2_Dev_Test_1.paf.exe (PID: 1456)
- VbsToExePortable.exe (PID: 7064)
- Vbs_To_Exe_(x64).exe (PID: 5696)
SUSPICIOUS
Executable content was dropped or overwritten
- VbsToExePortable_3.2_Dev_Test_1.paf.exe (PID: 1456)
- VbsToExePortable.exe (PID: 7064)
- Vbs_To_Exe_(x64).exe (PID: 5696)
The process creates files with name similar to system file names
- VbsToExePortable_3.2_Dev_Test_1.paf.exe (PID: 1456)
- VbsToExePortable.exe (PID: 7064)
Malware-specific behavior (creating "System.dll" in Temp)
- VbsToExePortable_3.2_Dev_Test_1.paf.exe (PID: 1456)
- VbsToExePortable.exe (PID: 7064)
Reads the date of Windows installation
- VbsToExePortable_3.2_Dev_Test_1.paf.exe (PID: 1456)
Reads security settings of Internet Explorer
- VbsToExePortable_3.2_Dev_Test_1.paf.exe (PID: 1456)
- VbsToExePortable.exe (PID: 7064)
- Vbs_To_Exe_(x64).exe (PID: 5696)
There is functionality for taking screenshot (YARA)
- Vbs_To_Exe_(x64).exe (PID: 5696)
Reads Microsoft Outlook installation path
- Vbs_To_Exe_(x64).exe (PID: 5696)
Reads Internet Explorer settings
- Vbs_To_Exe_(x64).exe (PID: 5696)
INFO
Checks supported languages
- VbsToExePortable_3.2_Dev_Test_1.paf.exe (PID: 1456)
- VbsToExePortable.exe (PID: 7064)
- Vbs_To_Exe_(x64).exe (PID: 5696)
Reads the computer name
- VbsToExePortable_3.2_Dev_Test_1.paf.exe (PID: 1456)
- VbsToExePortable.exe (PID: 7064)
- Vbs_To_Exe_(x64).exe (PID: 5696)
Create files in a temporary directory
- VbsToExePortable_3.2_Dev_Test_1.paf.exe (PID: 1456)
- VbsToExePortable.exe (PID: 7064)
- Vbs_To_Exe_(x64).exe (PID: 5696)
Process checks Internet Explorer phishing filters
- Vbs_To_Exe_(x64).exe (PID: 5696)
UPX packer has been detected
- Vbs_To_Exe_(x64).exe (PID: 5696)
Checks proxy server information
- Vbs_To_Exe_(x64).exe (PID: 5696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:26:01+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 428544 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x34a5 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.1.99.1 |
| ProductVersionNumber: | 3.1.99.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | For additional details, visit PortableApps.com |
| CompanyName: | PortableApps.com |
| FileDescription: | VbsToExe Portable |
| FileVersion: | 3.1.99.1 |
| InternalName: | VbsToExe Portable |
| LegalCopyright: | 2007-2019 PortableApps.com, PortableApps.com Installer 3.5.14.0 |
| LegalTrademarks: | PortableApps.com is a registered trademark of Rare Ideas, LLC. |
| OriginalFileName: | VbsToExePortable_3.2_Dev_Test_1.paf.exe |
| PortableAppscomAppID: | VbsToExePortable |
| PortableAppscomFormatVersion: | 3.5.14 |
| PortableAppscomInstallerVersion: | 3.5.14.0 |
| ProductName: | VbsToExe Portable |
| ProductVersion: | 3.1.99.1 |
Total processes
139
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1456 | "C:\Users\admin\AppData\Local\Temp\VbsToExePortable_3.2_Dev_Test_1.paf.exe" | C:\Users\admin\AppData\Local\Temp\VbsToExePortable_3.2_Dev_Test_1.paf.exe | explorer.exe | ||||||||||||
User: admin Company: PortableApps.com Integrity Level: MEDIUM Description: VbsToExe Portable Exit code: 0 Version: 3.1.99.1 Modules
| |||||||||||||||
| 5696 | "C:\Users\admin\Desktop\VbsToExe\VbsToExePortable\App\VbsToExe\Vbs_To_Exe_(x64).exe" | C:\Users\admin\Desktop\VbsToExe\VbsToExePortable\App\VbsToExe\Vbs_To_Exe_(x64).exe | VbsToExePortable.exe | ||||||||||||
User: admin Company: Fatih Kodak Integrity Level: MEDIUM Description: Vbs To Exe Version: 3.2 Modules
| |||||||||||||||
| 6868 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7064 | "C:\Users\admin\Desktop\VbsToExe\VbsToExePortable\VbsToExePortable.exe" | C:\Users\admin\Desktop\VbsToExe\VbsToExePortable\VbsToExePortable.exe | VbsToExePortable_3.2_Dev_Test_1.paf.exe | ||||||||||||
User: admin Company: PortableApps.com Integrity Level: MEDIUM Description: VbsToExe Portable (PortableApps.com Launcher) Version: 2.2.1.0 Modules
| |||||||||||||||
Total events
18 975
Read events
18 915
Write events
56
Delete events
4
Modification events
| (PID) Process: | (1456) VbsToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 87 | |||
| (PID) Process: | (1456) VbsToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 8AFE9D6600000000 | |||
| (PID) Process: | (1456) VbsToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-123 |
Value: Microsoft Word Document | |||
| (PID) Process: | (1456) VbsToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-174 |
Value: Microsoft PowerPoint Presentation | |||
| (PID) Process: | (1456) VbsToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-131 |
Value: Rich Text Format | |||
| (PID) Process: | (1456) VbsToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-101 |
Value: Microsoft Excel Worksheet | |||
| (PID) Process: | (1456) VbsToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\ShellNew |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1456) VbsToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\ShellNew |
| Operation: | write | Name: | Classes |
Value: .accdb | |||
| (PID) Process: | (1456) VbsToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\ShellNew |
| Operation: | write | Name: | ~reserved~ |
Value: 0800000000000600 | |||
| (PID) Process: | (1456) VbsToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
Executable files
13
Suspicious files
7
Text files
44
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1456 | VbsToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\AppData\Local\Temp\nszA411.tmp\modern-header.bmp | image | |
MD5:B38AB57798D466422DFD9146A5DE37A9 | SHA256:F11C32AC449E53052B607374B92E5C9B52D6145C9092C7F029023ADC61FD4AC7 | |||
| 1456 | VbsToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\AppData\Local\Temp\nszA411.tmp\LangDLL.dll | executable | |
MD5:AB1DB56369412FE8476FEFFFD11E4CC0 | SHA256:6F14C8F01F50A30743DAC68C5AC813451463DFB427EB4E35FCDFE2410E1A913B | |||
| 1456 | VbsToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\Desktop\VbsToExe\VbsToExePortable\App\Readme.txt | text | |
MD5:39809395CA95E97C59CB866F342435E3 | SHA256:6DDD6B23FDDDEFD100900089CC6873D6506D4EB496B7D570AB388823E44675C4 | |||
| 1456 | VbsToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\AppData\Local\Temp\nszA411.tmp\w7tbp.dll | executable | |
MD5:9A3031CC4CEF0DBA236A28EECDF0AFB5 | SHA256:53BB519E3293164947AC7CBD7E612F637D77A7B863E3534BA1A7E39B350D3C00 | |||
| 1456 | VbsToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\Desktop\VbsToExe\VbsToExePortable\App\AppInfo\appicon_256.png | image | |
MD5:0D2F25B26FCFBA86D666328F4EE0AF19 | SHA256:839EBBC3B683060288E93D81E3824172EA2C0EA4C98422822BEDCD2891EB5123 | |||
| 1456 | VbsToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\Desktop\VbsToExe\VbsToExePortable\App\AppInfo\appicon_128.png | image | |
MD5:17AE1CE224B839F70CAE38802A27CC51 | SHA256:7D5CB97236C79DDB04BF08D4BC6C5A065A881786429CEAB3176A372061E6161F | |||
| 1456 | VbsToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\Desktop\VbsToExe\VbsToExePortable\App\AppInfo\appicon_32.png | image | |
MD5:B935639C20E0F3C3FDE34536D7C11BDE | SHA256:71EC24BDC833FC38FF7B11612502532503536AE03C987E915022C5E73805375D | |||
| 1456 | VbsToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\Desktop\VbsToExe\VbsToExePortable\App\AppInfo\Launcher\VbsToExePortable.ini | ini | |
MD5:BE7DC6460C7A46D987EE3EA03DEE5F1B | SHA256:E52E67AEBF3C1B0D332C9C957B6BE40A958D7BD71F90AD34A6EA8624E7E35F27 | |||
| 1456 | VbsToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\Desktop\VbsToExe\VbsToExePortable\help.html | html | |
MD5:46A3C4E95E0EF1533932875026B3B74B | SHA256:73218D023F0B2677F6D30157EAA278C0949A62DDF54054CD7904762F0B350470 | |||
| 1456 | VbsToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\AppData\Local\Temp\nszA411.tmp\System.dll | executable | |
MD5:0D7AD4F45DC6F5AA87F606D0331C6901 | SHA256:3EB38AE99653A7DBC724132EE240F6E5C4AF4BFE7C01D31D23FAF373F9F2EACA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
33
DNS requests
13
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4716 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5620 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7856 | svchost.exe | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.113.110.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2760 | svchost.exe | 40.113.110.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7976 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4716 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5620 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |