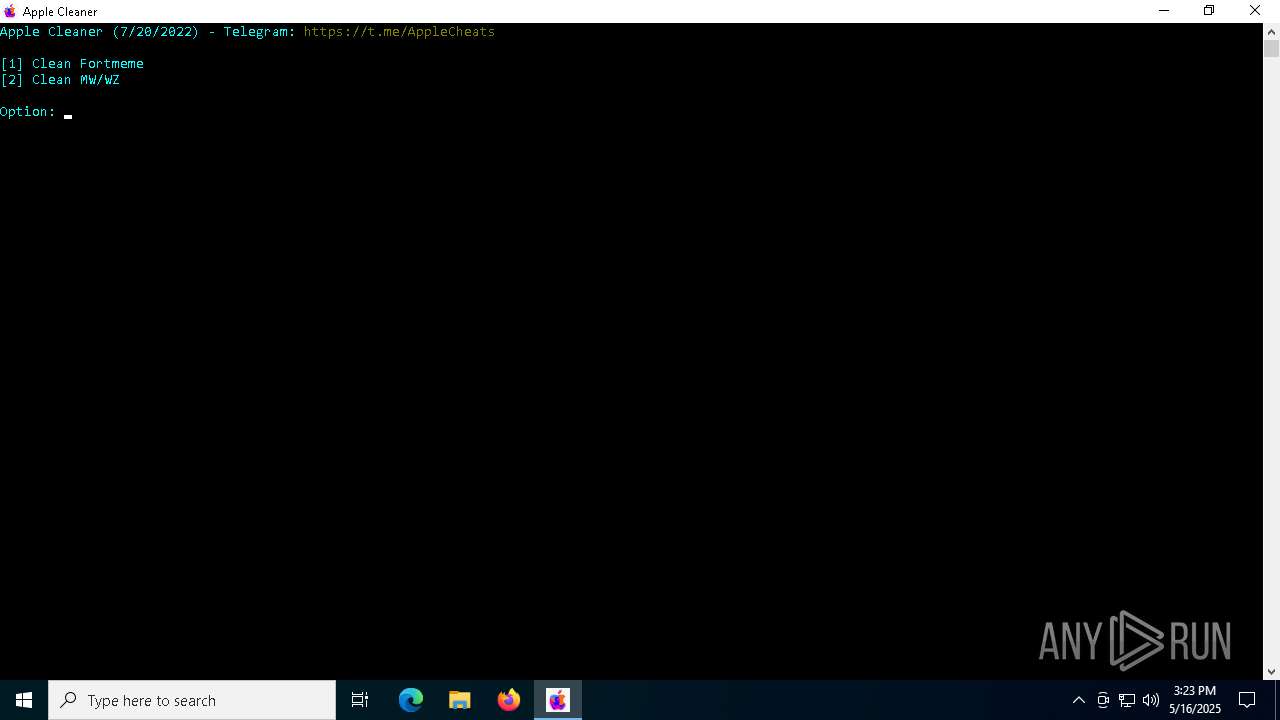
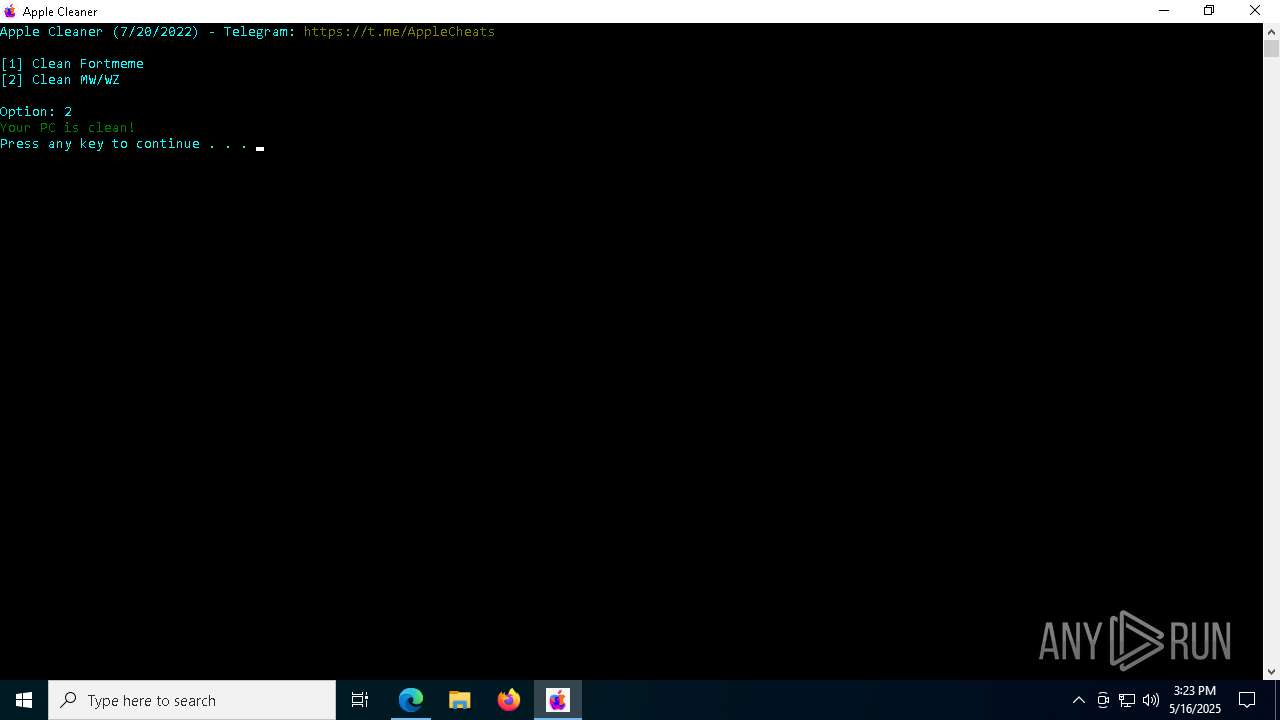
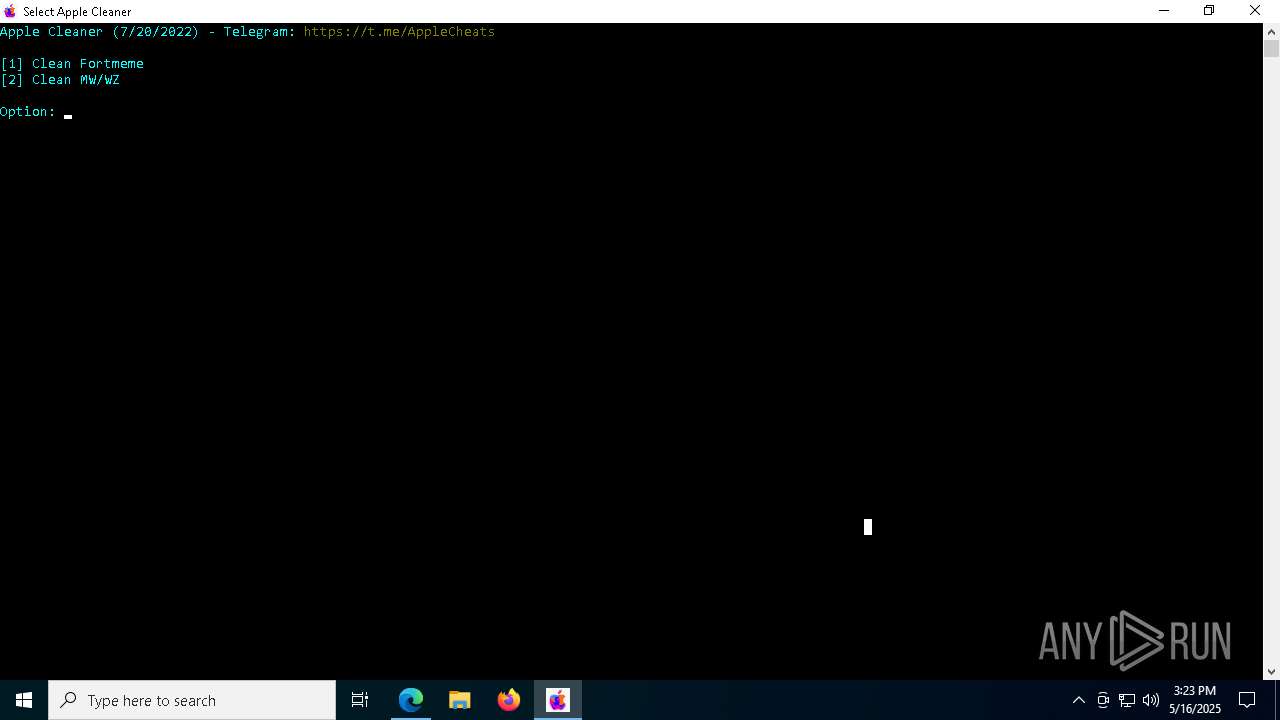
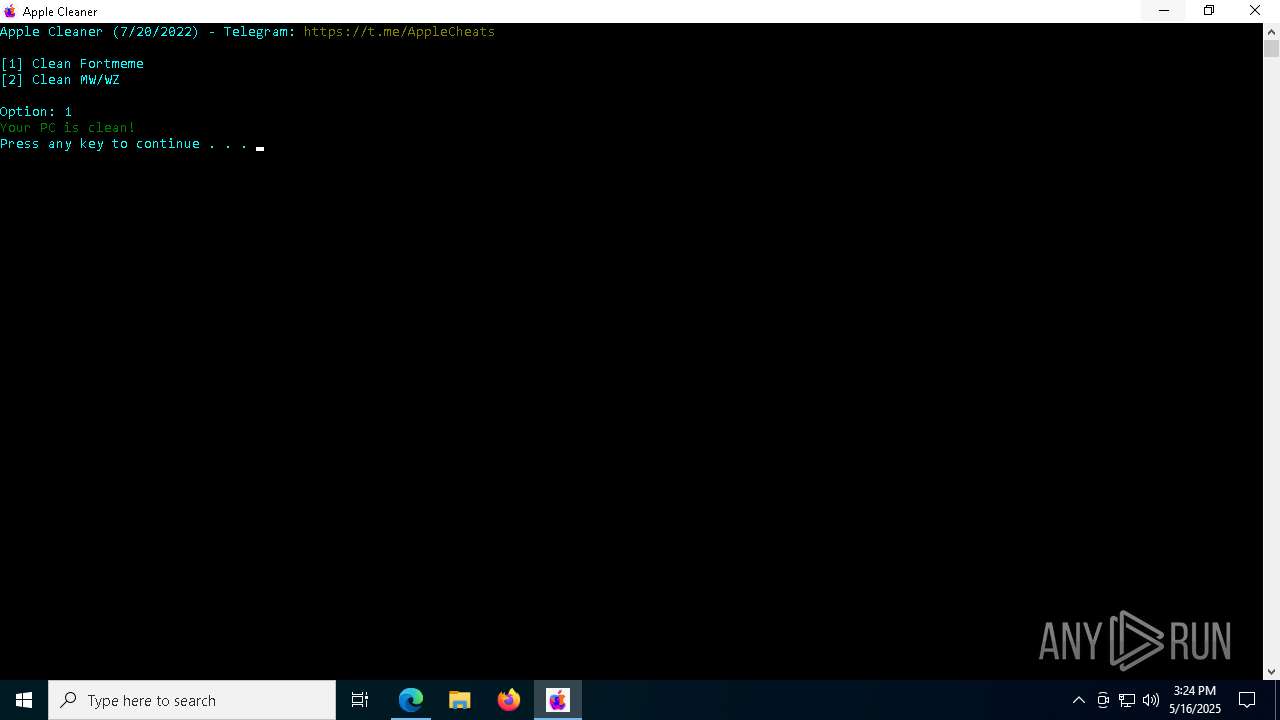
| File name: | applecleaner.exe |
| Full analysis: | https://app.any.run/tasks/fc50726c-aa56-4618-9034-ca84f58d45f2 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 15:22:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 12 sections |
| MD5: | F96EB2236970FB3EA97101B923AF4228 |
| SHA1: | E0EED80F1054ACBF5389A7B8860A4503DD3E184A |
| SHA256: | 46FE5192387D3F897A134D29C069EBF39C72094C892134D2F0E77B12B11A6172 |
| SSDEEP: | 98304:z7m+ij9HD0+jCihNRkl/W6aG/wcKnfu8NUT6Ko:e+y4ihkl/Wo/afHPb |
MALICIOUS
Changes the autorun value in the registry
- applecleaner.exe (PID: 4024)
- netsh.exe (PID: 8496)
- netsh.exe (PID: 1096)
Scans artifacts that could help determine the target
- applecleaner.exe (PID: 4024)
SUSPICIOUS
Reads the BIOS version
- applecleaner.exe (PID: 4024)
Hides command output
- cmd.exe (PID: 7252)
- cmd.exe (PID: 7364)
- cmd.exe (PID: 7420)
- cmd.exe (PID: 8660)
- cmd.exe (PID: 8600)
- cmd.exe (PID: 8780)
- cmd.exe (PID: 8840)
- cmd.exe (PID: 8320)
- cmd.exe (PID: 8480)
- cmd.exe (PID: 8540)
- cmd.exe (PID: 8720)
- cmd.exe (PID: 8992)
- cmd.exe (PID: 8948)
- cmd.exe (PID: 9036)
- cmd.exe (PID: 9080)
- cmd.exe (PID: 9124)
- cmd.exe (PID: 9168)
- cmd.exe (PID: 9212)
- cmd.exe (PID: 5744)
- cmd.exe (PID: 8900)
- cmd.exe (PID: 8268)
- cmd.exe (PID: 8540)
- cmd.exe (PID: 8696)
- cmd.exe (PID: 8756)
- cmd.exe (PID: 7908)
- cmd.exe (PID: 8484)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 2040)
- cmd.exe (PID: 6208)
- cmd.exe (PID: 2240)
- cmd.exe (PID: 8436)
- cmd.exe (PID: 6108)
- cmd.exe (PID: 5360)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 8584)
- cmd.exe (PID: 8320)
- cmd.exe (PID: 8536)
- cmd.exe (PID: 8680)
- cmd.exe (PID: 8600)
- cmd.exe (PID: 8732)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7252)
- cmd.exe (PID: 7364)
- cmd.exe (PID: 7420)
Reads security settings of Internet Explorer
- applecleaner.exe (PID: 4024)
Reads the Windows owner or organization settings
- applecleaner.exe (PID: 4024)
Detected use of alternative data streams (AltDS)
- applecleaner.exe (PID: 4024)
Starts CMD.EXE for commands execution
- applecleaner.exe (PID: 4024)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 8600)
- cmd.exe (PID: 8660)
- cmd.exe (PID: 8720)
- cmd.exe (PID: 8780)
- cmd.exe (PID: 8840)
- cmd.exe (PID: 8480)
- cmd.exe (PID: 8540)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 7908)
- cmd.exe (PID: 2040)
- cmd.exe (PID: 8436)
- cmd.exe (PID: 5360)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 2240)
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 8948)
- cmd.exe (PID: 8900)
- cmd.exe (PID: 6108)
- cmd.exe (PID: 6208)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 8992)
- cmd.exe (PID: 8320)
Uses WMIC.EXE
- cmd.exe (PID: 9212)
- cmd.exe (PID: 5744)
- cmd.exe (PID: 8268)
- cmd.exe (PID: 8484)
- cmd.exe (PID: 8540)
- cmd.exe (PID: 8696)
- cmd.exe (PID: 8732)
Process uses ARP to discover network configuration
- cmd.exe (PID: 9124)
- cmd.exe (PID: 8600)
Process uses NBTSTAT to discover network configuration
- cmd.exe (PID: 9036)
- cmd.exe (PID: 8584)
INFO
Process checks whether UAC notifications are on
- applecleaner.exe (PID: 4024)
Checks supported languages
- applecleaner.exe (PID: 4024)
- identity_helper.exe (PID: 7972)
Reads the machine GUID from the registry
- applecleaner.exe (PID: 4024)
Reads Environment values
- applecleaner.exe (PID: 4024)
- identity_helper.exe (PID: 7972)
Reads Windows Product ID
- applecleaner.exe (PID: 4024)
Reads the computer name
- applecleaner.exe (PID: 4024)
- identity_helper.exe (PID: 7972)
Creates files or folders in the user directory
- applecleaner.exe (PID: 4024)
Checks proxy server information
- applecleaner.exe (PID: 4024)
Reads the software policy settings
- applecleaner.exe (PID: 4024)
Manual execution by a user
- msedge.exe (PID: 7848)
Application launched itself
- msedge.exe (PID: 7572)
- msedge.exe (PID: 7848)
Disables trace logs
- netsh.exe (PID: 8556)
- netsh.exe (PID: 8676)
- netsh.exe (PID: 8736)
- netsh.exe (PID: 8796)
- netsh.exe (PID: 8856)
- netsh.exe (PID: 7444)
- netsh.exe (PID: 1128)
- netsh.exe (PID: 7364)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 8196)
- WMIC.exe (PID: 6760)
- WMIC.exe (PID: 8292)
- WMIC.exe (PID: 8576)
- WMIC.exe (PID: 8684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:04:13 04:07:30+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.31 |
| CodeSize: | 146432 |
| InitializedDataSize: | 101376 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x62c058 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
280
Monitored processes
142
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6200 --field-trial-handle=2428,i,8793537783953505167,8663555654445918313,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1040 | C:\WINDOWS\system32\cmd.exe /c NETSH WINSOCK RESET >nul 2>&1 | C:\Windows\System32\cmd.exe | — | applecleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | NETSH WINSOCK RESET | C:\Windows\System32\netsh.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | NETSH INTERFACE TCP RESET | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=5960 --field-trial-handle=2428,i,8793537783953505167,8663555654445918313,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2040 | C:\WINDOWS\system32\cmd.exe /c NETSH INTERFACE IPV6 RESET >nul 2>&1 | C:\Windows\System32\cmd.exe | — | applecleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=4192 --field-trial-handle=2428,i,8793537783953505167,8663555654445918313,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2240 | C:\WINDOWS\system32\cmd.exe /c NETSH INTERFACE TCP RESET >nul 2>&1 | C:\Windows\System32\cmd.exe | — | applecleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | applecleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2332 | IPCONFIG /RELEASE | C:\Windows\System32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 741
Read events
15 742
Write events
723
Delete events
276
Modification events
| (PID) Process: | (7524) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7524) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4024) applecleaner.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography |
| Operation: | write | Name: | MachineGuid |
Value: 4bf9fffa-cc43-aad0-eea5-3e9cad330ebb | |||
| (PID) Process: | (4024) applecleaner.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion |
| Operation: | write | Name: | InstallTime |
Value: 04790000C8290000 | |||
| (PID) Process: | (4024) applecleaner.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion |
| Operation: | write | Name: | InstallDate |
Value: FF6E0000C4130000 | |||
| (PID) Process: | (4024) applecleaner.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion |
| Operation: | write | Name: | BuildLabEx |
Value: 1c992.a.d118d0d2.e7_93ea971.419cd2-323f | |||
| (PID) Process: | (4024) applecleaner.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\IDConfigDB\Hardware Profiles\0001 |
| Operation: | write | Name: | HwProfileGuid |
Value: {e7dffb0e-c8bc-d243-e0db-b58845831de5} | |||
| (PID) Process: | (4024) applecleaner.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\ComputerName\ActiveComputerName |
| Operation: | write | Name: | ComputerName |
Value: DESKTOP-ONGQKDE | |||
| (PID) Process: | (4024) applecleaner.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\ComputerName\ComputerName |
| Operation: | write | Name: | ComputerName |
Value: DESKTOP-MQLGDBA | |||
| (PID) Process: | (4024) applecleaner.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters |
| Operation: | write | Name: | Hostname |
Value: DESKTOP-AKFFJGB | |||
Executable files
10
Suspicious files
228
Text files
37
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF110bf3.TMP | — | |
MD5:— | SHA256:— | |||
| 7848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF110bf3.TMP | — | |
MD5:— | SHA256:— | |||
| 7848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:1AF1D1ED27A40F9FDA977B6C353EC48B | SHA256:01B66ED195749BF7909E0B655A6C4C6AFDECD665D7304653D09CD538191CC50A | |||
| 7848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF110bf3.TMP | — | |
MD5:— | SHA256:— | |||
| 7848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7848 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7572 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:1E9E15EF6E531C4557100F20C9C76F01 | SHA256:46CB063CC268B69B172660F166C4394D5B4EDD802388B3EC16766DEBDB9F86C3 | |||
| 7572 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:C7E2197BAE099B13BBB3ADEB1433487D | SHA256:3460EEAF45D581DD43A6E4E17AF8102DDAFF5AEAA88B10099527CF85211629E9 | |||
| 7572 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\7080924e-9de2-4ec4-bfd4-297d90498f1b.tmp | binary | |
MD5:EFB3E148B7E38E0A821674F5EC40F0E4 | SHA256:52F430D162F45B6F98AF07B9FB3940FD35776A83C7633EA1BBE571B21DDABAB6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
52
DNS requests
45
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.32:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4024 | applecleaner.exe | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
4024 | applecleaner.exe | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
8380 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8380 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3768 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.32:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
applecheats.cc |
| unknown |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
8164 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
8164 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
8164 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
8164 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
8164 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
4024 | applecleaner.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |