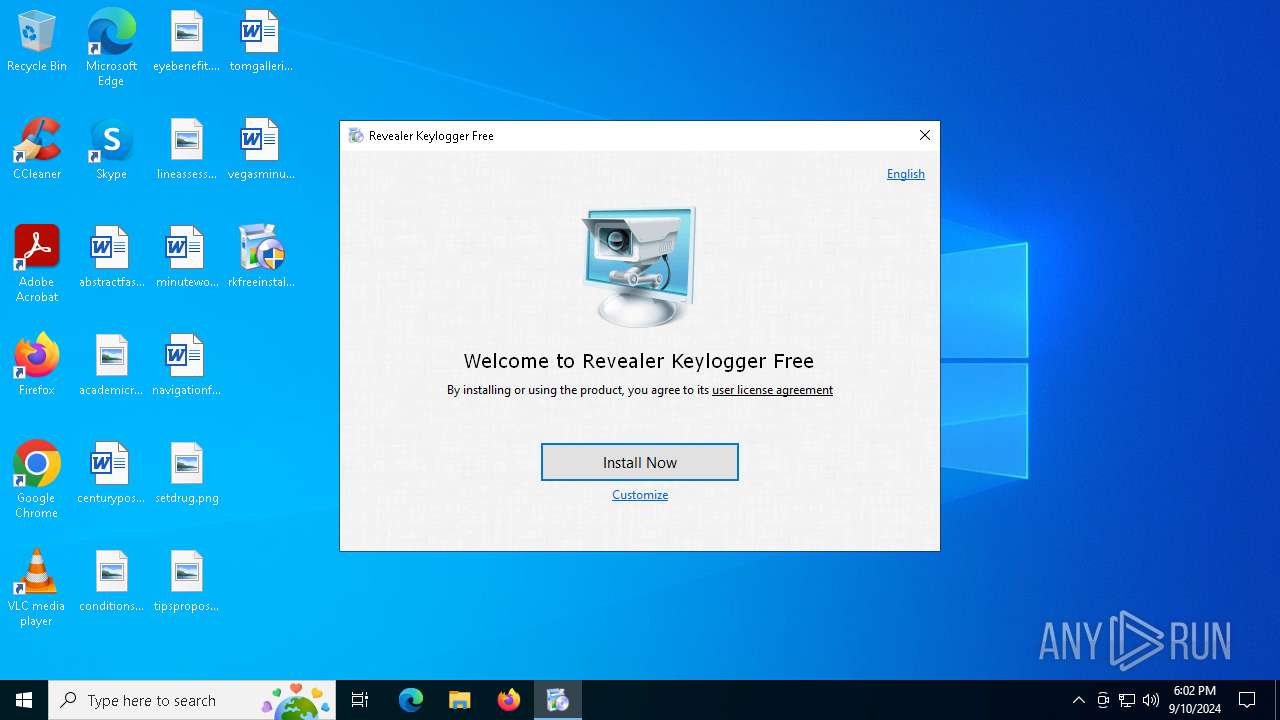
| File name: | rkfreeinstall302.exe |
| Full analysis: | https://app.any.run/tasks/3513110a-7666-4586-b928-a6b584590780 |
| Verdict: | Malicious activity |
| Analysis date: | September 10, 2024, 18:02:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6F12B81F9C8C1A63FD3D2DE19ABE0FAE |
| SHA1: | FDE4557585A33B9C31429B336203652F45A73D56 |
| SHA256: | 46DAA1444C0305EF1B691380AFD049B7E3868B46AEB9E74A5F7AC43D81B726B6 |
| SSDEEP: | 24576:DoDuHJIHmF+TMJfzsUJd7pyrd1R/90qwJfzsUxeOP:FAmsT0bJdEhVZYbxeOP |
MALICIOUS
Modifies exclusions in Windows Defender
- rkfree_setup64.exe (PID: 5184)
Create files in the Startup directory
- rvlkl.exe (PID: 3208)
SUSPICIOUS
Reads security settings of Internet Explorer
- rkfreeinstall302.exe (PID: 5276)
- rkfree_setup64.exe (PID: 5184)
- rvlkl.exe (PID: 3352)
Executable content was dropped or overwritten
- rkfreeinstall302.exe (PID: 5276)
- rkfree_setup64.exe (PID: 5184)
Detected use of alternative data streams (AltDS)
- rkfree_setup64.exe (PID: 5184)
Reads the date of Windows installation
- rkfree_setup64.exe (PID: 5184)
INFO
Reads the computer name
- rkfreeinstall302.exe (PID: 5276)
- rkfree_setup64.exe (PID: 5184)
- rvlkl.exe (PID: 3208)
- rvlkl.exe (PID: 3352)
Checks supported languages
- rkfreeinstall302.exe (PID: 5276)
- rkfree_setup64.exe (PID: 5184)
- rvlkl.exe (PID: 3208)
- rvlkl.exe (PID: 3352)
The process uses the downloaded file
- rkfreeinstall302.exe (PID: 5276)
- rkfree_setup64.exe (PID: 5184)
Create files in a temporary directory
- rkfreeinstall302.exe (PID: 5276)
Process checks computer location settings
- rkfreeinstall302.exe (PID: 5276)
- rkfree_setup64.exe (PID: 5184)
Creates files in the program directory
- rkfree_setup64.exe (PID: 5184)
- rvlkl.exe (PID: 3208)
- rvlkl.exe (PID: 3352)
Reads the machine GUID from the registry
- rkfree_setup64.exe (PID: 5184)
- rvlkl.exe (PID: 3208)
- rvlkl.exe (PID: 3352)
Manual execution by a user
- rvlkl.exe (PID: 2008)
- rvlkl.exe (PID: 3352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:20 09:51:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 90624 |
| InitializedDataSize: | 1738752 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xbcbc |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
133
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2008 | "C:\WINDOWS\system32\rvlkl.exe" | C:\Windows\System32\rvlkl.exe | — | explorer.exe | |||||||||||
User: admin Company: Logixoft Integrity Level: MEDIUM Description: Revealer Free Exit code: 3221226540 Version: 3.0.2.0 Modules
| |||||||||||||||
| 3208 | "C:\WINDOWS\system32\rvlkl.exe" -install -lang 9 | C:\Windows\System32\rvlkl.exe | rkfree_setup64.exe | ||||||||||||
User: admin Company: Logixoft Integrity Level: HIGH Description: Revealer Free Exit code: 0 Version: 3.0.2.0 Modules
| |||||||||||||||
| 3352 | "C:\WINDOWS\system32\rvlkl.exe" | C:\Windows\System32\rvlkl.exe | explorer.exe | ||||||||||||
User: admin Company: Logixoft Integrity Level: HIGH Description: Revealer Free Version: 3.0.2.0 Modules
| |||||||||||||||
| 3832 | "C:\WINDOWS\system32\rvlkl.exe" -install -lang 9 | C:\Windows\System32\rvlkl.exe | — | rkfree_setup64.exe | |||||||||||
User: admin Company: Logixoft Integrity Level: HIGH Description: Revealer Free Exit code: 3221226540 Version: 3.0.2.0 Modules
| |||||||||||||||
| 4880 | "C:\Users\admin\Desktop\rkfreeinstall302.exe" | C:\Users\admin\Desktop\rkfreeinstall302.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5184 | "C:\Users\admin\AppData\Local\Temp\rkfree_setup\rkfree_setup64.exe" | C:\Users\admin\AppData\Local\Temp\rkfree_setup\rkfree_setup64.exe | rkfreeinstall302.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 5276 | "C:\Users\admin\Desktop\rkfreeinstall302.exe" | C:\Users\admin\Desktop\rkfreeinstall302.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
910
Read events
906
Write events
2
Delete events
2
Modification events
| (PID) Process: | (5184) rkfree_setup64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | rvlkl |
Value: | |||
| (PID) Process: | (5184) rkfree_setup64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | rkfree |
Value: | |||
| (PID) Process: | (5184) rkfree_setup64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths |
| Operation: | write | Name: | C:\WINDOWS\system32\rvlkl.exe |
Value: 0 | |||
| (PID) Process: | (5184) rkfree_setup64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Exclusions\Processes |
| Operation: | write | Name: | C:\WINDOWS\system32\rvlkl.exe |
Value: 0 | |||
Executable files
3
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3208 | rvlkl.exe | C:\ProgramData\rvlkl\conf_ | binary | |
MD5:DDC8E01AA11B7F97A04EA9810ED351DF | SHA256:50E6A8AD6E9A10682402613C7D2E71D57540F69B2E17682F2CAE4309B6DC14CF | |||
| 3208 | rvlkl.exe | C:\ProgramData\rvlkl\conf | text | |
MD5:F029B85E498793E0CB73175040B0E24B | SHA256:438084D39D670AC7EC780D9DF98DC9CD57B3008A3923706A4BB7DFE91BB0E2BD | |||
| 3352 | rvlkl.exe | C:\ProgramData\rvlkl\conf_ | text | |
MD5:5A4E16DC903DE1A204597D3403C1A009 | SHA256:DB812EDA87DB5EEE5B843B85ADE588BCA66957AC1BEA6303CFBAA5DFCA6D07C9 | |||
| 5184 | rkfree_setup64.exe | C:\Windows\System32\rvlkl.exe | executable | |
MD5:B09C3B6B4EEA27786B99038235D4164F | SHA256:F92362CA925CC4B6CBC3BD9A236FDD66450A0AD08BE9C67106DE56E04E82670D | |||
| 3208 | rvlkl.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\rvlkl.lnk | binary | |
MD5:ECC4F2A8385FF26EE3CBE8F06D21A6FF | SHA256:6E32EFC744AF276343E380C05B7463A2573EB397A89CE5F0A6DA52B95FA5F9D3 | |||
| 5276 | rkfreeinstall302.exe | C:\Users\admin\AppData\Local\Temp\rkfree_setup\rkfree_setup64.exe | executable | |
MD5:2AE115D44F94104757F756289FB7E63A | SHA256:C64BFB0B57F9426E7CDB8EEB2517D48EDC7DAD89A67BBCA1DEB5E1883403B5C2 | |||
| 5184 | rkfree_setup64.exe | C:\ProgramData\rvlkl\log.css | text | |
MD5:A35BD6E012B609D94A076699C5372657 | SHA256:6EF8CFC8307115A02E5B60AF549867DC79BDF3018EB95A9417E8E6C3632EABB5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
18
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | 20.44.239.154:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
— | — | 20.44.239.154:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.106.86.13:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4324 | svchost.exe | 20.106.86.13:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6856 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |