| File name: | 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507 |
| Full analysis: | https://app.any.run/tasks/15586623-6e1a-4778-b02b-7beddfbcd6da |
| Verdict: | Malicious activity |
| Analysis date: | June 05, 2025, 14:30:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | F1959E3467C4BC406222EA22AA06C17B |
| SHA1: | 09DC8E395E12D8F5C71A0E8B768F82A7BB9D8AEA |
| SHA256: | 46B049715B7DF8C4B776ED2C57D1DEF183F4F2409168959E293FE6F3A8E8F507 |
| SSDEEP: | 49152:gng0HMXBqcJentBaRlVSvoPRZGJXvvJ/kZaMYwFhpdkOheYJc14OAmyNEQgIti3r:gnlSQtBmlVSvo5Zcv9aaMpjiA7VmyGtL |
MALICIOUS
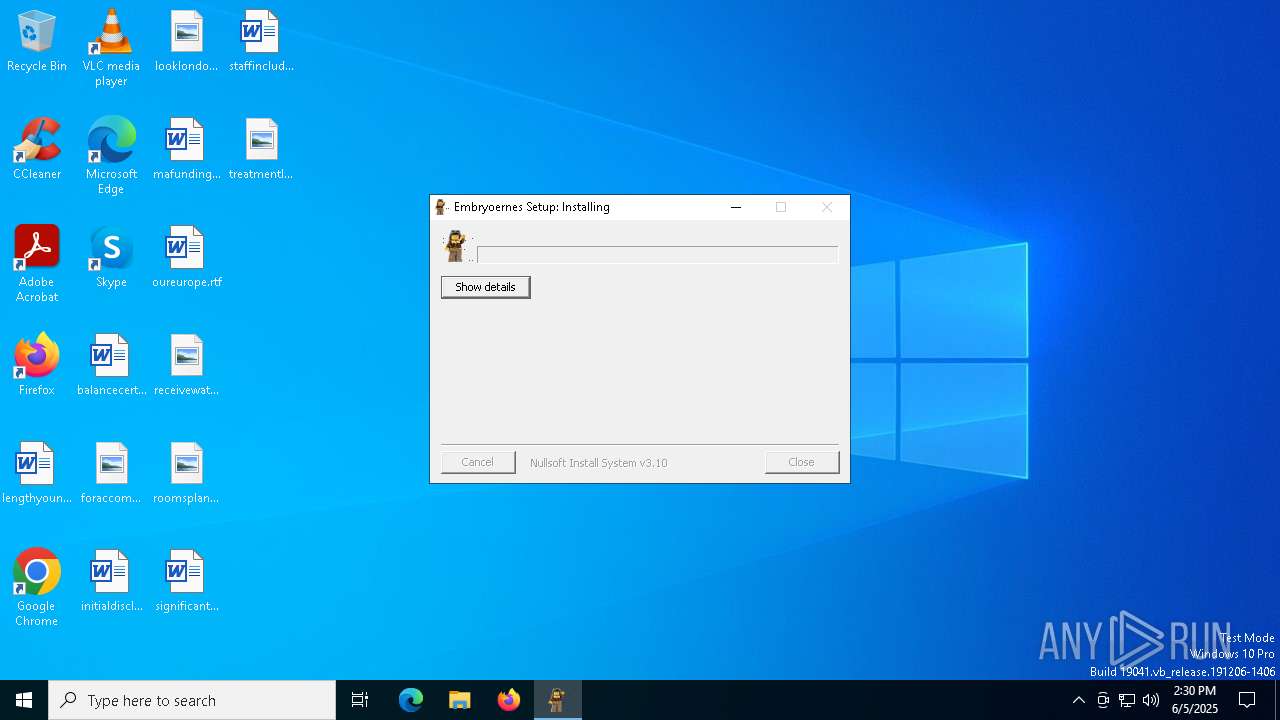
Executing a file with an untrusted certificate
- 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe (PID: 3268)
SUSPICIOUS
The process creates files with name similar to system file names
- 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe (PID: 6476)
Malware-specific behavior (creating "System.dll" in Temp)
- 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe (PID: 6476)
Application launched itself
- 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe (PID: 6476)
Executable content was dropped or overwritten
- 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe (PID: 6476)
Reads security settings of Internet Explorer
- 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe (PID: 3268)
There is functionality for taking screenshot (YARA)
- 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe (PID: 3268)
INFO
The sample compiled with english language support
- 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe (PID: 6476)
Create files in a temporary directory
- 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe (PID: 6476)
Checks supported languages
- 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe (PID: 3268)
Reads the computer name
- 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe (PID: 3268)
Checks proxy server information
- 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe (PID: 3268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:55:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 184832 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.0.0 |
| ProductVersionNumber: | 1.1.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | guldstolene universitylike snail |
| CompanyName: | uniques radbrkningerne |
| FileVersion: | 1.1.0.0 |
| OriginalFileName: | dreck.exe |
| ProductName: | disgregate breeches |
Total processes
129
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3140 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | "C:\Users\admin\AppData\Local\Temp\46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe" | C:\Users\admin\AppData\Local\Temp\46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | ||||||||||||
User: admin Company: uniques radbrkningerne Integrity Level: MEDIUM Version: 1.1.0.0 Modules
| |||||||||||||||
| 6476 | "C:\Users\admin\AppData\Local\Temp\46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe" | C:\Users\admin\AppData\Local\Temp\46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | explorer.exe | ||||||||||||
User: admin Company: uniques radbrkningerne Integrity Level: MEDIUM Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
Total events
872
Read events
646
Write events
226
Delete events
0
Modification events
| (PID) Process: | (6476) 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: u | |||
| (PID) Process: | (6476) 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: us | |||
| (PID) Process: | (6476) 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: use | |||
| (PID) Process: | (6476) 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user | |||
| (PID) Process: | (6476) 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user3 | |||
| (PID) Process: | (6476) 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32 | |||
| (PID) Process: | (6476) 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32: | |||
| (PID) Process: | (6476) 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32:: | |||
| (PID) Process: | (6476) 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32::S | |||
| (PID) Process: | (6476) 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Locales Approx |
| Operation: | write | Name: | C Langs |
Value: user32::Sh | |||
Executable files
1
Suspicious files
3
Text files
11
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6476 | 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | C:\Users\admin\AppData\Local\Temp\Ordbogsfunktions214\Speronaras\datakopien.suc | — | |
MD5:— | SHA256:— | |||
| 6476 | 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | C:\Users\admin\AppData\Local\Temp\Ordbogsfunktions214\Speronaras\luged.pol | — | |
MD5:— | SHA256:— | |||
| 6476 | 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | C:\Users\admin\AppData\Local\Temp\Ordbogsfunktions214\Speronaras\adjoinant.txt | text | |
MD5:193610FF34141180B6DFC3E02BBFBE1F | SHA256:CB25B91EAD3DAD5403254266386EB62E663763FBCB9972C562B4905EE98C57E2 | |||
| 6476 | 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | C:\Users\admin\AppData\Local\Temp\Ordbogsfunktions214\Speronaras\Buffaloing.ini | text | |
MD5:665503E33B0DDE7088BC3A822F82CFD5 | SHA256:57F079DA982132AF37350DE4AD8975AAE4FD8A7CBFB577718816C4782581A919 | |||
| 6476 | 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | C:\Users\admin\AppData\Local\Temp\Ordbogsfunktions214\tastearbejderne\solderiers.jpg | image | |
MD5:320E78214B4B59A0D455C40B716F0554 | SHA256:F7E53C36EF622BD335A53CBAAA63B7BE5F0BA5E2CF192F550188FE98528E303A | |||
| 6476 | 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | C:\Users\admin\AppData\Local\Temp\Ordbogsfunktions214\tastearbejderne\reperible.jpg | image | |
MD5:E2CFA80E57702BDCCFC11F0CF0E57B18 | SHA256:DDF2F5DD11ECDD8CC1BAF887418F23D762F469C85FB3920FF4D8C71E040CF55E | |||
| 6476 | 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | C:\Users\admin\AppData\Local\Temp\Ordbogsfunktions214\tastearbejderne\machinizing.ini | text | |
MD5:E80B5F48798DA2F63CC43CB9F3A9DE0D | SHA256:E63DC9B3D775D63DD796416013BEAF412BC1F464A54859D1C545FF4672906DDC | |||
| 6476 | 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | C:\Users\admin\AppData\Local\Temp\Ordbogsfunktions214\tastearbejderne\terrakottavase.txt | text | |
MD5:E9ABF84F9195D5746813BC70F3329D08 | SHA256:5F10CB37B246B4917338DEA907B9031FABC11051FB847493B53ACDD3502BD1DA | |||
| 6476 | 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | C:\Users\admin\AppData\Local\Temp\Ordbogsfunktions214\Aarpenges.Fla | binary | |
MD5:C2C5154250698508F89ED15D61859AE1 | SHA256:CD78E844688CDF27FD5B933DC79CF81E96EE7C84726EDA4D47EA2980F819A7B2 | |||
| 6476 | 46b049715b7df8c4b776ed2c57d1def183f4f2409168959e293fe6f3a8e8f507.exe | C:\Users\admin\AppData\Local\Temp\Ordbogsfunktions214\Speronaras\Sknhedsdronnings126.ser | binary | |
MD5:DA28BA9694B628DE74CA826A3F4119FD | SHA256:1C7921D39417DC664B7C0C02C7BF40B845A87863C79D3B28AE36C91096BDC6F1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.198.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.22.98.7:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6920 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6920 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.198.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7564 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
7564 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.22.98.7:80 | ocsp.digicert.com | AKAMAI-AS | GB | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |