| File name: | DroidJoy_Setup_x64_2.1.0.exe |
| Full analysis: | https://app.any.run/tasks/746e711d-0bc6-41e4-a669-b51fa6054b77 |
| Verdict: | Malicious activity |
| Analysis date: | October 12, 2024, 13:24:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 61D3FF519DBA0DE113B402DB36CE1F5F |
| SHA1: | 5F922D3BB53390D97A0BB181E06A84FD3F204CAB |
| SHA256: | 468D6A54941D876AABD8D842BA6B198C635FA7639B410D794128E24DEF5CAE2D |
| SSDEEP: | 98304:MtEeMwy51y+qJBUIwiYDo6J4XfsjXoYc45wRNw7U1/Z5fLZFms9xQ7AmdkaEHHb/:rbn6Tjp0A6RrS |
MALICIOUS
No malicious indicators.SUSPICIOUS
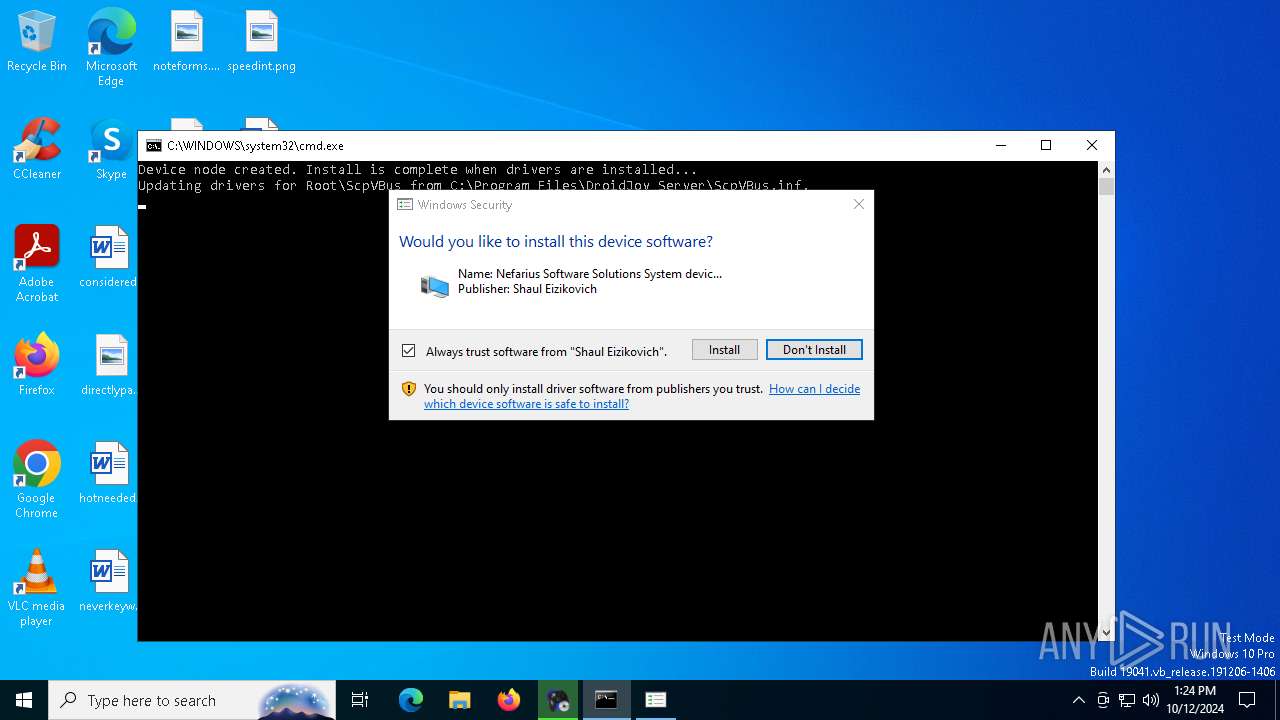
Executable content was dropped or overwritten
- DroidJoy_Setup_x64_2.1.0.exe (PID: 6728)
- DroidJoy_Setup_x64_2.1.0.exe (PID: 3644)
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 5036)
- devcon.exe (PID: 7108)
- drvinst.exe (PID: 4448)
- drvinst.exe (PID: 5064)
Reads security settings of Internet Explorer
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 6556)
Reads the Windows owner or organization settings
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 5036)
Process drops legitimate windows executable
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 5036)
- devcon.exe (PID: 7108)
- drvinst.exe (PID: 4448)
- drvinst.exe (PID: 5064)
The process drops C-runtime libraries
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 5036)
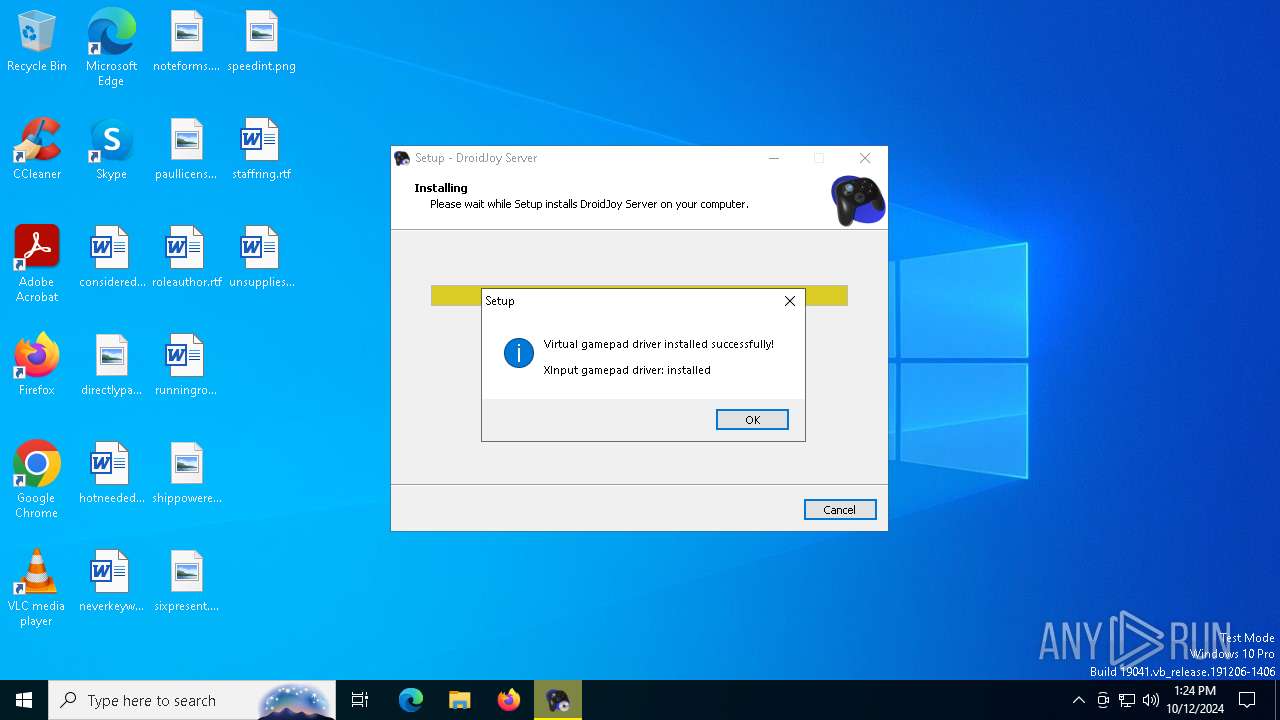
Drops a system driver (possible attempt to evade defenses)
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 5036)
- devcon.exe (PID: 7108)
- drvinst.exe (PID: 4448)
- drvinst.exe (PID: 5064)
Starts CMD.EXE for commands execution
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 5036)
INFO
Checks supported languages
- DroidJoy_Setup_x64_2.1.0.exe (PID: 6728)
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 6556)
- DroidJoy_Setup_x64_2.1.0.exe (PID: 3644)
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 5036)
Create files in a temporary directory
- DroidJoy_Setup_x64_2.1.0.exe (PID: 6728)
- DroidJoy_Setup_x64_2.1.0.exe (PID: 3644)
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 5036)
Reads the computer name
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 6556)
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 5036)
Process checks computer location settings
- DroidJoy_Setup_x64_2.1.0.tmp (PID: 6556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (74.3) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (9.6) |
| .scr | | | Windows screen saver (8.8) |
| .exe | | | Win32 Executable (generic) (3) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 40448 |
| InitializedDataSize: | 360448 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa5f8 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Florian Grill |
| FileDescription: | DroidJoy Server Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | DroidJoy Server |
| ProductVersion: | 2.1.0 |
Total processes
153
Monitored processes
17
Malicious processes
2
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | "cmd.exe" /C devcon.exe remove Root\ScpVBus | C:\Windows\System32\cmd.exe | — | DroidJoy_Setup_x64_2.1.0.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3644 | "C:\Users\admin\AppData\Local\Temp\DroidJoy_Setup_x64_2.1.0.exe" /SPAWNWND=$402EC /NOTIFYWND=$60078 | C:\Users\admin\AppData\Local\Temp\DroidJoy_Setup_x64_2.1.0.exe | DroidJoy_Setup_x64_2.1.0.tmp | ||||||||||||
User: admin Company: Florian Grill Integrity Level: HIGH Description: DroidJoy Server Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3964 | devcon.exe remove Root\ScpVBus | C:\Program Files\DroidJoy Server\devcon.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 10.0.10240.16399 (th1.150722-1625) Modules
| |||||||||||||||
| 4408 | "cmd.exe" /C devcon.exe install ScpVBus.inf Root\ScpVBus | C:\Windows\System32\cmd.exe | — | DroidJoy_Setup_x64_2.1.0.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4448 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{f3760f72-a76f-9b4a-bcd0-747ad8e89dfe}\scpvbus.inf" "9" "4b5cfab93" "0000000000000174" "WinSta0\Default" "00000000000001DC" "208" "c:\program files\droidjoy server" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4676 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5036 | "C:\Users\admin\AppData\Local\Temp\is-JQGRK.tmp\DroidJoy_Setup_x64_2.1.0.tmp" /SL5="$150208,5588858,401920,C:\Users\admin\AppData\Local\Temp\DroidJoy_Setup_x64_2.1.0.exe" /SPAWNWND=$402EC /NOTIFYWND=$60078 | C:\Users\admin\AppData\Local\Temp\is-JQGRK.tmp\DroidJoy_Setup_x64_2.1.0.tmp | DroidJoy_Setup_x64_2.1.0.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 5064 | DrvInst.exe "2" "211" "ROOT\SYSTEM\0001" "C:\WINDOWS\INF\oem1.inf" "oem1.inf:c14ce88487555a35:ScpVBus_Device:9.11.9.337:root\scpvbus," "4b5cfab93" "0000000000000174" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5980 | DrvInst.exe "1" "0" "USB\VID_045E&PID_028E\0000001" "" "" "4c8dd300b" "0000000000000000" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 413
Read events
16 336
Write events
58
Delete events
19
Modification events
| (PID) Process: | (5036) DroidJoy_Setup_x64_2.1.0.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | DroidJoyServer |
Value: "C:\Program Files\DroidJoy Server\DroidJoyServer.exe" | |||
| (PID) Process: | (7108) devcon.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
| (PID) Process: | (4448) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\TrustedPublisher\Certificates |
| Operation: | delete value | Name: | 6D5471DF6BBFAFA5D5900C88C08DF0E9C513690A |
Value: | |||
| (PID) Process: | (4448) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\TrustedPublisher\Certificates\6D5471DF6BBFAFA5D5900C88C08DF0E9C513690A |
| Operation: | write | Name: | Blob |
Value: 0300000001000000140000006D5471DF6BBFAFA5D5900C88C08DF0E9C513690A04000000010000001000000086411E51162C575E6B01F1AD328554D41400000001000000140000003F6C1520E941D7010624BECC9542D067C3E146F619000000010000001000000003EAC495545951172A0ED4D6B54E72530F0000000100000014000000A69435278FDBFA78B94B878F4BB2C03C1DECAB1220000000010000001F0500003082051B30820403A003020102021002CE5E9397278F47E86D94315363CC30300D06092A864886F70D01010505003073310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D313230300603550403132944696769436572742048696768204173737572616E636520436F6465205369676E696E672043412D31301E170D3135303430393030303030305A170D3137303431333132303030305A306D310B300906035504061302494C3111300F0603550408130854656C2041766976311530130603550407130C486F64204861536861726F6E31193017060355040A1310536861756C2045697A696B6F766963683119301706035504031310536861756C2045697A696B6F7669636830820122300D06092A864886F70D01010105000382010F003082010A0282010100A222A2B05738F997EE3DB86DDB6B75AB997FEB85DC596D81530928D652CB849334C2AC86AAF7ABFC19A8A82A17ADF35D30CDF92F4636DF8212C78B571547DF8B7B92937AEF1EC1CC2CE96E2E503E0772BB5AF2BCDE50369706E9A2133FE815FF2E43388C8B566C5CD27F7B0A6360B3C32108A6E1E3F89E2C743E96CD5C5F90185D31FF19FB7CC39AC0B22054A32AA6560CF883EEF9D643C02BA8C15429A9D2A95D7D047EF9972ECE8026FC95D638293E1620DB6ED7551C250D15A3BDDDC3BDC41AB9112D4672DDAD31010690F3FE9C15F672C366D910FD4FD3FEA28CB3FA35261918DD13BB8B47187A16BBF952A7164EDECF7B7C4F5AF57A07B0838D9B2A29630203010001A38201AF308201AB301F0603551D23041830168014974803EB15086BB9B25823CC942EF1C665D2648E301D0603551D0E041604143F6C1520E941D7010624BECC9542D067C3E146F6300E0603551D0F0101FF04040302078030130603551D25040C300A06082B0601050507030330690603551D1F04623060302EA02CA02A8628687474703A2F2F63726C332E64696769636572742E636F6D2F68612D63732D32303131612E63726C302EA02CA02A8628687474703A2F2F63726C342E64696769636572742E636F6D2F68612D63732D32303131612E63726C30420603551D20043B3039303706096086480186FD6C0301302A302806082B06010505070201161C68747470733A2F2F7777772E64696769636572742E636F6D2F43505330818606082B06010505070101047A3078302406082B060105050730018618687474703A2F2F6F6373702E64696769636572742E636F6D305006082B060105050730028644687474703A2F2F636163657274732E64696769636572742E636F6D2F4469676943657274486967684173737572616E6365436F64655369676E696E6743412D312E637274300C0603551D130101FF04023000300D06092A864886F70D010105050003820101009D0681BEE5C594F86777FD380CCCFF28DE91A236829B6F6F4FE873E1532F3DD802B47C4ABD1BD16D4C36E97BCF8F8B9AE6F52AD2AF8B2FC48659C29662ECDA141AA251E486D146B8BD718C62E481BBDBD1FCB914B80A0FB254F29E9C425DD8044A4938896D56C0993D8C15971951C6F5B5007BA5F14D5618E3BDB6DDB0DDFF23D1B478F30E73D62A8216674EE30F5E09940CAEB4B06B5CA272B709043DCCC456EA1BB3D7D342DF5FFA0B75B1D7DEB1543A86B37C5025618600DAF0D411C8C179D121B3AE4443A914B8B80FBA0F00DAAE85AF46B22A8847E3CF5E88894260A95D1D33607377CFE6ABB8205A97AD235659D15C9DECAD77418FA3591218840A6055 | |||
| (PID) Process: | (5064) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\ScpVBus |
| Operation: | write | Name: | Owners |
Value: oem1.inf | |||
| (PID) Process: | (5064) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\ScpVBus\Parameters\Wdf |
| Operation: | write | Name: | KmdfLibraryVersion |
Value: 1.9 | |||
| (PID) Process: | (5064) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\PnpLockdownFiles\%SystemRoot%/System32/drivers/ScpVBus.sys |
| Operation: | write | Name: | Owners |
Value: oem1.inf | |||
| (PID) Process: | (5064) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\PnpLockdownFiles\%SystemRoot%/System32/WdfCoInstaller01009.dll |
| Operation: | write | Name: | Owners |
Value: oem1.inf | |||
| (PID) Process: | (5064) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\DriverDatabase\DriverPackages\scpvbus.inf_amd64_0753931c84d85377\Descriptors\Root\ScpVBus |
| Operation: | write | Name: | Configuration |
Value: ScpVBus_Device.NT | |||
| (PID) Process: | (5064) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\DriverDatabase\DriverPackages\scpvbus.inf_amd64_0753931c84d85377\Descriptors\Root\ScpVBus |
| Operation: | write | Name: | Manufacturer |
Value: %manufacturername% | |||
Executable files
70
Suspicious files
23
Text files
11
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3644 | DroidJoy_Setup_x64_2.1.0.exe | C:\Users\admin\AppData\Local\Temp\is-JQGRK.tmp\DroidJoy_Setup_x64_2.1.0.tmp | executable | |
MD5:062054A501F35E28DE02DCE408074414 | SHA256:53BF279912E85DAC5B45C120BA8AB78D36E606C1EFBF610C8ABA0B5A1EE3C587 | |||
| 6728 | DroidJoy_Setup_x64_2.1.0.exe | C:\Users\admin\AppData\Local\Temp\is-L3V3P.tmp\DroidJoy_Setup_x64_2.1.0.tmp | executable | |
MD5:062054A501F35E28DE02DCE408074414 | SHA256:53BF279912E85DAC5B45C120BA8AB78D36E606C1EFBF610C8ABA0B5A1EE3C587 | |||
| 5036 | DroidJoy_Setup_x64_2.1.0.tmp | C:\Program Files\DroidJoy Server\GalaSoft.MvvmLight.Extras.dll | executable | |
MD5:43312122AF66A3E99CF2F9C597012C22 | SHA256:8E248E95E6DC65317AF9CAAF6A43091D5CB75FD1302BAE0A49DEA821FA21DC8E | |||
| 5036 | DroidJoy_Setup_x64_2.1.0.tmp | C:\Program Files\DroidJoy Server\is-VLD65.tmp | text | |
MD5:AE917FCC79E98DAA70D4D75ED11F57B7 | SHA256:0D0E6592F4A9F5FC804A14E4B3EDBD4497E3475A941D632ACE36CB00F431F76F | |||
| 5036 | DroidJoy_Setup_x64_2.1.0.tmp | C:\Program Files\DroidJoy Server\eula.txt | text | |
MD5:AE917FCC79E98DAA70D4D75ED11F57B7 | SHA256:0D0E6592F4A9F5FC804A14E4B3EDBD4497E3475A941D632ACE36CB00F431F76F | |||
| 5036 | DroidJoy_Setup_x64_2.1.0.tmp | C:\Program Files\DroidJoy Server\DroidJoyServer.exe.config | xml | |
MD5:B708059B94EE4BBFD81151459A5E54F5 | SHA256:B73BFBD62F900EEF76EE36B0F078D4438AFFE3C3DB193A8F37B112C9B58519F5 | |||
| 5036 | DroidJoy_Setup_x64_2.1.0.tmp | C:\Program Files\DroidJoy Server\GalaSoft.MvvmLight.dll | executable | |
MD5:B349A5C9165CBB8663F82C31F9402D35 | SHA256:60FFBD8A891ACBE1ADBE79D320806A32AE826575F5218A51379FFC83F03F62A7 | |||
| 5036 | DroidJoy_Setup_x64_2.1.0.tmp | C:\Program Files\DroidJoy Server\unins000.exe | executable | |
MD5:81599E87ECB3FD8C8D72F639FD1FEC0B | SHA256:DB761BFDF45D1A18225D310463D12910996ACCED249CB3E5548E7813BFDB1E49 | |||
| 5036 | DroidJoy_Setup_x64_2.1.0.tmp | C:\Program Files\DroidJoy Server\is-6O2RE.tmp | executable | |
MD5:6F8D41BE2AB322E1F13F4D5DC2207E0C | SHA256:5D91629E82F4F0EEE5832F0A21CF46B4F29ECA5BFFAD29268E8209E917AF4D07 | |||
| 5036 | DroidJoy_Setup_x64_2.1.0.tmp | C:\Program Files\DroidJoy Server\DroidJoyServer.exe | executable | |
MD5:030C59574D527570E3C94314F4CF00FC | SHA256:AFEB49CF7D22CC63090B7E18AD0832C2B050D1936E53FDC5601C1F9BE77BD729 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
60
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7028 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6992 | DroidJoyServer.exe | GET | 200 | 23.192.154.58:80 | http://ocsp.entrust.net/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQYZiPAAGkmN%2BgbjpL0XWVofDLNAQUKgpvMiwpICF2arGsjDyvk44Oa6ICEEpjPndabzP8AAAAAFVlfGA%3D | unknown | — | — | whitelisted |
2980 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6992 | DroidJoyServer.exe | GET | 200 | 23.192.154.58:80 | http://ocsp.entrust.net/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCDQCHglJgAAAAAFHTc9k%3D | unknown | — | — | whitelisted |
6736 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6736 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1764 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 104.126.37.160:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7028 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7028 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4360 | SearchApp.exe | 104.126.37.154:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
DroidJoyServer.exe | 32feet.NET: 'InTheHand.Net.Personal, Version=3.5.605.0, Culture=neutral, PublicKeyToken=ea38caa273134499'
versions: '3.5.605.0' and '3.5.0605.0'.
|
DroidJoyServer.exe | IBtIf using WidcommStBtIf.
|
DroidJoyServer.exe | Dependency DLL '32feetWidcomm' status: NotFound.
|
DroidJoyServer.exe | System.PlatformNotSupportedException: Microsoft Bluetooth stack not supported (radio).
|
DroidJoyServer.exe | System.Reflection.TargetInvocationException: Dependency DLL '32feetWidcomm' status: NotFound. ---> System.PlatformNotSupportedException: Dependency DLL '32feetWidcomm' status: NotFound. ---> System.DllNotFoundException: Unable to load DLL '32feetWidcomm': The specified module could not be found. (Exception from HRESULT: 0x8007007E)
|
DroidJoyServer.exe | System.DllNotFoundException: Unable to load DLL 'BsSDK': The specified module could not be found. (Exception from HRESULT: 0x8007007E)
|
DroidJoyServer.exe | 32feet.NET: 'InTheHand.Net.Personal, Version=3.5.605.0, Culture=neutral, PublicKeyToken=ea38caa273134499'
versions: '3.5.605.0' and '3.5.0605.0'.
|
DroidJoyServer.exe | IBtIf using WidcommStBtIf.
|
DroidJoyServer.exe | Dependency DLL '32feetWidcomm' status: NotFound.
|
DroidJoyServer.exe | System.PlatformNotSupportedException: Microsoft Bluetooth stack not supported (radio).
|