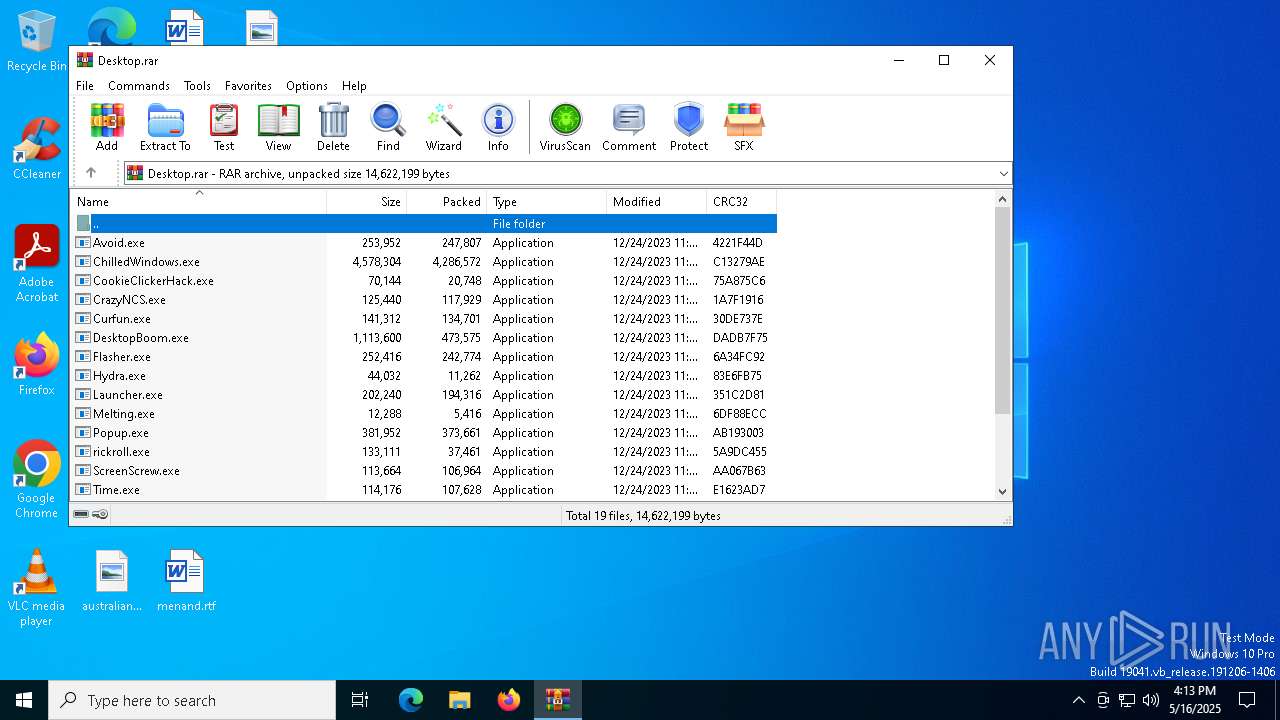
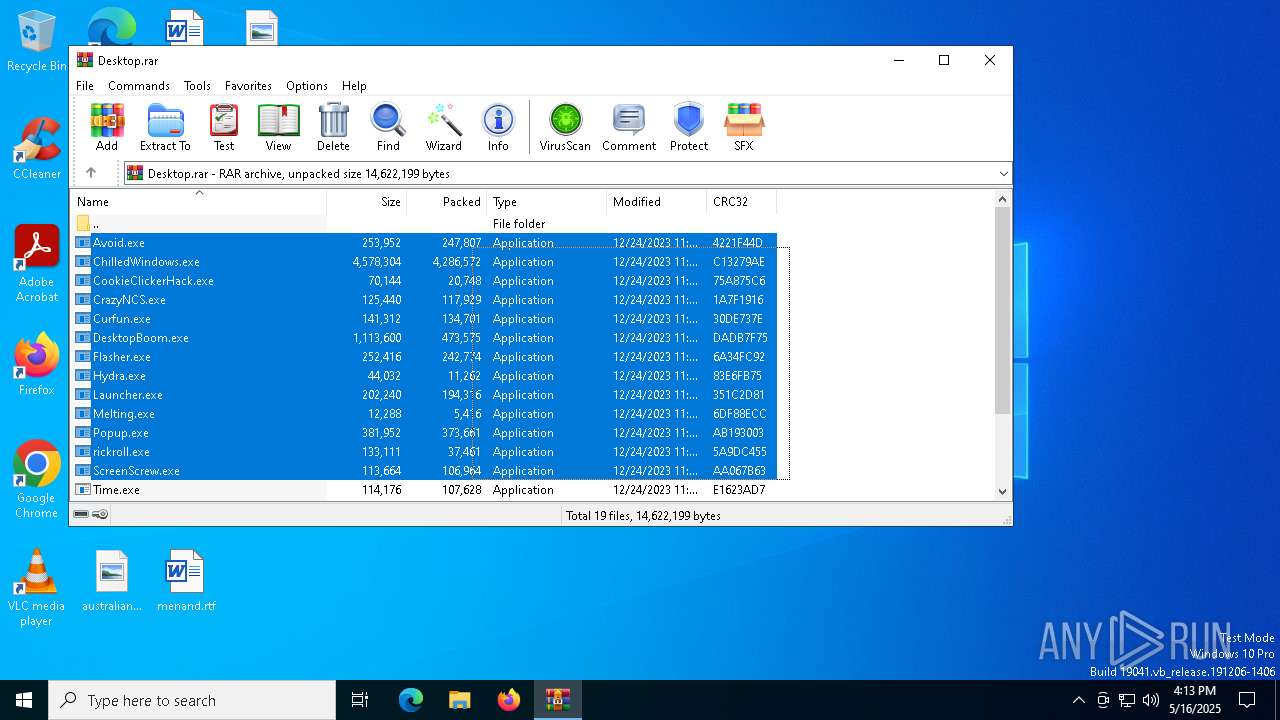
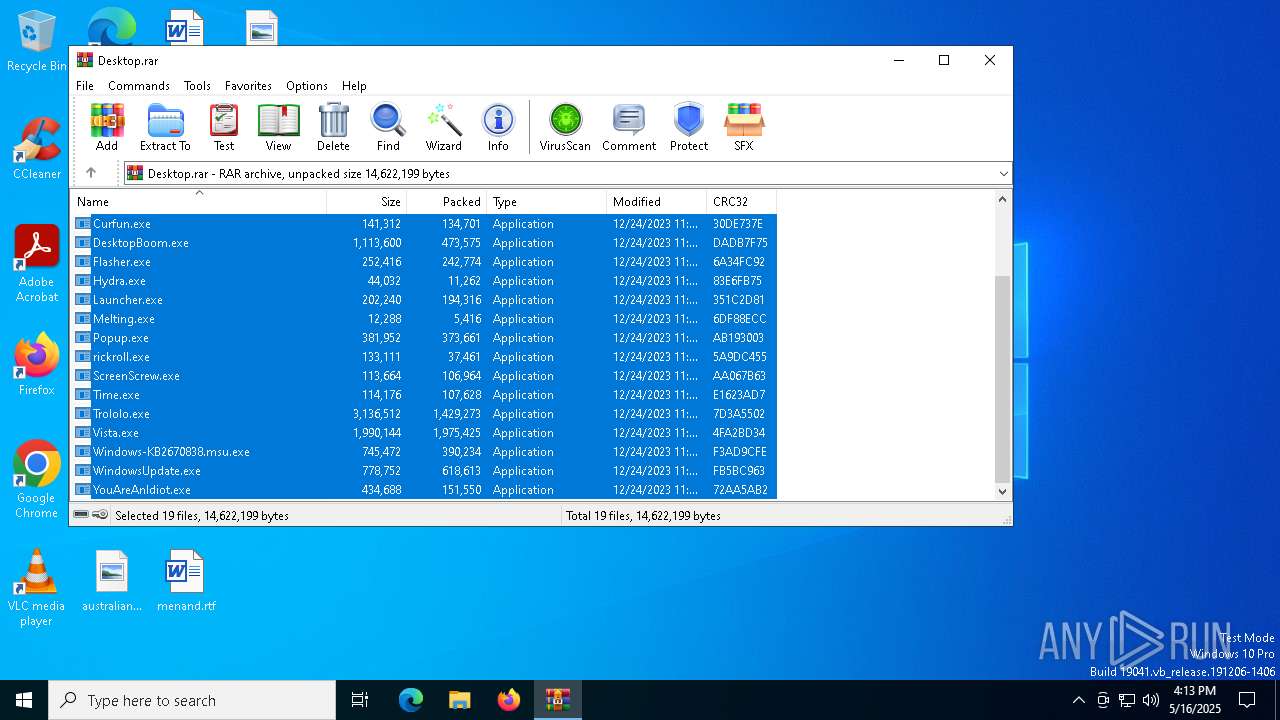
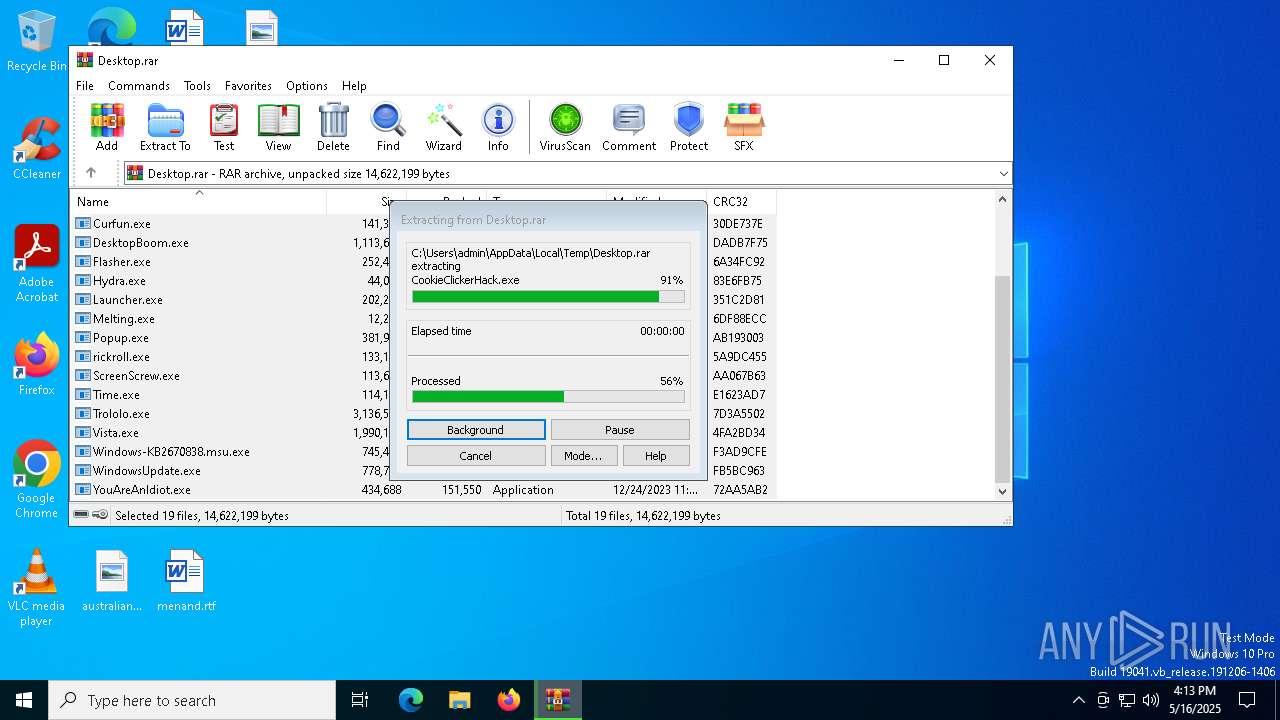
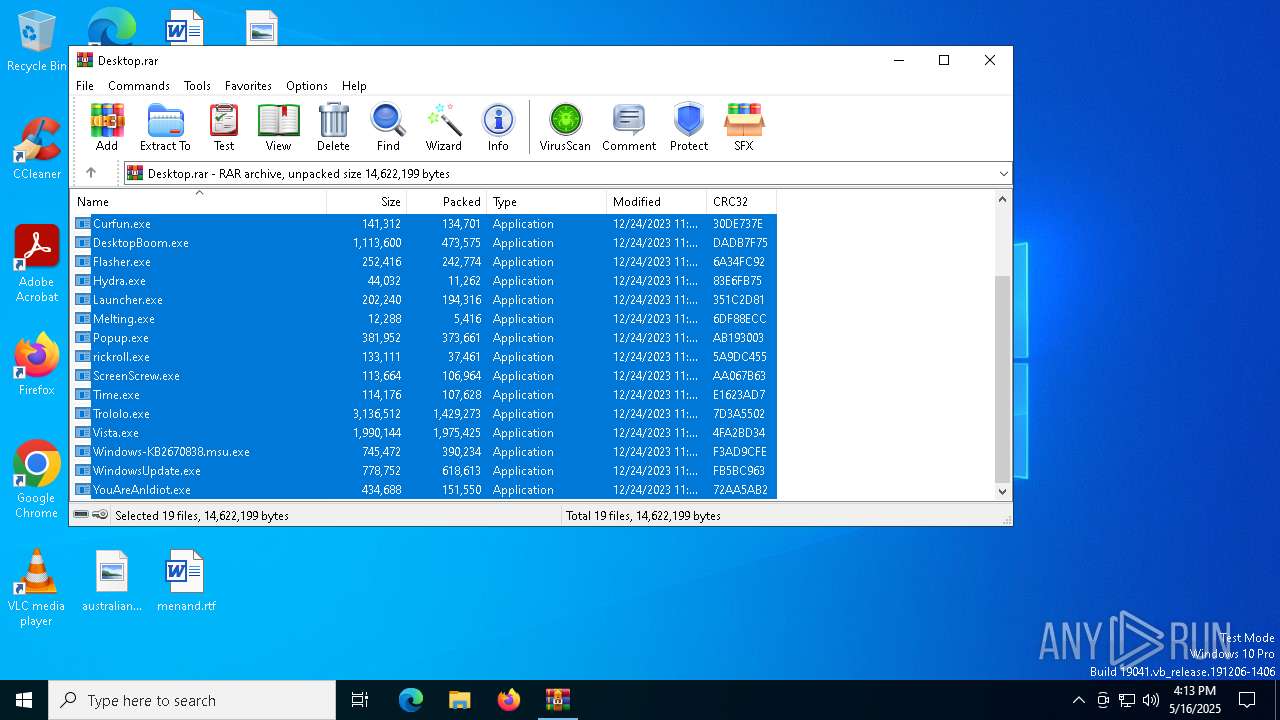
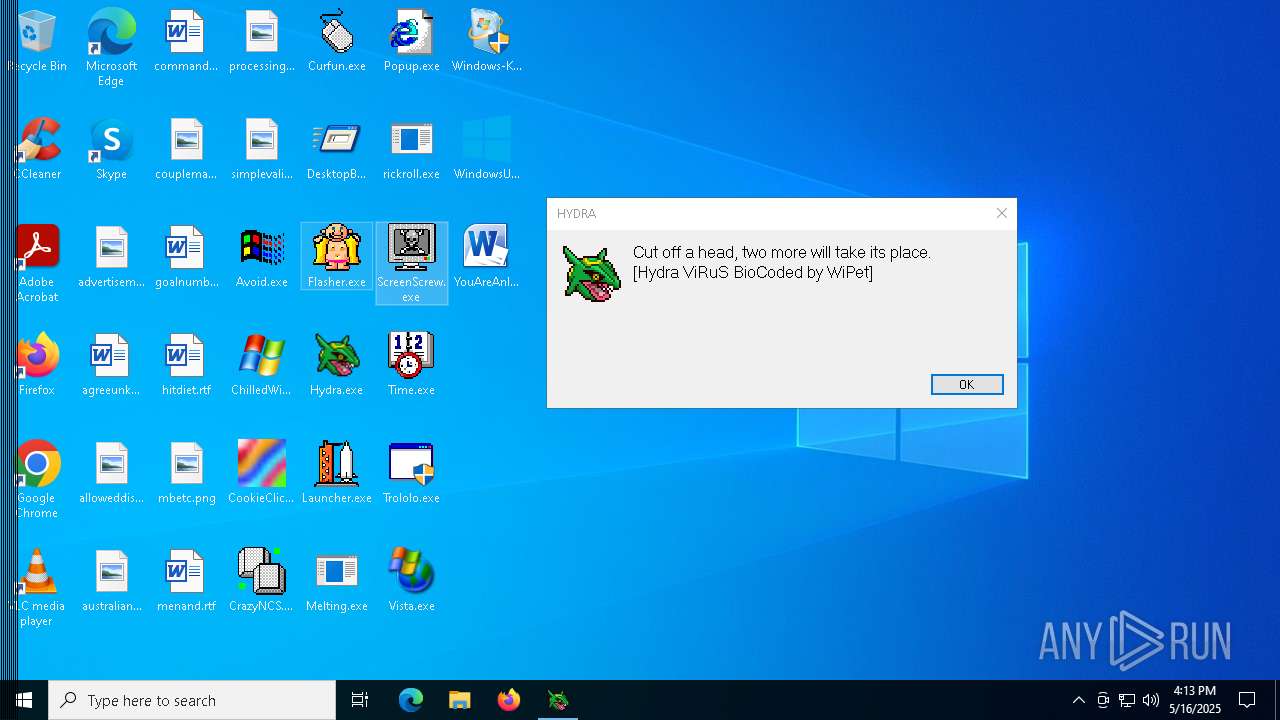
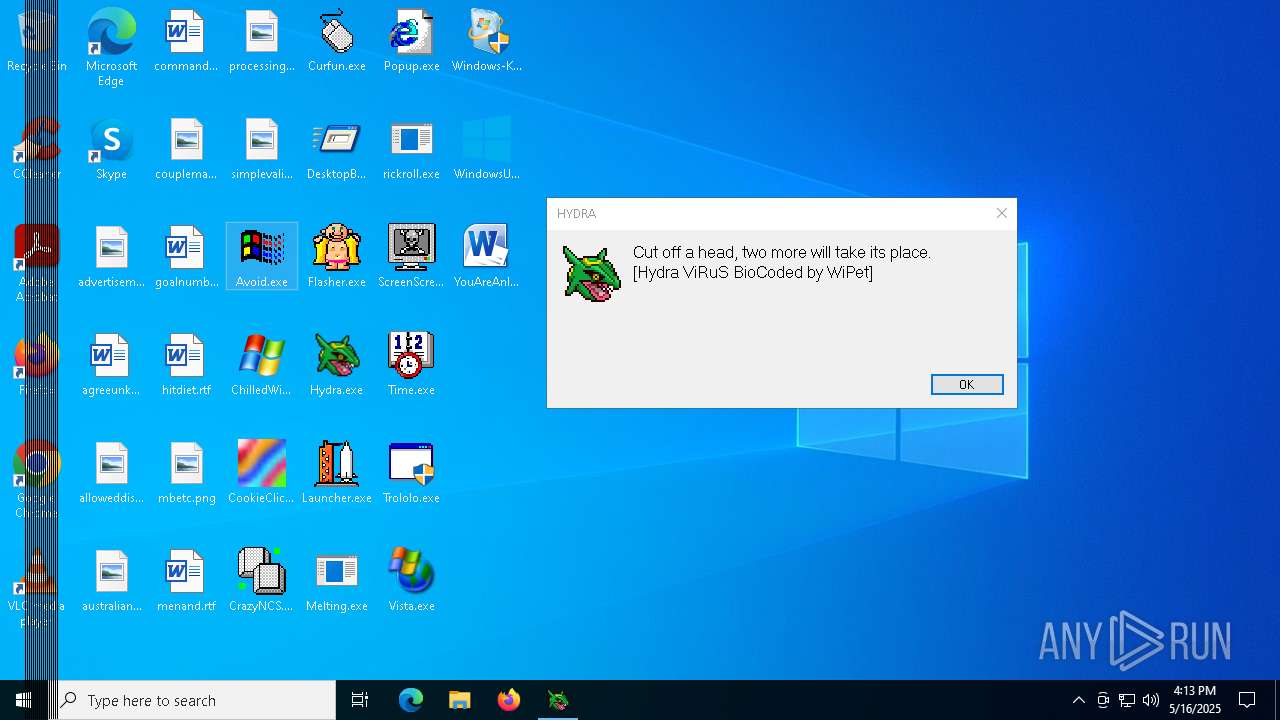
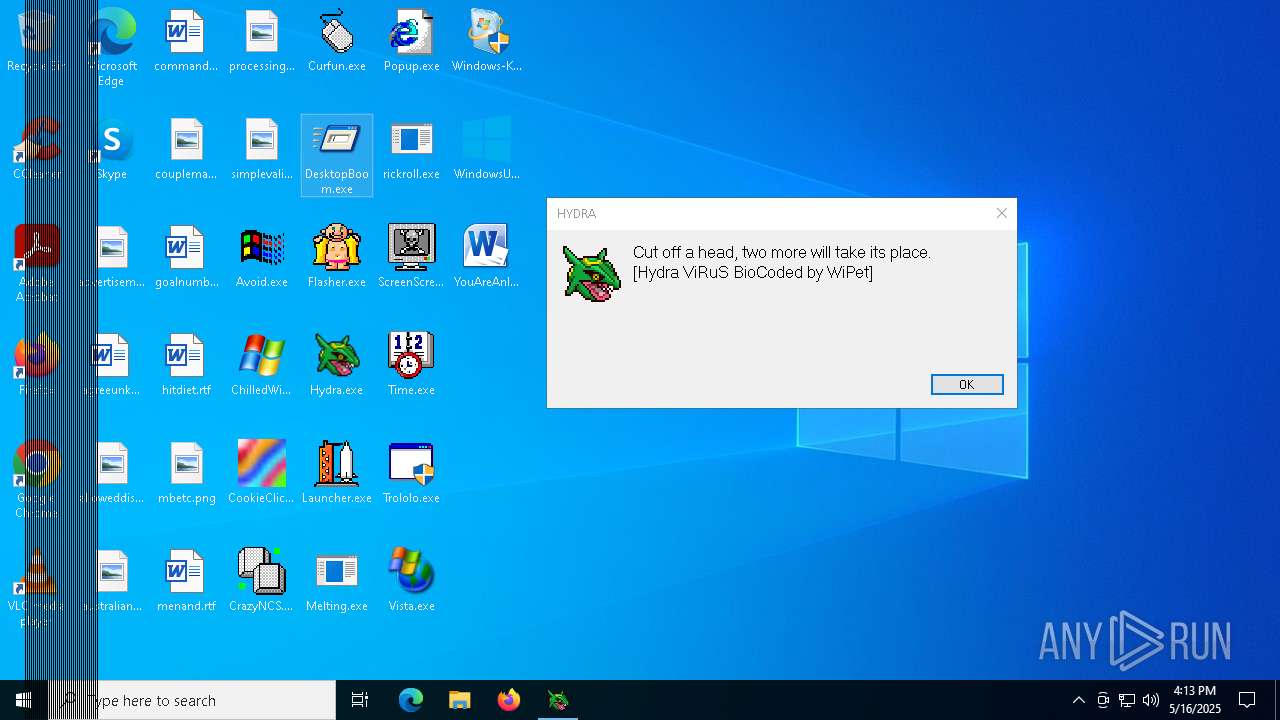
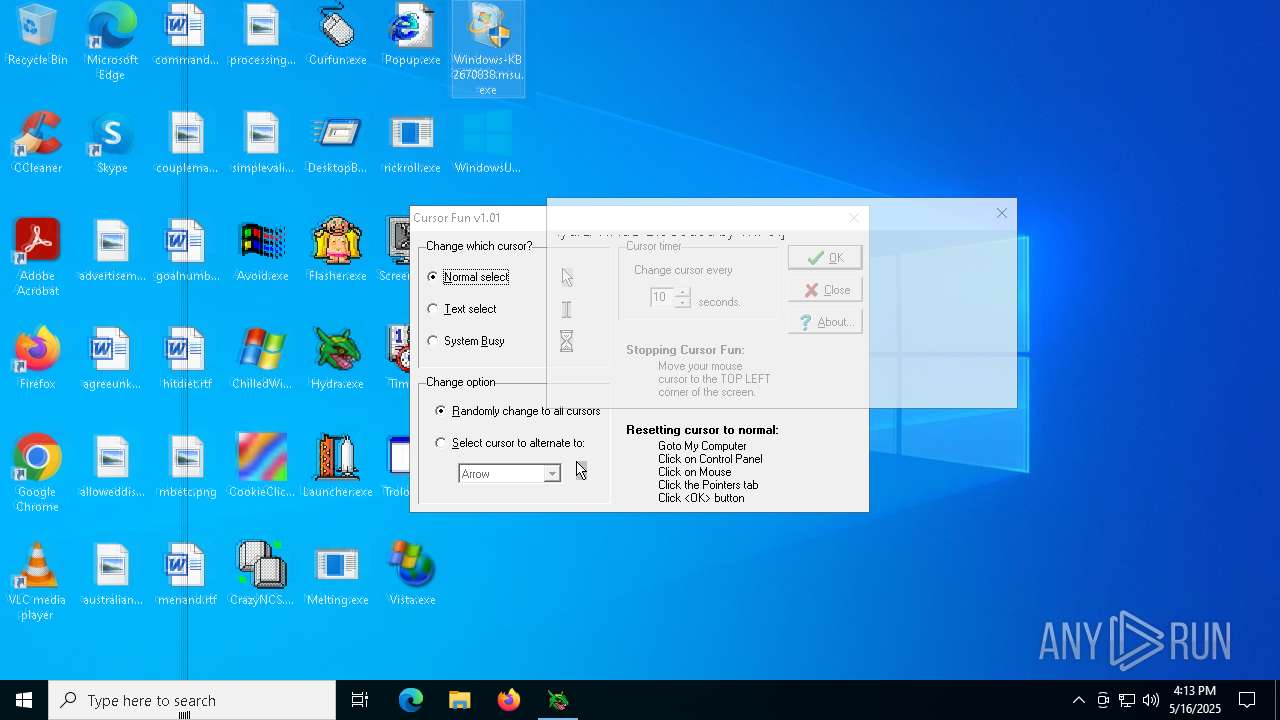
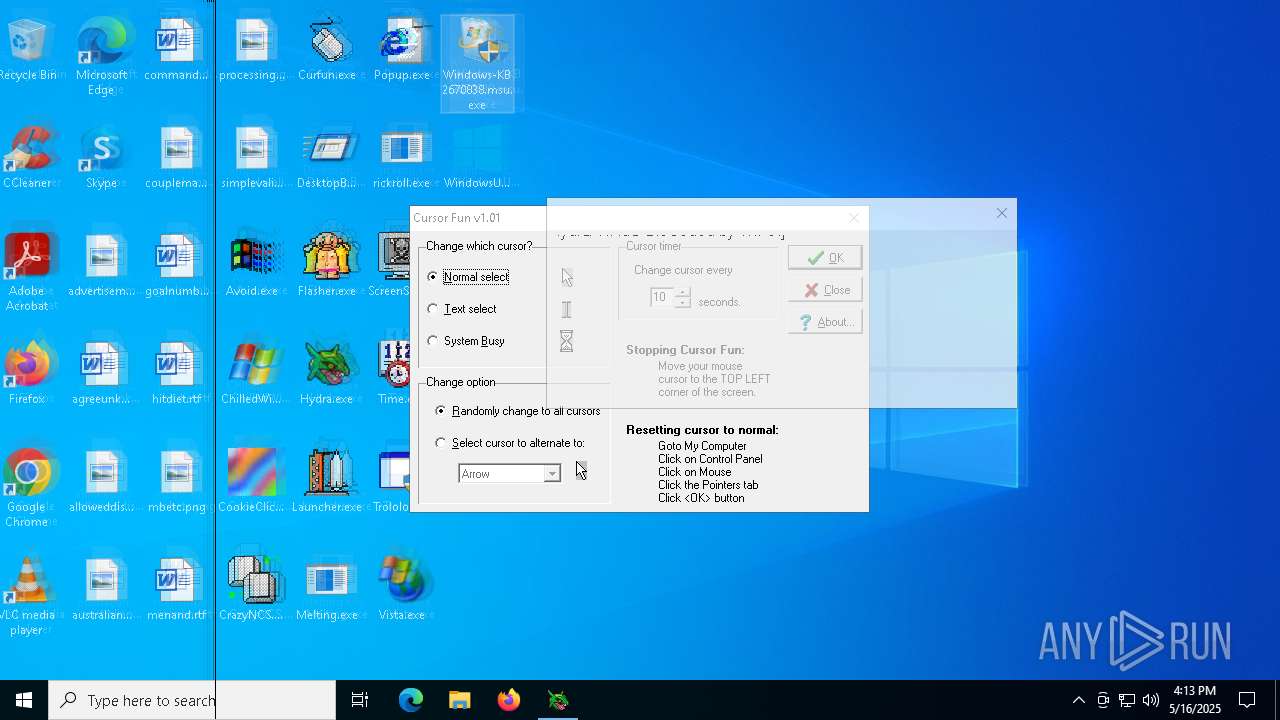
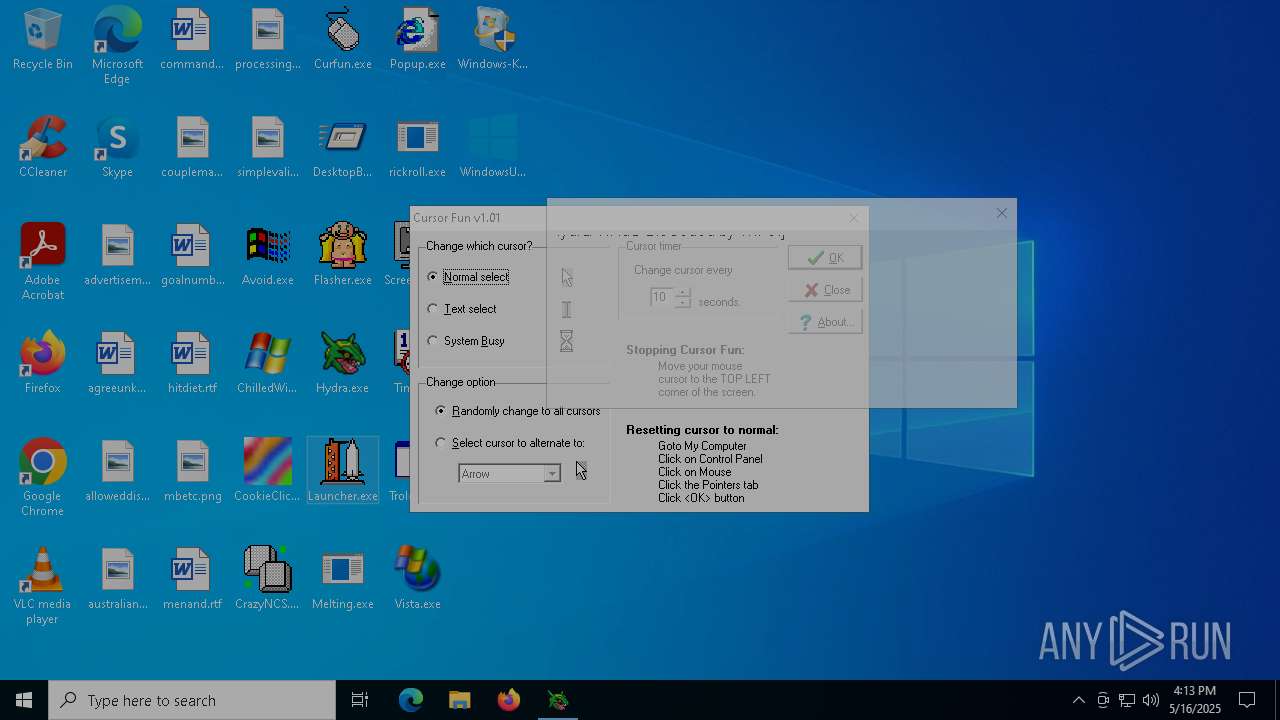
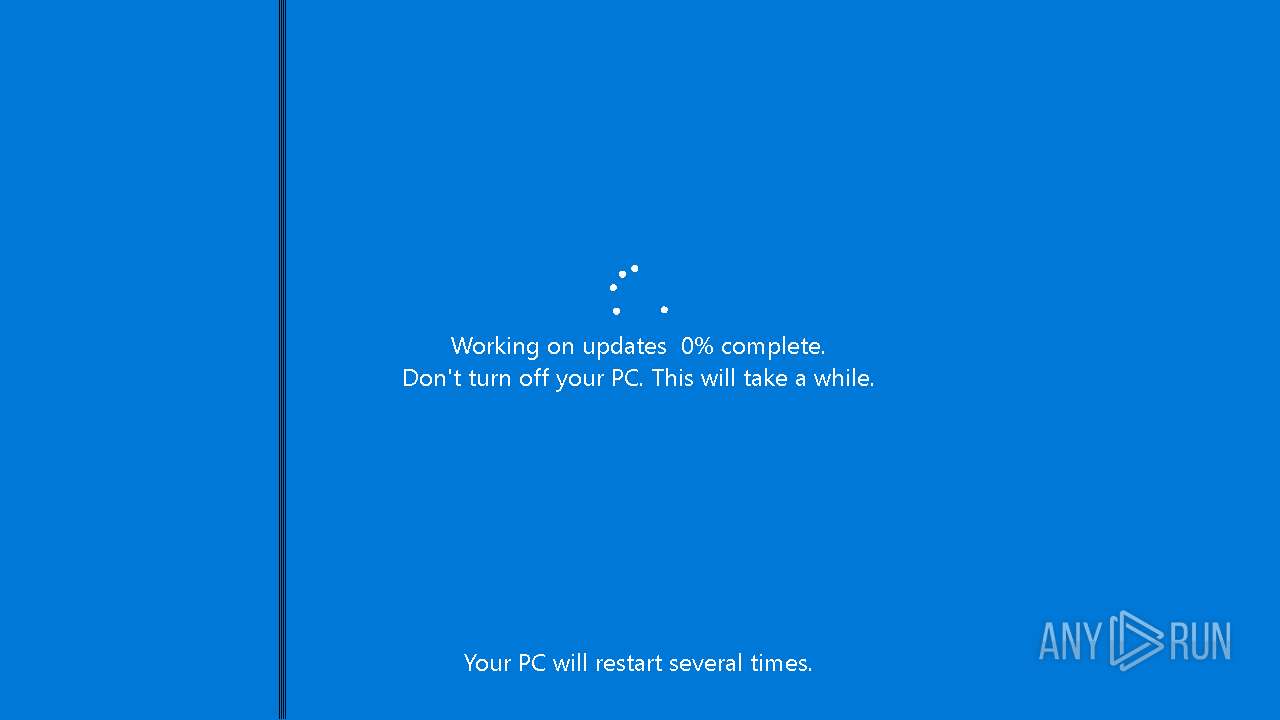
| File name: | Desktop.rar |
| Full analysis: | https://app.any.run/tasks/379de6e3-a867-4112-b6ae-890973070849 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 16:13:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 63164CC07D602BB8E8D77FBBED09F25D |
| SHA1: | EC577F5990E8D2EEE43AC6CAD2773CED043C2181 |
| SHA256: | 467CE8FBC13403703069B6D4EDDF940F12532E79E824C95C78CA33EE6820FBFD |
| SSDEEP: | 98304:9LYdDw5fU6Vh7vEmhqAdAt6+26hFmTztG4E+1e9xuMWudny3MzMnbK40r/9nqjVz:x7fgURW8KGZsueu6dBa |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6760)
GENERIC has been found (auto)
- WinRAR.exe (PID: 6760)
DESKTOPBOOM has been detected
- WinRAR.exe (PID: 6760)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6760)
Starts a Microsoft application from unusual location
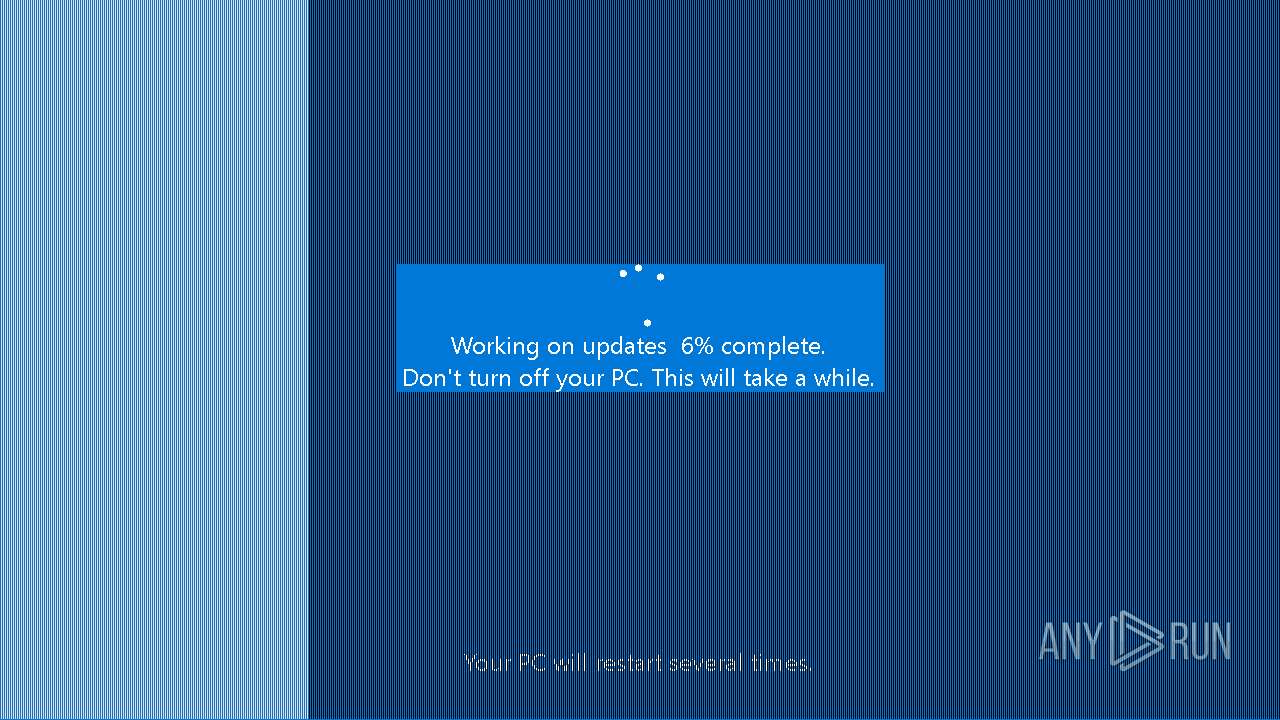
- Hydra.exe (PID: 904)
- Windows-KB2670838.msu.exe (PID: 6512)
- Windows-KB2670838.msu.exe (PID: 5260)
Executes application which crashes
- YouAreAnIdiot.exe (PID: 1660)
There is functionality for taking screenshot (YARA)
- ScreenScrew.exe (PID: 2236)
- Time.exe (PID: 6184)
- Flasher.exe (PID: 3180)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6760)
The sample compiled with english language support
- WinRAR.exe (PID: 6760)
Manual execution by a user
- Hydra.exe (PID: 904)
- Time.exe (PID: 6184)
- YouAreAnIdiot.exe (PID: 1660)
- ScreenScrew.exe (PID: 2236)
- Flasher.exe (PID: 3180)
- Windows-KB2670838.msu.exe (PID: 5260)
- Windows-KB2670838.msu.exe (PID: 6512)
- DesktopBoom.exe (PID: 1088)
- rickroll.exe (PID: 4152)
- Curfun.exe (PID: 3020)
Checks supported languages
- Hydra.exe (PID: 904)
- Time.exe (PID: 6184)
- YouAreAnIdiot.exe (PID: 1660)
- ScreenScrew.exe (PID: 2236)
- Flasher.exe (PID: 3180)
- DesktopBoom.exe (PID: 1088)
- Curfun.exe (PID: 3020)
- Windows-KB2670838.msu.exe (PID: 5260)
- rickroll.exe (PID: 4152)
Reads the computer name
- Hydra.exe (PID: 904)
- YouAreAnIdiot.exe (PID: 1660)
- Windows-KB2670838.msu.exe (PID: 5260)
- Curfun.exe (PID: 3020)
Reads the machine GUID from the registry
- Hydra.exe (PID: 904)
- YouAreAnIdiot.exe (PID: 1660)
- Windows-KB2670838.msu.exe (PID: 5260)
Creates files or folders in the user directory
- WerFault.exe (PID: 2432)
Compiled with Borland Delphi (YARA)
- Time.exe (PID: 6184)
- ScreenScrew.exe (PID: 2236)
- Flasher.exe (PID: 3180)
Aspack has been detected
- ScreenScrew.exe (PID: 2236)
- Flasher.exe (PID: 3180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 247807 |
| UncompressedSize: | 253952 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Avoid.exe |
Total processes
134
Monitored processes
14
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 904 | "C:\Users\admin\Desktop\Hydra.exe" | C:\Users\admin\Desktop\Hydra.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Hydra Version: 1.0.0.0 Modules
| |||||||||||||||
| 1088 | "C:\Users\admin\Desktop\DesktopBoom.exe" | C:\Users\admin\Desktop\DesktopBoom.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: DesktopBoom - by Nay1l Version: 1.0.0.0 Modules
| |||||||||||||||
| 1660 | "C:\Users\admin\Desktop\YouAreAnIdiot.exe" | C:\Users\admin\Desktop\YouAreAnIdiot.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: Microsoft Word 2010 Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2236 | "C:\Users\admin\Desktop\ScreenScrew.exe" | C:\Users\admin\Desktop\ScreenScrew.exe | — | explorer.exe | |||||||||||
User: admin Company: RJL Software, Inc. Integrity Level: MEDIUM Description: Screws with your screen :) Version: 1.0.0.0 Modules
| |||||||||||||||
| 2432 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1660 -s 1200 | C:\Windows\SysWOW64\WerFault.exe | — | YouAreAnIdiot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3020 | "C:\Users\admin\Desktop\Curfun.exe" | C:\Users\admin\Desktop\Curfun.exe | — | explorer.exe | |||||||||||
User: admin Company: RJL Software Integrity Level: MEDIUM Description: Randomly changes cursor Version: 1.0.1.0 Modules
| |||||||||||||||
| 3180 | "C:\Users\admin\Desktop\Flasher.exe" | C:\Users\admin\Desktop\Flasher.exe | — | explorer.exe | |||||||||||
User: admin Company: RJL Software, Inc. Integrity Level: MEDIUM Description: Flashes any image to the screen quickly. Version: 1.0.0.0 Modules
| |||||||||||||||
| 4152 | "C:\Users\admin\Desktop\rickroll.exe" | C:\Users\admin\Desktop\rickroll.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5260 | "C:\Users\admin\Desktop\Windows-KB2670838.msu.exe" | C:\Users\admin\Desktop\Windows-KB2670838.msu.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WindowsUpdate Version: 1.0.0.0 Modules
| |||||||||||||||
| 6184 | "C:\Users\admin\Desktop\Time.exe" | C:\Users\admin\Desktop\Time.exe | — | explorer.exe | |||||||||||
User: admin Company: RJL Software, Inc. Integrity Level: MEDIUM Description: Randomly changes the time Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
3 882
Read events
3 864
Write events
18
Delete events
0
Modification events
| (PID) Process: | (6760) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6760) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6760) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6760) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Desktop.rar | |||
| (PID) Process: | (6760) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6760) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6760) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6760) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6760) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6760) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
19
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6760 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6760.31773\Avoid.exe | executable | |
MD5:20D2C71D6D9DAF4499FFC4A5D164F1C3 | SHA256:3AC8CC58DCBCEAEC3DAB046AEA050357E0E2248D30B0804C738C9A5B037C220D | |||
| 6760 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6760.31773\CrazyNCS.exe | executable | |
MD5:D043BA91E42E0D9A68C9866F002E8A21 | SHA256:6820C71DF417E434C5AD26438C901C780FC5A80B28A466821B47D20B8424EF08 | |||
| 6760 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6760.31773\CookieClickerHack.exe | executable | |
MD5:BC1E7D033A999C4FD006109C24599F4D | SHA256:13ADAE722719839AF8102F98730F3AF1C5A56B58069BFCE8995ACD2123628401 | |||
| 2432 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_YouAreAnIdiot.ex_693db284b24f4d6e5531f56e6b669968df89bc_74378ff6_b65b5ef6-595a-4bc2-8b82-b18824d0e058\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2432 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\YouAreAnIdiot.exe.1660.dmp | — | |
MD5:— | SHA256:— | |||
| 6760 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6760.31773\ScreenScrew.exe | executable | |
MD5:E87A04C270F98BB6B5677CC789D1AD1D | SHA256:E03520794F00FB39EF3CFFF012F72A5D03C60F89DE28DBE69016F6ED151B5338 | |||
| 6760 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6760.31773\Launcher.exe | executable | |
MD5:7506EB94C661522AFF09A5C96D6F182B | SHA256:D5B962DFE37671B5134F0B741A662610B568C2B5374010EE92B5B7857D87872C | |||
| 2432 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER905.tmp.dmp | binary | |
MD5:505F7FCEA004735CB0B46588A8B10A9E | SHA256:6F80966F25716747D02D7706E8BDC699774B48C5CC6172AB994D4B292CEEA807 | |||
| 6760 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6760.31773\ChilledWindows.exe | executable | |
MD5:6A4853CD0584DC90067E15AFB43C4962 | SHA256:CCB9502BF8BA5BECF8B758CA04A5625C30B79E2D10D2677CC43AE4253E1288EC | |||
| 6760 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6760.31773\rickroll.exe | executable | |
MD5:0EC108E32C12CA7648254CF9718AD8D5 | SHA256:48B08EA78124CA010784D9F0FAAE751FC4A0C72C0E7149DED81FC03819F5D723 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
26
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4976 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |