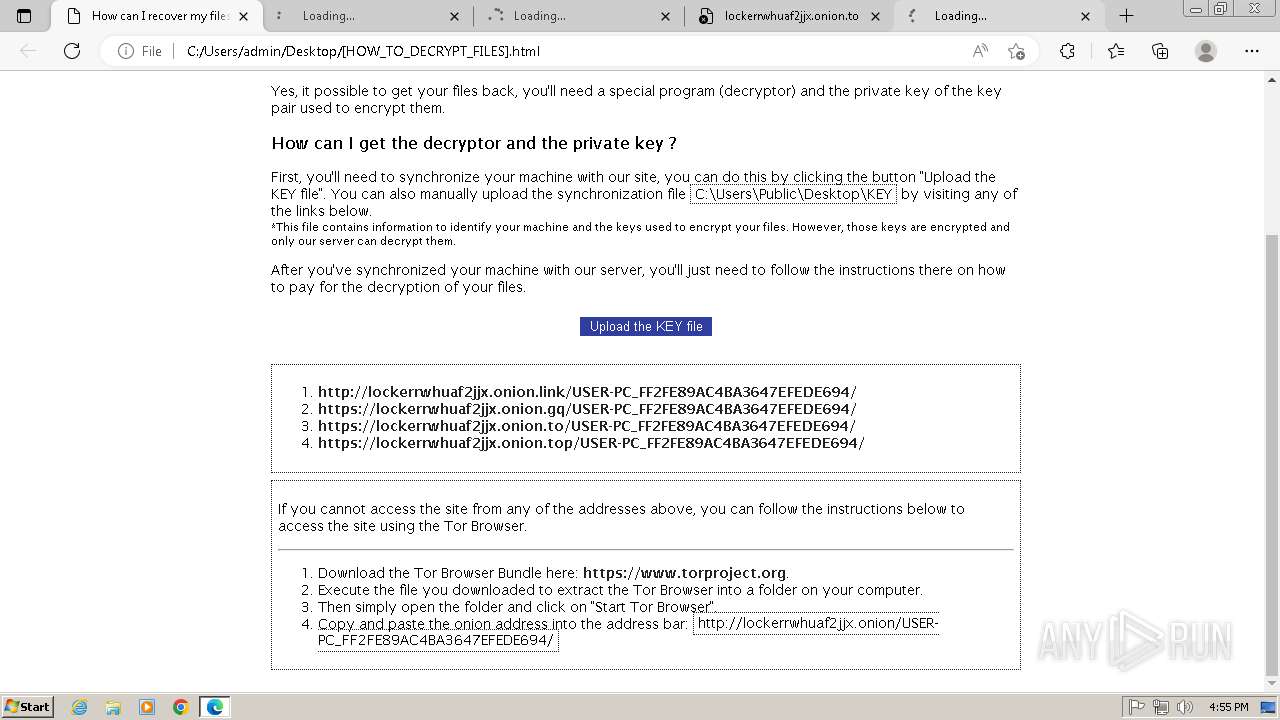
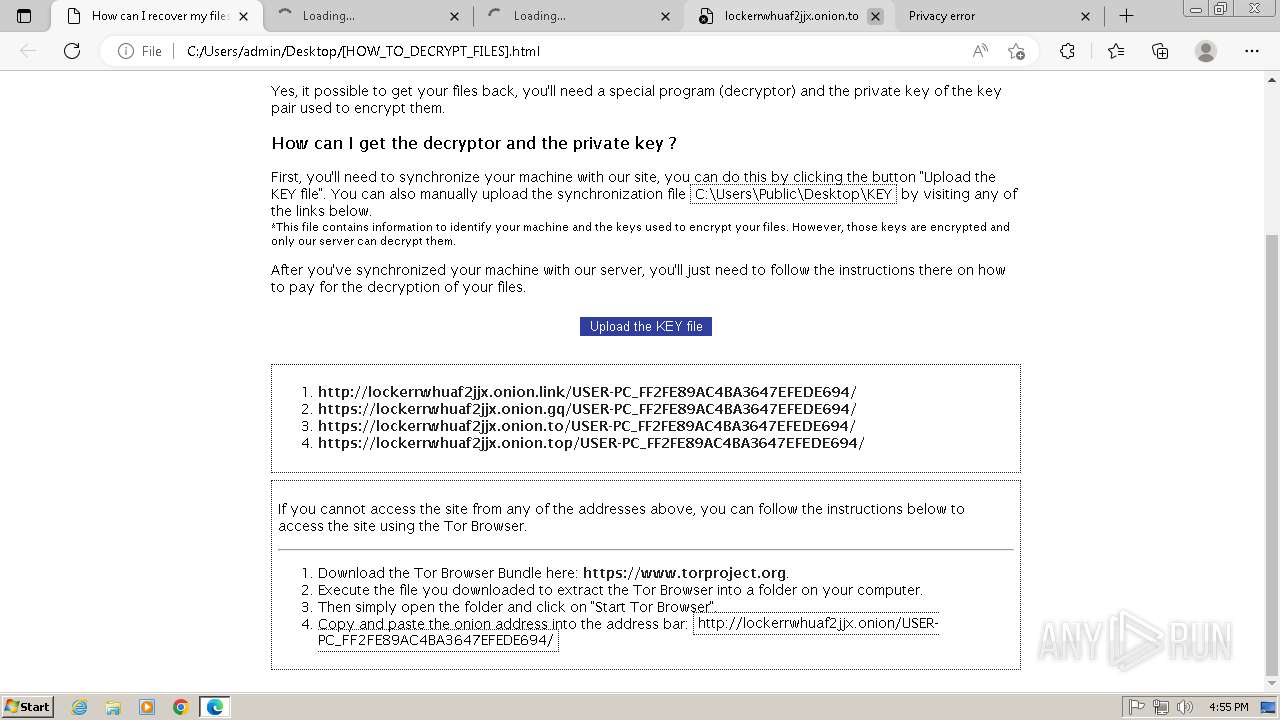
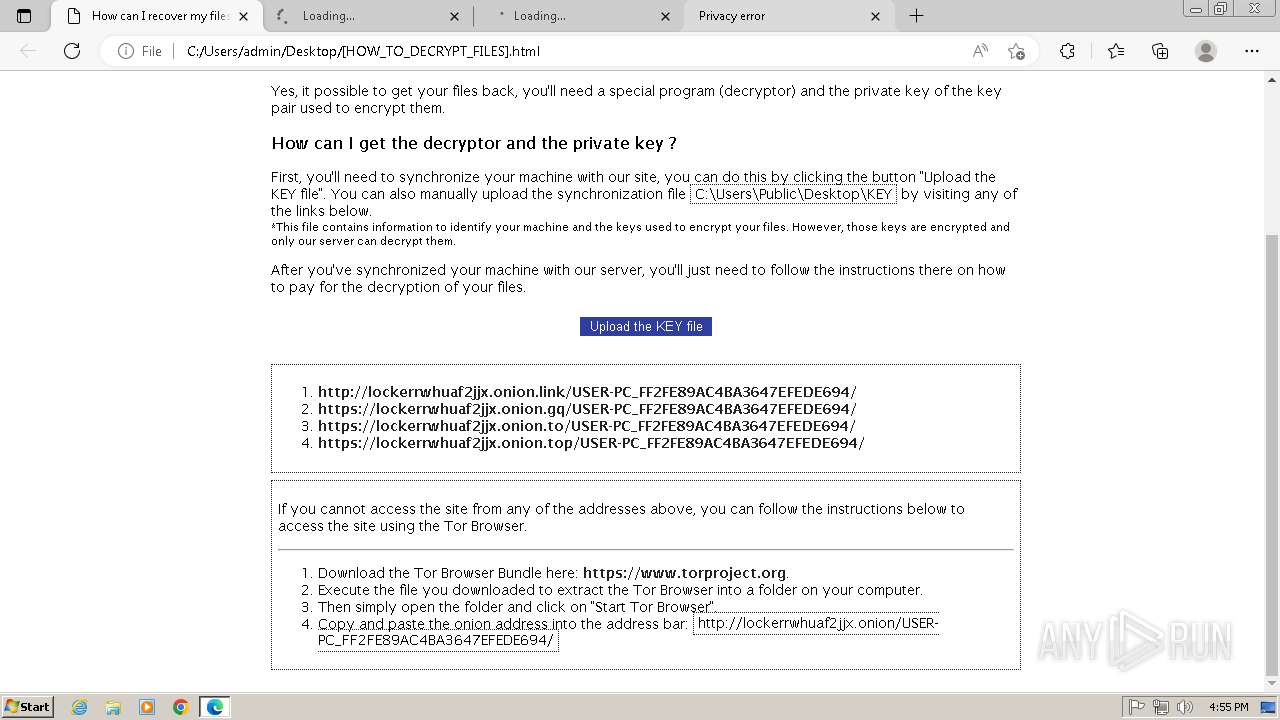
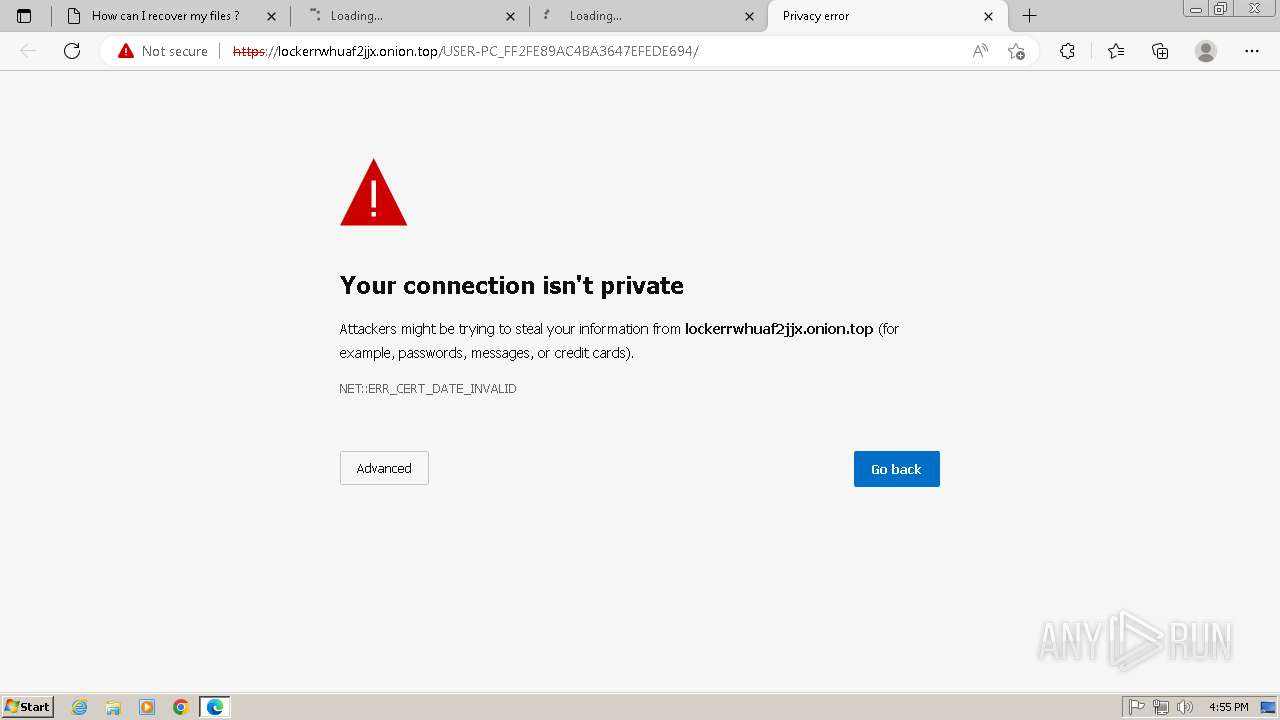
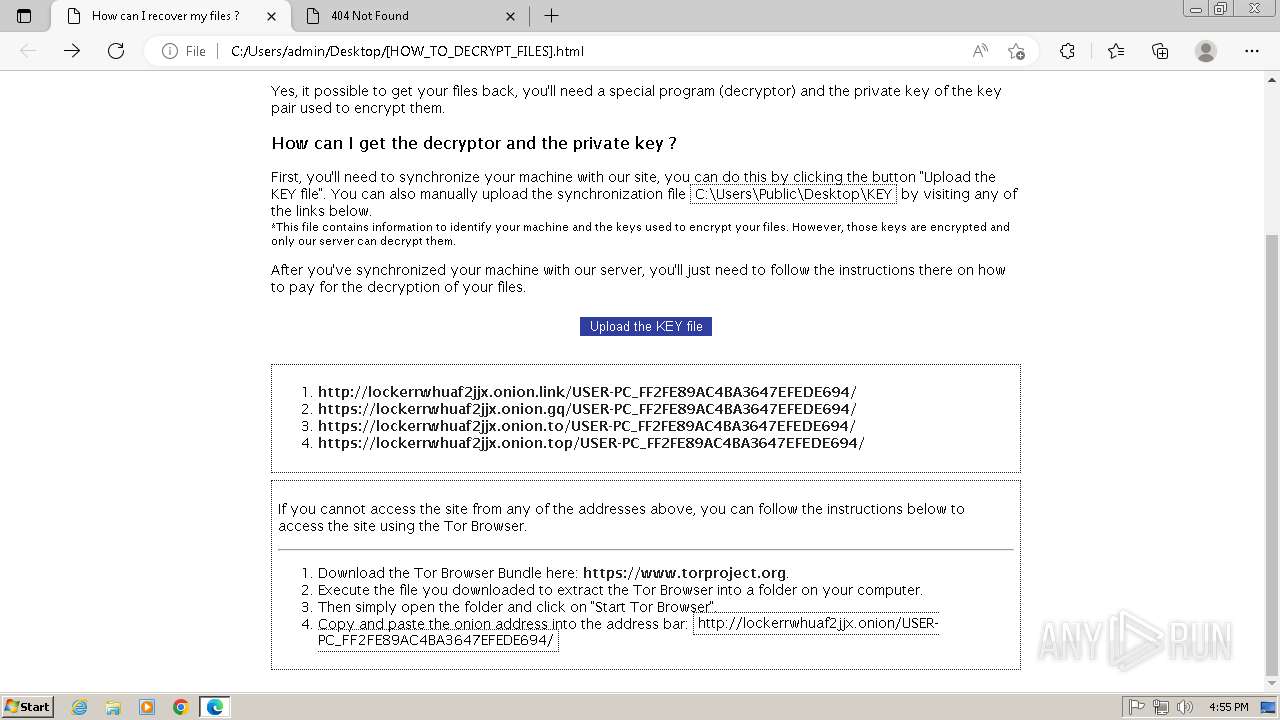
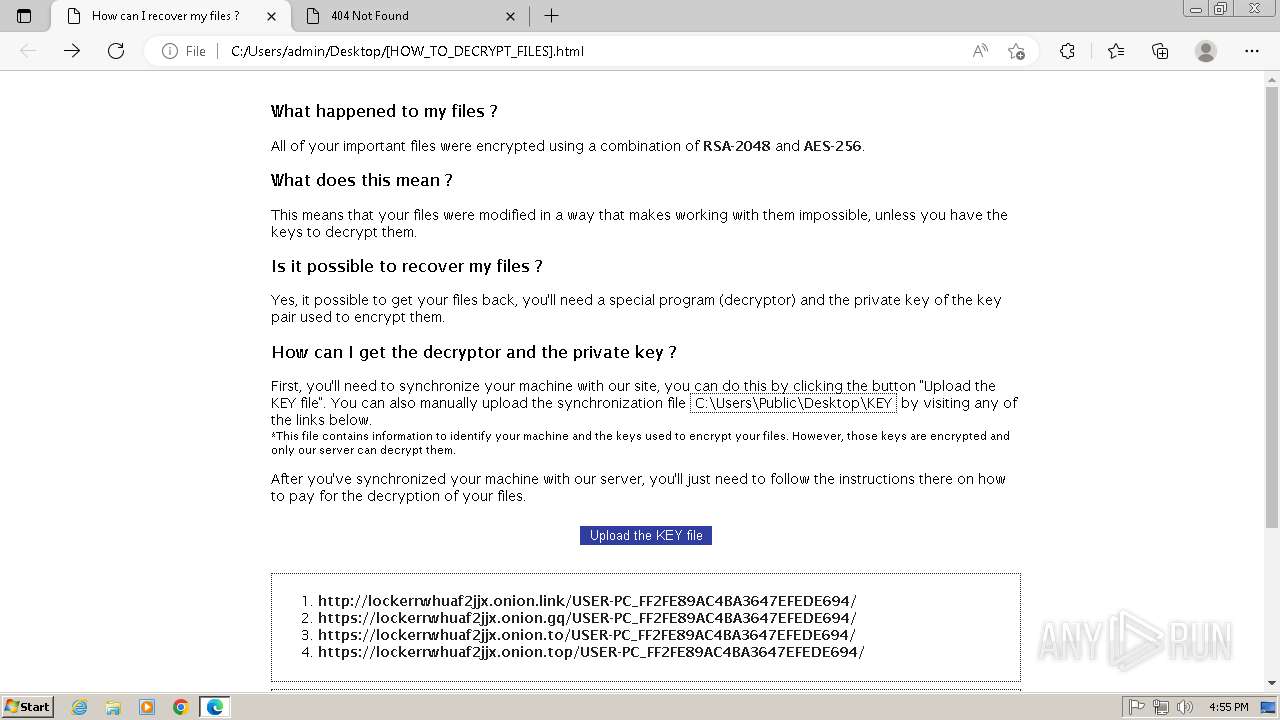
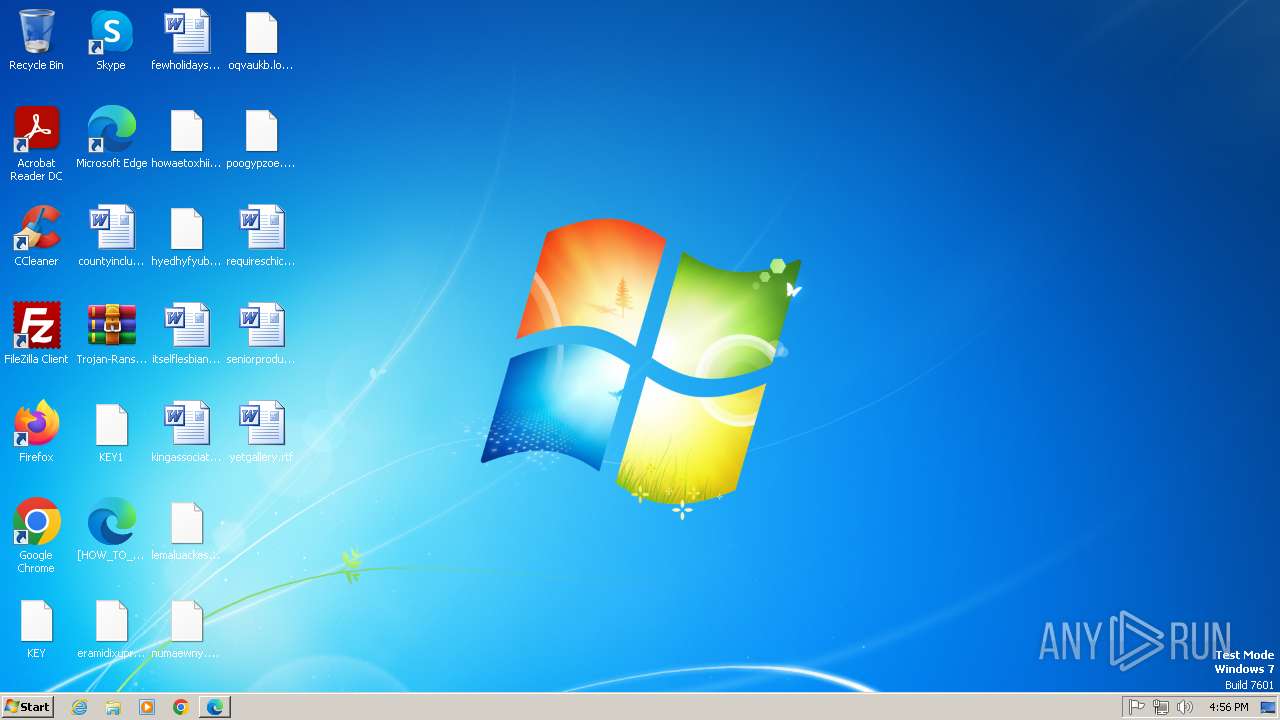
| File name: | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.7z |
| Full analysis: | https://app.any.run/tasks/e33e02af-9abc-4f8a-9bd7-b86f927186cb |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 15:51:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 18EF6DBA4ADE5857DEA1BA2E4D2811B3 |
| SHA1: | 8CAD1CC297B6061E2B6673BF51979F34D0864799 |
| SHA256: | 4647713DED8B45022FC1FEA022ACC8D7C4469C66FEACDDB246952D20A95543CF |
| SSDEEP: | 1536:matjg/4YzcdBOK7oIuW7M+ZmyVmvOLbVqF:9j27zcdEK7oIuWp4QVi |
MALICIOUS
Deletes shadow copies
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
Modifies files in the Chrome extension folder
- usuk.exe (PID: 2772)
Changes the autorun value in the registry
- usuk.exe (PID: 2772)
SUSPICIOUS
Reads the Internet Settings
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
- WMIC.exe (PID: 2356)
Reads security settings of Internet Explorer
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
Reads the date of Windows installation
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
Executes as Windows Service
- VSSVC.exe (PID: 1396)
Block-list domains
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
Reads settings of System Certificates
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
Potential Corporate Privacy Violation
- svchost.exe (PID: 1080)
- msedge.exe (PID: 3536)
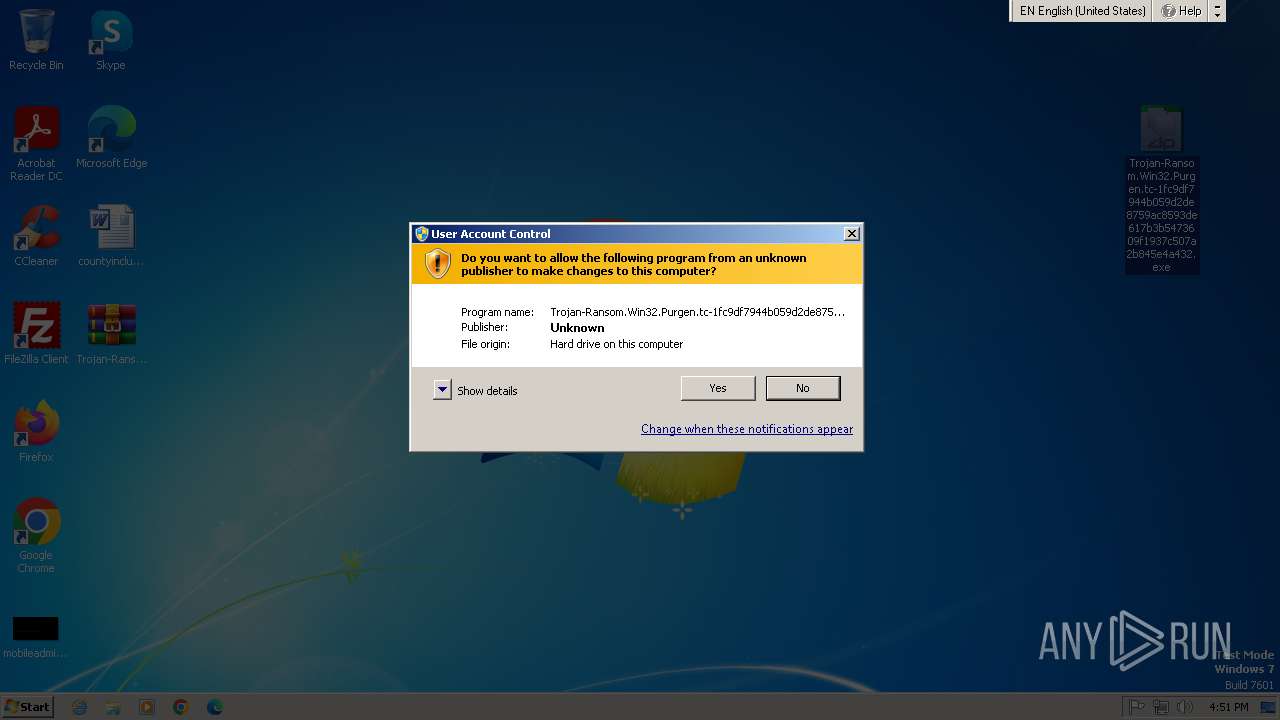
Starts itself from another location
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
Executable content was dropped or overwritten
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
Executing commands from a ".bat" file
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
Starts CMD.EXE for commands execution
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
Reads browser cookies
- usuk.exe (PID: 2772)
Adds/modifies Windows certificates
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
Creates file in the systems drive root
- usuk.exe (PID: 2772)
INFO
Process checks computer location settings
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
- usuk.exe (PID: 2772)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2168)
Checks supported languages
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
- usuk.exe (PID: 2772)
Reads the computer name
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
- usuk.exe (PID: 2772)
Manual execution by a user
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
- msedge.exe (PID: 3384)
Creates files in the program directory
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
- usuk.exe (PID: 2772)
Reads the machine GUID from the registry
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
- usuk.exe (PID: 2772)
Checks proxy server information
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
Creates files or folders in the user directory
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
- usuk.exe (PID: 2772)
Reads the software policy settings
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
Create files in a temporary directory
- Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe (PID: 2432)
- usuk.exe (PID: 2772)
Application launched itself
- msedge.exe (PID: 3384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2018:03:04 19:10:44+00:00 |
| ArchivedFileName: | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe |
Total processes
84
Monitored processes
35
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=3624 --field-trial-handle=1292,i,10155930598367602854,13866863677798047002,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 656 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2188 --field-trial-handle=1292,i,10155930598367602854,13866863677798047002,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 672 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=4084 --field-trial-handle=1292,i,10155930598367602854,13866863677798047002,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 676 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=16 --mojo-platform-channel-handle=4292 --field-trial-handle=1292,i,10155930598367602854,13866863677798047002,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 692 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1632 --field-trial-handle=1292,i,10155930598367602854,13866863677798047002,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 856 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3212 --field-trial-handle=1292,i,10155930598367602854,13866863677798047002,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 988 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4672 --field-trial-handle=1292,i,10155930598367602854,13866863677798047002,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1080 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1108 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --mojo-platform-channel-handle=3292 --field-trial-handle=1292,i,10155930598367602854,13866863677798047002,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1396 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
62 472
Read events
62 030
Write events
426
Delete events
16
Modification events
| (PID) Process: | (1080) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {4040CF00-1B3E-486A-B407-FA14C56B6FC0} |
Value: D4DA6D42058C | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.7z | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
2
Suspicious files
3 440
Text files
387
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1080 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\CabA831.tmp | compressed | |
MD5:77B20B5CD41BC6BB475CCA3F91AE6E3C | SHA256:5511A9B9F9144ED7BDE4CCB074733B7C564D918D2A8B10D391AFC6BE5B3B1509 | |||
| 2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E39EC26C9674650589C7927EB524F7A5 | binary | |
MD5:05CD8C6ABC483F7406CA7149130F451A | SHA256:28BB64CA04335DC9512DEC4BBD1D92A2AAAF19884A64138A0876709B993304A2 | |||
| 2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E39EC26C9674650589C7927EB524F7A5 | binary | |
MD5:AF1C77AECC8D77E9AACB0C475840C392 | SHA256:9D7C3F1AA6AD2B2EC0D5CF1E246F8D9AE6CBC9FD0755AD37BB974B1F2FB603F3 | |||
| 2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E192462F281446B5D1500D474FBACC4B | SHA256:F1BA9F1B63C447682EBF9DE956D0DA2A027B1B779ABEF9522D347D3479139A60 | |||
| 2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys\44190d0b5097f6f34d65bce40e5da119_90059c37-1320-41a4-b58d-2b75a9850d2f | dbf | |
MD5:9458ADDEF151953E6BC40B92F3945C4F | SHA256:8421A88F22044A832D8AA2791B33306D2DE4F511B77963209AED957A83417EC0 | |||
| 2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:856C58930492E691D4CF462109F4D81B | SHA256:4E8FAA037BF5304F7FDEA9A478A921E470103105653A7E01CF3B31C37C67B6E1 | |||
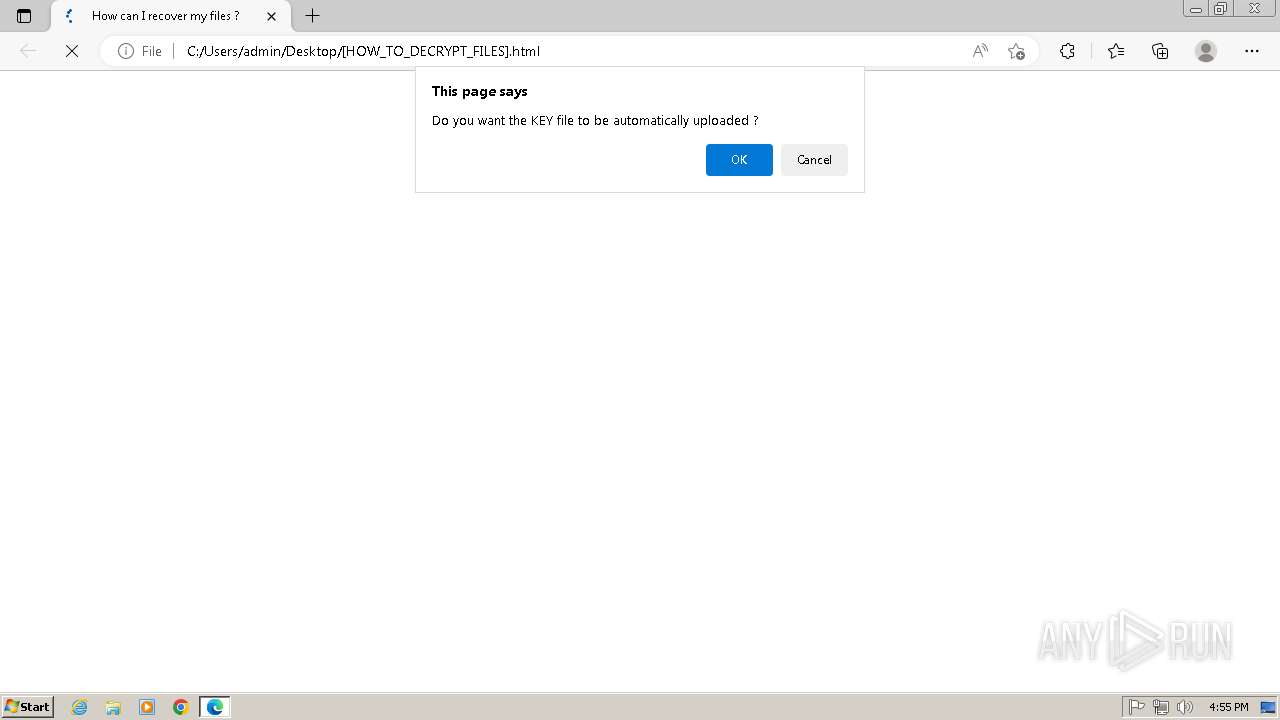
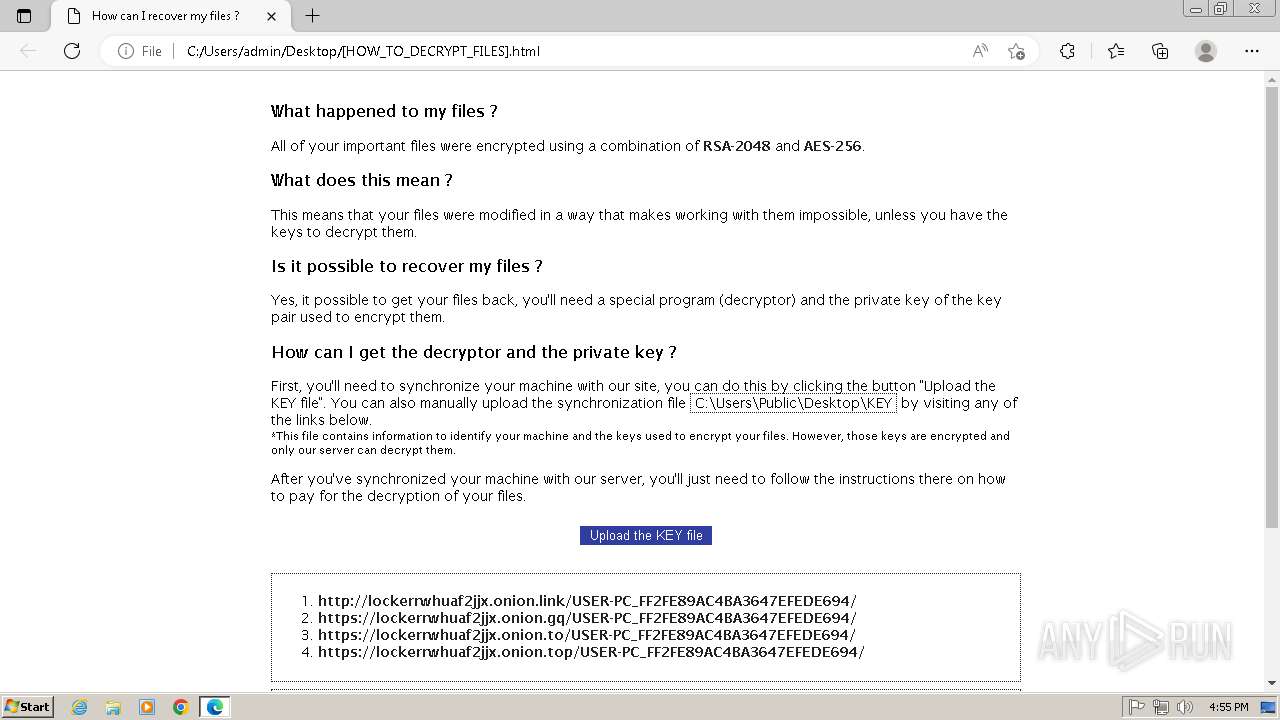
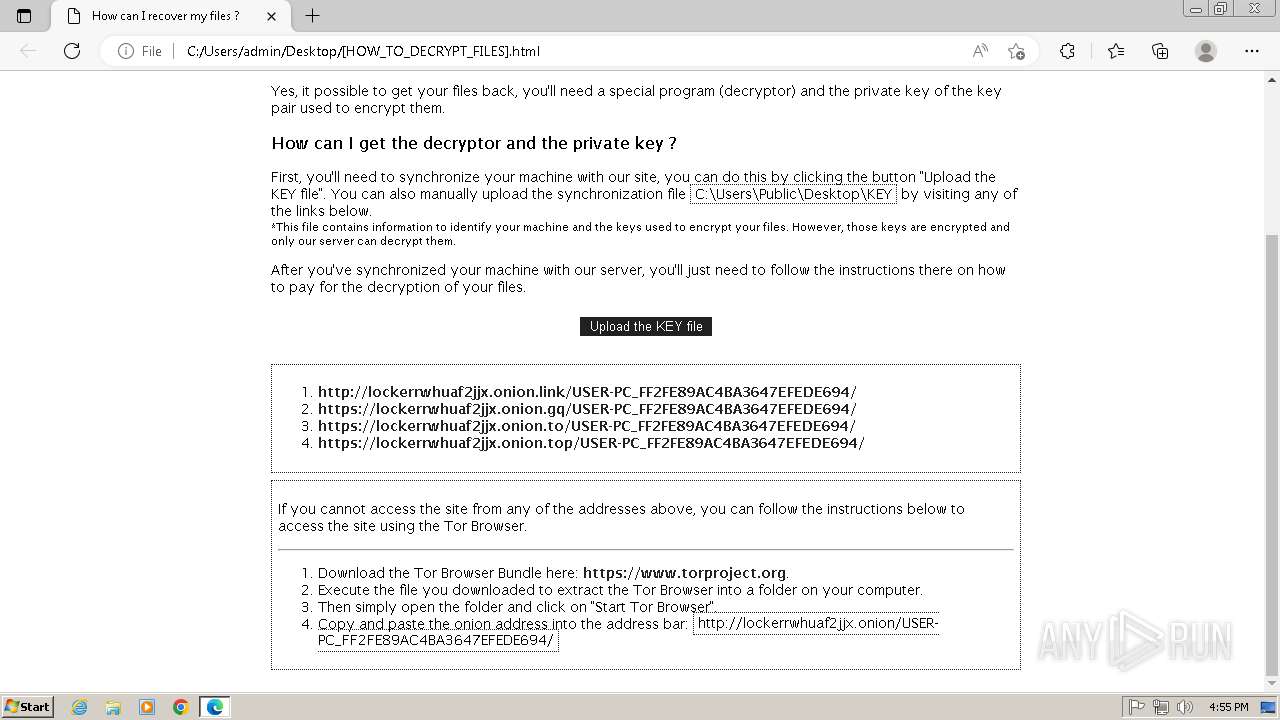
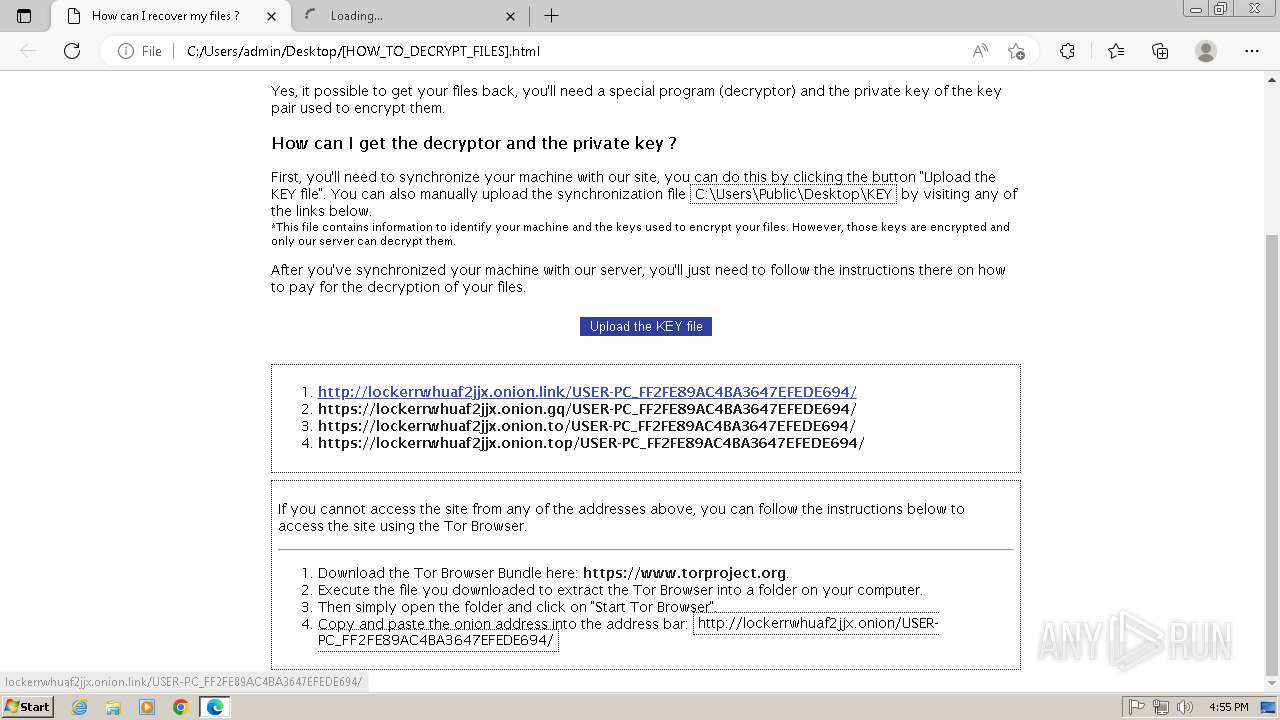
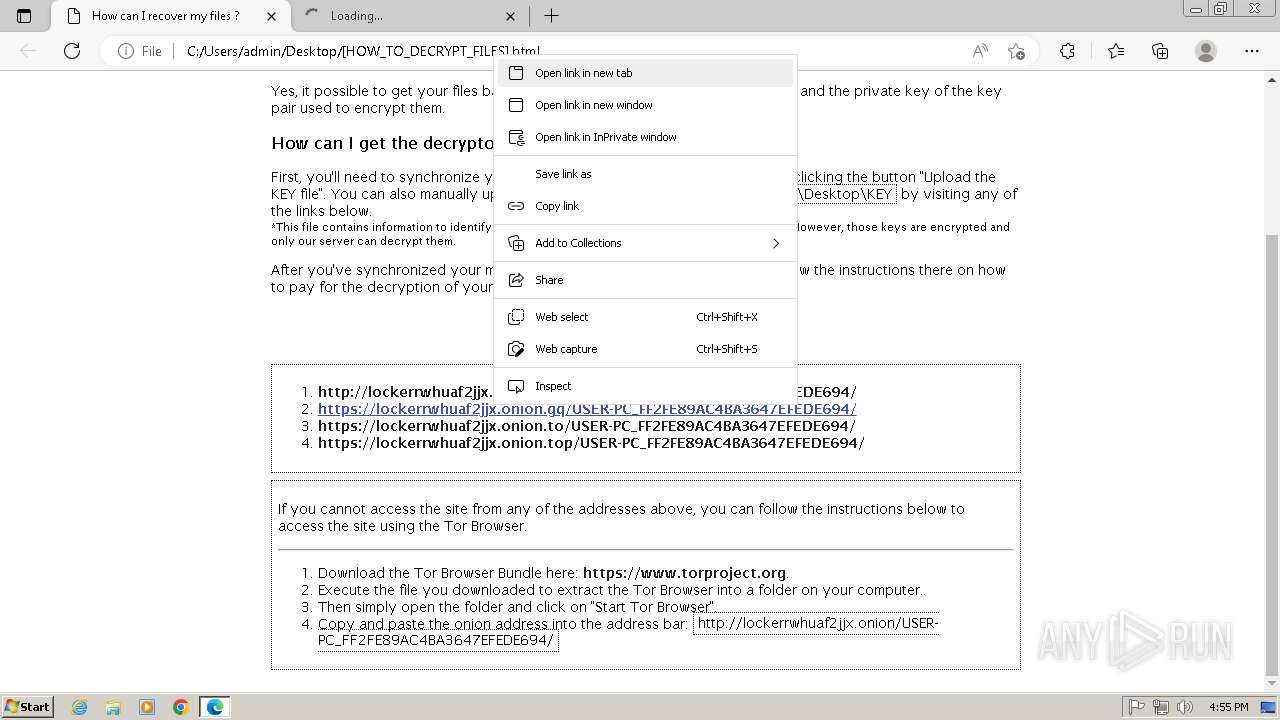
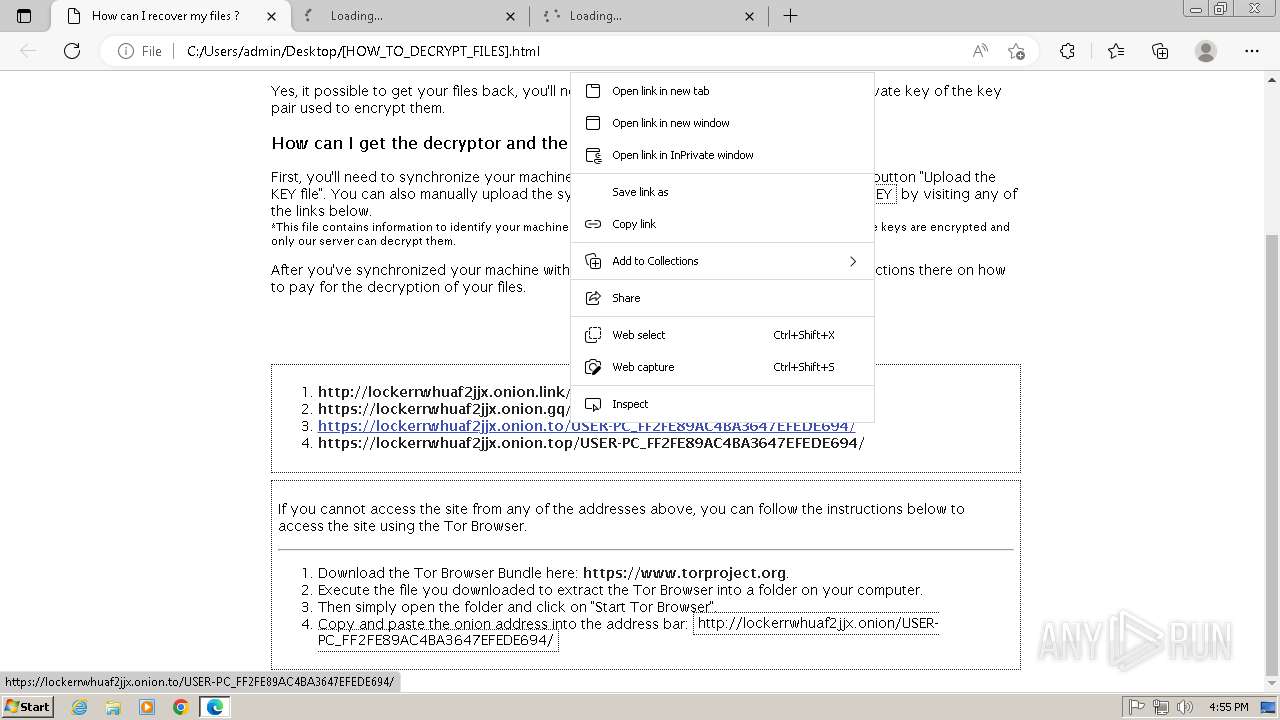
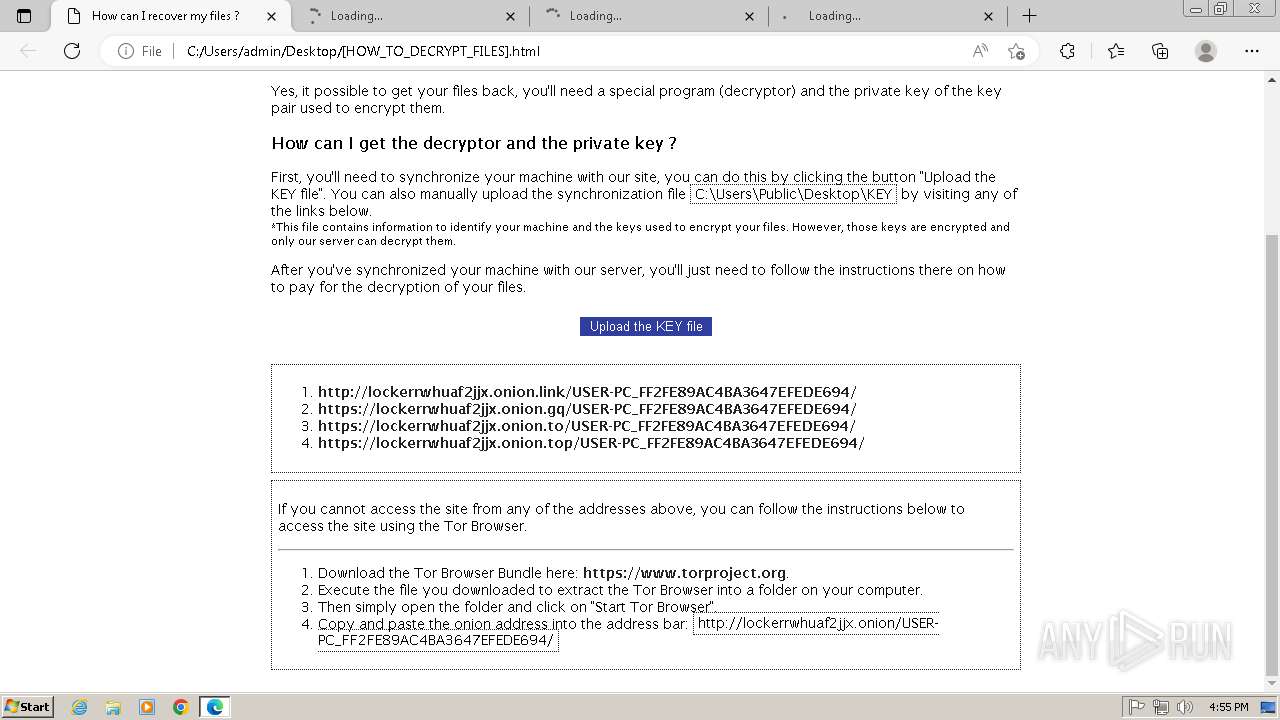
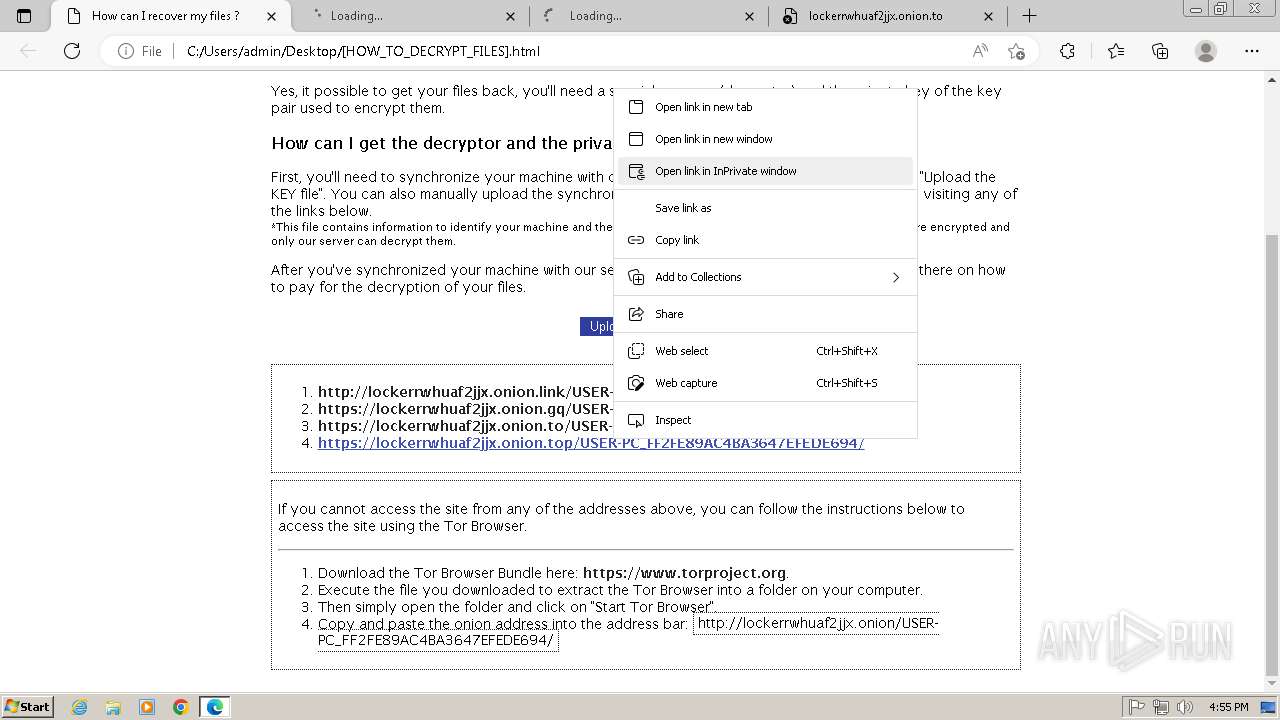
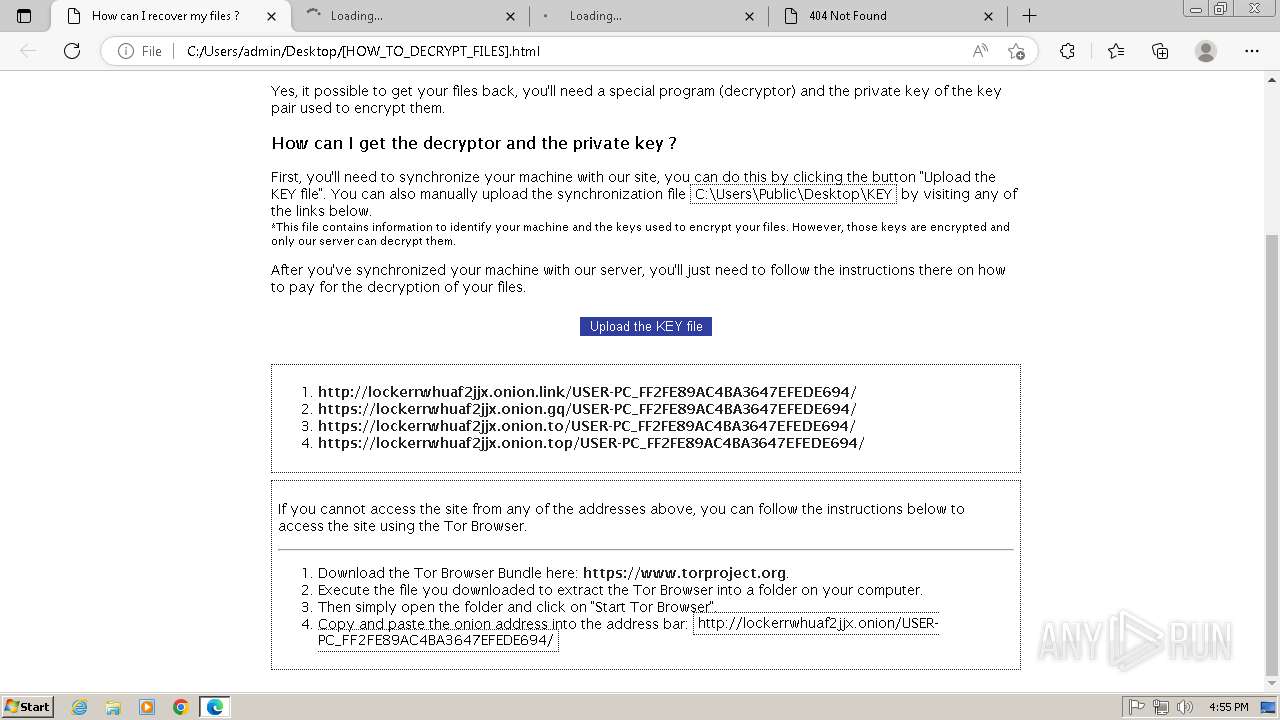
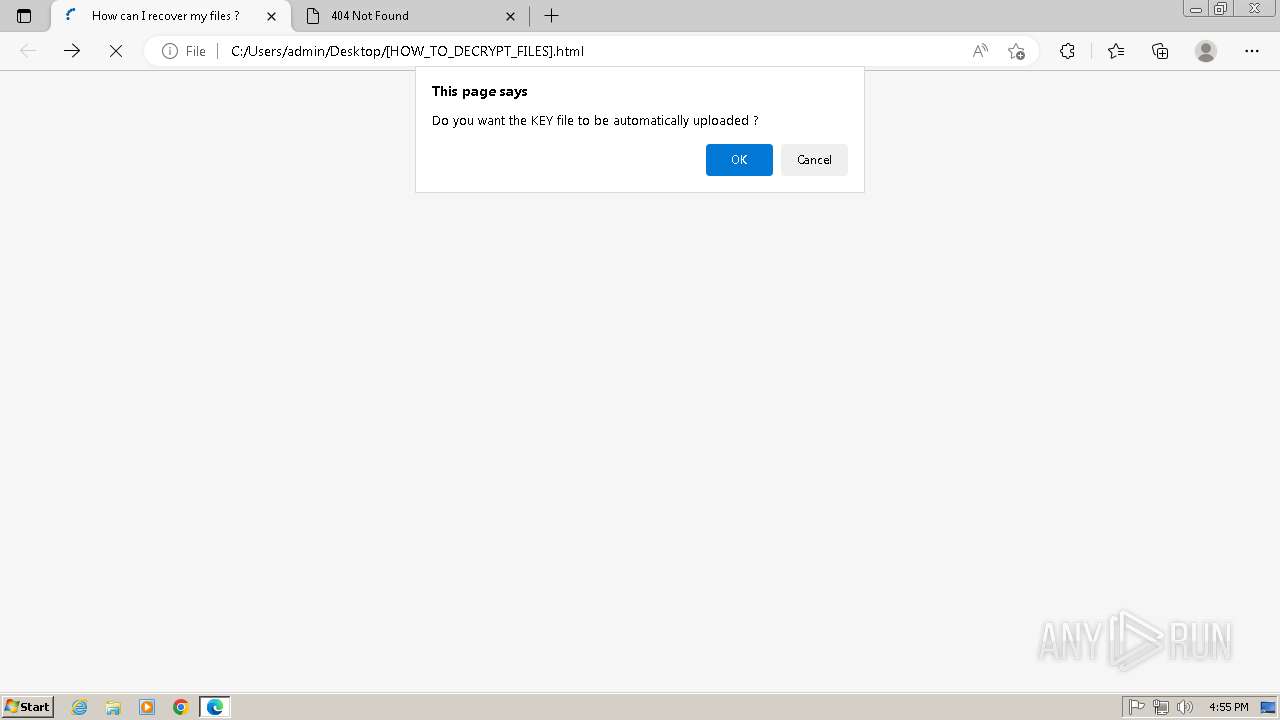
| 2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | C:\Users\Public\Desktop\KEY | binary | |
MD5:08FC1B125CBCA245C4C4E5E9907832C1 | SHA256:7E203FCBC592DFDC7ED1160DBF96182E8202B8F63BEFF77D708F1D0A235EF33C | |||
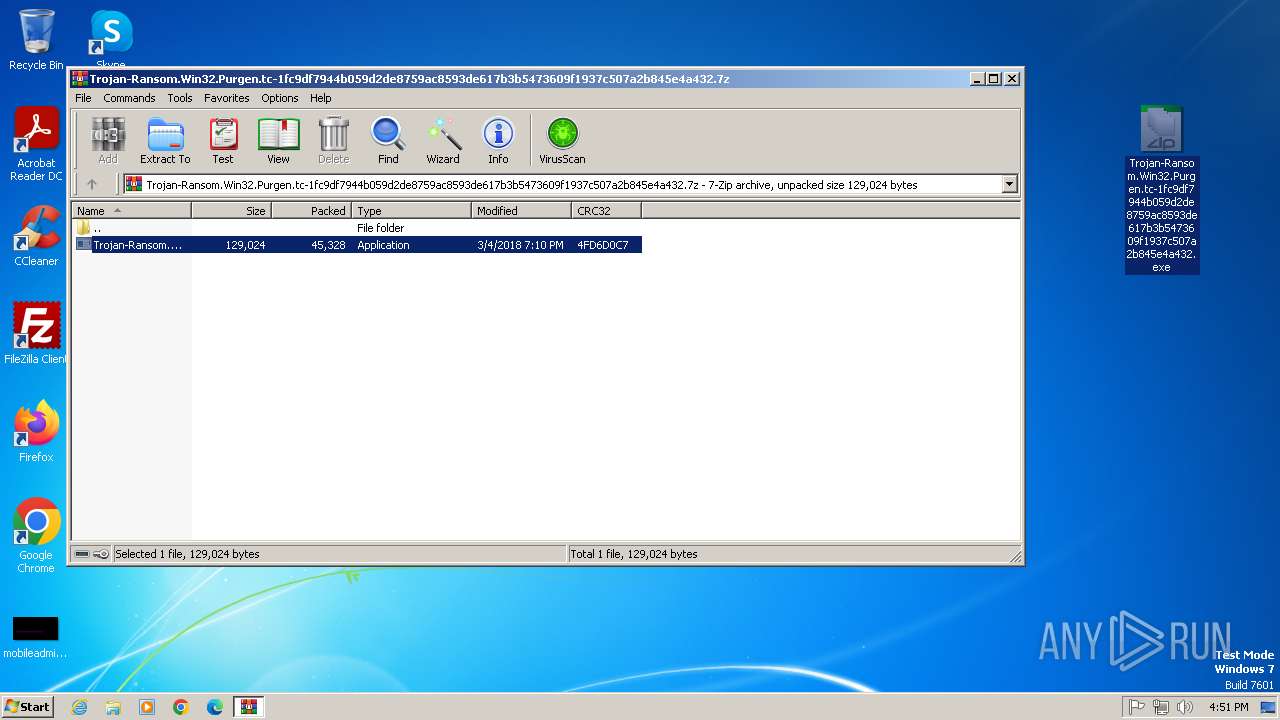
| 2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | C:\Users\admin\AppData\Roaming\Raty\usuk.exe | executable | |
MD5:7B76433B7EC9F02556083474C8DBE5D2 | SHA256:1FC9DF7944B059D2DE8759AC8593DE617B3B5473609F1937C507A2B845E4A432 | |||
| 2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys\e5c2a7ab6b2ddfe46b77fc3505e1c4b0_90059c37-1320-41a4-b58d-2b75a9850d2f | binary | |
MD5:CE62F008AD11C2F7FDAC096CB54C0378 | SHA256:66F9380BB12FDE2D763623A6CE21311A20A4CCAC4CBF9B9611A4A2D2E673929F | |||
| 2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4F3E8D8AE2151BD5B73D29FF2BF40AF1_78FAC4979CF576ED1AE23B2DDDF9066F | binary | |
MD5:ED9DBA22D1EB24A2602A2C477D3515C1 | SHA256:4C888BF34DB3E11DBB59C814DABB07E18BE28D7D151F5BDA1728CB1FAC67FF8E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
45
DNS requests
46
Threats
23
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?895e8458d2d829fb | unknown | — | — | whitelisted |
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | POST | 301 | 144.202.70.158:80 | http://i56bvhjey5gzakmd.onion.pw/gate | unknown | — | — | malicious |
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | GET | 200 | 2.23.227.210:80 | http://r10.i.lencr.org/ | unknown | — | — | whitelisted |
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | GET | 200 | 2.16.168.113:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgU3NapuaGZsp6UOj9fWI9GsjQ%3D%3D | unknown | — | — | whitelisted |
3536 | msedge.exe | GET | 200 | 23.209.209.135:80 | http://x1.i.lencr.org/ | unknown | — | — | whitelisted |
3536 | msedge.exe | GET | 204 | 150.171.74.11:80 | http://edge-http.microsoft.com/captiveportal/generate_204 | unknown | — | — | whitelisted |
3536 | msedge.exe | GET | 200 | 2.23.227.205:80 | http://r10.i.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
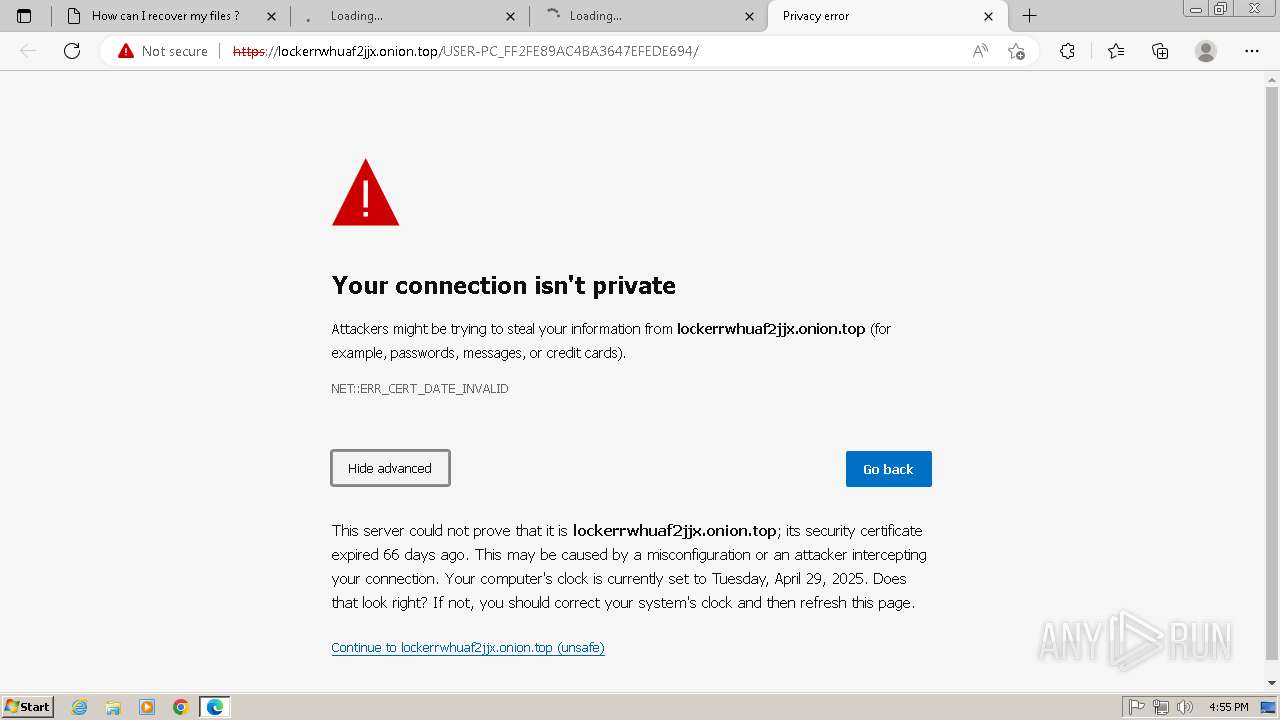
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | 103.198.0.111:80 | i56bvhjey5gzakmd.onion.link | — | — | malicious |
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | 208.117.43.225:443 | i56bvhjey5gzakmd.onion.top | STEADFAST | US | malicious |
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | 144.202.70.158:80 | i56bvhjey5gzakmd.onion.pw | AS-CHOOPA | US | unknown |
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | 144.202.70.158:443 | i56bvhjey5gzakmd.onion.pw | AS-CHOOPA | US | unknown |
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | 2.23.227.210:80 | r10.i.lencr.org | Ooredoo Q.S.C. | QA | whitelisted |
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | 23.209.209.135:80 | x1.c.lencr.org | PT. Telekomunikasi Selular | ID | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
i56bvhjey5gzakmd.onion.link |
| unknown |
i56bvhjey5gzakmd.onion.to |
| whitelisted |
i56bvhjey5gzakmd.onion.sx |
| unknown |
i56bvhjey5gzakmd.onion.top |
| malicious |
i56bvhjey5gzakmd.onion.pw |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
r10.i.lencr.org |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r10.o.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO DNS Query to .onion proxy Domain (onion.link) |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1080 | svchost.exe | Potential Corporate Privacy Violation | ET INFO DNS Query to .onion proxy Domain (onion.top) |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query to .onion proxy Domain (onion. sx) |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query to .onion proxy Domain (onion.to) |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query to .onion proxy Domain (onion. pw) |
2432 | Trojan-Ransom.Win32.Purgen.tc-1fc9df7944b059d2de8759ac8593de617b3b5473609f1937c507a2b845e4a432.exe | Misc activity | ET INFO HTTP Request to a *.pw domain |
3536 | msedge.exe | Misc activity | ET INFO DNS Query to .onion proxy Domain (onion.link) |