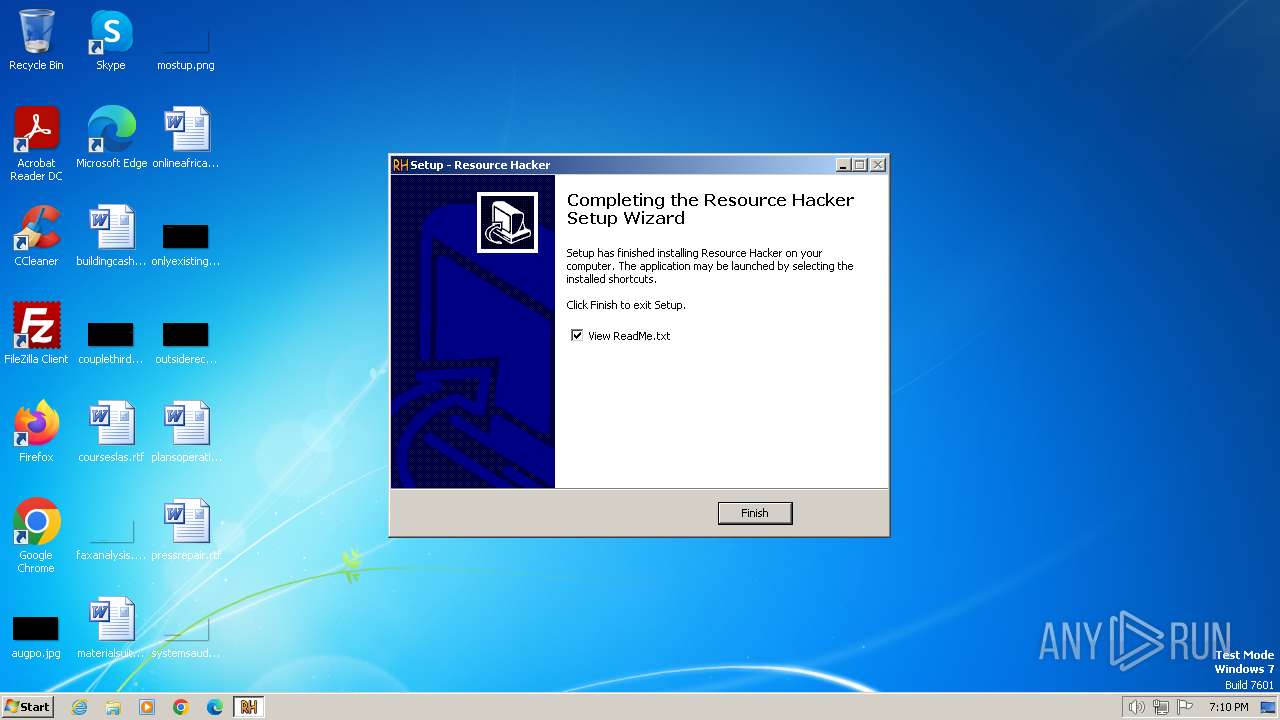
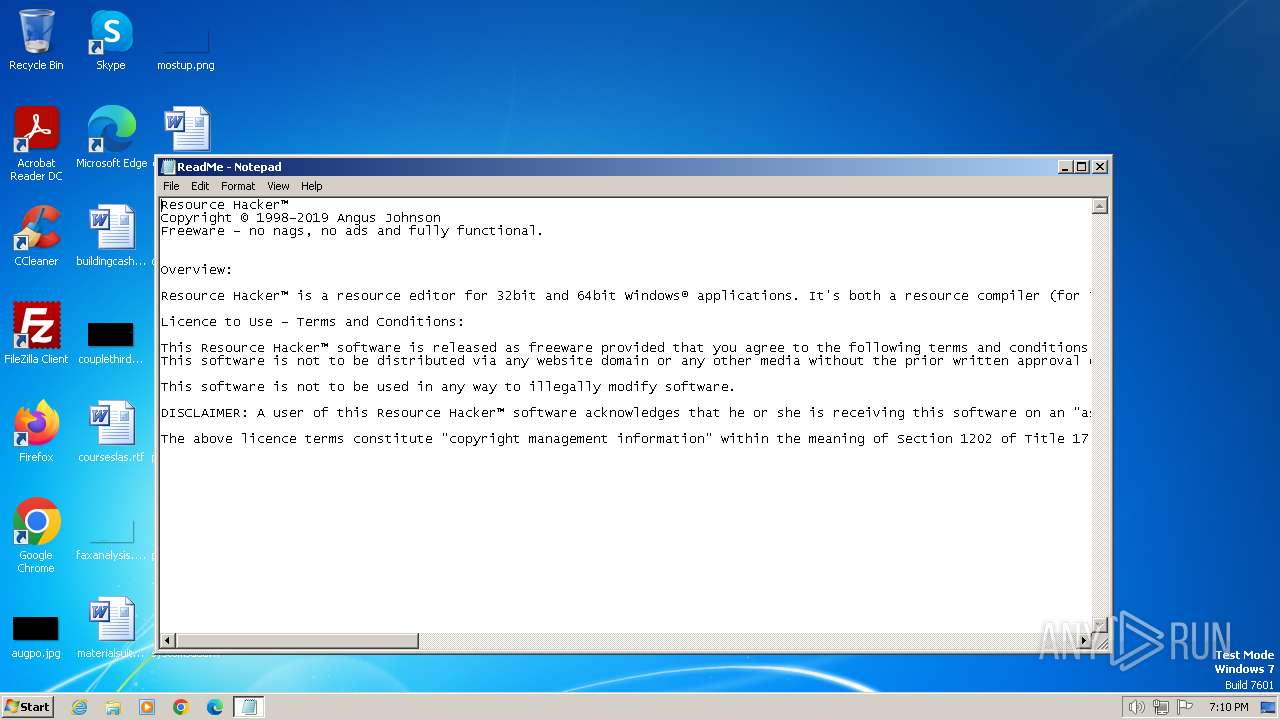
| File name: | reshacker_setup.exe |
| Full analysis: | https://app.any.run/tasks/a51711f2-ee33-4137-aa4f-c9f643ae7269 |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2024, 19:10:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C2734FF00DA8A35A8319F6D4EE3E07D3 |
| SHA1: | DF3D047CE866E17852286044C099E0675034B534 |
| SHA256: | 46431DDF68FD664B0F58DFB1625A52936AF3BA48EE340CC05D89346024DD6601 |
| SSDEEP: | 98304:hKRjZAp7hM1K0EW2juaWYKRb8+WKtmkssyjPfwBnc8W8mQwoWEzCI4uIX9jcDujO:zxRFI |
MALICIOUS
Drops the executable file immediately after the start
- runas.exe (PID: 3864)
- reshacker_setup.exe (PID: 3732)
- reshacker_setup.tmp (PID: 3216)
SUSPICIOUS
Executable content was dropped or overwritten
- reshacker_setup.exe (PID: 3732)
- reshacker_setup.tmp (PID: 3216)
Reads the Windows owner or organization settings
- reshacker_setup.tmp (PID: 3216)
Start notepad (likely ransomware note)
- reshacker_setup.tmp (PID: 3216)
Reads the Internet Settings
- ResourceHacker.exe (PID: 1492)
Reads the date of Windows installation
- ResourceHacker.exe (PID: 1492)
Loads DLL from Mozilla Firefox
- ResourceHacker.exe (PID: 1492)
INFO
Checks supported languages
- reshacker_setup.exe (PID: 3732)
- reshacker_setup.tmp (PID: 3216)
- ResourceHacker.exe (PID: 1492)
Creates files in the program directory
- reshacker_setup.tmp (PID: 3216)
- ResourceHacker.exe (PID: 1492)
Reads the computer name
- reshacker_setup.tmp (PID: 3216)
- ResourceHacker.exe (PID: 1492)
Creates a software uninstall entry
- reshacker_setup.tmp (PID: 3216)
Manual execution by a user
- ResourceHacker.exe (PID: 1492)
- rundll32.exe (PID: 2896)
- notepad++.exe (PID: 848)
Reads the machine GUID from the registry
- ResourceHacker.exe (PID: 1492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (81.5) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10.5) |
| .exe | | | Win32 Executable (generic) (3.3) |
| .exe | | | Win16/32 Executable Delphi generic (1.5) |
| .exe | | | Generic Win/DOS Executable (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41472 |
| InitializedDataSize: | 105472 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaa98 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | Resource Hacker Setup |
| FileVersion: | |
| LegalCopyright: | Copyright © 1998 - 2019 Angus Johnson. |
| ProductName: | Resource Hacker |
| ProductVersion: |
Total processes
46
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\fff.res" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Resource Hacker\ResourceHacker.exe" | C:\Program Files\Resource Hacker\ResourceHacker.exe | — | explorer.exe | |||||||||||
User: admin Company: Angus Johnson Integrity Level: MEDIUM Description: Resource viewer, decompiler & recompiler Exit code: 0 Version: 5.1.7.343 Modules
| |||||||||||||||
| 2840 | "C:\Windows\system32\NOTEPAD.EXE" C:\Program Files\Resource Hacker\ReadMe.txt | C:\Windows\System32\notepad.exe | — | reshacker_setup.tmp | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2896 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\fff.res | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3216 | "C:\Users\ADMINI~1\AppData\Local\Temp\is-F2768.tmp\reshacker_setup.tmp" /SL5="$E0214,2649214,147968,C:\Users\admin\Downloads\reshacker_setup.exe" | C:\Users\Administrator\AppData\Local\Temp\is-F2768.tmp\reshacker_setup.tmp | reshacker_setup.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3732 | C:\Users\admin\Downloads\reshacker_setup.exe | C:\Users\admin\Downloads\reshacker_setup.exe | runas.exe | ||||||||||||
User: Administrator Company: Integrity Level: HIGH Description: Resource Hacker Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3864 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\Downloads\reshacker_setup.exe | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
14 662
Read events
14 015
Write events
565
Delete events
82
Modification events
| (PID) Process: | (3216) reshacker_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 900C0000A49158F71D5DDA01 | |||
| (PID) Process: | (3216) reshacker_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 11A02E5AE0DEBB4AB75C124BDE5DB983615659BE774D5969DEE4EFDEB91FC99A | |||
| (PID) Process: | (3216) reshacker_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3216) reshacker_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Resource Hacker\ResourceHacker.exe | |||
| (PID) Process: | (3216) reshacker_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 1EE8F21520CE73E6A7FA8E046A21856CD0B9643110EADDEAA998A8D5C42BE315 | |||
| (PID) Process: | (3216) reshacker_setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ResourceHacker_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.9 (a) | |||
| (PID) Process: | (3216) reshacker_setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ResourceHacker_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\Resource Hacker | |||
| (PID) Process: | (3216) reshacker_setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ResourceHacker_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Resource Hacker\ | |||
| (PID) Process: | (3216) reshacker_setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ResourceHacker_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Resource Hacker | |||
| (PID) Process: | (3216) reshacker_setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ResourceHacker_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: Administrator | |||
Executable files
8
Suspicious files
4
Text files
34
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3216 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\is-0H67O.tmp | executable | |
MD5:1126825F25C71AFC621EC89D2B026240 | SHA256:4B255534D59E984E8B87827BE6EF7EFE1E218301FF9EC81F8B3D750BB0951A99 | |||
| 3216 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\help\rh_dlg_ctrl.png | image | |
MD5:1DDEE97A31B52AF6E8A5E718B5B02C08 | SHA256:B4692A3BE299443A39350B0AF56A966F655EF06F140F3C142BC458FDA9BD9459 | |||
| 3216 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\help\is-SMGD9.tmp | html | |
MD5:7706B8D30FAB091187ED84C67C39CF45 | SHA256:D624DF13EC0225EB387F31BEBC94678DD12D5226779496E3CD928141F5479E4D | |||
| 3216 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\ReadMe.txt | text | |
MD5:1309C8B9CC851D5EE46D106423F25F68 | SHA256:4012BA4C95101983F5512F603E9ADEBE16EA9D553C09183A3CD2E4FC70B1963B | |||
| 3216 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\is-4KL4O.tmp | text | |
MD5:C3CDD3198E43F3EC42563E1378FA8522 | SHA256:1A79AC86A957F1DCAB9E97148ED9F1B4056505F049AEF58CF5B4058468868825 | |||
| 3216 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\unins000.exe | executable | |
MD5:C03332CF42786FD312E13E3B901D3F2A | SHA256:4836B10877D86FA87FAC91EE9E6D02CCBFF4DCF8B1FAB68367E9698F8B7AA46B | |||
| 3216 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\help\is-TCM3U.tmp | image | |
MD5:B6577C2A048E6F9FA588994345A21400 | SHA256:0BB5001274535E7BD4A88E95FA5497D28507313BD8C9C5FE6D16E763DA5F8B25 | |||
| 3216 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\is-LURLV.tmp | text | |
MD5:1309C8B9CC851D5EE46D106423F25F68 | SHA256:4012BA4C95101983F5512F603E9ADEBE16EA9D553C09183A3CD2E4FC70B1963B | |||
| 3216 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\help\index.htm | html | |
MD5:7706B8D30FAB091187ED84C67C39CF45 | SHA256:D624DF13EC0225EB387F31BEBC94678DD12D5226779496E3CD928141F5479E4D | |||
| 3216 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\help\rh_icon.png | image | |
MD5:0513C11177A2EDE618D8FC375F9C3767 | SHA256:55826A6FD5E1056F3CD85110EFAC33EABF28364E1B2E3370CF565793DC0FBB26 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|