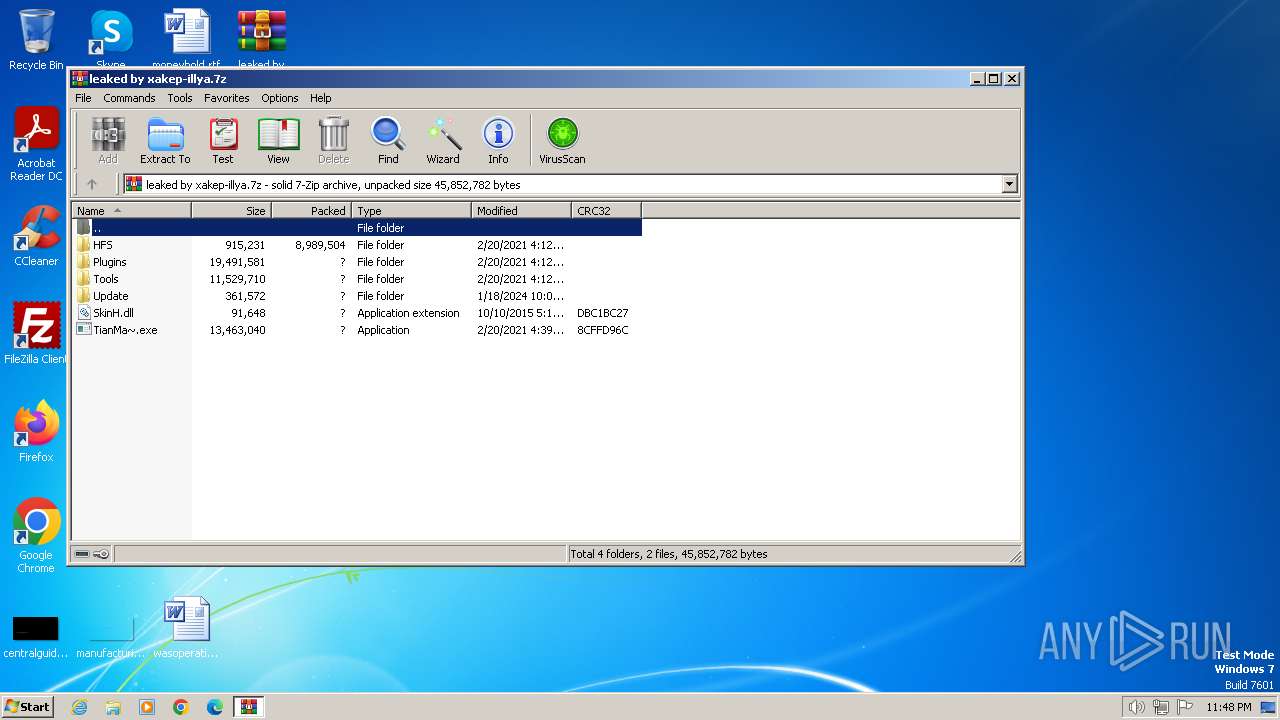
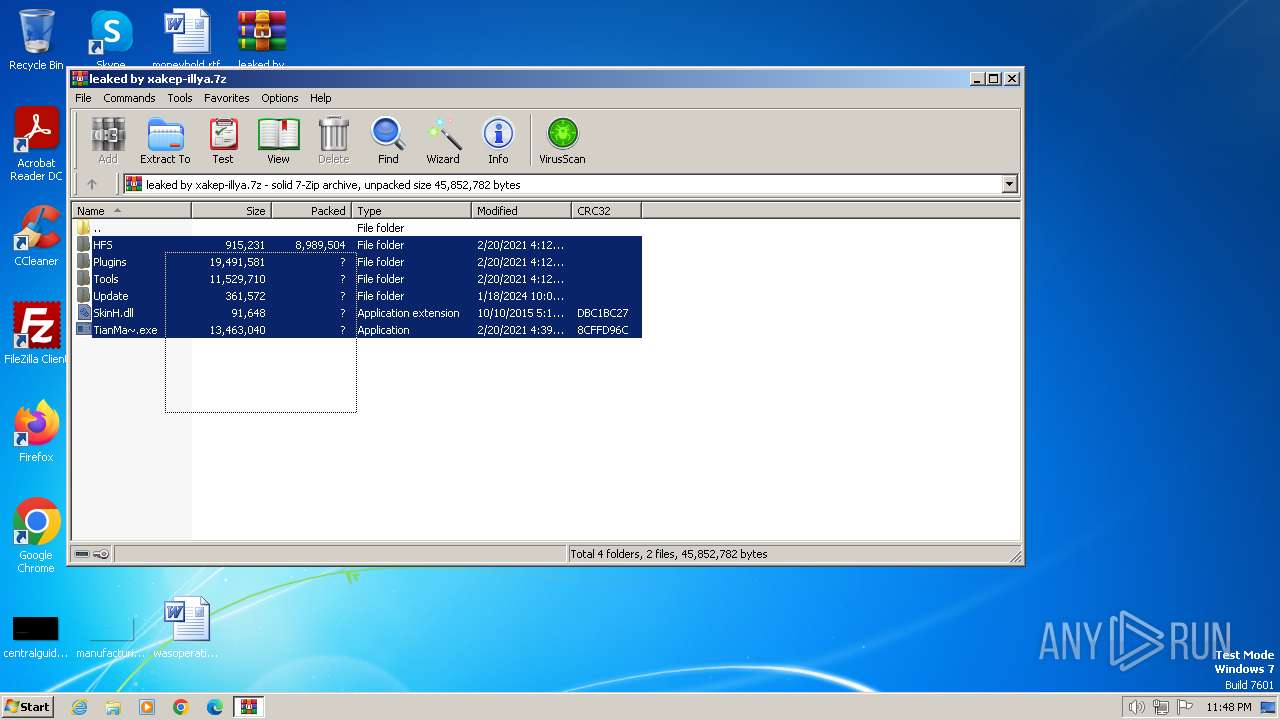
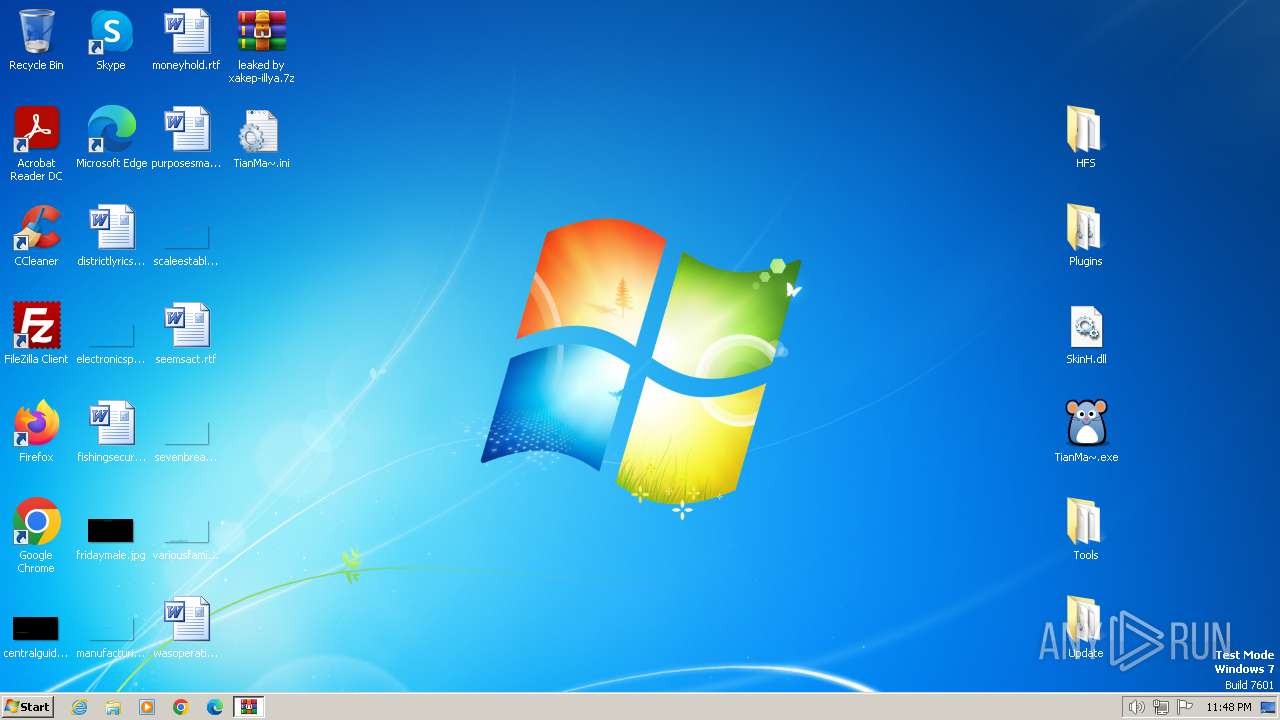
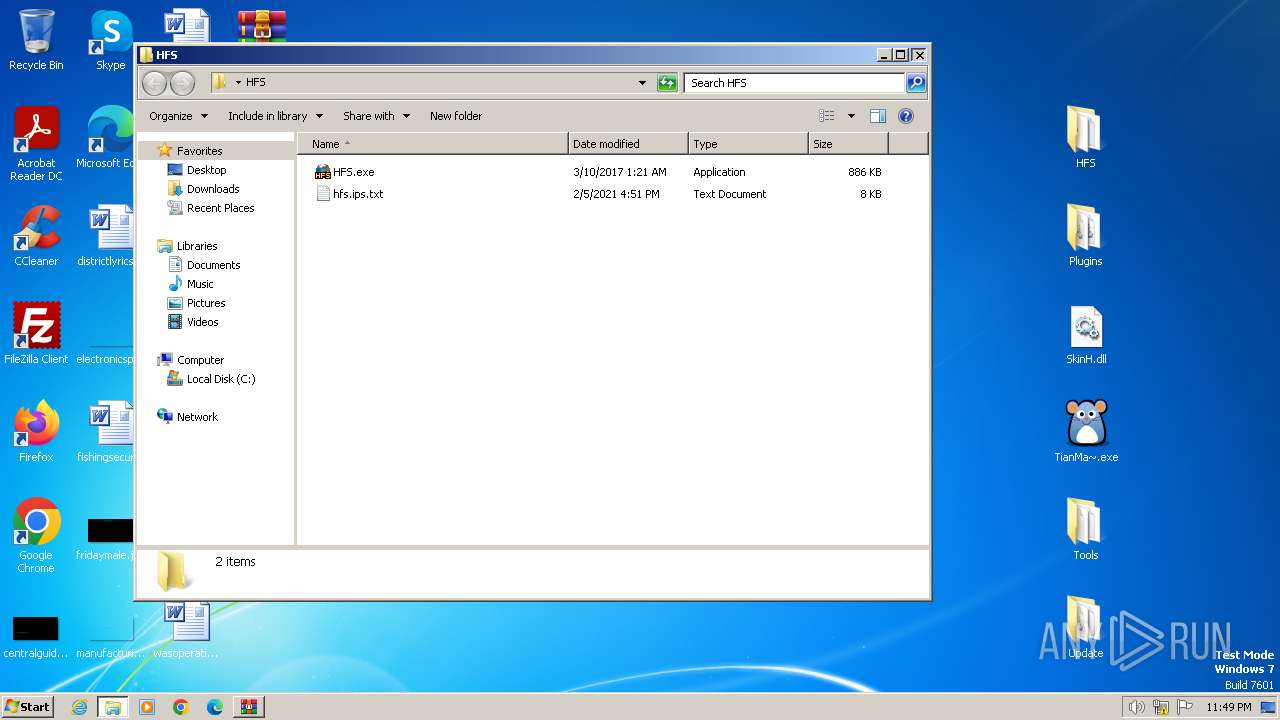
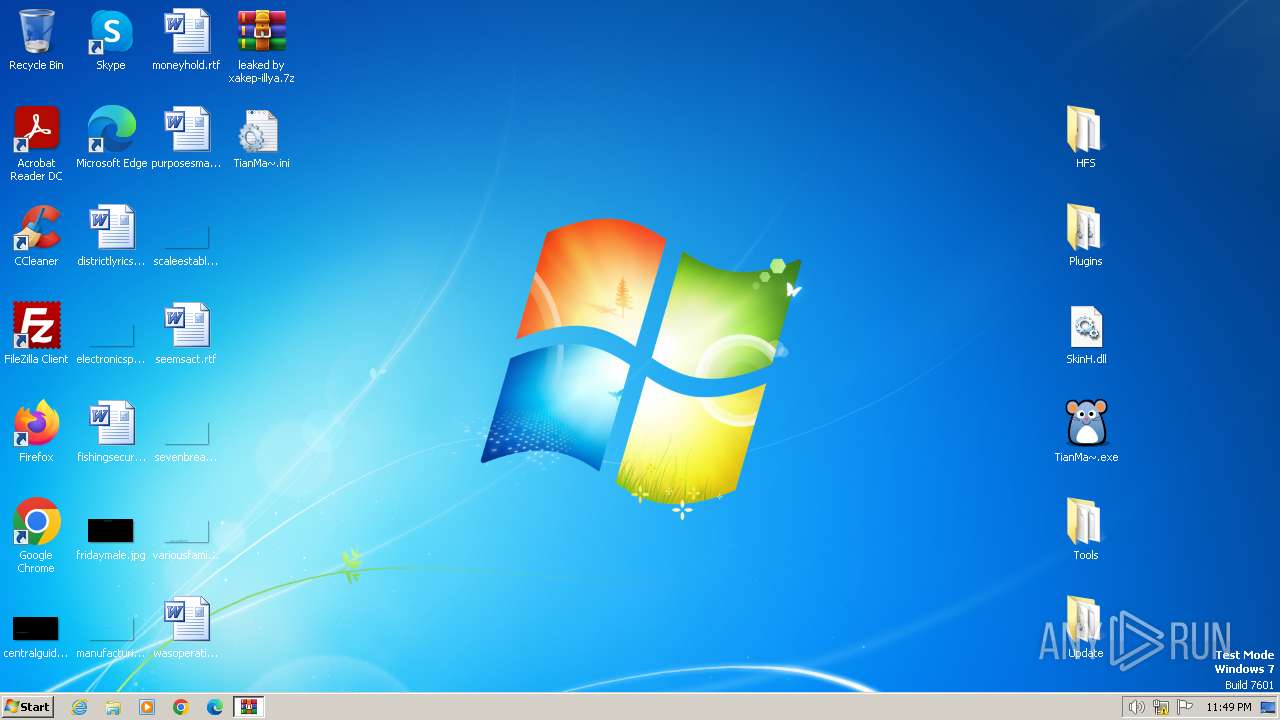
| File name: | leaked by xakep-illya.7z |
| Full analysis: | https://app.any.run/tasks/4576a687-6a46-4ab6-997b-d753c5ed6824 |
| Verdict: | Malicious activity |
| Analysis date: | February 15, 2024, 23:47:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 128BB26FEA797F3817DBEEBAD6968CB9 |
| SHA1: | 59E6B02B429F1FB0D480103F1E37F00A8137554B |
| SHA256: | 4642D79EA650349FDD95AF222826B28D91B5945F8EE3C19A67857495B01AEAE8 |
| SSDEEP: | 98304:tVs1QSepIa7CYh1QfpXZFzxADH7mTAUBwO23Req6HeMVghXQNh5mVP64phDReHnZ:+AiE9bnkLZJJ9/a8 |
MALICIOUS
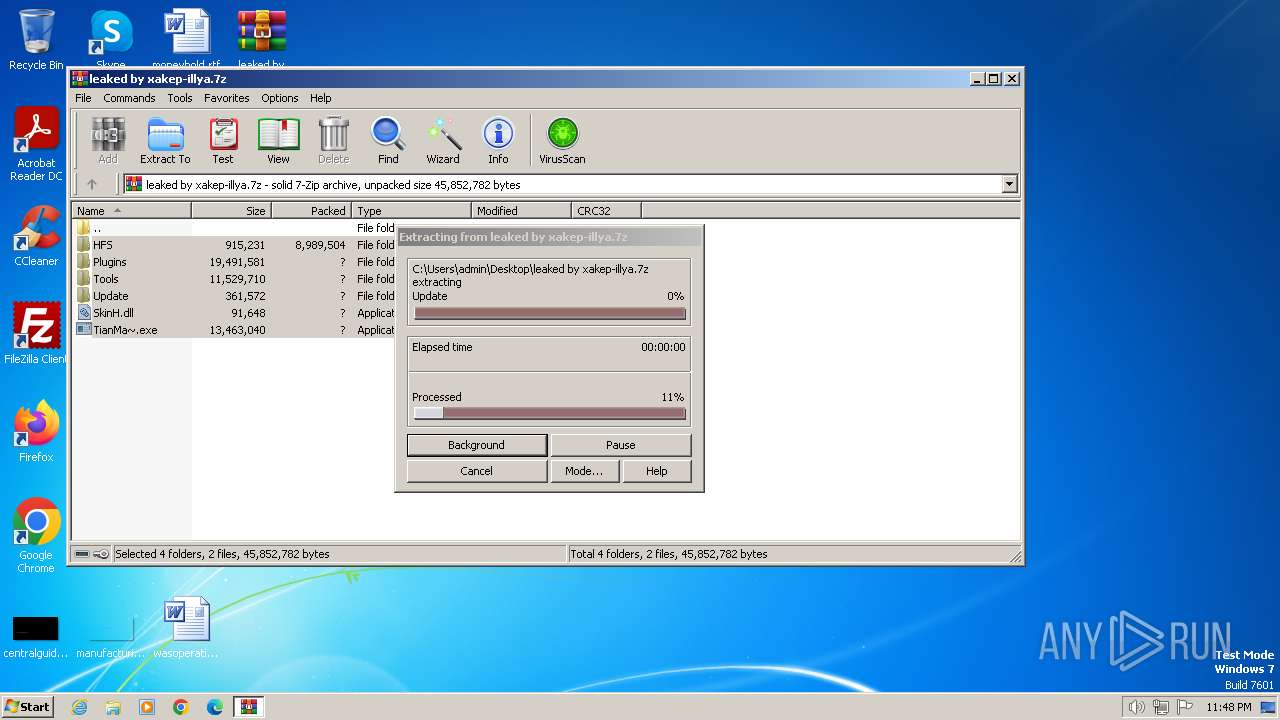
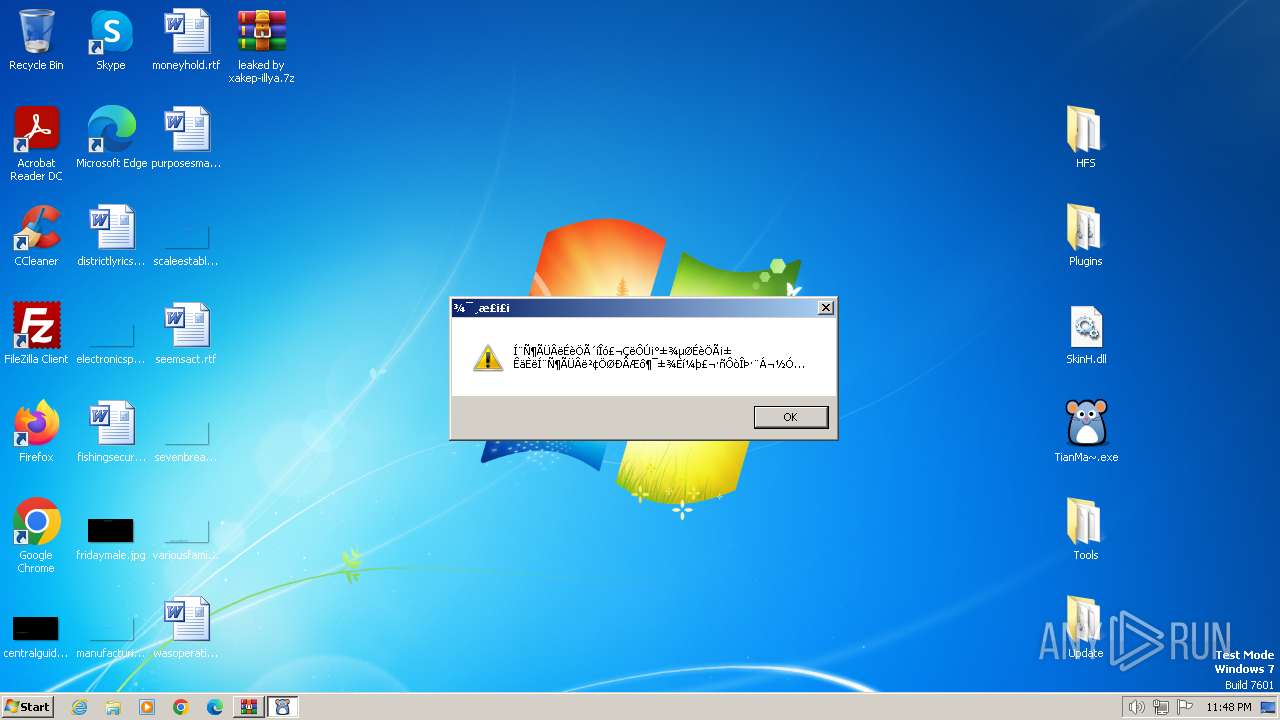
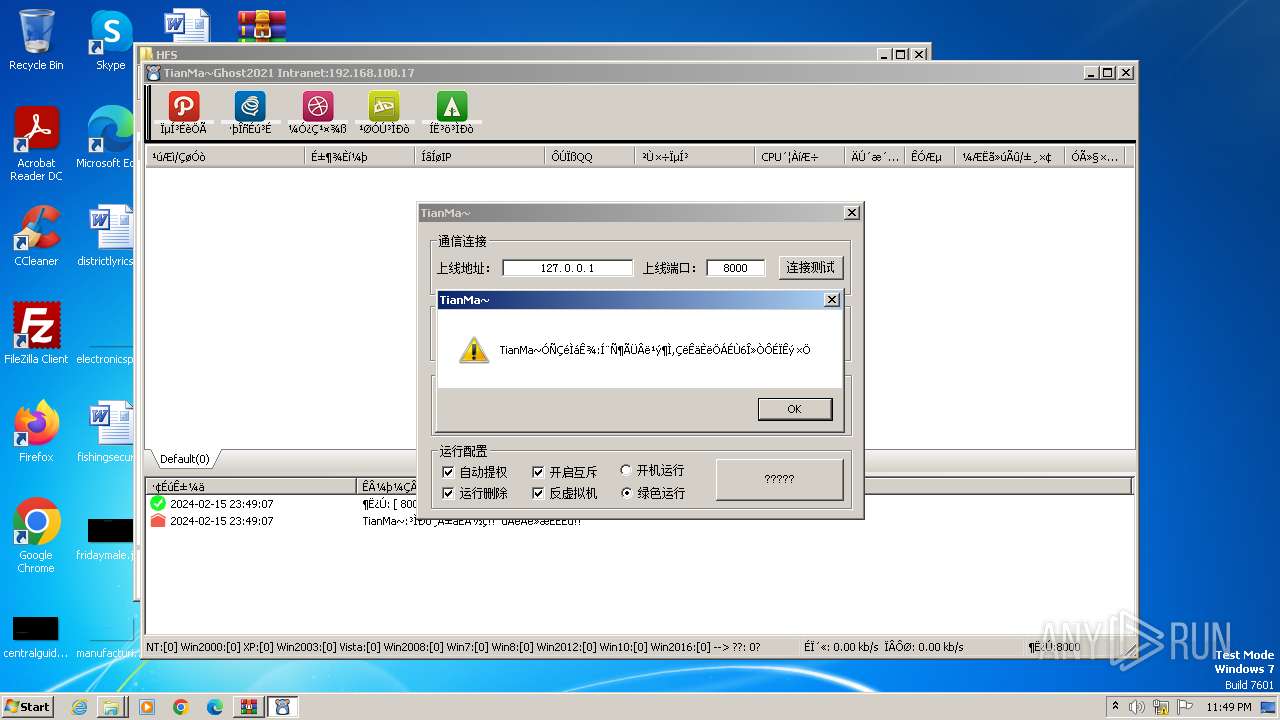
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1384)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1384)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 1384)
Reads security settings of Internet Explorer
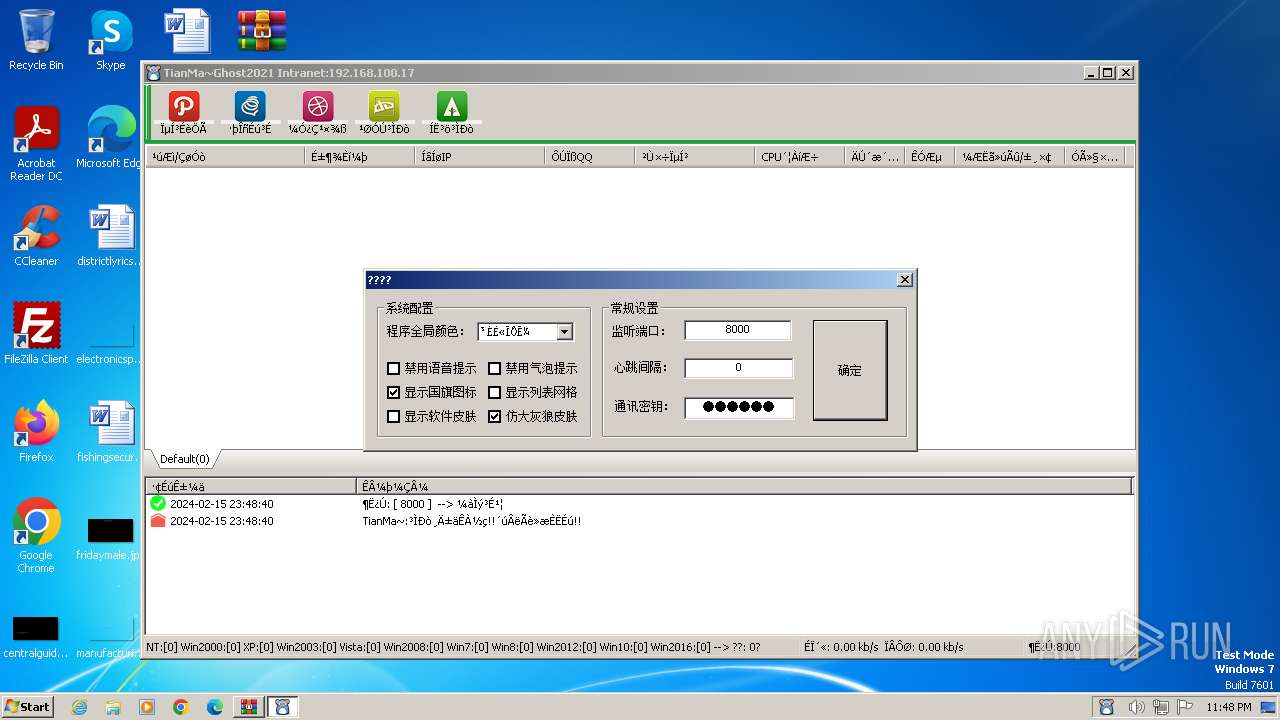
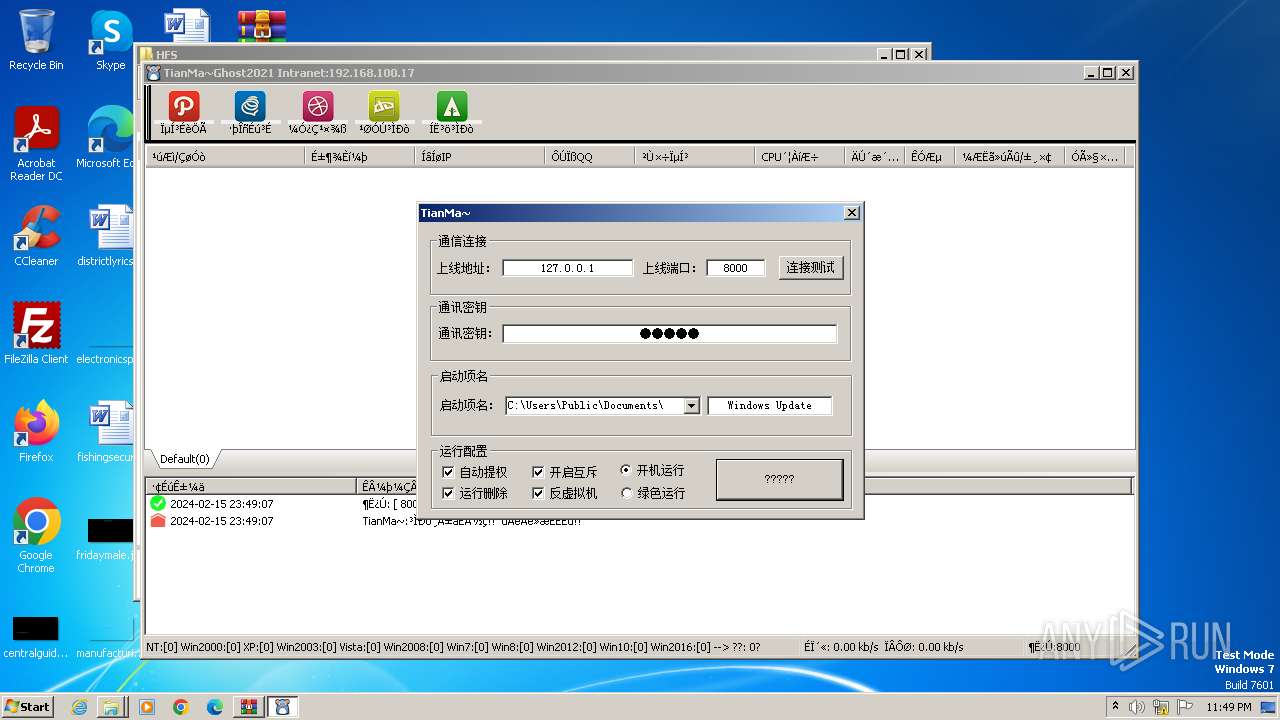
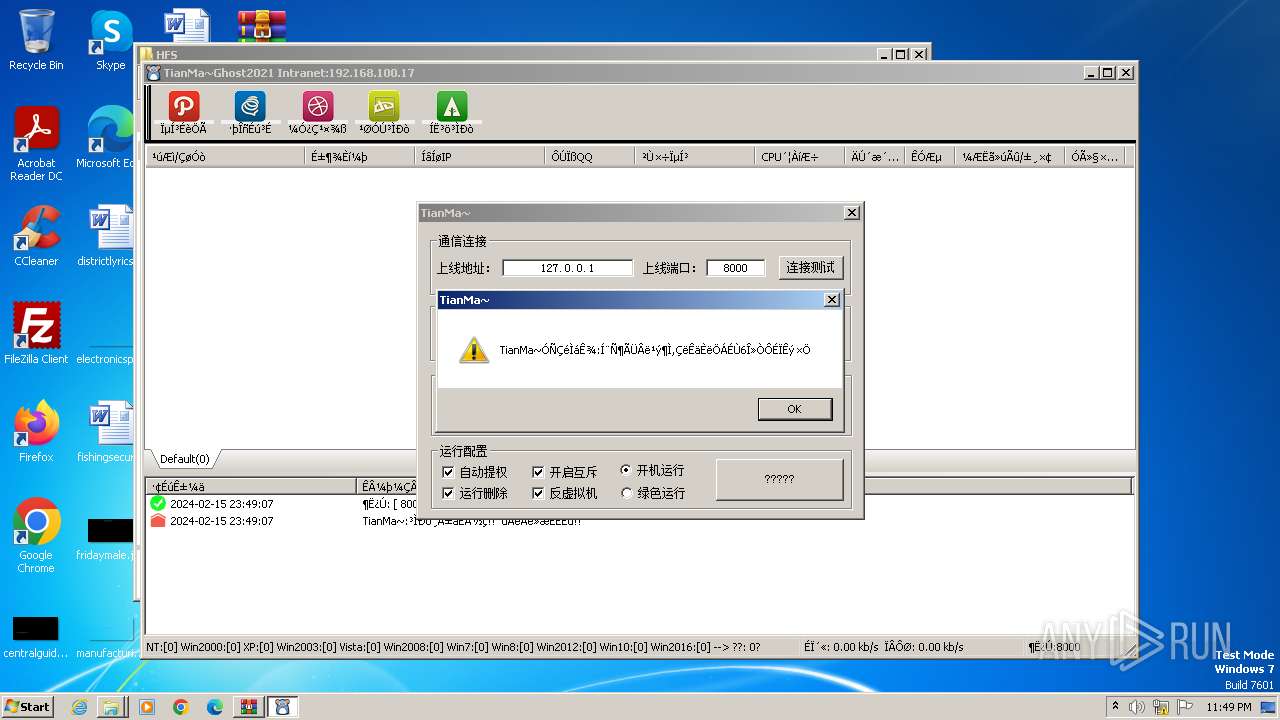
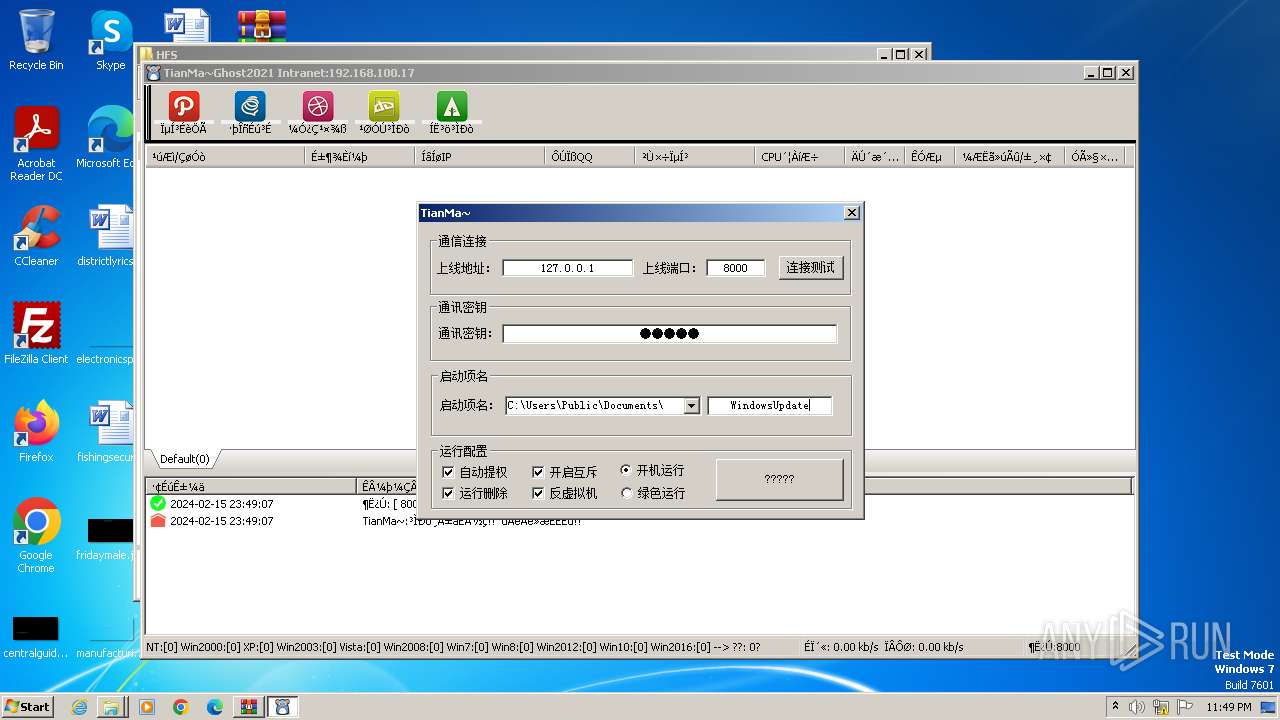
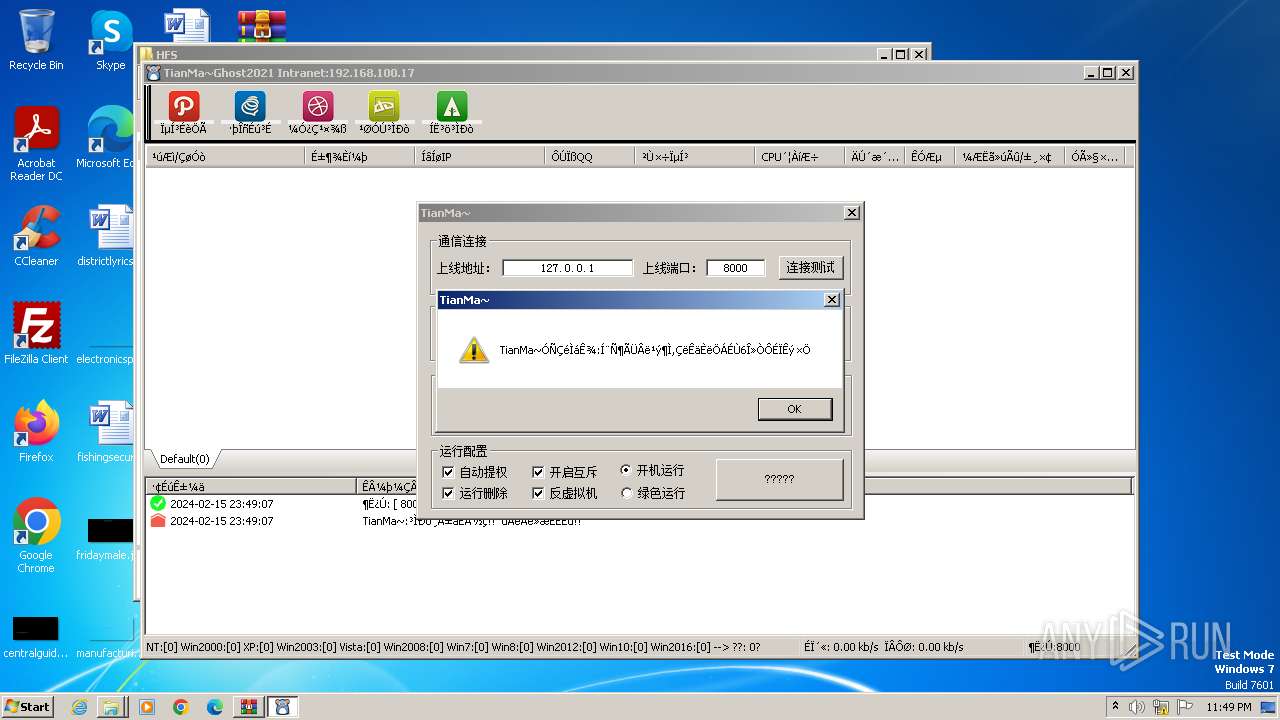
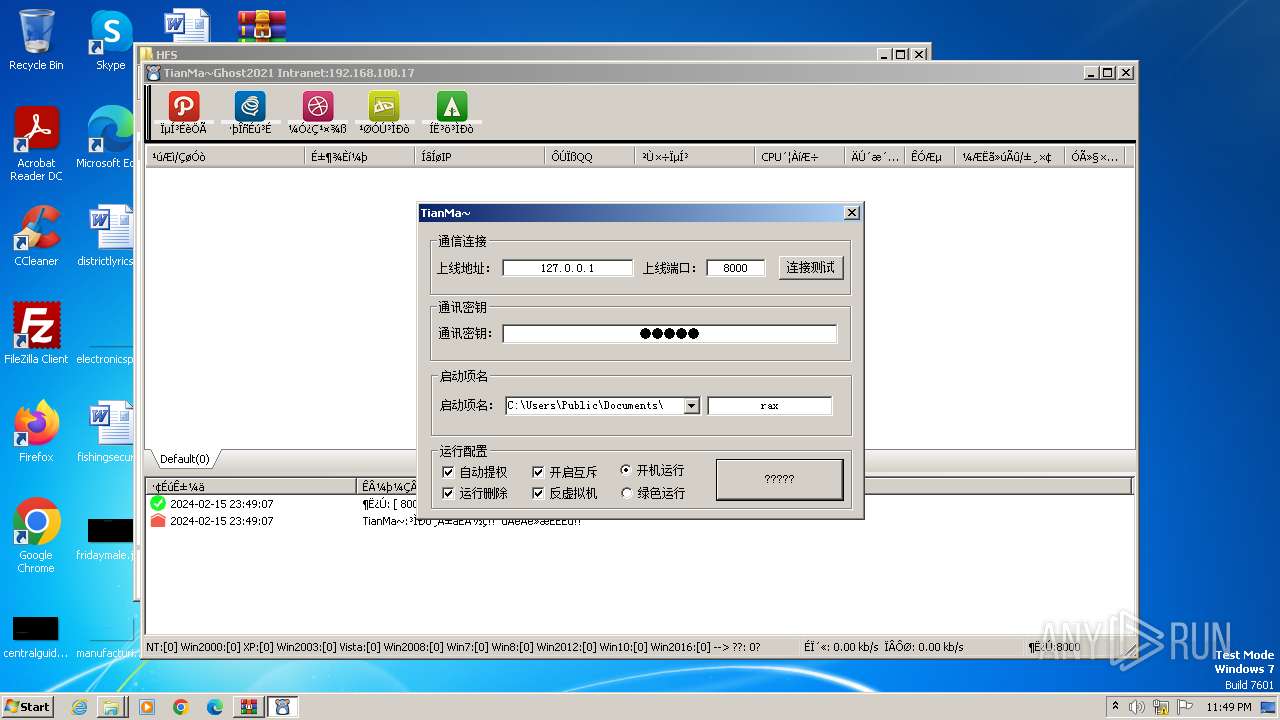
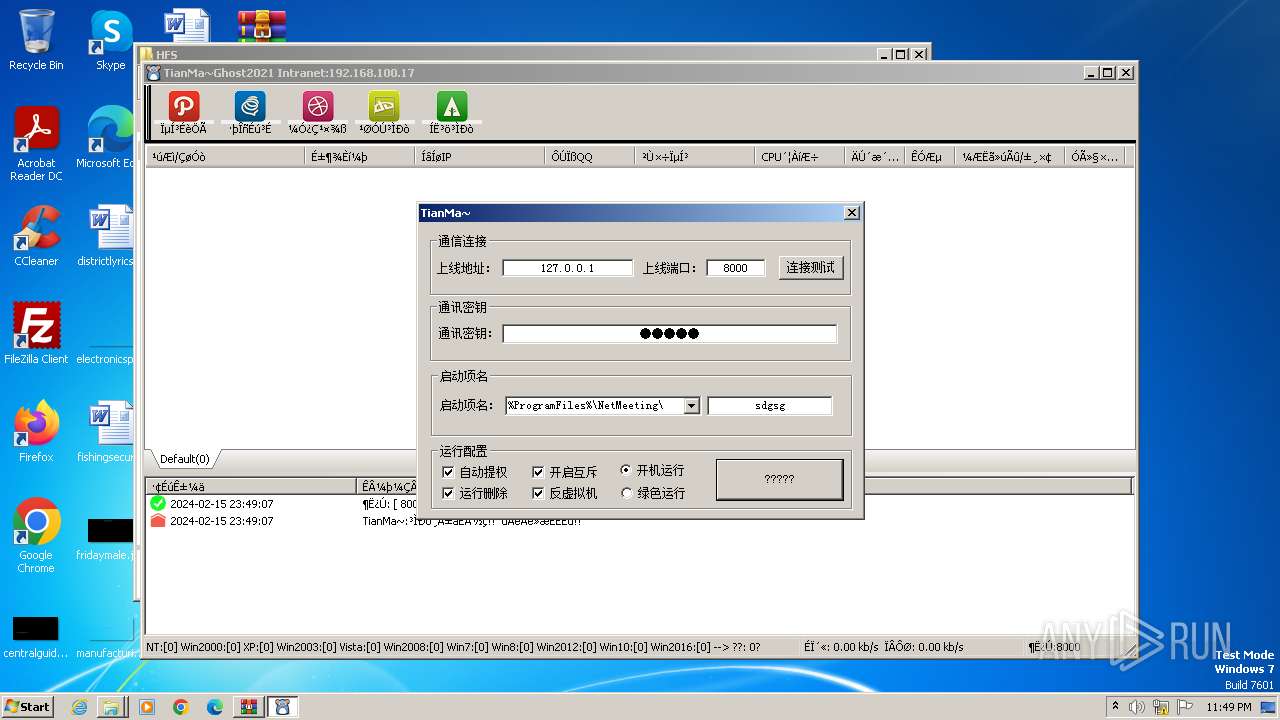
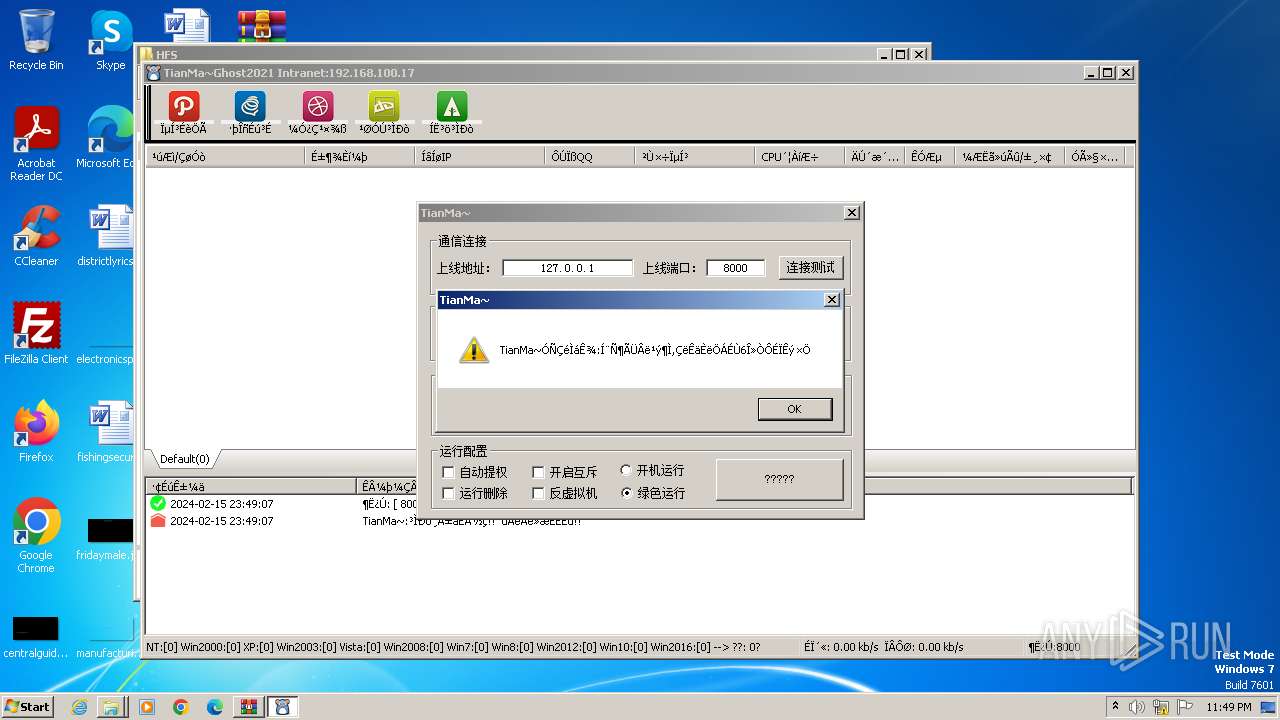
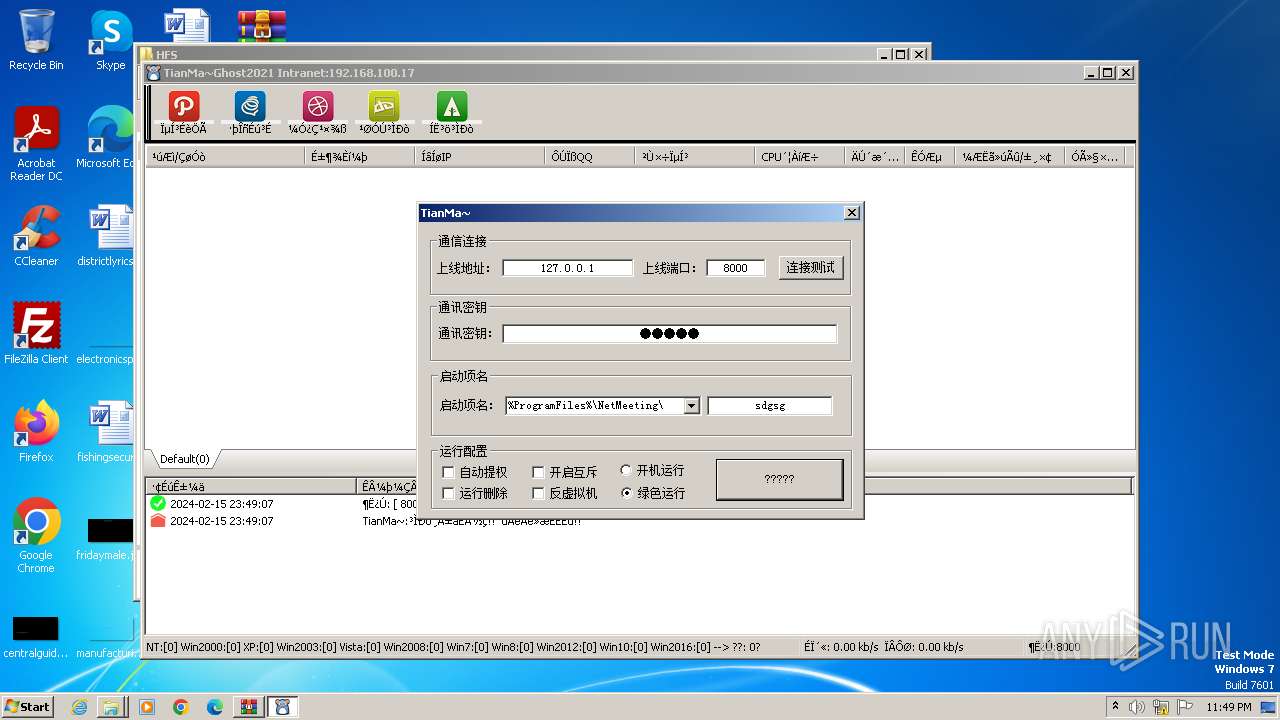
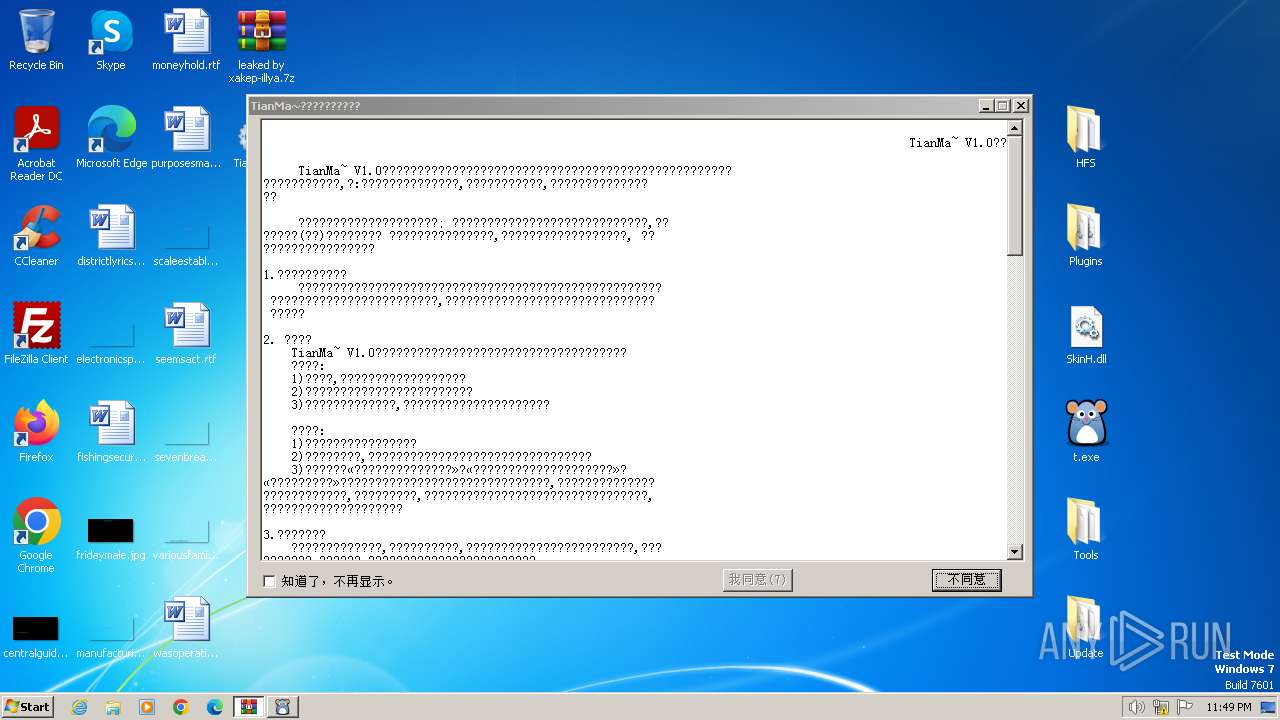
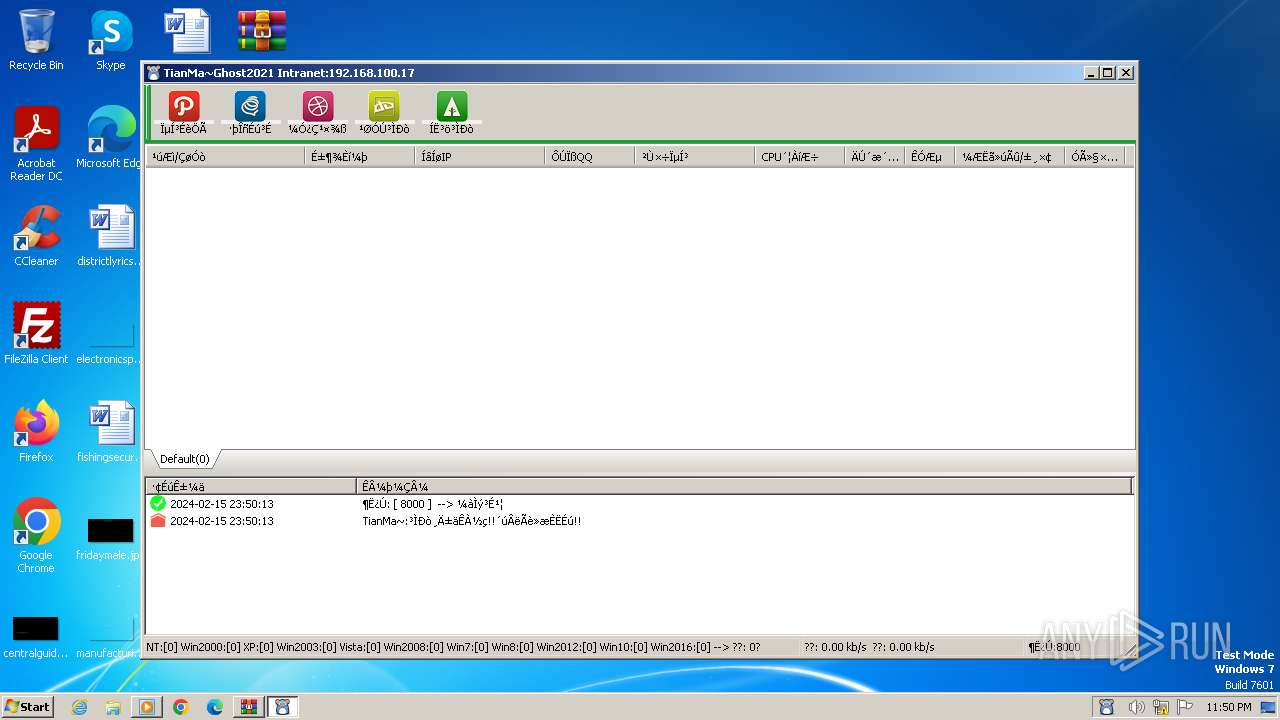
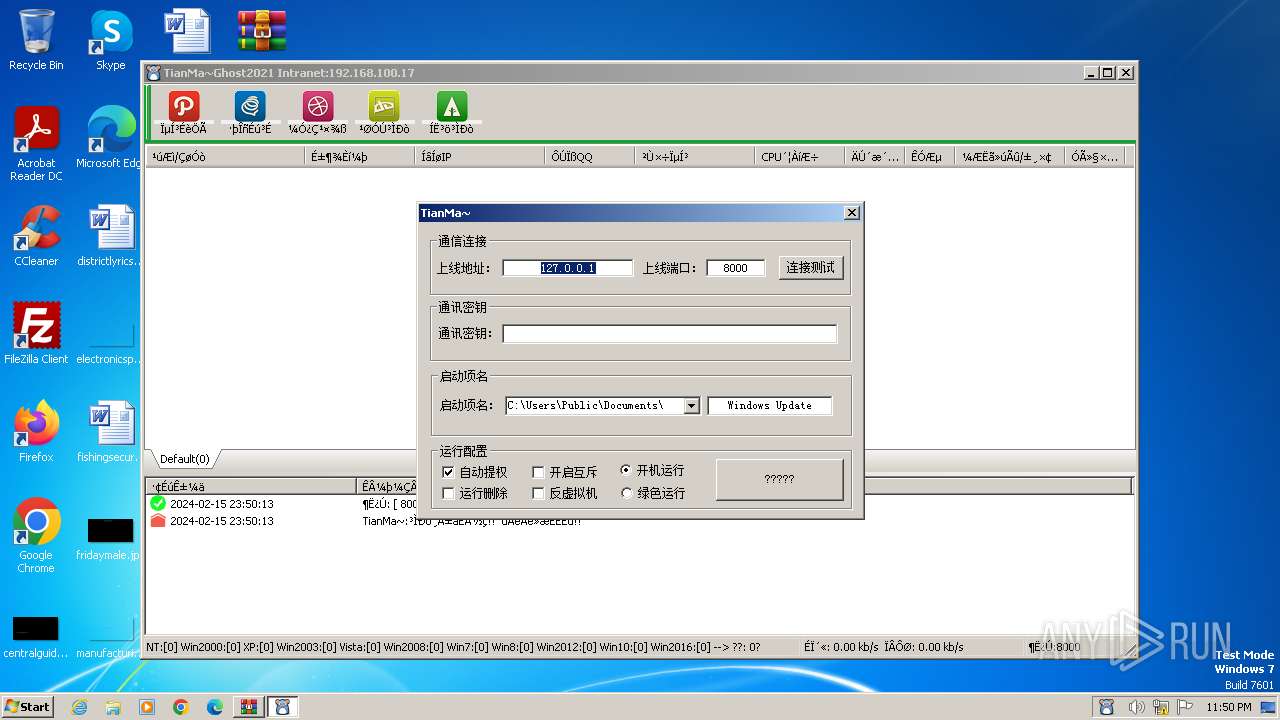
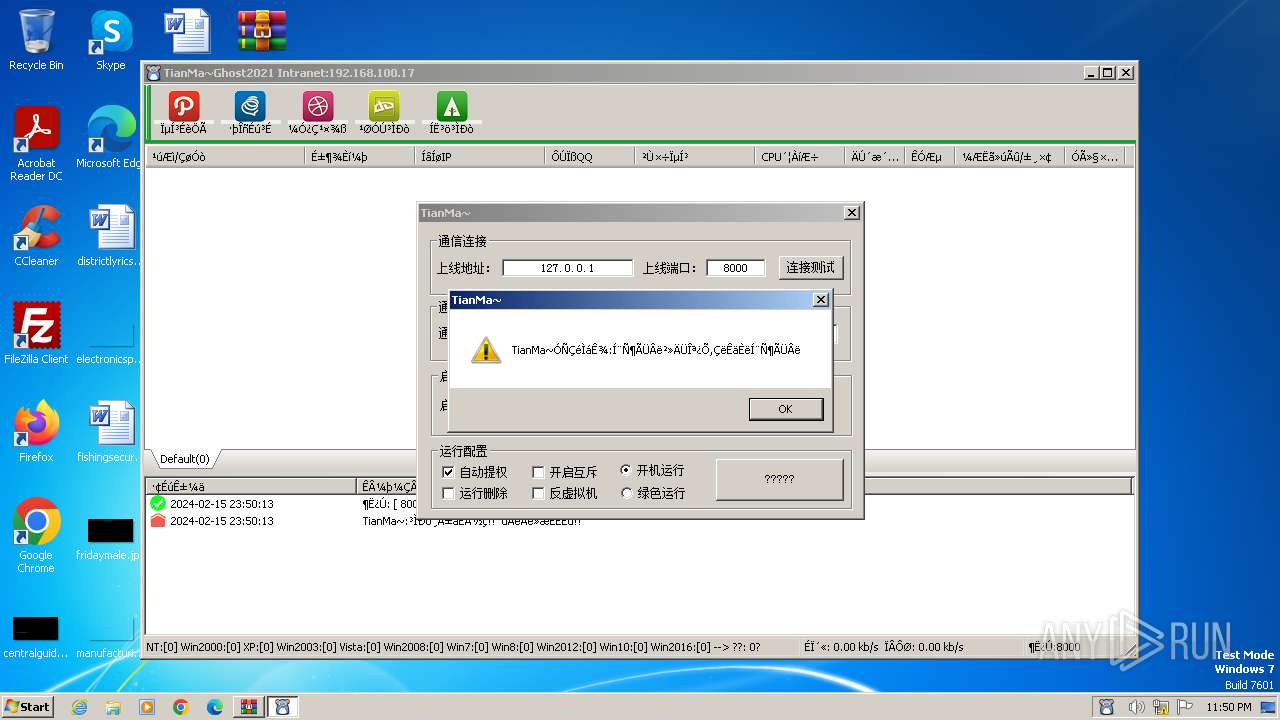
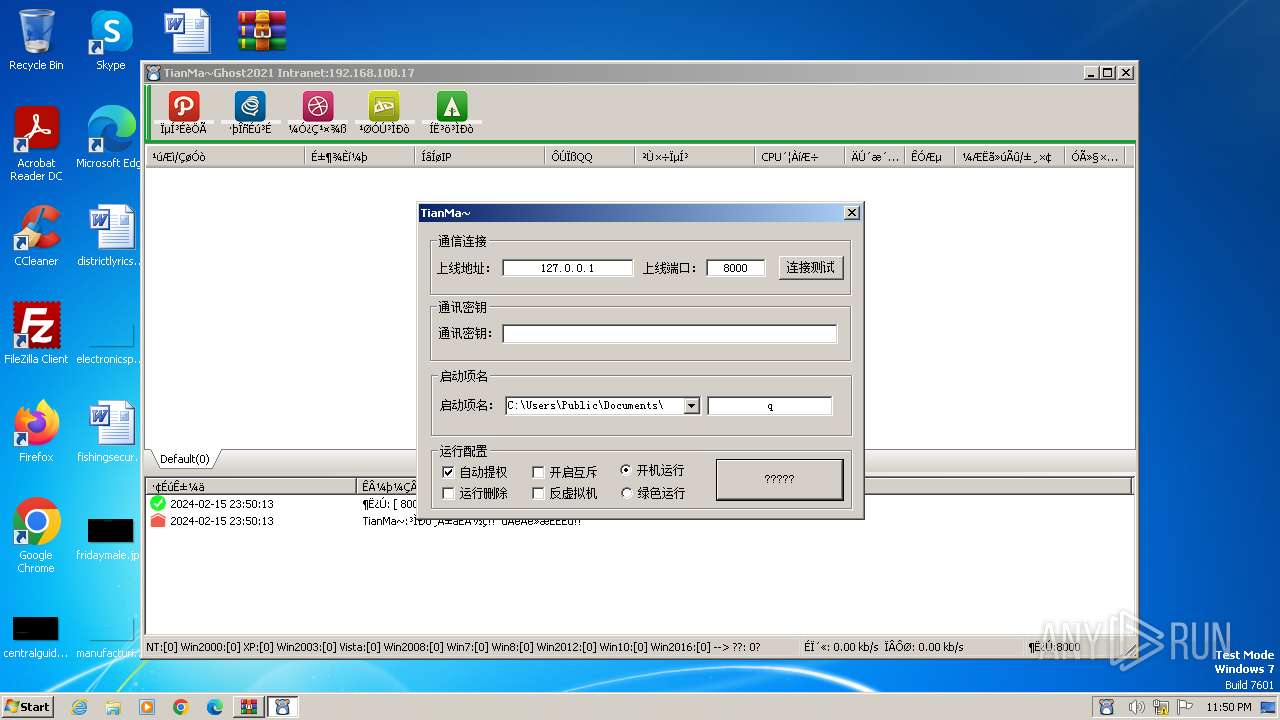
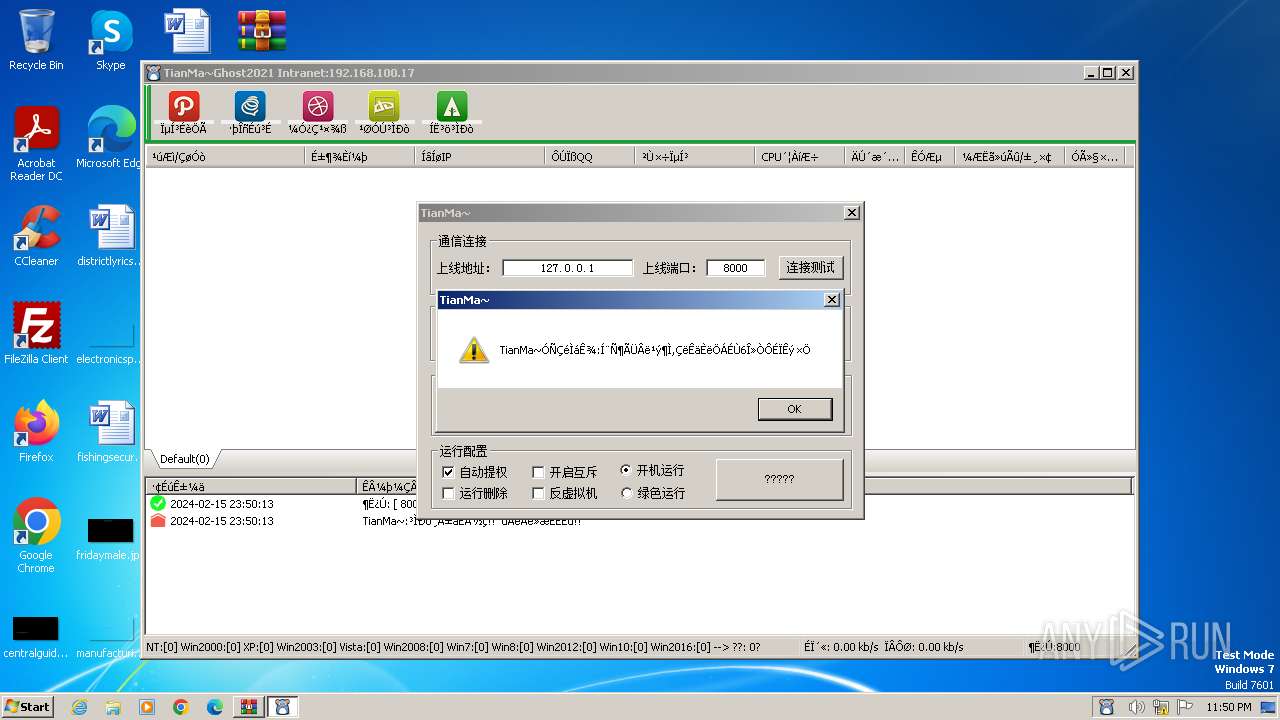
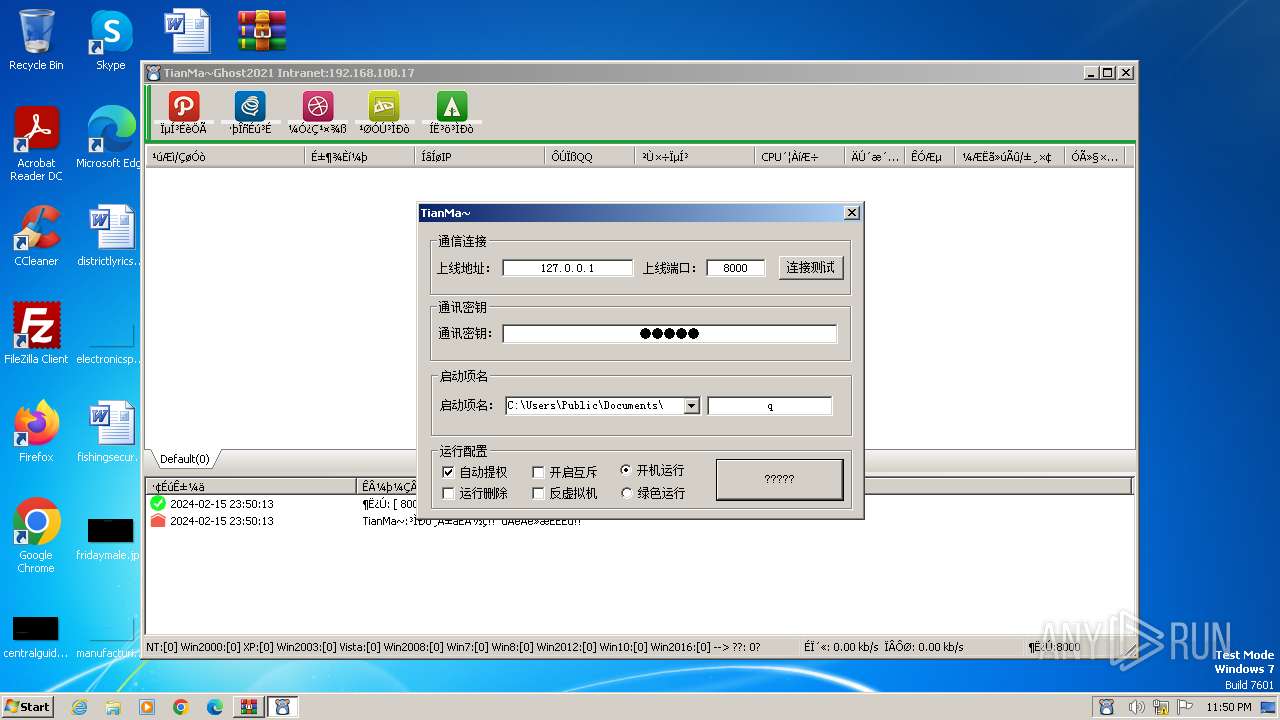
- TianMa~.exe (PID: 1492)
- t.exe (PID: 2592)
- TianMa~.exe (PID: 696)
Reads the Internet Settings
- TianMa~.exe (PID: 696)
- t.exe (PID: 2592)
- TianMa~.exe (PID: 1492)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3348)
- TianMa~.exe (PID: 696)
- wmpnscfg.exe (PID: 2960)
- TianMa~.exe (PID: 1492)
- t.exe (PID: 2592)
Checks supported languages
- wmpnscfg.exe (PID: 2960)
- TianMa~.exe (PID: 1492)
- wmpnscfg.exe (PID: 3348)
- TianMa~.exe (PID: 696)
- t.exe (PID: 2592)
Reads the computer name
- wmpnscfg.exe (PID: 3348)
- TianMa~.exe (PID: 1492)
- wmpnscfg.exe (PID: 2960)
- TianMa~.exe (PID: 696)
- t.exe (PID: 2592)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1384)
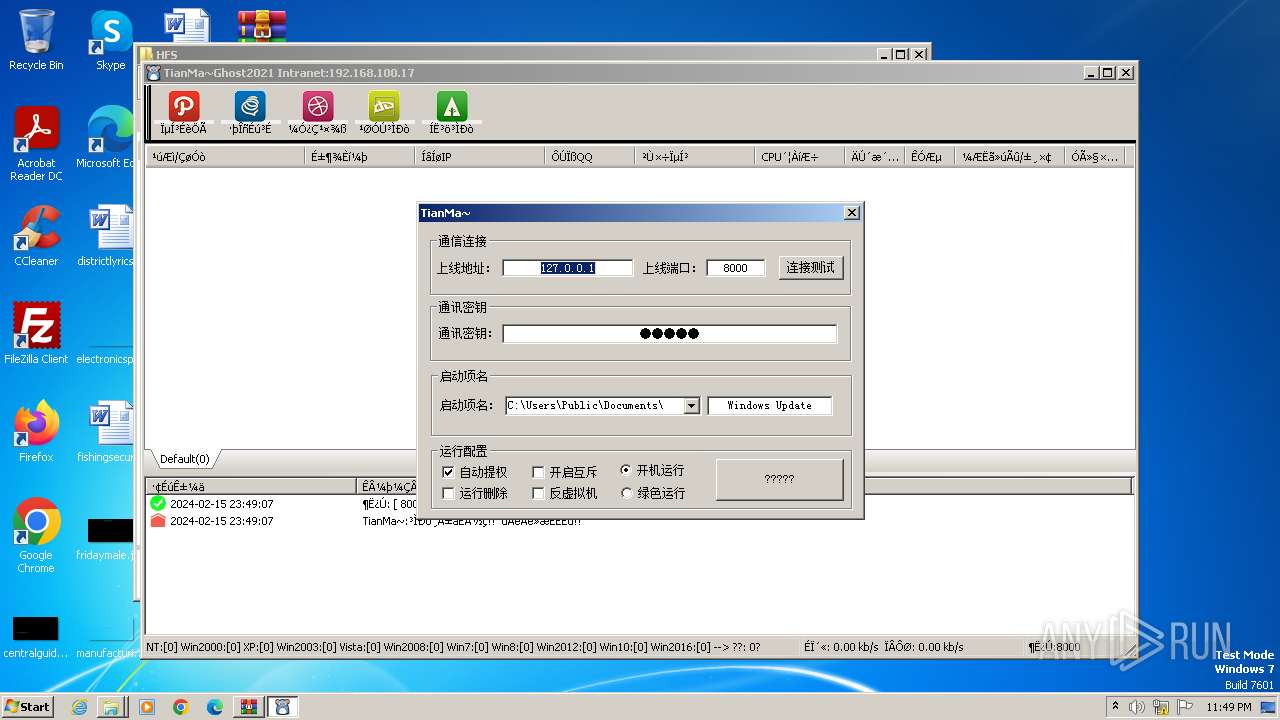
Checks proxy server information
- TianMa~.exe (PID: 1492)
- TianMa~.exe (PID: 696)
- t.exe (PID: 2592)
Reads the machine GUID from the registry
- TianMa~.exe (PID: 696)
- t.exe (PID: 2592)
- TianMa~.exe (PID: 1492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
49
Monitored processes
6
Malicious processes
0
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
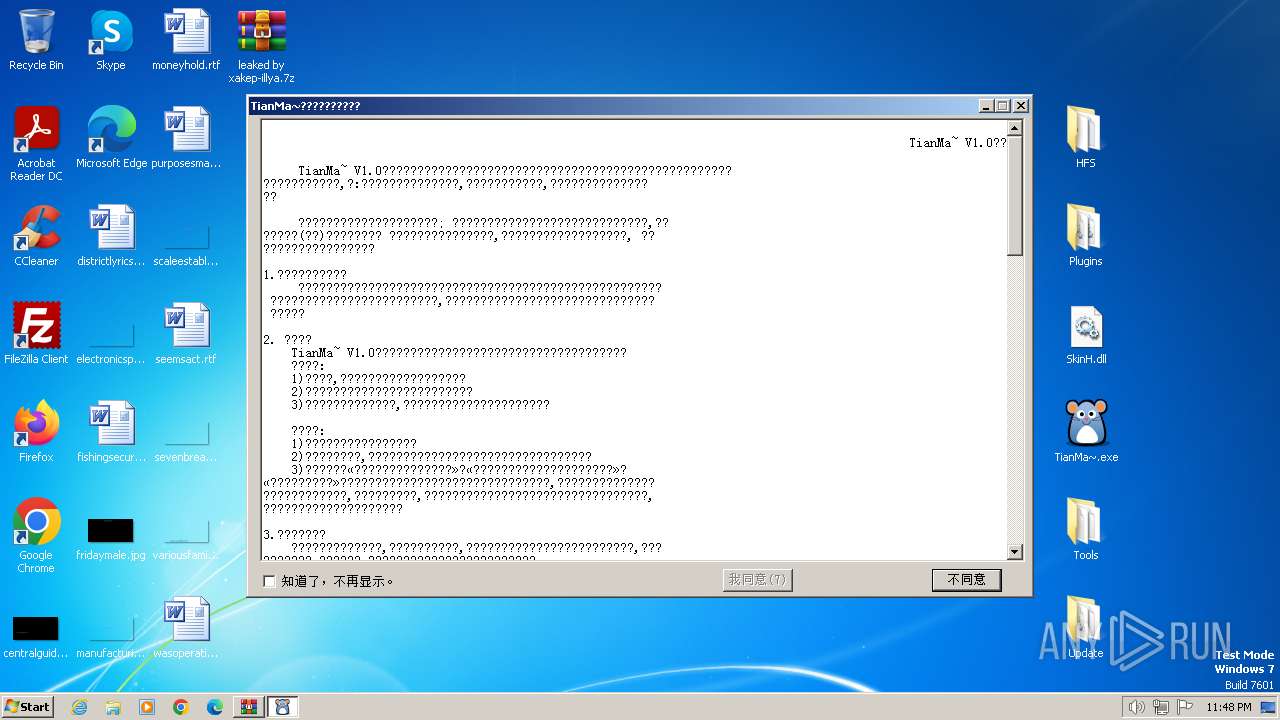
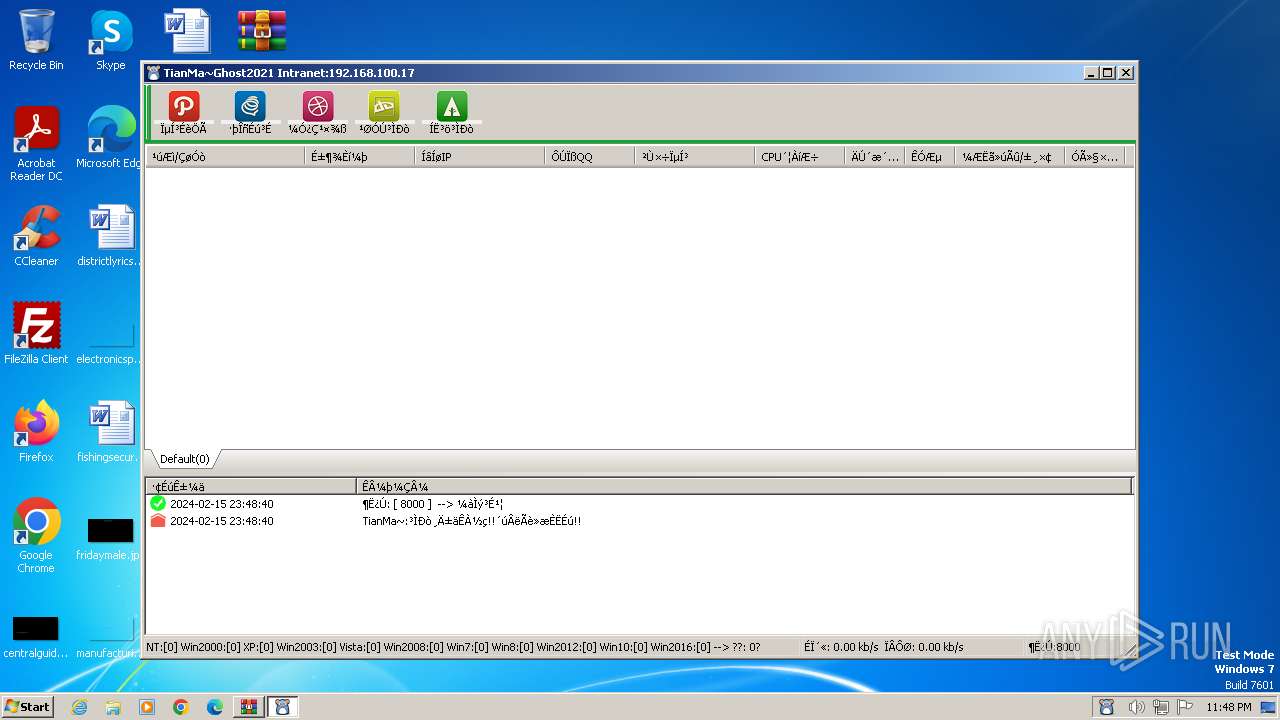
| 696 | "C:\Users\admin\Desktop\TianMa~.exe" | C:\Users\admin\Desktop\TianMa~.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: TianMa~程序改变世界 代码描绘人生! Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 1384 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\leaked by xakep-illya.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1492 | "C:\Users\admin\Desktop\TianMa~.exe" | C:\Users\admin\Desktop\TianMa~.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: TianMa~程序改变世界 代码描绘人生! Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2592 | "C:\Users\admin\Desktop\t.exe" | C:\Users\admin\Desktop\t.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: TianMa~程序改变世界 代码描绘人生! Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2960 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3348 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 106
Read events
4 947
Write events
120
Delete events
39
Modification events
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\leaked by xakep-illya.7z | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
22
Suspicious files
3
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
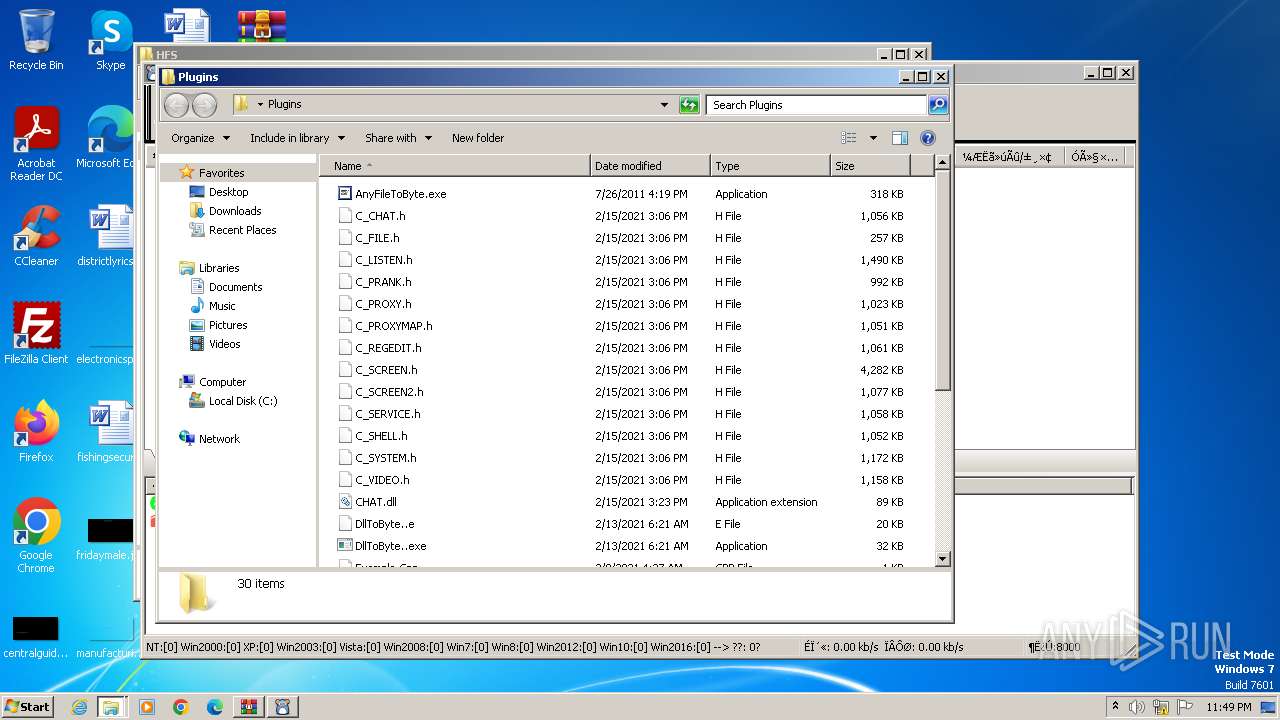
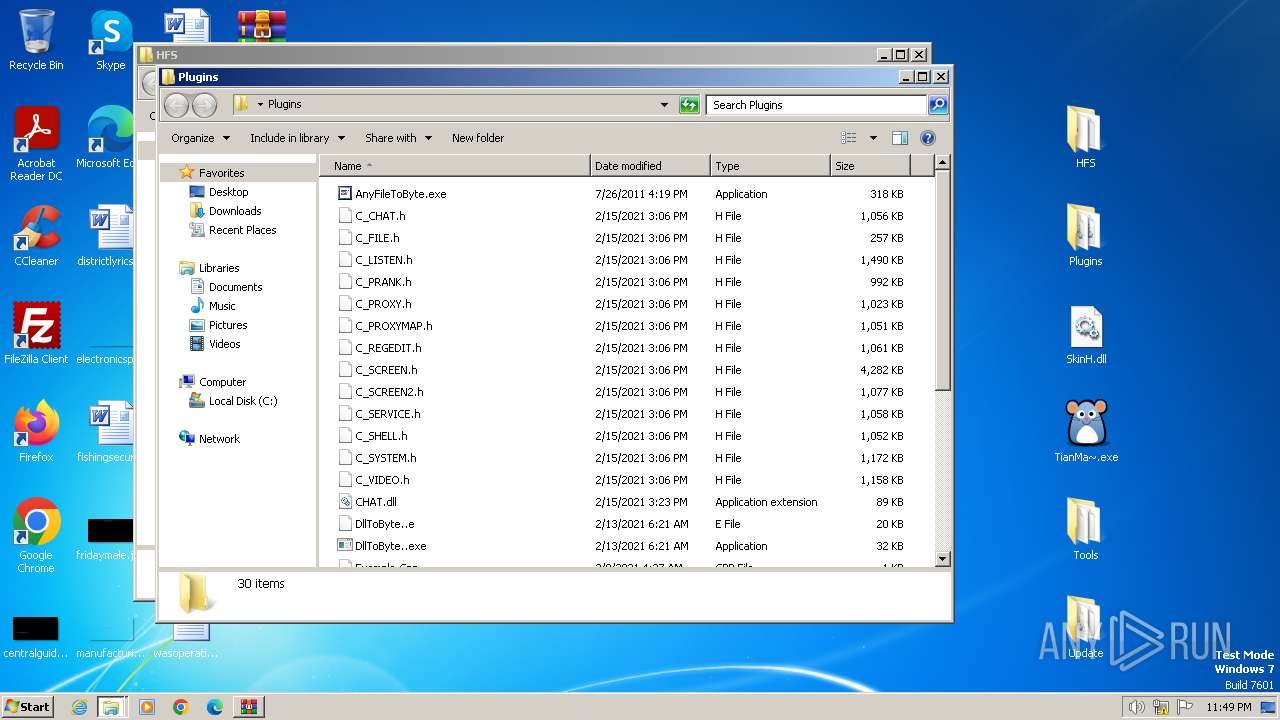
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.37679\Plugins\C_SCREEN.h | — | |
MD5:— | SHA256:— | |||
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.37679\Tools\QQwry.dat | — | |
MD5:— | SHA256:— | |||
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.37679\Plugins\C_PRANK.h | text | |
MD5:94B1C8A0762F00F5422531451BEE5841 | SHA256:9A6CD9C3C899B3B77D3DB1BAC1A8AE5642988C7E16F08E98F1FAAB95ABE0063C | |||
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.37679\HFS\hfs.ips.txt | text | |
MD5:9B3DE729FB9E735152EBA9C76E0A211A | SHA256:999A3D461D1628A91CBE0BA27D4A88CAA82DB6A1D3490A06318EF9CAB65A321A | |||
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.37679\Plugins\C_CHAT.h | text | |
MD5:6FDDF08B42AE72C2D3B6B1B19FA5BA93 | SHA256:83EC04A4935FC6E1BA1F76BF9851869E73654482EE4218476F5E500EF6FC00B1 | |||
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.37679\Plugins\C_SCREEN2.h | text | |
MD5:441A3AFA363FC713C46AEB7273CE2DB0 | SHA256:37BB3DE9D80E0CBBA12EB6FEC27E42D5E7A420B19484CE044E33B55AFA9B682F | |||
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.37679\Plugins\C_PROXY.h | text | |
MD5:D4E30D320999B859C3E0CC9EDEC61782 | SHA256:C4149210087EB05519C2B1511E83048A2EA71E68E34015968101244E72016B9C | |||
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.37679\Plugins\C_REGEDIT.h | text | |
MD5:CFA18B22D61C2E02B91A747B7B17EDBD | SHA256:76D003045FAB7E10447FA24E10947F0AA18B92E13EC6DD84B91FDC622C362499 | |||
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.37679\Plugins\C_LISTEN.h | text | |
MD5:4644A019B87E4A25162F7F5153D76657 | SHA256:CE2CCDB046648CFDC58C543E171FCB604C85EFFEE65FA03854FA97F3F5FD6FE6 | |||
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.37679\Tools\Encode.e | binary | |
MD5:8A87CD9B1CF6068752C4E60A671D1EE3 | SHA256:08C3B55936F5E7963E92C1A90D77EB66F3CA171FE737375DCDFDAFDBEE8E6655 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
15
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Check Domain in DNS Lookup (whois .pconline .com .cn) |
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Check Domain in DNS Lookup (whois .pconline .com .cn) |
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Check Domain in DNS Lookup (whois .pconline .com .cn) |
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Check Domain in DNS Lookup (whois .pconline .com .cn) |
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Check Domain in DNS Lookup (whois .pconline .com .cn) |
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Check Domain in DNS Lookup (whois .pconline .com .cn) |
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Check Domain in DNS Lookup (whois .pconline .com .cn) |
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Check Domain in DNS Lookup (whois .pconline .com .cn) |
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Check Domain in DNS Lookup (whois .pconline .com .cn) |
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Check Domain in DNS Lookup (whois .pconline .com .cn) |