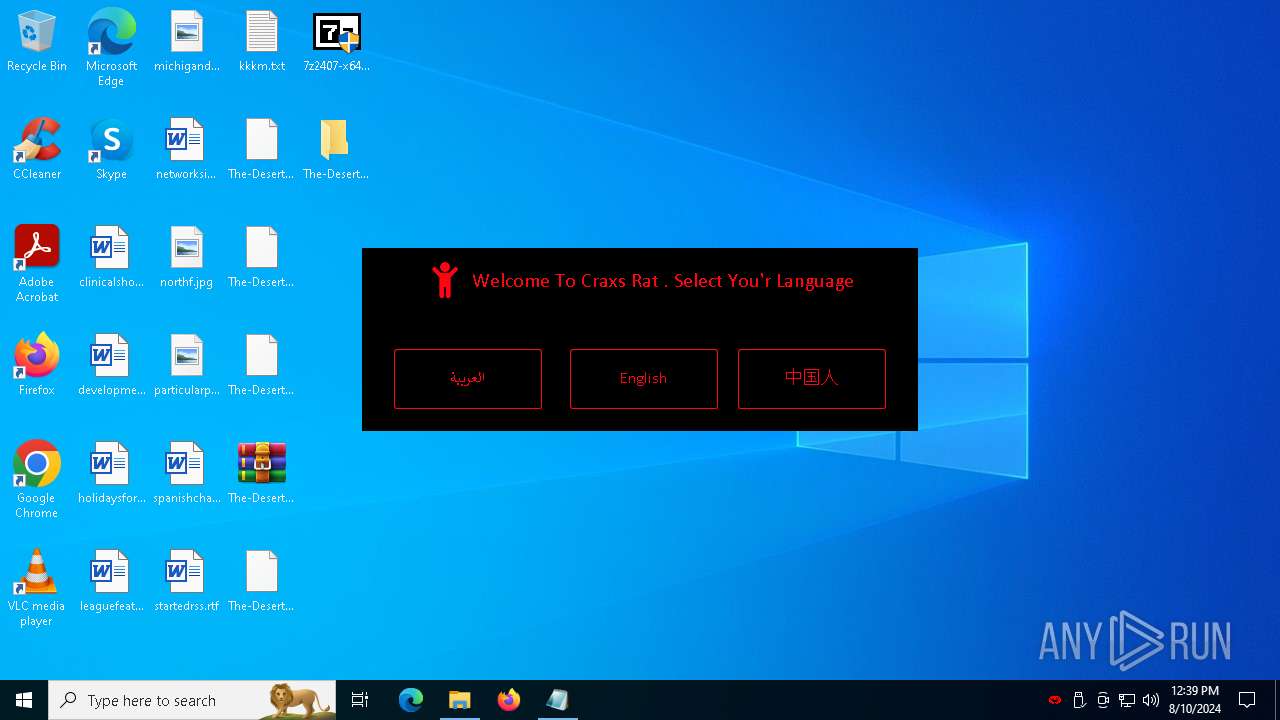
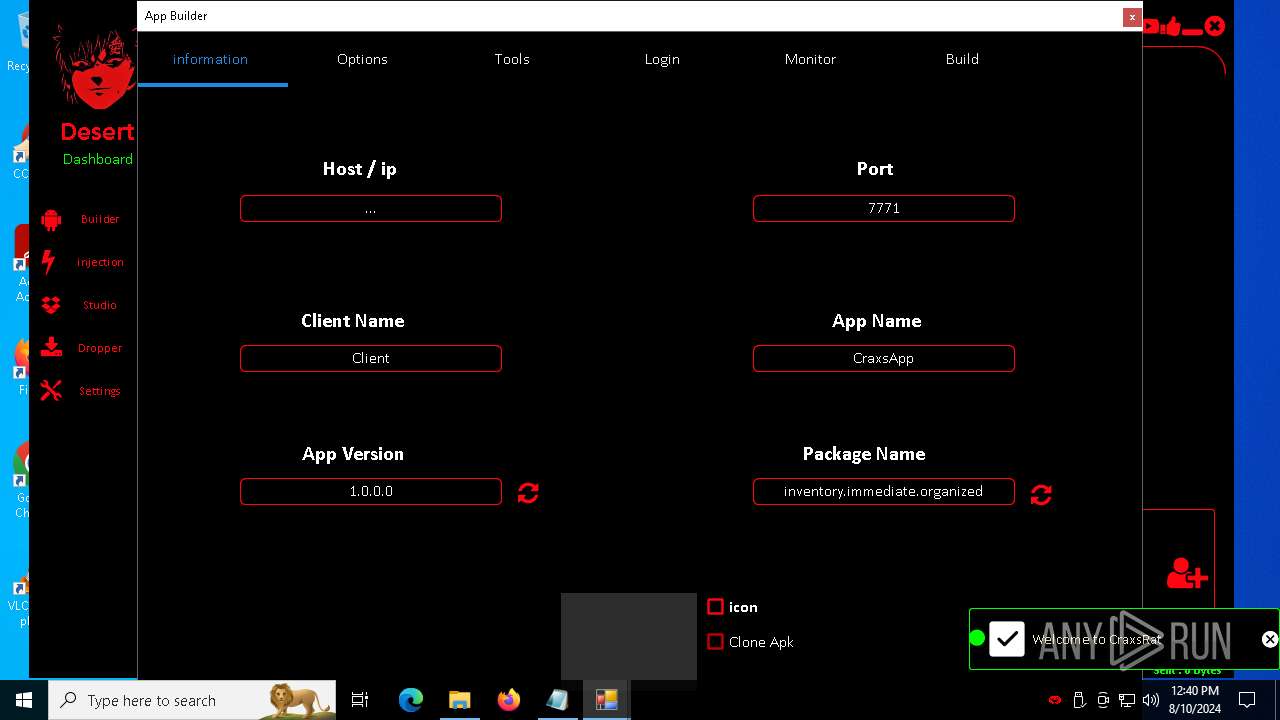
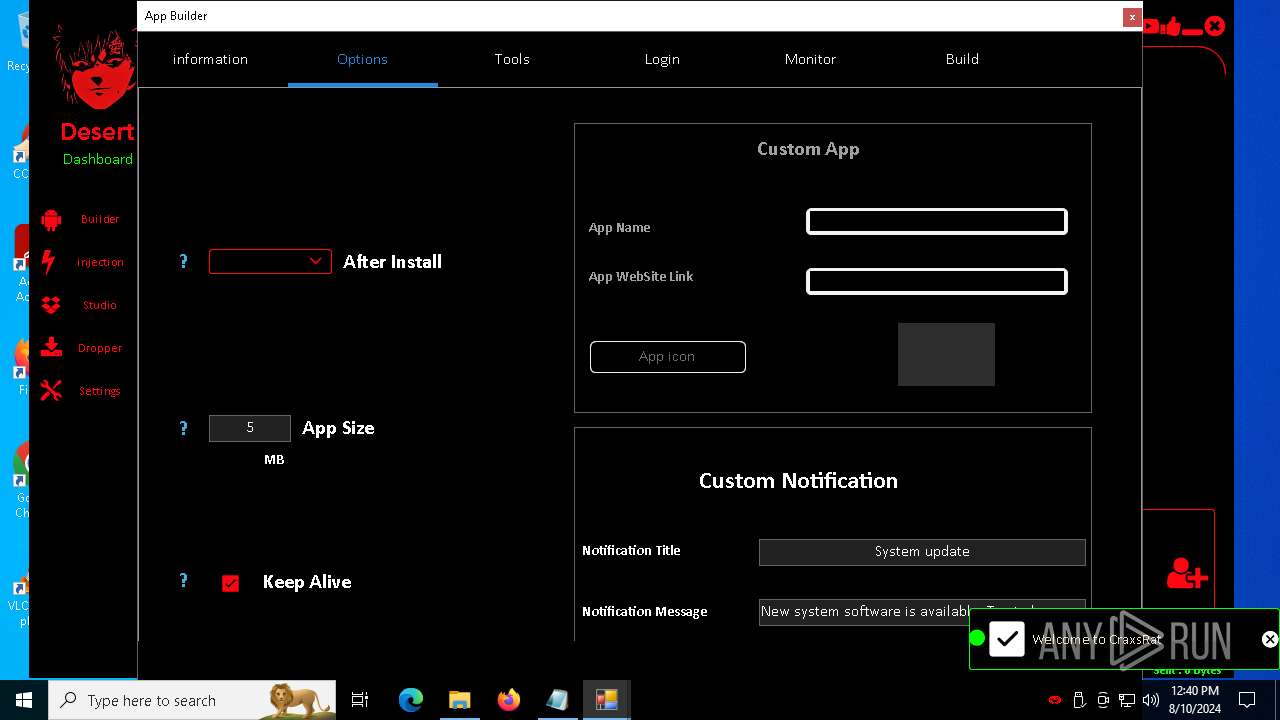
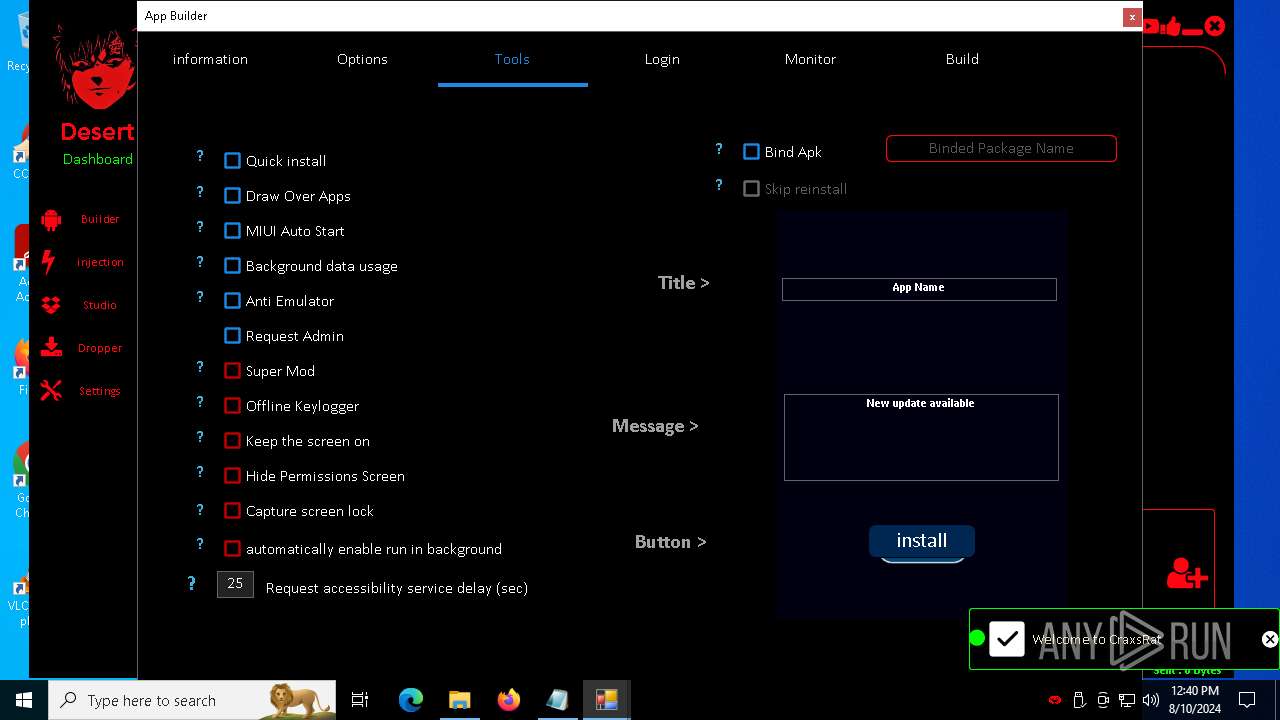
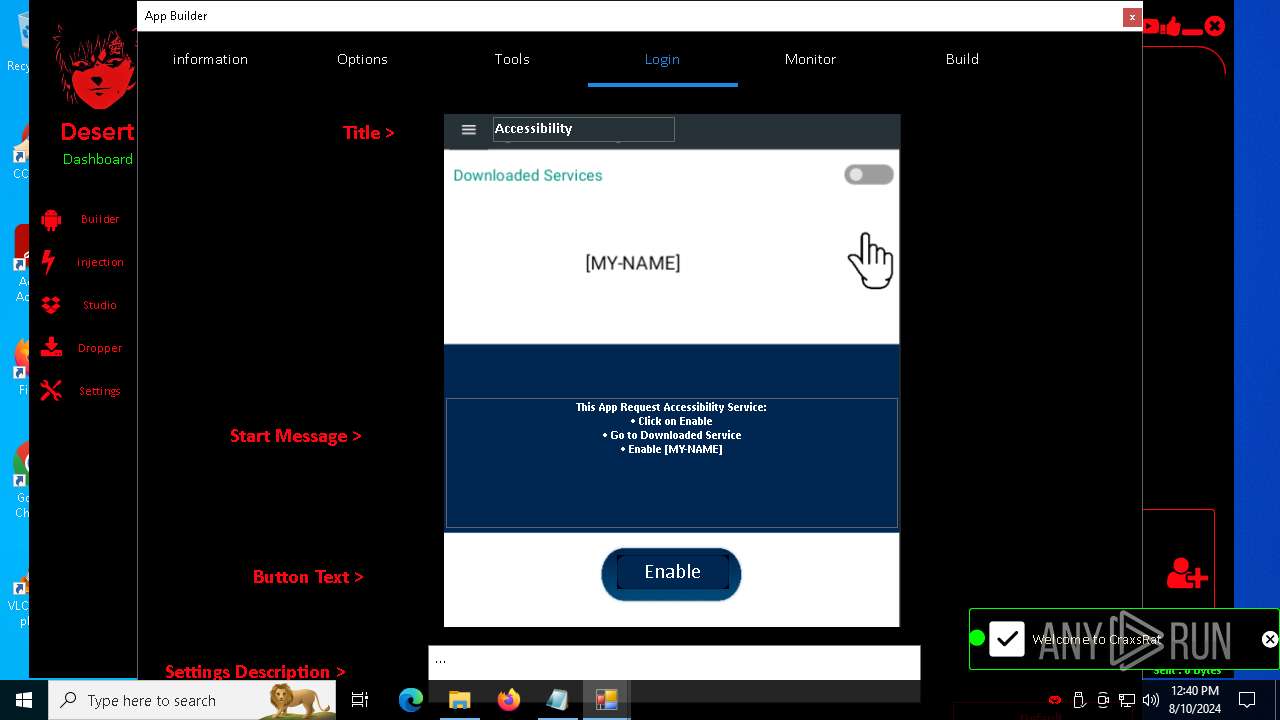
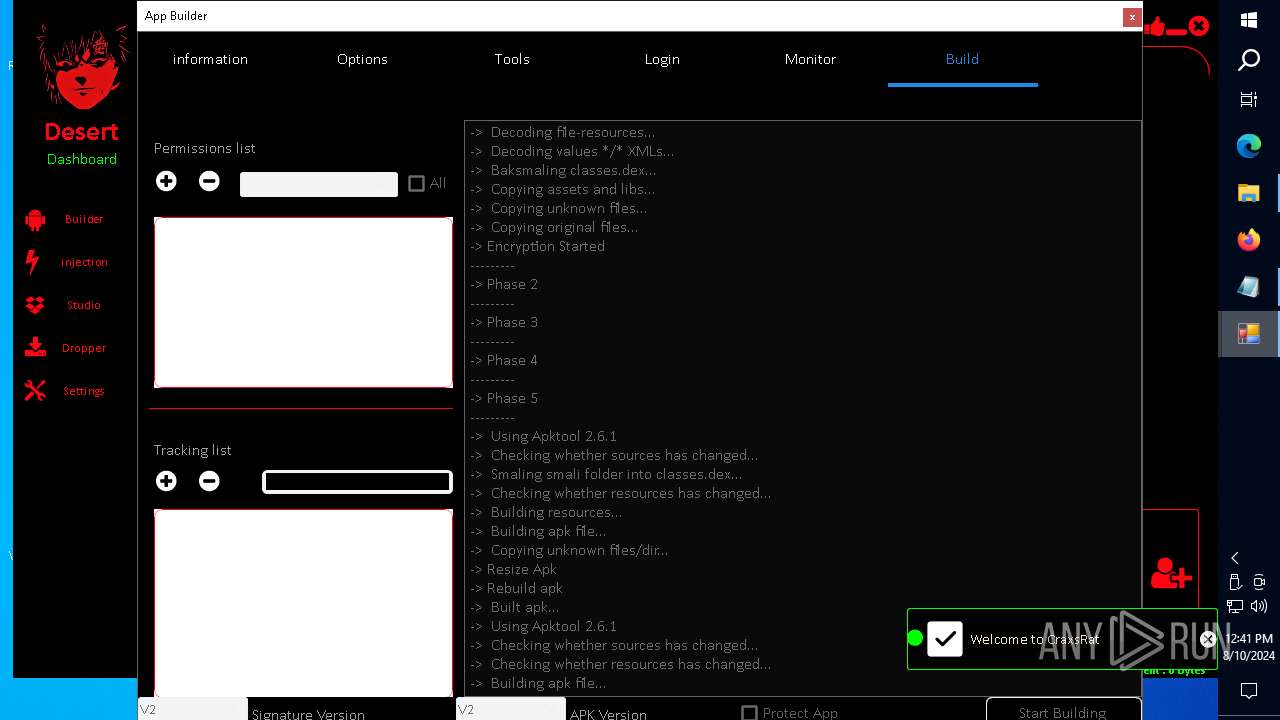
| File name: | kkkm.txt |
| Full analysis: | https://app.any.run/tasks/f33a1bd7-220b-460a-af0b-f9cd282731a4 |
| Verdict: | Malicious activity |
| Analysis date: | August 10, 2024, 12:37:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 0BF5D291252105BC6049E3DE1BD201E0 |
| SHA1: | 1EA585526C73535B160BFEAA9A1A0C3CF5E3D059 |
| SHA256: | 46391FA27B4DE3382B70ED228F45C70805B40716748BFE89323782C10F450129 |
| SSDEEP: | 3:YI:l |
MALICIOUS
No malicious indicators.SUSPICIOUS
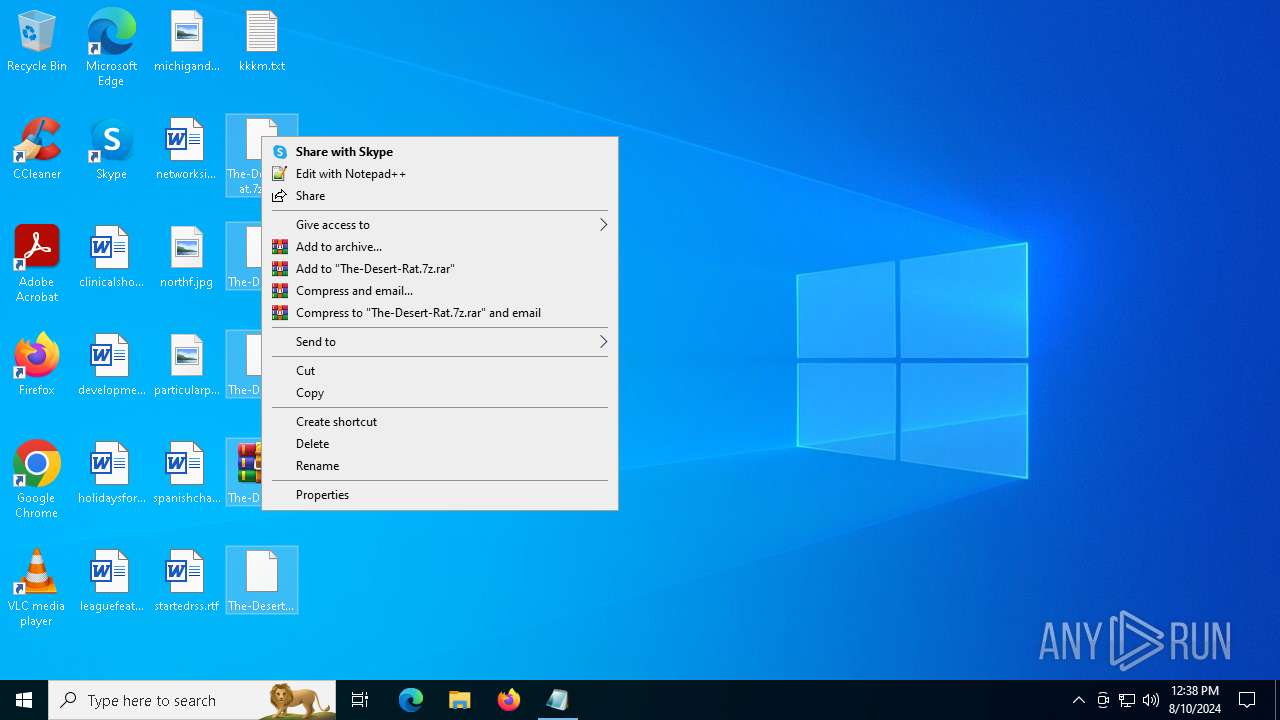
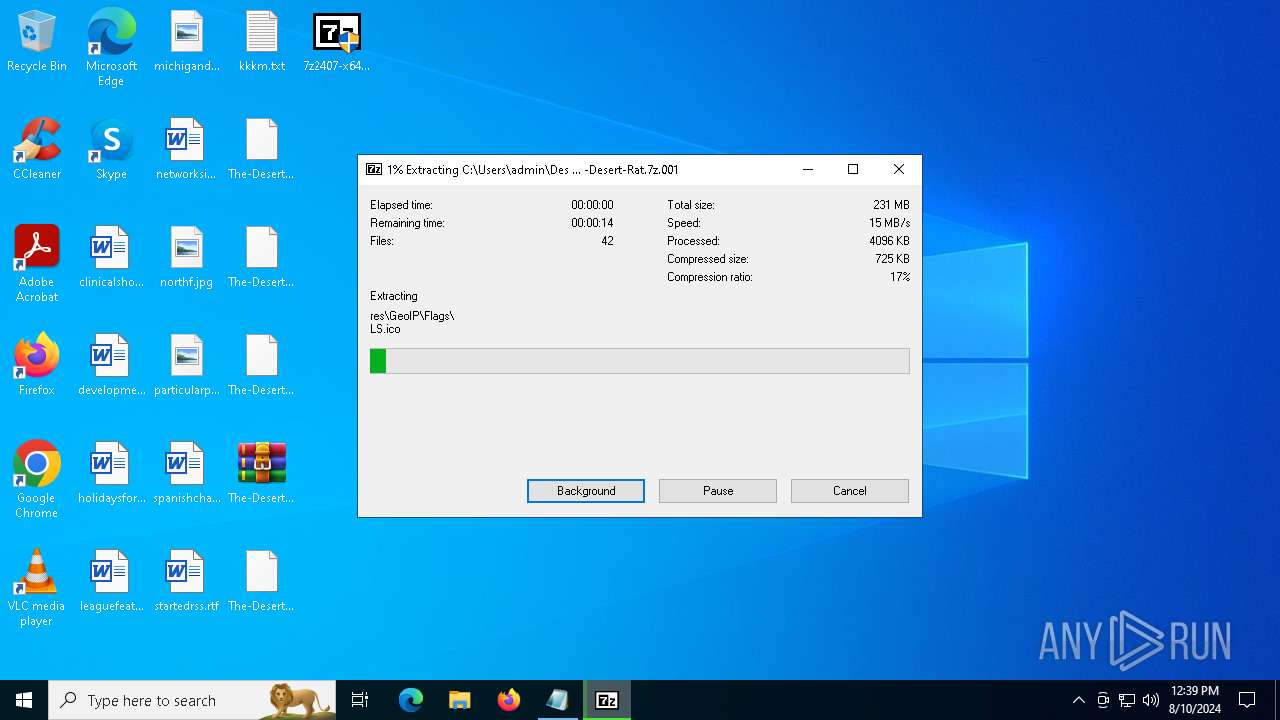
Drops the executable file immediately after the start
- 7z2407-x64.exe (PID: 300)
- 7zG.exe (PID: 6648)
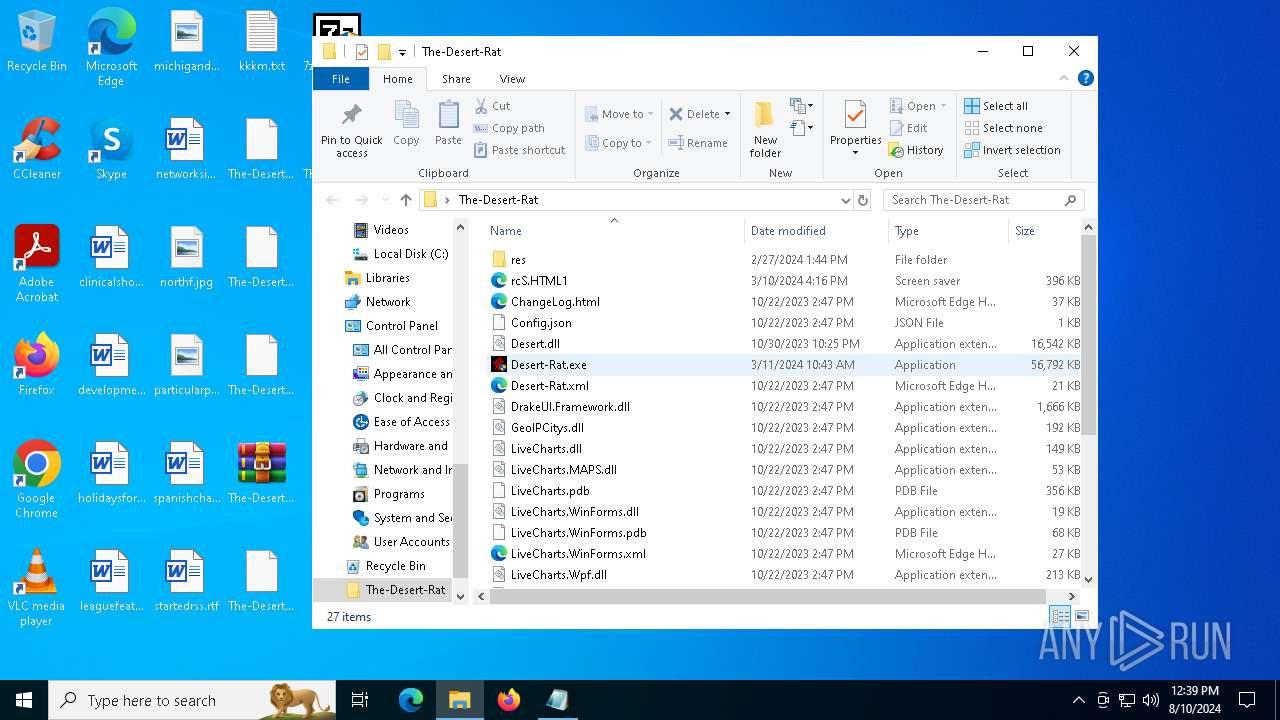
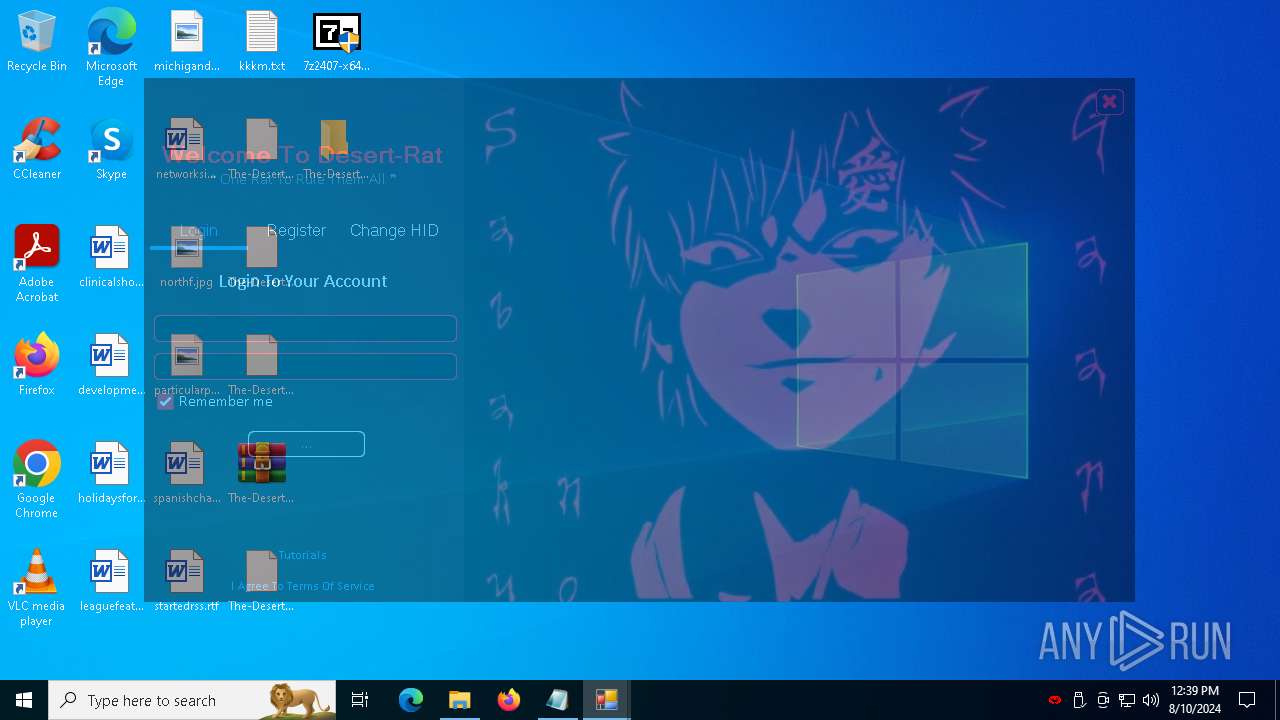
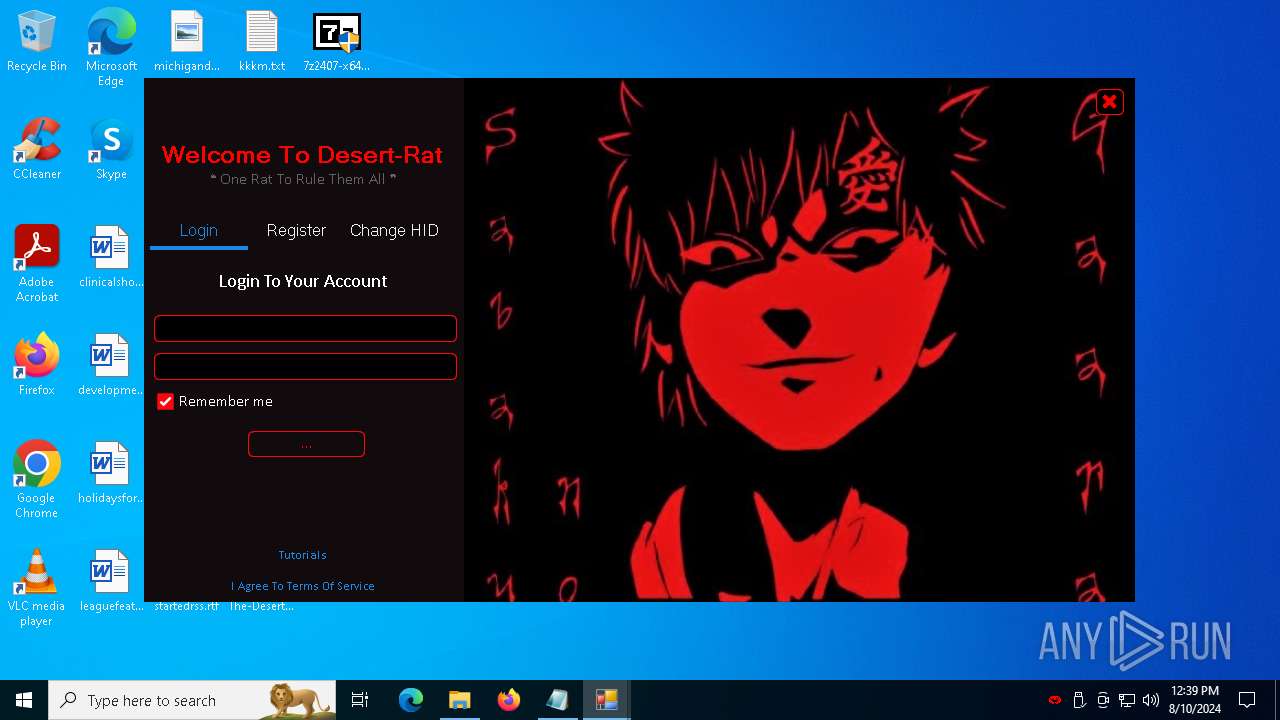
- Desert-Rat.exe (PID: 872)
- java.exe (PID: 6764)
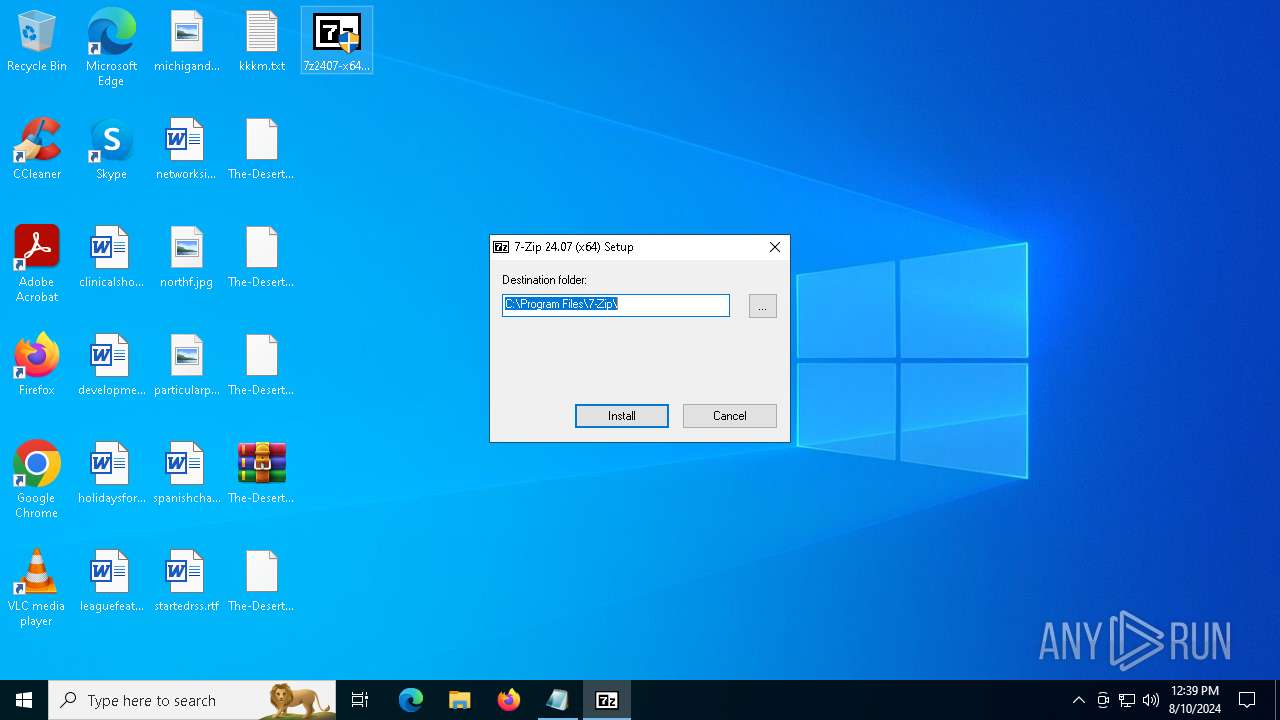
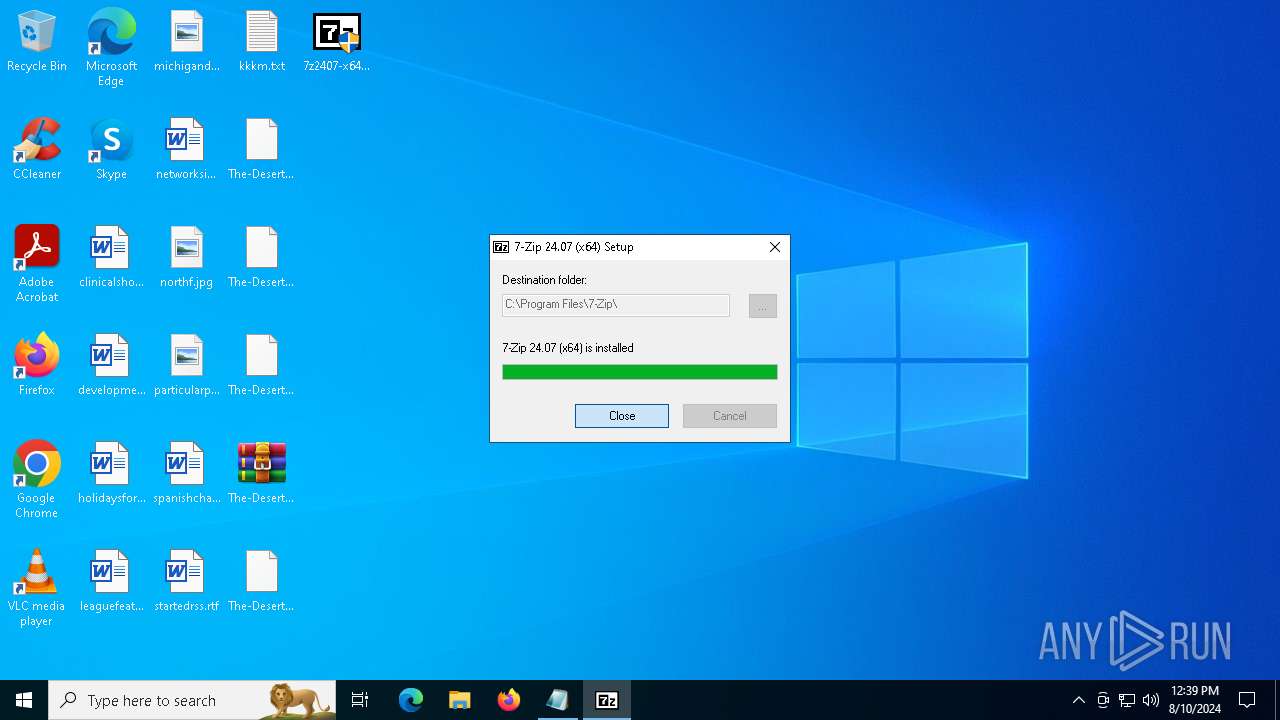
Drops 7-zip archiver for unpacking
- 7z2407-x64.exe (PID: 300)
- 7zG.exe (PID: 6648)
Creates/Modifies COM task schedule object
- 7z2407-x64.exe (PID: 300)
Creates a software uninstall entry
- 7z2407-x64.exe (PID: 300)
Executable content was dropped or overwritten
- 7z2407-x64.exe (PID: 300)
- 7zG.exe (PID: 6648)
- Desert-Rat.exe (PID: 872)
- java.exe (PID: 6764)
Process drops legitimate windows executable
- 7zG.exe (PID: 6648)
- Desert-Rat.exe (PID: 872)
Reads security settings of Internet Explorer
- Desert-Rat.exe (PID: 872)
The process drops C-runtime libraries
- Desert-Rat.exe (PID: 872)
Starts CMD.EXE for commands execution
- Desert-Rat.exe (PID: 872)
Starts application with an unusual extension
- java.exe (PID: 6764)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 6320)
Reads the computer name
- 7z2407-x64.exe (PID: 300)
- 7zG.exe (PID: 6648)
- Desert-Rat.exe (PID: 872)
- java.exe (PID: 6764)
- java.exe (PID: 4160)
- java.exe (PID: 4664)
- java.exe (PID: 4540)
Creates files in the program directory
- 7z2407-x64.exe (PID: 300)
Manual execution by a user
- 7z2407-x64.exe (PID: 300)
- 7z2407-x64.exe (PID: 5140)
- 7zG.exe (PID: 6648)
- Desert-Rat.exe (PID: 872)
- Desert-Rat.exe (PID: 3068)
Checks supported languages
- 7z2407-x64.exe (PID: 300)
- 7zG.exe (PID: 6648)
- java.exe (PID: 4084)
- java.exe (PID: 4664)
- Desert-Rat.exe (PID: 872)
- java.exe (PID: 4160)
- brut_util_Jar_5283480696019906251276296063637272497.tmp (PID: 6520)
- java.exe (PID: 4540)
- java.exe (PID: 6764)
- zipalign.exe (PID: 6632)
Create files in a temporary directory
- java.exe (PID: 4664)
- java.exe (PID: 4084)
- Desert-Rat.exe (PID: 872)
- brut_util_Jar_5283480696019906251276296063637272497.tmp (PID: 6520)
- java.exe (PID: 4160)
- java.exe (PID: 6764)
- java.exe (PID: 4540)
Creates files or folders in the user directory
- Desert-Rat.exe (PID: 872)
- java.exe (PID: 4664)
Checks proxy server information
- Desert-Rat.exe (PID: 872)
Reads the machine GUID from the registry
- Desert-Rat.exe (PID: 872)
- java.exe (PID: 6764)
- java.exe (PID: 4664)
- java.exe (PID: 4540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
156
Monitored processes
17
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Users\admin\Desktop\7z2407-x64.exe" | C:\Users\admin\Desktop\7z2407-x64.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Installer Exit code: 0 Version: 24.07 Modules
| |||||||||||||||
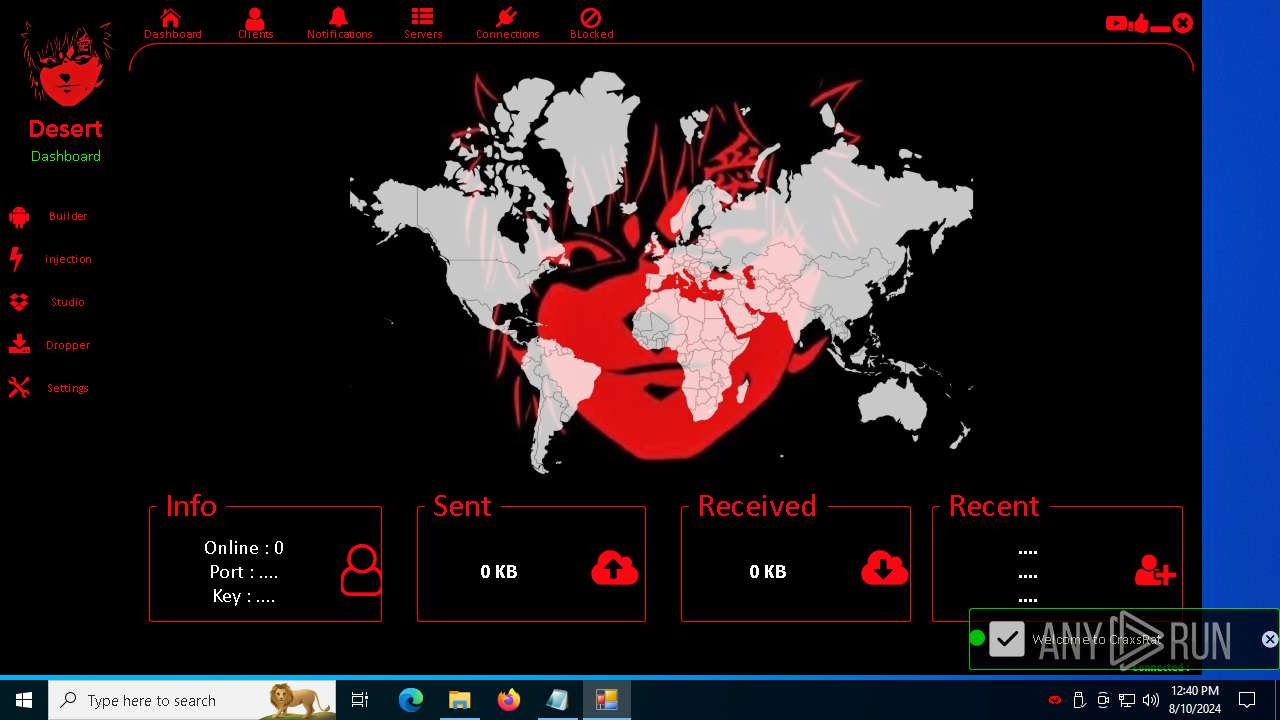
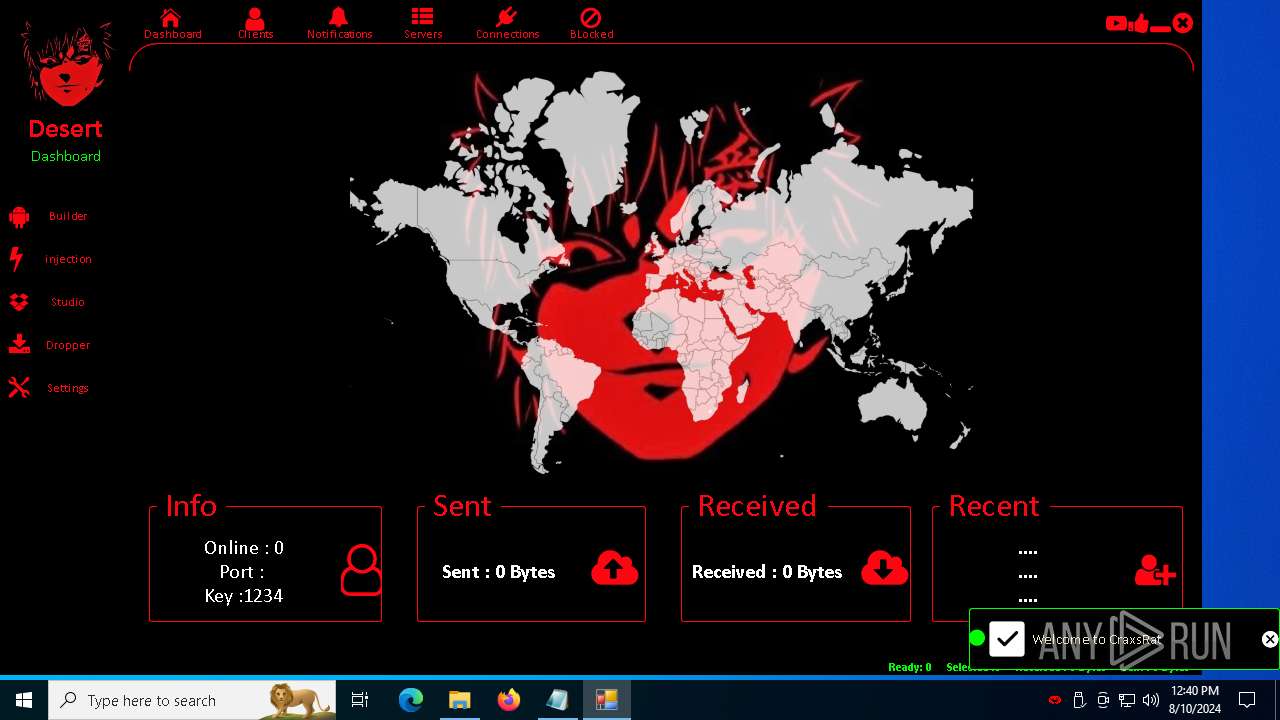
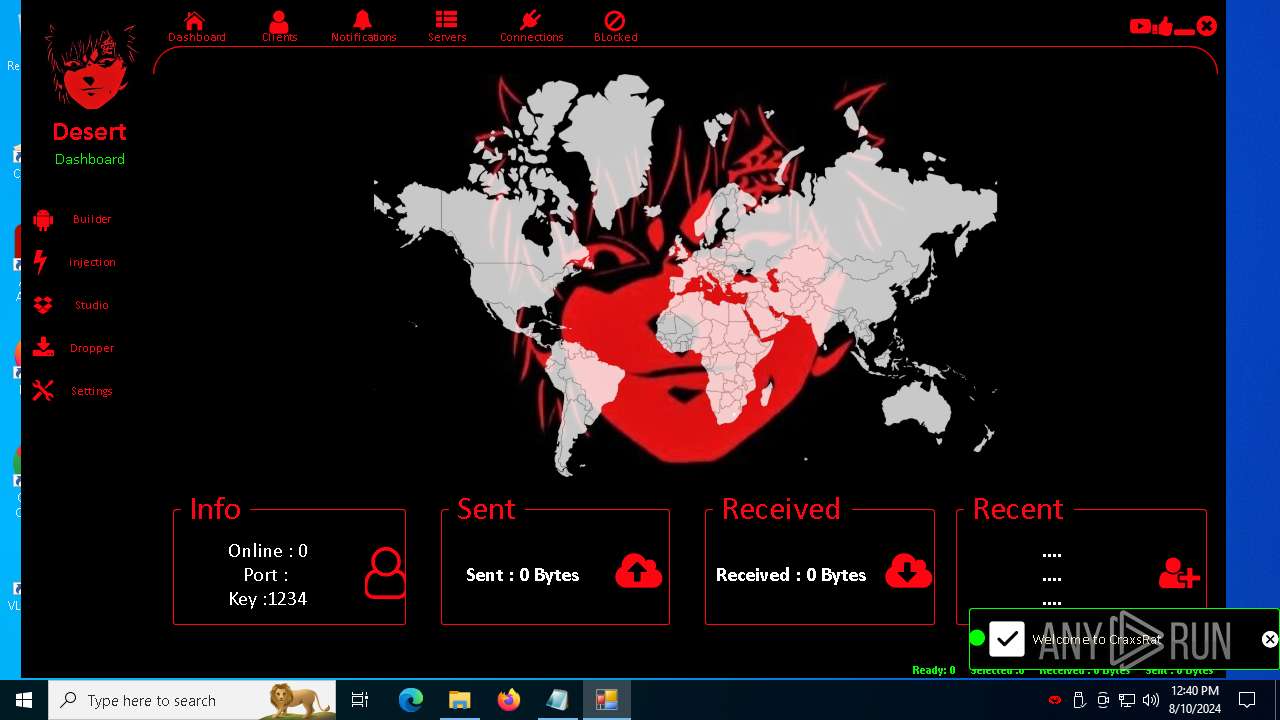
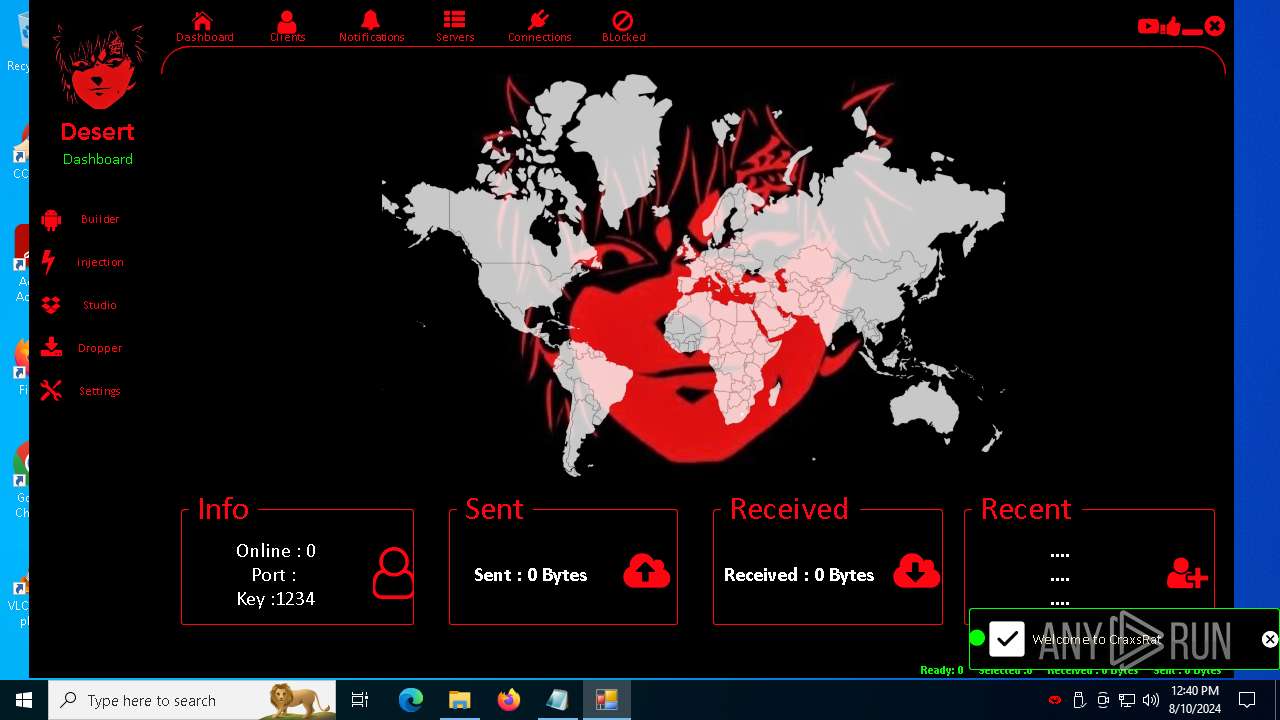
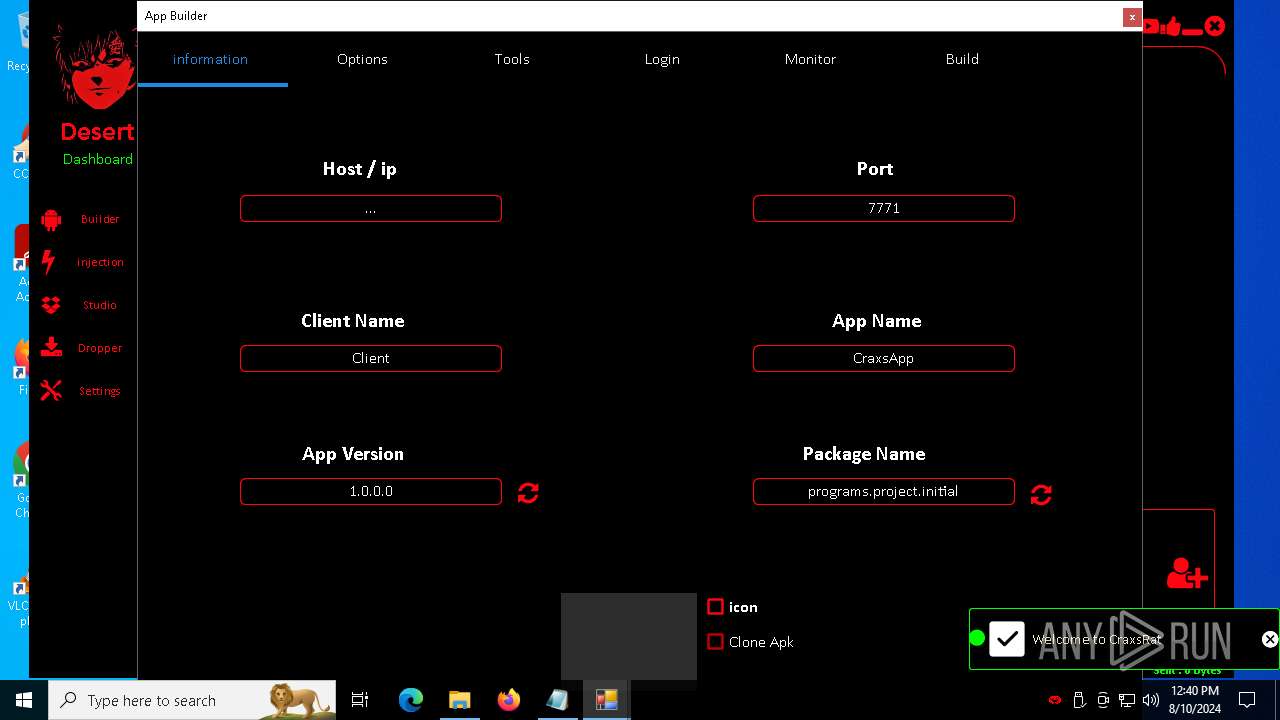
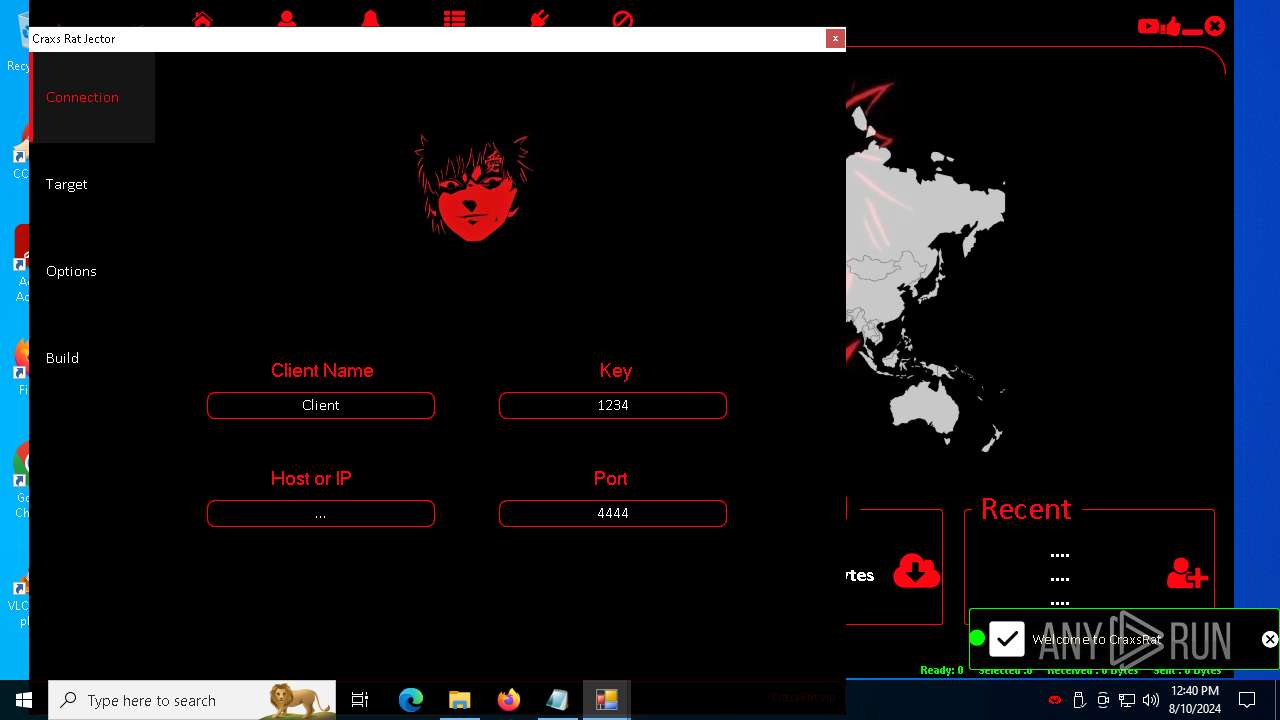
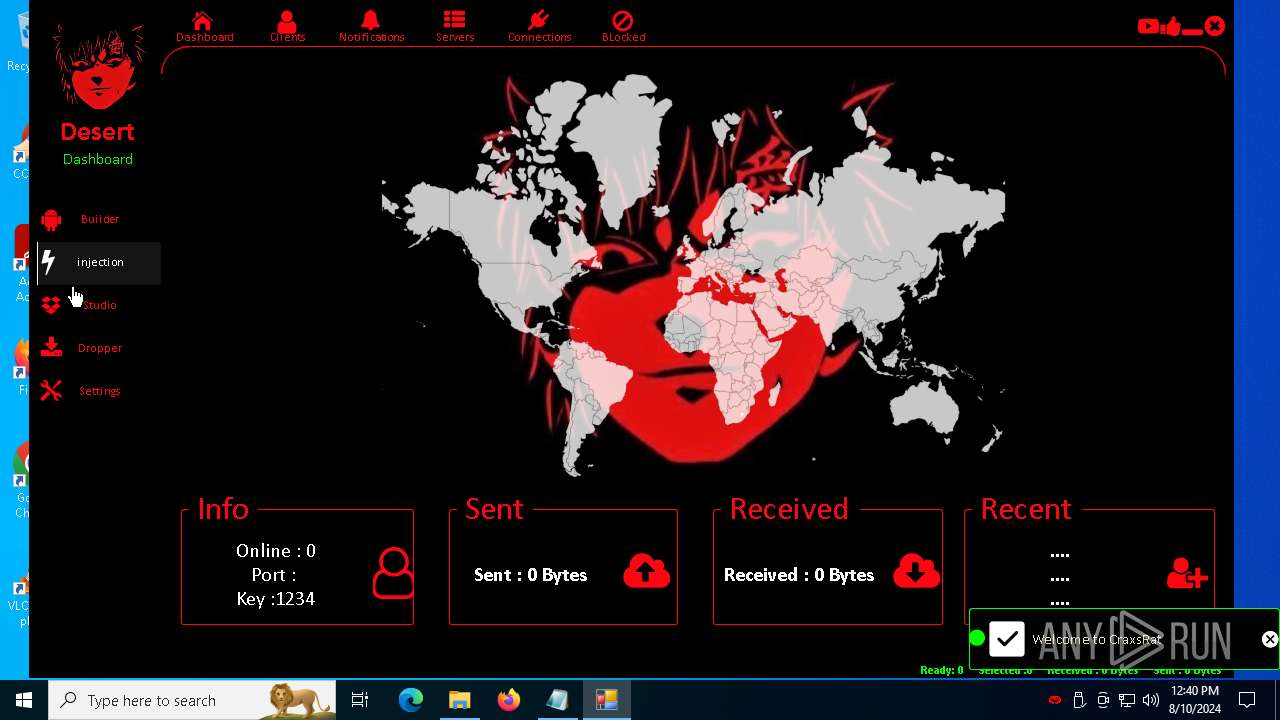
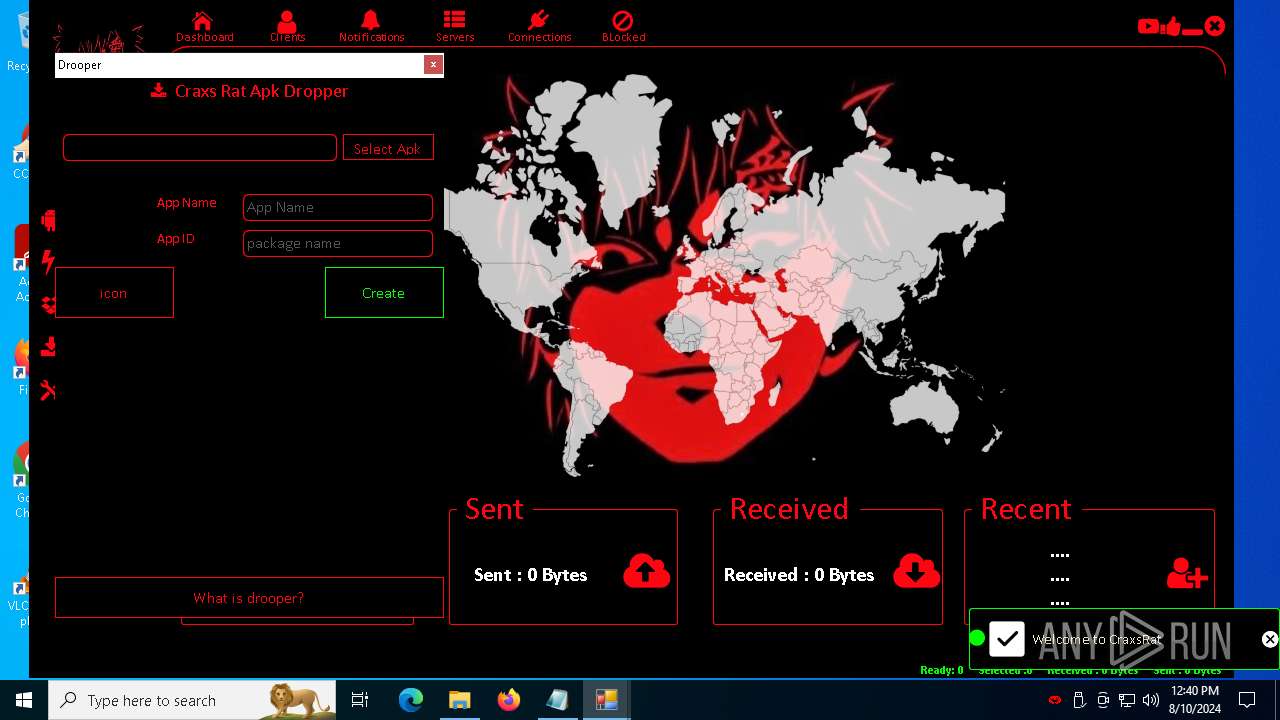
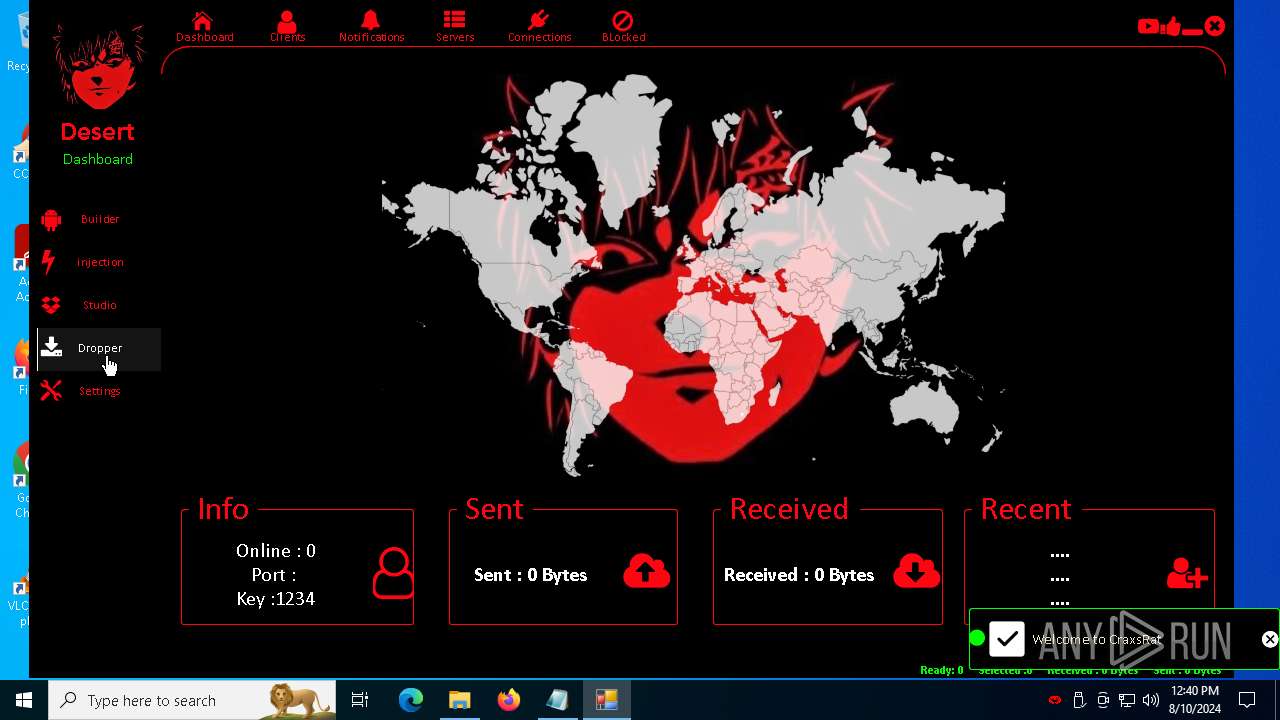
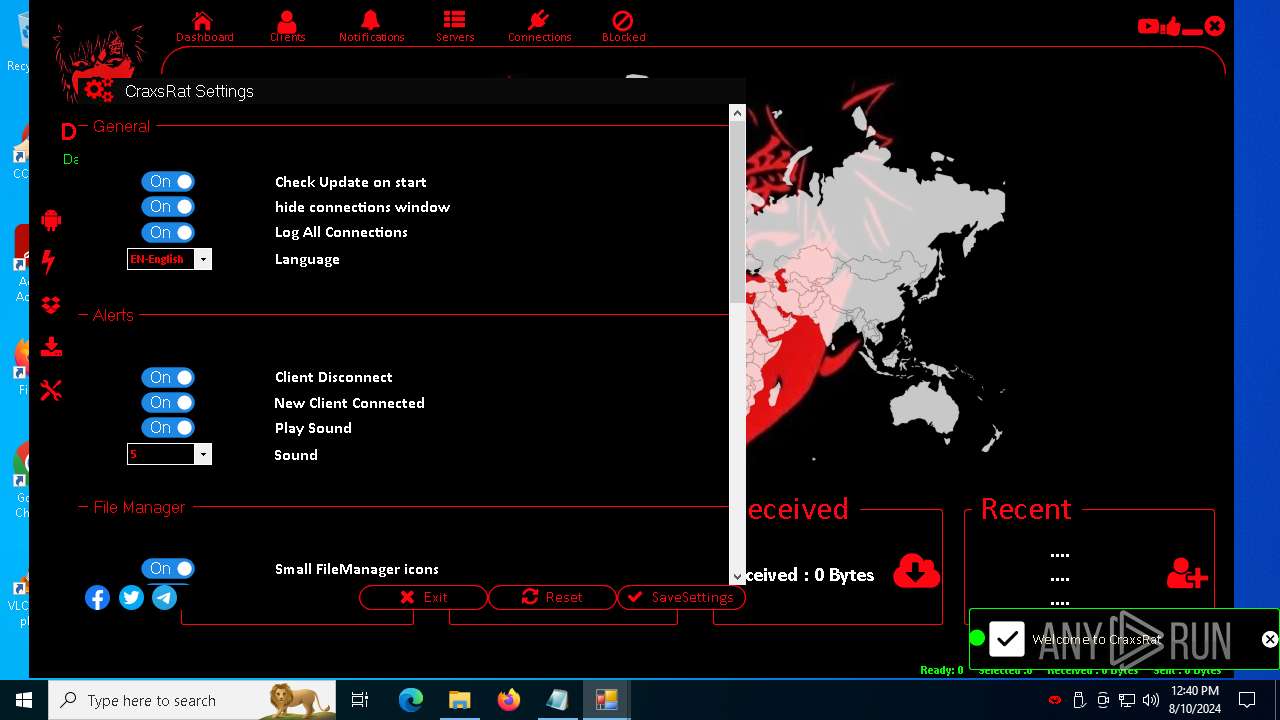
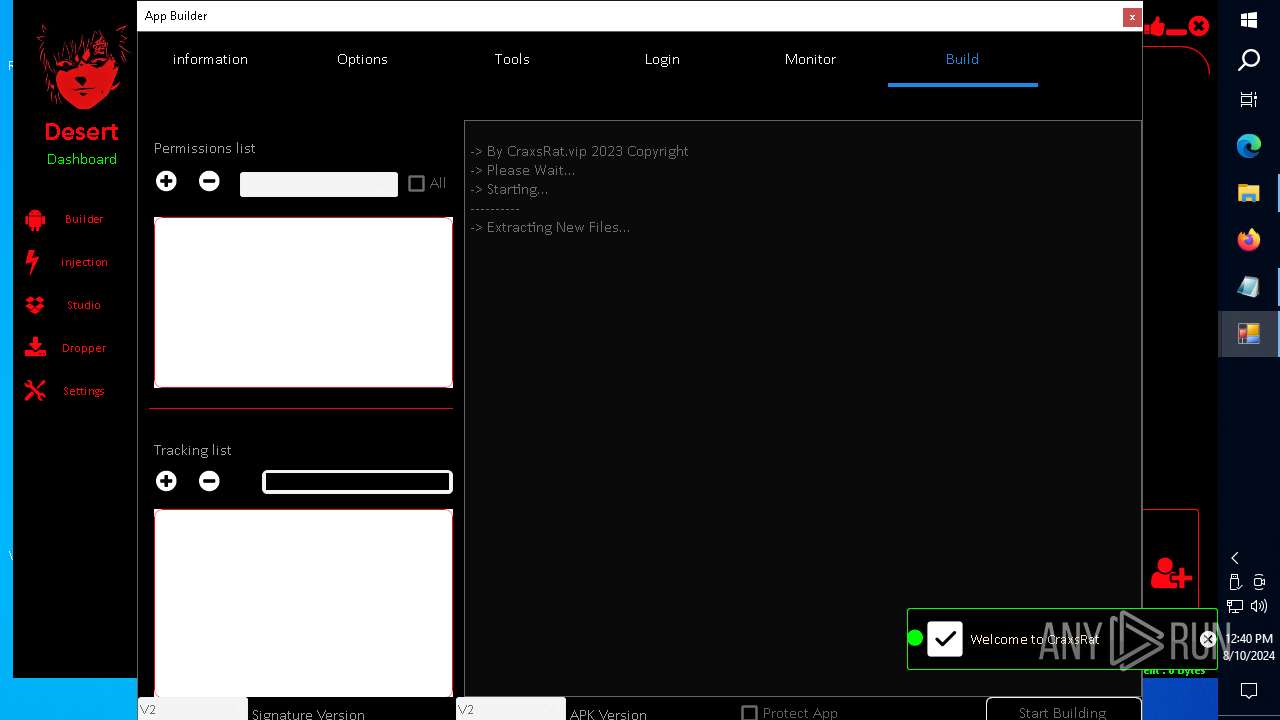
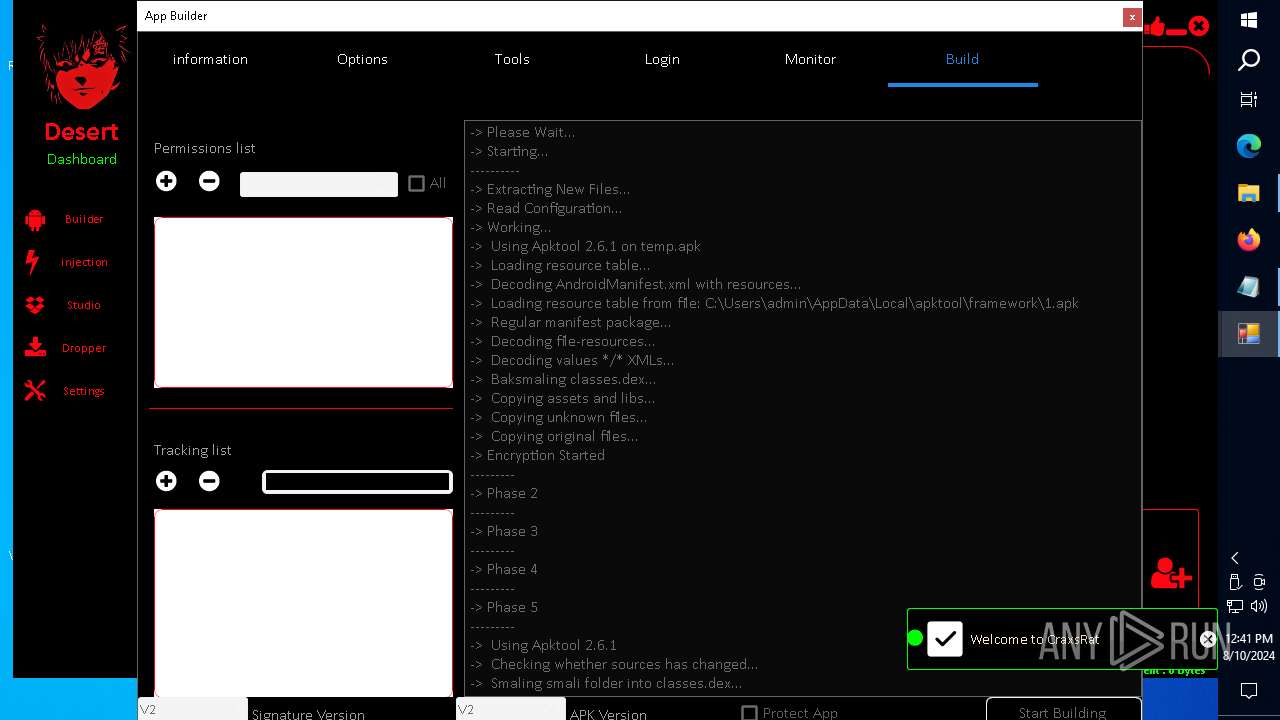
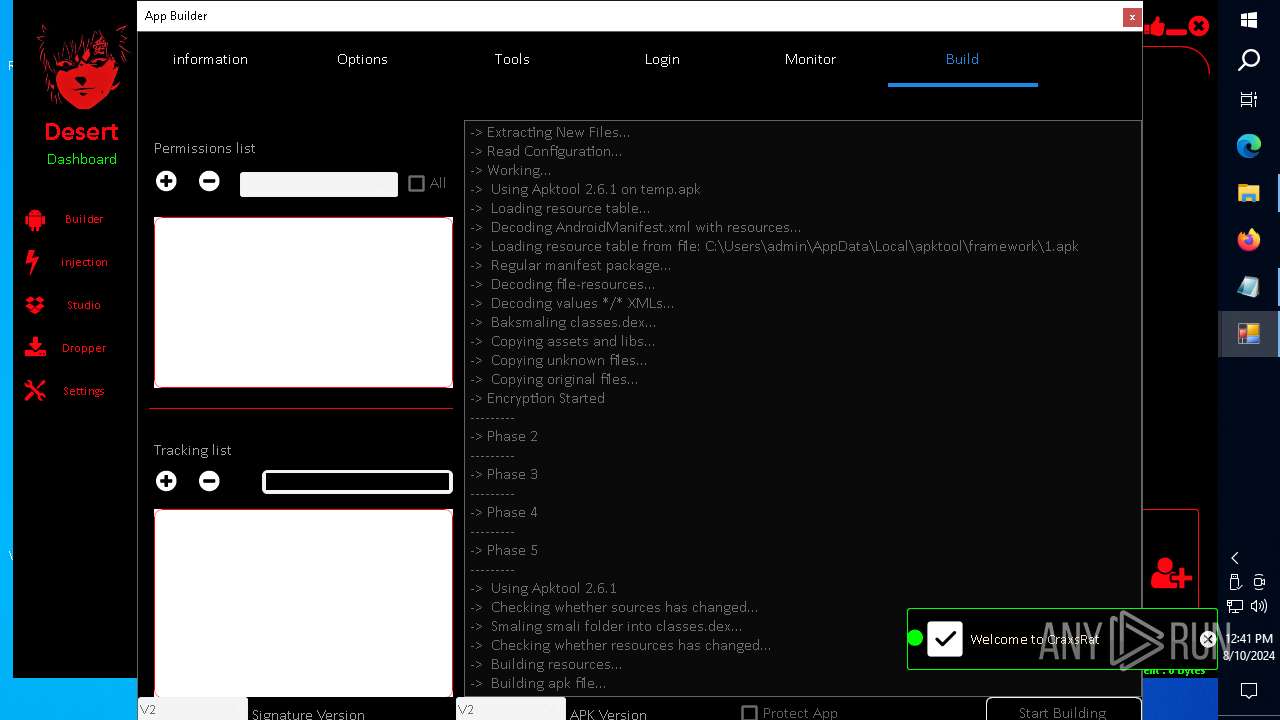
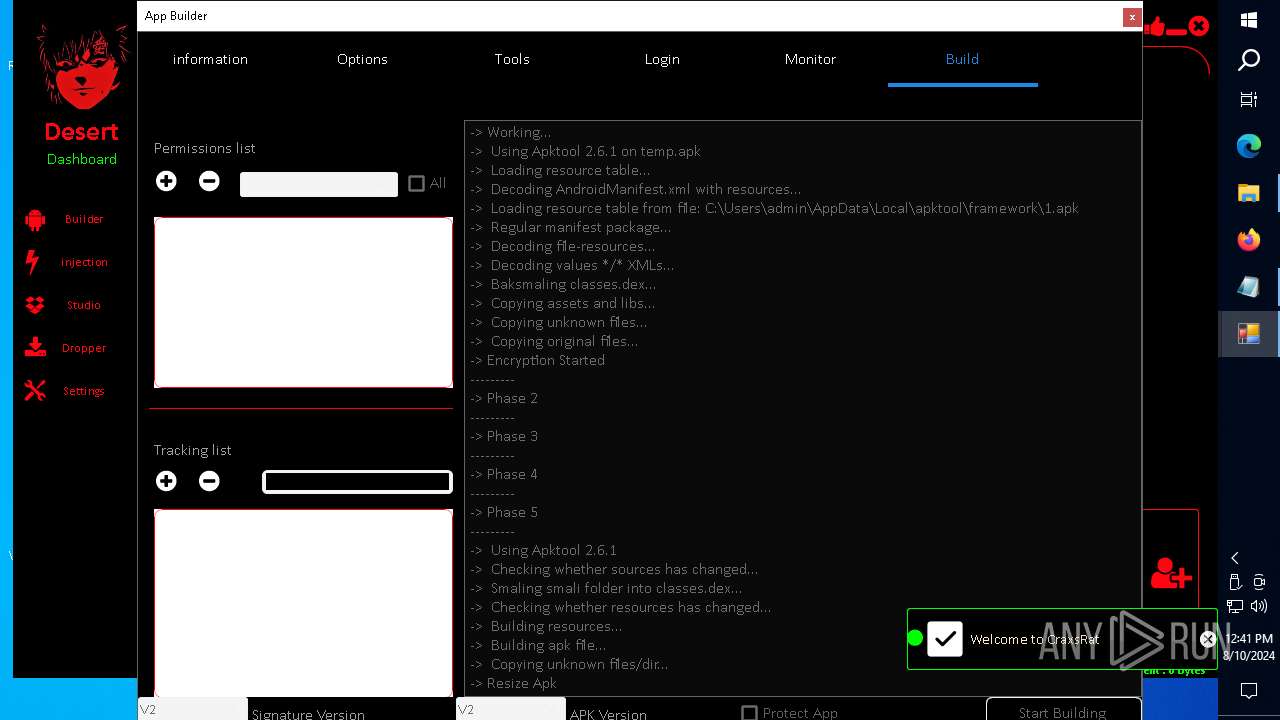
| 872 | "C:\Users\admin\Desktop\The-Desert-Rat\Desert-Rat.exe" | C:\Users\admin\Desktop\The-Desert-Rat\Desert-Rat.exe | explorer.exe | ||||||||||||
User: admin Company: EVLF - t.me/evlfdev Integrity Level: HIGH Description: Craxs Rat v7.1 Version: 7.1.0.0 Modules
| |||||||||||||||
| 1120 | "cmd.exe" | C:\Windows\System32\cmd.exe | — | Desert-Rat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2876 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3068 | "C:\Users\admin\Desktop\The-Desert-Rat\Desert-Rat.exe" | C:\Users\admin\Desktop\The-Desert-Rat\Desert-Rat.exe | — | explorer.exe | |||||||||||
User: admin Company: EVLF - t.me/evlfdev Integrity Level: MEDIUM Description: Craxs Rat v7.1 Exit code: 3221226540 Version: 7.1.0.0 Modules
| |||||||||||||||
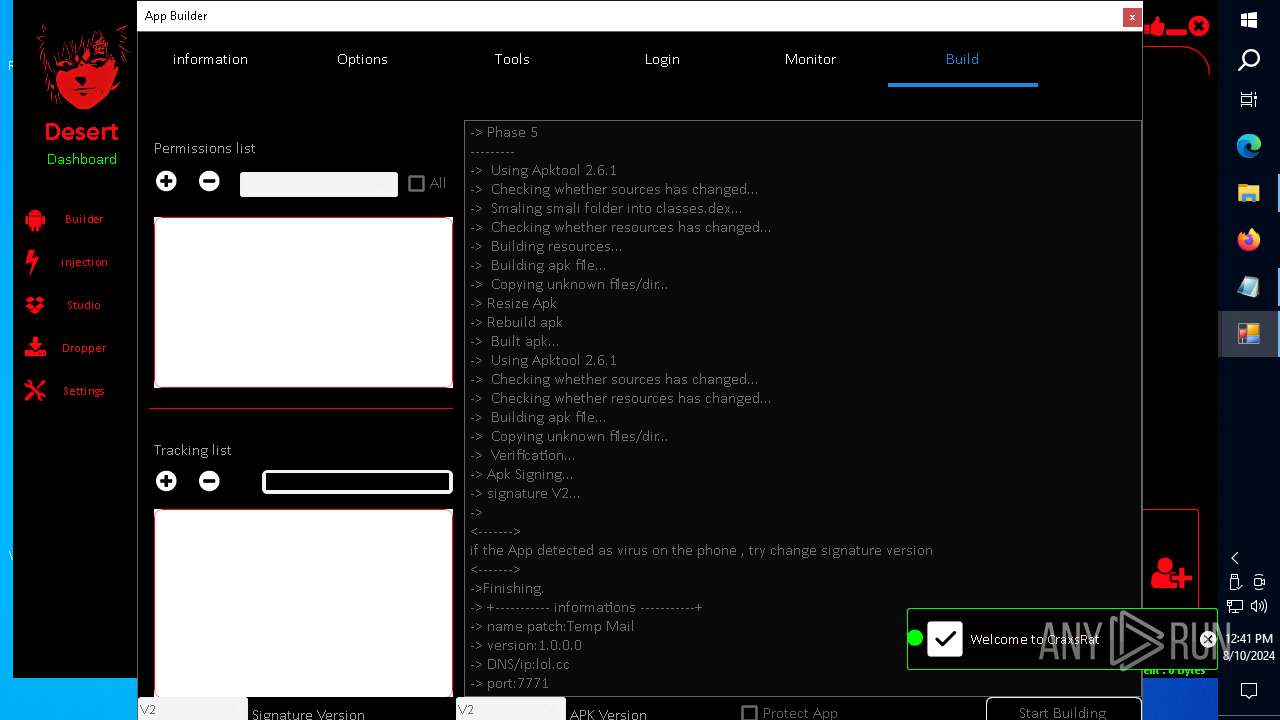
| 4084 | java -version | C:\CraxsRat_Bilder\platformBinary64\bin\java.exe | — | cmd.exe | |||||||||||
User: admin Company: N/A Integrity Level: HIGH Description: OpenJDK Platform binary Exit code: 0 Version: 8.0.1520.1 Modules
| |||||||||||||||
| 4160 | java -jar -Duser.language=en "C:\CraxsRat_Bilder\platformBinary64\bin\\apktool.jar" b temp | C:\CraxsRat_Bilder\platformBinary64\bin\java.exe | — | cmd.exe | |||||||||||
User: admin Company: N/A Integrity Level: HIGH Description: OpenJDK Platform binary Exit code: 0 Version: 8.0.1520.1 Modules
| |||||||||||||||
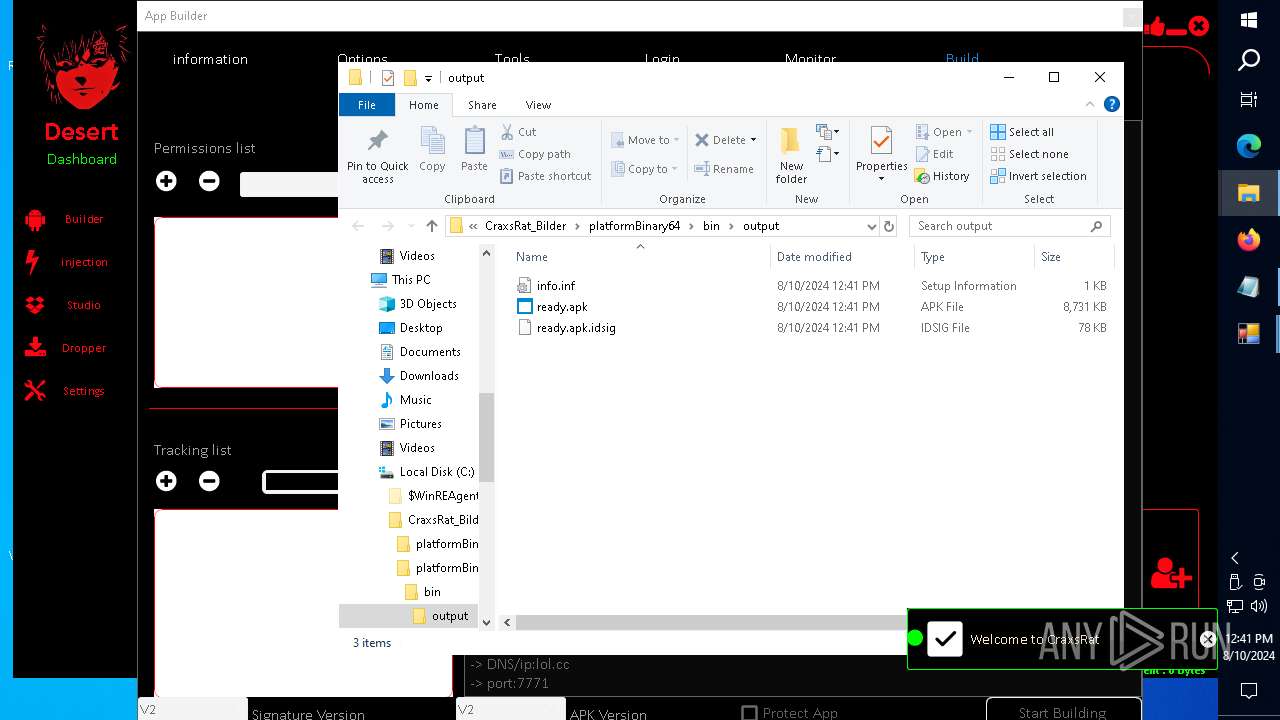
| 4540 | java -jar C:\CraxsRat_Bilder\platformBinary64\bin\SignApk.jar sign --key C:\CraxsRat_Bilder\platformBinary64\bin\key.pk8 --cert C:\CraxsRat_Bilder\platformBinary64\bin\certificate.pem --v2-signing-enabled true --v3-signing-enabled true --out C:\CraxsRat_Bilder\platformBinary64\bin\output\ready.apk C:\CraxsRat_Bilder\platformBinary64\bin\temp\dist\temp.apk | C:\CraxsRat_Bilder\platformBinary64\bin\java.exe | — | cmd.exe | |||||||||||
User: admin Company: N/A Integrity Level: HIGH Description: OpenJDK Platform binary Exit code: 0 Version: 8.0.1520.1 Modules
| |||||||||||||||
| 4664 | java -jar -Duser.language=en "C:\CraxsRat_Bilder\platformBinary64\bin\\apktool.jar" d temp.apk | C:\CraxsRat_Bilder\platformBinary64\bin\java.exe | — | cmd.exe | |||||||||||
User: admin Company: N/A Integrity Level: HIGH Description: OpenJDK Platform binary Exit code: 0 Version: 8.0.1520.1 Modules
| |||||||||||||||
| 5140 | "C:\Users\admin\Desktop\7z2407-x64.exe" | C:\Users\admin\Desktop\7z2407-x64.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Installer Exit code: 3221226540 Version: 24.07 Modules
| |||||||||||||||
Total events
6 323
Read events
6 287
Write events
34
Delete events
2
Modification events
| (PID) Process: | (300) 7z2407-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path64 |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (300) 7z2407-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (300) 7z2407-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path64 |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (300) 7z2407-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (300) 7z2407-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (300) 7z2407-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (300) 7z2407-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {23170F69-40C1-278A-1000-000100020000} |
Value: 7-Zip Shell Extension | |||
| (PID) Process: | (300) 7z2407-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {23170F69-40C1-278A-1000-000100020000} |
Value: 7-Zip Shell Extension | |||
| (PID) Process: | (300) 7z2407-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\7zFM.exe |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (300) 7z2407-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\7-Zip |
| Operation: | write | Name: | DisplayName |
Value: 7-Zip 24.07 (x64) | |||
Executable files
194
Suspicious files
74
Text files
1 753
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 300 | 7z2407-x64.exe | C:\Program Files\7-Zip\descript.ion | text | |
MD5:EB7E322BDC62614E49DED60E0FB23845 | SHA256:1DA513F5A4E8018B9AE143884EB3EAF72454B606FD51F2401B7CFD9BE4DBBF4F | |||
| 300 | 7z2407-x64.exe | C:\Program Files\7-Zip\Lang\ar.txt | text | |
MD5:5747381DC970306051432B18FB2236F2 | SHA256:85A26C7B59D6D9932F71518CCD03ECEEBA42043CB1707719B72BFC348C1C1D72 | |||
| 300 | 7z2407-x64.exe | C:\Program Files\7-Zip\Lang\ast.txt | text | |
MD5:1CF6411FF9154A34AFB512901BA3EE02 | SHA256:F5F2174DAF36E65790C7F0E9A4496B12E14816DAD2EE5B1D48A52307076BE35F | |||
| 300 | 7z2407-x64.exe | C:\Program Files\7-Zip\Lang\af.txt | text | |
MD5:DF216FAE5B13D3C3AFE87E405FD34B97 | SHA256:9CF684EA88EA5A479F510750E4089AEE60BBB2452AA85285312BAFCC02C10A34 | |||
| 300 | 7z2407-x64.exe | C:\Program Files\7-Zip\History.txt | text | |
MD5:553A02739D516379833451440076F884 | SHA256:83B1AE6D3486C2653766A28806AC110C9A0AFDE17020CA6AA0B7550A2F10E147 | |||
| 300 | 7z2407-x64.exe | C:\Program Files\7-Zip\Lang\az.txt | text | |
MD5:3C297FBE9B1ED5582BEABFC112B55523 | SHA256:055EC86AED86ABBDBD52D8E99FEC6E868D073A6DF92C60225ADD16676994C314 | |||
| 300 | 7z2407-x64.exe | C:\Program Files\7-Zip\Lang\de.txt | text | |
MD5:1E30A705DA680AAECEAEC26DCF2981DE | SHA256:895F76BFA4B1165E4C5A11BDAB70A774E7D05D4BBDAEC0230F29DCC85D5D3563 | |||
| 300 | 7z2407-x64.exe | C:\Program Files\7-Zip\Lang\ba.txt | text | |
MD5:387FF78CF5F524FC44640F3025746145 | SHA256:8A85C3FCB5F81157490971EE4F5E6B9E4F80BE69A802EBED04E6724CE859713F | |||
| 300 | 7z2407-x64.exe | C:\Program Files\7-Zip\Lang\be.txt | text | |
MD5:B1DD654E9D8C8C1B001F7B3A15D7B5D3 | SHA256:32071222AF04465A3D98BB30E253579AA4BECEAEB6B21AC7C15B25F46620BF30 | |||
| 300 | 7z2407-x64.exe | C:\Program Files\7-Zip\Lang\an.txt | text | |
MD5:F16218139E027338A16C3199091D0600 | SHA256:3AB9F7AACD38C4CDE814F86BC37EEC2B9DF8D0DDDB95FC1D09A5F5BCB11F0EEB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
41
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6780 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1568 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1568 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6836 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5512 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1120 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5512 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 184.86.251.19:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1568 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |