| File name: | ä¸é®éå¾äºæ¬¡å .exe |
| Full analysis: | https://app.any.run/tasks/902b5b95-ccc0-43f1-8689-50c7921f5d91 |
| Verdict: | Malicious activity |
| Analysis date: | June 22, 2025, 06:59:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 16ABB374EB1B759235AAEA1B03EEF712 |
| SHA1: | 495B467CE61E5D891690FAED3CAABCB04156C56A |
| SHA256: | 4608BCC2632C46335CD9FABEED46837C4FAE07D624BC86CDBB43CECC0B701DD1 |
| SSDEEP: | 393216:LlvWJzq/qE6xebU0ybDPEHDO+hGLZFMwdIhaQE:L1WJzq/5RJfjOu+W0 |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7116)
SUSPICIOUS
Executable content was dropped or overwritten
- ä¸é®éå¾äºæ¬¡å .exe (PID: 6680)
Process drops python dynamic module
- ä¸é®éå¾äºæ¬¡å .exe (PID: 6680)
The process drops C-runtime libraries
- ä¸é®éå¾äºæ¬¡å .exe (PID: 6680)
Process drops legitimate windows executable
- ä¸é®éå¾äºæ¬¡å .exe (PID: 6680)
Application launched itself
- ä¸é®éå¾äºæ¬¡å .exe (PID: 6680)
Loads Python modules
- ä¸é®éå¾äºæ¬¡å .exe (PID: 632)
Hides command output
- cmd.exe (PID: 7116)
Starts CMD.EXE for commands execution
- ä¸é®éå¾äºæ¬¡å .exe (PID: 632)
There is functionality for taking screenshot (YARA)
- ä¸é®éå¾äºæ¬¡å .exe (PID: 6680)
- ä¸é®éå¾äºæ¬¡å .exe (PID: 632)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6896)
- cmd.exe (PID: 6228)
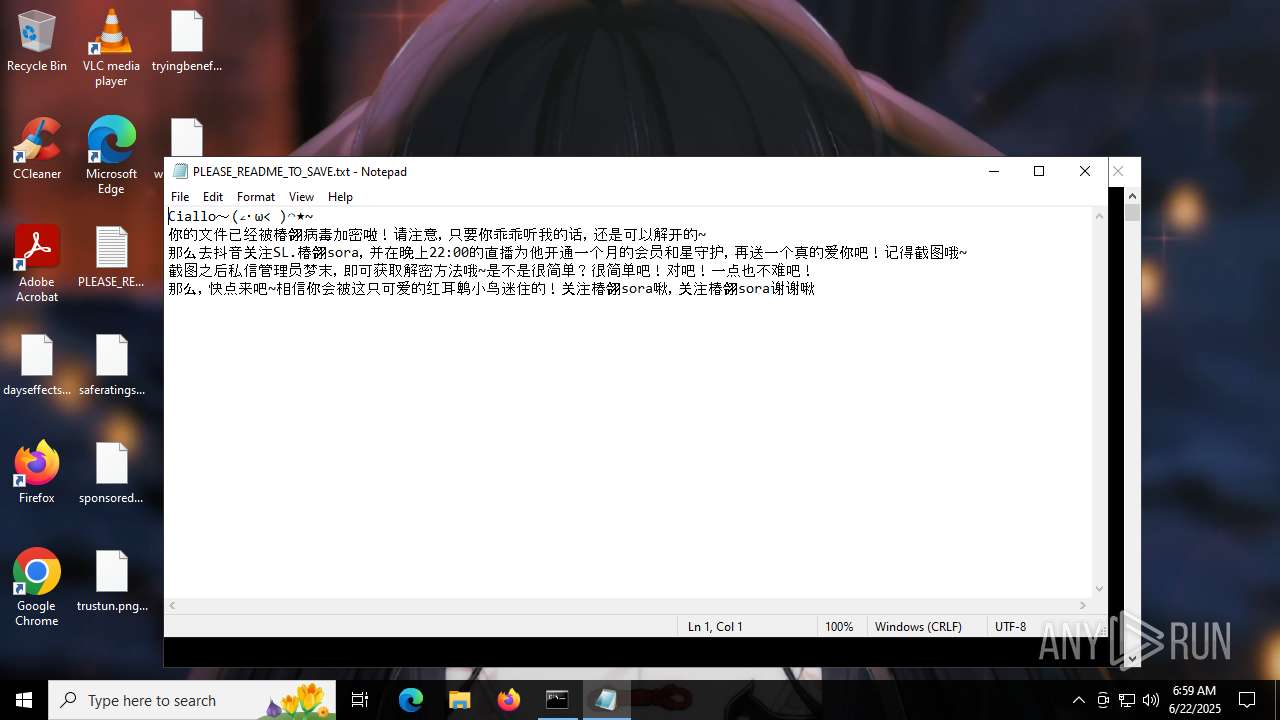
Changes the desktop background image
- ä¸é®éå¾äºæ¬¡å .exe (PID: 632)
INFO
Reads the computer name
- ä¸é®éå¾äºæ¬¡å .exe (PID: 6680)
- ä¸é®éå¾äºæ¬¡å .exe (PID: 632)
Checks supported languages
- ä¸é®éå¾äºæ¬¡å .exe (PID: 6680)
- ä¸é®éå¾äºæ¬¡å .exe (PID: 632)
The sample compiled with english language support
- ä¸é®éå¾äºæ¬¡å .exe (PID: 6680)
Create files in a temporary directory
- ä¸é®éå¾äºæ¬¡å .exe (PID: 6680)
- ä¸é®éå¾äºæ¬¡å .exe (PID: 632)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5780)
PyInstaller has been detected (YARA)
- ä¸é®éå¾äºæ¬¡å .exe (PID: 6680)
- ä¸é®éå¾äºæ¬¡å .exe (PID: 632)
Checks proxy server information
- slui.exe (PID: 6404)
- ä¸é®éå¾äºæ¬¡å .exe (PID: 632)
Reads the software policy settings
- slui.exe (PID: 6404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:20 05:27:02+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 167936 |
| InitializedDataSize: | 104448 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xbe20 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
151
Monitored processes
15
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Users\admin\AppData\Local\Temp\ä¸é®éå¾äºæ¬¡å .exe" | C:\Users\admin\AppData\Local\Temp\ä¸é®éå¾äºæ¬¡å .exe | ä¸é®éå¾äºæ¬¡å .exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2296 | C:\WINDOWS\system32\cmd.exe /c notepad %UserProfile%\Desktop\PLEASE_README_TO_SAVE.txt | C:\Windows\System32\cmd.exe | — | ä¸é®éå¾äºæ¬¡å .exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2808 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4372 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4580 | attrib +s +h "C:\Users\admin\Desktop\logo.ico" | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4768 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4816 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5780 | notepad C:\Users\admin\Desktop\PLEASE_README_TO_SAVE.txt | C:\Windows\System32\notepad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5900 | attrib +s +h "C:\Users\admin\Desktop\main_bg.png" | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6228 | C:\WINDOWS\system32\cmd.exe /c attrib +s +h "C:\Users\admin\Desktop\logo.ico" | C:\Windows\System32\cmd.exe | — | ä¸é®éå¾äºæ¬¡å .exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 152
Read events
7 151
Write events
1
Delete events
0
Modification events
| (PID) Process: | (632) ä¸é®éå¾äºæ¬¡å .exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: %UserProfile%\Desktop\main_bg.png | |||
Executable files
100
Suspicious files
2
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6680 | ä¸é®éå¾äºæ¬¡å .exe | C:\Users\admin\AppData\Local\Temp\_MEI66802\PIL\_imagingtk.cp312-win_amd64.pyd | executable | |
MD5:7E912D07A39E16BB25CF32B7153515C8 | SHA256:D1E5D023821A9C38967FFAA9BDBF4DDE998A3A6BC37942CA334A13E55A1FC711 | |||
| 6680 | ä¸é®éå¾äºæ¬¡å .exe | C:\Users\admin\AppData\Local\Temp\_MEI66802\PIL\_imaging.cp312-win_amd64.pyd | executable | |
MD5:0376776F076CD4F4AC15EC4D813C5470 | SHA256:A7DDF4D7CAB08676BB88A42059353C5374600901B3AB880E17EE1A0D0150C380 | |||
| 6680 | ä¸é®éå¾äºæ¬¡å .exe | C:\Users\admin\AppData\Local\Temp\_MEI66802\_queue.pyd | executable | |
MD5:5AA4B057BA2331EED6B4B30F4B3E0D52 | SHA256:D43DCA0E00C3C11329B68177E967CF5240495C4786F5AFA76AC4F267C3A5CDB9 | |||
| 6680 | ä¸é®éå¾äºæ¬¡å .exe | C:\Users\admin\AppData\Local\Temp\_MEI66802\PIL\_imagingcms.cp312-win_amd64.pyd | executable | |
MD5:48F7F14636DA0BC081A34ACBFE30D77D | SHA256:3C2CEDEBABB5748F78FBA56634FD49CDAAD02C18D808D7E2B4F50E2800C7930F | |||
| 6680 | ä¸é®éå¾äºæ¬¡å .exe | C:\Users\admin\AppData\Local\Temp\_MEI66802\VCRUNTIME140.dll | executable | |
MD5:BE8DBE2DC77EBE7F88F910C61AEC691A | SHA256:4D292623516F65C80482081E62D5DADB759DC16E851DE5DB24C3CBB57B87DB83 | |||
| 6680 | ä¸é®éå¾äºæ¬¡å .exe | C:\Users\admin\AppData\Local\Temp\_MEI66802\PIL\_imagingmath.cp312-win_amd64.pyd | executable | |
MD5:8F67156CE61C7DE23E19F9445C8BA504 | SHA256:8287A2A551BD99B5D55E18E461FEDB3704B74B0FB60F1E0881C792F90A18CE46 | |||
| 6680 | ä¸é®éå¾äºæ¬¡å .exe | C:\Users\admin\AppData\Local\Temp\_MEI66802\VCRUNTIME140_1.dll | executable | |
MD5:F8DFA78045620CF8A732E67D1B1EB53D | SHA256:A113F192195F245F17389E6ECBED8005990BCB2476DDAD33F7C4C6C86327AFE5 | |||
| 6680 | ä¸é®éå¾äºæ¬¡å .exe | C:\Users\admin\AppData\Local\Temp\_MEI66802\PIL\_webp.cp312-win_amd64.pyd | executable | |
MD5:12D05951F8004E24EEAA0E45D587FE8E | SHA256:D96B196126A033F1D7832E29CEE44928683FAB00242E812815FF95FFFED1AF54 | |||
| 6680 | ä¸é®éå¾äºæ¬¡å .exe | C:\Users\admin\AppData\Local\Temp\_MEI66802\Pythonwin\win32ui.pyd | executable | |
MD5:621449EFF843B6128E15BA20B40E2688 | SHA256:AA9F43412393CD50340570ABF6AE6FD5C3A2119555B5D6CAF43AC693CC2AA244 | |||
| 6680 | ä¸é®éå¾äºæ¬¡å .exe | C:\Users\admin\AppData\Local\Temp\_MEI66802\_hashlib.pyd | executable | |
MD5:8BAEB2BD6E52BA38F445EF71EF43A6B8 | SHA256:6C50C9801A5CAF0BB52B384F9A0D5A4AA182CA835F293A39E8999CF6EDF2F087 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
29
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3100 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6376 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6376 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.16.252.233:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6172 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3100 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3100 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
632 | ä¸é®éå¾äºæ¬¡å
.exe | 49.232.237.64:443 | tc.z.wiki | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
tc.z.wiki |
| unknown |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |