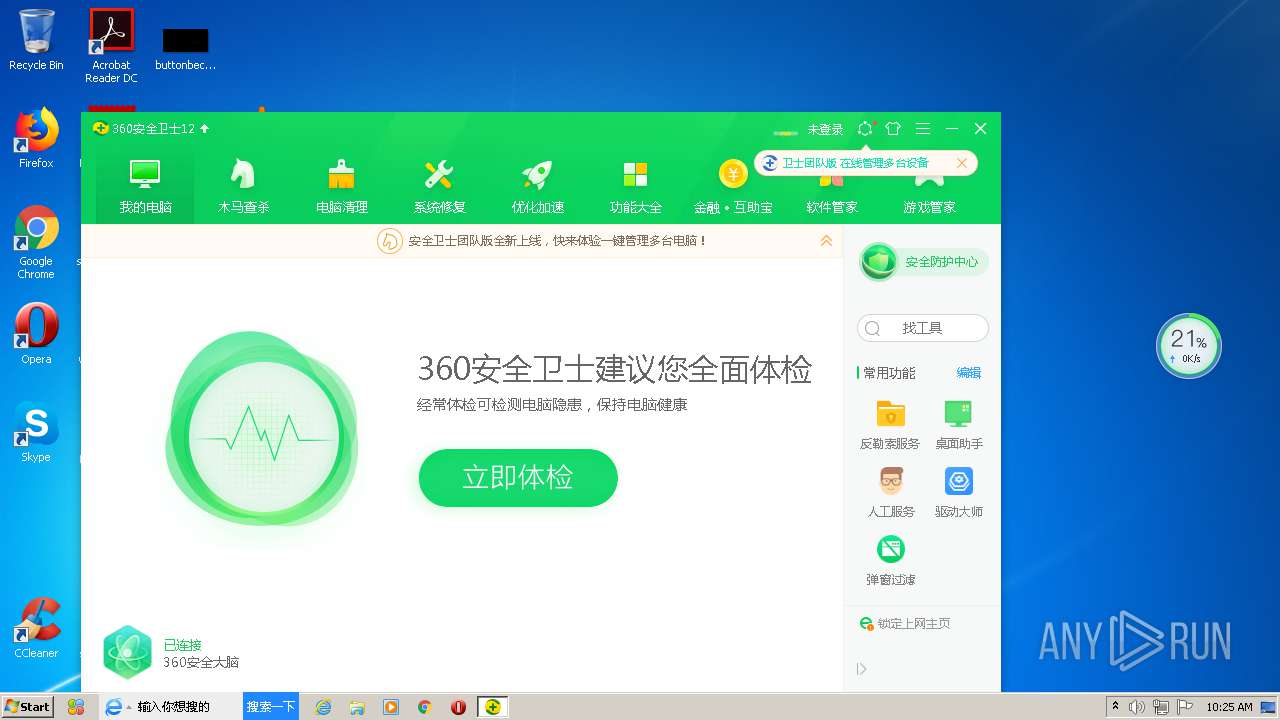
| File name: | inst.exe |
| Full analysis: | https://app.any.run/tasks/e1acd560-7f06-458d-b399-97000ddae335 |
| Verdict: | Malicious activity |
| Analysis date: | November 27, 2020, 10:20:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3D478D0F8B0E654180197664ECFB5E2B |
| SHA1: | F6F7E5DBCA5A15DA61AC8D6455539B084E23799F |
| SHA256: | 460466EB951079B30697863A3D1C9667C82BF9DEE02F8E13BEDAD7B5A8694E02 |
| SSDEEP: | 98304:wp16is14Jfu2l14FL8VIavYtmvnMyK7vHO4wKQ3eDDfHrai1PEEwk:QtiouU4yVI4P0zU3SDfLaSkk |
MALICIOUS
Drops executable file immediately after starts
- inst.exe (PID: 3844)
Loads dropped or rewritten executable
- inst.exe (PID: 3844)
- setup.exe (PID: 3024)
- 360SecLogonHelper.exe (PID: 1448)
- PopWndTracker.exe (PID: 1888)
- zhudongfangyu.exe (PID: 4012)
- 360tray.exe (PID: 2868)
- 360Safe.exe (PID: 2600)
- zhudongfangyu.exe (PID: 1396)
- 360entcall.exe (PID: 3484)
- SoftupNotify.exe (PID: 1228)
- zhudongfangyu.exe (PID: 2804)
- regsvr32.exe (PID: 2144)
- regsvr32.exe (PID: 3012)
- 360leakfixer.exe (PID: 2472)
- 360UHelper.exe (PID: 2388)
- LiveUpdate360.exe (PID: 2648)
- PowerSaver.exe (PID: 3120)
- SoftMgrLite.exe (PID: 1408)
- 360IA.exe (PID: 1356)
- SDIS.exe (PID: 3804)
- explorer.exe (PID: 292)
- WINWORD.EXE (PID: 1788)
- SoftupNotify.exe (PID: 2188)
- SoftManager.exe (PID: 1964)
- GameChrome.exe (PID: 2500)
- ModuleUpdate.exe (PID: 2792)
- DllHost.exe (PID: 976)
- SoftMgr.exe (PID: 2540)
- services.exe (PID: 476)
- 360DayPop.exe (PID: 2692)
Actions looks like stealing of personal data
- inst.exe (PID: 3844)
- setup.exe (PID: 3024)
Changes the autorun value in the registry
- setup.exe (PID: 3024)
Application was dropped or rewritten from another process
- 360SecLogonHelper.exe (PID: 1448)
- PopWndTracker.exe (PID: 1888)
- zhudongfangyu.exe (PID: 4012)
- PowerSaver.exe (PID: 3120)
- PowerSaver.exe (PID: 2740)
- 360Safe.exe (PID: 2600)
- 360tray.exe (PID: 2868)
- 360entcall.exe (PID: 3484)
- SoftupNotify.exe (PID: 1228)
- zhudongfangyu.exe (PID: 1396)
- zhudongfangyu.exe (PID: 2804)
- 360leakfixer.exe (PID: 2472)
- 360UHelper.exe (PID: 2388)
- LiveUpdate360.exe (PID: 2648)
- 360IA.exe (PID: 1356)
- SoftMgrLite.exe (PID: 1408)
- WscReg.exe (PID: 3788)
- 360safe.exe (PID: 3676)
- SDIS.exe (PID: 3804)
- SoftupNotify.exe (PID: 2188)
- SoftManager.exe (PID: 1964)
- SoftMgr.exe (PID: 2540)
- GameChrome.exe (PID: 2500)
- ModuleUpdate.exe (PID: 2792)
- WINWORD.EXE (PID: 1788)
- 360DayPop.exe (PID: 2692)
Changes settings of System certificates
- PowerSaver.exe (PID: 3120)
- 360UHelper.exe (PID: 2388)
- 360tray.exe (PID: 2868)
Registers / Runs the DLL via REGSVR32.EXE
- SoftupNotify.exe (PID: 1228)
Loads the Task Scheduler COM API
- OSPPSVC.EXE (PID: 1208)
SUSPICIOUS
Executable content was dropped or overwritten
- inst.exe (PID: 3844)
- setup.exe (PID: 3024)
- 360Safe.exe (PID: 2600)
- 360tray.exe (PID: 2868)
Low-level read access rights to disk partition
- inst.exe (PID: 3844)
- setup.exe (PID: 3024)
- 360SecLogonHelper.exe (PID: 1448)
- 360tray.exe (PID: 2868)
- 360Safe.exe (PID: 2600)
- 360leakfixer.exe (PID: 2472)
- SoftMgrLite.exe (PID: 1408)
- SDIS.exe (PID: 3804)
- SoftupNotify.exe (PID: 2188)
- SoftMgr.exe (PID: 2540)
- ModuleUpdate.exe (PID: 2792)
Creates a directory in Program Files
- inst.exe (PID: 3844)
- setup.exe (PID: 3024)
- 360UHelper.exe (PID: 2388)
- 360tray.exe (PID: 2868)
- SDIS.exe (PID: 3804)
- ModuleUpdate.exe (PID: 2792)
Creates files in the program directory
- inst.exe (PID: 3844)
- PopWndTracker.exe (PID: 1888)
- 360entcall.exe (PID: 3484)
- zhudongfangyu.exe (PID: 2804)
- SoftupNotify.exe (PID: 1228)
- 360Safe.exe (PID: 2600)
- LiveUpdate360.exe (PID: 2648)
- 360UHelper.exe (PID: 2388)
- SoftMgrLite.exe (PID: 1408)
- SDIS.exe (PID: 3804)
- setup.exe (PID: 3024)
- ModuleUpdate.exe (PID: 2792)
- SoftMgr.exe (PID: 2540)
- 360tray.exe (PID: 2868)
Drops a file that was compiled in debug mode
- inst.exe (PID: 3844)
- setup.exe (PID: 3024)
- 360Safe.exe (PID: 2600)
- 360tray.exe (PID: 2868)
Creates files in the user directory
- explorer.exe (PID: 292)
- setup.exe (PID: 3024)
- 360Safe.exe (PID: 2600)
- LiveUpdate360.exe (PID: 2648)
- SoftMgrLite.exe (PID: 1408)
- SDIS.exe (PID: 3804)
- SoftMgr.exe (PID: 2540)
- ModuleUpdate.exe (PID: 2792)
- 360tray.exe (PID: 2868)
Writes to a desktop.ini file (may be used to cloak folders)
- setup.exe (PID: 3024)
Drops a file with a compile date too recent
- setup.exe (PID: 3024)
- 360tray.exe (PID: 2868)
Drops a file with too old compile date
- setup.exe (PID: 3024)
- 360tray.exe (PID: 2868)
Creates files in the Windows directory
- setup.exe (PID: 3024)
- 360tray.exe (PID: 2868)
Creates a software uninstall entry
- setup.exe (PID: 3024)
Creates or modifies windows services
- services.exe (PID: 476)
- setup.exe (PID: 3024)
- zhudongfangyu.exe (PID: 2804)
- 360tray.exe (PID: 2868)
- zhudongfangyu.exe (PID: 4012)
Creates files in the driver directory
- setup.exe (PID: 3024)
- 360tray.exe (PID: 2868)
Creates COM task schedule object
- setup.exe (PID: 3024)
- 360tray.exe (PID: 2868)
- regsvr32.exe (PID: 2144)
- regsvr32.exe (PID: 3012)
Modifies the open verb of a shell class
- setup.exe (PID: 3024)
- SoftupNotify.exe (PID: 1228)
Reads the cookies of Google Chrome
- setup.exe (PID: 3024)
Executed as Windows Service
- zhudongfangyu.exe (PID: 2804)
Adds / modifies Windows certificates
- 360UHelper.exe (PID: 2388)
- 360tray.exe (PID: 2868)
Searches for installed software
- 360tray.exe (PID: 2868)
INFO
Manual execution by user
- explorer.exe (PID: 2972)
Dropped object may contain TOR URL's
- setup.exe (PID: 3024)
Dropped object may contain Bitcoin addresses
- setup.exe (PID: 3024)
- 360tray.exe (PID: 2868)
Reads settings of System Certificates
- 360tray.exe (PID: 2868)
- ModuleUpdate.exe (PID: 2792)
Starts Microsoft Office Application
- explorer.exe (PID: 292)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1788)
Creates files in the user directory
- WINWORD.EXE (PID: 1788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (18) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (2.9) |
| .exe | | | Generic Win/DOS Executable (1.3) |
| .exe | | | DOS Executable Generic (1.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:08:10 12:56:14+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 755200 |
| InitializedDataSize: | 4591616 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8b821 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 12.0.0.1191 |
| ProductVersionNumber: | 12.0.0.1191 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | Neutral 2 |
| CharacterSet: | Unicode |
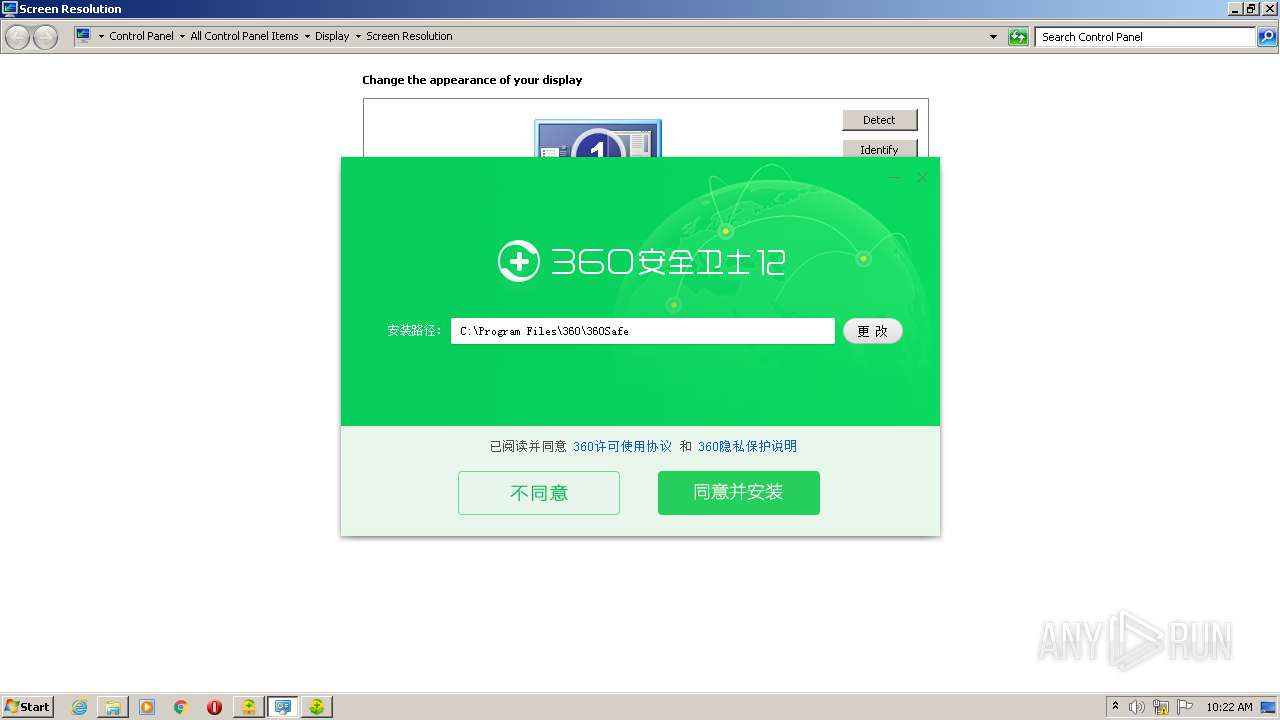
| CompanyName: | 360.cn |
| FileDescription: | 360 安全卫士在线安装程序 |
| FileVersion: | 12, 0, 0, 1191 |
| InternalName: | 360 Installer |
| LegalCopyright: | Copyright 2012 |
| OriginalFileName: | 360Installer.exe |
| ProductName: | 360 安全卫士在线安装程序 |
| ProductVersion: | 12, 0, 0, 1191 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 10-Aug-2020 10:56:14 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | 360.cn |
| FileDescription: | 360 安全卫士在线安装程序 |
| FileVersion: | 12, 0, 0, 1191 |
| InternalName: | 360 Installer |
| LegalCopyright: | Copyright 2012 |
| OriginalFilename: | 360Installer.exe |
| ProductName: | 360 安全卫士在线安装程序 |
| ProductVersion: | 12, 0, 0, 1191 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 10-Aug-2020 10:56:14 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000B8525 | 0x000B8600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.65874 |
.rdata | 0x000BA000 | 0x00022EB6 | 0x00023000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.71857 |
.data | 0x000DD000 | 0x0000D1CC | 0x00009600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.31059 |
.rsrc | 0x000EB000 | 0x00427F08 | 0x00428004 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.94949 |
.reloc | 0x00513000 | 0x0000C854 | 0x0000CA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 5.80136 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.26275 | 1064 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 4.56733 | 4264 | Latin 1 / Western European | Chinese - PRC | RT_ICON |
3 | 4.60391 | 1128 | Latin 1 / Western European | Chinese - PRC | RT_ICON |
4 | 4.16294 | 1384 | Latin 1 / Western European | Chinese - PRC | RT_ICON |
5 | 5.70608 | 1128 | Latin 1 / Western European | Chinese - PRC | RT_ICON |
9 | 5.80041 | 512 | Latin 1 / Western European | Chinese - PRC | RT_STRING |
10 | 5.78917 | 656 | Latin 1 / Western European | Chinese - PRC | RT_STRING |
11 | 5.86822 | 558 | Latin 1 / Western European | Chinese - PRC | RT_STRING |
12 | 6.37095 | 658 | Latin 1 / Western European | Chinese - PRC | RT_STRING |
13 | 6.15143 | 578 | Latin 1 / Western European | Chinese - PRC | RT_STRING |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
IPHLPAPI.DLL |
KERNEL32.dll |
MSIMG32.dll |
OLEAUT32.dll |
PSAPI.DLL |
SETUPAPI.dll |
SHELL32.dll |
Total processes
76
Monitored processes
36
Malicious processes
23
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 476 | C:\Windows\system32\services.exe | C:\Windows\System32\services.exe | — | wininit.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Services and Controller app Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 976 | C:\Windows\system32\DllHost.exe /Processid:{AB8902B4-09CA-4BB6-B78D-A8F59079A8D5} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1208 | "C:\Program Files\Common Files\Microsoft Shared\OfficeSoftwareProtectionPlatform\OSPPSVC.EXE" | C:\Program Files\Common Files\Microsoft Shared\OfficeSoftwareProtectionPlatform\OSPPSVC.EXE | — | services.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Office Software Protection Platform Service Exit code: 0 Version: 14.0.0370.400 (longhorn(wmbla).090811-1833) Modules
| |||||||||||||||
| 1228 | "C:\Program Files\360\360Safe\SoftMgr\SoftupNotify.exe" /install | C:\Program Files\360\360Safe\SoftMgr\SoftupNotify.exe | setup.exe | ||||||||||||
User: admin Company: 360.cn Integrity Level: HIGH Description: 360软件管家 Exit code: 0 Version: 2, 6, 0, 1950 Modules
| |||||||||||||||
| 1356 | "C:\Program Files\360\360Safe\Utils\360IA.exe" /src=probe /dpi=96 | C:\Program Files\360\360Safe\Utils\360IA.exe | — | 360tray.exe | |||||||||||
User: admin Company: 360.cn Integrity Level: HIGH Description: 360安全卫士 智能助手模块 Exit code: 0 Version: 12.0.0.1060 Modules
| |||||||||||||||
| 1396 | "C:\Program Files\360\360Safe\deepscan\zhudongfangyu.exe" /Start | C:\Program Files\360\360Safe\deepscan\zhudongfangyu.exe | — | setup.exe | |||||||||||
User: admin Company: 360.cn Integrity Level: HIGH Description: 360主动防御服务模块 Exit code: 0 Version: 3, 2, 2, 3055 Modules
| |||||||||||||||
| 1408 | "C:\Program Files\360\360Safe\SoftMgr\SML\SoftMgrLite.exe" | C:\Program Files\360\360Safe\SoftMgr\SML\SoftMgrLite.exe | 360tray.exe | ||||||||||||
User: admin Company: 360.cn Integrity Level: HIGH Description: 360软件小助手 Exit code: 0 Version: 3, 1, 0, 2090 Modules
| |||||||||||||||
| 1448 | "C:\Program Files\360\360Safe\Utils\360seclogon\360SecLogonHelper.exe" | C:\Program Files\360\360Safe\Utils\360seclogon\360SecLogonHelper.exe | setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 360安全卫士 系统安全登录辅助模块 Exit code: 0 Version: 1, 0, 0, 1037 Modules
| |||||||||||||||
| 1788 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\nagree.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
16 449
Read events
8 398
Write events
7 810
Delete events
241
Modification events
| (PID) Process: | (3844) inst.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3844) inst.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3844) inst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\360Safe\Liveup |
| Operation: | write | Name: | mid |
Value: b8c075ec50c0ffb37ec9c97cc27794fb6cf17a81aa848e72eb1b37cb1695e6ee | |||
| (PID) Process: | (3844) inst.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3844) inst.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3844) inst.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3844) inst.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3844) inst.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3844) inst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager |
| Operation: | write | Name: | PendingFileRenameOperations |
Value: \??\C:\Users\admin\AppData\Local\Temp\{31233B41-BBDB-4590-AC8E-D13808D26E6D}.tmp\360P2SP.dll | |||
| (PID) Process: | (3844) inst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\LiveUpdate360 |
| Operation: | write | Name: | proxytype |
Value: 1 | |||
Executable files
1 016
Suspicious files
1 161
Text files
1 431
Unknown types
107
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3844 | inst.exe | C:\Users\admin\AppData\Local\Temp\{6DA29EEA-41E3-4745-BF01-300E793DA2C2}.tmp | — | |
MD5:— | SHA256:— | |||
| 3844 | inst.exe | C:\Users\admin\AppData\Local\Temp\{E2C72B9A-D7C2-4ba9-A373-B74B005AE846}.tmp | — | |
MD5:— | SHA256:— | |||
| 3844 | inst.exe | C:\Program Files\360\360Safe\{42286722-76DE-4ad4-8D56-EA9EF09E1EFF}.tf | — | |
MD5:— | SHA256:— | |||
| 3844 | inst.exe | C:\Users\admin\AppData\Local\Temp\setup.exe.P2P | — | |
MD5:— | SHA256:— | |||
| 3844 | inst.exe | C:\Users\admin\AppData\Local\Temp\setup.exe | — | |
MD5:— | SHA256:— | |||
| 3844 | inst.exe | C:\Users\admin\AppData\Local\Temp\setup.exe.mem | — | |
MD5:— | SHA256:— | |||
| 3024 | setup.exe | C:\Users\admin\AppData\Local\Temp\{2AF7D413-3673-42d8-8D03-6F542E96079A}.tmp | — | |
MD5:— | SHA256:— | |||
| 3024 | setup.exe | C:\Users\admin\AppData\Local\Temp\{E403E0F7-5A1D-4464-B18B-EEFE20C46688}.tmp | — | |
MD5:— | SHA256:— | |||
| 3024 | setup.exe | C:\Users\admin\AppData\Local\Temp\{11DD124B-79F4-4b01-A27B-4E9F5E3E60E2}.tmp | — | |
MD5:— | SHA256:— | |||
| 3024 | setup.exe | C:\Users\admin\AppData\Local\Temp\{6020991B-08D5-4cb9-8DA6-347B6363FBF6}.tmp\miniui.xml | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
58
DNS requests
20
Threats
96
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3844 | inst.exe | GET | — | 180.163.235.152:80 | http://pinst.360.cn/360safe/safe_home_new.cab?rd=25317256 | CN | — | — | whitelisted |
3844 | inst.exe | GET | — | 171.8.167.89:80 | http://s.360.cn/safe/instcomp.htm?soft=1000&status=100&m=b8c075ec50c0ffb37ec9c97cc27794fb&from=safefinal_new&vv=10&installed=0&ver=12.0.0.1191 | CN | — | — | whitelisted |
3844 | inst.exe | GET | — | 171.8.167.89:80 | http://s.360.cn/safe/instcomp.htm?soft=1000&status=127&m=b8c075ec50c0ffb37ec9c97cc27794fb&from=safefinal_new&vv=10&installed=0&parent=explorer.exe&ver=12.0.0.1191 | CN | — | — | whitelisted |
3844 | inst.exe | GET | — | 180.163.235.151:80 | http://pinst.360.cn/360safe/safe_home_new.cab?rd=25317256 | CN | — | — | whitelisted |
3844 | inst.exe | GET | — | 104.192.108.21:80 | http://down.360safe.com/setup.exe | US | — | — | malicious |
3844 | inst.exe | GET | — | 104.192.108.21:80 | http://down.360safe.com/setup.exe | US | — | — | malicious |
3844 | inst.exe | GET | — | 104.192.108.21:80 | http://down.360safe.com/setup.exe | US | — | — | malicious |
3844 | inst.exe | GET | — | 104.192.108.21:80 | http://down.360safe.com/setup.exe | US | — | — | malicious |
3844 | inst.exe | GET | — | 104.192.108.21:80 | http://down.360safe.com/setup.exe | US | — | — | malicious |
3844 | inst.exe | GET | — | 104.192.108.21:80 | http://down.360safe.com/setup.exe | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3844 | inst.exe | 171.8.167.89:80 | s.360.cn | No.31,Jin-rong Street | CN | suspicious |
3844 | inst.exe | 1.192.136.136:3478 | st.p.360.cn | No.31,Jin-rong Street | CN | unknown |
3844 | inst.exe | 1.192.136.133:80 | tr.p.360.cn | No.31,Jin-rong Street | CN | unknown |
3844 | inst.exe | 180.163.235.151:80 | pinst.360.cn | China Telecom (Group) | CN | unknown |
3844 | inst.exe | 180.163.235.152:80 | pinst.360.cn | China Telecom (Group) | CN | unknown |
3844 | inst.exe | 104.192.108.21:80 | down.360safe.com | Beijing Qihu Technology Company Limited | US | malicious |
3024 | setup.exe | 171.8.167.89:80 | s.360.cn | No.31,Jin-rong Street | CN | suspicious |
1448 | 360SecLogonHelper.exe | 36.110.231.31:80 | s.f.360.cn | IDC, China Telecommunications Corporation | CN | suspicious |
2600 | 360Safe.exe | 36.110.231.31:80 | s.f.360.cn | IDC, China Telecommunications Corporation | CN | suspicious |
2600 | 360Safe.exe | 104.192.110.254:80 | conf.wsm.360.cn | Beijing Qihu Technology Company Limited | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s.360.cn |
| whitelisted |
st.p.360.cn |
| whitelisted |
tr.p.360.cn |
| suspicious |
agt.p.360.cn |
| whitelisted |
pinst.360.cn |
| whitelisted |
agd.p.360.cn |
| whitelisted |
down.360safe.com |
| malicious |
s.f.360.cn |
| suspicious |
skin.wsm.360.cn |
| suspicious |
static.360.cn |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3844 | inst.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag false) |
3844 | inst.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag true change port flag false) |
3844 | inst.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag true) |
3844 | inst.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1448 | 360SecLogonHelper.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
2648 | LiveUpdate360.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag false) |
2648 | LiveUpdate360.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag true change port flag false) |
2648 | LiveUpdate360.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag true) |
1448 | 360SecLogonHelper.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
1448 | 360SecLogonHelper.exe | Potentially Bad Traffic | AV POLICY HTTP traffic on port 443 to IP host (POST) |
Process | Message |
|---|---|
inst.exe | Begin Check |
inst.exe | Get Disk Space |
inst.exe | Is360SeExist : 0 |
inst.exe | Is360ChromeExist : 0 |
inst.exe | m_typePromote :1 |
SoftupNotify.exe | /install |
regsvr32.exe | 360softmgr.shellext.SafeExistThread |
regsvr32.exe | 360softmgr.shellext.SafeExistThread leave |