| File name: | Install_0007.exe |
| Full analysis: | https://app.any.run/tasks/0c9d7b22-46a1-461f-8602-dca34a31c400 |
| Verdict: | Malicious activity |
| Analysis date: | June 06, 2024, 12:25:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | E1B07111D364B557F502613E3C0E9564 |
| SHA1: | 8F9A41BEA4377398780FE35E553866FBA7E77907 |
| SHA256: | 45E2D4E071B2B312606BBEE55C6F527674479C9007E0F43BFD28BF0D547372F9 |
| SSDEEP: | 98304:zLH3dLg+qaojKOgVHtLZ3kROoXtaTMkpjeHIYDCls5mtddENZfoK+IH5fdiQYmN/:zMd/VlR/L1wTM4RY |
MALICIOUS
Drops the executable file immediately after the start
- Install_0007.exe (PID: 6384)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- Install_0007.exe (PID: 6384)
Creates/Modifies COM task schedule object
- Install_0007.exe (PID: 6384)
Executable content was dropped or overwritten
- Install_0007.exe (PID: 6384)
INFO
Checks supported languages
- Install_0007.exe (PID: 6384)
Reads the computer name
- Install_0007.exe (PID: 6384)
Creates files or folders in the user directory
- Install_0007.exe (PID: 6384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:08:28 12:18:49+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 939520 |
| InitializedDataSize: | 6601728 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xcf6bc |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 21.7.0.0 |
| ProductVersionNumber: | 21.7.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Igor Pavlov |
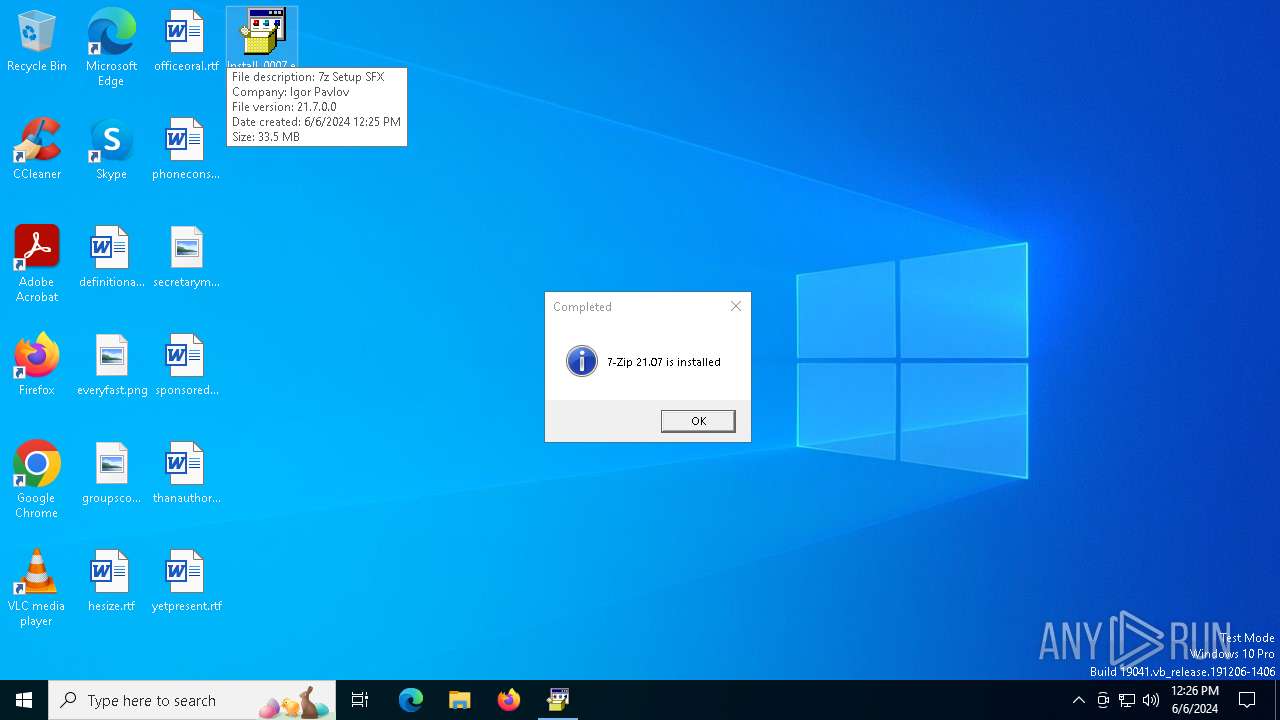
| FileDescription: | 7z Setup SFX |
| FileVersion: | 21.07 |
| InternalName: | 7zS.sfx |
| LegalCopyright: | Copyright (c) 1999-2021 Igor Pavlov |
| OriginalFileName: | 7zS.sfx.exe |
| ProductName: | 7-Zip |
| ProductVersion: | 21.07 |
Total processes
112
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6384 | "C:\Users\admin\Desktop\Install_0007.exe" | C:\Users\admin\Desktop\Install_0007.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7z Setup SFX Exit code: 0 Version: 21.07 Modules
| |||||||||||||||
Total events
1 721
Read events
1 717
Write events
4
Delete events
0
Modification events
| (PID) Process: | (6384) Install_0007.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Users\admin\AppData\Roaming\7zip | |||
| (PID) Process: | (6384) Install_0007.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path32 |
Value: C:\Users\admin\AppData\Roaming\7zip | |||
| (PID) Process: | (6384) Install_0007.exe | Key: | HKEY_CLASSES_ROOT\WOW6432Node\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (6384) Install_0007.exe | Key: | HKEY_CLASSES_ROOT\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
Executable files
9
Suspicious files
3
Text files
97
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6384 | Install_0007.exe | C:\Users\admin\AppData\Roaming\7zip\Lang\an.txt | text | |
MD5:BF8564B2DAD5D2506887F87AEE169A0A | SHA256:0E8DD119DFA6C6C1B3ACA993715092CDF1560947871092876D309DBC1940A14A | |||
| 6384 | Install_0007.exe | C:\Users\admin\AppData\Roaming\7zip\descript.ion | text | |
MD5:EB7E322BDC62614E49DED60E0FB23845 | SHA256:1DA513F5A4E8018B9AE143884EB3EAF72454B606FD51F2401B7CFD9BE4DBBF4F | |||
| 6384 | Install_0007.exe | C:\Users\admin\AppData\Roaming\7zip\Lang\ast.txt | text | |
MD5:1F86AE235BC747A279C9E9EC72675CE4 | SHA256:8FCD1B8CE6FED05F406C4B81AEA821132800BC494D3FD6F42A4258A81F8998EC | |||
| 6384 | Install_0007.exe | C:\Users\admin\AppData\Roaming\7zip\Lang\ar.txt | text | |
MD5:1C45E6A6ECB3B71A7316C466B6A77C1C | SHA256:972261B53289DE2BD8A65E787A6E7CD6DEFC2B5F7E344128F2FE0492ED30CCF1 | |||
| 6384 | Install_0007.exe | C:\Users\admin\AppData\Roaming\7zip\Lang\af.txt | text | |
MD5:FBBE51ACB879B525CC6B19D386697924 | SHA256:3793FB69EE9FD958CF15A272B1ED54E4B3D75592836EBCD085DC0E7B1400D1CB | |||
| 6384 | Install_0007.exe | C:\Users\admin\AppData\Roaming\7zip\7-zip.chm | binary | |
MD5:E8B5CF54C6BF22492B373715B8B59DC0 | SHA256:4F5C2170EFC2B6AF63873AADFED45E398BA73B414A87EE1E95C4A3AF3D5C7EC3 | |||
| 6384 | Install_0007.exe | C:\Users\admin\AppData\Roaming\7zip\Lang\cy.txt | text | |
MD5:0F5662A68805D859F871EDC07E766A57 | SHA256:931DE741A6C8F1348A946623776FE36C55DD2FC384C7B1478225F7467853199E | |||
| 6384 | Install_0007.exe | C:\Users\admin\AppData\Roaming\7zip\History.txt | text | |
MD5:D68C7D03873EB191F46BCC0CB6A89664 | SHA256:5355372CAD5A5142BC7A0991BD84DBB751BF65A4C272E9C7EDDF48CEE79DD24B | |||
| 6384 | Install_0007.exe | C:\Users\admin\AppData\Roaming\7zip\Lang\da.txt | text | |
MD5:D8ABA2DA47C1031832957B75A6524737 | SHA256:F65026AE33D4302A7EF06A856F6F062C9730100F5A87D5C00FB3FEAF5FCD5805 | |||
| 6384 | Install_0007.exe | C:\Users\admin\AppData\Roaming\7zip\Lang\be.txt | text | |
MD5:3C21135144AC7452E7DB66F0214F9D68 | SHA256:D095879B8BBC67A1C9875C5E9896942BACF730BD76155C06105544408068C59E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
25
DNS requests
8
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5140 | MoUsoCoreWorker.exe | GET | 200 | 23.45.119.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 184.29.138.50:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 200 | 172.67.75.22:443 | https://apponlineboutique.com/E0B1691BCA236D52/47957980191/D24CE03ADB209B34/71767675643?F646640742051BDD1717676756 | unknown | text | 32 b | unknown |
— | — | POST | 204 | 23.221.24.56:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
— | — | GET | 200 | 23.221.24.56:443 | https://www.bing.com/manifest/threshold.appcache | unknown | text | 3.36 Kb | unknown |
— | — | GET | 200 | 23.221.24.83:443 | https://r.bing.com/rb/17/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DygxdoIBhQGIAX95fLsBvgExrgExwQE&or=w | unknown | s | 21.3 Kb | unknown |
— | — | GET | 200 | 23.221.24.56:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | s | 21.3 Kb | unknown |
— | — | POST | 200 | 52.168.117.170:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2384 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
5140 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5140 | MoUsoCoreWorker.exe | 23.45.119.176:80 | crl.microsoft.com | Akamai International B.V. | US | unknown |
5140 | MoUsoCoreWorker.exe | 184.29.138.50:80 | www.microsoft.com | AKAMAI-AS | US | unknown |
6384 | Install_0007.exe | 172.67.75.22:443 | apponlineboutique.com | CLOUDFLARENET | US | unknown |
5456 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
apponlineboutique.com |
| unknown |
r.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA HTTP Request abnormal Content-Encoding header |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request abnormal Content-Encoding header |
1 ETPRO signatures available at the full report