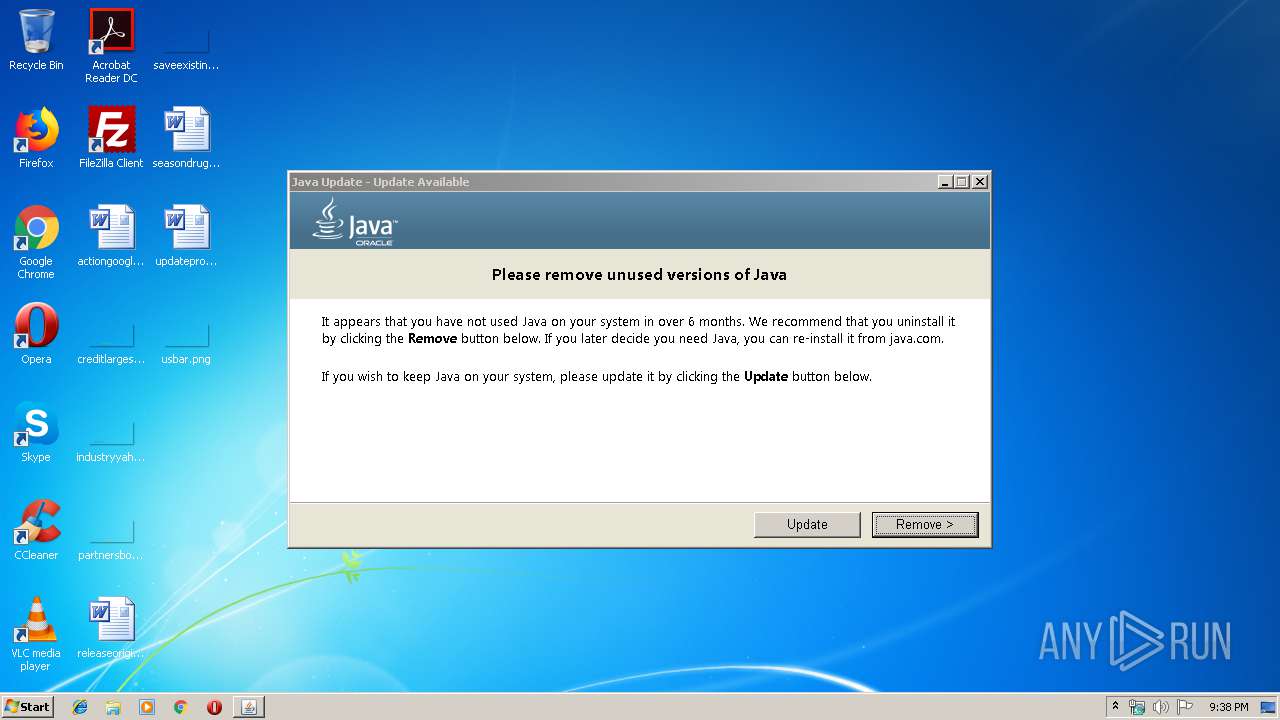
| File name: | jre-8u221-windows-au.exe |
| Full analysis: | https://app.any.run/tasks/80277ba9-44c7-494d-a49a-ce3ec2a5eebd |
| Verdict: | No threats detected |
| Analysis date: | July 18, 2019, 20:38:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A2E96353BAD5C7E0759048F4EFE7B7B9 |
| SHA1: | AAF26783FFD3F10D390C300A7F54CBFA708C1603 |
| SHA256: | 45B6654A9AC7231C6CD34BF6FCEBD9845C6D2A39F5FD734674C0207ED6E989D8 |
| SSDEEP: | 49152:eWauDwPQ9I3FKlFCX5cAdjWcTh4qCwEztVxnD:u72FCXWAdjW3z5D |
MALICIOUS
Application was dropped or rewritten from another process
- jre-8u221-windows-au.exe (PID: 2348)
SUSPICIOUS
Executable content was dropped or overwritten
- jre-8u221-windows-au.exe (PID: 2140)
Reads internet explorer settings
- jre-8u221-windows-au.exe (PID: 2348)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (54.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (34.8) |
| .exe | | | Win32 Executable (generic) (5.6) |
| .exe | | | Generic Win/DOS Executable (2.5) |
| .exe | | | DOS Executable Generic (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:07:05 07:23:52+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 137728 |
| InitializedDataSize: | 1934336 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe588 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.0.2210.11 |
| ProductVersionNumber: | 8.0.2210.11 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Oracle Corporation |
| FileDescription: | Java Platform SE binary |
| FileVersion: | 8.0.2210.11 |
| FullVersion: | 1.8.0_221-b11 |
| InternalName: | Setup Launcher |
| LegalCopyright: | Copyright © 2019 |
| OriginalFileName: | online_wrapper-forau.exe |
| ProductName: | Java Platform SE 8 U221 |
| ProductVersion: | 8.0.2210.11 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 05-Jul-2019 05:23:52 |
| Detected languages: |
|
| CompanyName: | Oracle Corporation |
| FileDescription: | Java Platform SE binary |
| FileVersion: | 8.0.2210.11 |
| Full Version: | 1.8.0_221-b11 |
| InternalName: | Setup Launcher |
| LegalCopyright: | Copyright © 2019 |
| OriginalFilename: | online_wrapper-forau.exe |
| ProductName: | Java Platform SE 8 U221 |
| ProductVersion: | 8.0.2210.11 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 05-Jul-2019 05:23:52 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000219ED | 0x00021A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.63037 |
.rdata | 0x00023000 | 0x00008B4C | 0x00008C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.83377 |
.data | 0x0002C000 | 0x00003D40 | 0x00001C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.18449 |
.rsrc | 0x00030000 | 0x001C7330 | 0x001C7400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.73841 |
.reloc | 0x001F8000 | 0x000044B4 | 0x00004600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 3.90837 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.8258 | 382 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 2.96826 | 744 | UNKNOWN | English - United States | RT_ICON |
3 | 2.90069 | 488 | UNKNOWN | English - United States | RT_ICON |
4 | 3.0155 | 296 | UNKNOWN | English - United States | RT_ICON |
5 | 5.58618 | 3752 | UNKNOWN | English - United States | RT_ICON |
6 | 5.53853 | 2216 | UNKNOWN | English - United States | RT_ICON |
7 | 3.94465 | 1736 | UNKNOWN | English - United States | RT_ICON |
8 | 2.81361 | 1384 | UNKNOWN | English - United States | RT_ICON |
9 | 5.4261 | 9640 | UNKNOWN | English - United States | RT_ICON |
10 | 5.68846 | 4264 | UNKNOWN | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
KERNEL32.dll |
Total processes
38
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2140 | "C:\Users\admin\AppData\Local\Temp\jre-8u221-windows-au.exe" | C:\Users\admin\AppData\Local\Temp\jre-8u221-windows-au.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.2210.11 Modules
| |||||||||||||||
| 2348 | "C:\Users\admin\AppData\Local\Temp\jds1560937.tmp\jre-8u221-windows-au.exe" | C:\Users\admin\AppData\Local\Temp\jds1560937.tmp\jre-8u221-windows-au.exe | jre-8u221-windows-au.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.2210.11 Modules
| |||||||||||||||
| 3728 | "C:\Users\admin\AppData\Local\Temp\jre-8u221-windows-au.exe" | C:\Users\admin\AppData\Local\Temp\jre-8u221-windows-au.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Platform SE binary Exit code: 3221226540 Version: 8.0.2210.11 Modules
| |||||||||||||||
Total events
129
Read events
101
Write events
28
Delete events
0
Modification events
| (PID) Process: | (2348) jre-8u221-windows-au.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jre-8u221-windows-au_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2348) jre-8u221-windows-au.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jre-8u221-windows-au_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2348) jre-8u221-windows-au.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jre-8u221-windows-au_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2348) jre-8u221-windows-au.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jre-8u221-windows-au_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2348) jre-8u221-windows-au.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jre-8u221-windows-au_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2348) jre-8u221-windows-au.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jre-8u221-windows-au_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2348) jre-8u221-windows-au.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jre-8u221-windows-au_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2348) jre-8u221-windows-au.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jre-8u221-windows-au_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2348) jre-8u221-windows-au.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jre-8u221-windows-au_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2348) jre-8u221-windows-au.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\jre-8u221-windows-au_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
1
Suspicious files
0
Text files
114
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2140 | jre-8u221-windows-au.exe | C:\Users\admin\AppData\Local\Temp\jds1560937.tmp\jds1560937.tmp | — | |
MD5:— | SHA256:— | |||
| 2140 | jre-8u221-windows-au.exe | C:\Users\admin\AppData\Local\Temp\jusched.log | text | |
MD5:— | SHA256:— | |||
| 2348 | jre-8u221-windows-au.exe | C:\Users\admin\AppData\Local\Temp\jusched.log | text | |
MD5:— | SHA256:— | |||
| 2140 | jre-8u221-windows-au.exe | C:\Users\admin\AppData\Local\Temp\jds1560937.tmp\jre-8u221-windows-au.exe | executable | |
MD5:— | SHA256:— | |||
| 2348 | jre-8u221-windows-au.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\host[1] | text | |
MD5:A752A4469AC0D91DD2CB1B766BA157DE | SHA256:1E67043252582AEA0E042F5A7BE4A849B7CD01B133A489C3B2E67C10ADE086F3 | |||
| 2348 | jre-8u221-windows-au.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\rtutils[1] | text | |
MD5:C0A4CEBB2C15BE8262BF11DE37606E07 | SHA256:7DA9AA32AA10B69F34B9D3602A3B8A15EB7C03957512714392F12458726AC5F1 | |||
| 2348 | jre-8u221-windows-au.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\remove[1] | html | |
MD5:49572CA5693BC144C9441A38985C3E82 | SHA256:7A6A0277E175DCC72DB02D306619DD62606F117CA7B4D2A9A1330AA4F90ECEE8 | |||
| 2348 | jre-8u221-windows-au.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\runtime[1] | text | |
MD5:7C1C66944BF6D37D5C665A4C7D5810D3 | SHA256:196A6A4918EB72D430CE1EF49EADBAF27C70F6E14F5383AA08213072DCC9841C | |||
| 2348 | jre-8u221-windows-au.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\l10n[1] | html | |
MD5:1FD5111B757493A27E697D57B351BB56 | SHA256:85BBEC802E8624E7081ABEAE4F30BD98D9A9DF6574BD01FE5251047E8FDAF59F | |||
| 2348 | jre-8u221-windows-au.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\common[1] | text | |
MD5:F5BB484D82E7842A602337E34D11A8F6 | SHA256:219108BFEF63F97562C4532681B03675C9E698C5AE495205853DBCBFD93FAF1A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2348 | jre-8u221-windows-au.exe | 23.38.48.207:443 | javadl-esd-secure.oracle.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
javadl-esd-secure.oracle.com |
| whitelisted |