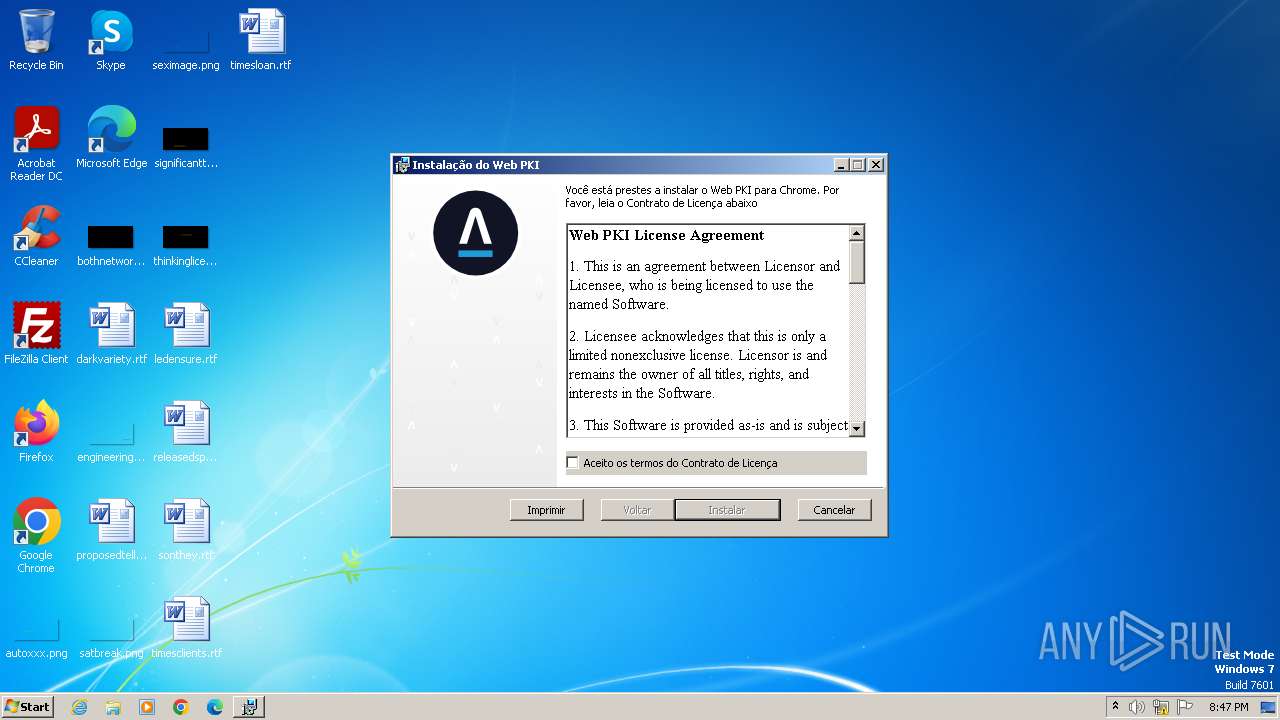
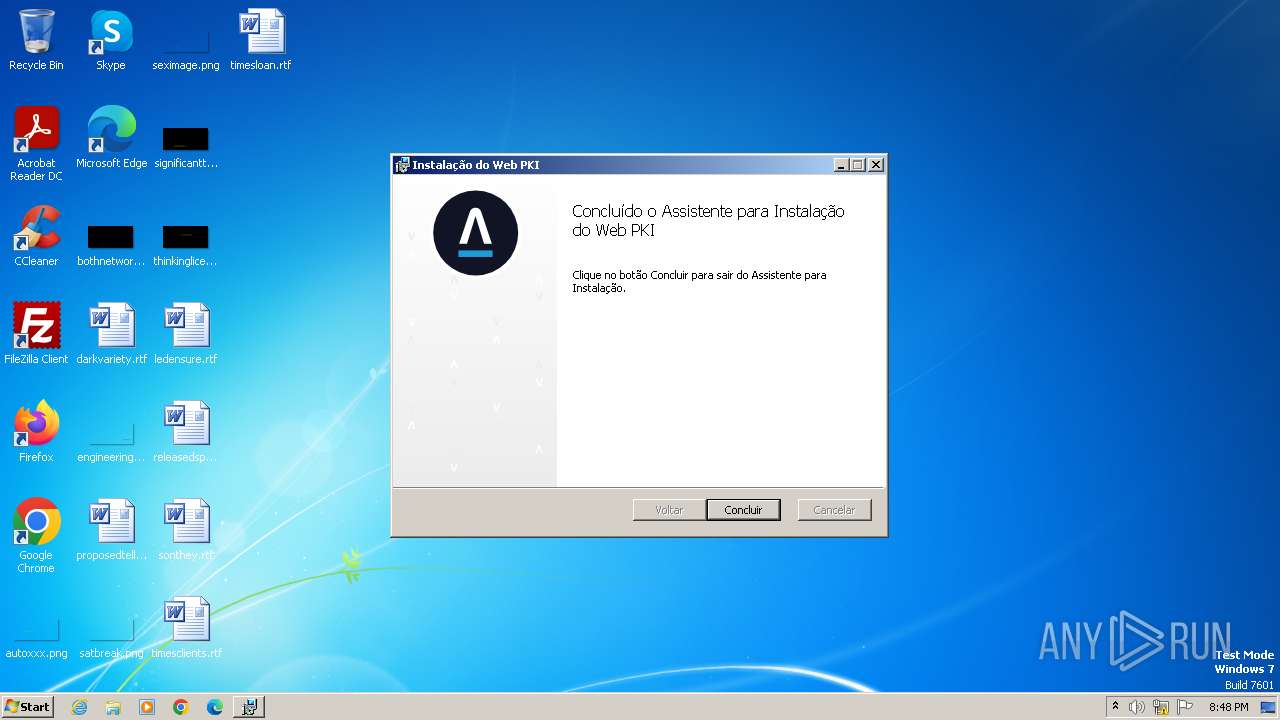
| File name: | WebPkiSetup_2.12.3_pt.msi |
| Full analysis: | https://app.any.run/tasks/1cbbea67-3539-4b5b-b147-096bf2551aa6 |
| Verdict: | Malicious activity |
| Analysis date: | November 23, 2023, 20:47:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Web PKI, Author: Lacuna Software, Keywords: Installer, Comments: This installer database contains the logic and data required to install Web PKI., Template: Intel;1033, Revision Number: {394F7544-0072-4360-98A3-0547DE7BBBA9}, Create Time/Date: Tue Oct 31 18:07:36 2023, Last Saved Time/Date: Tue Oct 31 18:07:36 2023, Number of Pages: 200, Number of Words: 10, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | 7089F4F475FBEF782F992407FF30BFB3 |
| SHA1: | 0B9C624B01B5BE170CF0B19AA753DAC820847129 |
| SHA256: | 45A1F4A415244143EC8A010F27270746B673E287303EFE64DD34E670FC03D7DF |
| SSDEEP: | 98304:IcOg1VONBs9rNv5q5yKmRdZ4vdViPh/IYsaWd54SV1MbVqYnQrx12R5MruQEJ+MQ:pbSz2OzgYJ |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3484)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 3124)
The process creates files with name similar to system file names
- msiexec.exe (PID: 3484)
Checks Windows Trust Settings
- msiexec.exe (PID: 3484)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3440)
Create files in a temporary directory
- msiexec.exe (PID: 3484)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3484)
Creates files or folders in the user directory
- msiexec.exe (PID: 3484)
Reads the computer name
- msiexec.exe (PID: 3484)
Checks supported languages
- msiexec.exe (PID: 3484)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Web PKI |
| Author: | Lacuna Software |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Web PKI. |
| Template: | Intel;1033 |
| RevisionNumber: | {394F7544-0072-4360-98A3-0547DE7BBBA9} |
| CreateDate: | 2023:10:31 18:07:36 |
| ModifyDate: | 2023:10:31 18:07:36 |
| Pages: | 200 |
| Words: | 10 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
37
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3124 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3440 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\WebPkiSetup_2.12.3_pt.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3484 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 649
Read events
8 600
Write events
39
Delete events
10
Modification events
| (PID) Process: | (3440) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3484) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3484) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3484) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 72 | |||
| (PID) Process: | (3484) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008C62D6BA16B0D901C80700002C0A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3484) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3484) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Enter) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D4070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3484) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Leave) |
Value: 400000000000000034645DBC16B0D901C80700002C0A0000D4070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3484) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Leave) |
Value: 4000000000000000781D5ABD16B0D901C80700002C0A0000D0070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3484) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Leave) |
Value: 4000000000000000781D5ABD16B0D901C80700002C0A0000D5070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
14
Suspicious files
12
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3484 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3484 | msiexec.exe | C:\Windows\Installer\16aa5e.msi | — | |
MD5:— | SHA256:— | |||
| 3484 | msiexec.exe | C:\Windows\Installer\16aa5f.ipi | binary | |
MD5:B3CC2BCA701A25A7C910AECA5729CC13 | SHA256:6DF89FA83BDB902F643A451FEAD187FA3C9AC87441F4E22BC2611C31F6AE0C36 | |||
| 3484 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:1697E1C27CF3E20B1775C09970D12982 | SHA256:CDF56E024F58AC3DFAFA581DDDDFE2B99681EDA36FD54E377918ABAE731F6404 | |||
| 3484 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{a47eb118-b979-46e1-bec1-2368e1ca4c1f}_OnDiskSnapshotProp | binary | |
MD5:1697E1C27CF3E20B1775C09970D12982 | SHA256:CDF56E024F58AC3DFAFA581DDDDFE2B99681EDA36FD54E377918ABAE731F6404 | |||
| 3484 | msiexec.exe | C:\Users\admin\AppData\Local\Lacuna Software\Web PKI\Lacuna.Capi.dll | executable | |
MD5:93485D40696CE668F5991EA23FF3390C | SHA256:C6901333A60AFE86ACC815E4159FBAC95B2BD660C8219F4767C73F29EDB38343 | |||
| 3484 | msiexec.exe | C:\Windows\Installer\16aa61.msi | — | |
MD5:— | SHA256:— | |||
| 3484 | msiexec.exe | C:\Users\admin\AppData\Local\Lacuna Software\Web PKI\Lacuna.WebPKI.ChromeWin.exe.config | xml | |
MD5:0BE55431DF6BB76393CC2A30B5971E76 | SHA256:417A2945343C1E53FB8EE20F082A963FC312BCAD2549621DC18FBEB5BB6EE125 | |||
| 3484 | msiexec.exe | C:\Users\admin\AppData\Local\Lacuna Software\Web PKI\Pkcs11Interop.dll | executable | |
MD5:5E6BDAB1F9C593617BCE16FBAF392D75 | SHA256:67408BE53E8C65B17000EC7BC435786B96763544B60C916B9E2F9C2C60286D9F | |||
| 3484 | msiexec.exe | C:\Users\admin\AppData\Local\Lacuna Software\Web PKI\Lacuna.Pki.Pkcs11.dll | executable | |
MD5:4513ACD9C4233CF298CDF0217C2F9B98 | SHA256:EA68C7FA46B604CC3E23F39F1F96FE3F36FC4E35F9D43A1AAF417FD0C5BA6FED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |