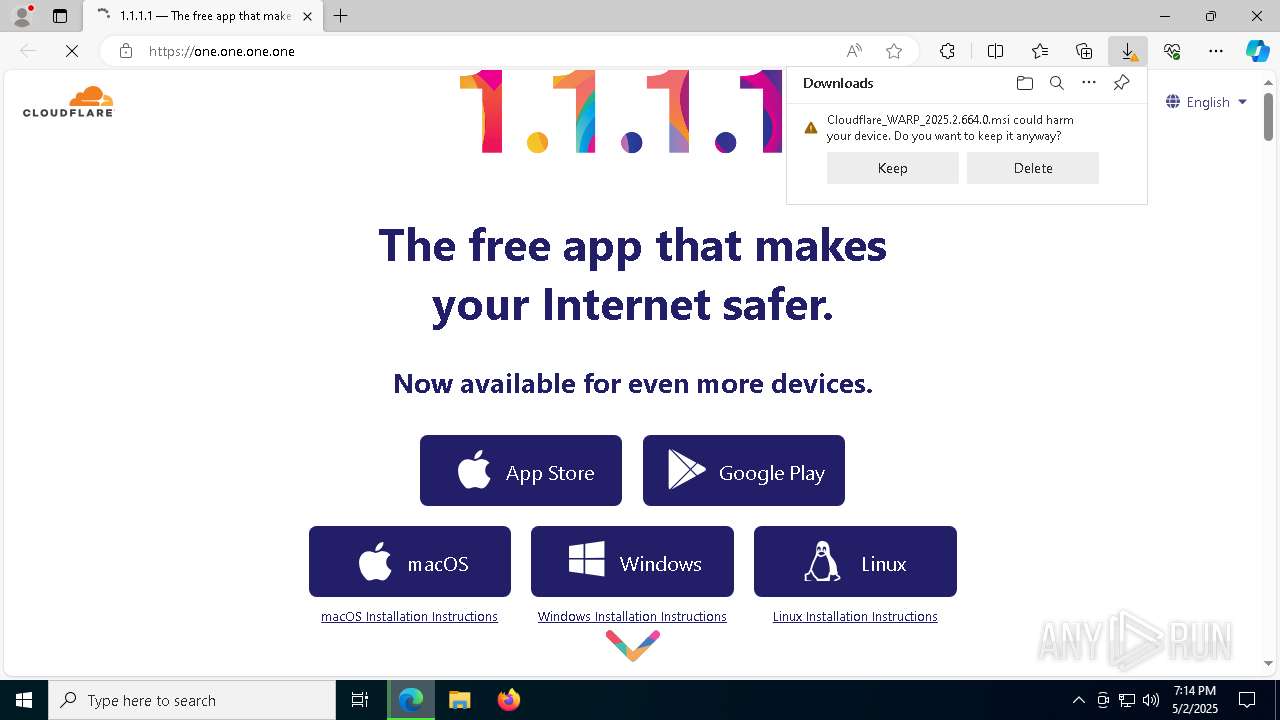
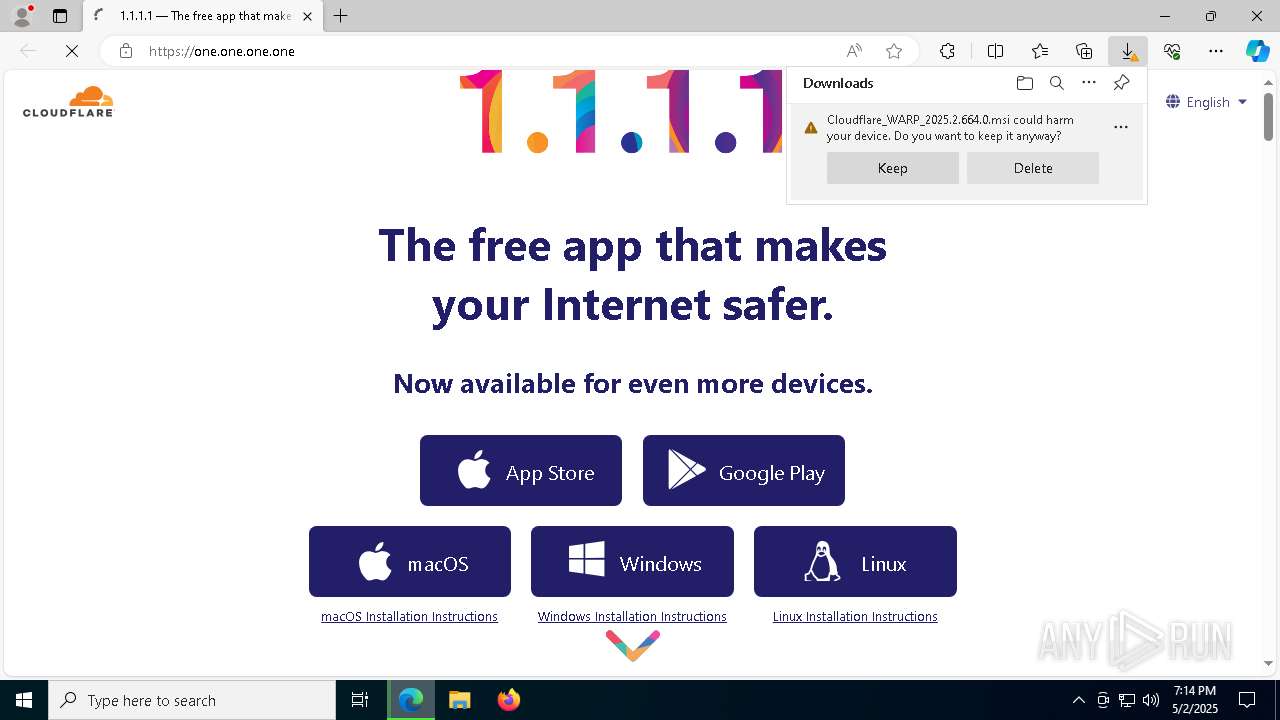
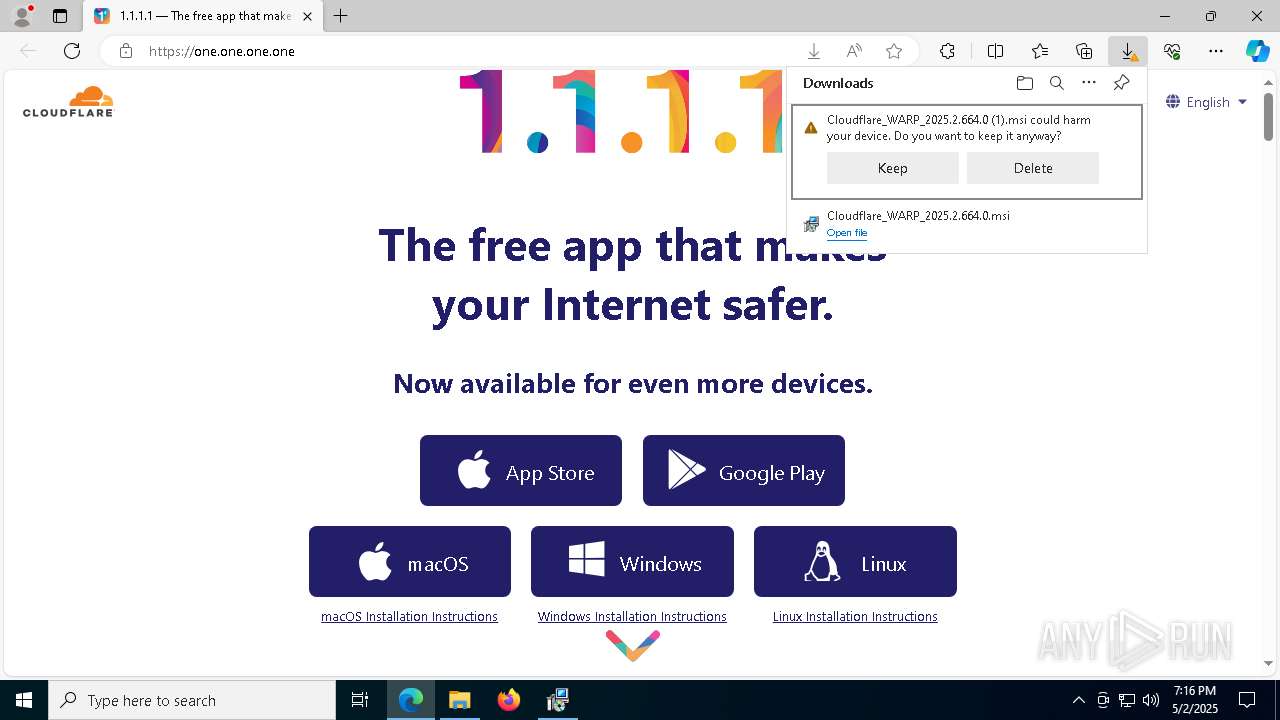
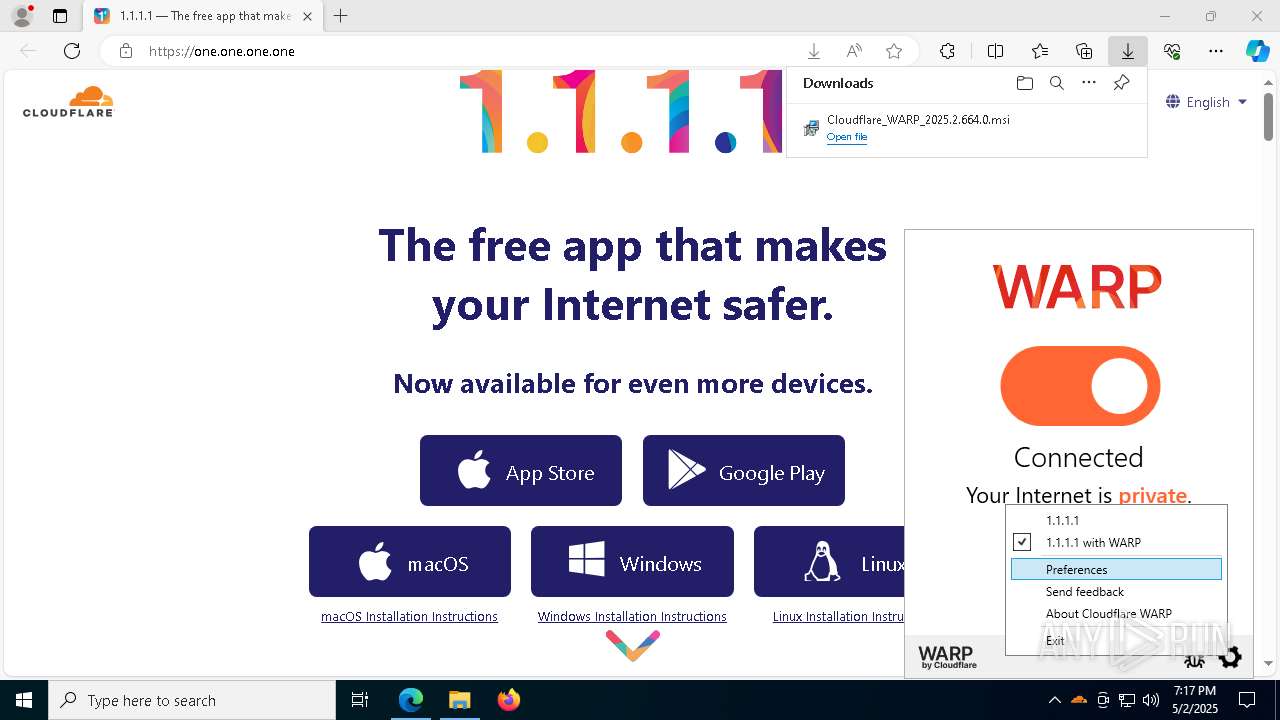
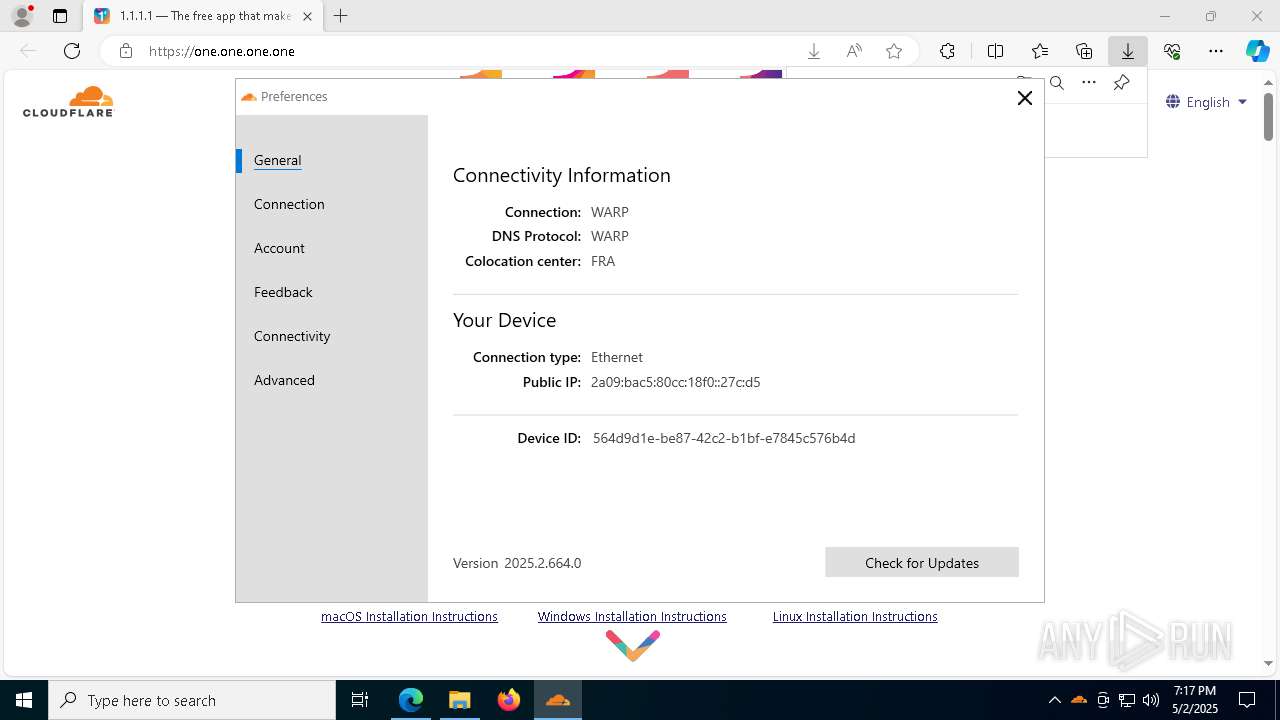
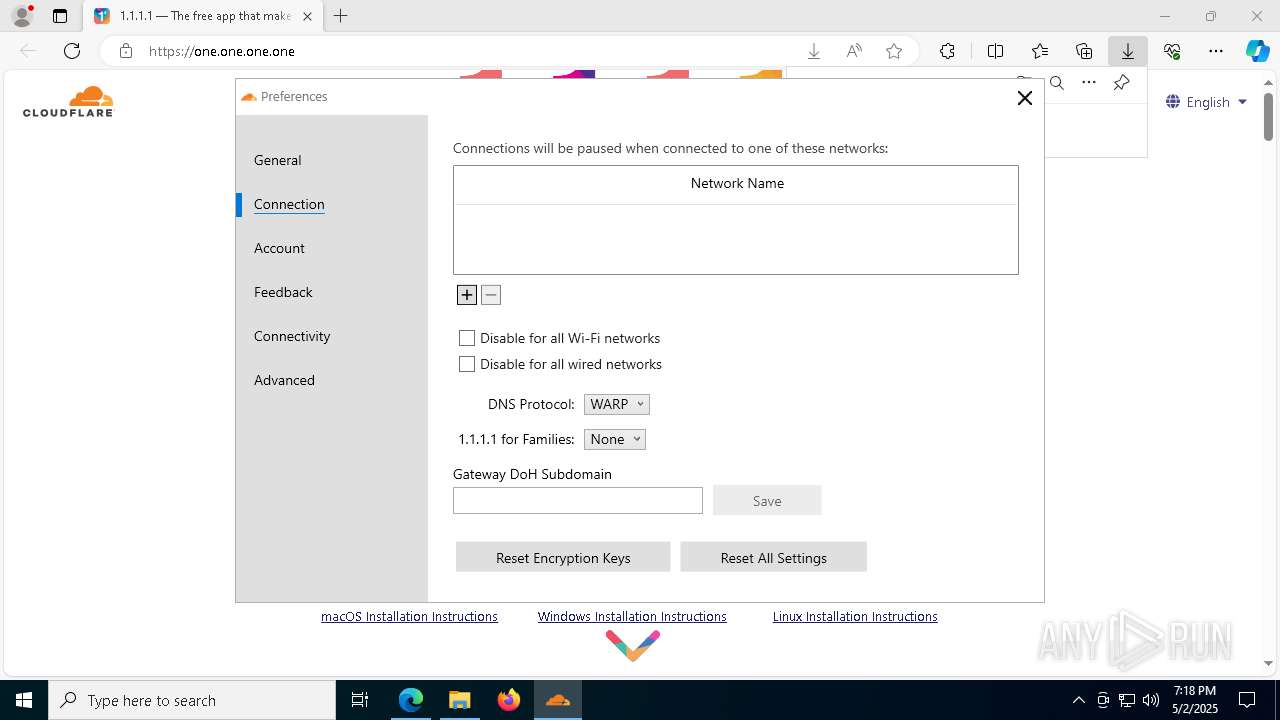
| URL: | https://one.one.one.one/ |
| Full analysis: | https://app.any.run/tasks/7c83cf7b-9377-4b9a-8159-7c8cf0e31076 |
| Verdict: | Malicious activity |
| Analysis date: | May 02, 2025, 19:14:27 |
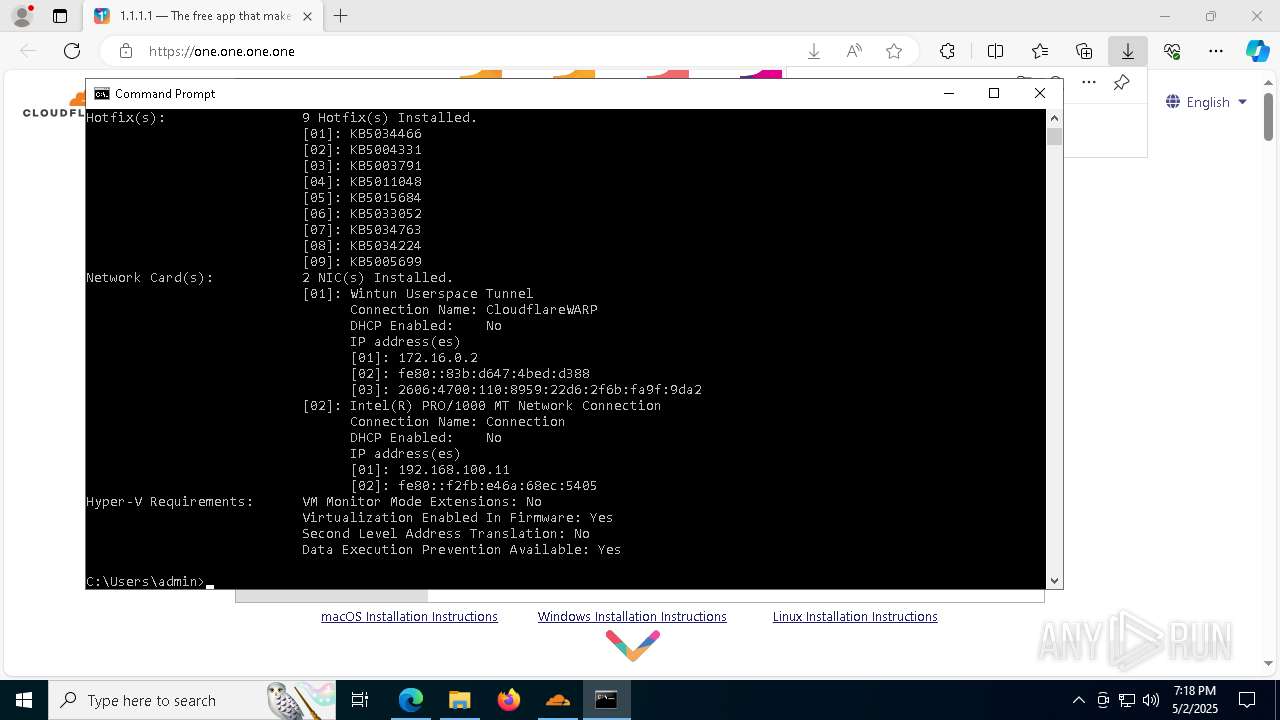
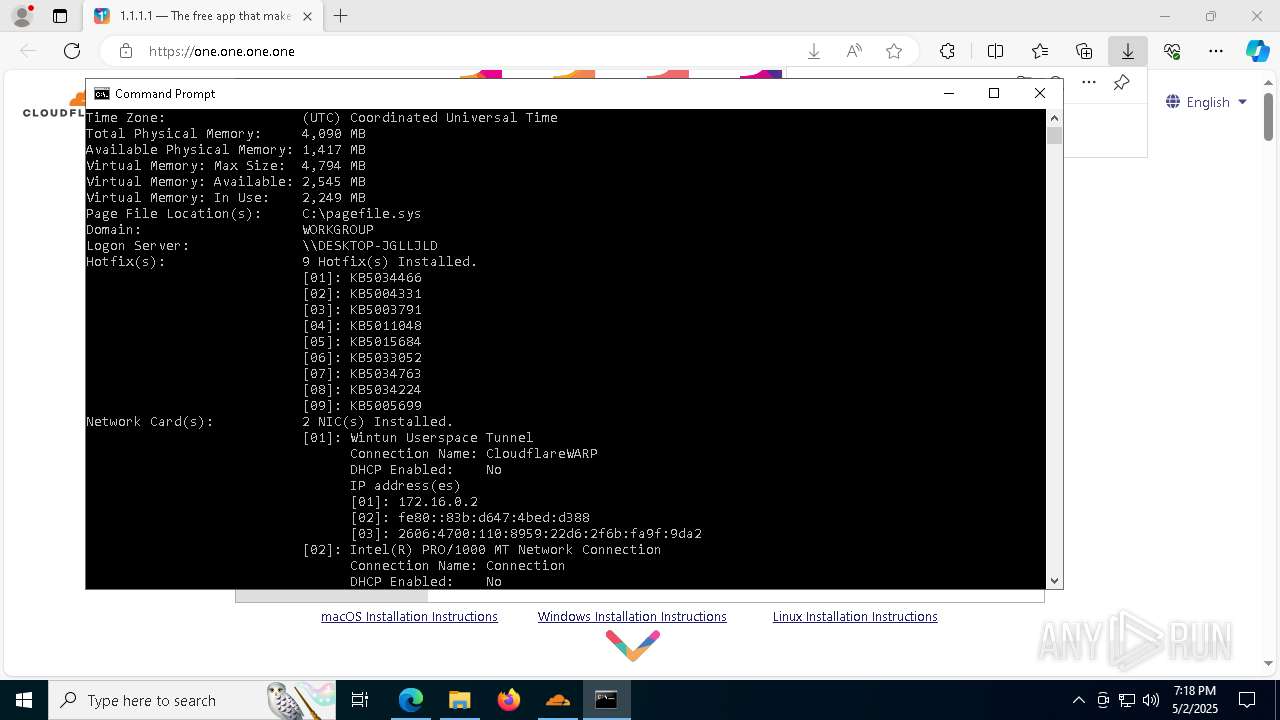
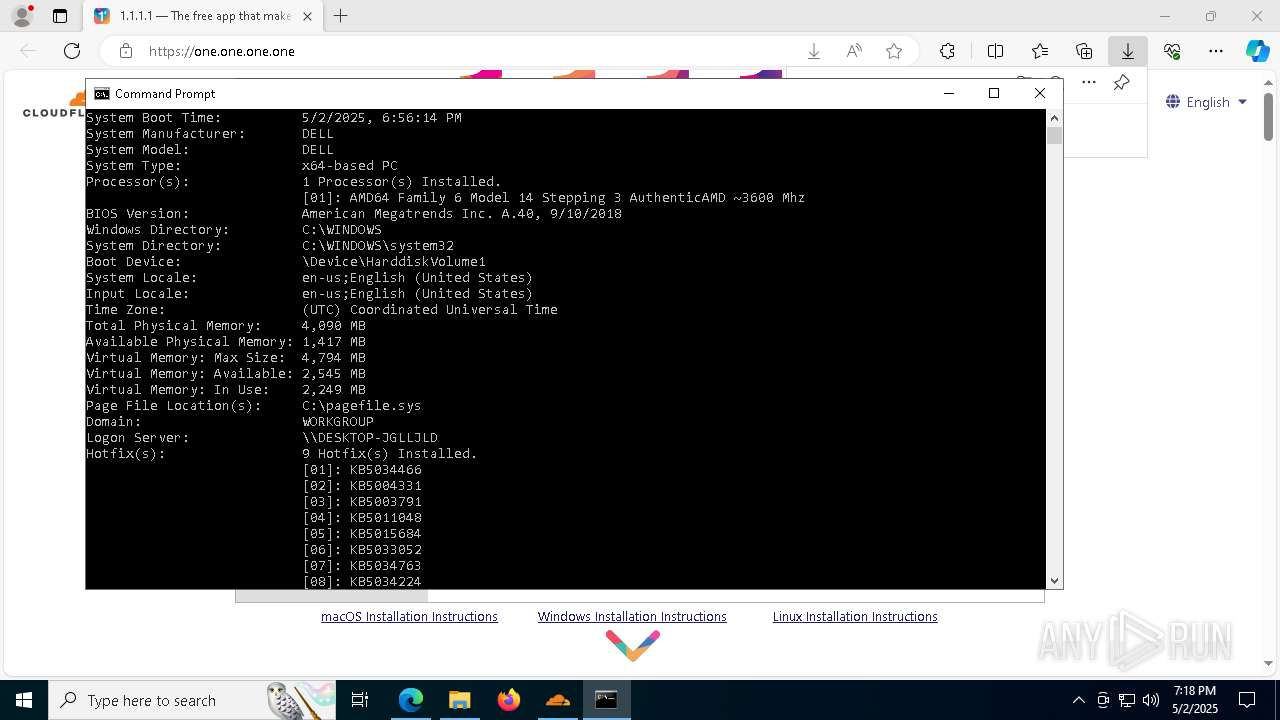
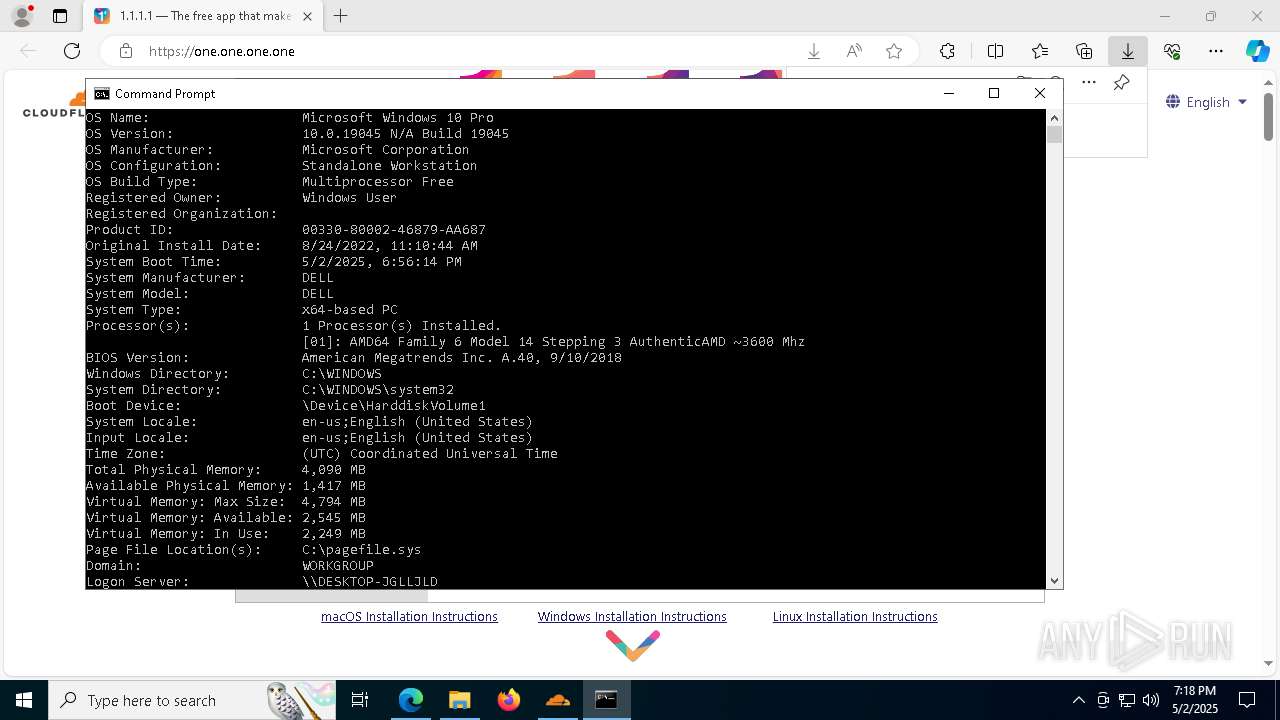
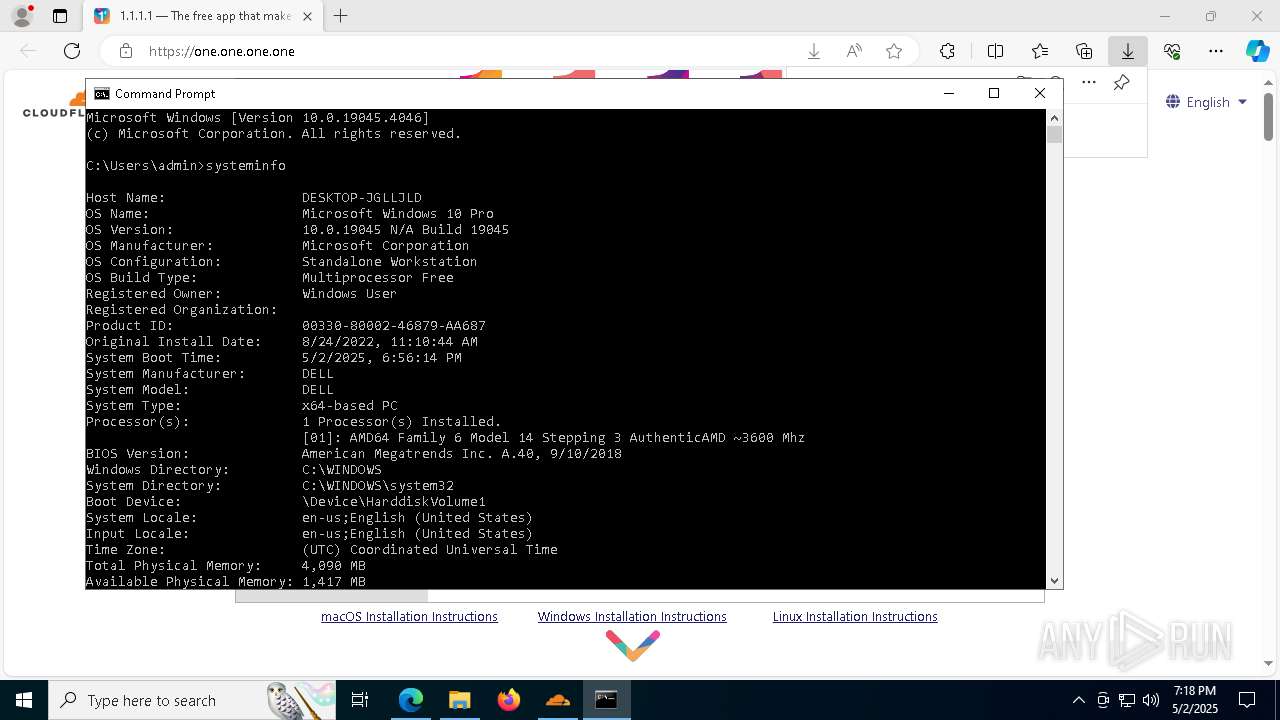
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | 7EB8C3836CAE930C02577B46EF6D96A4 |
| SHA1: | 365D2A74A48FD0F6D6CAEAB9AF92D88DD86E99C5 |
| SHA256: | 4598422E7B567765993E45F855DD58FDAABCF3B050F066799413863B40D2F84D |
| SSDEEP: | 3:N8CuQH:2CuQH |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates file in the systems drive root
- explorer.exe (PID: 5492)
Executes as Windows Service
- VSSVC.exe (PID: 7956)
- warp-svc.exe (PID: 1812)
Application launched itself
- msiexec.exe (PID: 672)
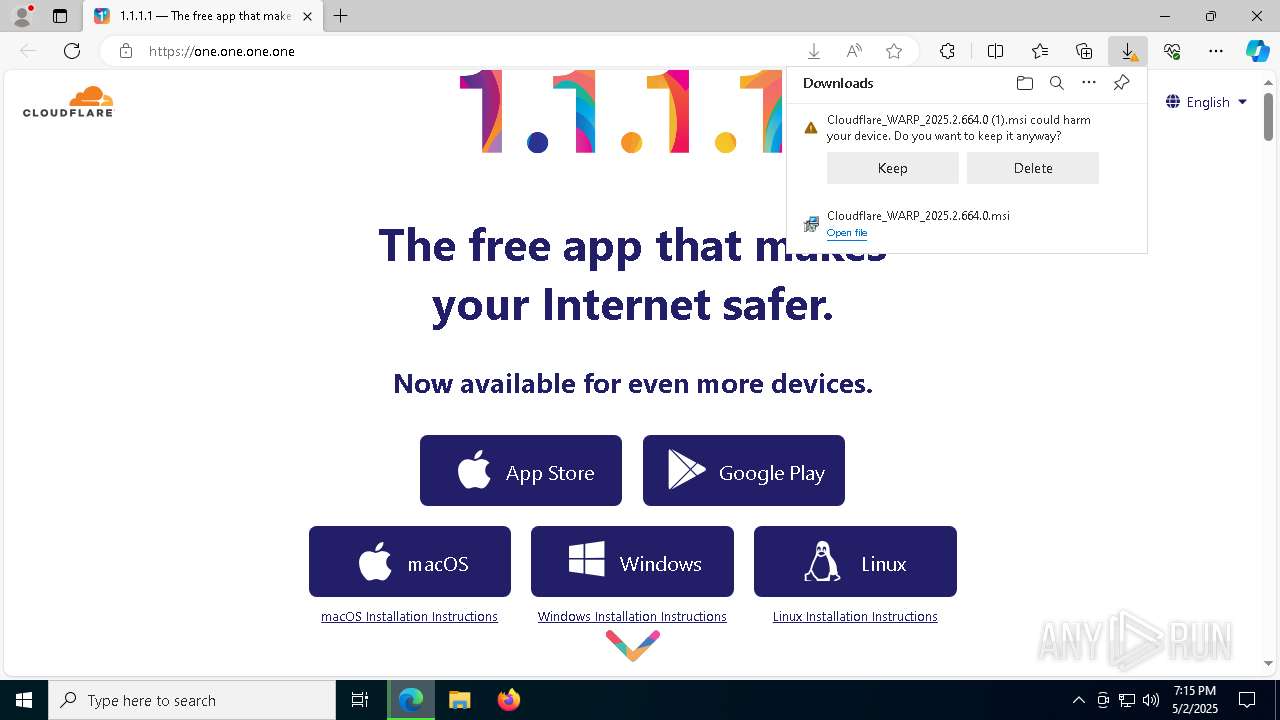
Executable content was dropped or overwritten
- rundll32.exe (PID: 8572)
- rundll32.exe (PID: 776)
- Cloudflare WARP.exe (PID: 6256)
- warp-svc.exe (PID: 1812)
- drvinst.exe (PID: 8288)
The process drops C-runtime libraries
- Cloudflare WARP.exe (PID: 6256)
Creates a new Windows service
- sc.exe (PID: 5132)
Restarts service on failure
- sc.exe (PID: 8292)
Starts SC.EXE for service management
- rundll32.exe (PID: 776)
Windows service management via SC.EXE
- sc.exe (PID: 8652)
- sc.exe (PID: 1852)
Process drops legitimate windows executable
- Cloudflare WARP.exe (PID: 6256)
Sets the service to start on system boot
- sc.exe (PID: 4756)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 8272)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 5492)
Drops a system driver (possible attempt to evade defenses)
- drvinst.exe (PID: 8288)
- warp-svc.exe (PID: 1812)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 5528)
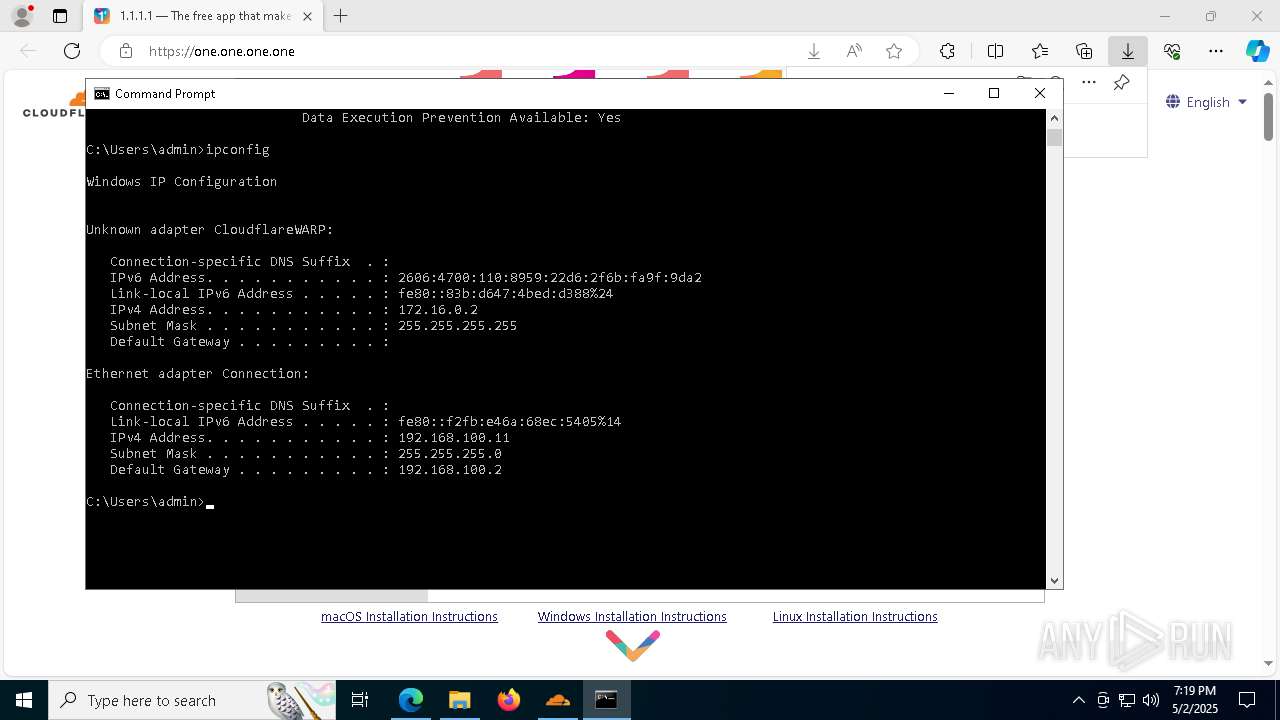
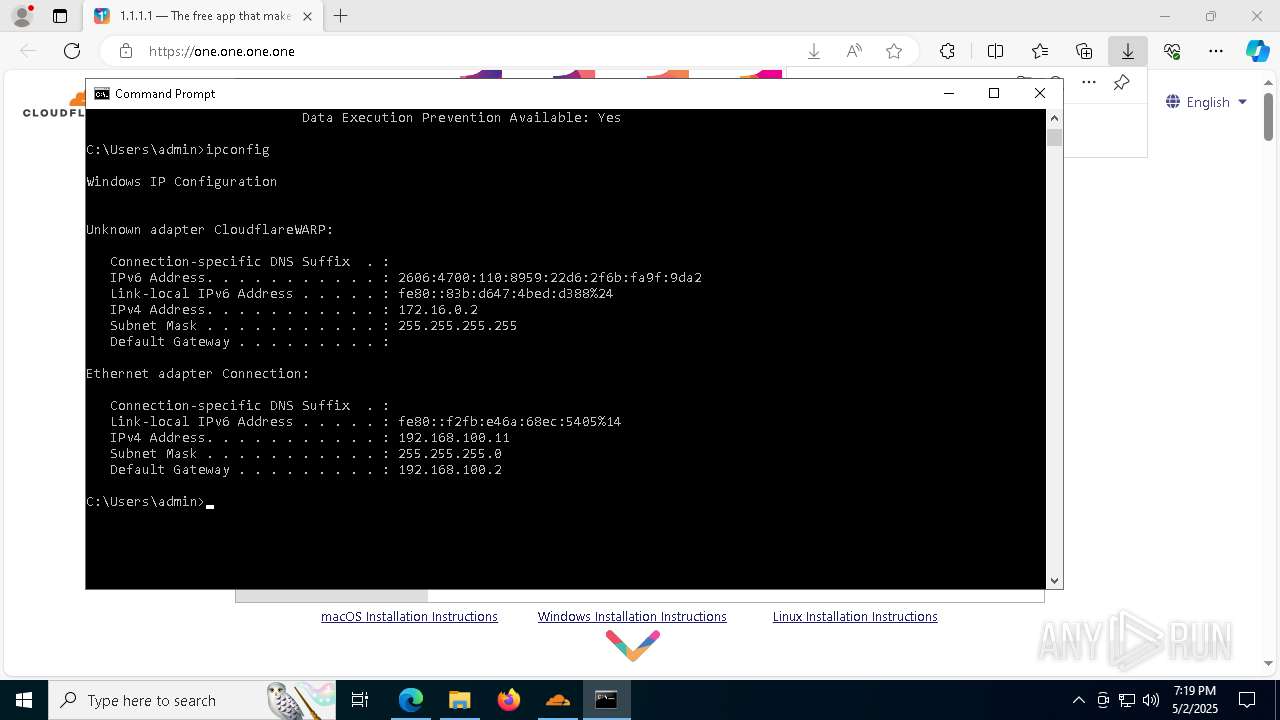
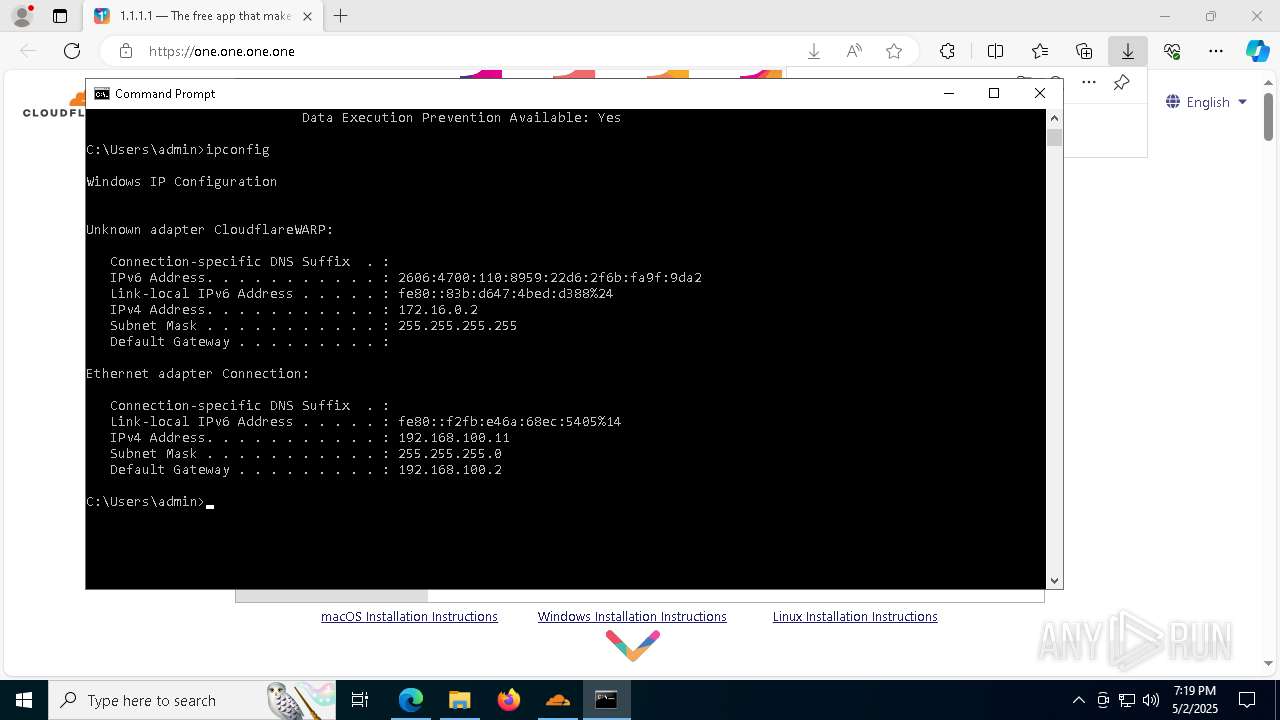
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 5528)
INFO
Reads the computer name
- identity_helper.exe (PID: 8708)
- msiexec.exe (PID: 672)
Creates files or folders in the user directory
- explorer.exe (PID: 5492)
Reads the software policy settings
- slui.exe (PID: 8120)
- explorer.exe (PID: 5492)
- msiexec.exe (PID: 2908)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
- msiexec.exe (PID: 2908)
Create files in a temporary directory
- msiexec.exe (PID: 2908)
Reads Environment values
- identity_helper.exe (PID: 8708)
Checks proxy server information
- explorer.exe (PID: 5492)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
Checks supported languages
- identity_helper.exe (PID: 8708)
- msiexec.exe (PID: 672)
Application launched itself
- msedge.exe (PID: 5048)
Executable content was dropped or overwritten
- msedge.exe (PID: 6828)
- msiexec.exe (PID: 672)
Manages system restore points
- SrTasks.exe (PID: 1568)
The sample compiled with english language support
- msedge.exe (PID: 6828)
- msiexec.exe (PID: 672)
- Cloudflare WARP.exe (PID: 6256)
- warp-svc.exe (PID: 1812)
- drvinst.exe (PID: 8288)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
252
Monitored processes
98
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7240 --field-trial-handle=2344,i,11147434635236036199,1044239521987401336,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 776 | rundll32.exe "C:\WINDOWS\Installer\MSIF48E.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1242578 36 Warp.Installer.Actions!Warp.Installer.Actions.CustomActions.InstallService | C:\Windows\System32\rundll32.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=32 --mojo-platform-channel-handle=5208 --field-trial-handle=2344,i,11147434635236036199,1044239521987401336,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 924 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8172 --field-trial-handle=2344,i,11147434635236036199,1044239521987401336,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1004 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6476 --field-trial-handle=2344,i,11147434635236036199,1044239521987401336,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1568 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | "C:\Program Files\Cloudflare\Cloudflare WARP\warp-svc.exe" | C:\Program Files\Cloudflare\Cloudflare WARP\warp-svc.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: warp-svc Version: 2025.2.0 Modules
| |||||||||||||||
| 1852 | "sc.exe" config CloudflareWARP depend= "wlansvc" | C:\Windows\System32\sc.exe | — | rundll32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
56 967
Read events
56 463
Write events
475
Delete events
29
Modification events
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 7DA38D3EC2922F00 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000802C6 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 766A993EC2922F00 | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524998 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {D8D57849-DE5C-4CF0-BF1A-D9903B24829E} | |||
| (PID) Process: | (5048) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524998 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C1990471-9CF0-44E3-A911-8FDC8B14E87F} | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000040306 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
Executable files
44
Suspicious files
443
Text files
87
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10d004.TMP | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10d004.TMP | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10cff4.TMP | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10d004.TMP | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10d042.TMP | — | |
MD5:— | SHA256:— | |||
| 5048 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
52
TCP/UDP connections
125
DNS requests
114
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4452 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8340 | svchost.exe | HEAD | 200 | 2.19.11.113:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1746418006&P2=404&P3=2&P4=Rwxj1ANj2Ca7SXgeJzpcyQsHx1Wozq7nRlY1I3wPPgzr6PF4b0MnTpvcEhqOP%2f7deIsIxk3MaijZ2ttKSeAoLQ%3d%3d | unknown | — | — | whitelisted |
8340 | svchost.exe | GET | 206 | 2.19.11.113:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1746418006&P2=404&P3=2&P4=Rwxj1ANj2Ca7SXgeJzpcyQsHx1Wozq7nRlY1I3wPPgzr6PF4b0MnTpvcEhqOP%2f7deIsIxk3MaijZ2ttKSeAoLQ%3d%3d | unknown | — | — | whitelisted |
8340 | svchost.exe | GET | 206 | 2.19.11.113:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1746418006&P2=404&P3=2&P4=Rwxj1ANj2Ca7SXgeJzpcyQsHx1Wozq7nRlY1I3wPPgzr6PF4b0MnTpvcEhqOP%2f7deIsIxk3MaijZ2ttKSeAoLQ%3d%3d | unknown | — | — | whitelisted |
8340 | svchost.exe | GET | 206 | 2.19.11.113:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/241074c3-f448-482a-8c90-855c388ea76a?P1=1746418006&P2=404&P3=2&P4=Rwxj1ANj2Ca7SXgeJzpcyQsHx1Wozq7nRlY1I3wPPgzr6PF4b0MnTpvcEhqOP%2f7deIsIxk3MaijZ2ttKSeAoLQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5048 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7316 | msedge.exe | 1.1.1.1:443 | one.one.one.one | — | — | whitelisted |
7316 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
one.one.one.one |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1812 | warp-svc.exe | Misc activity | ET INFO Observed Cloudflare DNS over HTTPS Domain (cloudflare-dns .com in TLS SNI) |
1812 | warp-svc.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
1812 | warp-svc.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
1812 | warp-svc.exe | Misc activity | ET INFO Microsoft Connection Test |
1812 | warp-svc.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
1812 | warp-svc.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
1812 | warp-svc.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
1812 | warp-svc.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
1812 | warp-svc.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
1812 | warp-svc.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |