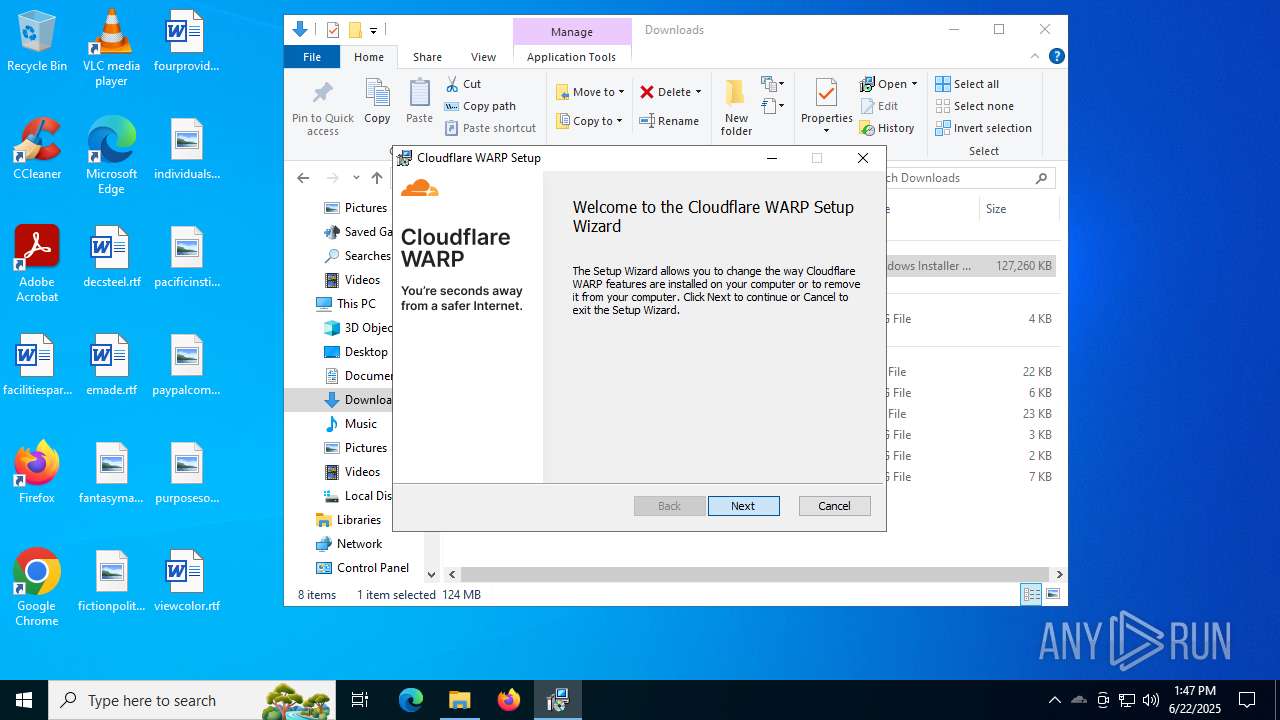
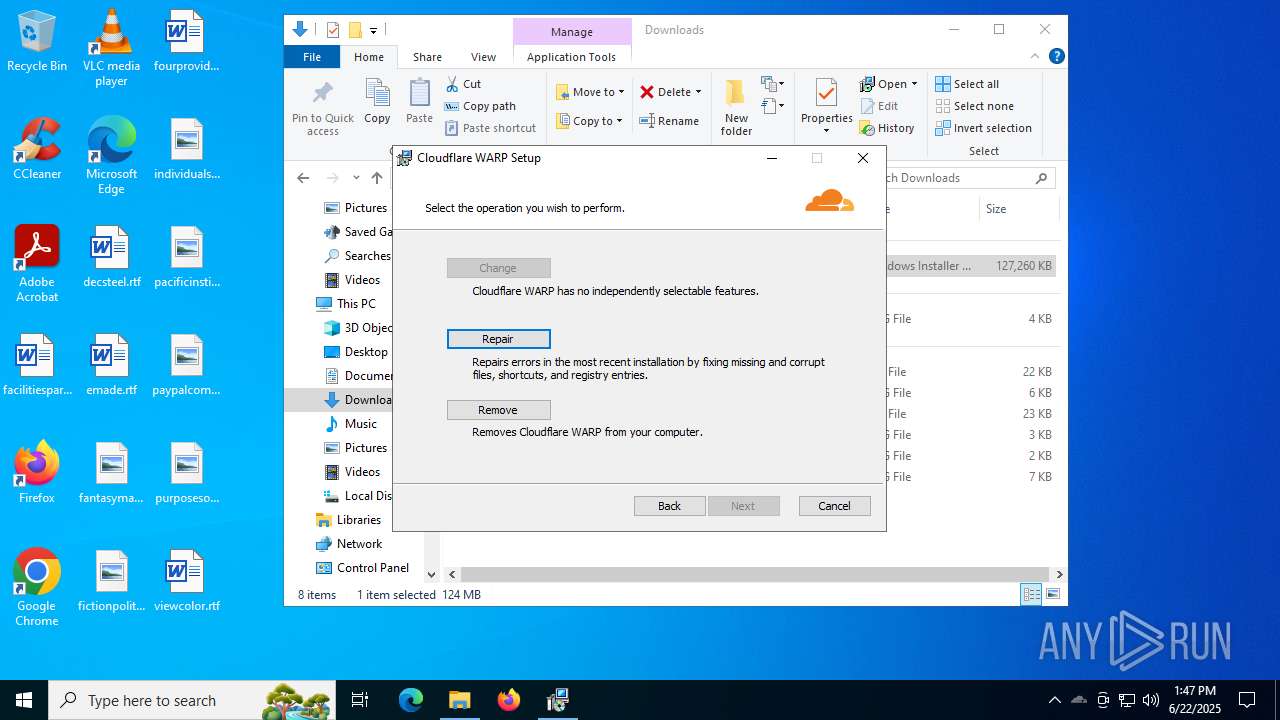
| URL: | https://one.one.one.one/ |
| Full analysis: | https://app.any.run/tasks/0e4d966a-b402-4320-be97-1874391da546 |
| Verdict: | Malicious activity |
| Analysis date: | June 22, 2025, 13:45:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | 7EB8C3836CAE930C02577B46EF6D96A4 |
| SHA1: | 365D2A74A48FD0F6D6CAEAB9AF92D88DD86E99C5 |
| SHA256: | 4598422E7B567765993E45F855DD58FDAABCF3B050F066799413863B40D2F84D |
| SSDEEP: | 3:N8CuQH:2CuQH |
MALICIOUS
Create files in the Startup directory
- msiexec.exe (PID: 7820)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 7892)
- warp-svc.exe (PID: 7928)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7820)
Application launched itself
- msiexec.exe (PID: 7820)
Executable content was dropped or overwritten
- rundll32.exe (PID: 7400)
- rundll32.exe (PID: 7392)
- Cloudflare WARP.exe (PID: 5348)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 7300)
Starts SC.EXE for service management
- rundll32.exe (PID: 7392)
Creates a new Windows service
- sc.exe (PID: 2552)
Restarts service on failure
- sc.exe (PID: 7384)
Windows service management via SC.EXE
- sc.exe (PID: 7556)
- sc.exe (PID: 7644)
The process checks if it is being run in the virtual environment
- warp-svc.exe (PID: 7928)
Sets the service to start on system boot
- sc.exe (PID: 7348)
Process drops legitimate windows executable
- Cloudflare WARP.exe (PID: 5348)
The process drops C-runtime libraries
- Cloudflare WARP.exe (PID: 5348)
Reads the date of Windows installation
- Cloudflare WARP.exe (PID: 5348)
Reads security settings of Internet Explorer
- Cloudflare WARP.exe (PID: 5348)
Detected use of alternative data streams (AltDS)
- Cloudflare WARP.exe (PID: 7312)
INFO
Reads the software policy settings
- msiexec.exe (PID: 7768)
- msiexec.exe (PID: 7820)
- warp-svc.exe (PID: 7928)
- Cloudflare WARP.exe (PID: 5348)
- SearchApp.exe (PID: 5328)
- slui.exe (PID: 1136)
Reads Microsoft Office registry keys
- chrome.exe (PID: 1068)
Create files in a temporary directory
- msiexec.exe (PID: 7768)
- Cloudflare WARP.exe (PID: 5348)
- msiexec.exe (PID: 8592)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7768)
Reads the computer name
- msiexec.exe (PID: 7820)
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 7300)
- warp-svc.exe (PID: 7928)
- msiexec.exe (PID: 8108)
- Cloudflare WARP.exe (PID: 5348)
- Cloudflare WARP.exe (PID: 7312)
- Cloudflare WARP.exe (PID: 7380)
Application launched itself
- chrome.exe (PID: 1068)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7820)
- warp-svc.exe (PID: 7928)
- SearchApp.exe (PID: 5328)
Manages system restore points
- SrTasks.exe (PID: 6160)
Checks supported languages
- msiexec.exe (PID: 7820)
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 7300)
- warp-svc.exe (PID: 7928)
- msiexec.exe (PID: 8108)
- Cloudflare WARP.exe (PID: 5348)
- SearchApp.exe (PID: 5328)
- Cloudflare WARP.exe (PID: 7312)
- Cloudflare WARP.exe (PID: 7380)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7820)
The sample compiled with english language support
- msiexec.exe (PID: 7820)
- Cloudflare WARP.exe (PID: 5348)
Creates files in the program directory
- warp-svc.exe (PID: 7928)
- Cloudflare WARP.exe (PID: 5348)
Launching a file from the Startup directory
- msiexec.exe (PID: 7820)
Process checks computer location settings
- SearchApp.exe (PID: 5328)
- Cloudflare WARP.exe (PID: 5348)
- Cloudflare WARP.exe (PID: 7312)
- Cloudflare WARP.exe (PID: 7380)
Reads Environment values
- Cloudflare WARP.exe (PID: 5348)
Creates files or folders in the user directory
- Cloudflare WARP.exe (PID: 5348)
- Cloudflare WARP.exe (PID: 7312)
- Cloudflare WARP.exe (PID: 7380)
Checks proxy server information
- Cloudflare WARP.exe (PID: 5348)
- slui.exe (PID: 1136)
Creates a software uninstall entry
- msiexec.exe (PID: 7820)
Manual execution by a user
- msiexec.exe (PID: 8592)
- Cloudflare WARP.exe (PID: 7312)
- Cloudflare WARP.exe (PID: 7380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
212
Monitored processes
40
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://one.one.one.one/" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1136 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1380 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --field-trial-handle=3060,i,4930076507032218915,4667549092775571181,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3104 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2072 | C:\Windows\syswow64\MsiExec.exe -Embedding 177AE36229E46711779AB2DA3C4CA5C2 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --extension-process --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=3548,i,4930076507032218915,4667549092775571181,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3572 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2468 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Cloudflare WARP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2552 | "sc.exe" create CloudflareWARP binPath= "\"C:\Program Files\Cloudflare\Cloudflare WARP\warp-svc.exe"\" displayname= "Cloudflare WARP" start= "auto" | C:\Windows\System32\sc.exe | — | rundll32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2804 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=133.0.6943.127 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc436bfff8,0x7ffc436c0004,0x7ffc436c0010 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2808 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=3068,i,4930076507032218915,4667549092775571181,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3128 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 3000 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
35 031
Read events
34 564
Write events
448
Delete events
19
Modification events
| (PID) Process: | (1068) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1068) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1068) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1068) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1068) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1068) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1068) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1068) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.msi\OpenWithProgids |
| Operation: | write | Name: | Msi.Package |
Value: | |||
| (PID) Process: | (7820) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000003458C3077CE3DB018C1E0000C41E0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7820) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000B87FC3077CE3DB018C1E0000C41E0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
32
Suspicious files
230
Text files
297
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1068 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF176699.TMP | — | |
MD5:— | SHA256:— | |||
| 1068 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1068 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF1766a9.TMP | — | |
MD5:— | SHA256:— | |||
| 1068 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RF1766b9.TMP | — | |
MD5:— | SHA256:— | |||
| 1068 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF1766b9.TMP | — | |
MD5:— | SHA256:— | |||
| 1068 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1766b9.TMP | — | |
MD5:— | SHA256:— | |||
| 1068 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1068 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1068 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF1766b9.TMP | — | |
MD5:— | SHA256:— | |||
| 1068 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
112
DNS requests
82
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5692 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5532 | chrome.exe | GET | 200 | 142.250.185.110:80 | http://clients2.google.com/time/1/current?cup2key=8:4rydmeIHT6E8QI3TXG5lty4nrv_k1rt493Z6JEyLqWo&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1068 | chrome.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
8044 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1068 | chrome.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEA5jYmfMjSHiYbPSIJ1fIWY%3D | unknown | — | — | whitelisted |
7928 | warp-svc.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnxLiz3Fu1WB6n1%2FE6xWn1b0jXiQQUdIWAwGbH3zfez70pN6oDHb7tzRcCEAJ9yMXhcpSuye0%2FZ3KOigg%3D | unknown | — | — | whitelisted |
8044 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1136 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5532 | chrome.exe | 142.250.185.170:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
5532 | chrome.exe | 142.250.185.110:80 | clients2.google.com | GOOGLE | US | whitelisted |
5532 | chrome.exe | 1.0.0.1:443 | one.one.one.one | CLOUDFLARENET | AU | whitelisted |
5532 | chrome.exe | 173.194.76.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
5532 | chrome.exe | 104.16.80.230:443 | 1111-releases.cloudflareclient.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
one.one.one.one |
| whitelisted |
accounts.google.com |
| whitelisted |
1111-releases.cloudflareclient.com |
| unknown |
downloads.cloudflareclient.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7928 | warp-svc.exe | Misc activity | ET INFO Observed Cloudflare DNS over HTTPS Domain (cloudflare-dns .com in TLS SNI) |
Process | Message |
|---|---|
Cloudflare WARP.exe | netsparkle: Using the following url for downloading the app cast: https://downloads.cloudflareclient.com/v1/update/sparkle/windows/ga
|