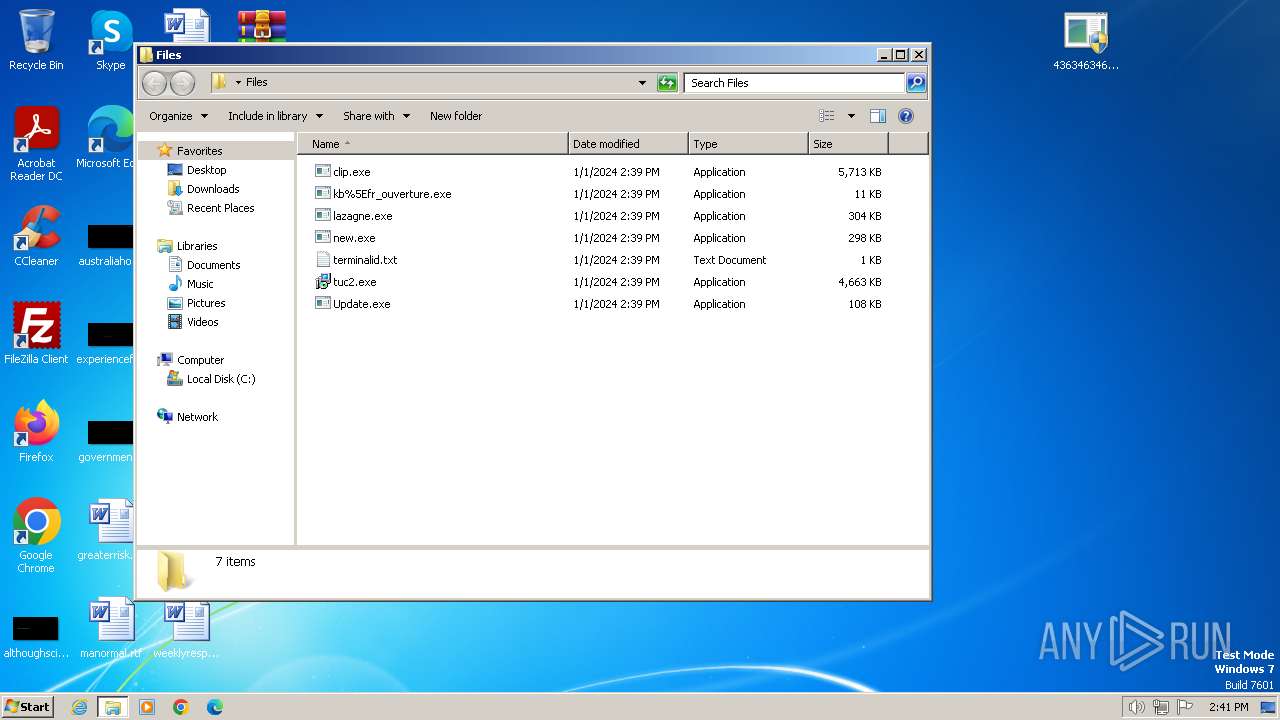
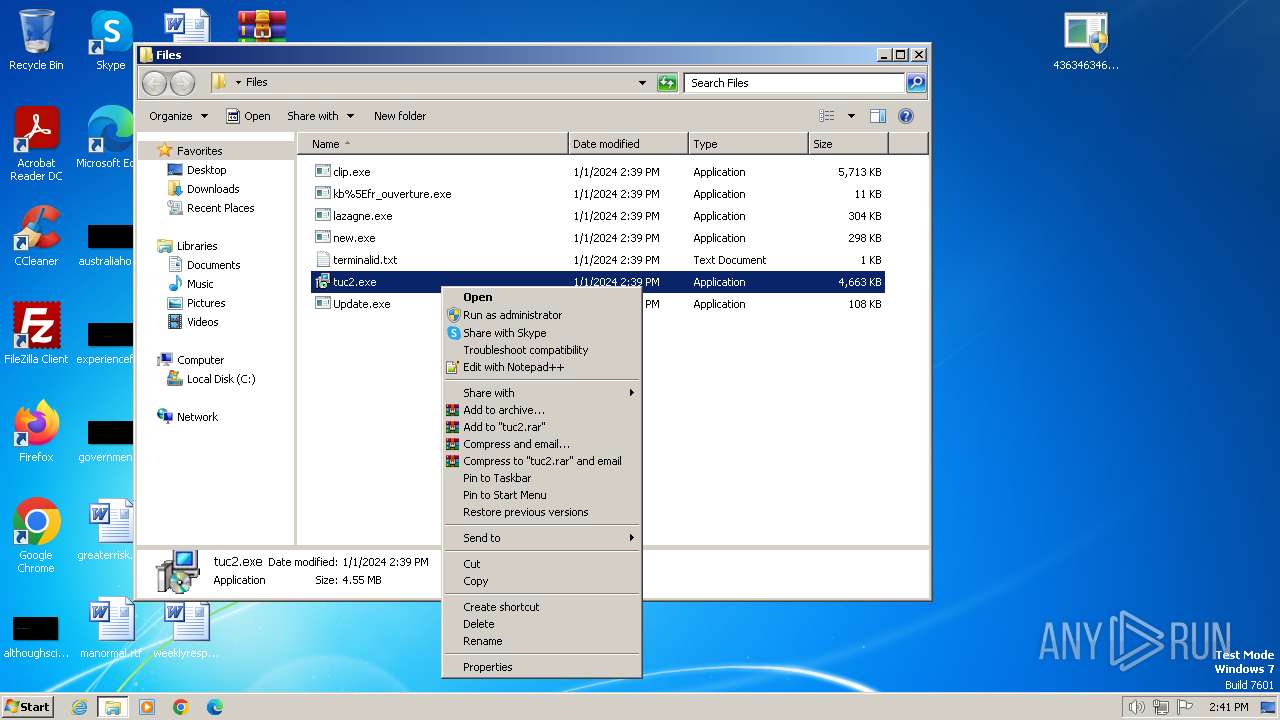
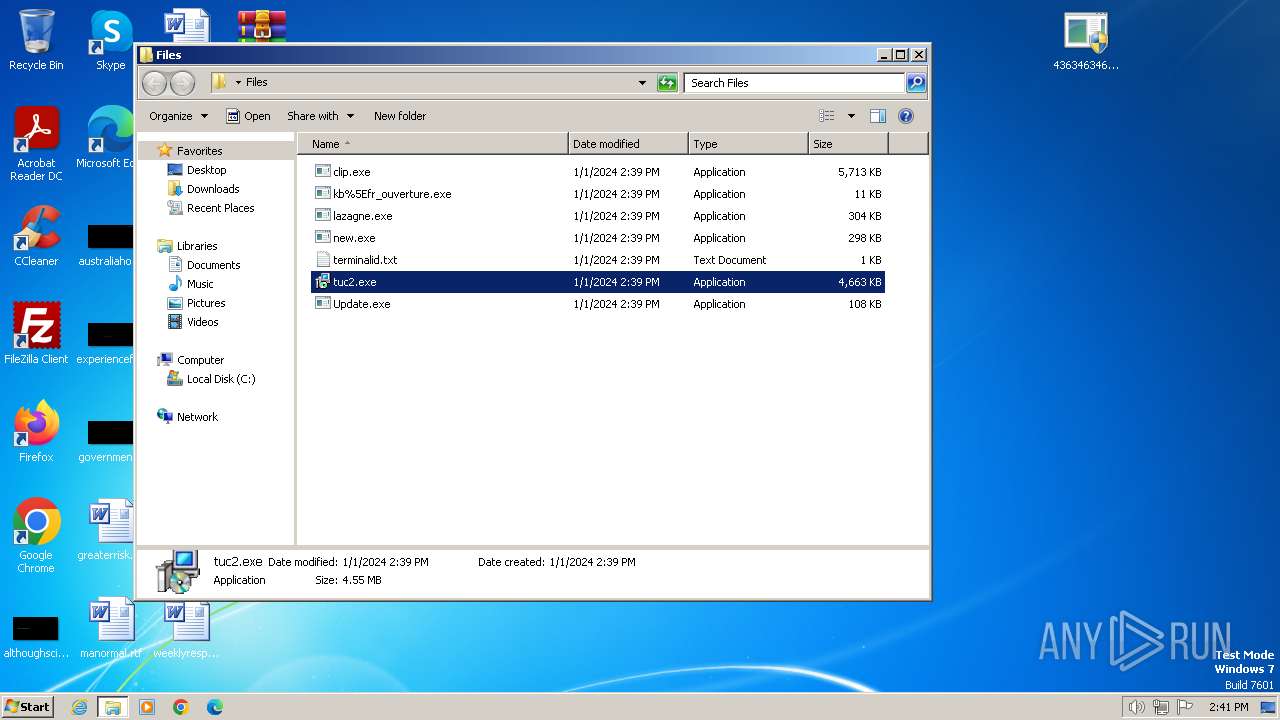
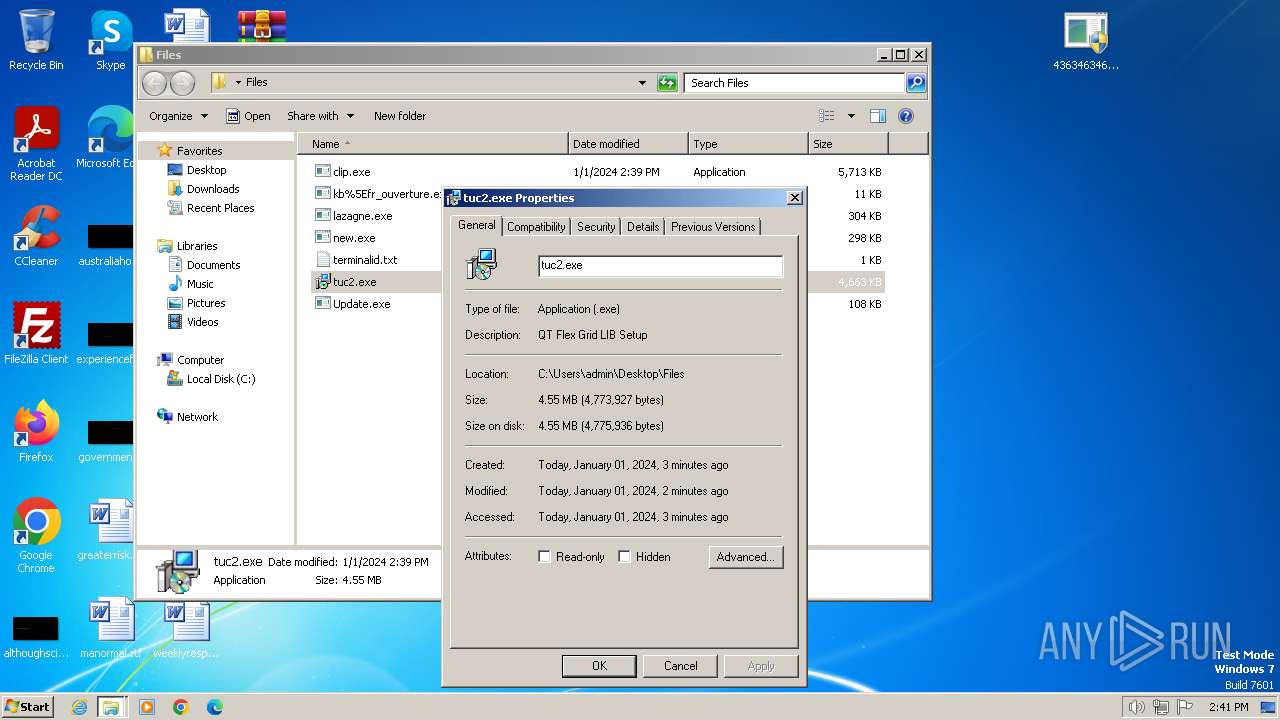
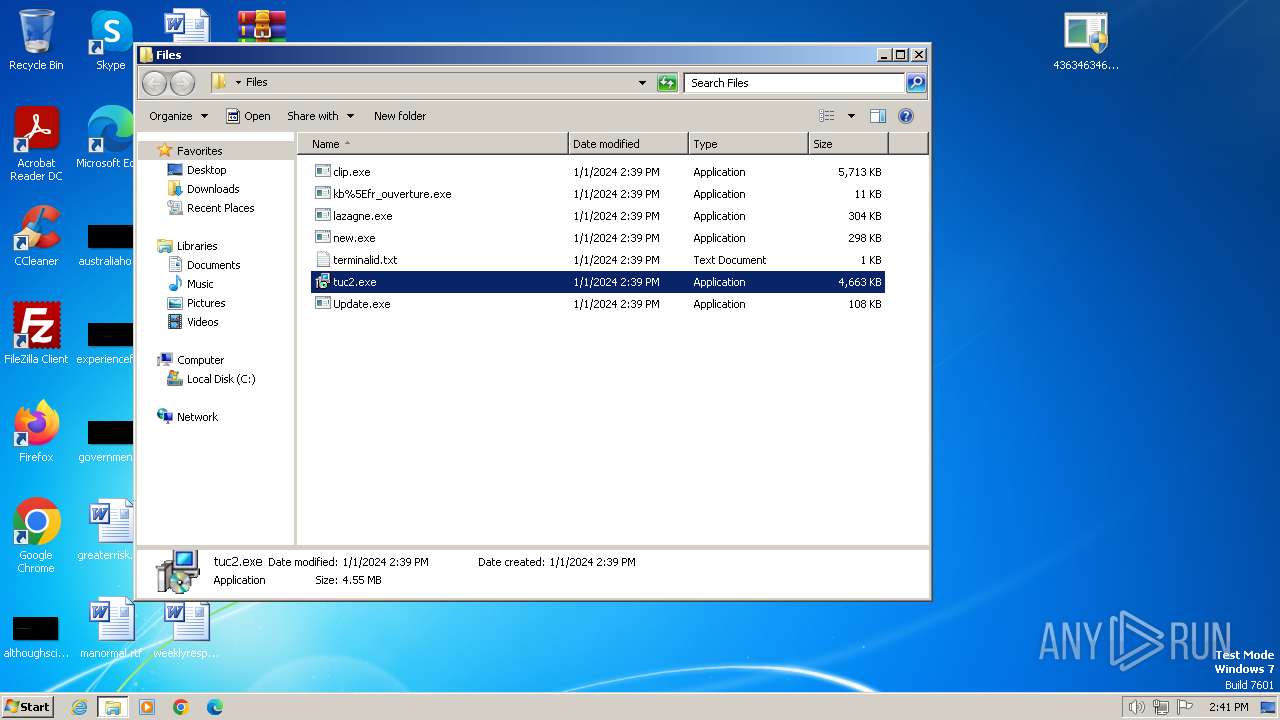
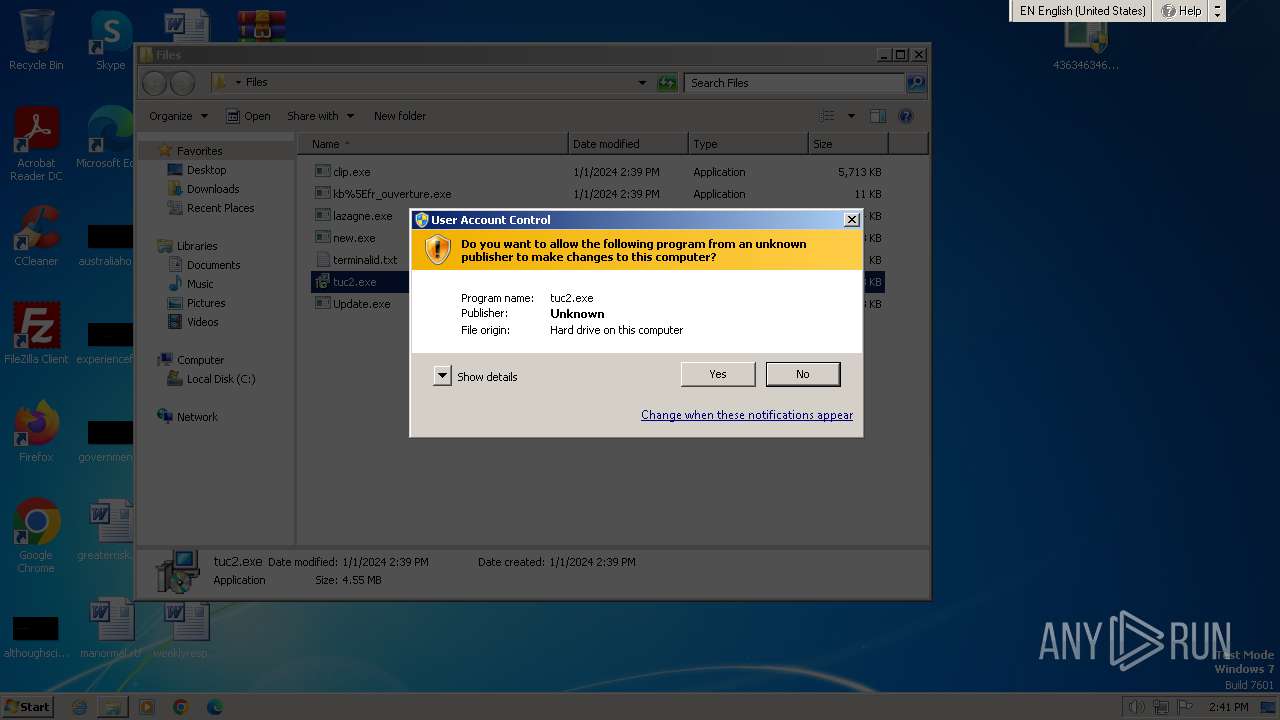
| File name: | 4363463463464363463463463.zip |
| Full analysis: | https://app.any.run/tasks/5c59adb1-1ace-4a2f-9d53-a458cf958010 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | January 01, 2024, 14:38:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 202786D1D9B71C375E6F940E6DD4828A |
| SHA1: | 7CAD95FAA33E92ACEEE3BCC809CD687BDA650D74 |
| SHA256: | 45930E1FF487557DD242214C1E7D07294DBEDFA7BC2CF712FAE46D8D6B61DE76 |
| SSDEEP: | 96:7pXGTVnZfv+eqbcCm7+RxqfALm5kgULw96+S4/Z4bkPjEf9VrRB2LG7Cp:o2z+bALsGW6+S72E1d2LG7G |
MALICIOUS
HAUSBOMBER has been detected (YARA)
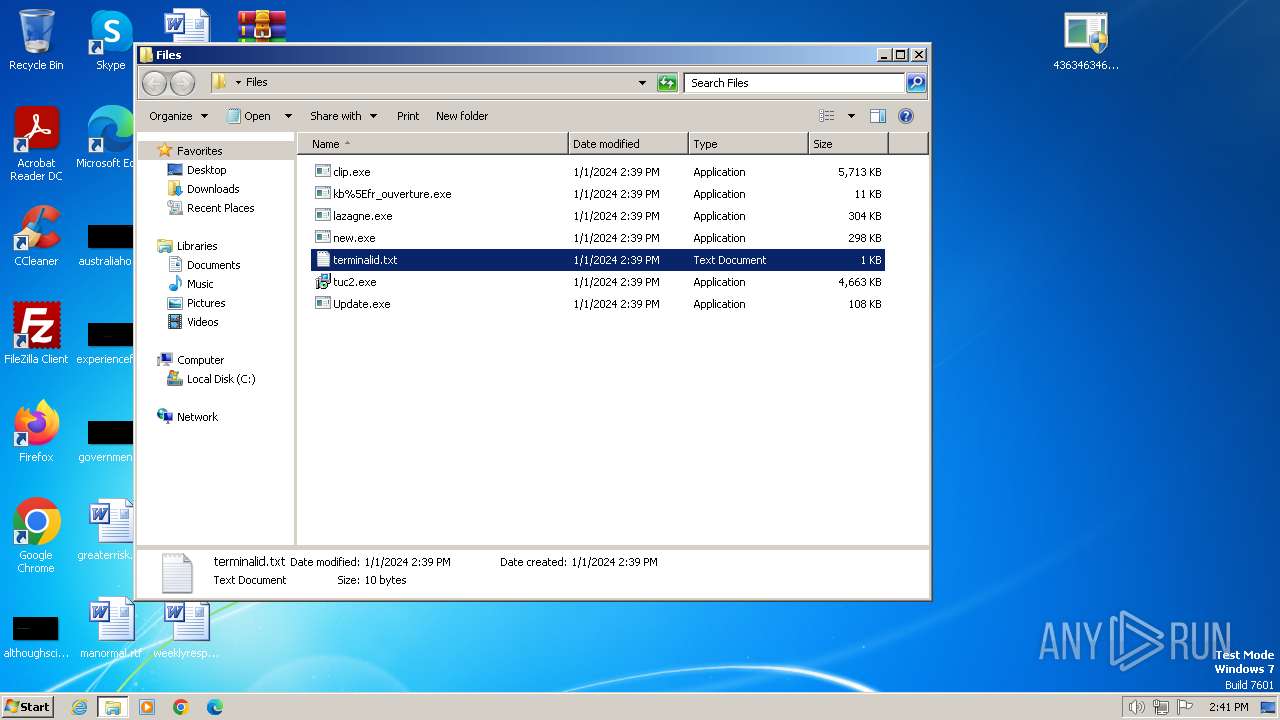
- 4363463463464363463463463.exe (PID: 2312)
Uses Task Scheduler to run other applications
- LEAJ.exe (PID: 3024)
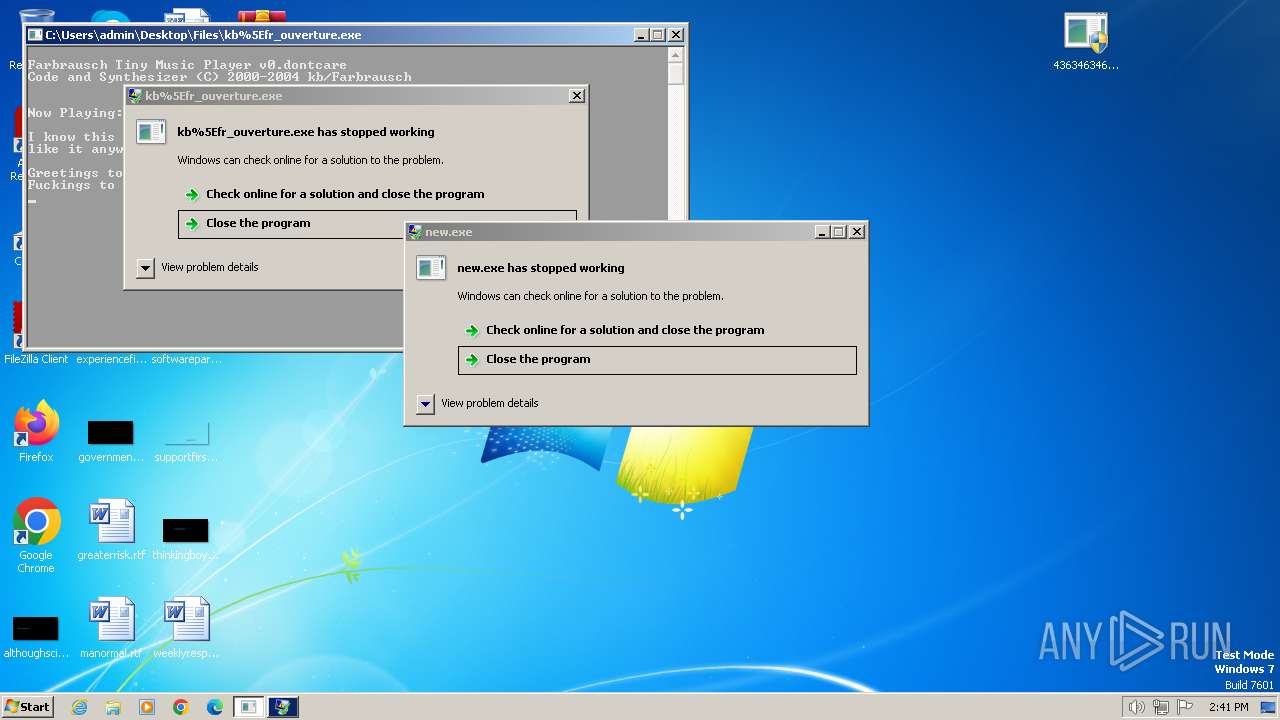
REDLINE has been detected (YARA)
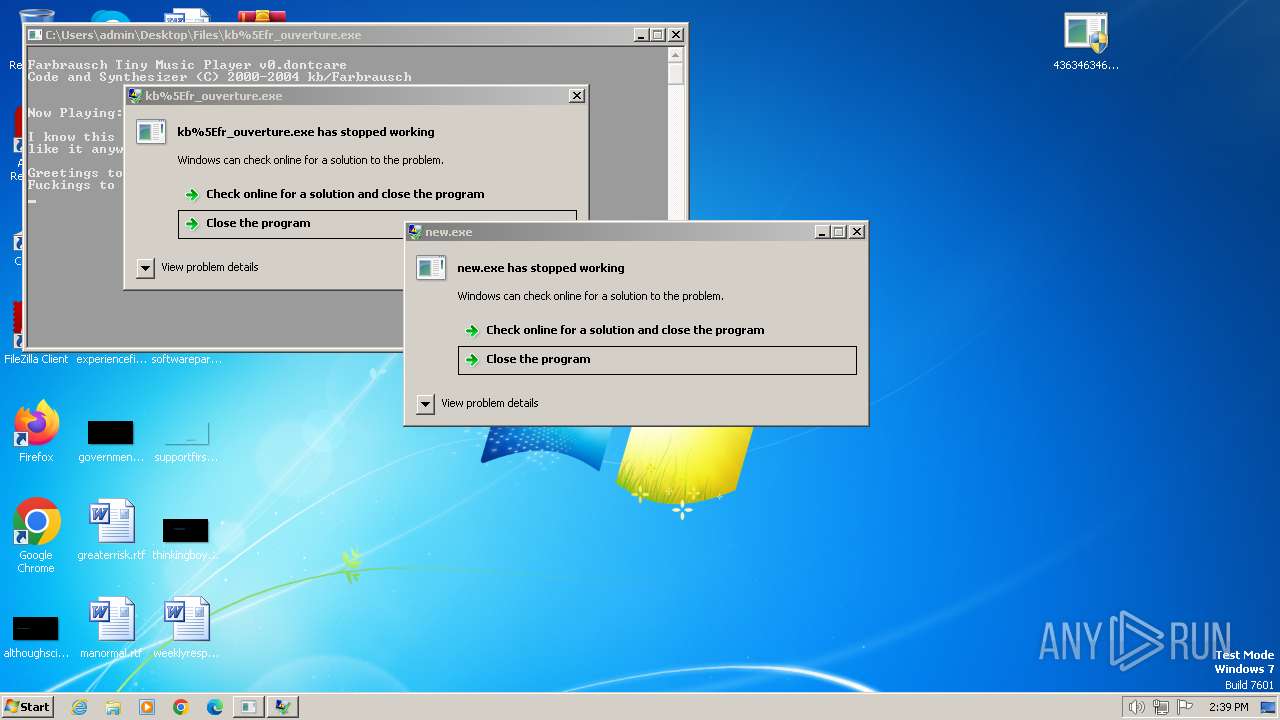
- new.exe (PID: 2828)
- vbc.exe (PID: 2788)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2312)
- Update.exe (PID: 2240)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 2312)
- clip.exe (PID: 3072)
- Update.exe (PID: 2240)
- LEAJ.exe (PID: 3024)
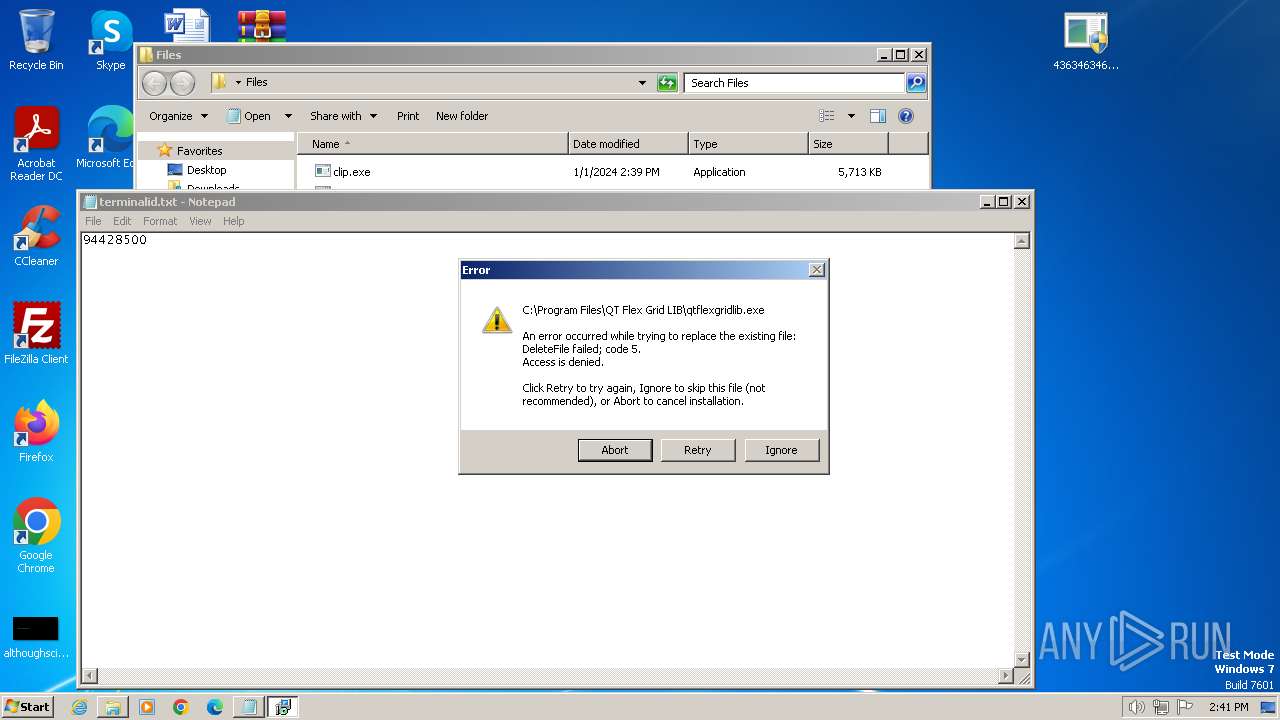
- qtflexgridlib.exe (PID: 2520)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2312)
- Update.exe (PID: 2240)
Reads the Windows owner or organization settings
- tuc2.tmp (PID: 1556)
- tuc2.tmp (PID: 324)
The process executes VB scripts
- new.exe (PID: 2828)
Reads the BIOS version
- clip.exe (PID: 3072)
- LEAJ.exe (PID: 1124)
- LEAJ.exe (PID: 2976)
- LEAJ.exe (PID: 3024)
- LEAJ.exe (PID: 1636)
- LEAJ.exe (PID: 1820)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3028)
Executing commands from a ".bat" file
- clip.exe (PID: 3072)
Starts CMD.EXE for commands execution
- clip.exe (PID: 3072)
Searches for installed software
- tuc2.tmp (PID: 324)
INFO
Checks supported languages
- 4363463463464363463463463.exe (PID: 2312)
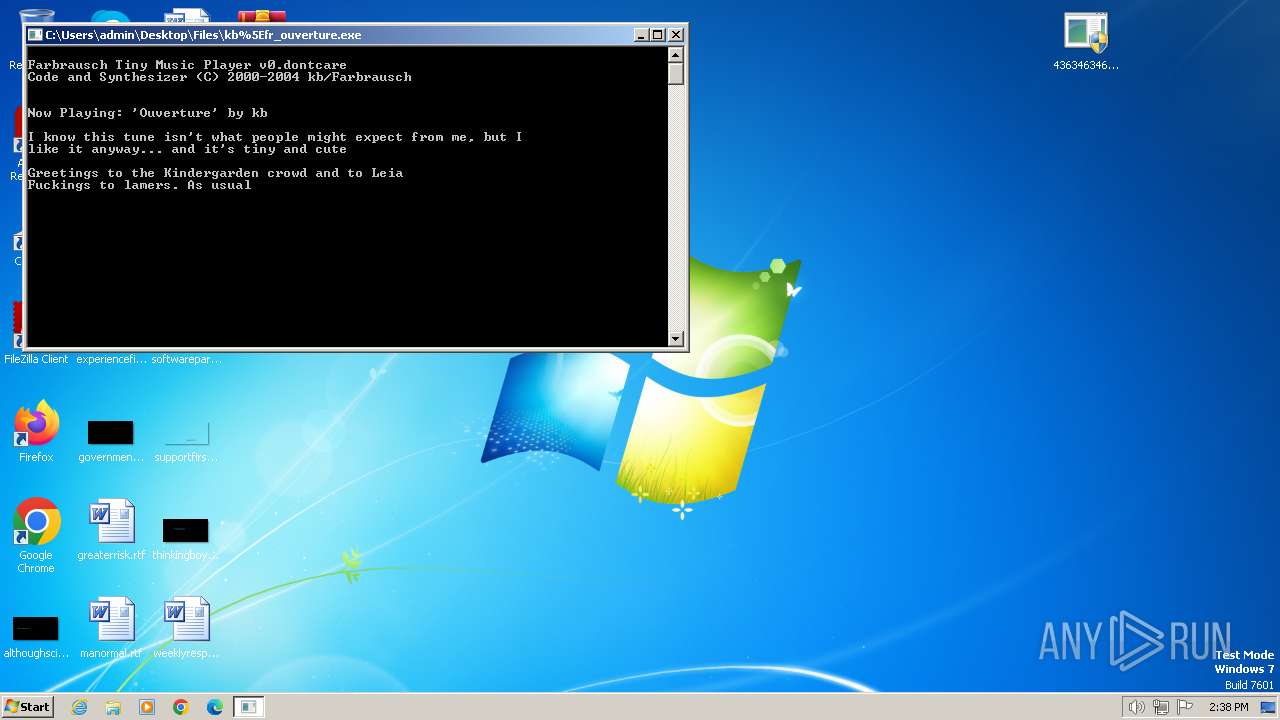
- kb%5Efr_ouverture.exe (PID: 1844)
- tuc2.exe (PID: 1572)
- tuc2.tmp (PID: 1556)
- qtflexgridlib.exe (PID: 2100)
- Update.exe (PID: 2240)
- vbc.exe (PID: 2788)
- new.exe (PID: 2828)
- qtflexgridlib.exe (PID: 2520)
- clip.exe (PID: 3072)
- LEAJ.exe (PID: 3024)
- LEAJ.exe (PID: 1124)
- LEAJ.exe (PID: 2976)
- tuc2.exe (PID: 3380)
- tuc2.tmp (PID: 4080)
- tuc2.exe (PID: 864)
- tuc2.tmp (PID: 324)
- LEAJ.exe (PID: 1820)
- LEAJ.exe (PID: 1636)
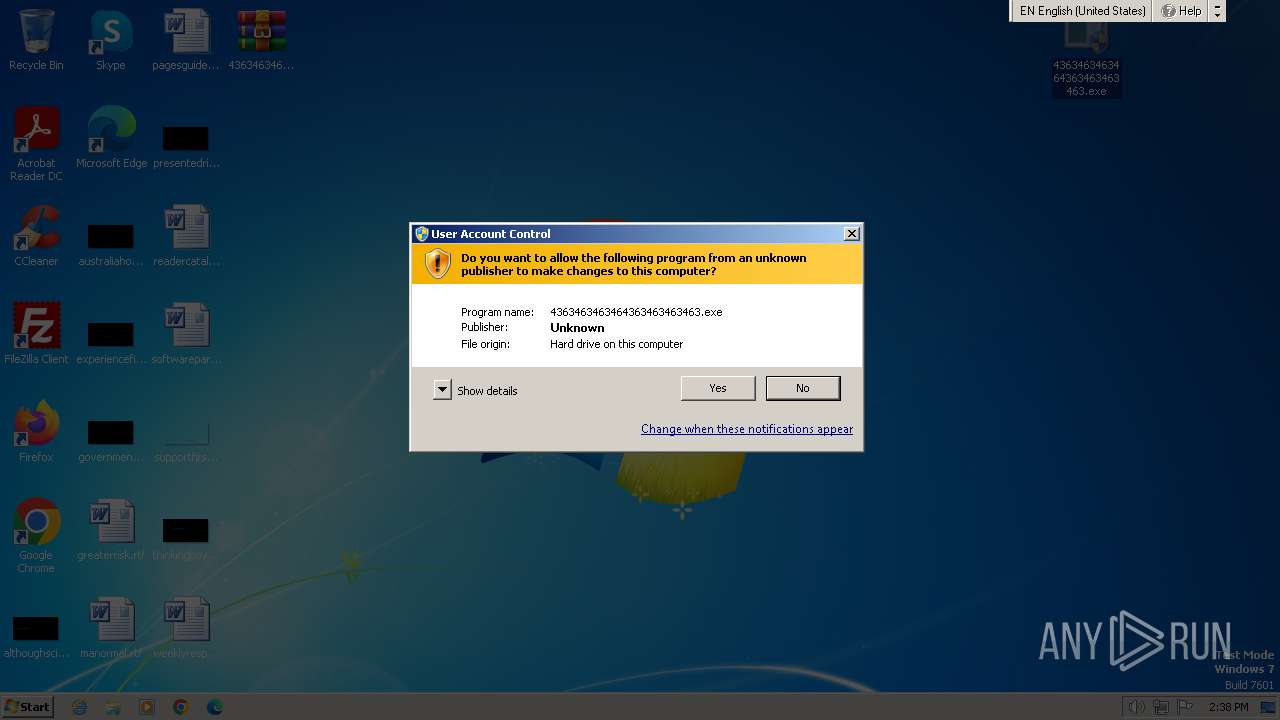
Manual execution by a user
- 4363463463464363463463463.exe (PID: 2312)
- 4363463463464363463463463.exe (PID: 548)
- tuc2.exe (PID: 3380)
- notepad.exe (PID: 2084)
Reads the computer name
- 4363463463464363463463463.exe (PID: 2312)
- kb%5Efr_ouverture.exe (PID: 1844)
- tuc2.tmp (PID: 1556)
- Update.exe (PID: 2240)
- vbc.exe (PID: 2788)
- qtflexgridlib.exe (PID: 2100)
- clip.exe (PID: 3072)
- LEAJ.exe (PID: 3024)
- qtflexgridlib.exe (PID: 2520)
- tuc2.tmp (PID: 4080)
- tuc2.tmp (PID: 324)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2044)
- tuc2.exe (PID: 1572)
- 4363463463464363463463463.exe (PID: 2312)
- tuc2.tmp (PID: 1556)
- qtflexgridlib.exe (PID: 2100)
- clip.exe (PID: 3072)
- tuc2.exe (PID: 3380)
- tuc2.exe (PID: 864)
- tuc2.tmp (PID: 324)
Reads Environment values
- 4363463463464363463463463.exe (PID: 2312)
- Update.exe (PID: 2240)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2312)
- Update.exe (PID: 2240)
- vbc.exe (PID: 2788)
- qtflexgridlib.exe (PID: 2520)
Create files in a temporary directory
- tuc2.exe (PID: 1572)
- tuc2.tmp (PID: 1556)
- clip.exe (PID: 3072)
- tuc2.exe (PID: 3380)
- tuc2.exe (PID: 864)
- tuc2.tmp (PID: 324)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 2312)
Process drops legitimate windows executable
- tuc2.tmp (PID: 1556)
- tuc2.tmp (PID: 324)
Drops 7-zip archiver for unpacking
- tuc2.tmp (PID: 1556)
- tuc2.tmp (PID: 324)
Creates files in the program directory
- tuc2.tmp (PID: 1556)
- qtflexgridlib.exe (PID: 2100)
- clip.exe (PID: 3072)
- qtflexgridlib.exe (PID: 2520)
- tuc2.tmp (PID: 324)
Process checks are UAC notifies on
- clip.exe (PID: 3072)
- LEAJ.exe (PID: 3024)
- LEAJ.exe (PID: 1124)
- LEAJ.exe (PID: 2976)
- LEAJ.exe (PID: 1820)
- LEAJ.exe (PID: 1636)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 2312)
- qtflexgridlib.exe (PID: 2520)
The process executes via Task Scheduler
- LEAJ.exe (PID: 1124)
- LEAJ.exe (PID: 2976)
- LEAJ.exe (PID: 1820)
- LEAJ.exe (PID: 1636)
Checks proxy server information
- qtflexgridlib.exe (PID: 2520)
Connects to the CnC server
- qtflexgridlib.exe (PID: 2520)
SOCKS5SYSTEMZ has been detected (SURICATA)
- qtflexgridlib.exe (PID: 2520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(2788) vbc.exe
C2 (2)chardhesha.xyz:81
jalocliche.xyz:81
Botneteasy11211
Options
ErrorMessage
Keys
XorScleral
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:30 02:51:06 |
| ZipCRC: | 0x31d44928 |
| ZipCompressedSize: | 4774 |
| ZipUncompressedSize: | 10752 |
| ZipFileName: | 4363463463464363463463463.exe |
Total processes
86
Monitored processes
27
Malicious processes
5
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | "C:\Users\admin\AppData\Local\Temp\is-HTQ32.tmp\tuc2.tmp" /SL5="$401C2,4519539,54272,C:\Users\admin\Desktop\Files\tuc2.exe" /SPAWNWND=$301C4 /NOTIFYWND=$601D6 | C:\Users\admin\AppData\Local\Temp\is-HTQ32.tmp\tuc2.tmp | — | tuc2.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 5 Version: 51.52.0.0 Modules
| |||||||||||||||
| 548 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 864 | "C:\Users\admin\Desktop\Files\tuc2.exe" /SPAWNWND=$301C4 /NOTIFYWND=$601D6 | C:\Users\admin\Desktop\Files\tuc2.exe | tuc2.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: QT Flex Grid LIB Setup Exit code: 5 Version: Modules
| |||||||||||||||
| 1124 | C:\ProgramData\presepuesto\LEAJ.exe | C:\ProgramData\presepuesto\LEAJ.exe | — | taskeng.exe | |||||||||||
User: admin Company: Intel Corporation Integrity Level: HIGH Description: Intel(R) Graphics Installer Exit code: 0 Version: 1, 7, 25, 0 Modules
| |||||||||||||||
| 1556 | "C:\Users\admin\AppData\Local\Temp\is-1GPCE.tmp\tuc2.tmp" /SL5="$40182,4519539,54272,C:\Users\admin\Desktop\Files\tuc2.exe" | C:\Users\admin\AppData\Local\Temp\is-1GPCE.tmp\tuc2.tmp | — | tuc2.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1572 | "C:\Users\admin\Desktop\Files\tuc2.exe" | C:\Users\admin\Desktop\Files\tuc2.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Integrity Level: HIGH Description: QT Flex Grid LIB Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1636 | C:\ProgramData\presepuesto\LEAJ.exe | C:\ProgramData\presepuesto\LEAJ.exe | — | taskeng.exe | |||||||||||
User: admin Company: Intel Corporation Integrity Level: HIGH Description: Intel(R) Graphics Installer Exit code: 0 Version: 1, 7, 25, 0 Modules
| |||||||||||||||
| 1820 | C:\ProgramData\presepuesto\LEAJ.exe | C:\ProgramData\presepuesto\LEAJ.exe | — | taskeng.exe | |||||||||||
User: admin Company: Intel Corporation Integrity Level: HIGH Description: Intel(R) Graphics Installer Exit code: 0 Version: 1, 7, 25, 0 Modules
| |||||||||||||||
| 1844 | "C:\Users\admin\Desktop\Files\kb%5Efr_ouverture.exe" | C:\Users\admin\Desktop\Files\kb%5Efr_ouverture.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 2044 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\4363463463464363463463463.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
10 451
Read events
10 348
Write events
103
Delete events
0
Modification events
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
172
Suspicious files
9
Text files
28
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1556 | tuc2.tmp | C:\Users\admin\AppData\Local\Temp\is-FR5G1.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 1556 | tuc2.tmp | C:\Users\admin\AppData\Local\Temp\is-FR5G1.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:0EE914C6F0BB93996C75941E1AD629C6 | SHA256:4DC09BAC0613590F1FAC8771D18AF5BE25A1E1CB8FDBF4031AA364F3057E74A2 | |||
| 1556 | tuc2.tmp | C:\Program Files\QT Flex Grid LIB\unins000.exe | executable | |
MD5:4E280484726620C8D08968E06BF856BA | SHA256:6A875B2538F1E25BEFDD8634AE0537F54CE6596A59D7FBB594C3B27D2DB41A86 | |||
| 1556 | tuc2.tmp | C:\Users\admin\AppData\Local\Temp\is-FR5G1.tmp\_isetup\_isdecmp.dll | executable | |
MD5:3ADAA386B671C2DF3BAE5B39DC093008 | SHA256:71CD2F5BC6E13B8349A7C98697C6D2E3FCDEEA92699CEDD591875BEA869FAE38 | |||
| 1556 | tuc2.tmp | C:\Program Files\QT Flex Grid LIB\is-28FND.tmp | executable | |
MD5:4E280484726620C8D08968E06BF856BA | SHA256:6A875B2538F1E25BEFDD8634AE0537F54CE6596A59D7FBB594C3B27D2DB41A86 | |||
| 1556 | tuc2.tmp | C:\Program Files\QT Flex Grid LIB\bin\x86\is-QT01H.tmp | executable | |
MD5:19E08B7F7B379A9D1F370E2B5CC622BD | SHA256:AC97E5492A3CE1689A2B3C25D588FAC68DFF5C2B79FCF4067F2D781F092BA2A1 | |||
| 1556 | tuc2.tmp | C:\Program Files\QT Flex Grid LIB\bin\x86\is-RABEB.tmp | executable | |
MD5:F0F973781B6A66ADF354B04A36C5E944 | SHA256:04AB613C895B35044AF8A9A98A372A5769C80245CC9D6BF710A94C5BC42FA1B3 | |||
| 1556 | tuc2.tmp | C:\Users\admin\AppData\Local\Temp\is-FR5G1.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 2044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2044.41460\4363463463464363463463463.exe | executable | |
MD5:2A94F3960C58C6E70826495F76D00B85 | SHA256:2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE | |||
| 2312 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\kb%5Efr_ouverture.exe | executable | |
MD5:2A872AE7AA325DAB4FD6F4D2A0A4FA21 | SHA256:693FBE27170B14EFDE45D627CF3E0AF36143762D2EF70A52A8402F121F6D6AE4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
18
DNS requests
10
Threats
35
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2312 | 4363463463464363463463463.exe | GET | 200 | 104.21.46.59:80 | http://cream.hitsturbo.com/order/tuc2.exe | unknown | executable | 4.55 Mb | unknown |
2312 | 4363463463464363463463463.exe | GET | 200 | 88.212.202.2:80 | http://websound.ru/issues/136_140/kb%5Efr_ouverture.exe | unknown | executable | 11.0 Kb | unknown |
2312 | 4363463463464363463463463.exe | GET | 200 | 212.12.151.74:80 | http://www.teknoarge.com/update/ana/Update.exe | unknown | executable | 108 Kb | unknown |
2312 | 4363463463464363463463463.exe | GET | — | 121.37.198.25:8287 | http://121.37.198.25:8287/lazagne.exe | unknown | — | — | unknown |
2312 | 4363463463464363463463463.exe | GET | 200 | 104.21.37.191:80 | http://rusticironstore.com/clip.exe | unknown | executable | 5.58 Mb | unknown |
2520 | qtflexgridlib.exe | GET | 200 | 185.196.8.22:80 | http://borfkyk.com/click/?counter=de7ef49b2c006853fb38357b3206f31360ff1905c311578eaae3c7edb62dde24353e1d9a943e9d15038842974dbc1dbaf7a1439f578166429e289d58869b3a226d55f676647fc3813369d184da325a568ed906f911ca | unknown | text | 3.30 Kb | unknown |
2520 | qtflexgridlib.exe | GET | 200 | 185.196.8.22:80 | http://borfkyk.com/click/?counter=de7ef49b2c006853fb38357b3206f31360ff1905c311578eaae3c7edb62cde24353e1d9a943e9d15038842935de14feaa4a21bca13c034069238dc1a959a22237244a421216497c02320889f8f71035f8edc06fd10ccd95cb322 | unknown | text | 14 b | unknown |
2520 | qtflexgridlib.exe | GET | 200 | 185.196.8.22:80 | http://borfkyk.com/click/?counter=de7ef49b2c006853fb38357b3206f31360ff1905c311578eaae3c7edb62cde24353e1d9a943e9d15038842935de14feaa4a21bca13c034069238dc1a959a22237244a421216497c02320889f8f71035f8edc06fd10ccd95cb322 | unknown | text | 3.16 Kb | unknown |
2520 | qtflexgridlib.exe | GET | 200 | 185.196.8.22:80 | http://borfkyk.com/click/?counter=de7ef49b2c006853fb38357b3206f31360ff1905c311578eaae3c7edb62cde24353e1d9a943e9d15038842935de14feaa4a21bca13c034069238dc1a959a22237244a421216497c02320889f8f71035f8edc06fd10ccd95cb322 | unknown | text | 14 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2312 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2312 | 4363463463464363463463463.exe | 88.212.202.2:80 | websound.ru | United Network LLC | RU | unknown |
2312 | 4363463463464363463463463.exe | 104.21.46.59:80 | cream.hitsturbo.com | CLOUDFLARENET | — | unknown |
2312 | 4363463463464363463463463.exe | 212.12.151.74:80 | www.teknoarge.com | Vodafone Net Iletisim Hizmetleri Anonim Sirketi | TR | unknown |
2312 | 4363463463464363463463463.exe | 185.85.191.197:443 | www.bakirkoynakliyat.gen.tr | Ideal Hosting Teknoloji A.S. | TR | unknown |
2312 | 4363463463464363463463463.exe | 46.252.148.24:443 | 1ecosolution.it | Netsons s.r.l. | IT | unknown |
2312 | 4363463463464363463463463.exe | 104.21.37.191:80 | rusticironstore.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
websound.ru |
| malicious |
cream.hitsturbo.com |
| malicious |
www.teknoarge.com |
| unknown |
www.bakirkoynakliyat.gen.tr |
| unknown |
1ecosolution.it |
| unknown |
rusticironstore.com |
| malicious |
chardhesha.xyz |
| unknown |
jalocliche.xyz |
| unknown |
borfkyk.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2312 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2312 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2312 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2312 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2312 | 4363463463464363463463463.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2312 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2312 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2312 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2312 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2312 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
Process | Message |
|---|---|
4363463463464363463463463.exe | The request was aborted: Could not create SSL/TLS secure channel.
|