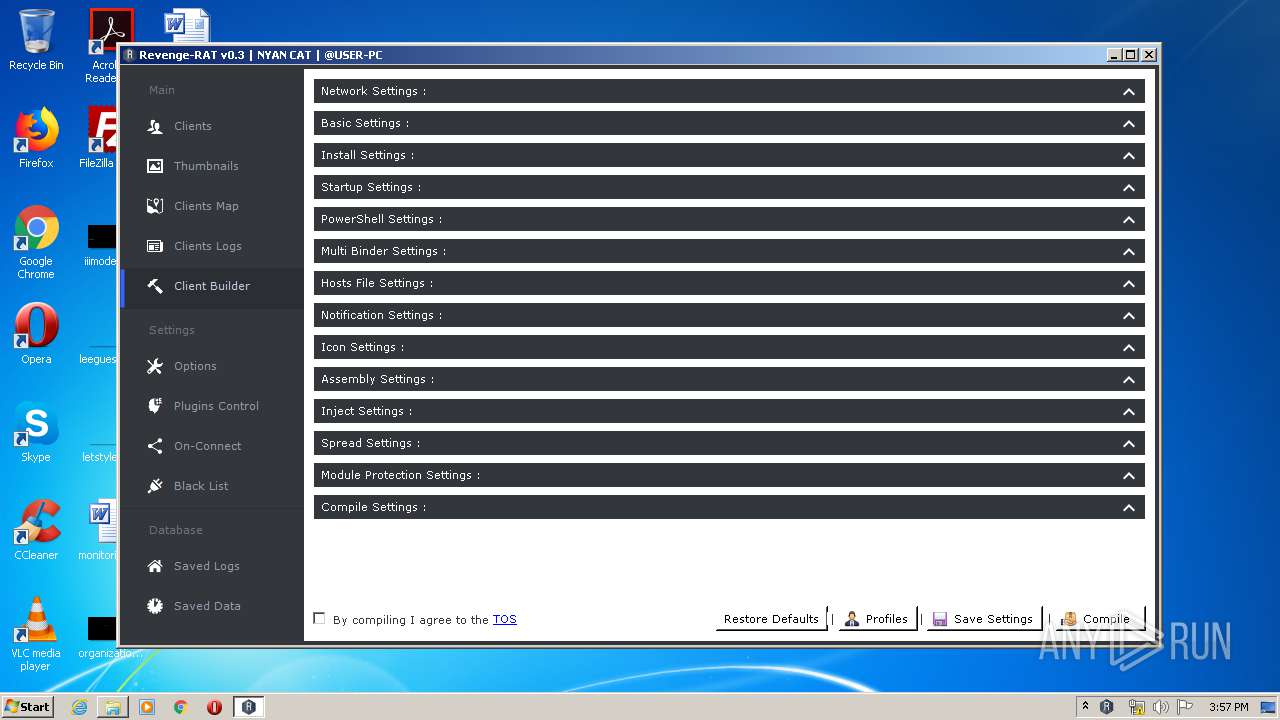
| File name: | Revenge-RAT v.0.3 Mod By NYAN CAT.rar |
| Full analysis: | https://app.any.run/tasks/62e023f9-622d-4aee-9c84-38d1a90ed910 |
| Verdict: | Malicious activity |
| Analysis date: | April 17, 2020, 14:56:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 8FC2F28088F2145F29AC70DC2658B34D |
| SHA1: | B24A6810C3AE97CCD56877E5226C06E3ED80E277 |
| SHA256: | 457E6E59293E7BB40D4BE31650E224B52FF71165D3CE8FCAA7360AAB881D0140 |
| SSDEEP: | 393216:scbu8oOu6g1p4TvH9kJpbsXmNqtRcj7aJKG+JT2:hS7xmT/SbemYXm73G+2 |
MALICIOUS
Actions looks like stealing of personal data
- WinRAR.exe (PID: 1544)
- SearchProtocolHost.exe (PID: 4088)
Application was dropped or rewritten from another process
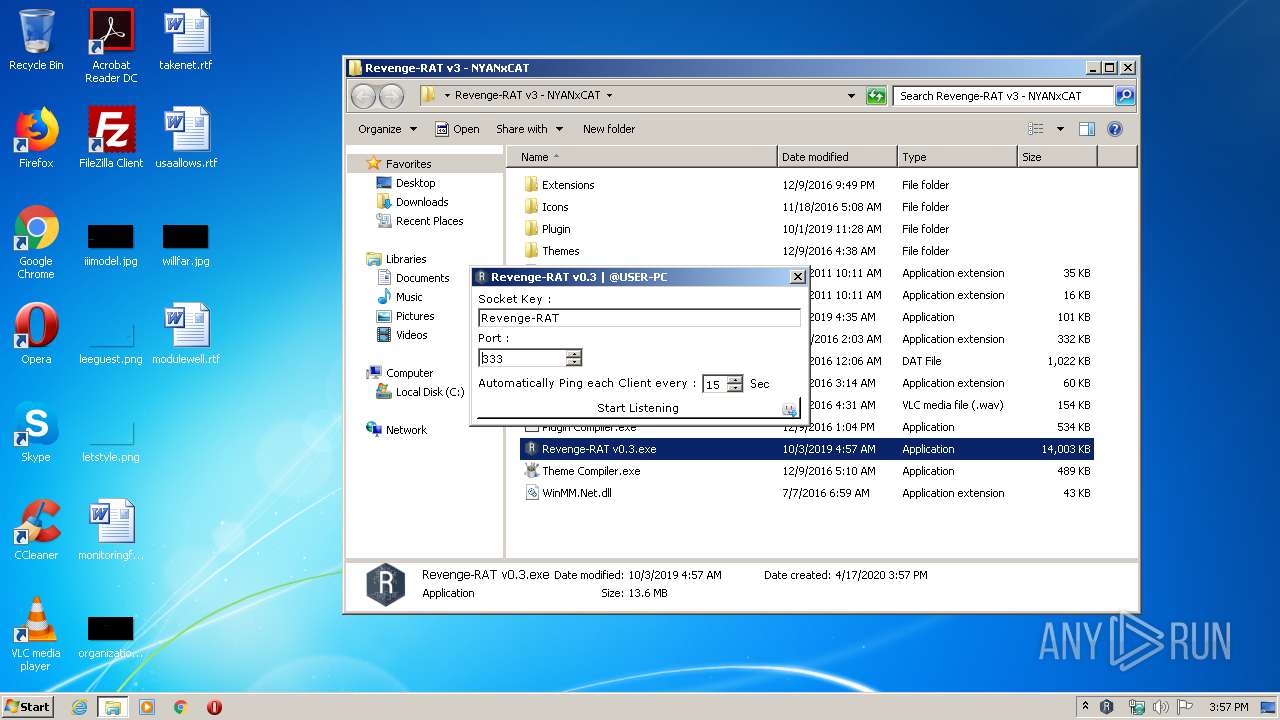
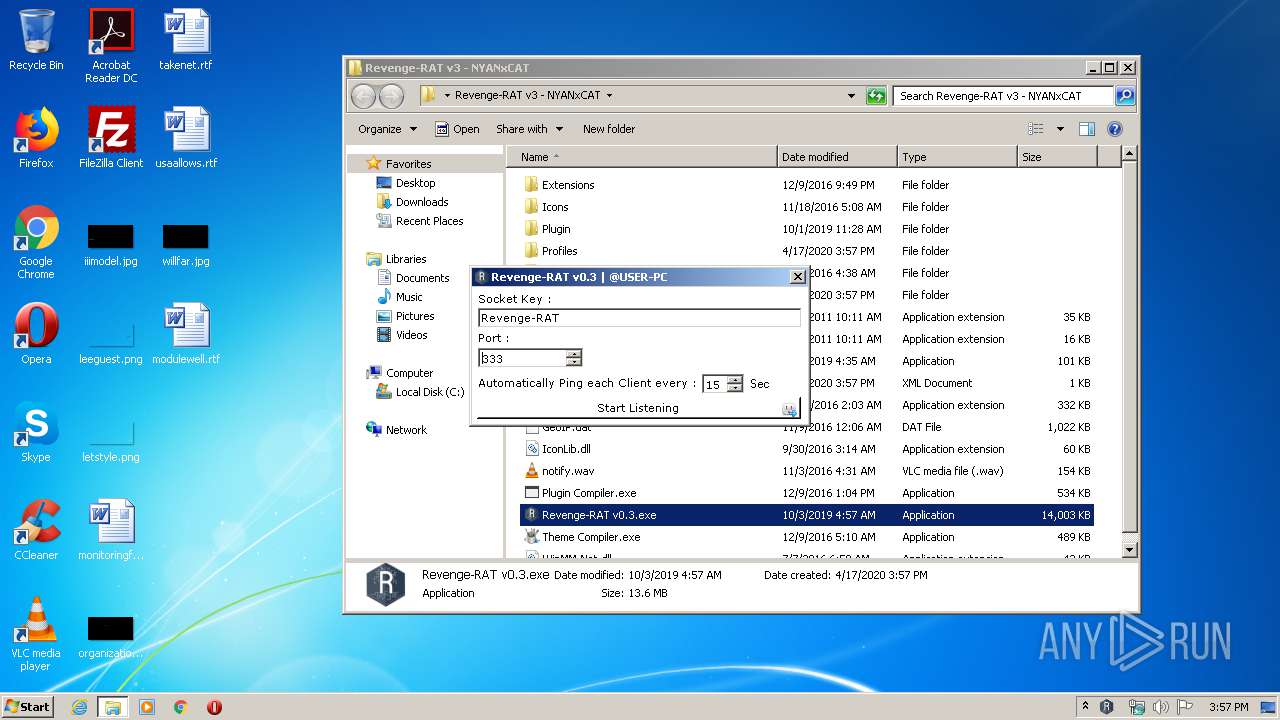
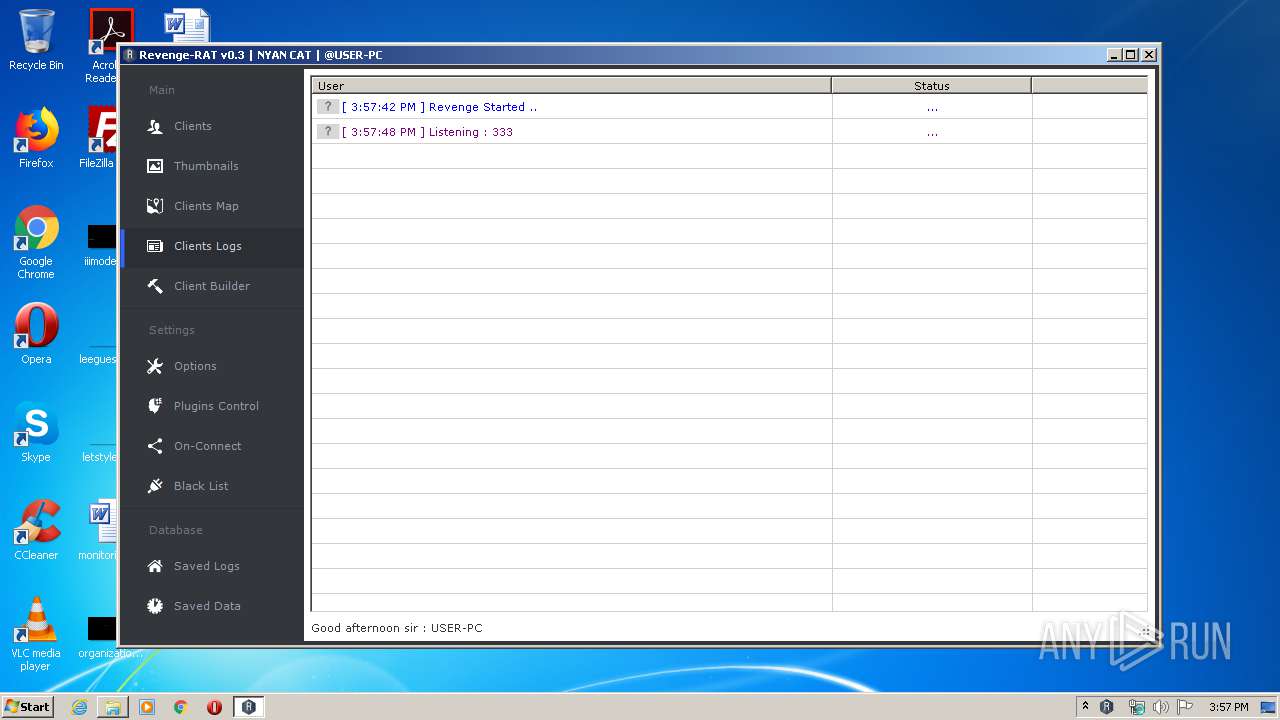
- Revenge-RAT v0.3.exe (PID: 3680)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 4088)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1544)
Reads internet explorer settings
- Revenge-RAT v0.3.exe (PID: 3680)
INFO
Manual execution by user
- Revenge-RAT v0.3.exe (PID: 3680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1544 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Revenge-RAT v.0.3 Mod By NYAN CAT.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3680 | "C:\Users\admin\Desktop\Revenge-RAT v3 - NYANxCAT\Revenge-RAT v0.3.exe" | C:\Users\admin\Desktop\Revenge-RAT v3 - NYANxCAT\Revenge-RAT v0.3.exe | — | explorer.exe | |||||||||||
User: admin Company: Revenge-RAT v0.3 Integrity Level: MEDIUM Description: Revenge-RAT v0.3 Exit code: 0 Version: 0.0.0.3 Modules
| |||||||||||||||
| 4088 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | SearchIndexer.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
810
Read events
785
Write events
25
Delete events
0
Modification events
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Revenge-RAT v.0.3 Mod By NYAN CAT.rar | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
19
Suspicious files
16
Text files
71
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1544.28009\Revenge-RAT v3 - NYANxCAT\Builder.exe | executable | |
MD5:— | SHA256:— | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1544.28009\Revenge-RAT v3 - NYANxCAT\Extensions\AHK\Ahk2Exe.exe | executable | |
MD5:D717D5943BDCA2758360E4FA3B008A49 | SHA256:E2A00647B5FA56B077D3D07B1C05E3B76B7269E07FC3EA84750EB03AD71024DE | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1544.28009\Revenge-RAT v3 - NYANxCAT\Extensions\Admin.res | res | |
MD5:9E434A1B7CAD1906E90769032E707B8F | SHA256:6BDDC039731D8FEE3F86CA1845507A6707E21954383E73483F1DC6B62854110B | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1544.28009\Revenge-RAT v3 - NYANxCAT\AForge.Video.dll | executable | |
MD5:A614D58E17BA34826B59C4942C32F078 | SHA256:311724FF73B331CD6DE0649B01923F7E43D168AA5B1E7F031B2B175148062757 | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1544.28009\Revenge-RAT v3 - NYANxCAT\Extensions\AHK\Unicode 32-bit.bin | executable | |
MD5:B86564D0EB29A5FAAB9E8DAACF269DF4 | SHA256:2514235C34D17FDB4A8448BD088D89F631F5D70F12F5F7D5EE552144A345ED2D | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1544.28009\Revenge-RAT v3 - NYANxCAT\AForge.Video.DirectShow.dll | executable | |
MD5:2343899EA6B3DFF06A6DB2F0FBD86406 | SHA256:643A7F9754D90D475DB3F84AF7B254A64DD555CED0F039AAA4F08B5B27AB4FDB | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1544.28009\Revenge-RAT v3 - NYANxCAT\Extensions\AHK\AHK.ahk | text | |
MD5:A908B151CC37C66AEAFF20D43BA0CAE0 | SHA256:B032B99C88289C02388BD1DB21A3CFC34AC9AB36BC48BE5D6570AC6497F70E56 | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1544.28009\Revenge-RAT v3 - NYANxCAT\Extensions\AHK\AutoHotkeySC.bin | executable | |
MD5:B86564D0EB29A5FAAB9E8DAACF269DF4 | SHA256:2514235C34D17FDB4A8448BD088D89F631F5D70F12F5F7D5EE552144A345ED2D | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1544.28009\Revenge-RAT v3 - NYANxCAT\Extensions\Aut2Exe\Icons\AutoIt_Main_v10_48x48_256.ico | image | |
MD5:88624B8E01AC8036B6F1971B497DBB7E | SHA256:BADC42DA4C0E29AF7F6C0C58711D9DB7B3D7D4760C18CB521F4113D8CDBC2F3D | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1544.28009\Revenge-RAT v3 - NYANxCAT\Extensions\Aut2Exe\Icons\AutoIt_Main_v9_48x48_256.ico | image | |
MD5:A87C314DD8B1FDE98FCA6E504F5FF8A0 | SHA256:C43AD7216D3F7553AE87A03F23D3BE0D6F9C5212E5DCE3D38B8E8A433A549DCA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report