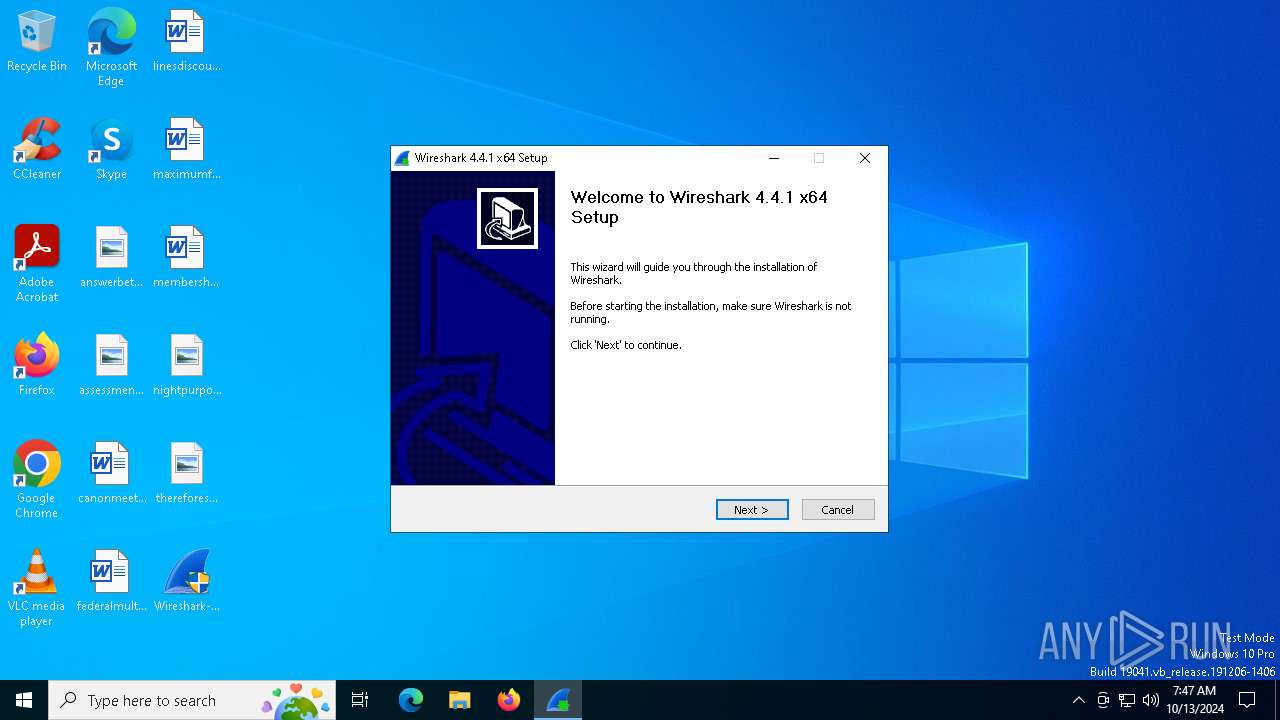
| File name: | Wireshark-4.4.1-x64.exe |
| Full analysis: | https://app.any.run/tasks/753dc38f-a192-4b6e-ae34-2addf013a76b |
| Verdict: | Malicious activity |
| Analysis date: | October 13, 2024, 07:46:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 01031C48A2D1417A33999B121EA77CAF |
| SHA1: | 2EC7A04154538D63DAD26E9E527AD55FA50CCF01 |
| SHA256: | 456AEC8658BAEE56FF4ADD4BCFD95ED532219536B568B5E45106A0120921E58D |
| SSDEEP: | 786432:pqfhgWiAzOlTCz/qWLP4Z/5LvuCxa0g2caIAedF/KL:0CWiAzyTC7qWT4F5LvuAjgGI7F/KL |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 6196)
- powershell.exe (PID: 6088)
- powershell.exe (PID: 5852)
- powershell.exe (PID: 3952)
- powershell.exe (PID: 6972)
- powershell.exe (PID: 5048)
SUSPICIOUS
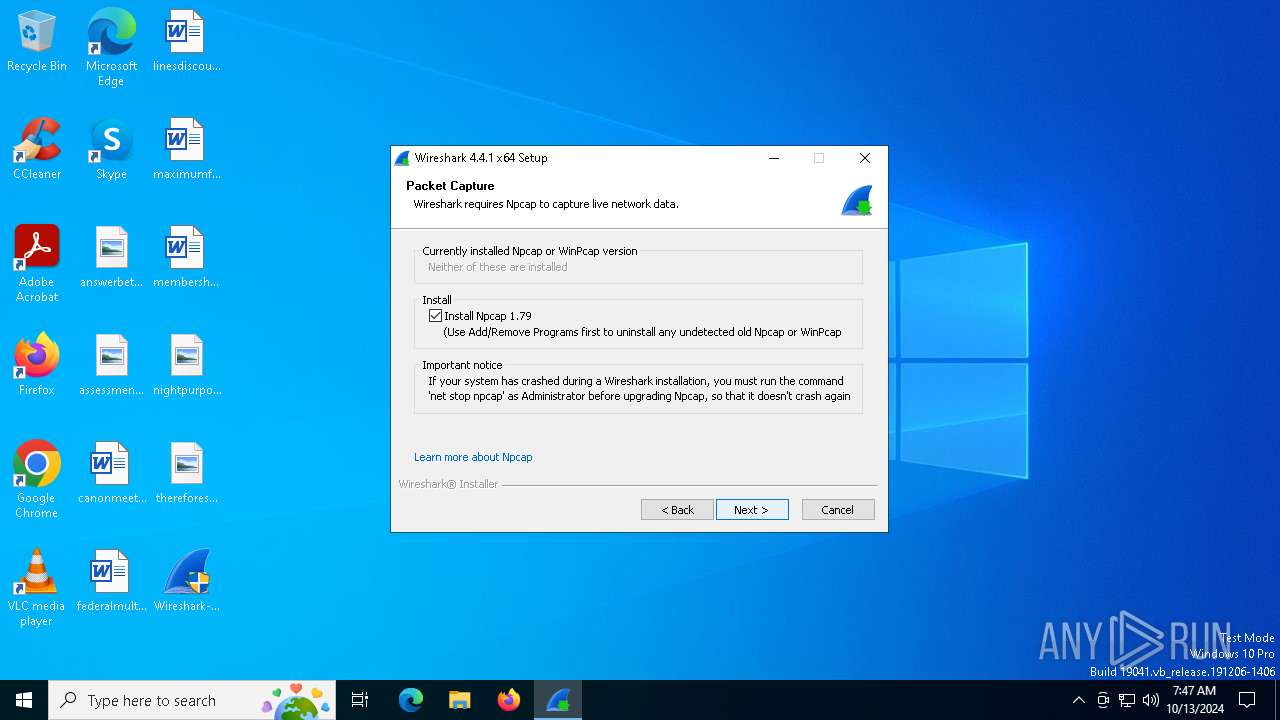
Malware-specific behavior (creating "System.dll" in Temp)
- Wireshark-4.4.1-x64.exe (PID: 6996)
- npcap-1.79.exe (PID: 2056)
Searches for installed software
- Wireshark-4.4.1-x64.exe (PID: 6996)
- vc_redist.x64.exe (PID: 6956)
- dllhost.exe (PID: 3944)
The process creates files with name similar to system file names
- Wireshark-4.4.1-x64.exe (PID: 6996)
Executable content was dropped or overwritten
- Wireshark-4.4.1-x64.exe (PID: 6996)
- vc_redist.x64.exe (PID: 7160)
- VC_redist.x64.exe (PID: 3772)
- vc_redist.x64.exe (PID: 6956)
- VC_redist.x64.exe (PID: 5160)
- VC_redist.x64.exe (PID: 6892)
- npcap-1.79.exe (PID: 2056)
- NPFInstall.exe (PID: 6604)
- drvinst.exe (PID: 6828)
Process drops legitimate windows executable
- Wireshark-4.4.1-x64.exe (PID: 6996)
- vc_redist.x64.exe (PID: 7160)
- vc_redist.x64.exe (PID: 6956)
- VC_redist.x64.exe (PID: 5160)
- VC_redist.x64.exe (PID: 3772)
- msiexec.exe (PID: 5588)
Starts a Microsoft application from unusual location
- vc_redist.x64.exe (PID: 6956)
- VC_redist.x64.exe (PID: 3772)
Reads security settings of Internet Explorer
- vc_redist.x64.exe (PID: 6956)
Starts itself from another location
- vc_redist.x64.exe (PID: 6956)
Executes as Windows Service
- VSSVC.exe (PID: 1784)
Application launched itself
- VC_redist.x64.exe (PID: 6892)
- VC_redist.x64.exe (PID: 7000)
Starts POWERSHELL.EXE for commands execution
- npcap-1.79.exe (PID: 2056)
Drops a system driver (possible attempt to evade defenses)
- npcap-1.79.exe (PID: 2056)
- NPFInstall.exe (PID: 6604)
- drvinst.exe (PID: 6828)
The process bypasses the loading of PowerShell profile settings
- npcap-1.79.exe (PID: 2056)
The process hide an interactive prompt from the user
- npcap-1.79.exe (PID: 2056)
The process drops C-runtime libraries
- msiexec.exe (PID: 5588)
INFO
Create files in a temporary directory
- Wireshark-4.4.1-x64.exe (PID: 6996)
- vc_redist.x64.exe (PID: 6956)
Checks supported languages
- Wireshark-4.4.1-x64.exe (PID: 6996)
- vc_redist.x64.exe (PID: 7160)
- VC_redist.x64.exe (PID: 3772)
- vc_redist.x64.exe (PID: 6956)
Reads the computer name
- Wireshark-4.4.1-x64.exe (PID: 6996)
- vc_redist.x64.exe (PID: 7160)
- VC_redist.x64.exe (PID: 3772)
- vc_redist.x64.exe (PID: 6956)
Creates files in the program directory
- Wireshark-4.4.1-x64.exe (PID: 6996)
The process uses the downloaded file
- vc_redist.x64.exe (PID: 6956)
Process checks computer location settings
- vc_redist.x64.exe (PID: 6956)
Manages system restore points
- SrTasks.exe (PID: 5932)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:02 02:09:43+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3645 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.4.1.0 |
| ProductVersionNumber: | 4.4.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | It's a great product with a great story to tell. I'm pumped! |
| CompanyName: | Wireshark development team |
| FileDescription: | Wireshark installer for Windows on x64 |
| FileVersion: | 4.4.1.0 |
| Language: | English |
| LegalCopyright: | © Gerald Combs and many others |
| LegalTrademarks: | Wireshark and the 'fin' logo are registered trademarks of the Wireshark Foundation |
| ProductName: | Wireshark |
| ProductVersion: | 4.4.1.0 |
Total processes
167
Monitored processes
49
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | pnputil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 700 | "C:\Program Files\Npcap\NPFInstall.exe" -n -c | C:\Program Files\Npcap\NPFInstall.exe | — | npcap-1.79.exe | |||||||||||
User: admin Company: Insecure.Com LLC. Integrity Level: HIGH Description: A LWF & WFP driver installation tool Exit code: 0 Version: 1.79 Modules
| |||||||||||||||
| 712 | certutil.exe -verifystore "Root" "0563b8630d62d75abbc8ab1e4bdfb5a899b24d43" | C:\Windows\SysWOW64\certutil.exe | — | npcap-1.79.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 2148073489 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1396 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1784 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2056 | "C:\Program Files\Wireshark\npcap-1.79.exe" /winpcap_mode=no /loopback_support=no | C:\Program Files\Wireshark\npcap-1.79.exe | Wireshark-4.4.1-x64.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Npcap 1.79 installer Version: 1.79 Modules
| |||||||||||||||
| 2808 | "C:\Program Files\Npcap\NPFInstall.exe" -n -iw | C:\Program Files\Npcap\NPFInstall.exe | — | npcap-1.79.exe | |||||||||||
User: admin Company: Insecure.Com LLC. Integrity Level: HIGH Description: A LWF & WFP driver installation tool Exit code: 0 Version: 1.79 Modules
| |||||||||||||||
| 3008 | "C:\Users\admin\AppData\Local\Temp\nsv398F.tmp\NPFInstall.exe" -n -check_dll | C:\Users\admin\AppData\Local\Temp\nsv398F.tmp\NPFInstall.exe | — | npcap-1.79.exe | |||||||||||
User: admin Company: Insecure.Com LLC. Integrity Level: HIGH Description: A LWF & WFP driver installation tool Exit code: 0 Version: 1.79 Modules
| |||||||||||||||
| 3508 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | NPFInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
58 457
Read events
57 373
Write events
697
Delete events
387
Modification events
| (PID) Process: | (3772) VC_redist.x64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000774D3731441DDB01BC0E00009C0E0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3944) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000774D3731441DDB01680F0000700B0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3944) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000010469431441DDB01680F0000700B0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3944) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000010469431441DDB01680F0000700B0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3944) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000009CA99631441DDB01680F0000700B0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3944) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000390D9931441DDB01680F0000700B0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3944) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (3944) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000BA881E32441DDB01680F0000700B0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3944) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000049EC2032441DDB01680F0000E4120000E8030000010000000000000000000000CBE8768786436D429F7BE4C8D82A73C800000000000000000000000000000000 | |||
| (PID) Process: | (1784) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000537D2A32441DDB01F806000058190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
148
Suspicious files
69
Text files
402
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6996 | Wireshark-4.4.1-x64.exe | C:\Program Files\Wireshark\libwireshark.dll | — | |
MD5:— | SHA256:— | |||
| 6996 | Wireshark-4.4.1-x64.exe | C:\Users\admin\AppData\Local\Temp\nsj1DBF.tmp\DonatePage.ini | text | |
MD5:A0580CB2D6831AB488353AB56658E59D | SHA256:B23B78B14231A2B48506BAB2AB82EE9477BA280A1BC31E2370640E644F5D35FF | |||
| 6996 | Wireshark-4.4.1-x64.exe | C:\Users\admin\AppData\Local\Temp\nsj1DBF.tmp\System.dll | executable | |
MD5:4ADD245D4BA34B04F213409BFE504C07 | SHA256:9111099EFE9D5C9B391DC132B2FAF0A3851A760D4106D5368E30AC744EB42706 | |||
| 6996 | Wireshark-4.4.1-x64.exe | C:\Users\admin\AppData\Local\Temp\nsj1DBF.tmp\InstallOptions.dll | executable | |
MD5:D095B082B7C5BA4665D40D9C5042AF6D | SHA256:B2091205E225FC07DAF1101218C64CE62A4690CACAC9C3D0644D12E93E4C213C | |||
| 6996 | Wireshark-4.4.1-x64.exe | C:\Users\admin\AppData\Local\Temp\nsj1DBF.tmp\NpcapPage.ini | text | |
MD5:96909F6D41A24839661D126CB8F1949F | SHA256:6E726FFB528C6135E2405AC37626A7537EF1AE0A354CBFB55DE0E6E5DBC325EF | |||
| 6996 | Wireshark-4.4.1-x64.exe | C:\Users\admin\AppData\Local\Temp\nsj1DBF.tmp\nsDialogs.dll | executable | |
MD5:1D8F01A83DDD259BC339902C1D33C8F1 | SHA256:4B7D17DA290F41EBE244827CC295CE7E580DA2F7E9F7CC3EFC1ABC6898E3C9ED | |||
| 6996 | Wireshark-4.4.1-x64.exe | C:\Users\admin\AppData\Local\Temp\nsj1DBF.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 6996 | Wireshark-4.4.1-x64.exe | C:\Program Files\Wireshark\charset-1.dll | executable | |
MD5:5193C4DD36157A59295EB1CECF4312D8 | SHA256:8E1CBBD370B4B358726426C0FDE4E5DE08F9D4FA6D1B51D5AA3CB0E241AD6A5F | |||
| 6996 | Wireshark-4.4.1-x64.exe | C:\Program Files\Wireshark\uninstall-wireshark.exe | executable | |
MD5:3EF19DAF7BFF4B65FCA47D8A4F9C74F4 | SHA256:A5E918E8DC78172FABE07EEC41BFFE48084262FBBF2566CAD4A3405FCF7F2F0A | |||
| 6996 | Wireshark-4.4.1-x64.exe | C:\Program Files\Wireshark\libwiretap.dll | executable | |
MD5:7AB890CD09D1F048045FCA9E127C0D71 | SHA256:10D07D4769856F774AB7F59DD96D26B8E356D3D047311AB63D908A8F5BD1D906 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
23
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5588 | msiexec.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5588 | msiexec.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
msiexec.exe | Failed to release Service
|