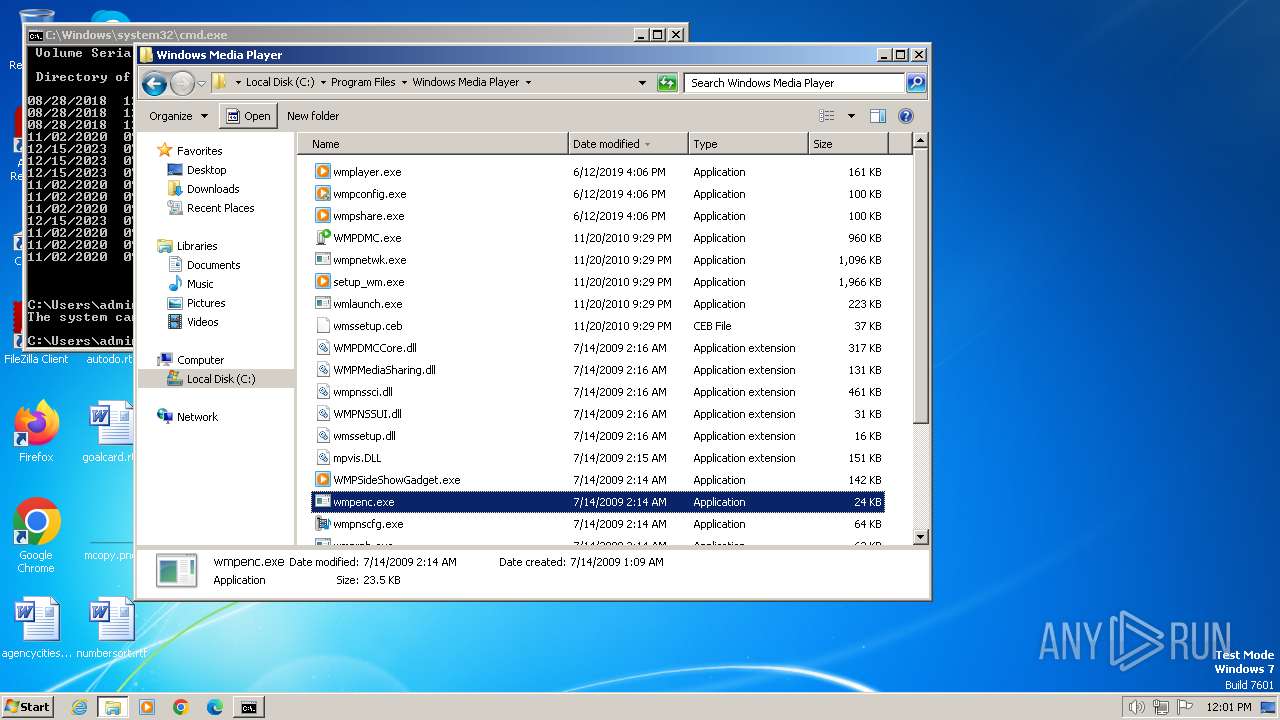
| File name: | Handala.exe |
| Full analysis: | https://app.any.run/tasks/7c3ad2d7-d3b7-434d-a911-4b058fc50c9e |
| Verdict: | Malicious activity |
| Analysis date: | December 20, 2023, 12:00:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 4551A6CDF8D23A96AA4124AC9BDB6D1D |
| SHA1: | B75B6CEBE869E1636F0F294954B7906A4905701A |
| SHA256: | 454E6D3782F23455875A5DB64E1A8CD8EB743400D8C6DADB1CD8FD2FFC2F9567 |
| SSDEEP: | 98304:iZRotmkeOvi8qq7bCIcjjjo7VexhVDWcyenO+ptBjVbezGqyZKoSRTkE: |
MALICIOUS
Drops the executable file immediately after the start
- Handala.exe (PID: 2184)
- cmd.exe (PID: 1044)
Actions looks like stealing of personal data
- dialer.exe (PID: 2620)
SUSPICIOUS
Get information on the list of running processes
- cmd.exe (PID: 1404)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1404)
Starts CMD.EXE for commands execution
- Handala.exe (PID: 2184)
- cmd.exe (PID: 116)
- cmd.exe (PID: 1404)
Application launched itself
- cmd.exe (PID: 116)
- cmd.exe (PID: 1404)
Drops the AutoIt3 executable file
- cmd.exe (PID: 1044)
Starts application with an unusual extension
- cmd.exe (PID: 1404)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1404)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 2620)
Connects to unusual port
- dialer.exe (PID: 2620)
Loads DLL from Mozilla Firefox
- dialer.exe (PID: 2620)
Searches for installed software
- dialer.exe (PID: 2620)
Accesses Microsoft Outlook profiles
- dialer.exe (PID: 2620)
Reads browser cookies
- dialer.exe (PID: 2620)
INFO
Checks supported languages
- Handala.exe (PID: 2184)
- Naples.pif (PID: 1608)
- wmpnscfg.exe (PID: 2060)
- setup_wm.exe (PID: 2960)
Create files in a temporary directory
- Handala.exe (PID: 2184)
The executable file from the user directory is run by the CMD process
- Naples.pif (PID: 1608)
Reads the computer name
- wmpnscfg.exe (PID: 2060)
- Naples.pif (PID: 1608)
- setup_wm.exe (PID: 2960)
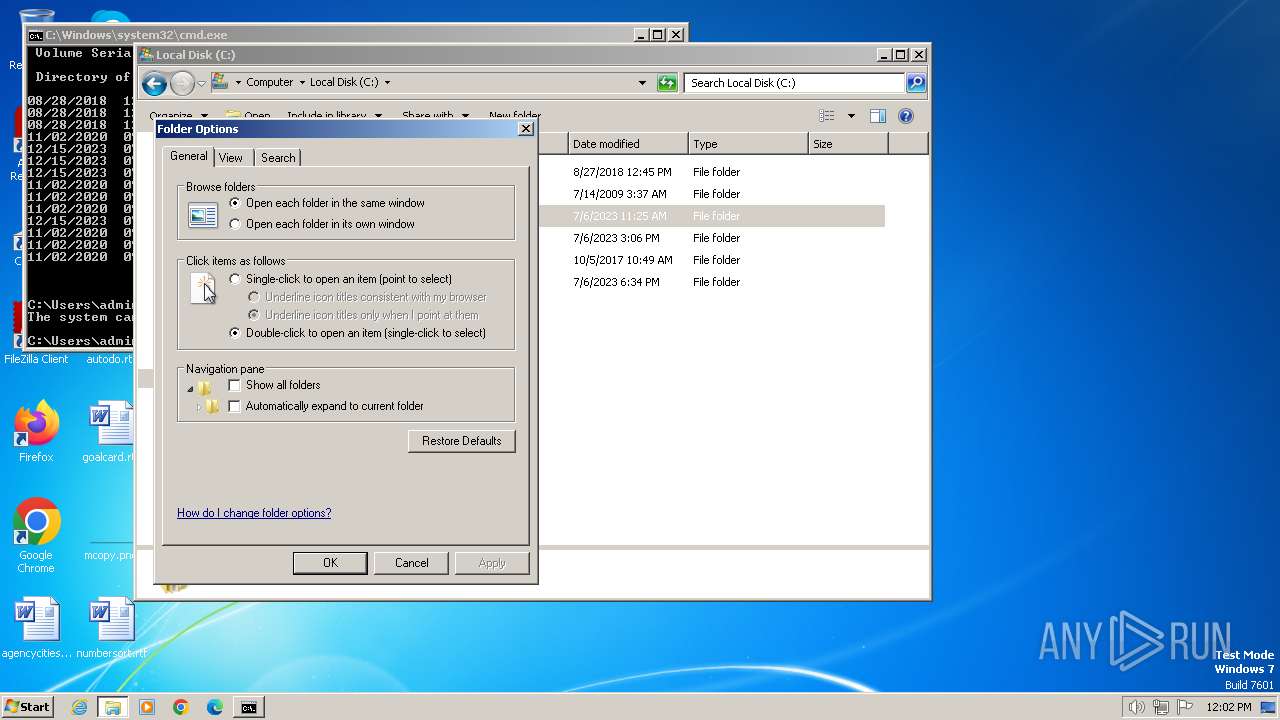
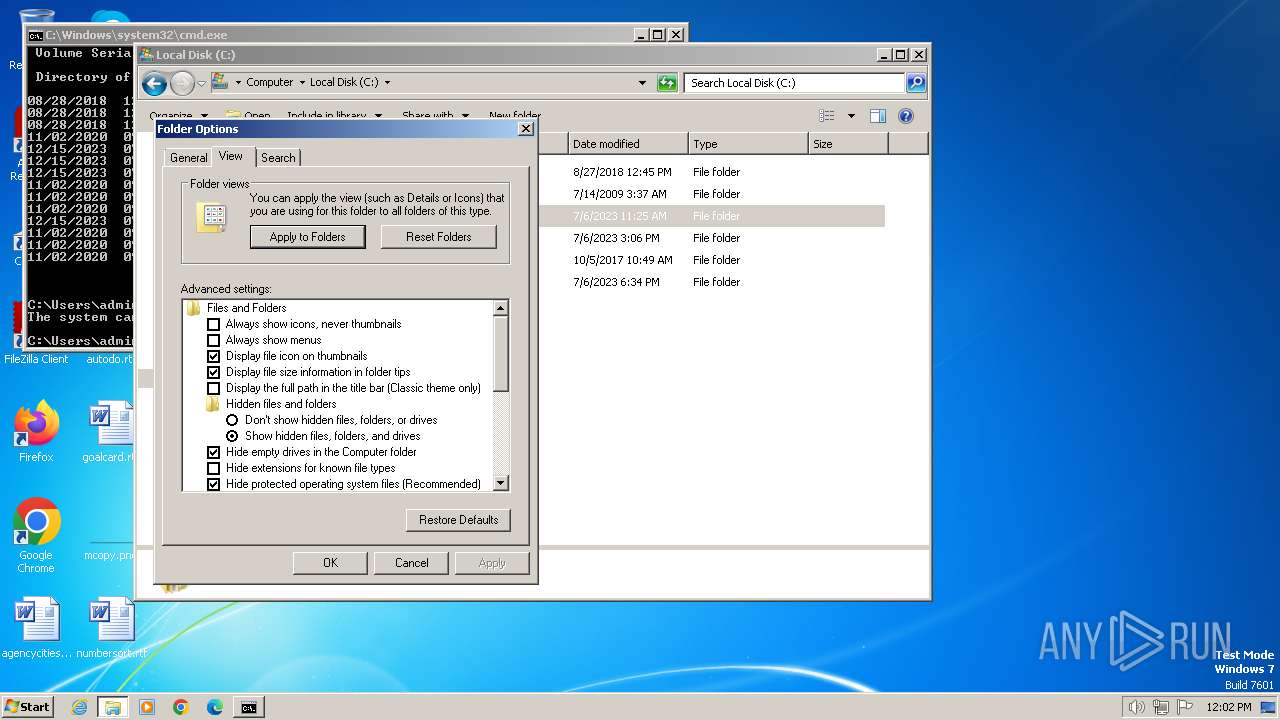
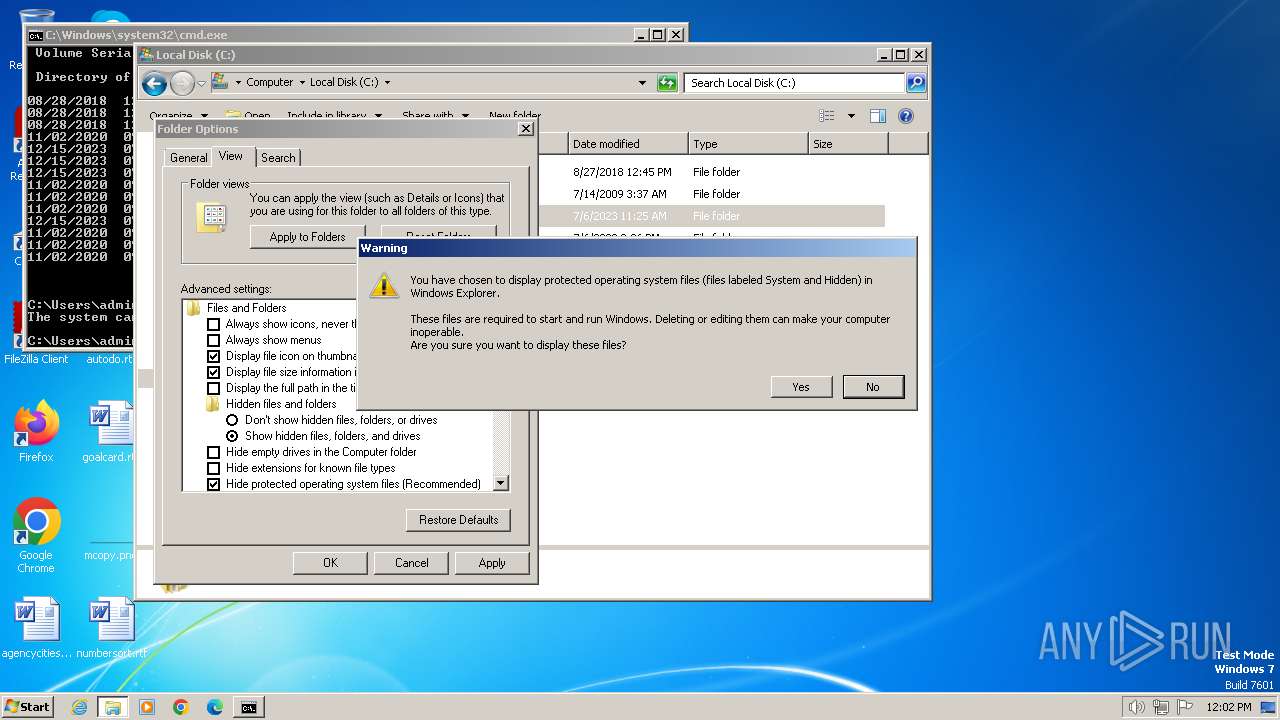
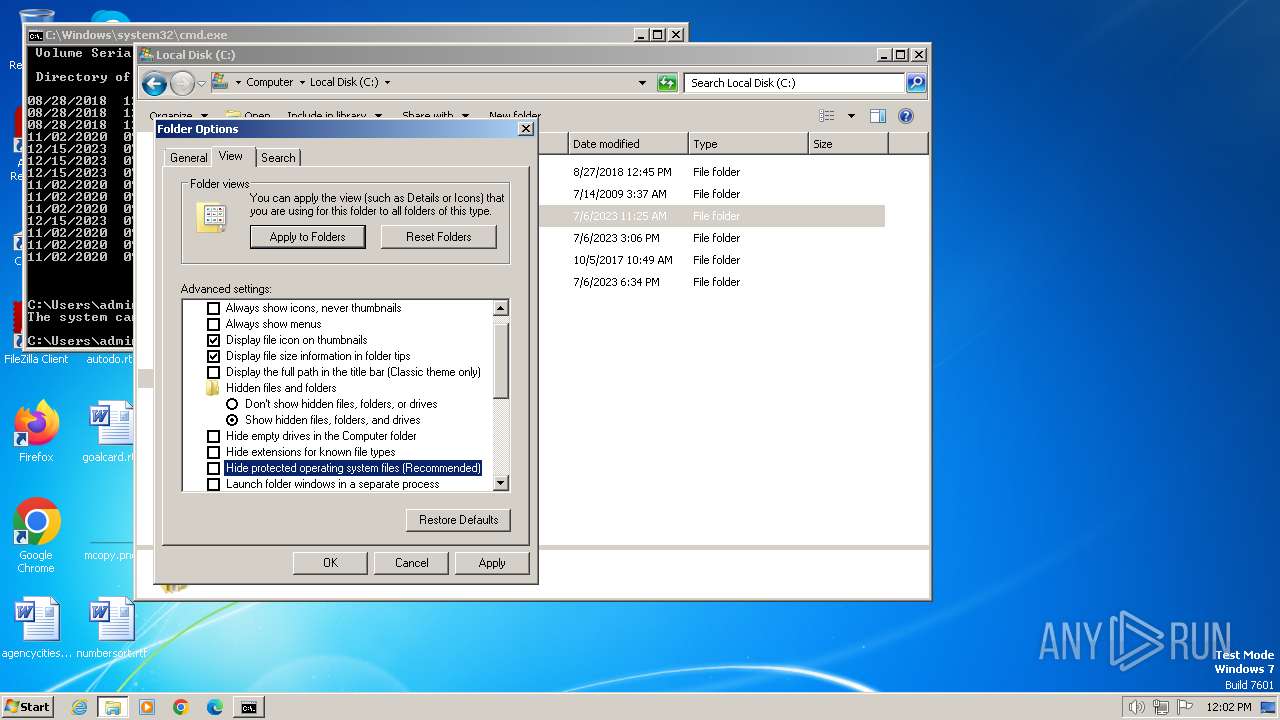
Manual execution by a user
- wmpnscfg.exe (PID: 2060)
- cmd.exe (PID: 1796)
- explorer.exe (PID: 1544)
Reads mouse settings
- Naples.pif (PID: 1608)
Reads the machine GUID from the registry
- setup_wm.exe (PID: 2960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (37.4) |
|---|---|---|
| .scr | | | Windows screen saver (34.5) |
| .exe | | | Win32 Executable (generic) (11.9) |
| .exe | | | Win16/32 Executable Delphi generic (5.4) |
| .exe | | | Generic Win/DOS Executable (5.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:06:01 06:51:40+02:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 677376 |
| InitializedDataSize: | 167424 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa6a40 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.9.2.5320 |
| ProductVersionNumber: | 3.9.2.5320 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | Safeguards pixel-perfect visuals. |
| CompanyName: | PixelGuard |
| FileDescription: | Safeguards pixel-perfect visuals. |
| FileVersion: | 3.09.2.05320 |
| InternalName: | PixelGuard |
| LegalCopyright: | Copyright © PixelShield Innovations 2009 |
| ProductName: | PixelGuard |
| ProductVersion: | 3.09.2.05320 |
Total processes
61
Monitored processes
17
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | cmd /k cmd < Closest & exit | C:\Windows\System32\cmd.exe | — | Handala.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 316 | cmd /c mkdir 5826 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 392 | findstr /I "avastui.exe avgui.exe nswscsvc.exe sophoshealth.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1044 | cmd /c copy /b Bw + Vessels + Boy + Conventions 5826\Naples.pif | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1308 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1404 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1504 | cmd /c copy /b Beastiality + Bicycle + Employee 5826\k | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1544 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1588 | ping -n 5 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1608 | 5826\Naples.pif 5826\k | C:\Users\admin\AppData\Local\Temp\1902\5826\Naples.pif | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 3221225477 Version: 3, 3, 15, 4 Modules
| |||||||||||||||
Total events
2 034
Read events
2 034
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
3
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2184 | Handala.exe | C:\Users\admin\AppData\Local\Temp\1902\Beastiality | text | |
MD5:2D384D381FFBA7D5076CDF42E98D9A81 | SHA256:435A75AEEA35A2A8FFCE5999B59CB10F2585297BA042534C74DC6020CC484021 | |||
| 2184 | Handala.exe | C:\Users\admin\AppData\Local\Temp\1902\Bw | executable | |
MD5:AE619C929286509B680A4A370639FFEE | SHA256:0FE492C8F80A8B86AF0BD3BF3AB3538A91E051C651CFCB885B4004E9BD02DEE3 | |||
| 1504 | cmd.exe | C:\Users\admin\AppData\Local\Temp\1902\5826\k | text | |
MD5:CB8F9591F7F71E6091BF54A768289A7D | SHA256:AAE989743DDDC84ADEF90622C657E45E23386488FA79D7FE7CF0863043B8ACD4 | |||
| 2184 | Handala.exe | C:\Users\admin\AppData\Local\Temp\1902\Conventions | binary | |
MD5:7B8E5E61631061632DF28F1D9AC15385 | SHA256:A3D1D89A9881AE98B23E5B9BD68CD38C51DDECC71364296BDB43832495C87F17 | |||
| 2184 | Handala.exe | C:\Users\admin\AppData\Local\Temp\1902\Vessels | binary | |
MD5:399FC3EE7AA5F8E199EA3B1E0CB6CBF7 | SHA256:20B618C9D4916218C5439C2AA06CB09E8C10011F20439DB907030A0E1EF96243 | |||
| 2184 | Handala.exe | C:\Users\admin\AppData\Local\Temp\1902\Bicycle | text | |
MD5:580E0CBEE6DB2BF834D325BFF5A56F63 | SHA256:E4A2F395CC17B865D017A9269C579995911307A4DB71D60EAA791C9FA9A466C0 | |||
| 1044 | cmd.exe | C:\Users\admin\AppData\Local\Temp\1902\5826\Naples.pif | executable | |
MD5:848164D084384C49937F99D5B894253E | SHA256:F58D3A4B2F3F7F10815C24586FAE91964EEED830369E7E0701B43895B0CEFBD3 | |||
| 2184 | Handala.exe | C:\Users\admin\AppData\Local\Temp\1902\Closest | text | |
MD5:3B08DFBE8A776B48A98A74F30E4A55B6 | SHA256:58C611FFD8453AA057CC9F0E0578CE69D75F84236B277DD363C3E539659D1CF3 | |||
| 2184 | Handala.exe | C:\Users\admin\AppData\Local\Temp\1902\Boy | binary | |
MD5:0847E05E476FD8D78518DCD87E25BB5F | SHA256:291A97997CD42C882E214D895B385620575B54F301FAB4EBC666F1E1F28ECEB4 | |||
| 2184 | Handala.exe | C:\Users\admin\AppData\Local\Temp\1902\Employee | text | |
MD5:C308F73152E8EABF669AE2BFD83E305F | SHA256:7B064F872F7556ED5FBD2E66A43642C95832438C0DCE4849052879DFA430E4C7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
9
DNS requests
1
Threats
8
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2620 | dialer.exe | 31.192.237.207:2515 | — | Chelyabinsk-Signal LLC | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
EmPrDEFzwuyuiFypScQwalNecR.EmPrDEFzwuyuiFypScQwalNecR |
| unknown |
Threats
8 ETPRO signatures available at the full report