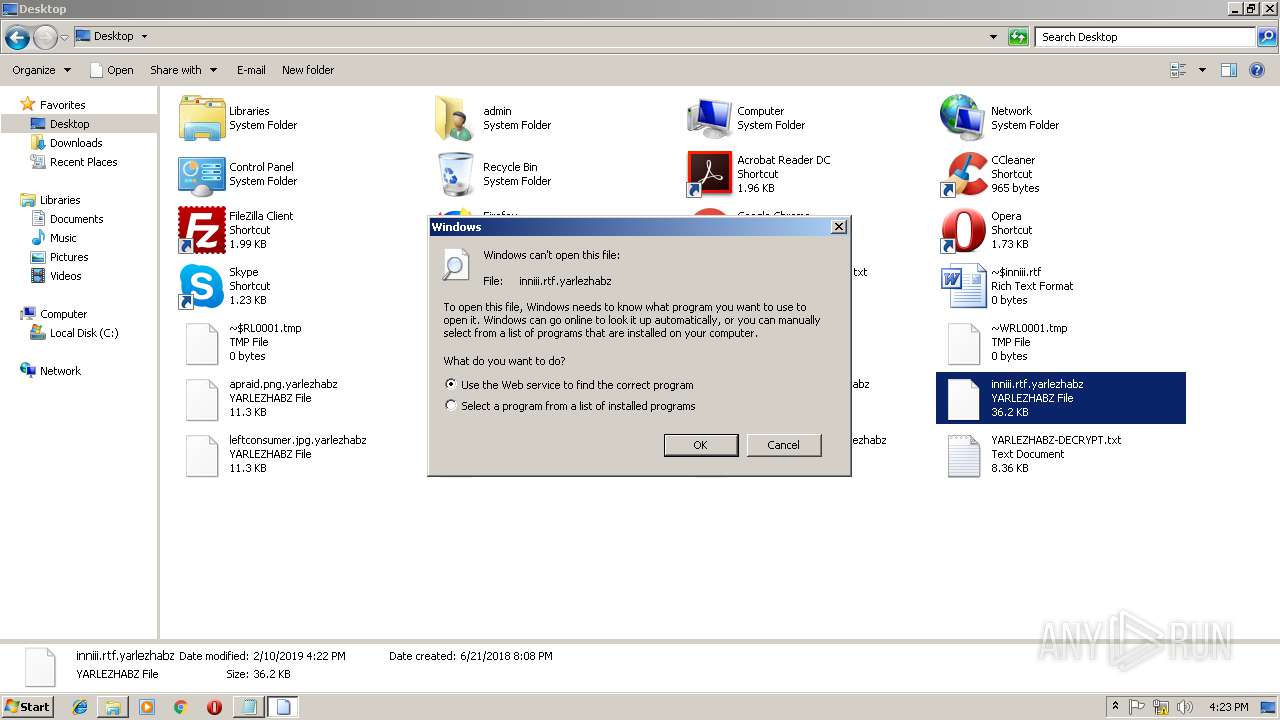
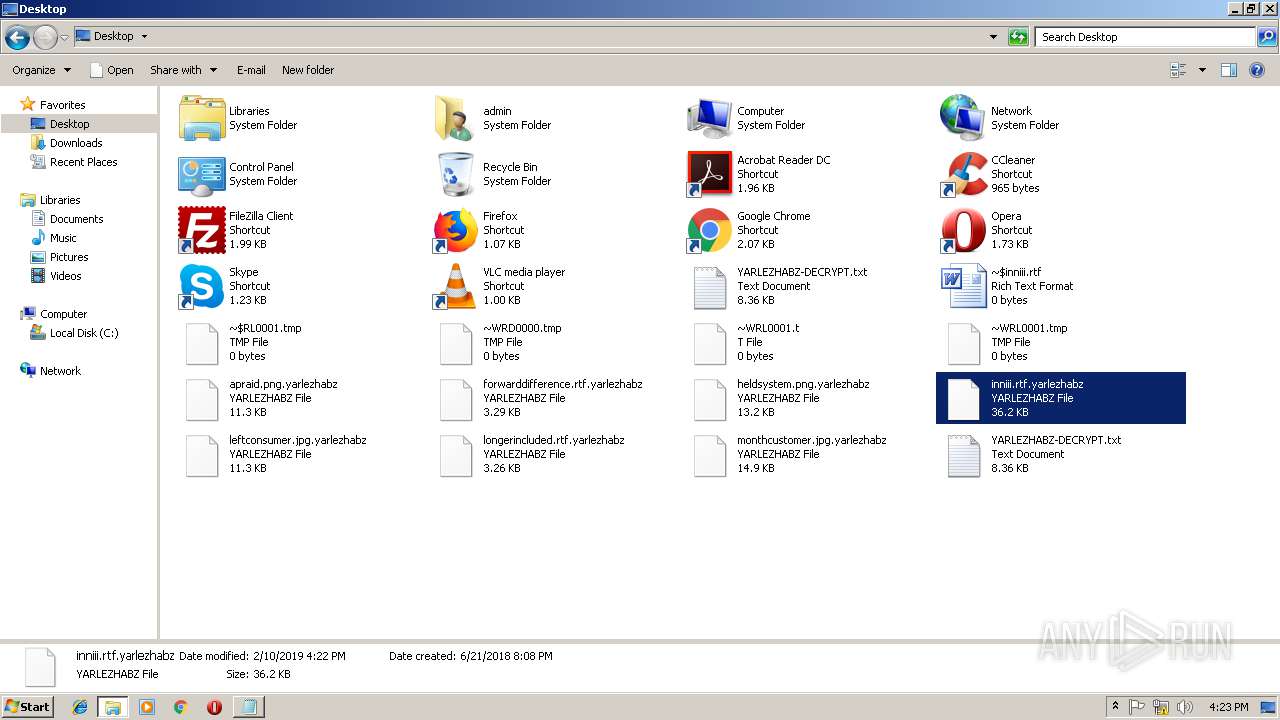
| File name: | 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111 |
| Full analysis: | https://app.any.run/tasks/3ed67abd-4cc2-4324-bfda-1ae691583600 |
| Verdict: | Malicious activity |
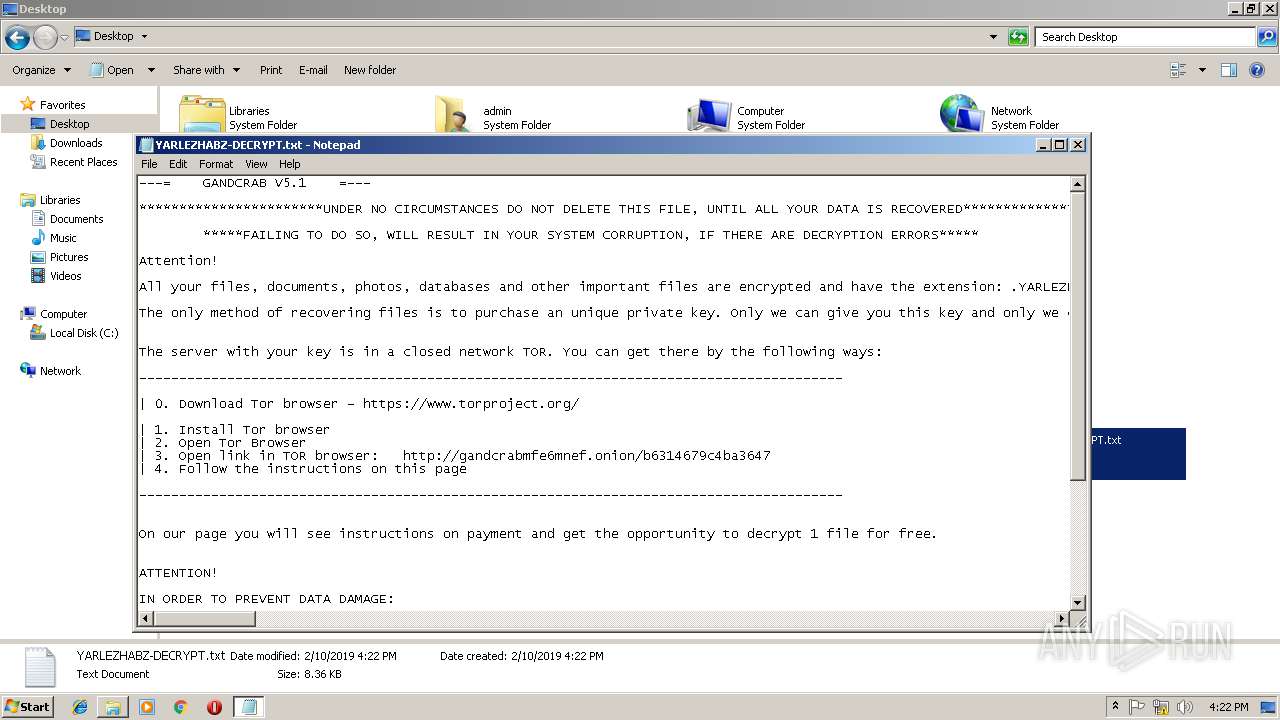
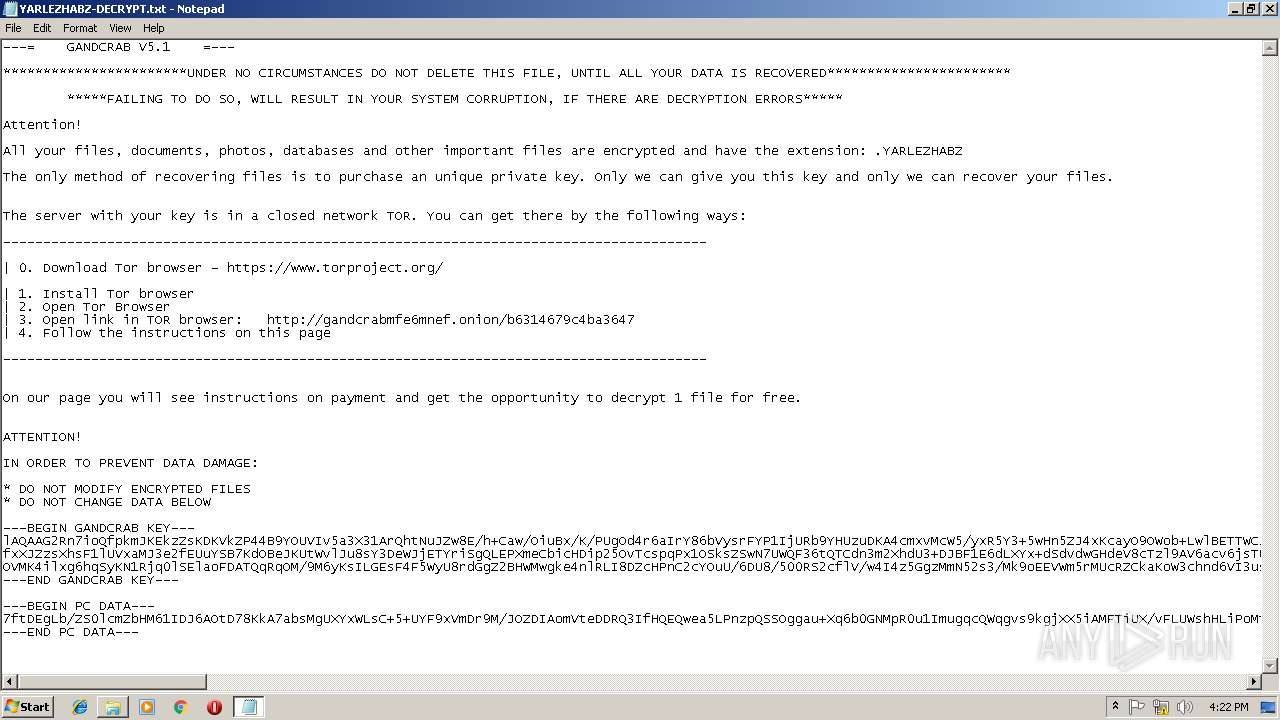
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | February 10, 2019, 16:20:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C8B8A95BB271B661CA6A5BBDA914B33A |
| SHA1: | D2432C48A146F7AC7AFAAEBF58CD2050F8B5672A |
| SHA256: | 454C7C90C090FF8A0C47C6059047FC0643D0AAC055EF9EC460AA15565A8E1111 |
| SSDEEP: | 12288:hdpI8dpIq7e7OWx35OYTKWbfzjUFkMouhJpKilTI9T817WgEDWjwxrZeC5r/jTIX:hd28d2B7kYTM0jFrs4/YJOlHH3qSr27X |
MALICIOUS
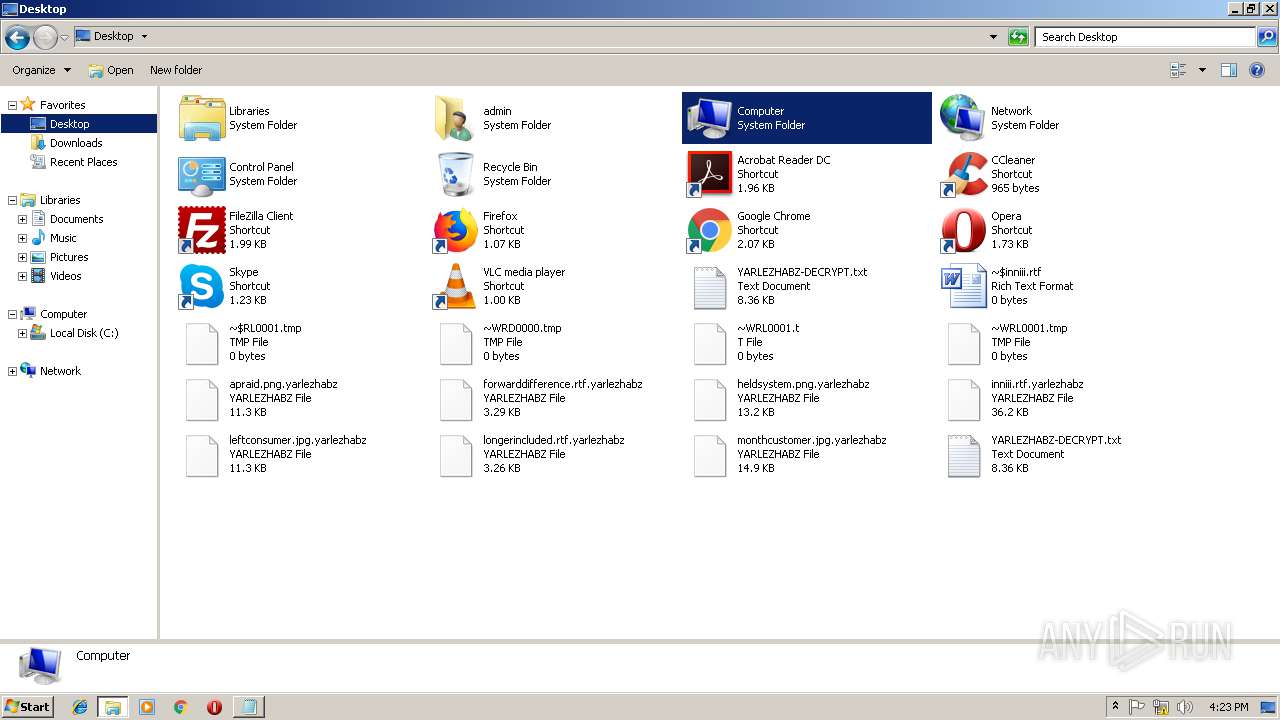
GandCrab keys found
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Writes file to Word startup folder
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
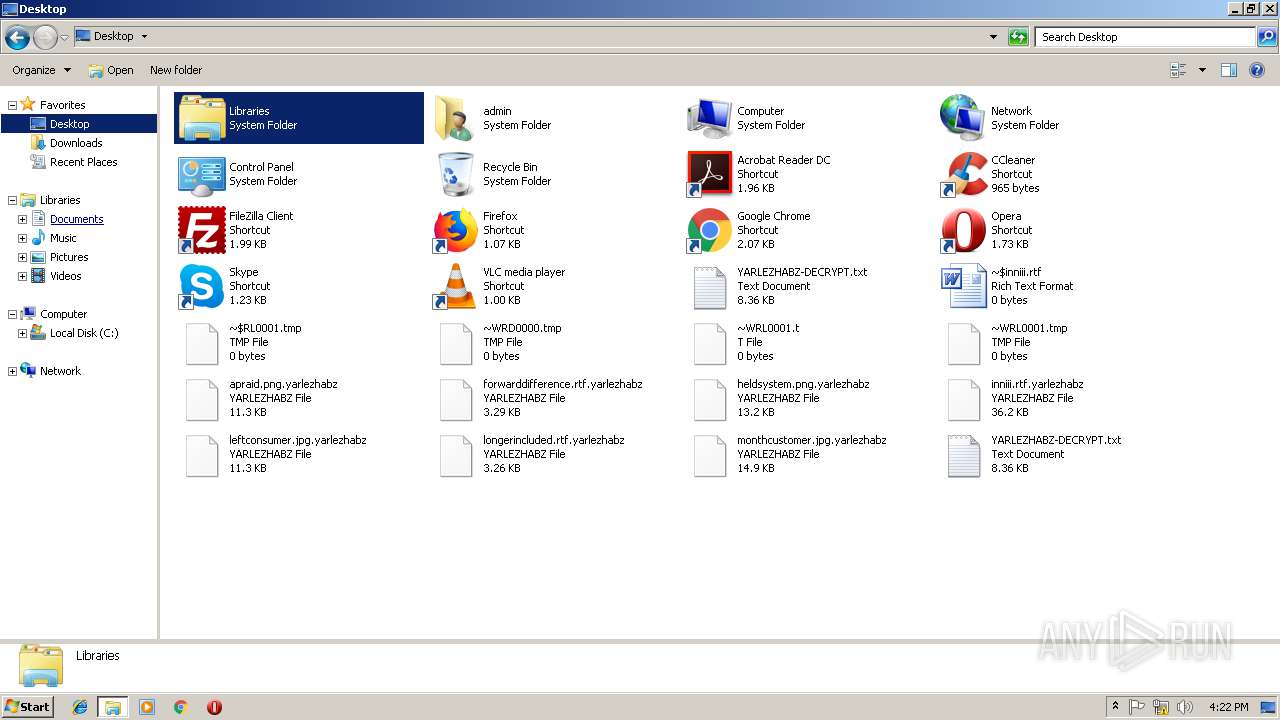
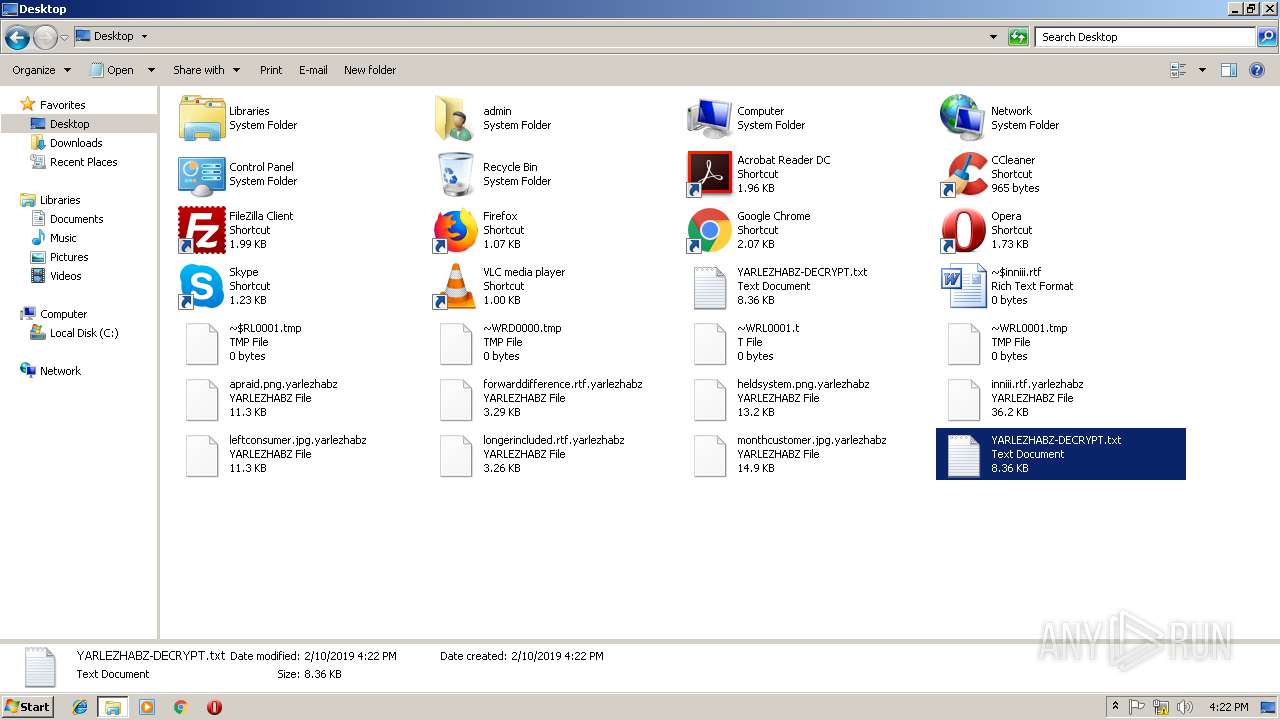
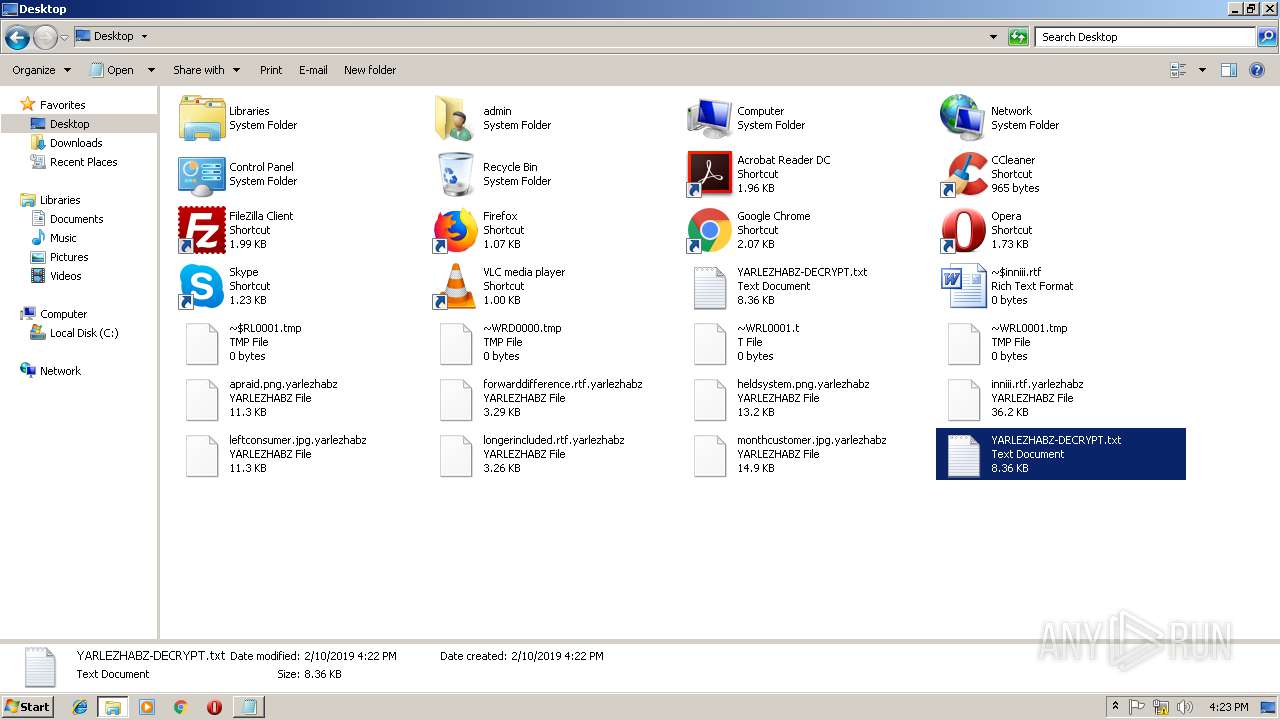
Renames files like Ransomware
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Deletes shadow copies
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Changes settings of System certificates
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Actions looks like stealing of personal data
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Dropped file may contain instructions of ransomware
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Connects to CnC server
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Changes the autorun value in the registry
- reg.exe (PID: 1516)
SUSPICIOUS
Changes tracing settings of the file or console
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3412)
Creates files in the user directory
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3412)
- Skype.exe (PID: 3712)
- Skype.exe (PID: 3324)
- Skype.exe (PID: 2884)
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Creates files in the program directory
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Reads the cookies of Mozilla Firefox
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Application launched itself
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 2956)
- Skype.exe (PID: 3712)
- Skype.exe (PID: 2884)
Adds / modifies Windows certificates
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Creates files like Ransomware instruction
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Reads internet explorer settings
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3700)
Reads Internet Cache Settings
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Uses REG.EXE to modify Windows registry
- Skype.exe (PID: 3712)
Modifies the open verb of a shell class
- Skype.exe (PID: 3712)
Reads CPU info
- Skype.exe (PID: 3712)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2508)
Creates files in the user directory
- WINWORD.EXE (PID: 2508)
Reads settings of System Certificates
- Skype.exe (PID: 3712)
Dropped object may contain TOR URL's
- 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe (PID: 3512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:08:28 21:03:59+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 667648 |
| InitializedDataSize: | 49152 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1100 |
| OSVersion: | 4 |
| ImageVersion: | 1.5 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.5.0.1 |
| ProductVersionNumber: | 1.5.0.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | cites7 |
| ProductName: | Agriculturally |
| FileVersion: | 1.05.0001 |
| ProductVersion: | 1.05.0001 |
| InternalName: | DIABOLICAL |
| OriginalFileName: | DIABOLICAL.exe |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 28-Aug-2012 19:03:59 |
| Detected languages: |
|
| FileDescription: | cites7 |
| ProductName: | Agriculturally |
| FileVersion: | 1.05.0001 |
| ProductVersion: | 1.05.0001 |
| InternalName: | DIABOLICAL |
| OriginalFilename: | DIABOLICAL.exe |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000B0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 28-Aug-2012 19:03:59 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000A22E0 | 0x000A3000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.01513 |
.data | 0x000A4000 | 0x00000D58 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x000A5000 | 0x0000A542 | 0x0000B000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.17273 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.27928 | 576 | Unicode (UTF 16LE) | English - United States | RT_VERSION |
30001 | 5.38779 | 5672 | Unicode (UTF 16LE) | UNKNOWN | RT_ICON |
30002 | 5.43834 | 3752 | Unicode (UTF 16LE) | UNKNOWN | RT_ICON |
30003 | 5.83458 | 2216 | Unicode (UTF 16LE) | UNKNOWN | RT_ICON |
30004 | 5.88217 | 1736 | Unicode (UTF 16LE) | UNKNOWN | RT_ICON |
30005 | 5.82384 | 1384 | Unicode (UTF 16LE) | UNKNOWN | RT_ICON |
30006 | 5.27757 | 12840 | Unicode (UTF 16LE) | UNKNOWN | RT_ICON |
30007 | 5.22317 | 7336 | Unicode (UTF 16LE) | UNKNOWN | RT_ICON |
30008 | 5.30698 | 3240 | Unicode (UTF 16LE) | UNKNOWN | RT_ICON |
30009 | 5.18375 | 1864 | Unicode (UTF 16LE) | UNKNOWN | RT_ICON |
Imports
MSVBVM60.DLL |
Total processes
58
Monitored processes
18
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1516 | C:\Windows\system32\reg.exe ADD HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v "Skype for Desktop" /t REG_SZ /d "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" /f | C:\Windows\system32\reg.exe | Skype.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2508 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\inniii.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2672 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | Skype.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 2756 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | Skype.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 2 Version: 8.29.0.50 Modules
| |||||||||||||||
| 2772 | C:\Windows\system32\reg.exe QUERY HKCU\Software\Microsoft\Skype /v RestartForUpdate | C:\Windows\system32\reg.exe | — | Skype.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2808 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2884 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --ms-disable-indexeddb-transaction-timeout --no-sandbox --service-pipe-token=37E0F359D99B332B83BE5DEF42999AB5 --lang=en-US --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar" --node-integration=false --webview-tag=true --no-sandbox --preload="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar\Preload.js" --context-id=2 --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=37E0F359D99B332B83BE5DEF42999AB5 --renderer-client-id=3 --mojo-platform-channel-handle=1540 /prefetch:1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 2896 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --ms-disable-indexeddb-transaction-timeout --no-sandbox --disable-databases --service-pipe-token=533EE68F0B38868AB5A214C4F5766962 --lang=en-US --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar" --node-integration=false --webview-tag=true --no-sandbox --preload="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar\WebViewPreload.js" --guest-instance-id=1 --enable-blink-features --disable-blink-features --context-id=2 --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=533EE68F0B38868AB5A214C4F5766962 --renderer-client-id=7 --mojo-platform-channel-handle=1840 /prefetch:1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 2956 | "C:\Users\admin\AppData\Local\Temp\454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe" | C:\Users\admin\AppData\Local\Temp\454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: cites7 Exit code: 0 Version: 1.05.0001 Modules
| |||||||||||||||
| 2964 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\YARLEZHABZ-DECRYPT.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 538
Read events
1 110
Write events
410
Delete events
18
Modification events
| (PID) Process: | (2508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 4*# |
Value: 342A2300CC090000010000000000000000000000 | |||
| (PID) Process: | (2508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2508) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1313472543 | |||
| (PID) Process: | (2508) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1313472656 | |||
| (PID) Process: | (2508) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1313472657 | |||
| (PID) Process: | (2508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: CC09000016A76B975CC1D40100000000 | |||
| (PID) Process: | (2508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 7,# |
Value: 372C2300CC09000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | 7,# |
Value: 372C2300CC09000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2508) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
428
Text files
353
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRB694.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2508 | WINWORD.EXE | C:\Users\admin\Desktop\~WRD0000.tmp | — | |
MD5:— | SHA256:— | |||
| 2508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{C02B49F4-C1FC-458D-8779-26501D8B742B}.tmp | — | |
MD5:— | SHA256:— | |||
| 2508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{0F986474-F707-4641-BAC7-5A647F1CF1F4}.tmp | — | |
MD5:— | SHA256:— | |||
| 2508 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{88DD8F0D-64A6-4C71-A14E-E27D8B055600}.tmp | — | |
MD5:— | SHA256:— | |||
| 2508 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3512 | 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\boot.sdi | — | |
MD5:— | SHA256:— | |||
| 3512 | 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe | C:\Config.Msi\YARLEZHABZ-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 3512 | 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\Winre.wim | — | |
MD5:— | SHA256:— | |||
| 3512 | 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\Winre.wim.yarlezhabz | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
17
DNS requests
15
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3512 | 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe | GET | 301 | 185.52.2.154:80 | http://www.kakaocorp.link/ | NL | html | 162 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3512 | 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe | 185.52.2.154:80 | www.kakaocorp.link | RouteLabel V.O.F. | NL | suspicious |
3512 | 454c7c90c090ff8a0c47c6059047fc0643d0aac055ef9ec460aa15565a8e1111.exe | 185.52.2.154:443 | www.kakaocorp.link | RouteLabel V.O.F. | NL | suspicious |
3712 | Skype.exe | 13.90.95.57:443 | get.skype.com | Microsoft Corporation | US | whitelisted |
3712 | Skype.exe | 23.101.158.111:443 | a.config.skype.com | Microsoft Corporation | US | whitelisted |
3712 | Skype.exe | 2.18.233.81:443 | download.skype.com | Akamai International B.V. | — | whitelisted |
3712 | Skype.exe | 13.107.3.128:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
3712 | Skype.exe | 172.217.21.206:443 | redirector.gvt1.com | Google Inc. | US | whitelisted |
3712 | Skype.exe | 52.114.132.23:443 | pipe.skype.com | Microsoft Corporation | US | whitelisted |
3712 | Skype.exe | 173.194.150.168:443 | r2---sn-5goeen76.gvt1.com | Google Inc. | US | whitelisted |
3712 | Skype.exe | 157.55.135.134:443 | login.live.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
shell.view |
| unknown |
askjhdaskdhshtd.ru |
| malicious |
qwerty12346.ru |
| malicious |
www.kakaocorp.link |
| malicious |
get.skype.com |
| whitelisted |
a.config.skype.com |
| whitelisted |
pipe.skype.com |
| whitelisted |
download.skype.com |
| whitelisted |
config.edge.skype.com |
| malicious |
redirector.gvt1.com |
| whitelisted |
Threats
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
Skype.exe | [2672:2872:0210/162400.271:VERBOSE1:crash_service_main.cc(78)] Session start. cmdline is [--reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1]
|
Skype.exe | [2672:2872:0210/162400.286:VERBOSE1:crash_service.cc(145)] window handle is 00050130
|
Skype.exe | [2672:2872:0210/162400.286:VERBOSE1:crash_service.cc(300)] pipe name is \\.\pipe\skype-preview Crash Service
dumps at C:\Users\admin\AppData\Local\Temp\skype-preview Crashes
|
Skype.exe | [2672:2872:0210/162400.286:VERBOSE1:crash_service.cc(304)] checkpoint is C:\Users\admin\AppData\Local\Temp\skype-preview Crashes\crash_checkpoint.txt
server is https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload
maximum 128 reports/day
reporter is electron-crash-service
|
Skype.exe | [2672:2872:0210/162400.286:VERBOSE1:crash_service_main.cc(94)] Ready to process crash requests
|
Skype.exe | [2672:864:0210/162400.286:VERBOSE1:crash_service.cc(333)] client start. pid = 3712
|
Skype.exe | [2672:864:0210/162402.451:VERBOSE1:crash_service.cc(333)] client start. pid = 2884
|
Skype.exe | [2756:1268:0210/162402.904:VERBOSE1:crash_service_main.cc(78)] Session start. cmdline is [--reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1]
|
Skype.exe | [2756:1268:0210/162402.904:VERBOSE1:crash_service.cc(145)] window handle is 00040150
|
Skype.exe | [2756:1268:0210/162402.920:VERBOSE1:crash_service.cc(300)] pipe name is \\.\pipe\skype-preview Crash Service
dumps at C:\Users\admin\AppData\Local\Temp\skype-preview Crashes
|