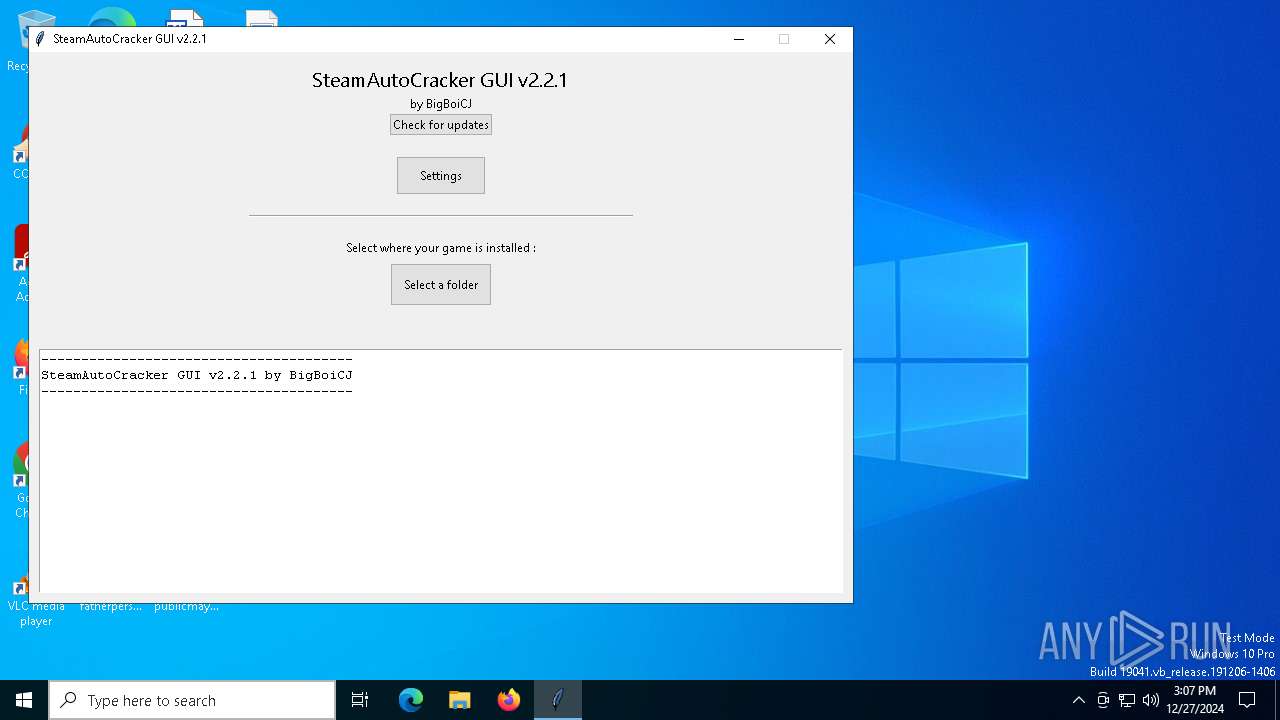
| File name: | steam_auto_cracker_gui.exe |
| Full analysis: | https://app.any.run/tasks/3d844002-6842-4460-9c9e-6080e4ceeb28 |
| Verdict: | Malicious activity |
| Analysis date: | December 27, 2024, 15:06:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 9B13D23586BC94A9A03A74C703544D2F |
| SHA1: | 404294664583896FC4E2FA82EFCF30CEA4D24A26 |
| SHA256: | 4544DD9CCCE49465D264ED6725036551C32975AB96014322F65499B79497F56A |
| SSDEEP: | 98304:FbX+u8MRtSpupLGPW37nSJq+xI/iuqrW7VTfxTlRplE9bbL/lHe6BISGlbI9SseR:5kYbreI4y |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- steam_auto_cracker_gui.exe (PID: 6396)
Executable content was dropped or overwritten
- steam_auto_cracker_gui.exe (PID: 6396)
Process drops python dynamic module
- steam_auto_cracker_gui.exe (PID: 6396)
Application launched itself
- steam_auto_cracker_gui.exe (PID: 6396)
Process drops legitimate windows executable
- steam_auto_cracker_gui.exe (PID: 6396)
Loads Python modules
- steam_auto_cracker_gui.exe (PID: 5464)
Starts CMD.EXE for commands execution
- steam_auto_cracker_gui.exe (PID: 5464)
INFO
Checks supported languages
- steam_auto_cracker_gui.exe (PID: 6396)
- steam_auto_cracker_gui.exe (PID: 5464)
Reads the computer name
- steam_auto_cracker_gui.exe (PID: 6396)
- steam_auto_cracker_gui.exe (PID: 5464)
Create files in a temporary directory
- steam_auto_cracker_gui.exe (PID: 6396)
PyInstaller has been detected (YARA)
- steam_auto_cracker_gui.exe (PID: 6396)
Reads the machine GUID from the registry
- steam_auto_cracker_gui.exe (PID: 5464)
Checks operating system version
- steam_auto_cracker_gui.exe (PID: 5464)
The sample compiled with english language support
- steam_auto_cracker_gui.exe (PID: 6396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:08:14 02:04:40+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.34 |
| CodeSize: | 165888 |
| InitializedDataSize: | 108544 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb310 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
125
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5464 | "C:\Users\admin\AppData\Local\Temp\steam_auto_cracker_gui.exe" | C:\Users\admin\AppData\Local\Temp\steam_auto_cracker_gui.exe | steam_auto_cracker_gui.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6228 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | steam_auto_cracker_gui.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6396 | "C:\Users\admin\AppData\Local\Temp\steam_auto_cracker_gui.exe" | C:\Users\admin\AppData\Local\Temp\steam_auto_cracker_gui.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
350
Read events
350
Write events
0
Delete events
0
Modification events
Executable files
61
Suspicious files
7
Text files
939
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6396 | steam_auto_cracker_gui.exe | C:\Users\admin\AppData\Local\Temp\_MEI63962\_hashlib.pyd | executable | |
MD5:69DC506CF2FA3DA9D0CABA05FCA6A35D | SHA256:C5B8C4582E201FEF2D8CB2C8672D07B86DEC31AFB4A17B758DBFB2CFF163B12F | |||
| 6396 | steam_auto_cracker_gui.exe | C:\Users\admin\AppData\Local\Temp\_MEI63962\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:BFB4E16944C3087713F7E42A415466B6 | SHA256:22845B42EC648D5F731B63734DF667A5BCB26F6EC065BFF6E13AB9B50A6777E7 | |||
| 6396 | steam_auto_cracker_gui.exe | C:\Users\admin\AppData\Local\Temp\_MEI63962\api-ms-win-core-heap-l1-1-0.dll | executable | |
MD5:1FAA2C61AB2380330C10248ED5122201 | SHA256:D4D74BA861D002EF6CA0412889A8F122CBE0E7FBF1F2EB1CF0024950CC8EE6A0 | |||
| 6396 | steam_auto_cracker_gui.exe | C:\Users\admin\AppData\Local\Temp\_MEI63962\VCRUNTIME140.dll | executable | |
MD5:F34EB034AA4A9735218686590CBA2E8B | SHA256:9D2B40F0395CC5D1B4D5EA17B84970C29971D448C37104676DB577586D4AD1B1 | |||
| 6396 | steam_auto_cracker_gui.exe | C:\Users\admin\AppData\Local\Temp\_MEI63962\_decimal.pyd | executable | |
MD5:FF0BF710EB2D7817C49E1F4E21502073 | SHA256:C6EB532DA62A115AE75F58766B632E005140A2E7C9C67A77564F1804685A377F | |||
| 6396 | steam_auto_cracker_gui.exe | C:\Users\admin\AppData\Local\Temp\_MEI63962\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:C20681E787260D065378768E80145A1A | SHA256:2B1F76820C279C4A7156E8F0011D75F5A6EE98524E0BBFA8F661A09FA1BBD076 | |||
| 6396 | steam_auto_cracker_gui.exe | C:\Users\admin\AppData\Local\Temp\_MEI63962\_tkinter.pyd | executable | |
MD5:77CF63868CAE43963B69B4561114CD19 | SHA256:313FB33E72028FCC893EC7874E0C825C035CDCEBE1B5B7C7D8D11EF3AD1B354F | |||
| 6396 | steam_auto_cracker_gui.exe | C:\Users\admin\AppData\Local\Temp\_MEI63962\api-ms-win-core-file-l1-1-0.dll | executable | |
MD5:402E72079A0FEE81E19730688147B32C | SHA256:A64A28D87AC02593148B5576B6BE383362B44AF84F8FA81FC646B8A804B6048A | |||
| 6396 | steam_auto_cracker_gui.exe | C:\Users\admin\AppData\Local\Temp\_MEI63962\api-ms-win-core-libraryloader-l1-1-0.dll | executable | |
MD5:E950AD90923A1AA956B03F2D4925DCC5 | SHA256:8F1BE271554EF75F742D08FA048B4EEB70E0A68FEB8DC15964DE24E5DB43D63D | |||
| 6396 | steam_auto_cracker_gui.exe | C:\Users\admin\AppData\Local\Temp\_MEI63962\_socket.pyd | executable | |
MD5:CD56F508E7C305D4BFDEB820ECF3A323 | SHA256:9E97B782B55400E5A914171817714BBBC713C0A396E30496C645FC82835E4B34 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
31
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7044 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7044 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.155:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6456 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.155:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.170:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |