| File name: | OIETIF.bat |
| Full analysis: | https://app.any.run/tasks/78efc78d-0676-4be2-9711-bc14f23f29cd |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2024, 01:15:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | C2852FB55116AC0B829DF7E9C0E3E04B |
| SHA1: | 220F2CD55B8A30A8ED1471BAEA68EADC146C2CC3 |
| SHA256: | 4540A0AF78874DACE7BF6D3C69E6E6E033D3CD65BE718BC1516A687916433662 |
| SSDEEP: | 96:jrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhi:jrhrhrhrhrhrhrhrhrhrhrhrhrhrhrhC |
MALICIOUS
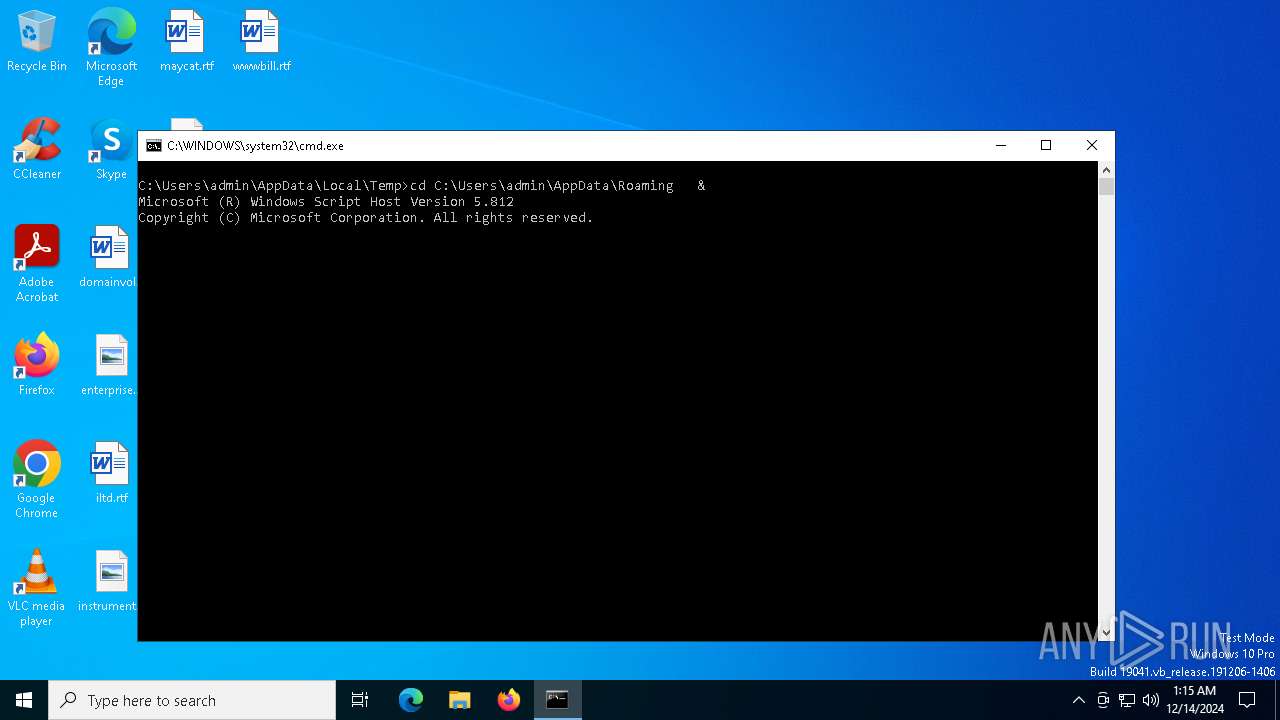
Gets a file object corresponding to the file in a specified path (SCRIPT)
- cscript.exe (PID: 3208)
Uses base64 encoding (SCRIPT)
- cscript.exe (PID: 3208)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 3208)
The process executes JS scripts
- cmd.exe (PID: 3744)
Creates a Folder object (SCRIPT)
- cscript.exe (PID: 3208)
Executable content was dropped or overwritten
- cscript.exe (PID: 3208)
Saves data to a binary file (SCRIPT)
- cscript.exe (PID: 3208)
The executable file from the user directory is run by the CMD process
- s.exe (PID: 3808)
- s.exe (PID: 5300)
- s.exe (PID: 1904)
Script creates XML DOM node (SCRIPT)
- cscript.exe (PID: 3208)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 3208)
Creates XML DOM element (SCRIPT)
- cscript.exe (PID: 3208)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 3208)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 3208)
INFO
Reads security settings of Internet Explorer
- cscript.exe (PID: 3208)
The process uses the downloaded file
- cscript.exe (PID: 3208)
- cmd.exe (PID: 3744)
Creates files or folders in the user directory
- cscript.exe (PID: 3208)
Checks supported languages
- s.exe (PID: 5300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
123
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
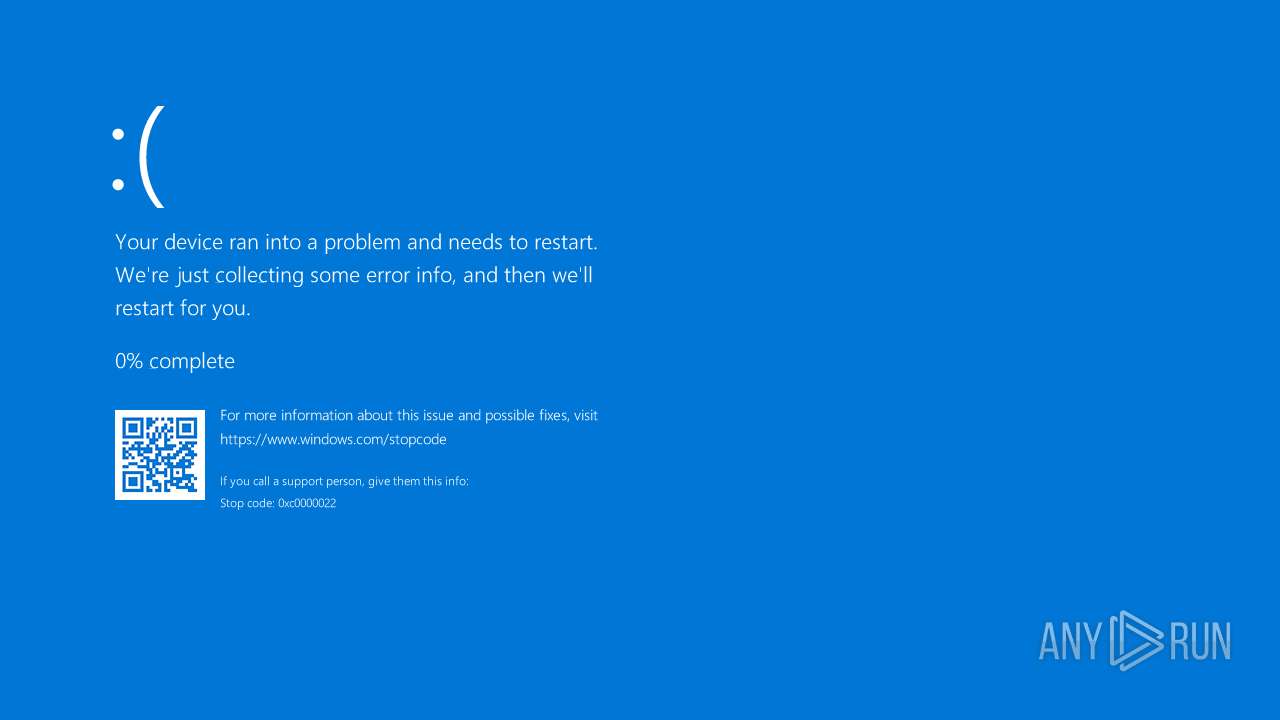
| 1904 | "C:\Users\admin\AppData\Roaming\s.exe" | C:\Users\admin\AppData\Roaming\s.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3208 | cscript x.js | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 3612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3744 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\OIETIF.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3808 | "C:\Users\admin\AppData\Roaming\s.exe" | C:\Users\admin\AppData\Roaming\s.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5300 | "C:\Users\admin\AppData\Roaming\s.exe" | C:\Users\admin\AppData\Roaming\s.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
1 299
Read events
1 297
Write events
2
Delete events
0
Modification events
| (PID) Process: | (3208) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000CF9EDE9DC54DDB01 | |||
| (PID) Process: | (3208) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\cscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 0A5A130000000000 | |||
Executable files
1
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5300 | s.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 3208 | cscript.exe | C:\Users\admin\AppData\Roaming\z.zip | compressed | |
MD5:A30962E7F10FA5A6F791B2D9AB453561 | SHA256:0C0A7F2E8EC916DC1E00110B6028E4EBABDBB3643838A073A8576DAACA475C4C | |||
| 3744 | cmd.exe | C:\Users\admin\AppData\Roaming\x | text | |
MD5:4B1389A9F78BF5D94E7EB81D1506CA47 | SHA256:BFADC1FA9A0D4D0809EA1EEBEE1DDEDC64C2680275D175EC3830176499775199 | |||
| 3744 | cmd.exe | C:\Users\admin\AppData\Roaming\x.js | text | |
MD5:D94C93F882CF030ED9D66CC35796731D | SHA256:F7941E6BE49D757B46B9D6FB5ECB15392EC36A64E8906692D2EEB2BA9FC67CB6 | |||
| 3208 | cscript.exe | C:\Users\admin\AppData\Roaming\s.exe | executable | |
MD5:358666B4D8C4D306651F4B0F8FCE89E5 | SHA256:856CA1A7C06A7E385170B70334113C9729B28E4090A0C961CD2B3F8758B81704 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
12
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2736 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |