| File name: | memesense crack.exe |
| Full analysis: | https://app.any.run/tasks/4bfc350b-15ef-458a-9de8-2da804d74eac |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | July 04, 2024, 21:42:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | FCDF2C48130CEEF992832F123DB2CEF0 |
| SHA1: | 87B0BEBC864EAF5E18E16F356283D3133B13134F |
| SHA256: | 453304567D779391E057A9321D00982E484E31B94751E9C955DAAF15B28586D4 |
| SSDEEP: | 98304:C1lK6psWPMMw+qquKhGm4UJECDzhY89YS8z9ySsXqcK24rEFRNLdImrW26RJdEPR:ws69cS |
MALICIOUS
Drops the executable file immediately after the start
- memesense crack.exe (PID: 3416)
- ms.exe (PID: 3272)
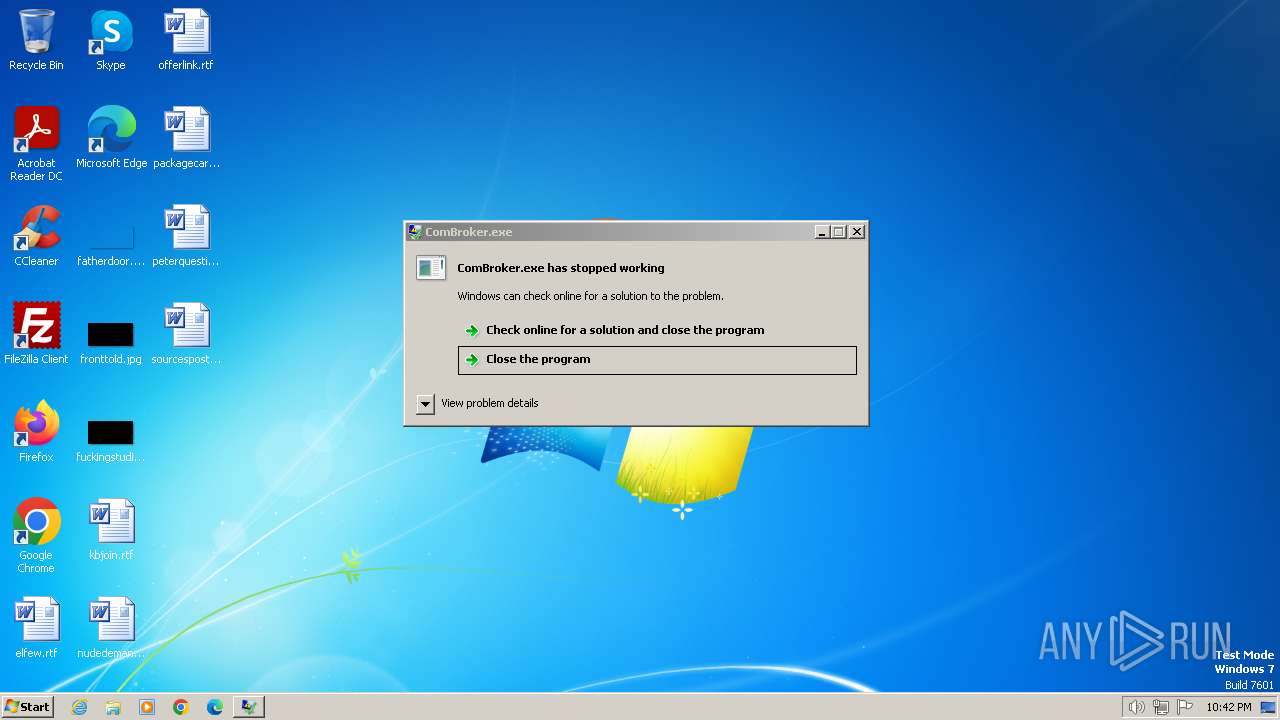
- ComBroker.exe (PID: 2100)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 3200)
DcRAT is detected
- ComBroker.exe (PID: 2100)
DCRAT has been detected (YARA)
- ComBroker.exe (PID: 2100)
SUSPICIOUS
Executable content was dropped or overwritten
- memesense crack.exe (PID: 3416)
- ms.exe (PID: 3272)
- ComBroker.exe (PID: 2100)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3200)
Executing commands from a ".bat" file
- wscript.exe (PID: 3200)
Reads security settings of Internet Explorer
- memesense crack.exe (PID: 3416)
- ms.exe (PID: 3272)
Reads the Internet Settings
- memesense crack.exe (PID: 3416)
- ms.exe (PID: 3272)
- wscript.exe (PID: 3200)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3200)
The executable file from the user directory is run by the CMD process
- ComBroker.exe (PID: 2100)
INFO
Checks supported languages
- memesense crack.exe (PID: 3416)
- Windows Defender.exe (PID: 3520)
- ms.exe (PID: 3272)
- ComBroker.exe (PID: 2100)
Reads the computer name
- memesense crack.exe (PID: 3416)
- Windows Defender.exe (PID: 3520)
- ms.exe (PID: 3272)
- ComBroker.exe (PID: 2100)
Create files in a temporary directory
- memesense crack.exe (PID: 3416)
Creates files or folders in the user directory
- ms.exe (PID: 3272)
Reads the machine GUID from the registry
- Windows Defender.exe (PID: 3520)
- ComBroker.exe (PID: 2100)
Reads Environment values
- ComBroker.exe (PID: 2100)
Reads product name
- ComBroker.exe (PID: 2100)
.NET Reactor protector has been detected
- ComBroker.exe (PID: 2100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ 4.x (75) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (15.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.6) |
| .exe | | | Win32 Executable (generic) (2.5) |
| .exe | | | Win16/32 Executable Delphi generic (1.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:06:15 16:44:28+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5.12 |
| CodeSize: | 3584 |
| InitializedDataSize: | 2638336 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ae1 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
45
Monitored processes
6
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2100 | "C:\Users\admin\AppData\Roaming\PortFontnetCommon/ComBroker.exe" | C:\Users\admin\AppData\Roaming\PortFontnetCommon\ComBroker.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.2.7.1277 Modules
| |||||||||||||||
| 2936 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Roaming\PortFontnetCommon\JQXlzsf9AWIo10t.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3200 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\PortFontnetCommon\ObBFQ9t1t.vbe" | C:\Windows\System32\wscript.exe | — | ms.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3272 | "C:\Users\admin\AppData\Local\Temp\ms.exe" | C:\Users\admin\AppData\Local\Temp\ms.exe | memesense crack.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3416 | "C:\Users\admin\AppData\Local\Temp\memesense crack.exe" | C:\Users\admin\AppData\Local\Temp\memesense crack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3520 | "C:\Users\admin\AppData\Local\Temp\Windows Defender.exe" | C:\Users\admin\AppData\Local\Temp\Windows Defender.exe | — | memesense crack.exe | |||||||||||
User: admin Company: Microsoft Publisher Integrity Level: MEDIUM Description: Malwarebytes Update Exit code: 0 Version: 192.263.263.64 Modules
| |||||||||||||||
Total events
8 304
Read events
8 258
Write events
46
Delete events
0
Modification events
| (PID) Process: | (3416) memesense crack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3416) memesense crack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3416) memesense crack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3416) memesense crack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3272) ms.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3272) ms.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3272) ms.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3272) ms.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3200) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3200) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
4
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3416 | memesense crack.exe | C:\Users\admin\AppData\Local\Temp\ms.exe | executable | |
MD5:5AFEB47C1CE90D5419864CE0CC10AE29 | SHA256:4F7F9490749F0C3BD159CF1C3A6457C18063FA50E2EE642AF3BF8B7CE4F38104 | |||
| 3272 | ms.exe | C:\Users\admin\AppData\Roaming\PortFontnetCommon\JQXlzsf9AWIo10t.bat | text | |
MD5:FC6DADBE24168800EE6B83E4DFDDF548 | SHA256:C331D5D0868B13726E9C97530470F6E04498289B352EAC0F1DA8A8E1C2099758 | |||
| 3272 | ms.exe | C:\Users\admin\AppData\Roaming\PortFontnetCommon\ObBFQ9t1t.vbe | binary | |
MD5:C03CD97778B7902975E167FB98307403 | SHA256:005FAF8A699ED00CB182214981B55A11BCD9E933D516255765688524EDC4C2E3 | |||
| 3272 | ms.exe | C:\Users\admin\AppData\Roaming\PortFontnetCommon\ComBroker.exe | executable | |
MD5:1F35FECBC358AC4D5C2BB4AA5FB962D1 | SHA256:C13292350EB68A3752F0152D4C7C4E13F6FB960485C6D7F8D830BF5EAB7855CB | |||
| 3416 | memesense crack.exe | C:\Users\admin\AppData\Local\Temp\Windows Defender.exe | executable | |
MD5:FA3F84D3150DAB7B7D8E35EFBB8D02DB | SHA256:A42D5A457EE0D90DEE5CB5BA969687A83BA5626ABF040A2F3ED496F83456C162 | |||
| 2100 | ComBroker.exe | C:\Users\admin\Desktop\uLWSYAyS.log | executable | |
MD5:D8BF2A0481C0A17A634D066A711C12E9 | SHA256:2B93377EA087225820A9F8E4F331005A0C600D557242366F06E0C1EAE003D669 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1372 | svchost.exe | 23.50.131.216:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1060 | svchost.exe | 23.50.131.200:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |