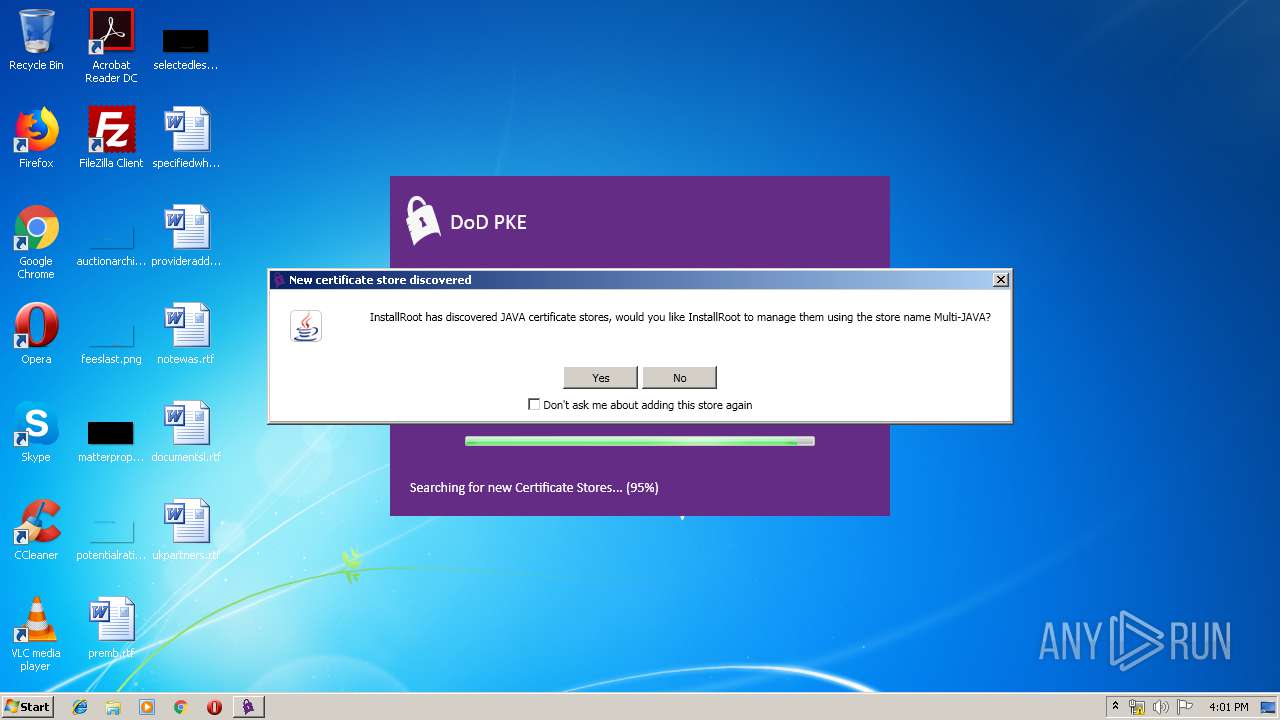
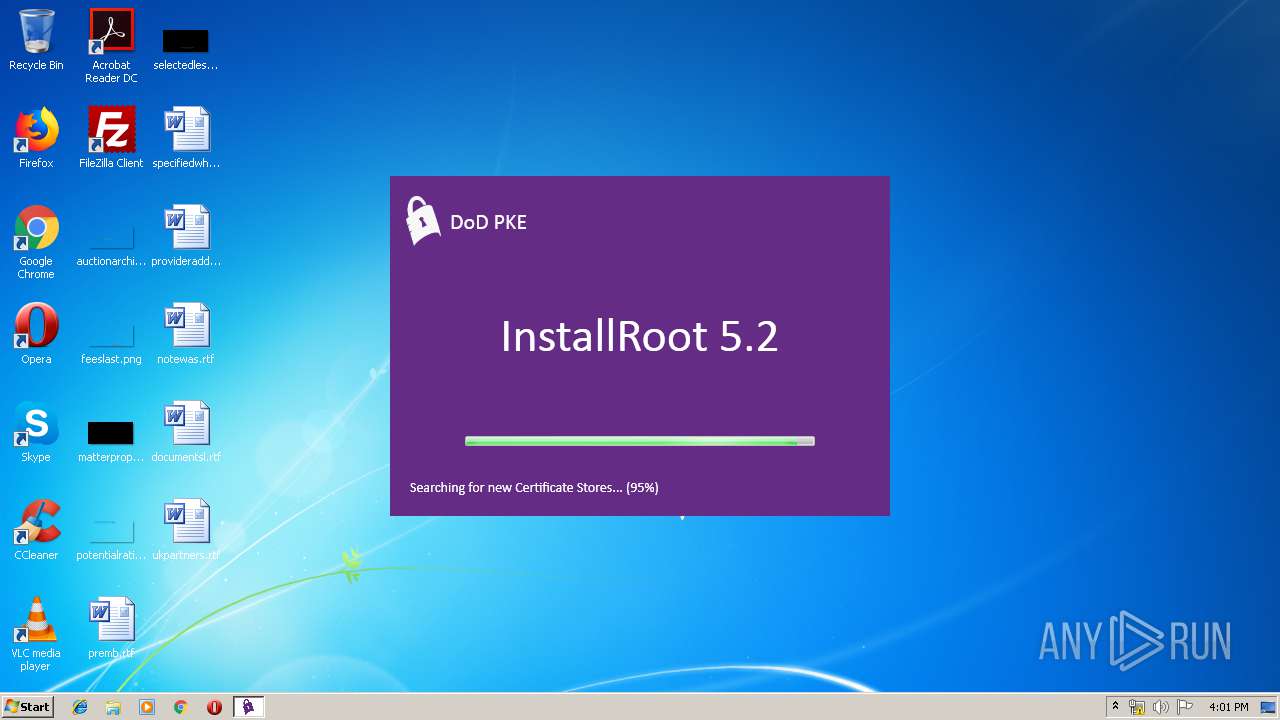
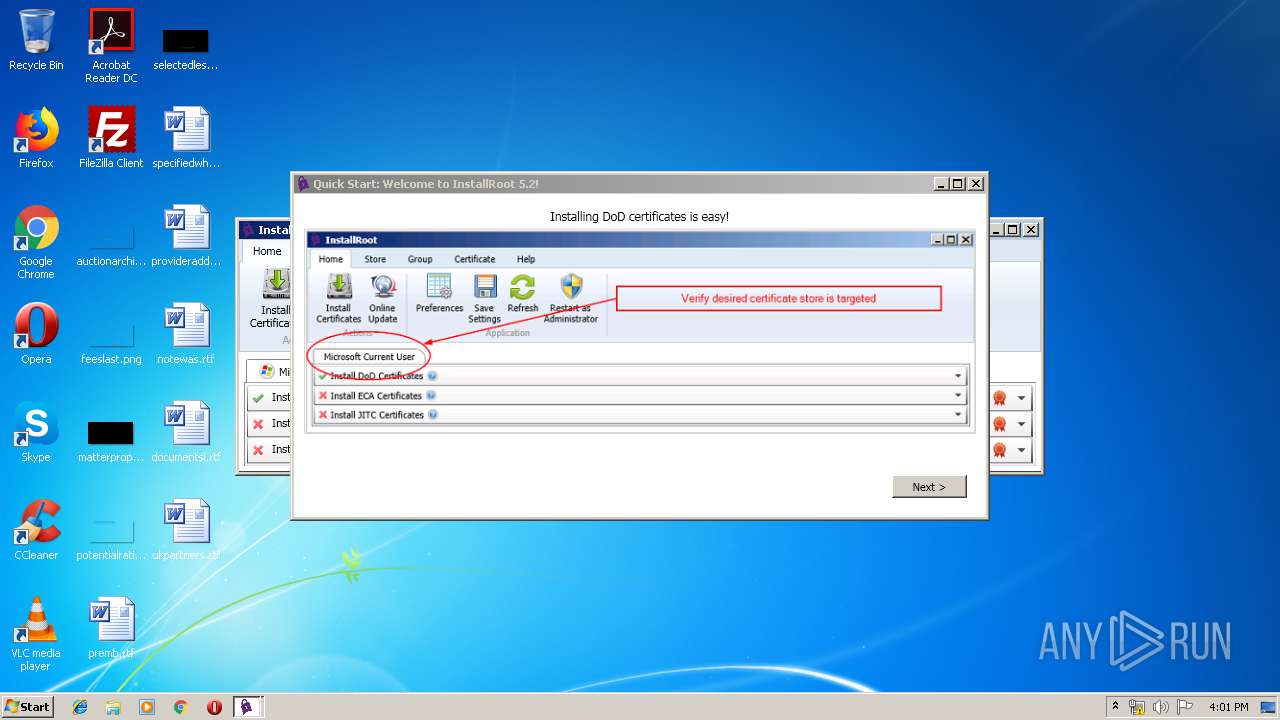
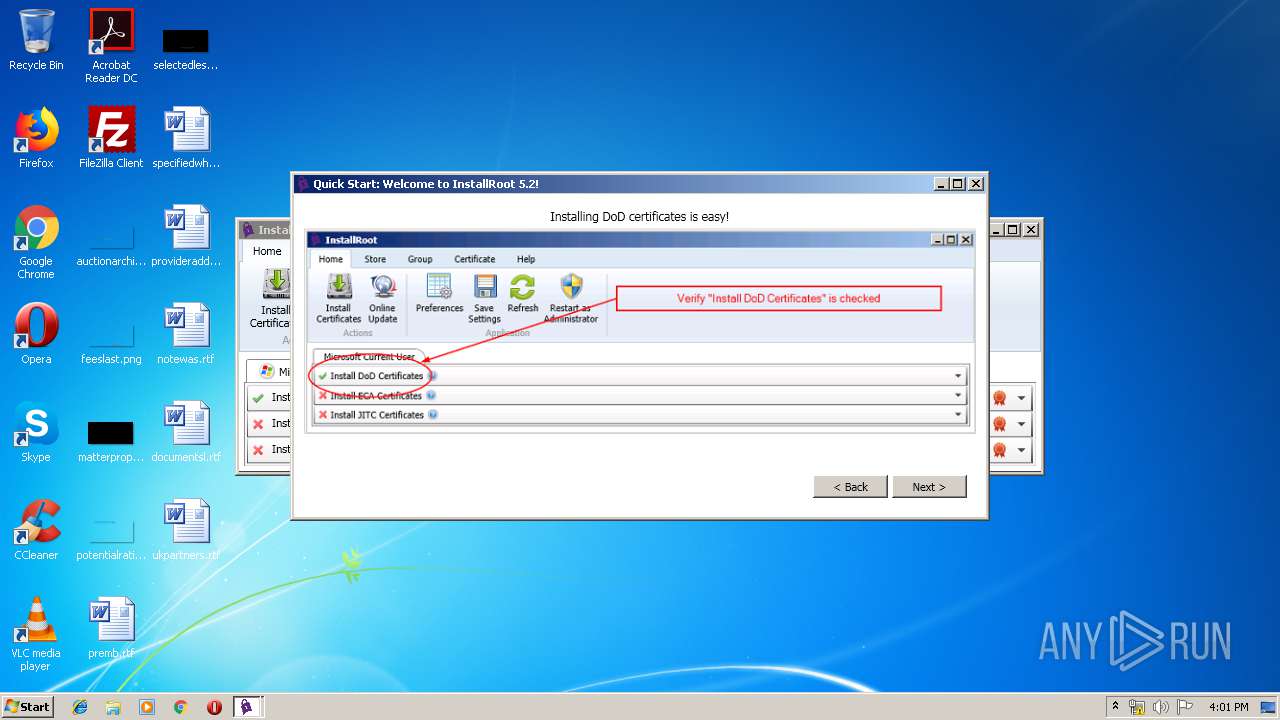
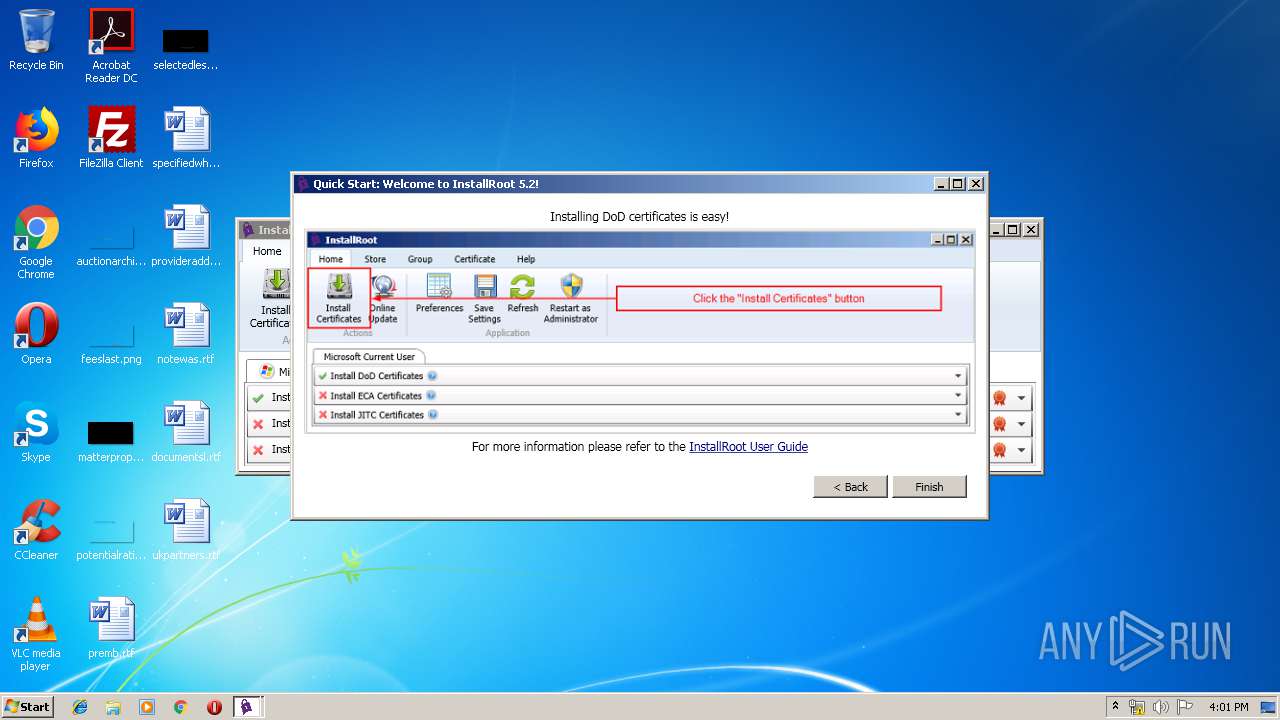
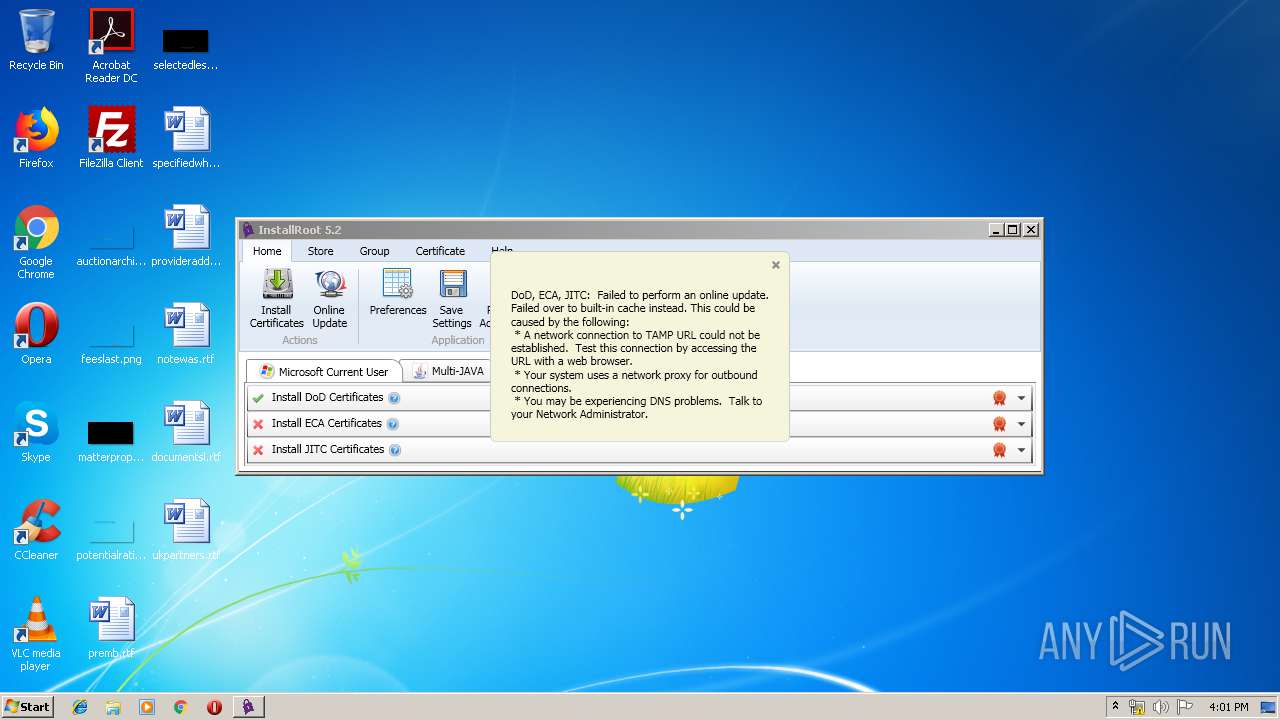
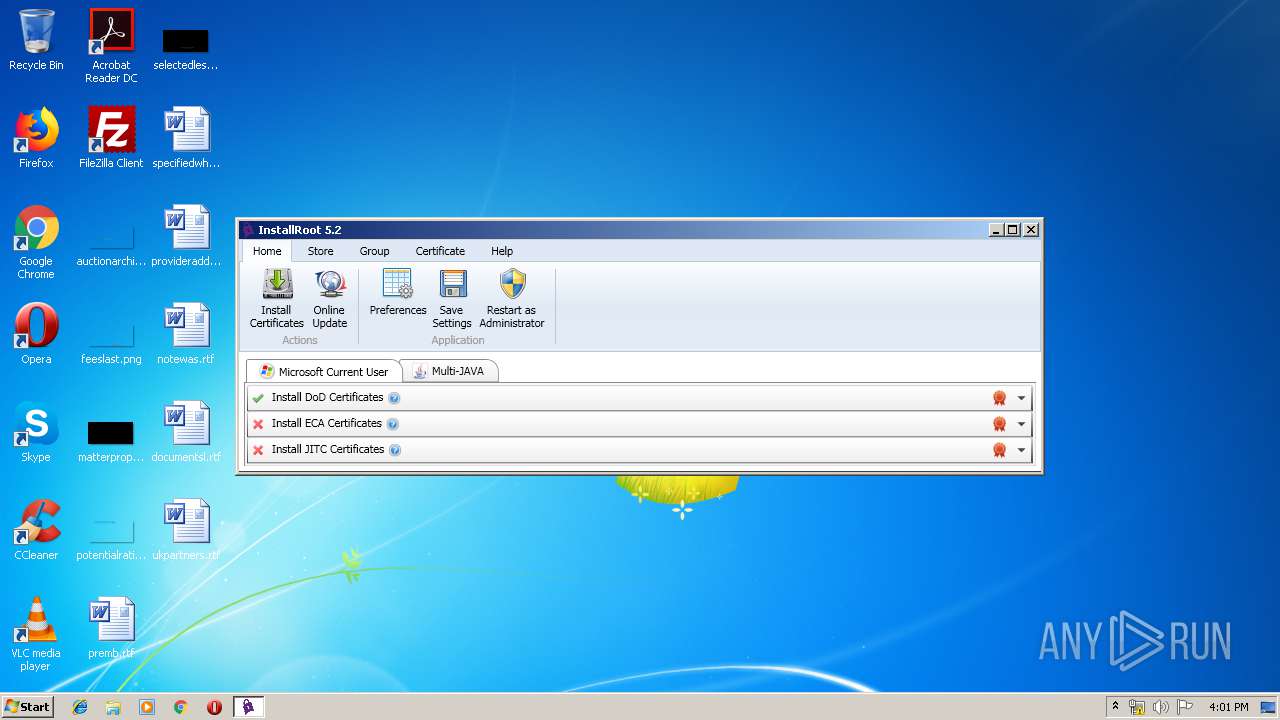
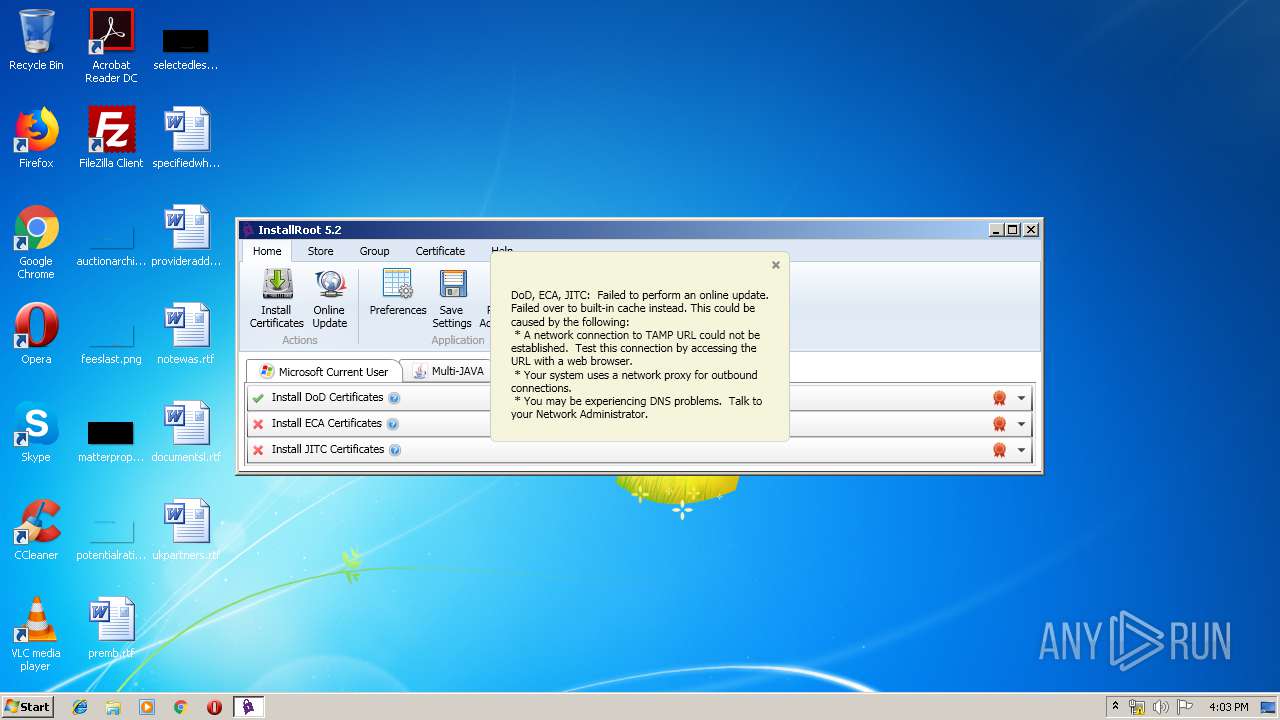
| download: | InstallRoot_5.2x32_NonAdmin.msi |
| Full analysis: | https://app.any.run/tasks/6f3bcf95-fc2f-4adc-bc77-326c833a8119 |
| Verdict: | Malicious activity |
| Analysis date: | October 01, 2019, 14:58:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Title: Installation Database, Keywords: Installer, MSI, Database, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Dec 11 11:47:44 2009, Number of Pages: 200, Security: 0, Code page: 1252, Revision Number: {30FE844D-F920-47C5-8D05-FA70189E2716}, Number of Words: 10, Subject: InstallRoot, Author: DoD PKE, Name of Creating Application: Advanced Installer 13.4 build 74004, Template: ;1033, Comments: This installer database contains the logic and data required to install InstallRoot. |
| MD5: | B23A7EFA563C259FE3A34E8B8DAF6293 |
| SHA1: | CAB005F02F54F5A44932CED3797C93112893BAE1 |
| SHA256: | 45204ED4646BFAB300149C2871B98B0BFF888F6B6C9C4AD774191AD7302838B2 |
| SSDEEP: | 786432:IhDw6IFMo9Wsbgrt/9vaRr0jdBsi5Ie8yt/mF:Ih0Nd8rx9CRr0jDI/yy |
MALICIOUS
Application was dropped or rewritten from another process
- InstallRootUI.exe (PID: 3204)
Loads dropped or rewritten executable
- InstallRootUI.exe (PID: 3204)
Actions looks like stealing of personal data
- InstallRootUI.exe (PID: 3204)
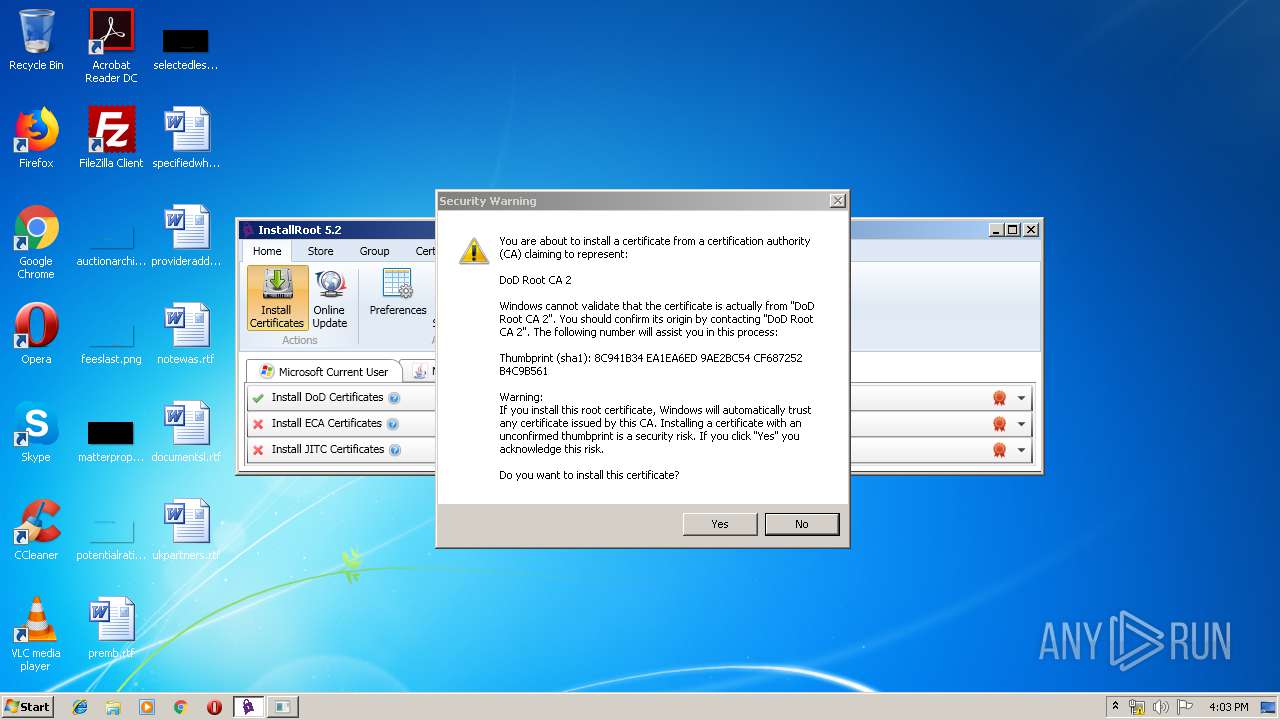
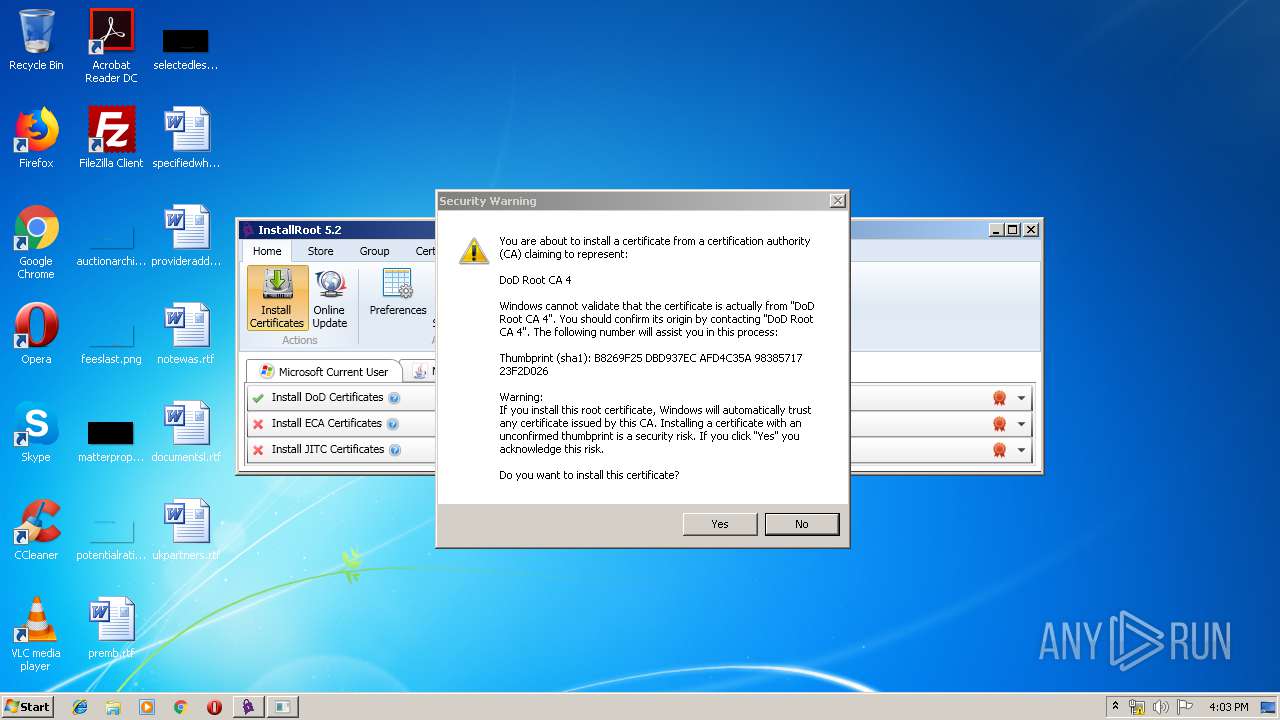
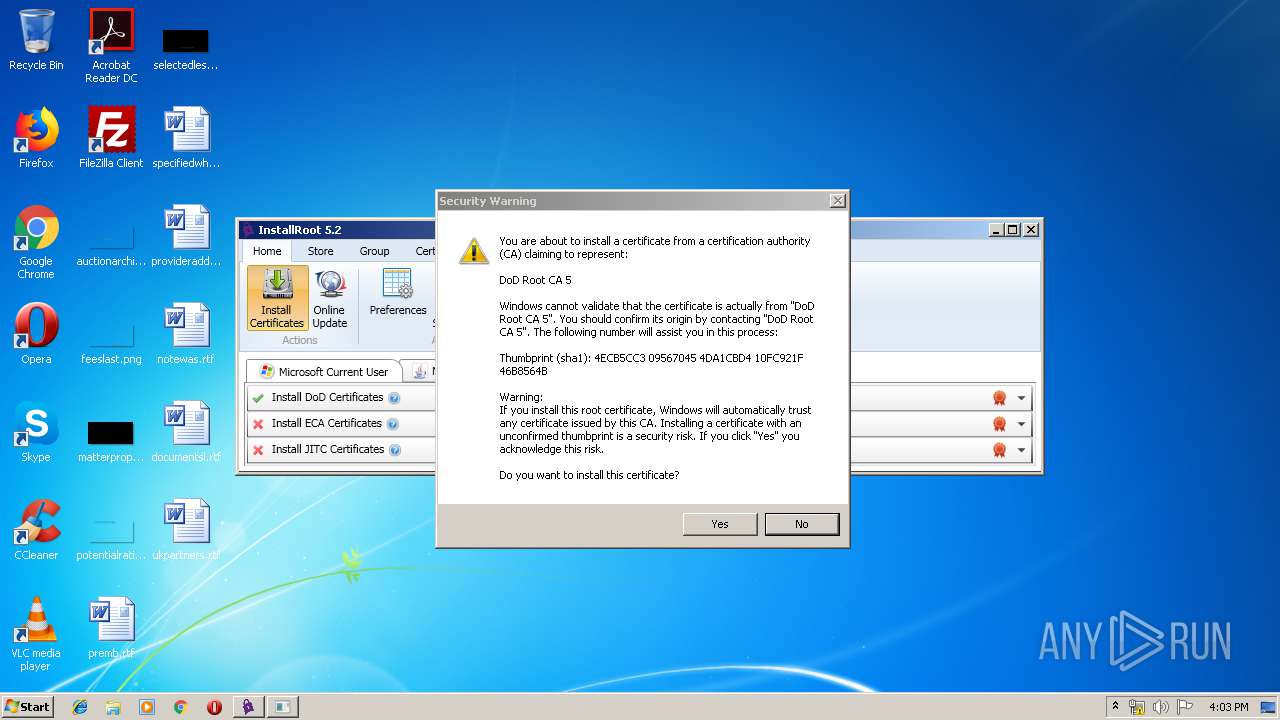
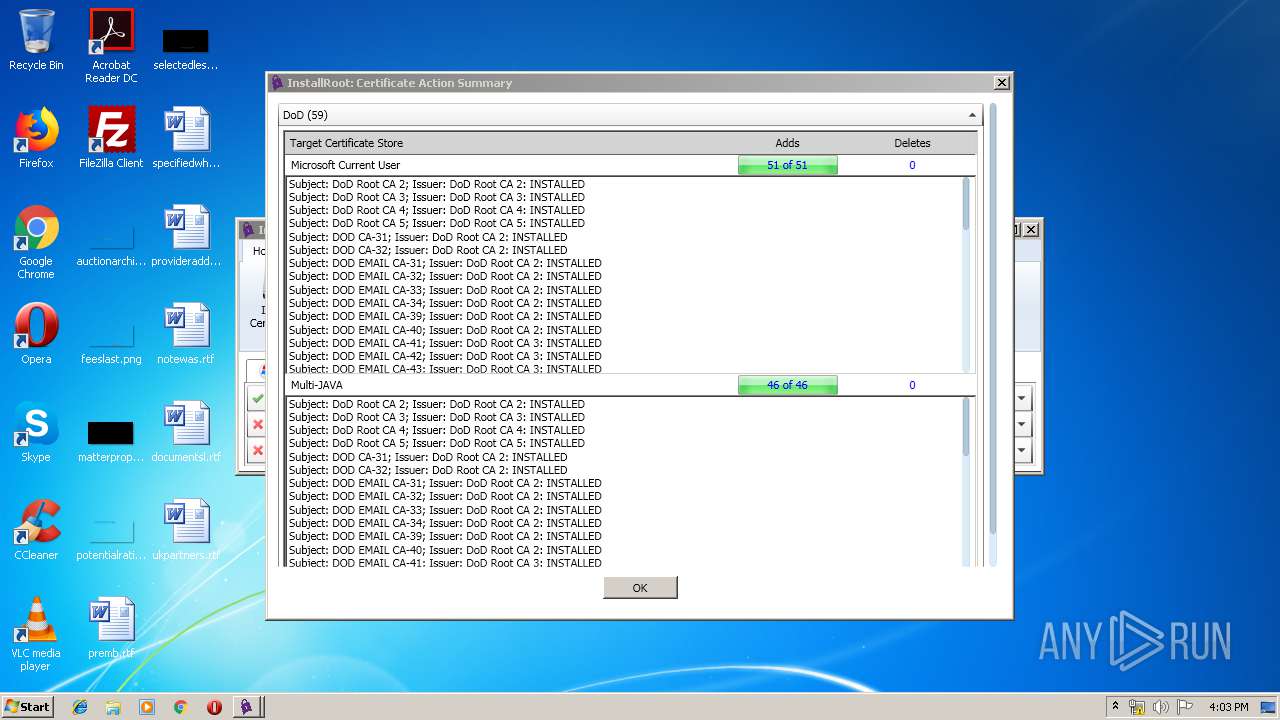
Changes settings of System certificates
- InstallRootUI.exe (PID: 3204)
SUSPICIOUS
Executed via COM
- DrvInst.exe (PID: 1052)
Creates files in the user directory
- msiexec.exe (PID: 2064)
- InstallRootUI.exe (PID: 3204)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2064)
- msiexec.exe (PID: 3532)
Reads Environment values
- InstallRootUI.exe (PID: 3204)
Executed as Windows Service
- vssvc.exe (PID: 3096)
INFO
Low-level read access rights to disk partition
- vssvc.exe (PID: 3096)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3980)
- MsiExec.exe (PID: 3764)
Creates a software uninstall entry
- msiexec.exe (PID: 2064)
Searches for installed software
- msiexec.exe (PID: 2064)
Application launched itself
- msiexec.exe (PID: 2064)
Reads settings of System Certificates
- InstallRootUI.exe (PID: 3204)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Title: | Installation Database |
|---|---|
| Keywords: | Installer, MSI, Database |
| LastPrinted: | 2009:12:11 11:47:44 |
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2009:12:11 11:47:44 |
| Pages: | 200 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {30FE844D-F920-47C5-8D05-FA70189E2716} |
| Words: | 10 |
| Subject: | InstallRoot |
| Author: | DoD PKE |
| LastModifiedBy: | - |
| Software: | Advanced Installer 13.4 build 74004 |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install InstallRoot. |
Total processes
42
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot22" "" "" "695c3f483" "00000000" "00000330" "000004B0" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2064 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3096 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3204 | "C:\Users\admin\AppData\Roaming\DoD-PKE\InstallRoot\InstallRootUI.exe" | C:\Users\admin\AppData\Roaming\DoD-PKE\InstallRoot\InstallRootUI.exe | MsiExec.exe | ||||||||||||
User: admin Company: DoD-PKE Integrity Level: MEDIUM Description: InstallRootUI Exit code: 0 Version: 5.2.0.0 Modules
| |||||||||||||||
| 3532 | "C:\Windows\System32\msiexec.exe" /i "C:\Windows\InstallRoot_5.2x32_NonAdmin.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3764 | C:\Windows\system32\MsiExec.exe -Embedding C976A50EA7A4C0274356967DBB99DEFC C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3980 | C:\Windows\system32\MsiExec.exe -Embedding D9ADF41CDFE9F8D7C2036FDF5FF3D991 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 850
Read events
1 450
Write events
388
Delete events
12
Modification events
| (PID) Process: | (3532) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2064) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000005EC717E26878D50110080000500B0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2064) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000B8291AE26878D50110080000500B0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2064) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 24 | |||
| (PID) Process: | (2064) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000301183E26878D50110080000500B0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2064) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000008A7385E26878D50110080000B0090000E8030000010000000000000000000000DD28D184CE42EA4BB13605BF0E2C8D470000000000000000 | |||
| (PID) Process: | (3096) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000076D4A6E26878D501180C00004C0E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3096) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000076D4A6E26878D501180C0000500A0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3096) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000076D4A6E26878D501180C0000340A0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3096) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000076D4A6E26878D501180C0000580E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
40
Suspicious files
27
Text files
300
Unknown types
124
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3532 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\Cab4973.tmp | — | |
MD5:— | SHA256:— | |||
| 3532 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\Tar4984.tmp | — | |
MD5:— | SHA256:— | |||
| 3532 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\Cab4A02.tmp | — | |
MD5:— | SHA256:— | |||
| 3532 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\Tar4A03.tmp | — | |
MD5:— | SHA256:— | |||
| 3532 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\Cab5668.tmp | — | |
MD5:— | SHA256:— | |||
| 3532 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\Tar5669.tmp | — | |
MD5:— | SHA256:— | |||
| 3764 | MsiExec.exe | C:\Users\admin\AppData\Local\Temp\MSI5958.tmp | — | |
MD5:— | SHA256:— | |||
| 3532 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI5A82.tmp | — | |
MD5:— | SHA256:— | |||
| 3532 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI5AE0.tmp | — | |
MD5:— | SHA256:— | |||
| 3532 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI5B5E.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
10
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3532 | msiexec.exe | GET | 200 | 143.204.101.109:80 | http://http.fpki.gov/bridge/caCertsIssuedTofbca2016.p7c | US | cat | 19.8 Kb | shared |
3532 | msiexec.exe | GET | 200 | 143.204.101.109:80 | http://http.fpki.gov/bridge/caCertsIssuedTofbca2016.p7c | US | cat | 19.8 Kb | shared |
2064 | msiexec.exe | GET | 200 | 143.204.101.109:80 | http://http.fpki.gov/bridge/caCertsIssuedTofbca2016.p7c | US | cat | 19.8 Kb | shared |
3204 | InstallRootUI.exe | GET | 200 | 52.85.183.38:80 | http://http.fpki.gov/bridge/caCertsIssuedTofbca2016.p7c | US | cat | 19.8 Kb | shared |
3532 | msiexec.exe | GET | 200 | 143.204.101.109:80 | http://http.fpki.gov/bridge/caCertsIssuedTofbca2016.p7c | US | cat | 19.8 Kb | shared |
3204 | InstallRootUI.exe | GET | 301 | 52.222.167.217:80 | http://iase.disa.mil/pki-pke/data/ir4/DoD.ir4 | US | html | 183 b | whitelisted |
3204 | InstallRootUI.exe | GET | 301 | 52.222.167.217:80 | http://iase.disa.mil/pki-pke/data/ir4/JITC.ir4 | US | html | 183 b | whitelisted |
3204 | InstallRootUI.exe | GET | 301 | 54.230.95.103:80 | http://iase.disa.mil/pki-pke/data/ir4/JITC.ir4 | US | html | 183 b | whitelisted |
3204 | InstallRootUI.exe | GET | 301 | 54.230.95.103:80 | http://iase.disa.mil/pki-pke/data/ir4/ECA.ir4 | US | html | 183 b | whitelisted |
3204 | InstallRootUI.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/8CF427FD790C3AD166068DE81E57EFBB932272D4.crt | US | der | 1.06 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3532 | msiexec.exe | 143.204.101.109:80 | http.fpki.gov | — | US | unknown |
3204 | InstallRootUI.exe | 52.85.183.38:80 | http.fpki.gov | Amazon.com, Inc. | US | unknown |
3204 | InstallRootUI.exe | 54.230.95.103:80 | iase.disa.mil | Amazon.com, Inc. | US | unknown |
3204 | InstallRootUI.exe | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3204 | InstallRootUI.exe | 54.230.95.103:443 | iase.disa.mil | Amazon.com, Inc. | US | unknown |
3532 | msiexec.exe | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3204 | InstallRootUI.exe | 156.112.94.142:80 | ocsp.disa.mil | DoD Network Information Center | US | unknown |
3204 | InstallRootUI.exe | 52.222.167.217:80 | iase.disa.mil | Amazon.com, Inc. | US | unknown |
2064 | msiexec.exe | 143.204.101.109:80 | http.fpki.gov | — | US | unknown |
3204 | InstallRootUI.exe | 52.222.167.217:443 | iase.disa.mil | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
http.fpki.gov |
| shared |
www.download.windowsupdate.com |
| whitelisted |
iase.disa.mil |
| whitelisted |
ocsp.disa.mil |
| unknown |
Threats
Process | Message |
|---|---|
MsiExec.exe | DBGHELP: Symbol Search Path: .
|
MsiExec.exe | DBGHELP: Symbol Search Path: C:\Windows\system32
|
MsiExec.exe | DBGHELP: SymSrv load failure: symsrv.dll
|
MsiExec.exe | DBGHELP: C:\Windows\system32\ntdll.pdb - file not found
|
MsiExec.exe | DBGHELP: C:\Windows\system32\dll\ntdll.pdb - file not found
|
MsiExec.exe | DBGHELP: C:\Windows\system32\symbols\dll\ntdll.pdb - file not found
|
MsiExec.exe | DBGHELP: ntdll.pdb - file not found
|
MsiExec.exe | DBGHELP: ntdll - export symbols
|
MsiExec.exe | DBGHELP: Symbol Search Path: .
|
MsiExec.exe | DBGHELP: Symbol Search Path: C:\Windows\system32
|