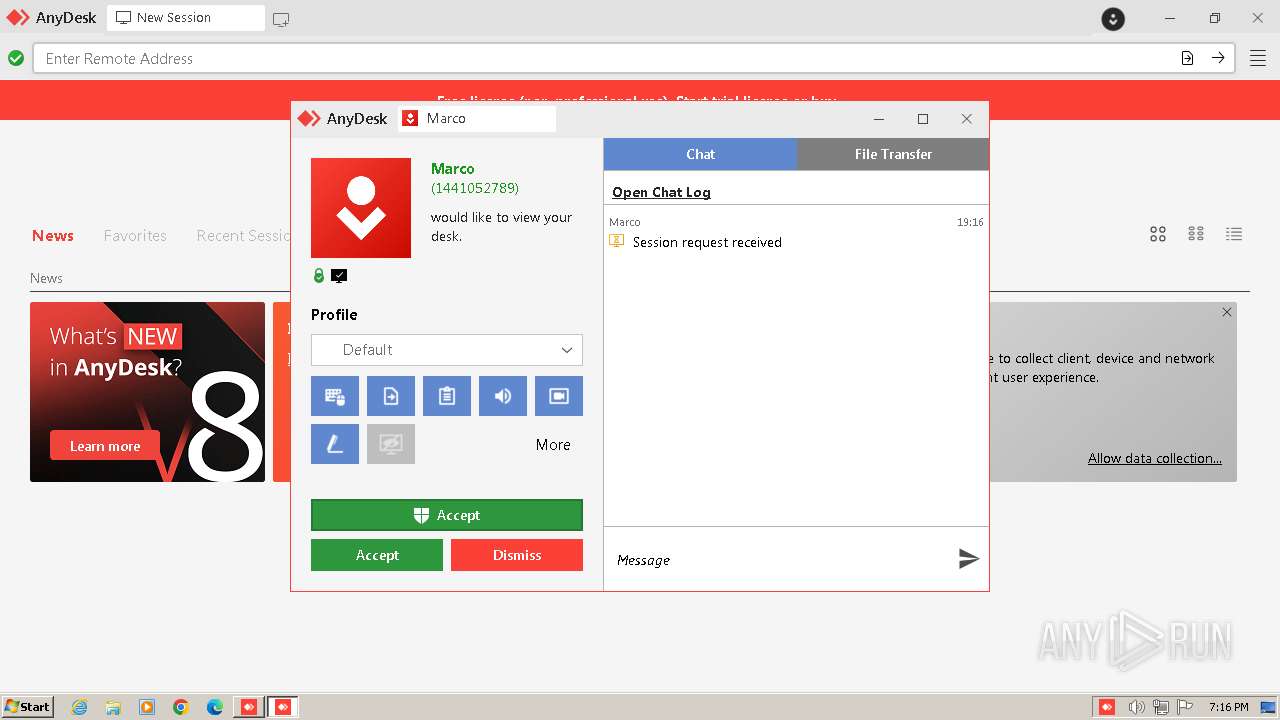
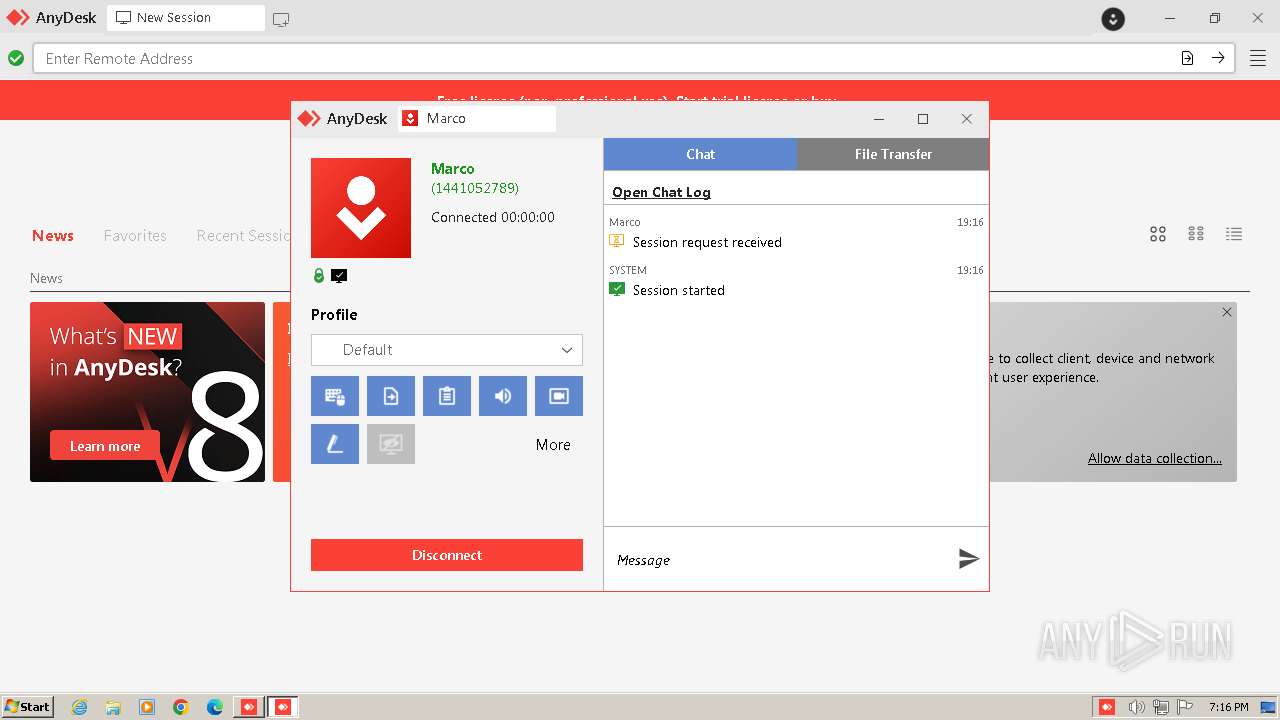
| File name: | AnyDesk.exe |
| Full analysis: | https://app.any.run/tasks/5526b81a-2786-4d99-99ac-d8653ccbea67 |
| Verdict: | Malicious activity |
| Analysis date: | April 21, 2024, 18:16:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 863FA58AA1FE8A88626625B191D4722E |
| SHA1: | E7FB4BF69BE5AC4583C0C02E26A17BD3CDEF4C02 |
| SHA256: | 45126297C07C6EF56B51440CD0DC30ACF7B3B938E2E9E656334886FE2F81F220 |
| SSDEEP: | 98304:6jO4INrECaBfiB7K0VzYi+Pu5whELA8WZK0/ToUAnJVRwgdt47WVBzGzTBAI9e04:nqmSqzDR |
MALICIOUS
Drops the executable file immediately after the start
- AnyDesk.exe (PID: 3768)
- AnyDesk.exe (PID: 2812)
SUSPICIOUS
Application launched itself
- AnyDesk.exe (PID: 3768)
- AnyDesk.exe (PID: 2812)
- AnyDesk.exe (PID: 1492)
Reads the Internet Settings
- AnyDesk.exe (PID: 2132)
- AnyDesk.exe (PID: 2812)
Executable content was dropped or overwritten
- AnyDesk.exe (PID: 2812)
Connects to unusual port
- AnyDesk.exe (PID: 2812)
Reads security settings of Internet Explorer
- AnyDesk.exe (PID: 2812)
Executes as Windows Service
- ehsched.exe (PID: 748)
Non-standard symbols in registry
- WINWORD.EXE (PID: 2420)
- WINWORD.EXE (PID: 2168)
- POWERPNT.EXE (PID: 3928)
INFO
Reads the computer name
- AnyDesk.exe (PID: 3768)
- AnyDesk.exe (PID: 2812)
- AnyDesk.exe (PID: 2132)
- AnyDesk.exe (PID: 3492)
- AnyDesk.exe (PID: 1492)
- AnyDesk.exe (PID: 1352)
- ehshell.exe (PID: 2232)
- ehtray.exe (PID: 948)
- ehrec.exe (PID: 2672)
- ehsched.exe (PID: 748)
Checks supported languages
- AnyDesk.exe (PID: 3768)
- AnyDesk.exe (PID: 2812)
- AnyDesk.exe (PID: 2132)
- AnyDesk.exe (PID: 3492)
- AnyDesk.exe (PID: 1492)
- AnyDesk.exe (PID: 1352)
- ehshell.exe (PID: 2232)
- ehsched.exe (PID: 748)
- ehtray.exe (PID: 948)
- ehrec.exe (PID: 2672)
Creates files or folders in the user directory
- AnyDesk.exe (PID: 3768)
- AnyDesk.exe (PID: 2812)
- ehshell.exe (PID: 2232)
Process checks whether UAC notifications are on
- AnyDesk.exe (PID: 3768)
Reads the machine GUID from the registry
- AnyDesk.exe (PID: 3768)
- AnyDesk.exe (PID: 2812)
- ehshell.exe (PID: 2232)
- ehtray.exe (PID: 948)
- ehrec.exe (PID: 2672)
- ehsched.exe (PID: 748)
Reads CPU info
- AnyDesk.exe (PID: 3768)
- ehshell.exe (PID: 2232)
Manual execution by a user
- ehshell.exe (PID: 2232)
- ehtray.exe (PID: 948)
- WINWORD.EXE (PID: 2420)
- WINWORD.EXE (PID: 2168)
- POWERPNT.EXE (PID: 3928)
- chrome.exe (PID: 2748)
- explorer.exe (PID: 1544)
Process checks computer location settings
- ehshell.exe (PID: 2232)
Creates files in the program directory
- ehshell.exe (PID: 2232)
- ehrec.exe (PID: 2672)
- ehsched.exe (PID: 748)
Application launched itself
- chrome.exe (PID: 2748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:28 10:30:11+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 10752 |
| InitializedDataSize: | 5292032 |
| UninitializedDataSize: | 19081216 |
| EntryPoint: | 0x1ce5 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.0.9.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | AnyDesk Software GmbH |
| FileDescription: | AnyDesk |
| FileVersion: | 8.0.9 |
| ProductName: | AnyDesk |
| ProductVersion: | 8 |
| LegalCopyright: | (C) 2022 AnyDesk Software GmbH |
Total processes
73
Monitored processes
28
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3428 --field-trial-handle=1196,i,10012604103331411864,11681021924867489904,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 748 | C:\Windows\ehome\ehsched.exe | C:\Windows\ehome\ehsched.exe | — | services.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Media Center Scheduler Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1284 --field-trial-handle=1196,i,10012604103331411864,11681021924867489904,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 948 | "C:\Windows\eHome\EhTray.exe" /nav:-2 | C:\Windows\ehome\ehtray.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Center Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3452 --field-trial-handle=1196,i,10012604103331411864,11681021924867489904,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1352 | "C:\Users\admin\AppData\Local\Temp\AnyDesk.exe" --backend | C:\Users\admin\AppData\Local\Temp\AnyDesk.exe | AnyDesk.exe | ||||||||||||
User: SYSTEM Company: AnyDesk Software GmbH Integrity Level: SYSTEM Description: AnyDesk Exit code: 1073807364 Version: 8.0.9 Modules
| |||||||||||||||
| 1492 | "C:\Users\admin\AppData\Local\Temp\AnyDesk.exe" --backproxy-system | C:\Users\admin\AppData\Local\Temp\AnyDesk.exe | AnyDesk.exe | ||||||||||||
User: admin Company: AnyDesk Software GmbH Integrity Level: HIGH Description: AnyDesk Exit code: 251659592 Version: 8.0.9 Modules
| |||||||||||||||
| 1544 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1812 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2144 --field-trial-handle=1196,i,10012604103331411864,11681021924867489904,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1888 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2164 --field-trial-handle=1196,i,10012604103331411864,11681021924867489904,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
31 808
Read events
30 469
Write events
698
Delete events
641
Modification events
| (PID) Process: | (2812) AnyDesk.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2812) AnyDesk.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2812) AnyDesk.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2812) AnyDesk.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1352) AnyDesk.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {D9144DCD-E998-4ECA-AB6A-DCD83CCBA16D} {0C6C4200-C589-11D0-999A-00C04FD655E1} 0xFFFF |
Value: 010000000000000047C4A0101894DA01 | |||
| (PID) Process: | (1352) AnyDesk.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {4E77131D-3629-431C-9818-C5679DC83E81} {0C6C4200-C589-11D0-999A-00C04FD655E1} 0xFFFF |
Value: 010000000000000047C4A0101894DA01 | |||
| (PID) Process: | (1352) AnyDesk.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {08244EE6-92F0-47F2-9FC9-929BAA2E7235} {0C6C4200-C589-11D0-999A-00C04FD655E1} 0xFFFF |
Value: 010000000000000047C4A0101894DA01 | |||
| (PID) Process: | (1352) AnyDesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\DirectDraw\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: AnyDesk.exe | |||
| (PID) Process: | (1352) AnyDesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\DirectDraw\MostRecentApplication |
| Operation: | write | Name: | ID |
Value: | |||
| (PID) Process: | (2232) ehshell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: ehshell.exe | |||
Executable files
1
Suspicious files
43
Text files
23
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2420 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVREFB7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3768 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\75fdacd8330bac18.customDestinations-ms~RF1ca010.TMP | binary | |
MD5:4CA1B6F61F6C7D86A2DF092DB2733AD6 | SHA256:CE6398DAFA154D1DD3445E2835DA6526C9ADE9F9235914E74AE83DD705803137 | |||
| 3768 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\75fdacd8330bac18.customDestinations-ms~RF1ca020.TMP | binary | |
MD5:63B7372C0B7FBEABC541DBCD720A6010 | SHA256:DC17CEBCD2B12014FDABA93B9DC6F1AFEE9AB6667492A3FFBAE026B29834446A | |||
| 3768 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\user.conf | text | |
MD5:A787C308BD30D6D844E711D7579BE552 | SHA256:8A395011A6A877D3BDD53CC8688EF146160DAB9D42140EB4A70716AD4293A440 | |||
| 948 | ehtray.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\R9BU43L5KJ6YY4F07WWF.temp | binary | |
MD5:B9BD716DE6739E51C620F2086F9C31E4 | SHA256:7116FF028244A01F3D17F1D3BC2E1506BC9999C2E40E388458F0CCCC4E117312 | |||
| 2812 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\connection_trace.txt | binary | |
MD5:6D1E0BD0768785D1343C7CAD603AB8F3 | SHA256:41299A4EA0B7FE15AA9E19D6A86C95EF55934D30BC5A67D4F1B43EEED709BBD1 | |||
| 3492 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\ad.trace | text | |
MD5:E8F5CC370511EA7459634D64CA67549E | SHA256:D812E755D3C481A10DCAA65D45EC565778394BDD2CE886CF05DE9752640E02BF | |||
| 2812 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\AnyDesk\system.conf | text | |
MD5:0C04AD1083DC5C7C45E3EE2CD344AE38 | SHA256:6452273C017DB7CBE0FFC5B109BBF3F8D3282FB91BFA3C5EABC4FB8F1FC98CB0 | |||
| 3768 | AnyDesk.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2QKYW619Q2GRHGOVO2X5.temp | binary | |
MD5:63B7372C0B7FBEABC541DBCD720A6010 | SHA256:DC17CEBCD2B12014FDABA93B9DC6F1AFEE9AB6667492A3FFBAE026B29834446A | |||
| 2812 | AnyDesk.exe | C:\Users\admin\AppData\Local\Temp\gcapi.dll | executable | |
MD5:1CE7D5A1566C8C449D0F6772A8C27900 | SHA256:73170761D6776C0DEBACFBBC61B6988CB8270A20174BF5C049768A264BB8FFAF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
23
DNS requests
22
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2812 | AnyDesk.exe | 195.181.174.174:443 | boot.net.anydesk.com | Datacamp Limited | DE | unknown |
2812 | AnyDesk.exe | 51.83.238.211:443 | relay-9c18490c.net.anydesk.com | OVH SAS | PL | unknown |
2812 | AnyDesk.exe | 130.25.156.152:64957 | — | Vodafone Italia S.p.A. | IT | unknown |
2812 | AnyDesk.exe | 130.25.156.152:7070 | — | Vodafone Italia S.p.A. | IT | unknown |
2748 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
2476 | chrome.exe | 142.250.185.163:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
boot.net.anydesk.com |
| unknown |
relay-9c18490c.net.anydesk.com |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
Threats
Process | Message |
|---|---|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|